防火墙配置
1.拓扑图
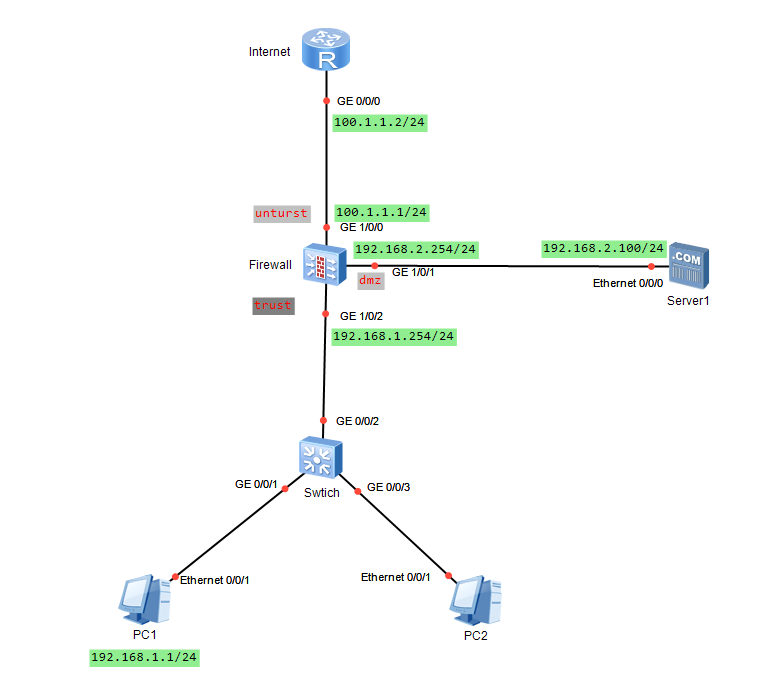
画了两个版本的拓扑图,前一个被误删了,这个版本只是端口号不一致,配置一样的。
2.配置要求
(1)防火墙接口的IP地址如拓扑所示,将接口划入相应的安全区域。
(2)内网主机PC1可以主动访问Internet,但Internet无法主动访问PC1。
(3)出口防火墙进行NAT,NAT公网地址池100.1.1.10 - 100.1.1.20。
(4)Internet可以通过公网地址100.1.1.100/24 访问目的地址为 192.168.2.100/24 的内部Web服务。
3.配置步骤
配置PC的IP地址
配置Internet的IP地址
<Huawei>sys
[Huawei]sysname Internet
[Internet]interface g0/0/0
[Internet-GigabitEthernet0/0/0]ip add 100.1.1.2 24
[Internet-GigabitEthernet0/0/0]q
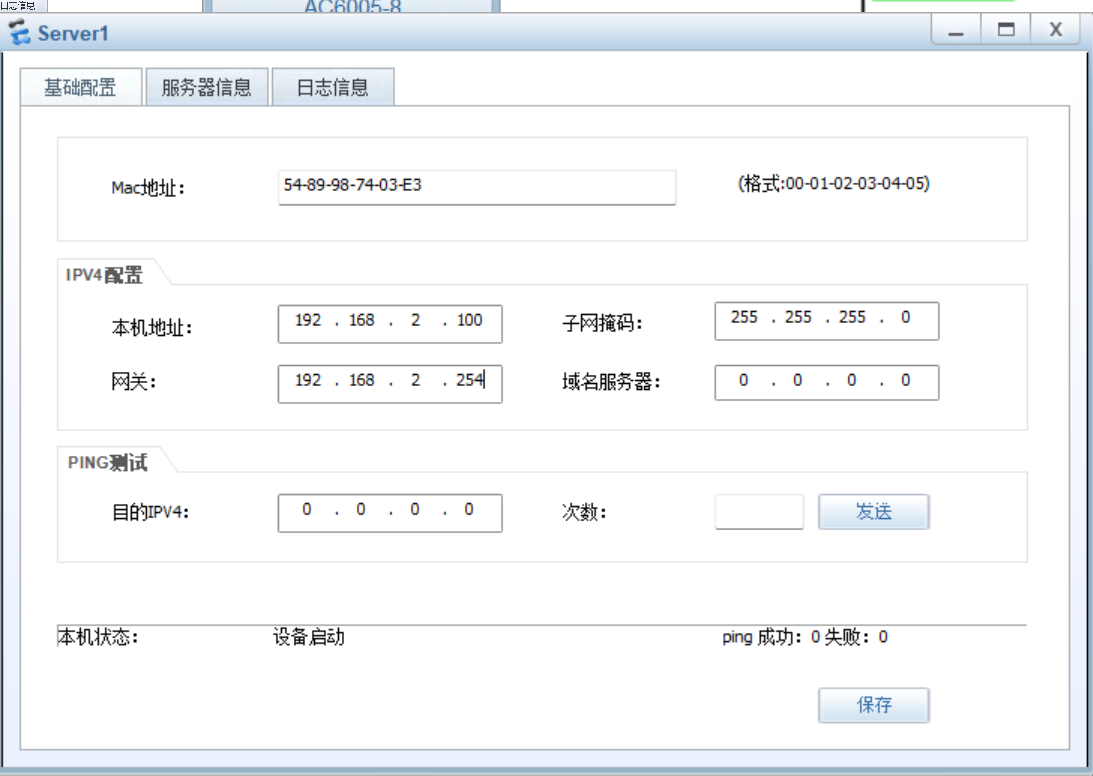
配置服务器
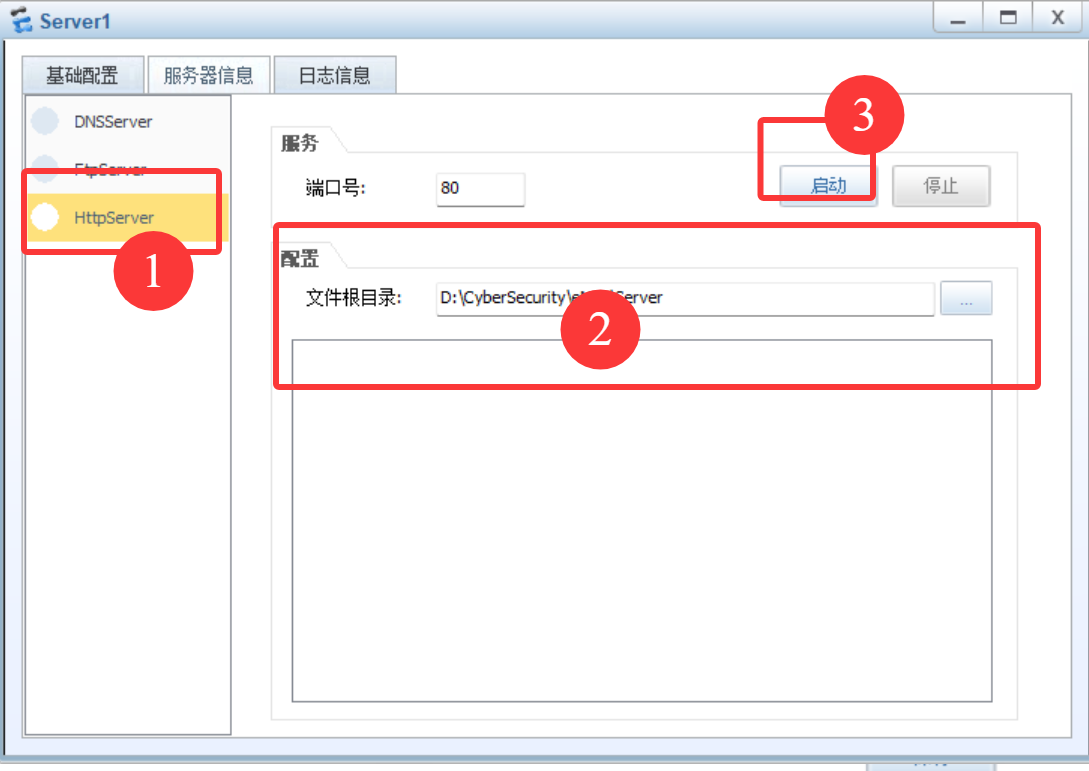
配置防火墙
密码在Admin@123和Admin@1234互相切换Username:admin
Password:
The password needs to be changed. Change now? [Y/N]: y
Please enter old password:
Please enter new password:
Error: The password is invalid.
The password needs to be changed. Change now? [Y/N]:
Error: Please choose 'YES' or 'NO' first before pressing 'Enter'. [Y/N]:y
Please enter old password:
Please enter new password:
Please confirm new password: Info: Your password has been changed. Save the change to survive a reboot.
*************************************************************************
* Copyright (C) 2014-2018 Huawei Technologies Co., Ltd. *
* All rights reserved. *
* Without the owner's prior written consent, *
* no decompiling or reverse-engineering shall be allowed. *
*************************************************************************
配置防火墙的接口IP地址
<USG6000V1>sys
[Firewall]int g1/0/3
[Firewall-GigabitEthernet1/0/3]ip add 100.1.1.1 24
[USG6000V1-GigabitEthernet1/0/3]int g1/0/0
[USG6000V1-GigabitEthernet1/0/0]ip add 192.168.1.254 24
[USG6000V1-GigabitEthernet1/0/0]int g1/0/1
[USG6000V1-GigabitEthernet1/0/1]ip add 192.168.2.254 24
[USG6000V1-GigabitEthernet1/0/1]q
[USG6000V1]sysname Firewall
[Firewall]
将防火墙的三个接口加入到安全域中[Firewall]firewall zone trust
[Firewall-zone-trust]add interface GigabitEthernet 1/0/0
[Firewall-zone-trust]q[Firewall]firewall zone untrust
[Firewall-zone-untrust]add interface GigabitEthernet 0/0/0Error: The interface has been added to trust security zone.
[Firewall-zone-untrust]q[Firewall]firewall zone dmz
[Firewall-zone-dmz]add interface GigabitEthernet 1/0/1
[Firewall-zone-dmz]q
配置安全策略
[Firewall]security-policy
[Firewall-policy-security]rule ?copy Indicate copy a rulemove Indicate move a rulename Indicate configure rule namerename Indicate rename a rule[Firewall-policy-security]rule name trust_to_untrust
[Firewall-policy-security-rule-trust_to_untrust]source-zone trust
[Firewall-policy-security-rule-trust_to_untrust]destination-zone untrust
[Firewall-policy-security-rule-trust_to_untrust]source-address 192.168.1.0 24
[Firewall-policy-security-rule-trust_to_untrust]destination-address any[Firewall-policy-security-rule-trust_to_untrust]action ?deny Indicate the rule action denypermit Indicate the rule action permit
[Firewall-policy-security-rule-trust_to_untrust]action permit
[Firewall-policy-security-rule-trust_to_untrust]q
在PC1上做测试,不能正常访问,要在防火墙上做NATPC>ping 100.1.1.1Ping 100.1.1.1: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!
在防火墙中配置NAT
1.配置NAT的地址池,开启端口转换
[Firewall]nat address-group addressgroup1
[Firewall-address-group-addressgroup1]mode pat
配置公网的地址池
[Firewall-address-group-addressgroup1]section 0 100.1.1.10 100.1.1.20
[Firewall-address-group-addressgroup1]q2.配置源NAT策略,实现私网指定网段访问Internet时自动进行源地址转换。[Firewall]nat-policy
[Firewall-policy-nat]rule name policy_nat1
[Firewall-policy-nat-rule-policy_nat1]source-zone trust
[Firewall-policy-nat-rule-policy_nat1]destination-zone untrust
[Firewall-policy-nat-rule-policy_nat1]source-address 192.168.1.0 24
[Firewall-policy-nat-rule-policy_nat1]destination-address any[Firewall-policy-nat-rule-policy_nat1]action source-nat address-group addressgroup1
[Firewall-policy-nat-rule-policy_nat1]q
[Firewall-policy-nat][Firewall]display firewall session table
2025-09-07 13:30:39.320 Current Total Sessions : 0
[Firewall]
ping 不通是因为被禁止ping了,需要手动开启:
[Firewall-GigabitEthernet1/0/2]dis this
2025-09-08 15:17:39.590
#
interface GigabitEthernet1/0/2undo shutdownip address 192.168.1.254 255.255.255.0
#
return
[Firewall-GigabitEthernet1/0/2]service-manage ping ?deny deny permit permit
[Firewall-GigabitEthernet1/0/2]service-manage ping permit 在PC1上测试:
PC>ping 100.1.1.2Ping 100.1.1.2: 32 data bytes, Press Ctrl_C to break
From 100.1.1.2: bytes=32 seq=1 ttl=254 time=31 ms
From 100.1.1.2: bytes=32 seq=2 ttl=254 time=32 msping通之后:[Firewall]dis firewall session table
2025-09-08 15:19:31.830 Current Total Sessions : 0
[Firewall]dis firewall session table
2025-09-08 15:19:42.530 Current Total Sessions : 5[Firewall]dis firewall session table
2025-09-08 15:21:08.050 Current Total Sessions : 8icmp VPN: public --> public 192.168.1.1:26356[100.1.1.20:2055] --> 100.1.1.2:2048icmp VPN: public --> public 192.168.1.1:24564[100.1.1.20:2050] --> 100.1.1.2:2048icmp VPN: public --> public 192.168.1.1:25076[100.1.1.20:2052] --> 100.1.1.2:2048icmp VPN: public --> public 192.168.1.1:24308[100.1.1.20:2049] --> 100.1.1.2:2048icmp VPN: public --> public 192.168.1.1:25844[100.1.1.20:2053] --> 100.1.1.2:2048icmp VPN: public --> public 192.168.1.1:24820[100.1.1.20:2051] --> 100.1.1.2:2048icmp VPN: public --> public 192.168.1.1:26100[100.1.1.20:2054] --> 100.1.1.2:2048icmp VPN: public --> public 192.168.1.1:23796[100.1.1.20:2048] --> 100.1.1.2:2048icmp VPN: public --> public 192.168.1.1:4340 --> 192.168.1.254:2048icmp VPN: public --> public 192.168.1.1:3828 --> 192.168.1.254:2048icmp VPN: public --> public 192.168.1.1:3572 --> 192.168.1.254:2048icmp VPN: public --> public 192.168.1.1:4084 --> 192.168.1.254:2048icmp VPN: public --> public 192.168.1.1:3316 --> 192.168.1.254:2048配置服务器的访问
测试无法访问PC>ping 192.168.2.100Ping 192.168.2.100: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!配置防火墙:
[Firewall]security-policy
[Firewall-policy-security]rule name trust_to_dmz
[Firewall-policy-security-rule-trust_to_dmz]source-zone trust
[Firewall-policy-security-rule-trust_to_dmz]destination-zone dmz
[Firewall-policy-security-rule-trust_to_dmz]action permit
[Firewall-policy-security-rule-trust_to_dmz]q在PC上测试:
PC>ping 192.168.2.100Ping 192.168.2.100: 32 data bytes, Press Ctrl_C to break
From 192.168.2.100: bytes=32 seq=1 ttl=254 time=46 ms
From 192.168.2.100: bytes=32 seq=2 ttl=254 time=32 ms端口映射配置
[Firewall]nat server protocol tcp global 100.1.1.100 80 inside 192.168.2.100 ?<0-65535> Port numberCHARgen Character generator (19)X.X.X.X Local IP address of the last server hostany Any protocol (0)bgp Border Gateway Protocol (179)cmd Remote commands (rcmd, 514)daytime Daytime (13)discard Discard (9)domain Domain Name Service (53)echo Echo (7)exec Exec (rsh, 512)finger Finger (79)ftp File Transfer Protocol (21)gopher Gopher (70)h323 H323 (1719)hostname NIC hostname server (101)ils Internet Location Service (1002)irc Internet Relay Chat (194)klogin Kerberos login (543)kshell Kerberos shell (544)login Login (rlogin, 513)lpd Printer service (515)mms Mircosoft Media Server Protocol(1755)netbios-ssn NETBIOS Session Service (139)nntp Network News Transport Protocol (119)pop2 Post Office Protocol v2 (109)pop3 Post Office Protocol v3 (110)pptp Point to Point Tunnel Protocol (1723)rpc Remote Procedure Call (135)rtsp Real Time Streaming Protocol (554)sccp Cisco Skinny Client Control Protocol (2000)sip Session Initiation Protocol (5060)smtp Simple Mail Transport Protocol (25)sqlnet SQLNET(1521)sunrpc Sun Remote Procedure Call (111)tacacs TAC Access Control System (49)talk Talk (517)telnet Telnet (23)time Time (37)uucp Unix-to-Unix Copy Program (540)whois Nicname (43)www World Wide Web (HTTP, 80)[Firewall]nat server protocol tcp global 100.1.1.100 80 inside 192.168.2.100 www[Firewall]security-policy
[Firewall-policy-security]rule name untrust_to_dmz
[Firewall-policy-security-rule-untrust_to_dmz]source-zone untrust
[Firewall-policy-security-rule-untrust_to_dmz]destination-zone dmz
[Firewall-policy-security-rule-untrust_to_dmz]destination-address 192.168.2.100 32
[Firewall-policy-security-rule-untrust_to_dmz]action permit 在互联网上测试<Internet>telnet 100.1.1.100 80Press CTRL_] to quit telnet modeTrying 100.1.1.100 ...Connected to 100.1.1.100 ...[Firewall]dis firewall session table
2025-09-08 15:36:01.160 Current Total Sessions : 1http VPN: public --> public 100.1.1.2:49187 --> 100.1.1.100:80[192.168.2.100:80]