Nacos敏感信息加密
<dependency><groupId>com.github.ulisesbocchio</groupId><artifactId>jasypt-spring-boot-starter</artifactId><version>3.0.5</version>
</dependency>运行main 方法完成敏感信息加密:
java -cp jasypt-1.9.3.jar org.jasypt.intf.cli.JasyptPBEStringEncryptionCLI input="my-secret-db-password" password=your-strong-key algorithm=PBEWithMD5AndDES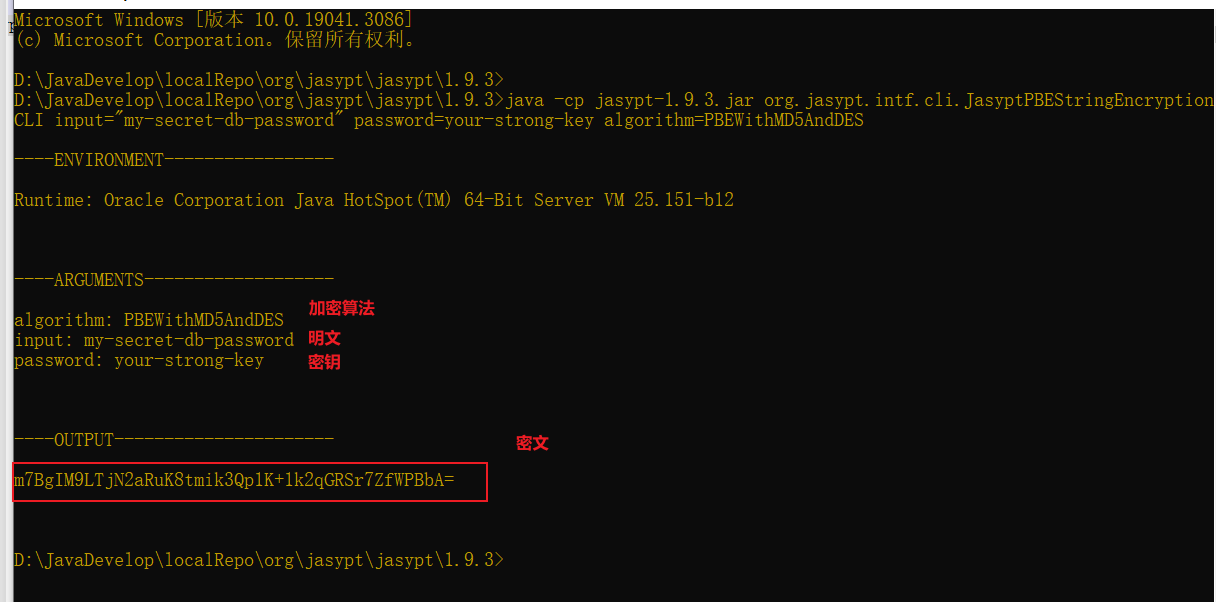
application.yml 配置加密信息
# Nacos 配置
spring:datasource:password: ENC(m7BgIM9LTjN2aRuK8tmik3Qp1K+1k2qGRSr7ZfWPBbA=) # 加密后的源码默认开启springboot自动配置:
@Configuration
@ConditionalOnProperty(name = {"jasypt.encryptor.bootstrap"},havingValue = "true",matchIfMissing = true
)
@Import({EnableEncryptablePropertiesConfiguration.class})
public class JasyptSpringCloudBootstrapConfiguration {public JasyptSpringCloudBootstrapConfiguration() {}
}
应用启动时:
java -Djasypt.encryptor.password=your-strong-key -jar app.jarGitee(码云)的 CI/CD(Gitee Go 或企业版流水线)支持 加密环境变量,这是最安全的方式
➕ 添加变量:
| 变量名 | 值 | 是否加密 |
|---|---|---|
JASYPT_PASSWORD | your-strong-key-123 | ✅ 是(加密) |
步骤 2:在 gitee-ci.yml(或流水线脚本)中使用
jobs:build:runs-on: ubuntu-lateststeps:- name: Checkout codeuses: actions/checkout@v3- name: Set up JDK 17uses: actions/setup-java@v3with:java-version: 17distribution: 'temurin'- name: Build with Mavenrun: mvn clean package -DskipTests- name: Run App with Jasyptrun: java -Djasypt.encryptor.password=${{ secrets.JASYPT_PASSWORD }} -jar target/app.jarJenkins(自建)
设置:
- 进入:
Manage Jenkins -> Credentials -> 添加 Secret Text 在 Pipeline 中使用:
pipeline {agent anyenvironment {JASYPT_PASSWORD = credentials('jasypt-pass')}stages {stage('Deploy') {steps {sh 'java -Djasypt.encryptor.password=$JASYPT_PASSWORD -jar app.jar'}}} }
