Linux 下逆向解析 VNC Server 密码文件为明文密码(逆向解析passwd)
描述
一般来说,vnc密码都会存储与.vnc文件中的,一个为passwd文件,这个文件是二进制的,一般普通文本编辑后,看不到明文密码
这个操作需要根据开源仓库来配合解析。
Git仓库地址:https://github.com/BetterDefender/vncpwd.git
如果打不开,下载国内地址:https://download.csdn.net/download/u014641168/91961334
动手能力强的,不用下载了,可以看附上的代码。
操作
1、克隆或解压操作
git clone https://github.com/BetterDefender/vncpwd.git
如果打不开,下载我提供的国内地址
tar -zxvf vncpwd.tar.gz -C ./
2、编译
cd vncpwd
yum install -y gcc
在 vncpwd 文件夹内执行 make 命令编译(源码中已包含 Makefile,无需手动写编译指令)
make
如果出现以下错误,请更换命令
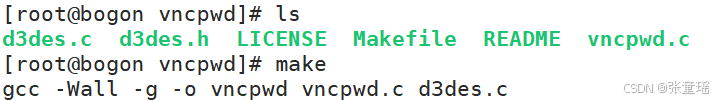
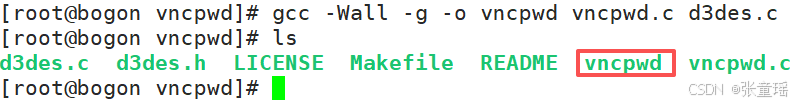
gcc -Wall -g -o vncpwd vncpwd.c d3des.c
编译完成后,目录下会多出个 vncpwd 文件。
3、运行解密
./vncpwd [你的vnc密码文件]
示例
./vncpwd /opt/test/passwd
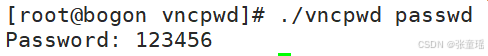
附上所有代码
d3des.c
/* D3DES (V5.09) - ** A portable, public domain, version of the Data Encryption Standard.** Written with Symantec's THINK (Lightspeed) C by Richard Outerbridge.* Thanks to: Dan Hoey for his excellent Initial and Inverse permutation* code; Jim Gillogly & Phil Karn for the DES key schedule code; Dennis* Ferguson, Eric Young and Dana How for comparing notes; and Ray Lau,* for humouring me on. ** THIS SOFTWARE PLACED IN THE PUBLIC DOMAIN BY THE AUTHOUR* 920825 19:42 EDST** Copyright (c) 1988,1989,1990,1991,1992 by Richard Outerbridge.* (GEnie : OUTER; CIS : [71755,204]) Graven Imagery, 1992.*//*Changed: 2003-02-21 by Patrik Karlsson to reflect VNC changes tobytebit[] array. See comment below*/
#include "d3des.h"static void scrunch(unsigned char *, unsigned long *);
static void unscrun(unsigned long *, unsigned char *);
static void desfunc(unsigned long *, unsigned long *);
static void cookey(unsigned long *);static unsigned long KnL[32] = { 0L };
static unsigned long KnR[32] = { 0L };
static unsigned long Kn3[32] = { 0L };
static unsigned char Df_Key[24] = {0x01,0x23,0x45,0x67,0x89,0xab,0xcd,0xef,0xfe,0xdc,0xba,0x98,0x76,0x54,0x32,0x10,0x89,0xab,0xcd,0xef,0x01,0x23,0x45,0x67 };/*
static unsigned short bytebit[8] = {0200, 0100, 040, 020, 010, 04, 02, 01 };
*/
/* changed by patrik 2003-02-21 */
static unsigned short bytebit[8] = {01, 02, 04, 010, 020, 040, 0100, 0200 };static unsigned long bigbyte[24] = {0x800000L, 0x400000L, 0x200000L, 0x100000L,0x80000L, 0x40000L, 0x20000L, 0x10000L,0x8000L, 0x4000L, 0x2000L, 0x1000L,0x800L, 0x400L, 0x200L, 0x100L,0x80L, 0x40L, 0x20L, 0x10L,0x8L, 0x4L, 0x2L, 0x1L };/* Use the key schedule specified in the Standard (ANSI X3.92-1981). */static unsigned char pc1[56] = {56, 48, 40, 32, 24, 16, 8, 0, 57, 49, 41, 33, 25, 17,9, 1, 58, 50, 42, 34, 26, 18, 10, 2, 59, 51, 43, 35,62, 54, 46, 38, 30, 22, 14, 6, 61, 53, 45, 37, 29, 21,13, 5, 60, 52, 44, 36, 28, 20, 12, 4, 27, 19, 11, 3 };static unsigned char totrot[16] = {1,2,4,6,8,10,12,14,15,17,19,21,23,25,27,28 };static unsigned char pc2[48] = {13, 16, 10, 23, 0, 4, 2, 27, 14, 5, 20, 9,22, 18, 11, 3, 25, 7, 15, 6, 26, 19, 12, 1,40, 51, 30, 36, 46, 54, 29, 39, 50, 44, 32, 47,43, 48, 38, 55, 33, 52, 45, 41, 49, 35, 28, 31 };void deskey(key, edf) /* Thanks to James Gillogly & Phil Karn! */
unsigned char *key;
short edf;
{int i, j, l, m, n;unsigned char pc1m[56], pcr[56];unsigned long kn[32];for ( j = 0; j < 56; j++ ) {l = pc1[j];m = l & 07;pc1m[j] = (key[l >> 3] & bytebit[m]) ? 1 : 0;}for( i = 0; i < 16; i++ ) {if( edf == DE1 ) m = (15 - i) << 1;else m = i << 1;n = m + 1;kn[m] = kn[n] = 0L;for( j = 0; j < 28; j++ ) {l = j + totrot[i];if( l < 28 ) pcr[j] = pc1m[l];else pcr[j] = pc1m[l - 28];}for( j = 28; j < 56; j++ ) {l = j + totrot[i];if( l < 56 ) pcr[j] = pc1m[l];else pcr[j] = pc1m[l - 28];}for( j = 0; j < 24; j++ ) {if( pcr[pc2[j]] ) kn[m] |= bigbyte[j];if( pcr[pc2[j+24]] ) kn[n] |= bigbyte[j];}}cookey(kn);return;}static void cookey(raw1)
unsigned long *raw1;
{unsigned long *cook, *raw0;unsigned long dough[32];int i;cook = dough;for( i = 0; i < 16; i++, raw1++ ) {raw0 = raw1++;*cook = (*raw0 & 0x00fc0000L) << 6;*cook |= (*raw0 & 0x00000fc0L) << 10;*cook |= (*raw1 & 0x00fc0000L) >> 10;*cook++ |= (*raw1 & 0x00000fc0L) >> 6;*cook = (*raw0 & 0x0003f000L) << 12;*cook |= (*raw0 & 0x0000003fL) << 16;*cook |= (*raw1 & 0x0003f000L) >> 4;*cook++ |= (*raw1 & 0x0000003fL);}usekey(dough);return;}void cpkey(into)
unsigned long *into;
{unsigned long *from, *endp;from = KnL, endp = &KnL[32];while( from < endp ) *into++ = *from++;return;}void usekey(from)
unsigned long *from;
{unsigned long *to, *endp;to = KnL, endp = &KnL[32];while( to < endp ) *to++ = *from++;return;}void des(inblock, outblock)
unsigned char *inblock, *outblock;
{unsigned long work[2];scrunch(inblock, work);desfunc(work, KnL);unscrun(work, outblock);return;}static void scrunch(outof, into)
unsigned char *outof;
unsigned long *into;
{*into = (*outof++ & 0xffL) << 24;*into |= (*outof++ & 0xffL) << 16;*into |= (*outof++ & 0xffL) << 8;*into++ |= (*outof++ & 0xffL);*into = (*outof++ & 0xffL) << 24;*into |= (*outof++ & 0xffL) << 16;*into |= (*outof++ & 0xffL) << 8;*into |= (*outof & 0xffL);return;}static void unscrun(outof, into)
unsigned long *outof;
unsigned char *into;
{*into++ = (*outof >> 24) & 0xffL;*into++ = (*outof >> 16) & 0xffL;*into++ = (*outof >> 8) & 0xffL;*into++ = *outof++ & 0xffL;*into++ = (*outof >> 24) & 0xffL;*into++ = (*outof >> 16) & 0xffL;*into++ = (*outof >> 8) & 0xffL;*into = *outof & 0xffL;return;}static unsigned long SP1[64] = {0x01010400L, 0x00000000L, 0x00010000L, 0x01010404L,0x01010004L, 0x00010404L, 0x00000004L, 0x00010000L,0x00000400L, 0x01010400L, 0x01010404L, 0x00000400L,0x01000404L, 0x01010004L, 0x01000000L, 0x00000004L,0x00000404L, 0x01000400L, 0x01000400L, 0x00010400L,0x00010400L, 0x01010000L, 0x01010000L, 0x01000404L,0x00010004L, 0x01000004L, 0x01000004L, 0x00010004L,0x00000000L, 0x00000404L, 0x00010404L, 0x01000000L,0x00010000L, 0x01010404L, 0x00000004L, 0x01010000L,0x01010400L, 0x01000000L, 0x01000000L, 0x00000400L,0x01010004L, 0x00010000L, 0x00010400L, 0x01000004L,0x00000400L, 0x00000004L, 0x01000404L, 0x00010404L,0x01010404L, 0x00010004L, 0x01010000L, 0x01000404L,0x01000004L, 0x00000404L, 0x00010404L, 0x01010400L,0x00000404L, 0x01000400L, 0x01000400L, 0x00000000L,0x00010004L, 0x00010400L, 0x00000000L, 0x01010004L };static unsigned long SP2[64] = {0x80108020L, 0x80008000L, 0x00008000L, 0x00108020L,0x00100000L, 0x00000020L, 0x80100020L, 0x80008020L,0x80000020L, 0x80108020L, 0x80108000L, 0x80000000L,0x80008000L, 0x00100000L, 0x00000020L, 0x80100020L,0x00108000L, 0x00100020L, 0x80008020L, 0x00000000L,0x80000000L, 0x00008000L, 0x00108020L, 0x80100000L,0x00100020L, 0x80000020L, 0x00000000L, 0x00108000L,0x00008020L, 0x80108000L, 0x80100000L, 0x00008020L,0x00000000L, 0x00108020L, 0x80100020L, 0x00100000L,0x80008020L, 0x80100000L, 0x80108000L, 0x00008000L,0x80100000L, 0x80008000L, 0x00000020L, 0x80108020L,0x00108020L, 0x00000020L, 0x00008000L, 0x80000000L,0x00008020L, 0x80108000L, 0x00100000L, 0x80000020L,0x00100020L, 0x80008020L, 0x80000020L, 0x00100020L,0x00108000L, 0x00000000L, 0x80008000L, 0x00008020L,0x80000000L, 0x80100020L, 0x80108020L, 0x00108000L };static unsigned long SP3[64] = {0x00000208L, 0x08020200L, 0x00000000L, 0x08020008L,0x08000200L, 0x00000000L, 0x00020208L, 0x08000200L,0x00020008L, 0x08000008L, 0x08000008L, 0x00020000L,0x08020208L, 0x00020008L, 0x08020000L, 0x00000208L,0x08000000L, 0x00000008L, 0x08020200L, 0x00000200L,0x00020200L, 0x08020000L, 0x08020008L, 0x00020208L,0x08000208L, 0x00020200L, 0x00020000L, 0x08000208L,0x00000008L, 0x08020208L, 0x00000200L, 0x08000000L,0x08020200L, 0x08000000L, 0x00020008L, 0x00000208L,0x00020000L, 0x08020200L, 0x08000200L, 0x00000000L,0x00000200L, 0x00020008L, 0x08020208L, 0x08000200L,0x08000008L, 0x00000200L, 0x00000000L, 0x08020008L,0x08000208L, 0x00020000L, 0x08000000L, 0x08020208L,0x00000008L, 0x00020208L, 0x00020200L, 0x08000008L,0x08020000L, 0x08000208L, 0x00000208L, 0x08020000L,0x00020208L, 0x00000008L, 0x08020008L, 0x00020200L };static unsigned long SP4[64] = {0x00802001L, 0x00002081L, 0x00002081L, 0x00000080L,0x00802080L, 0x00800081L, 0x00800001L, 0x00002001L,0x00000000L, 0x00802000L, 0x00802000L, 0x00802081L,0x00000081L, 0x00000000L, 0x00800080L, 0x00800001L,0x00000001L, 0x00002000L, 0x00800000L, 0x00802001L,0x00000080L, 0x00800000L, 0x00002001L, 0x00002080L,0x00800081L, 0x00000001L, 0x00002080L, 0x00800080L,0x00002000L, 0x00802080L, 0x00802081L, 0x00000081L,0x00800080L, 0x00800001L, 0x00802000L, 0x00802081L,0x00000081L, 0x00000000L, 0x00000000L, 0x00802000L,0x00002080L, 0x00800080L, 0x00800081L, 0x00000001L,0x00802001L, 0x00002081L, 0x00002081L, 0x00000080L,0x00802081L, 0x00000081L, 0x00000001L, 0x00002000L,0x00800001L, 0x00002001L, 0x00802080L, 0x00800081L,0x00002001L, 0x00002080L, 0x00800000L, 0x00802001L,0x00000080L, 0x00800000L, 0x00002000L, 0x00802080L };static unsigned long SP5[64] = {0x00000100L, 0x02080100L, 0x02080000L, 0x42000100L,0x00080000L, 0x00000100L, 0x40000000L, 0x02080000L,0x40080100L, 0x00080000L, 0x02000100L, 0x40080100L,0x42000100L, 0x42080000L, 0x00080100L, 0x40000000L,0x02000000L, 0x40080000L, 0x40080000L, 0x00000000L,0x40000100L, 0x42080100L, 0x42080100L, 0x02000100L,0x42080000L, 0x40000100L, 0x00000000L, 0x42000000L,0x02080100L, 0x02000000L, 0x42000000L, 0x00080100L,0x00080000L, 0x42000100L, 0x00000100L, 0x02000000L,0x40000000L, 0x02080000L, 0x42000100L, 0x40080100L,0x02000100L, 0x40000000L, 0x42080000L, 0x02080100L,0x40080100L, 0x00000100L, 0x02000000L, 0x42080000L,0x42080100L, 0x00080100L, 0x42000000L, 0x42080100L,0x02080000L, 0x00000000L, 0x40080000L, 0x42000000L,0x00080100L, 0x02000100L, 0x40000100L, 0x00080000L,0x00000000L, 0x40080000L, 0x02080100L, 0x40000100L };static unsigned long SP6[64] = {0x20000010L, 0x20400000L, 0x00004000L, 0x20404010L,0x20400000L, 0x00000010L, 0x20404010L, 0x00400000L,0x20004000L, 0x00404010L, 0x00400000L, 0x20000010L,0x00400010L, 0x20004000L, 0x20000000L, 0x00004010L,0x00000000L, 0x00400010L, 0x20004010L, 0x00004000L,0x00404000L, 0x20004010L, 0x00000010L, 0x20400010L,0x20400010L, 0x00000000L, 0x00404010L, 0x20404000L,0x00004010L, 0x00404000L, 0x20404000L, 0x20000000L,0x20004000L, 0x00000010L, 0x20400010L, 0x00404000L,0x20404010L, 0x00400000L, 0x00004010L, 0x20000010L,0x00400000L, 0x20004000L, 0x20000000L, 0x00004010L,0x20000010L, 0x20404010L, 0x00404000L, 0x20400000L,0x00404010L, 0x20404000L, 0x00000000L, 0x20400010L,0x00000010L, 0x00004000L, 0x20400000L, 0x00404010L,0x00004000L, 0x00400010L, 0x20004010L, 0x00000000L,0x20404000L, 0x20000000L, 0x00400010L, 0x20004010L };static unsigned long SP7[64] = {0x00200000L, 0x04200002L, 0x04000802L, 0x00000000L,0x00000800L, 0x04000802L, 0x00200802L, 0x04200800L,0x04200802L, 0x00200000L, 0x00000000L, 0x04000002L,0x00000002L, 0x04000000L, 0x04200002L, 0x00000802L,0x04000800L, 0x00200802L, 0x00200002L, 0x04000800L,0x04000002L, 0x04200000L, 0x04200800L, 0x00200002L,0x04200000L, 0x00000800L, 0x00000802L, 0x04200802L,0x00200800L, 0x00000002L, 0x04000000L, 0x00200800L,0x04000000L, 0x00200800L, 0x00200000L, 0x04000802L,0x04000802L, 0x04200002L, 0x04200002L, 0x00000002L,0x00200002L, 0x04000000L, 0x04000800L, 0x00200000L,0x04200800L, 0x00000802L, 0x00200802L, 0x04200800L,0x00000802L, 0x04000002L, 0x04200802L, 0x04200000L,0x00200800L, 0x00000000L, 0x00000002L, 0x04200802L,0x00000000L, 0x00200802L, 0x04200000L, 0x00000800L,0x04000002L, 0x04000800L, 0x00000800L, 0x00200002L };static unsigned long SP8[64] = {0x10001040L, 0x00001000L, 0x00040000L, 0x10041040L,0x10000000L, 0x10001040L, 0x00000040L, 0x10000000L,0x00040040L, 0x10040000L, 0x10041040L, 0x00041000L,0x10041000L, 0x00041040L, 0x00001000L, 0x00000040L,0x10040000L, 0x10000040L, 0x10001000L, 0x00001040L,0x00041000L, 0x00040040L, 0x10040040L, 0x10041000L,0x00001040L, 0x00000000L, 0x00000000L, 0x10040040L,0x10000040L, 0x10001000L, 0x00041040L, 0x00040000L,0x00041040L, 0x00040000L, 0x10041000L, 0x00001000L,0x00000040L, 0x10040040L, 0x00001000L, 0x00041040L,0x10001000L, 0x00000040L, 0x10000040L, 0x10040000L,0x10040040L, 0x10000000L, 0x00040000L, 0x10001040L,0x00000000L, 0x10041040L, 0x00040040L, 0x10000040L,0x10040000L, 0x10001000L, 0x10001040L, 0x00000000L,0x10041040L, 0x00041000L, 0x00041000L, 0x00001040L,0x00001040L, 0x00040040L, 0x10000000L, 0x10041000L };static void desfunc(block, keys)
unsigned long *block, *keys;
{unsigned long fval, work, right, leftt;int round;leftt = block[0];right = block[1];work = ((leftt >> 4) ^ right) & 0x0f0f0f0fL;right ^= work;leftt ^= (work << 4);work = ((leftt >> 16) ^ right) & 0x0000ffffL;right ^= work;leftt ^= (work << 16);work = ((right >> 2) ^ leftt) & 0x33333333L;leftt ^= work;right ^= (work << 2);work = ((right >> 8) ^ leftt) & 0x00ff00ffL;leftt ^= work;right ^= (work << 8);right = ((right << 1) | ((right >> 31) & 1L)) & 0xffffffffL;work = (leftt ^ right) & 0xaaaaaaaaL;leftt ^= work;right ^= work;leftt = ((leftt << 1) | ((leftt >> 31) & 1L)) & 0xffffffffL;for( round = 0; round < 8; round++ ) {work = (right << 28) | (right >> 4);work ^= *keys++;fval = SP7[ work & 0x3fL];fval |= SP5[(work >> 8) & 0x3fL];fval |= SP3[(work >> 16) & 0x3fL];fval |= SP1[(work >> 24) & 0x3fL];work = right ^ *keys++;fval |= SP8[ work & 0x3fL];fval |= SP6[(work >> 8) & 0x3fL];fval |= SP4[(work >> 16) & 0x3fL];fval |= SP2[(work >> 24) & 0x3fL];leftt ^= fval;work = (leftt << 28) | (leftt >> 4);work ^= *keys++;fval = SP7[ work & 0x3fL];fval |= SP5[(work >> 8) & 0x3fL];fval |= SP3[(work >> 16) & 0x3fL];fval |= SP1[(work >> 24) & 0x3fL];work = leftt ^ *keys++;fval |= SP8[ work & 0x3fL];fval |= SP6[(work >> 8) & 0x3fL];fval |= SP4[(work >> 16) & 0x3fL];fval |= SP2[(work >> 24) & 0x3fL];right ^= fval;}right = (right << 31) | (right >> 1);work = (leftt ^ right) & 0xaaaaaaaaL;leftt ^= work;right ^= work;leftt = (leftt << 31) | (leftt >> 1);work = ((leftt >> 8) ^ right) & 0x00ff00ffL;right ^= work;leftt ^= (work << 8);work = ((leftt >> 2) ^ right) & 0x33333333L;right ^= work;leftt ^= (work << 2);work = ((right >> 16) ^ leftt) & 0x0000ffffL;leftt ^= work;right ^= (work << 16);work = ((right >> 4) ^ leftt) & 0x0f0f0f0fL;leftt ^= work;right ^= (work << 4);*block++ = right;*block = leftt;return;}#ifdef D2_DESvoid des2key(hexkey, mode) /* stomps on Kn3 too */
unsigned char *hexkey; /* unsigned char[16] */
short mode;
{short revmod;revmod = (mode == EN0) ? DE1 : EN0;deskey(&hexkey[8], revmod);cpkey(KnR);deskey(hexkey, mode);cpkey(Kn3); /* Kn3 = KnL */return;}void Ddes(from, into)
unsigned char *from, *into; /* unsigned char[8] */
{unsigned long work[2];scrunch(from, work);desfunc(work, KnL);desfunc(work, KnR);desfunc(work, Kn3);unscrun(work, into);return;}void D2des(from, into)
unsigned char *from; /* unsigned char[16] */
unsigned char *into; /* unsigned char[16] */
{unsigned long *right, *l1, swap;unsigned long leftt[2], bufR[2];right = bufR;l1 = &leftt[1];scrunch(from, leftt);scrunch(&from[8], right);desfunc(leftt, KnL);desfunc(right, KnL);swap = *l1;*l1 = *right;*right = swap;desfunc(leftt, KnR);desfunc(right, KnR);swap = *l1;*l1 = *right;*right = swap;desfunc(leftt, Kn3);desfunc(right, Kn3);unscrun(leftt, into);unscrun(right, &into[8]);return;}void makekey(aptr, kptr)
char *aptr; /* NULL-terminated */
unsigned char *kptr; /* unsigned char[8] */
{unsigned char *store;int first, i;unsigned long savek[96];cpDkey(savek);des2key(Df_Key, EN0);for( i = 0; i < 8; i++ ) kptr[i] = Df_Key[i];first = 1;while( (*aptr != '\0') || first ) {store = kptr;for( i = 0; i < 8 && (*aptr != '\0'); i++ ) {*store++ ^= *aptr & 0x7f;*aptr++ = '\0';}Ddes(kptr, kptr);first = 0;}useDkey(savek);return;}void make2key(aptr, kptr)
char *aptr; /* NULL-terminated */
unsigned char *kptr; /* unsigned char[16] */
{unsigned char *store;int first, i;unsigned long savek[96];cpDkey(savek);des2key(Df_Key, EN0);for( i = 0; i < 16; i++ ) kptr[i] = Df_Key[i];first = 1;while( (*aptr != '\0') || first ) {store = kptr;for( i = 0; i < 16 && (*aptr != '\0'); i++ ) {*store++ ^= *aptr & 0x7f;*aptr++ = '\0';}D2des(kptr, kptr);first = 0;}useDkey(savek);return;}#ifndef D3_DES /* D2_DES only */void cp2key(into)
unsigned long *into; /* unsigned long[64] */
{unsigned long *from, *endp;cpkey(into);into = &into[32];from = KnR, endp = &KnR[32];while( from < endp ) *into++ = *from++;return;}void use2key(from) /* stomps on Kn3 too */
unsigned long *from; /* unsigned long[64] */
{unsigned long *to, *endp;usekey(from);from = &from[32];to = KnR, endp = &KnR[32];while( to < endp ) *to++ = *from++;cpkey(Kn3); /* Kn3 = KnL */return;}#else /* D3_DES too */void des3key(hexkey, mode)
unsigned char *hexkey; /* unsigned char[24] */
short mode;
{unsigned char *first, *third;short revmod;if( mode == EN0 ) {revmod = DE1;first = hexkey;third = &hexkey[16];}else {revmod = EN0;first = &hexkey[16];third = hexkey;}deskey(&hexkey[8], revmod);cpkey(KnR);deskey(third, mode);cpkey(Kn3);deskey(first, mode);return;}void cp3key(into)
unsigned long *into; /* unsigned long[96] */
{unsigned long *from, *endp;cpkey(into);into = &into[32];from = KnR, endp = &KnR[32];while( from < endp ) *into++ = *from++;from = Kn3, endp = &Kn3[32];while( from < endp ) *into++ = *from++;return;}void use3key(from)
unsigned long *from; /* unsigned long[96] */
{unsigned long *to, *endp;usekey(from);from = &from[32];to = KnR, endp = &KnR[32];while( to < endp ) *to++ = *from++;to = Kn3, endp = &Kn3[32];while( to < endp ) *to++ = *from++;return;}static void D3des(unsigned char *, unsigned char *);static void D3des(from, into) /* amateur theatrics */
unsigned char *from; /* unsigned char[24] */
unsigned char *into; /* unsigned char[24] */
{unsigned long swap, leftt[2], middl[2], right[2];scrunch(from, leftt);scrunch(&from[8], middl);scrunch(&from[16], right);desfunc(leftt, KnL);desfunc(middl, KnL);desfunc(right, KnL);swap = leftt[1];leftt[1] = middl[0];middl[0] = swap;swap = middl[1];middl[1] = right[0];right[0] = swap;desfunc(leftt, KnR);desfunc(middl, KnR);desfunc(right, KnR);swap = leftt[1];leftt[1] = middl[0];middl[0] = swap;swap = middl[1];middl[1] = right[0];right[0] = swap;desfunc(leftt, Kn3);desfunc(middl, Kn3);desfunc(right, Kn3);unscrun(leftt, into);unscrun(middl, &into[8]);unscrun(right, &into[16]);return;} void make3key(aptr, kptr)
char *aptr; /* NULL-terminated */
unsigned char *kptr; /* unsigned char[24] */
{unsigned char *store;int first, i;unsigned long savek[96];cp3key(savek);des3key(Df_Key, EN0);for( i = 0; i < 24; i++ ) kptr[i] = Df_Key[i];first = 1;while( (*aptr != '\0') || first ) {store = kptr;for( i = 0; i < 24 && (*aptr != '\0'); i++ ) {*store++ ^= *aptr & 0x7f;*aptr++ = '\0';}D3des(kptr, kptr);first = 0;}use3key(savek);return;}#endif /* D3_DES */
#endif /* D2_DES *//* Validation sets:** Single-length key, single-length plaintext -* Key : 0123 4567 89ab cdef* Plain : 0123 4567 89ab cde7* Cipher : c957 4425 6a5e d31d** Double-length key, single-length plaintext -* Key : 0123 4567 89ab cdef fedc ba98 7654 3210* Plain : 0123 4567 89ab cde7* Cipher : 7f1d 0a77 826b 8aff** Double-length key, double-length plaintext -* Key : 0123 4567 89ab cdef fedc ba98 7654 3210* Plain : 0123 4567 89ab cdef 0123 4567 89ab cdff* Cipher : 27a0 8440 406a df60 278f 47cf 42d6 15d7** Triple-length key, single-length plaintext -* Key : 0123 4567 89ab cdef fedc ba98 7654 3210 89ab cdef 0123 4567* Plain : 0123 4567 89ab cde7* Cipher : de0b 7c06 ae5e 0ed5** Triple-length key, double-length plaintext -* Key : 0123 4567 89ab cdef fedc ba98 7654 3210 89ab cdef 0123 4567* Plain : 0123 4567 89ab cdef 0123 4567 89ab cdff* Cipher : ad0d 1b30 ac17 cf07 0ed1 1c63 81e4 4de5** d3des V5.09 rwo 9208.04 20:31 Graven Imagery**********************************************************************/d3des.h
/* d3des.h -** Headers and defines for d3des.c* Graven Imagery, 1992.** THIS SOFTWARE PLACED IN THE PUBLIC DOMAIN BY THE AUTHOUR* 920825 19:42 EDST** Copyright (c) 1988,1989,1990,1991,1992 by Richard Outerbridge* (GEnie : OUTER; CIS : [71755,204])*/#define D2_DES /* include double-length support */
#define D3_DES /* include triple-length support */#ifdef D3_DES
#ifndef D2_DES
#define D2_DES /* D2_DES is needed for D3_DES */
#endif
#endif#define EN0 0 /* MODE == encrypt */
#define DE1 1 /* MODE == decrypt *//* Useful on 68000-ish machines, but NOT USED here. */typedef union {unsigned long blok[2];unsigned short word[4];unsigned char byte[8];} M68K;typedef union {unsigned long dblok[4];unsigned short dword[8];unsigned char dbyte[16];} M68K2;extern void deskey(unsigned char *, short);
/* hexkey[8] MODE* Sets the internal key register according to the hexadecimal* key contained in the 8 bytes of hexkey, according to the DES,* for encryption or decryption according to MODE.*/extern void usekey(unsigned long *);
/* cookedkey[32]* Loads the internal key register with the data in cookedkey.*/extern void cpkey(unsigned long *);
/* cookedkey[32]* Copies the contents of the internal key register into the storage* located at &cookedkey[0].*/extern void des(unsigned char *, unsigned char *);
/* from[8] to[8]* Encrypts/Decrypts (according to the key currently loaded in the* internal key register) one block of eight bytes at address 'from'* into the block at address 'to'. They can be the same.*/#ifdef D2_DES#define desDkey(a,b) des2key((a),(b))
extern void des2key(unsigned char *, short);
/* hexkey[16] MODE* Sets the internal key registerS according to the hexadecimal* keyS contained in the 16 bytes of hexkey, according to the DES,* for DOUBLE encryption or decryption according to MODE.* NOTE: this clobbers all three key registers!*/extern void Ddes(unsigned char *, unsigned char *);
/* from[8] to[8]* Encrypts/Decrypts (according to the keyS currently loaded in the* internal key registerS) one block of eight bytes at address 'from'* into the block at address 'to'. They can be the same.*/extern void D2des(unsigned char *, unsigned char *);
/* from[16] to[16]* Encrypts/Decrypts (according to the keyS currently loaded in the* internal key registerS) one block of SIXTEEN bytes at address 'from'* into the block at address 'to'. They can be the same.*/extern void makekey(char *, unsigned char *);
/* *password, single-length key[8]* With a double-length default key, this routine hashes a NULL-terminated* string into an eight-byte random-looking key, suitable for use with the* deskey() routine.*/#define makeDkey(a,b) make2key((a),(b))
extern void make2key(char *, unsigned char *);
/* *password, double-length key[16]* With a double-length default key, this routine hashes a NULL-terminated* string into a sixteen-byte random-looking key, suitable for use with the* des2key() routine.*/#ifndef D3_DES /* D2_DES only */#define useDkey(a) use2key((a))
#define cpDkey(a) cp2key((a))extern void use2key(unsigned long *);
/* cookedkey[64]* Loads the internal key registerS with the data in cookedkey.* NOTE: this clobbers all three key registers!*/extern void cp2key(unsigned long *);
/* cookedkey[64]* Copies the contents of the internal key registerS into the storage* located at &cookedkey[0].*/#else /* D3_DES too */#define useDkey(a) use3key((a))
#define cpDkey(a) cp3key((a))extern void des3key(unsigned char *, short);
/* hexkey[24] MODE* Sets the internal key registerS according to the hexadecimal* keyS contained in the 24 bytes of hexkey, according to the DES,* for DOUBLE encryption or decryption according to MODE.*/extern void use3key(unsigned long *);
/* cookedkey[96]* Loads the 3 internal key registerS with the data in cookedkey.*/extern void cp3key(unsigned long *);
/* cookedkey[96]* Copies the contents of the 3 internal key registerS into the storage* located at &cookedkey[0].*/extern void make3key(char *, unsigned char *);
/* *password, triple-length key[24]* With a triple-length default key, this routine hashes a NULL-terminated* string into a twenty-four-byte random-looking key, suitable for use with* the des3key() routine.*/#endif /* D3_DES */
#endif /* D2_DES *//* d3des.h V5.09 rwo 9208.04 15:06 Graven Imagery********************************************************************/vncpwd.c
/*VNC Password DecrypterCopyright (c) 2018 Jeroen Nijhof <jeroen@jeroennijhof.nl>This program is free software: you can redistribute it and/or modifyit under the terms of the GNU General Public License as published bythe Free Software Foundation, either version 3 of the License, or(at your option) any later version.This program is distributed in the hope that it will be useful,but WITHOUT ANY WARRANTY; without even the implied warranty ofMERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See theGNU General Public License for more details.You should have received a copy of the GNU General Public Licensealong with this program. If not, see <http://www.gnu.org/licenses/>.
*/#include <stdio.h>
#include <stdlib.h>
#include <sys/types.h>
#include <unistd.h>
#include "d3des.h"static u_char obfKey[8] = {23,82,107,6,35,78,88,7};void decryptPw( unsigned char *pPW ) {unsigned char clrtxt[10];deskey(obfKey, DE1);des(pPW, clrtxt);clrtxt[8] = 0;fprintf(stdout, "Password: %s\n", clrtxt);
}int main(int argc, char *argv[]) {FILE *fp;unsigned char *pwd;if (argc < 2) {fprintf(stdout, "Usage: vncpwd <password file>\n");return 1;}if ((fp = fopen(argv[1], "r")) == NULL) {fprintf(stderr, "Error: can not open password file: %s\n", argv[1]);return 1;}pwd = malloc(1024);fread(pwd, 1024, 1, fp);fclose(fp);decryptPw(pwd);free(pwd);return 0;
}Makefile
CFLAGS = -Wall -g
PREFIX = /usr
BINDIR = ${PREFIX}/binall:gcc ${CFLAGS} -o vncpwd vncpwd.c d3des.cinstall:install -D -m 755 vncpwd ${DESTDIR}${BINDIR}/vncpwdclean:rm vncpwdREADME
VNC Password DecrypterIt decrypts the stored vnc password.COMPILE
Just run make or gcc -o vncpwd vncpwd.c d3des.cUSAGE
vncpwd <vnc password file>EXAMPLE
$ vncpwd .vnc/passwd
Password: helloworldCopyright (c) 2018 Jeroen Nijhof <jeroen@jeroennijhof.nl>This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.You should have received a copy of the GNU General Public License
along with this program. If not, see <http://www.gnu.org/licenses/>.常见问题解决
编译报错 “fatal error: stdio.h: No such file or directory”
原因是缺少 C 语言标准库,安装 libc6-dev 即可:
yum install -y glibc-devel
提示 “Permission denied”
若执行 ./vncpwd 时提示权限不足,给文件加可执行权限:
chmod +x vncpwd
解密结果为空或乱码
确认密码文件路径正确,且该文件是 NOVNC 生成的 原始密码文件(非其他加密格式文件);另外 VNC 仅加密密码前 8 位,若原始密码超过 8 位,解密结果仅显示前 8 位。
