记一次nginx服务器安全防护实战之“恶意目录探测攻击”防护
问题修复效果:
不再有类似的错误日志记录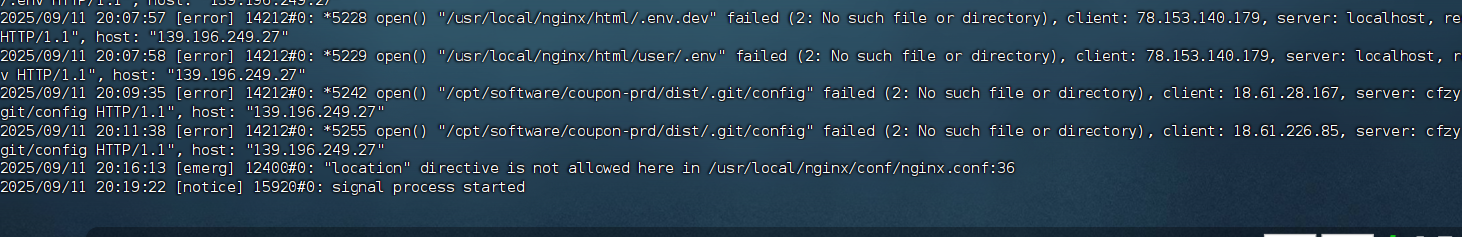
一.安全问题现象
nginx错误日志文件里有不明日志来源,具体显示如下:
2025/09/11 18:25:01 [error] 14212#0: *1949 open() "/usr/local/nginx/html/developmentserver/metadatauploader" failed (2: No such file or directory), client: 20.163.14.130, server: localhost, request: "GET /developmentserver/metadatauploader HTTP/1.1", host: "135.176.233.22"
2025/09/11 18:25:17 [error] 14212#0: *1953 open() "/usr/local/nginx/html/.git/config" failed (2: No such file or directory), client: 16.112.26.214, server: localhost, request: "GET /.git/config HTTP/1.1", host: "135.176.233.22"
2025/09/11 18:25:40 [error] 14212#0: *1957 open() "/usr/local/nginx/html/.git/config" failed (2: No such file or directory), client: 3.96.168.145, server: localhost, request: "GET /.git/config HTTP/1.1", host: "135.176.233.22"
2025/09/11 18:27:45 [error] 14212#0: *1970 open() "/opt/software/coupon-prd/dist/.git/config" failed (2: No such file or directory), client: 15.156.69.58, server: demo.top, request: "GET /.git/config HTTP/1.1", host: "135.176.233.22"
2025/09/11 18:29:18 [error] 14212#0: *1983 open() "/opt/software/coupon-prd/dist/.git/config" failed (2: No such file or directory), client: 16.112.19.219, server: demo.top, request: "GET /.git/config HTTP/1.1", host: "135.176.233.22"
2025/09/11 18:29:43 [error] 14212#0: *1987 open() "/usr/local/nginx/html/.git/config" failed (2: No such file or directory), client: 52.78.192.211, server: localhost, request: "GET /.git/config HTTP/1.1", host: "135.176.233.22"
2025/09/11 18:49:46 [error] 14212#0: *2083 open() "/opt/software/coupon-prd/dist/.git/config" failed (2: No such file or directory), client: 16.112.32.172, server: demo.top, request: "GET /.git/config HTTP/1.1", host: "135.176.233.22"
2025/09/11 18:55:46 [error] 14212#0: *4904 open() "/opt/software/coupon-prd/dist/.git/config" failed (2: No such file or directory), client: 52.78.192.211, server: demo.top, request: "GET /.git/config HTTP/1.1", host: "135.176.233.22"
2025/09/11 19:00:56 [error] 14212#0: *5100 open() "/opt/software/coupon-prd/dist/.git/config" failed (2: No such file or directory), client: 18.61.29.13, server: demo.top, request: "GET /.git/config HTTP/1.1", host: "135.176.233.22"
2025/09/11 19:03:23 [error] 14212#0: *5102 open() "/usr/local/nginx/html/favicon.ico" failed (2: No such file or directory), client: 59.82.21.145, server: localhost, request: "GET /favicon.ico HTTP/1.1", host: "csp.demo.top"二.问题分析
由于nginx是部署了一个系统 的后台,使用了https,但实际上并没有部署代码,更没有安装git,所以团队内人员没有对该服务器进行git访问的可能,故考虑是被攻击。
查证,ip确实不属于本团队成员的ip,由此 明确该错误日志表明是有被攻击的情况
三.深入分析被攻击类型
继续进行安全威胁确认
上面的日志显示是对.git目录进行访问和配置文件进行访问,该类问题属于探测攻击,即日志表明服务器正在遭受恶意目录探测攻击:
- 攻击模式:攻击者扫描
.git/config文件(包含敏感信息如远程仓库凭证) - 攻击特征:
- 目标路径:
/opt/software/coupon-prd/dist/.git/config和/usr/local/nginx/html/.git/config - 恶意IP:
16.112.19.219(美国)、52.78.192.211(韩国)、16.112.32.172(美国)
- 目标路径:
- 风险等级:高危(可能导致源码泄露、服务器沦陷)
四.紧急处置方案(立即执行)
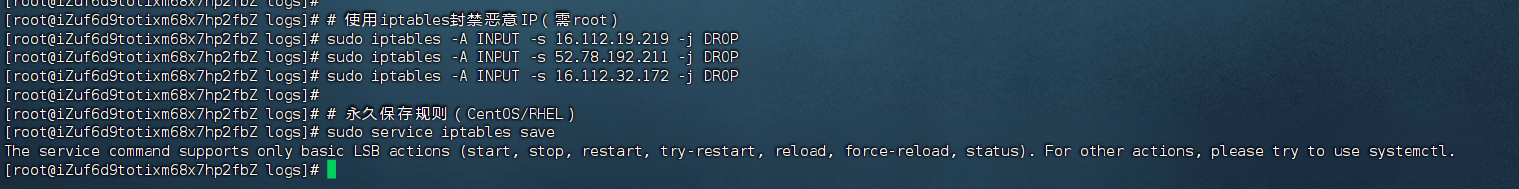
第一步:阻断攻击源
# 使用iptables封禁恶意IP(需root)
sudo iptables -A INPUT -s 16.112.19.219 -j DROP
sudo iptables -A INPUT -s 52.78.192.211 -j DROP
sudo iptables -A INPUT -s 16.112.32.172 -j DROP# 永久保存规则(CentOS/RHEL)
sudo service iptables save
第二步:清除敏感文件
# 删除暴露的.git目录(关键防护)
sudo find /opt/software/coupon-prd/dist -name ".git" -exec rm -rf {} \; 2>/dev/null
sudo rm -rf /usr/local/nginx/html/.git# 全局扫描残留.git目录
sudo find / -type d -name ".git" -print 2>/dev/null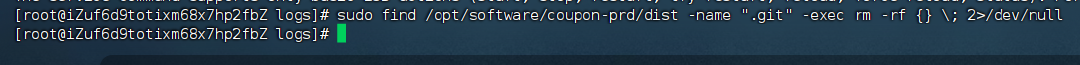
第三步:配置Nginx防护规则
# 在nginx配置中增加以下防护(/etc/nginx/nginx.conf)
server {# 禁止访问所有隐藏文件(含.git)location ~ /\. {deny all;return 403;}# 特定防护:阻断Git探测location ~ \.git/config {return 444; # 静默丢弃连接access_log off;log_not_found off;}
}由于本文不涉及,故不需要处理
重载配置:
sudo nginx -t && sudo nginx -s reload
五.深度安全加固(防止二次攻击)
1. 服务器级防护
# 安装入侵检测系统(AIDE)
sudo yum install aide -y
sudo aide --init
sudo mv /var/lib/aide/aide.db.new.gz /var/lib/aide/aide.db.gz# 配置每日自动扫描
echo "0 3 * * * /usr/sbin/aide --check" | sudo tee -a /etc/crontab由于会安装新组件,需要先评估对服务器的影响。由于本服务器不涉及git代码,故跳过该步骤
2. Web应用加固
# 添加WAF防护(ModSecurity)
sudo yum install mod_security -y
sudo cp /usr/share/mod_security/modsecurity.conf-recommended /etc/nginx/modsecurity.conf# 加载OWASP核心规则集
sudo git clone https://github.com/SpiderLabs/owasp-modsecurity-crs /etc/nginx/owasp-crs
sudo echo "Include /etc/nginx/owasp-crs/crs-setup.conf" >> /etc/nginx/modsecurity.conf
sudo echo "Include /etc/nginx/owasp-crs/rules/*.conf" >> /etc/nginx/modsecurity.conf同样需要评估对服务器的影响,仍然跳过
3. 自动化攻击阻断
创建脚本 /usr/local/bin/block_scanners.sh:
#!/bin/bash
# 自动封禁扫描.git的IP
tail -n 100 /var/log/nginx/error.log | grep '\.git/config' | awk '{print \$14}' | cut -d: -f1 | sort | uniq | while read ip; doif ! iptables -L -n | grep -q $ip; theniptables -A INPUT -s $ip -j DROPecho "[$(date)] Blocked malicious IP: $ip" >> /var/log/git_scan_block.logfi
done添加定时任务:
(crontab -l ; echo "*/5 * * * * /usr/local/bin/block_scanners.sh") | crontab -
sudo chmod +x /usr/local/bin/block_scanners.sh该方案不仅可以阻止git的问题,其他文件或者类型的攻击也可以使用该方法,自动化阻击。
六.安全验证流程
- 日志监控:
# 尝试触发防护规则(应返回403) curl -I http://localhost/.git/config curl -I http://localhost/.env - 日志监控:
# 实时监控攻击行为 sudo tail -f /var/log/nginx/access.log | grep -E '403|444'# 或者 sudo tail -f /usr/local/nginx/logs/error.log -
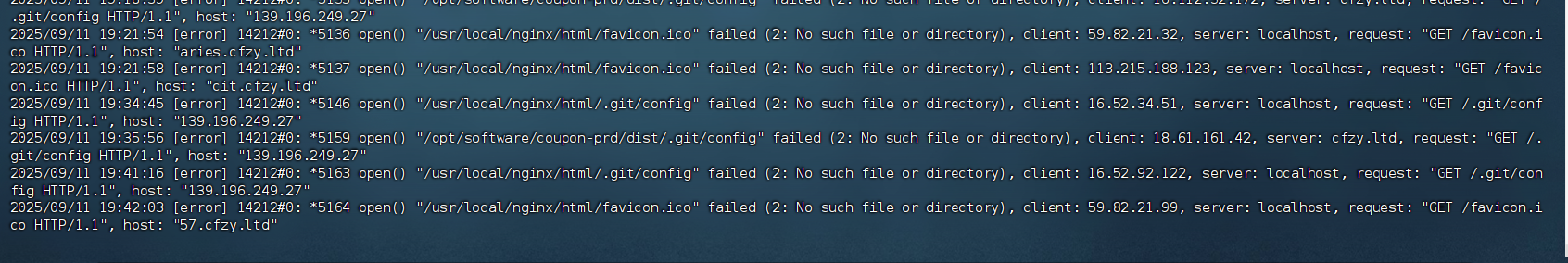
- 漏洞扫描:
# 使用工具扫描残留风险 sudo yum install nikto -y nikto -h http://localhost涉及对线上环境的扫描,生成环境有系统运行请谨慎使用,避免扫描对服务器性能造成影响
七.总结与防护体系
由于是线上环境,先将攻击ip进行紧急封禁,对第四步进行处理。然后做好深度加固方案,杜绝此类问题的发生。
| 防护层级 | 实施措施 | 防护效果 |
|---|---|---|
| 网络层 | IP实时封禁 | 即时阻断攻击源 |
| 应用层 | Nginx规则防护 | 防止.git文件泄露 |
| 系统层 | 文件完整性监控 | 检测非法文件变更 |
| 主动防御 | WAF规则集 | 阻断OWASP Top 10攻击 |
后续建议:
- 立即更改所有Git仓库密码(包括代码托管平台)
- 审查服务器是否有后门:
sudo rkhunter --check - 部署云防火墙(如阿里云云盾、腾讯云防火墙)
- 每月进行安全审计:
sudo lynis audit system
最后检查:执行
sudo iptables -L -n确认恶意IP已在DROP链中,观察Nginx错误日志是否仍有.git探测记录。
