Kubernetes Ingress与安全机制
Kubernetes Ingress与安全机制详解
- 前言
- 一、Ingress 服务
- 1. Ingress 简介
- 1.1 Service 的作用回顾
- 1.2 外部访问集群服务的常见方式
- 2. Ingress 的组成
- 2.1 Ingress(规则定义对象)
- 2.2 Ingress Controller(规则执行者 / 流量入口)
- 三、Ingress 工作原理
- 四、Ingress 的部署方式
- 1. DaemonSet + HostNetwork + nodeSelector
- 2. Deployment + Service(type=NodePort)
- 五、Ingress 的安全机制
- 1. TLS 加密
- 2. 基本认证(BasicAuth)
- 六、常见检查与排错要点
- 结语
前言
在当今的云原生时代,Kubernetes(简称K8s)已经成为了容器编排领域的事实标准。随着微服务架构的广泛应用,如何有效地管理和暴露服务成为了运维和开发人员面临的重要挑战。Kubernetes 提供了多种服务暴露方式,其中 Ingress 作为一种七层反向代理,因其灵活性和高效性,逐渐成为了服务暴露的主流选择。本文将深入探讨 Kubernetes Ingress 的概念、组成、工作原理及其部署方式,并结合实际案例,帮助读者全面理解和掌握 Ingress 的使用。
一、Ingress 服务
1. Ingress 简介
1.1 Service 的作用回顾
在 Kubernetes 中,Service 主要承担两个角色:
- 对集群内部:持续跟踪 Pod 的变化,维护一个稳定的 Endpoints 列表,为集群内其他组件提供服务发现机制。
- 对集群外部:作为访问 Pod 的统一入口,类似于传统的负载均衡器。
但需要注意的是:
Pod IP 和 Service 的 ClusterIP 仅在 Kubernetes 集群内部可访问,外部用户无法直接通过这些 IP 访问服务。
因此,为了将集群内部的服务暴露给外部用户,Kubernetes 提供了多种方案:
1.2 外部访问集群服务的常见方式
| 方式 | 说明 | 适用场景 | 缺点/限制 |
|---|---|---|---|
| NodePort | 在每个节点的 IP 上开放一个静态端口(范围:30000-32767),将流量转发到对应的 Service | 适用于测试、小规模环境 | 端口管理复杂,不适合生产大规模部署 |
| LoadBalancer | 通过云厂商的负载均衡器(LB)将外部流量导入到 Service,由云平台自动创建和管理 LB | 适合公有云环境 | 依赖云厂商,通常会产生额外费用 |
| externalIPs | 给 Service 指定一个外部可达的 IP,当该 IP 的流量到达集群节点时,会被转发到对应的 Service | 适用于自有 IP 资源的场景 | 需自行管理 IP 和路由,不常用 |
| Ingress(推荐) | 基于 HTTP/HTTPS 的七层路由,通过域名或路径将请求路由到不同的 Service,只需一个或少量公网 IP 即可管理多个服务 | 适合生产环境,尤其是需要基于域名或路径做路由管理的场景 | 需要额外部署 Ingress Controller |
✅ 小结:
- Ingress 的核心价值在于:使用少量的公网 IP 或负载均衡器,通过 HTTP/HTTPS 协议,基于域名或路径,智能地路由到后端多个 Service。
- Ingress 本身只是规则定义(YAML 配置),真正负责流量转发的是 Ingress Controller。
2. Ingress 的组成
Ingress 的完整功能由两个核心部分组成:
2.1 Ingress(规则定义对象)
- 是什么:Ingress 是一个 Kubernetes 的API 资源对象,通过 YAML 文件定义,描述如何将外部请求(基于域名 / URL 路径)路由到对应的 Service。
- 功能包括:
- 基于 域名 的虚拟主机路由(如
example.com→ service-A) - 基于 URL 路径 的路由(如
/api→ service-B,/web→ service-C) - 支持 TLS/SSL 加密(HTTPS)
- 提供基础的负载均衡能力(由 Ingress Controller 实现)
- 基于 域名 的虚拟主机路由(如
- 关键点:Ingress 只定义规则,不负责实际流量转发,它需要依赖 Ingress Controller 来生效。
📌 示例用途:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:name: example-ingress
spec:rules:- host: example.comhttp:paths:- path: /pathType: Prefixbackend:service:name: my-serviceport:number: 80
-------------------------------------------------------------------------------------
kubectl create deployment myapp-demo1 --image=soscscs/myapp:v1 --replicas=2 --port=80
kubectl expose deployment myapp-demo1 --port=80 --target-port=80
kubectl expose deployment myapp-demo1 --port=80 --target-port=80 --dry-run=client -o yaml > ch.yaml
apiVersion: v1
kind: Service
metadata:labels:app: myapp-demo1name: myapp-demo1
spec:externalIPs:- 192.168.10.12ports:- port: 80protocol: TCPtargetPort: 80selector:app: myapp-demo1
status:
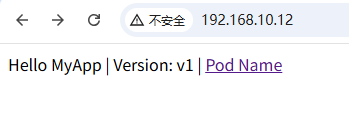
2.2 Ingress Controller(规则执行者 / 流量入口)
-
是什么:Ingress Controller 是一个运行在集群中的组件(通常以 Pod 形式存在),它的职责是:
- 监听集群中的 Ingress 资源变化
- 根据 Ingress 中定义的规则,动态生成负载均衡配置(如 Nginx 配置)
- 实际接收外部流量,并按照规则将请求转发到对应的 Service,实现反向代理和负载均衡
-
特点:
- 不是 Kubernetes 内置组件,需要单独部署
- 常见的实现有:
- 官方维护:https://github.com/kubernetes/ingress-nginx(基于 Nginx)、https://cloud.google.com/kubernetes-engine/docs/concepts/ingress(Google Cloud 专用)
- 第三方:Traefik、HAProxy Ingress、Istio Gateway、Caddy 等
- 通常以 Pod 形式运行在集群中,内部包含:
- 一个控制器进程(负责监听 API Server,感知 Ingress 变化,生成配置)
- 一个反向代理程序(如 Nginx,负责实际流量处理)
-
工作流程简述:
- 用户提交 Ingress YAML 到 Kubernetes API Server
- Ingress Controller 监听到变化
- 根据 Ingress 规则,动态生成或更新代理配置(如 Nginx.conf)
- 重新加载或热更新代理服务
- 外部用户通过指定的域名 / IP 访问,流量被 Ingress Controller 接收并路由到后端 Service
✅ 总结:
- Ingress = 路由规则(YAML 配置)
- Ingress Controller = 流量入口 + 规则执行者(真正干活的,提供反向代理、负载均衡、SSL 等能力)
- 没有 Ingress Controller,Ingress 规则不会生效!
| 组件 | 作用 | 是否必须 | 备注 |
|---|---|---|---|
| Service | 提供集群内服务发现 & 集群内访问入口 | ✅ 必须 | 是后端真实服务的抽象 |
| Ingress | 定义外部访问的路由规则(域名 / 路径 → Service) | ✅ 需要使用 Ingress 功能时 | 本身不转发流量 |
| Ingress Controller | 实现 Ingress 规则,提供反向代理、负载均衡、SSL 等能力 | ✅ 必须(如果要用 Ingress) | 需单独部署,比如 ingress-nginx |
三、Ingress 工作原理
Ingress 的工作原理主要包括以下几个步骤:
- 感知规则变化:Ingress Controller 与 APIServer 交互,动态地去感知 Ingress 规则变化。
- 生成配置:读取规则并按自定义模板生成 Nginx 配置。
- 写入配置:将生成的 Nginx 配置写入 Ingress Controller 的 Pod 中,通常位于 /etc/nginx.conf 文件中。
- 生效配置:执行 reload 使配置生效,实现按域名分流与动态更新。
四、Ingress 的部署方式
Ingress 的部署方式主要有三种:Deployment + Service(type=LoadBalancer)、DaemonSet + HostNetwork + nodeSelector 和 Deployment + Service(type=NodePort)。
1. DaemonSet + HostNetwork + nodeSelector
这种方式在特定节点以 DaemonSet 方式部署 Controller,并使用 HostNetwork 与宿主机网络打通,直接占用宿主机 80/443 端口。该方式链路最短、性能最好,适合大并发生产环境。
#
ingree.contro.tar ingree.contro.tar.gz mandatory.yaml
docker load -i ingree.contro.tar
--------------------------------------------------------------------------------------
kubectl label node node2 ingress=true
kubectl get nodes --show-labels
vim mandatory.yaml
apiVersion: v1
kind: Namespace
metadata:name: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
apiVersion: v1
metadata:name: nginx-configurationnamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
apiVersion: v1
metadata:name: tcp-servicesnamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
apiVersion: v1
metadata:name: udp-servicesnamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
---
apiVersion: v1
kind: ServiceAccount
metadata:name: nginx-ingress-serviceaccountnamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRole
metadata:name: nginx-ingress-clusterrolelabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
rules:- apiGroups:- ""resources:- configmaps- endpoints- nodes- pods- secretsverbs:- list- watch- apiGroups:- ""resources:- nodesverbs:- get- apiGroups:- ""resources:- servicesverbs:- get- list- watch- apiGroups:- "extensions"- "networking.k8s.io"resources:- ingressesverbs:- get- list- watch- apiGroups:- ""resources:- eventsverbs:- create- patch- apiGroups:- "extensions"- "networking.k8s.io"resources:- ingresses/statusverbs:- update
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: Role
metadata:name: nginx-ingress-rolenamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
rules:- apiGroups:- ""resources:- configmaps- pods- secrets- namespacesverbs:- get- apiGroups:- ""resources:- configmapsresourceNames:# Defaults to "<election-id>-<ingress-class>"# Here: "<ingress-controller-leader>-<nginx>"# This has to be adapted if you change either parameter# when launching the nginx-ingress-controller.- "ingress-controller-leader-nginx"verbs:- get- update- apiGroups:- ""resources:- configmapsverbs:- create- apiGroups:- ""resources:- endpointsverbs:- get
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: RoleBinding
metadata:name: nginx-ingress-role-nisa-bindingnamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
roleRef:apiGroup: rbac.authorization.k8s.iokind: Rolename: nginx-ingress-role
subjects:- kind: ServiceAccountname: nginx-ingress-serviceaccountnamespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:name: nginx-ingress-clusterrole-nisa-bindinglabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
roleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: nginx-ingress-clusterrole
subjects:- kind: ServiceAccountname: nginx-ingress-serviceaccountnamespace: ingress-nginx
---
apiVersion: apps/v1
kind: Deployment
metadata:name: nginx-ingress-controllernamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
spec:
# replicas: 1selector:matchLabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginxtemplate:metadata:labels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginxannotations:prometheus.io/port: "10254"prometheus.io/scrape: "true"spec:hostNetwork: truenodeSelector:ingress: "true"serviceAccountName: nginx-ingress-serviceaccountcontainers:- name: nginx-ingress-controllerimage: quay.io/kubernetes-ingress-controller/nginx-ingress-controller:0.25.0args:- /nginx-ingress-controller- --configmap=$(POD_NAMESPACE)/nginx-configuration- --tcp-services-configmap=$(POD_NAMESPACE)/tcp-services- --udp-services-configmap=$(POD_NAMESPACE)/udp-services- --publish-service=$(POD_NAMESPACE)/ingress-nginx- --annotations-prefix=nginx.ingress.kubernetes.iosecurityContext:allowPrivilegeEscalation: truecapabilities:drop:- ALLadd:- NET_BIND_SERVICE# www-data -> 33runAsUser: 33env:- name: POD_NAMEvalueFrom:fieldRef:fieldPath: metadata.name- name: POD_NAMESPACEvalueFrom:fieldRef:fieldPath: metadata.namespaceports:- name: httpcontainerPort: 80- name: httpscontainerPort: 443livenessProbe:failureThreshold: 3httpGet:path: /healthzport: 10254scheme: HTTPinitialDelaySeconds: 10periodSeconds: 10successThreshold: 1timeoutSeconds: 10readinessProbe:failureThreshold: 3httpGet:path: /healthzport: 10254scheme: HTTPperiodSeconds: 10successThreshold: 1timeoutSeconds: 10
---
--------------------------------------------------------------------------------------
vim svc-nginx.yaml
apiVersion: apps/v1
kind: Deployment
metadata:name: nginx-app
spec:replicas: 2selector:matchLabels:app: nginxtemplate:metadata:labels:app: nginxspec:containers:- name: nginximage: nginximagePullPolicy: IfNotPresentports:- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:name: nginx-app-svc
spec:type: ClusterIPports:- protocol: TCPport: 80targetPort: 80selector:app: nginx
--------------------------------------------------------------------------------------
vim ingress.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:name: nginx-app-ingress
spec:rules:- host: www.nh.comhttp:paths:- path: /pathType: Prefix # 也可使用 Exactbackend:service:name: nginx-app-svcport:number: 80
--------------------------------------------------------------------------------------
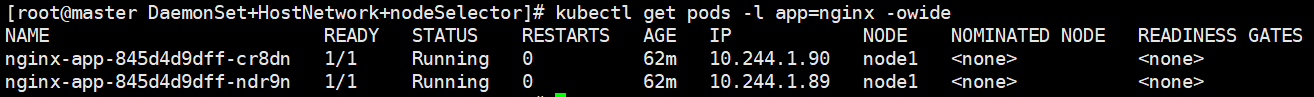
kubectl get pod -n ingress-nginx -o wide
kubectl get pods -l app=nginx -o wide
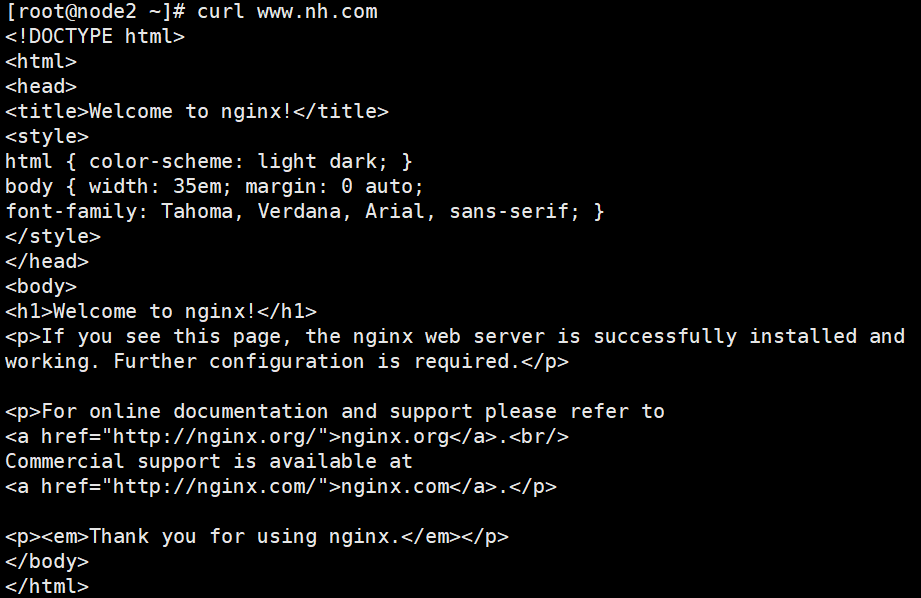
2. Deployment + Service(type=NodePort)
这种方式以 Deployment 部署 Controller,并创建 NodePort Service 暴露。由于 NodePort 是随机端口,通常前置一层负载均衡。该方式多一层 NAT,大流量场景可能影响性能。
docker load -i ingress-controller-0.30.0.tar
# mandatory.yaml
apiVersion: v1
kind: Namespace
metadata:name: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
---
apiVersion: v1
kind: ConfigMap
metadata:name: nginx-configurationnamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
---
apiVersion: v1
kind: ConfigMap
metadata:name: tcp-servicesnamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
---
apiVersion: v1
kind: ConfigMap
metadata:name: udp-servicesnamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
---
apiVersion: v1
kind: ServiceAccount
metadata:name: nginx-ingress-serviceaccountnamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:name: nginx-ingress-clusterrolenamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
rules:- apiGroups:- ""resources:- configmaps- endpoints- nodes- pods- secretsverbs:- list- watch- apiGroups:- ""resources:- nodesverbs:- get- apiGroups:- ""resources:- servicesverbs:- get- list- watch- apiGroups:- ""resources:- eventsverbs:- create- patch- apiGroups:- "extensions"- "networking.k8s.io"resources:- ingressesverbs:- get- list- watch- apiGroups:- "extensions"- "networking.k8s.io"resources:- ingresses/statusverbs:- update
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:name: nginx-ingress-rolenamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
rules:- apiGroups:- ""resources:- configmaps- pods- secrets- namespacesverbs:- get- apiGroups:- ""resources:- configmapsresourceNames:- "ingress-controller-leader-nginx"verbs:- get- update- apiGroups:- ""resources:- configmapsverbs:- create- apiGroups:- ""resources:- endpointsverbs:- get
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:name: nginx-ingress-role-nisa-bindingnamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
roleRef:apiGroup: rbac.authorization.k8s.iokind: Rolename: nginx-ingress-role
subjects:- kind: ServiceAccountname: nginx-ingress-serviceaccountnamespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:name: nginx-ingress-clusterrole-nisa-bindinglabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
roleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: nginx-ingress-clusterrole
subjects:- kind: ServiceAccountname: nginx-ingress-serviceaccountnamespace: ingress-nginx
---
apiVersion: apps/v1
kind: Deployment
metadata:name: nginx-ingress-controllernamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
spec:replicas: 1selector:matchLabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginxtemplate:metadata:labels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginxannotations:prometheus.io/port: "10254"prometheus.io/scrape: "true"spec:terminationGracePeriodSeconds: 300serviceAccountName: nginx-ingress-serviceaccountnodeSelector:kubernetes.io/os: linuxcontainers:- name: nginx-ingress-controllerimage: quay.io/kubernetes-ingress-controller/nginx-ingress-controller:0.30.0 args:- /nginx-ingress-controller- --configmap=$(POD_NAMESPACE)/nginx-configuration- --tcp-services-configmap=$(POD_NAMESPACE)/tcp-services- --udp-services-configmap=$(POD_NAMESPACE)/udp-services- --publish-service=$(POD_NAMESPACE)/ingress-nginx- --annotations-prefix=nginx.ingress.kubernetes.iosecurityContext:allowPrivilegeEscalation: truecapabilities:drop:- ALLadd:- NET_BIND_SERVICErunAsUser: 101env:- name: POD_NAMEvalueFrom:fieldRef:fieldPath: metadata.name- name: POD_NAMESPACEvalueFrom:fieldRef:fieldPath: metadata.namespaceports:- name: httpcontainerPort: 80protocol: TCP- name: httpscontainerPort: 443protocol: TCPlivenessProbe:failureThreshold: 3httpGet:path: /healthzport: 10254scheme: HTTPinitialDelaySeconds: 10periodSeconds: 10successThreshold: 1timeoutSeconds: 10readinessProbe:failureThreshold: 3httpGet:path: /healthzport: 10254scheme: HTTPperiodSeconds: 10successThreshold: 1timeoutSeconds: 10lifecycle:preStop:exec:command:- /wait-shutdown
---
apiVersion: v1
kind: LimitRange
metadata:name: ingress-nginxnamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
spec:limits:- min:memory: 90Micpu: 100mtype: Container
======================================================================================
# service-nodeport.yaml
apiVersion: v1
kind: Service
metadata:name: ingress-nginxnamespace: ingress-nginxlabels:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
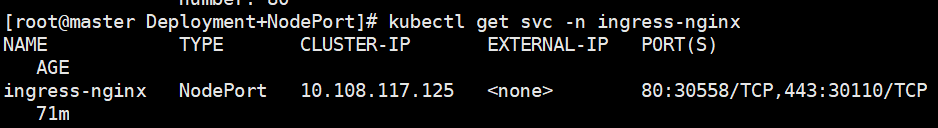
spec:type: NodePortports:- name: httpport: 80targetPort: 80protocol: TCP# nodePort: 30080 # 可选,如需固定端口则取消注释并设置- name: httpsport: 443targetPort: 443protocol: TCP# nodePort: 30443 # 可选selector:app.kubernetes.io/name: ingress-nginxapp.kubernetes.io/part-of: ingress-nginx
======================================================================================
#ingress-svc.yaml
apiVersion: apps/v1
kind: Deployment
metadata:name: nginx-app
spec:replicas: 2selector:matchLabels:app: nginxtemplate:metadata:labels:app: nginx # 必须与下方 Service 的 selector 一致spec:containers:- name: nginximage: nginximagePullPolicy: IfNotPresentports:- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:name: nginx-svc
spec:ports:- port: 80targetPort: 80protocol: TCPselector:app: nginx
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:name: nginx-test
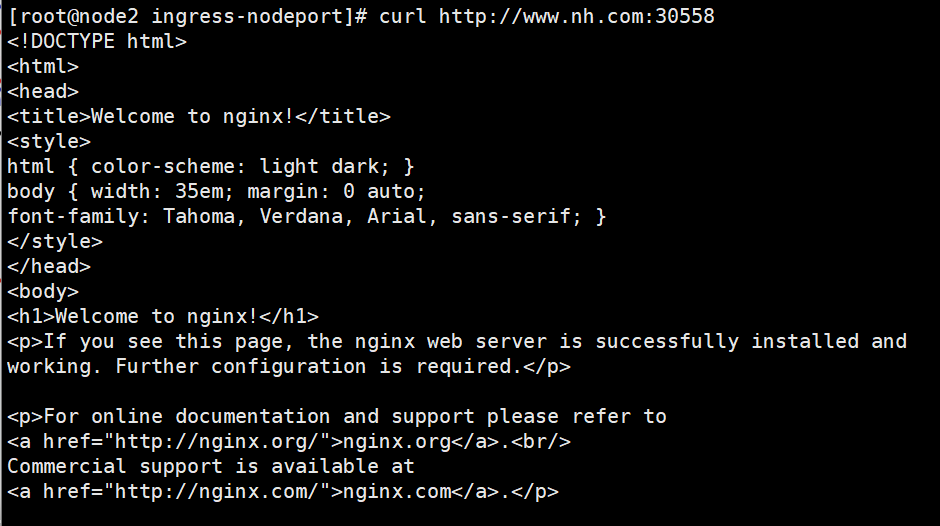
spec:rules:- host: www.nh.comhttp:paths:- path: /pathType: Prefixbackend:service:name: nginx-svcport:number: 80
apiVersion: apps/v1
kind: Deployment
metadata:name: deployment1
spec:replicas: 2selector:matchLabels:name: nginx1template:metadata:labels:name: nginx1spec:containers:- name: nginx1image: soscscs/myapp:v1imagePullPolicy: IfNotPresentports:- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:name: svc-1
spec:ports:- port: 80targetPort: 80protocol: TCPselector:name: nginx1
---
# deployment2.yaml(v2)
apiVersion: apps/v1
kind: Deployment
metadata:name: deployment2
spec:replicas: 2selector:matchLabels:name: nginx2template:metadata:labels:name: nginx2spec:containers:- name: nginx2image: soscscs/myapp:v2imagePullPolicy: IfNotPresentports:- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:name: svc-2
spec:ports:- port: 80targetPort: 80protocol: TCPselector:name: nginx2---
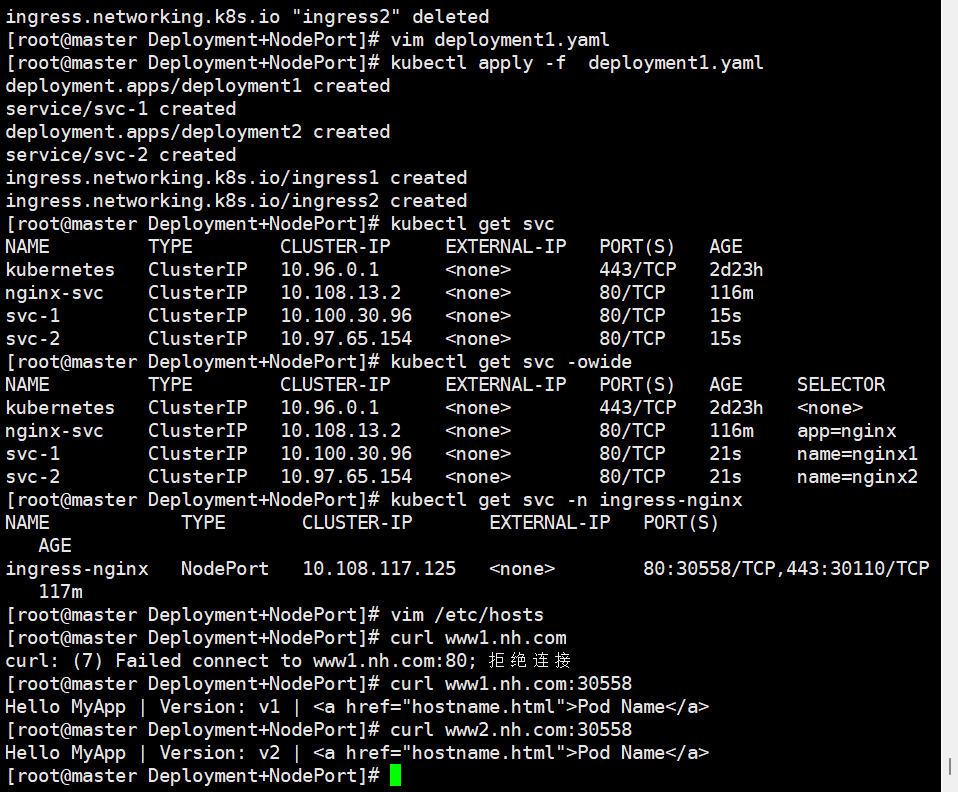
# ingress-nginx.yaml(双主机名)
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:name: ingress1
spec:rules:- host: www1.nh.comhttp:paths:- path: /pathType: Prefixbackend:service:name: svc-1port:number: 80
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:name: ingress2
spec:rules:- host: www2.nh.comhttp:paths:- path: /pathType: Prefixbackend:service:name: svc-2port:number: 80
五、Ingress 的安全机制
在 Ingress 的使用过程中,安全性是一个不可忽视的重要方面。以下是一些常见的安全机制:
1. TLS 加密
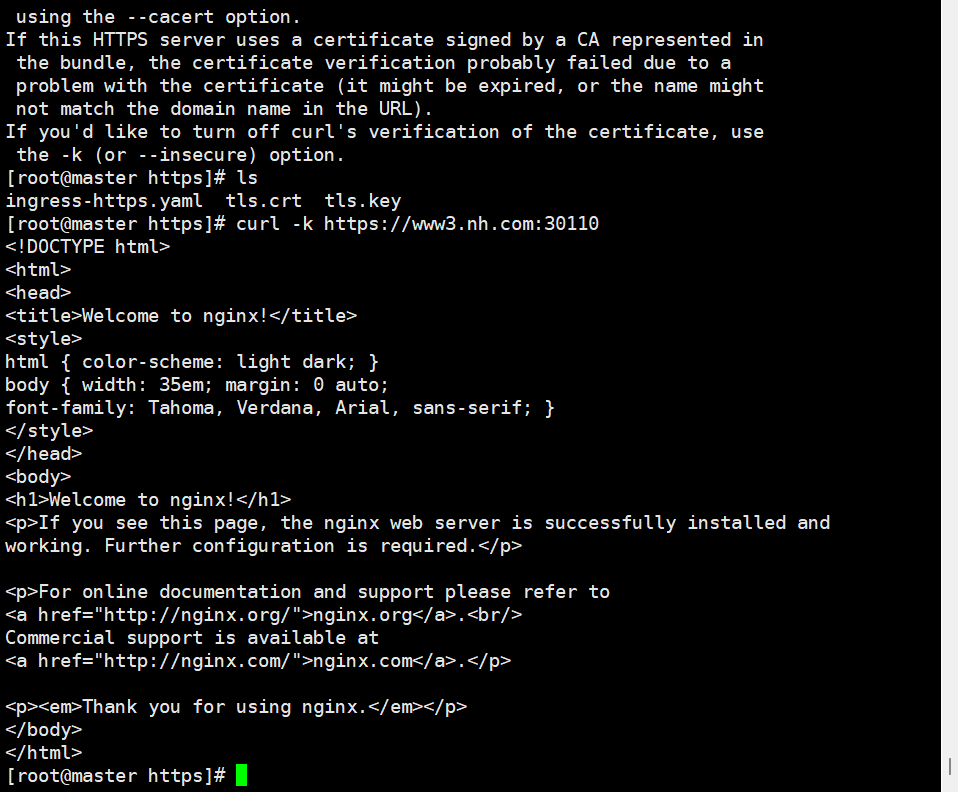
通过配置 TLS 证书,Ingress 可以实现 HTTPS 访问,确保数据传输的加密和安全性。例如,可以通过生成自签证书并创建相应的 Secret,然后在 Ingress 配置中引用该 Secret 来实现 HTTPS 代理访问。
mkdir -p /opt/ingress-nodeport/https && cd /opt/ingress-nodeport/https
openssl req -x509 -sha256 -nodes -days 365 \-newkey rsa:2048 -keyout tls.key -out tls.crt \-subj "/CN=nginxsvc/O=nginxsvc"# 创建 secret
kubectl create secret tls tls-secret --key tls.key --cert tls.crt
kubectl get secret tls-secret -o yaml
apiVersion: apps/v1
kind: Deployment
metadata:name: nginx-app
spec:replicas: 2selector:matchLabels:name: nginxtemplate:metadata:labels:name: nginxspec:containers:- name: nginximage: nginxports:- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:name: nginx-svc
spec:ports:- port: 80targetPort: 80protocol: TCPselector:name: nginx
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:name: nginx-https
spec:tls:- hosts:- www3.nh.comsecretName: tls-secretrules:- host: www3.nh.comhttp:paths:- path: /pathType: Prefixbackend:service:name: nginx-svcport:number: 80
2. 基本认证(BasicAuth)
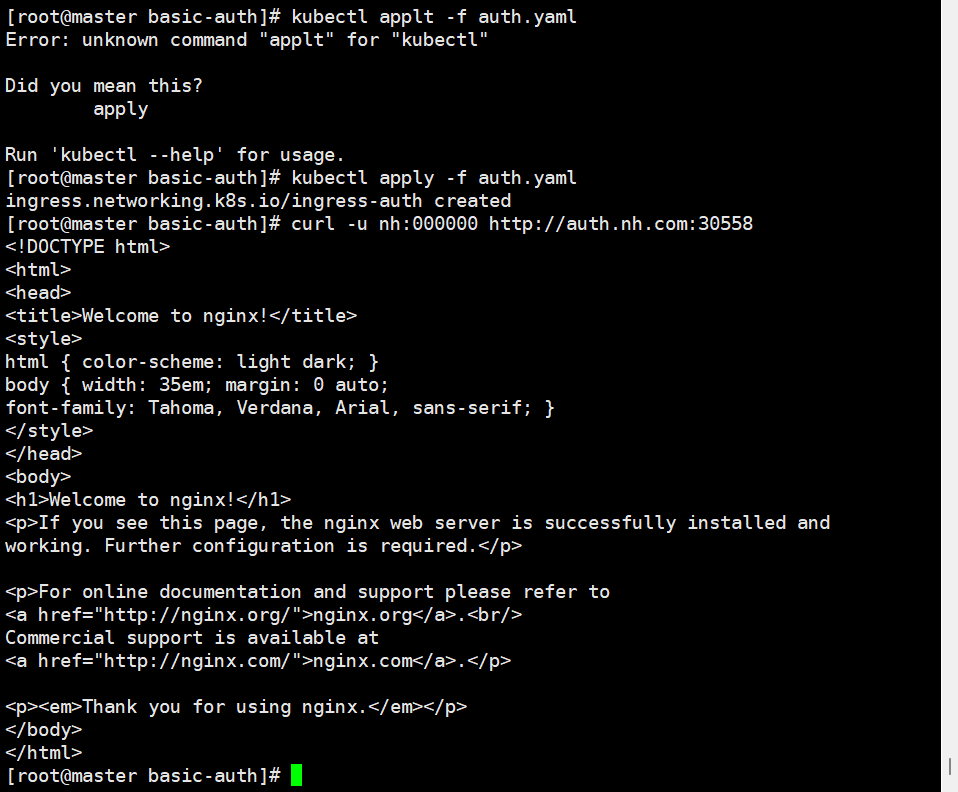
Ingress 支持基本认证,通过配置 BasicAuth,可以对访问者进行身份验证,确保只有授权用户才能访问服务。例如,可以使用 htpasswd 生成认证文件,并将其作为 Secret 引用到 Ingress 配置中。
mkdir -p /opt/ingress-nodeport/basic-auth && cd /opt/ingress-nodeport/basic-auth
yum -y install httpd
htpasswd -c auth nh
kubectl create secret generic basic-auth --from-file=auth
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:name: ingress-authannotations:nginx.ingress.kubernetes.io/auth-type: basicnginx.ingress.kubernetes.io/auth-secret: basic-authnginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - nh'
spec:rules:- host: auth.nh.comhttp:paths:- path: /pathType: Prefixbackend:service:name: nginx-svcport:number: 80
六、常见检查与排错要点
在使用 Ingress 过程中,可能会遇到各种问题,以下是一些常见的检查与排错要点:
- 查看 Controller 运行与端口:通过
kubectl get pod -n ingress-nginx -o wide和netstat -lntp | grep nginx等命令,检查 Ingress Controller 的运行状态和端口监听情况。 - 进入 Pod 检查 Nginx 配置:通过
kubectl exec -it <controller-pod> -n ingress-nginx -- /bin/bash命令,进入 Ingress Controller Pod,检查生成的 Nginx 配置文件,确保配置正确。 - 调度失败:如果遇到调度失败问题,可以检查节点标签和 YAML 配置,确保节点标签匹配或删除不必要的 nodeSelector。
结语
Kubernetes Ingress 作为服务暴露的重要工具,提供了灵活、高效的 HTTP/HTTPS 服务管理能力。通过本文的介绍,我们了解了 Ingress 的概念、组成、工作原理及其部署方式,并结合实际案例,展示了如何在不同环境中部署和配置 Ingress。同时,我们也探讨了 Ingress 的安全机制和常见检查与排错要点,帮助读者在实际使用中更好地应对各种挑战。
在生产环境中,合理选择和配置 Ingress,结合多节点部署、前置负载均衡、监控告警及安全加固等措施,可以有效提升服务的可用性、性能和安全性。希望本文能为读者在 Kubernetes Ingress 的使用和优化过程中提供有价值的参考和指导。
