防火墙(firewalld)
防火墙(firewalld)
一、什么是防火墙
网络安全模式,通过它可以隔离风险区域与安全区域的链接
目的:-----保证安全
1.可以显示他人进入内部网络,过滤掉不安全的服务和非法用户
2.防止入侵者接近防御设施
3.限定用户访问特殊网络
4.为监视internet安全提供方便
二、netfilter模块–网络过滤模块(防火墙的模块)
cd /lib/modules/3.10.0-957.el7.x86_64/kernel/net/netfilter
加载到内核中的模块
[root@stw ~]# cd /lib/modules
[root@stw modules]# ls
3.10.0-957.el7.x86_64
[root@stw modules]# cd 3.10.0-957.el7.x86_64/
[root@stw 3.10.0-957.el7.x86_64]# ls
build modules.alias.bin modules.dep modules.modesetting modules.symbols vdso
extra modules.block modules.dep.bin modules.networking modules.symbols.bin weak-updates
kernel modules.builtin modules.devname modules.order source
modules.alias modules.builtin.bin modules.drm modules.softdep updates
[root@stw 3.10.0-957.el7.x86_64]# cd kernel/
[root@stw kernel]# ls
arch crypto drivers fs kernel lib mm net sound virt
[root@stw kernel]# cd net
[root@stw net]# ls
6lowpan atm can dccp ipv4 l2tp mac802154 openvswitch rfkill sunrpc wireless
802 bluetooth ceph dns_resolver ipv6 llc netfilter packet sched unix xfrm
8021q bridge core ieee802154 key mac80211 netlink psample sctp vmw_vsock
[root@stw net]# cd netfilter/
[root@stw netfilter]# ls
ipset nfnetlink_acct.ko.xz xt_addrtype.ko.xz xt_hl.ko.xz xt_rateest.ko.xz
ipvs nfnetlink_cthelper.ko.xz xt_AUDIT.ko.xz xt_HL.ko.xz xt_RATEEST.ko.xz
nf_conntrack_amanda.ko.xz nfnetlink_cttimeout.ko.xz xt_bpf.ko.xz xt_HMARK.ko.xz xt_realm.ko.xz
nf_conntrack_broadcast.ko.xz nfnetlink.ko.xz xt_cgroup.ko.xz xt_IDLETIMER.ko.xz xt_recent.ko.xz
nf_conntrack_ftp.ko.xz nfnetlink_log.ko.xz xt_CHECKSUM.ko.xz xt_iprange.ko.xz xt_REDIRECT.ko.xz
nf_conntrack_h323.ko.xz nfnetlink_queue.ko.xz xt_CLASSIFY.ko.xz xt_ipvs.ko.xz xt_sctp.ko.xz
nf_conntrack_irc.ko.xz nf_synproxy_core.ko.xz xt_cluster.ko.xz xt_LED.ko.xz xt_SECMARK.ko.xz
nf_conntrack.ko.xz nf_tables_inet.ko.xz xt_comment.ko.xz xt_length.ko.xz xt_set.ko.xz
nf_conntrack_netbios_ns.ko.xz nf_tables.ko.xz xt_connbytes.ko.xz xt_limit.ko.xz xt_socket.ko.xz
nf_conntrack_netlink.ko.xz nft_compat.ko.xz xt_connlabel.ko.xz xt_LOG.ko.xz xt_state.ko.xz
nf_conntrack_pptp.ko.xz nft_counter.ko.xz xt_connlimit.ko.xz xt_mac.ko.xz xt_statistic.ko.xz
nf_conntrack_proto_gre.ko.xz nft_ct.ko.xz xt_connmark.ko.xz xt_mark.ko.xz xt_string.ko.xz
nf_conntrack_sane.ko.xz nft_exthdr.ko.xz xt_CONNSECMARK.ko.xz xt_multiport.ko.xz xt_tcpmss.ko.xz
nf_conntrack_sip.ko.xz nft_hash.ko.xz xt_conntrack.ko.xz xt_nat.ko.xz xt_TCPMSS.ko.xz
nf_conntrack_snmp.ko.xz nft_limit.ko.xz xt_cpu.ko.xz xt_NETMAP.ko.xz xt_TCPOPTSTRIP.ko.xz
nf_conntrack_tftp.ko.xz nft_log.ko.xz xt_CT.ko.xz xt_nfacct.ko.xz xt_TEE.ko.xz
nf_log_common.ko.xz nft_masq.ko.xz xt_dccp.ko.xz xt_NFLOG.ko.xz xt_time.ko.xz
nf_nat_amanda.ko.xz nft_meta.ko.xz xt_devgroup.ko.xz xt_NFQUEUE.ko.xz xt_TPROXY.ko.xz
nf_nat_ftp.ko.xz nft_nat.ko.xz xt_dscp.ko.xz xt_osf.ko.xz xt_TRACE.ko.xz
nf_nat_irc.ko.xz nft_queue.ko.xz xt_DSCP.ko.xz xt_owner.ko.xz xt_u32.ko.xz
nf_nat.ko.xz nft_rbtree.ko.xz xt_ecn.ko.xz xt_physdev.ko.xz
nf_nat_redirect.ko.xz nft_redir.ko.xz xt_esp.ko.xz xt_pkttype.ko.xz
nf_nat_sip.ko.xz nft_reject_inet.ko.xz xt_hashlimit.ko.xz xt_policy.ko.xz
nf_nat_tftp.ko.xz nft_reject.ko.xz xt_helper.ko.xz xt_quota.ko.xz
[root@stw netfilter]# pwd
/lib/modules/3.10.0-957.el7.x86_64/kernel/net/netfilter
三、管理防火墙
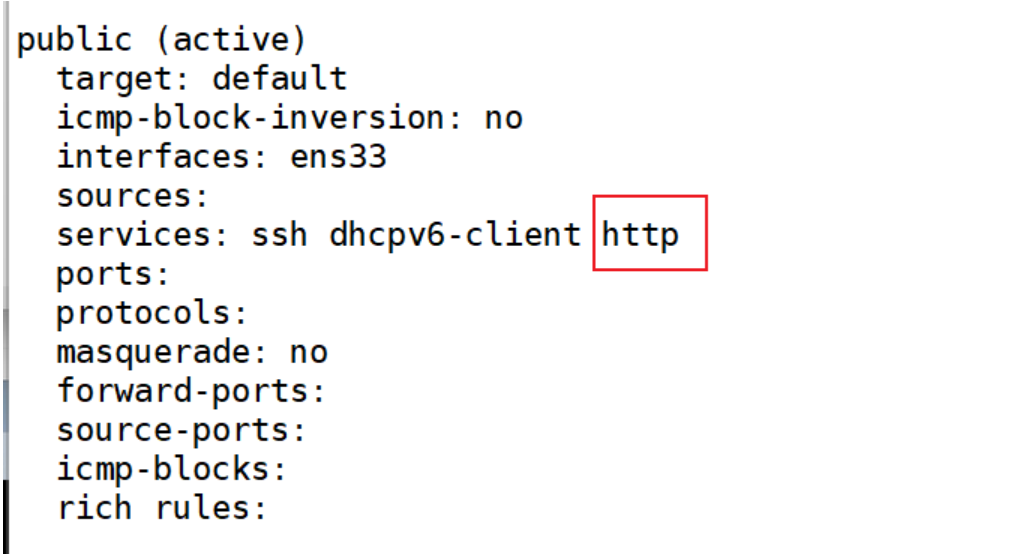
public 默认区域
Firewall有3个特殊区域
drop 强制拒绝,不反馈消息
block 拒绝,但是反馈消息
trusted 所有流量允许(防火墙不起作用)
drop和block ,不管是否勾选,都是禁止,而trusted ,不管是否勾选,都是允许
1、配置yum仓库,安装httpd服务
[root@stw ~]# cd /etc/yum.repos.d/
[root@stw yum.repos.d]# ls
server.repo
[root@stw yum.repos.d]# cat server.repo
[aa]
name=a
baseurl=file:///mnt
enabled=1
gpgcheck=0[root@stw yum.repos.d]# cd
[root@stw ~]# mount /dev/cdrom /mnt
mount: /dev/sr0 is write-protected, mounting read-only
[root@stw ~]# yum -y install httpd
[root@stw ~]# systemctl restart httpd
[root@stw ~]# systemctl enable httpd
Created symlink from /etc/systemd/system/multi-user.target.wants/httpd.service to /usr/lib/systemd/system/httpd.service.
2、查看防火墙相关信息
[root@stw ~]# firewall-cmd --list-all //查看防火墙信息
public (active)target: defaulticmp-block-inversion: nointerfaces: ens33sources: services: ssh dhcpv6-clientports: protocols: masquerade: noforward-ports: source-ports: icmp-blocks: rich rules: [root@stw ~]# firewall-cmd --get-default-zone //查看当前默认区域
public[root@stw ~]# firewall-cmd --list-all-zone //查看所有区域信息
blocktarget: %%REJECT%%icmp-block-inversion: nointerfaces: sources: services: ports: protocols: masquerade: noforward-ports: source-ports: icmp-blocks: rich rules: dmztarget: defaulticmp-block-inversion: nointerfaces: sources: services: sshports: protocols: masquerade: noforward-ports: source-ports: icmp-blocks: rich rules: droptarget: DROPicmp-block-inversion: nointerfaces: sources: services: ports: protocols: masquerade: noforward-ports: source-ports: icmp-blocks: rich rules: externaltarget: defaulticmp-block-inversion: nointerfaces: sources: services: sshports: protocols: masquerade: yesforward-ports: source-ports: icmp-blocks: rich rules: hometarget: defaulticmp-block-inversion: nointerfaces: sources: services: ssh mdns samba-client dhcpv6-clientports: protocols: masquerade: noforward-ports: source-ports: icmp-blocks: rich rules: internaltarget: defaulticmp-block-inversion: nointerfaces: sources: services: ssh mdns samba-client dhcpv6-clientports: protocols: masquerade: noforward-ports: source-ports: icmp-blocks: rich rules: public (active)target: defaulticmp-block-inversion: nointerfaces: ens33sources: services: ssh dhcpv6-clientports: protocols: masquerade: noforward-ports: source-ports: icmp-blocks: rich rules: trustedtarget: ACCEPTicmp-block-inversion: nointerfaces: sources: services: ports: protocols: masquerade: noforward-ports: source-ports: icmp-blocks: rich rules: worktarget: defaulticmp-block-inversion: nointerfaces: sources: services: ssh dhcpv6-clientports: protocols: masquerade: noforward-ports: source-ports: icmp-blocks: rich rules:
3、设置默认区域为home
[root@stw ~]# firewall-cmd --set-default-zone=home
success
[root@stw ~]# firewall-cmd --get-default-zone
home
[root@stw ~]# firewall-cmd --set-default-zone=public
success
[root@stw ~]# firewall-cmd --get-default-zone
public4、添加服务到默认区域(http服务)
[root@stw ~]# firewall-cmd --add-service=http --permanent
success
[root@stw ~]# firewall-cmd --reload
success
[root@stw ~]# firewall-cmd --list-all-zone
添加服务后可以访问网页
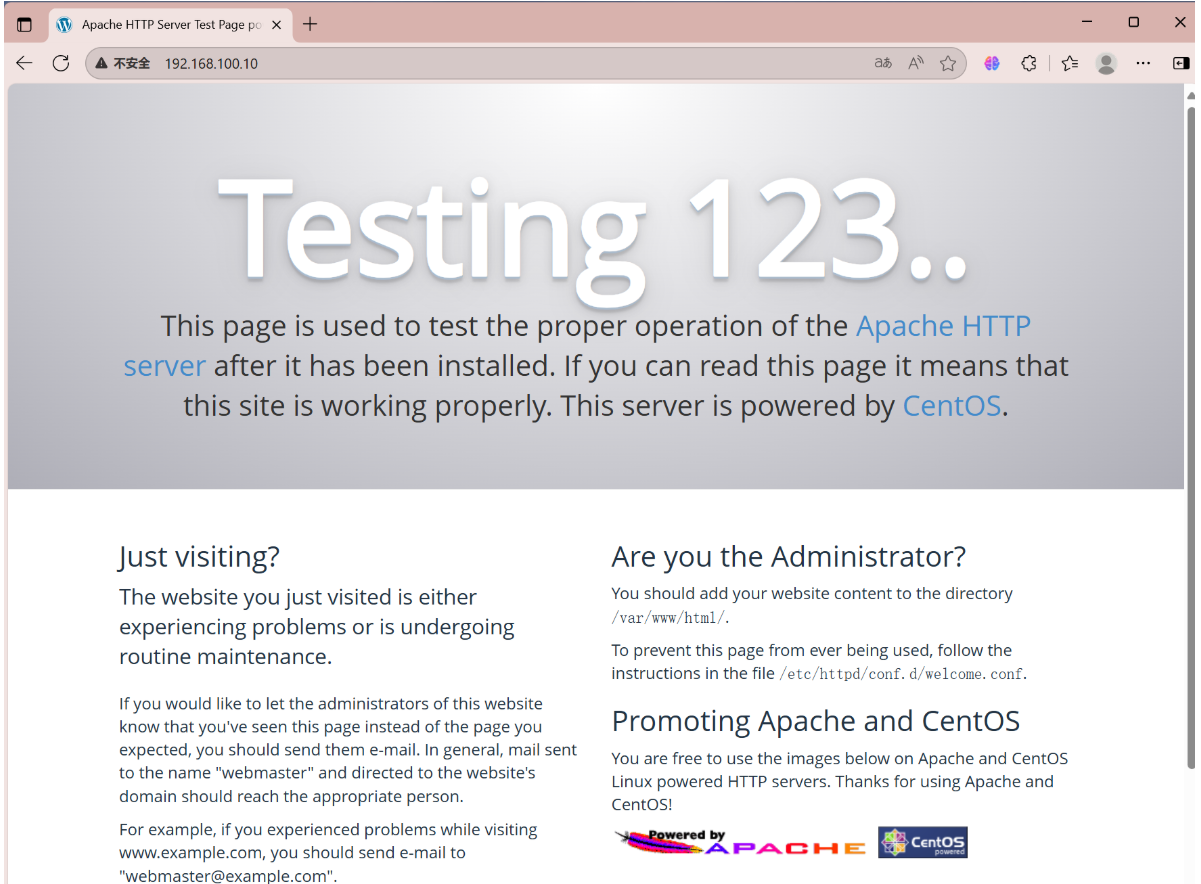
http的默认访问端口为80
5、添加端口
修改端口:把默认端口80更改为8080
[root@stw ~]# vim /etc/httpd/conf/httpd.conf
[root@stw ~]# systemctl restart httpd
[root@stw ~]# systemctl enable httpd
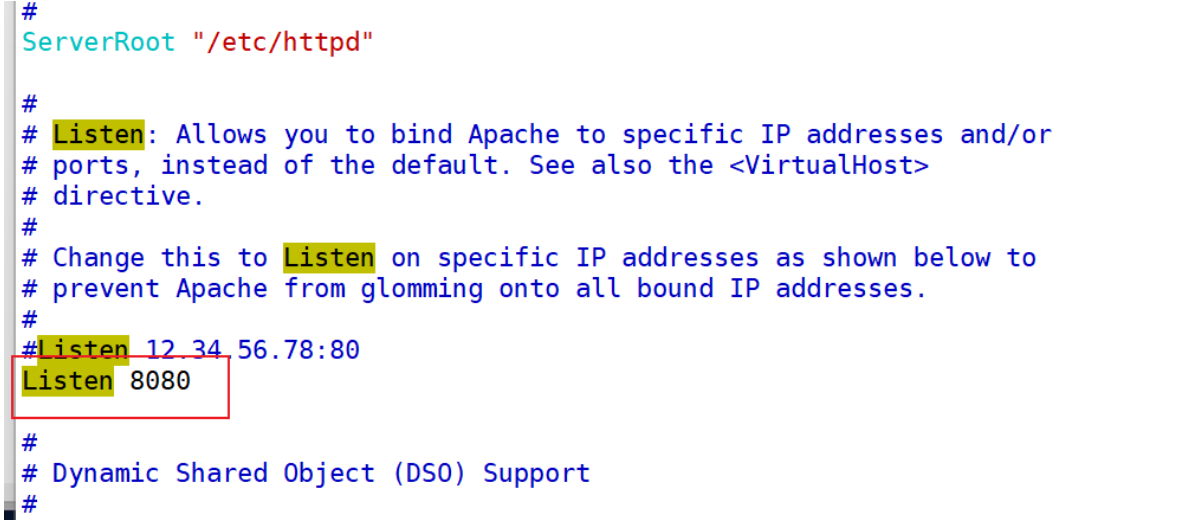
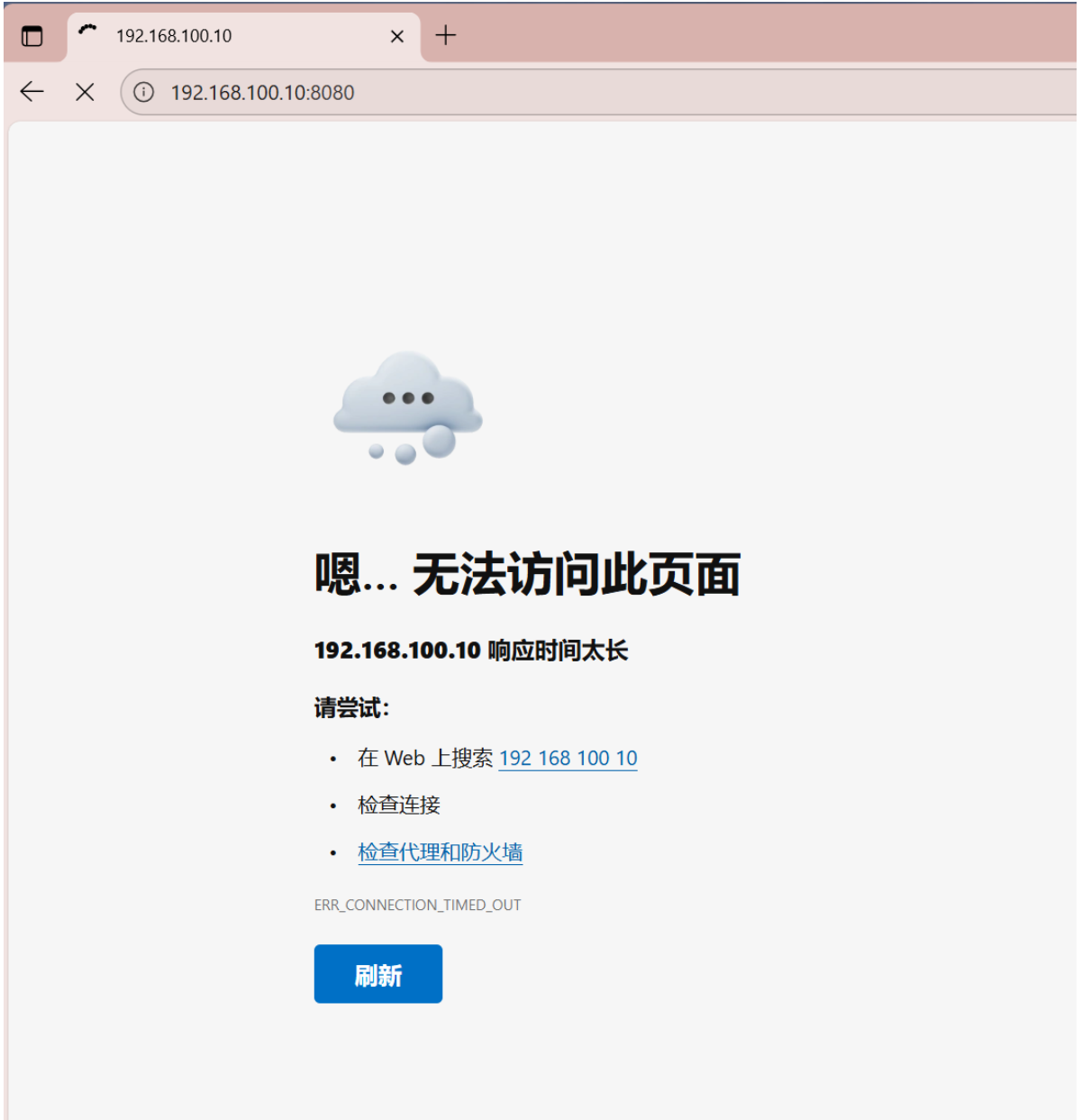
把8080端口添加到默认区域中
[root@stw ~]# firewall-cmd --add-port=8080/tcp --permanent
success
[root@stw ~]# firewall-cmd --reload
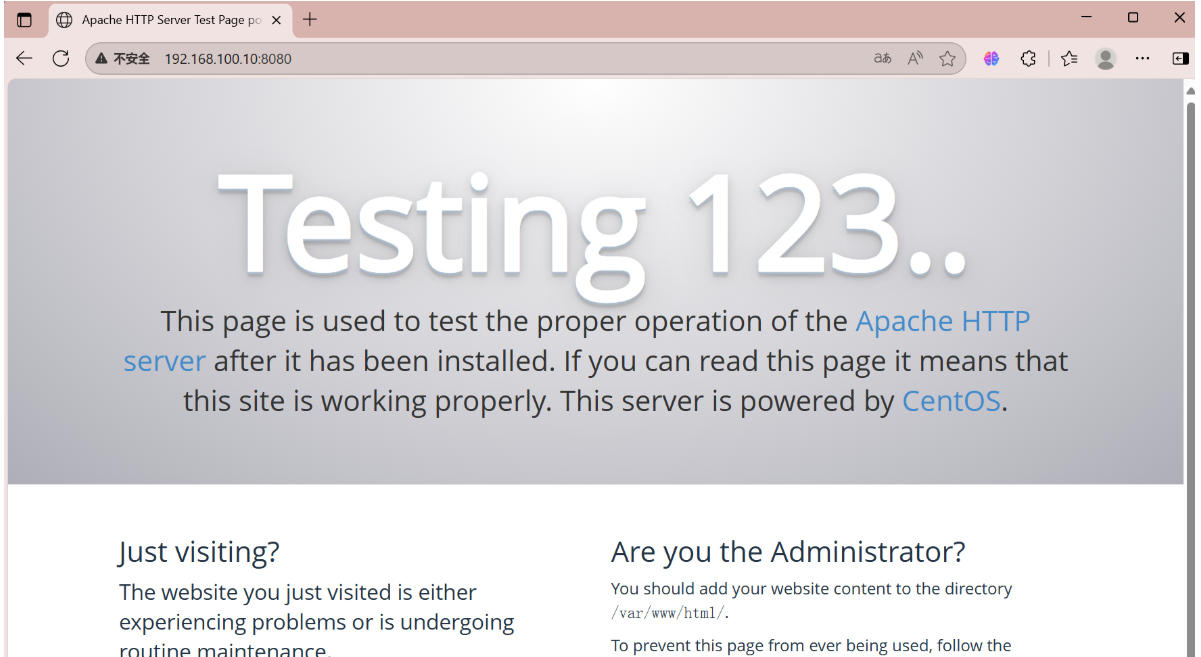
6、富规则(限定来源时使用)
accept 允许,reject和drop都是拒绝
reject 这个丢弃数据时会很礼貌的回应你一个
drop 只是简单的直接丢弃数据,不做任何反馈
两个发生冲突时,先读拒绝再读允许
[root@stw ~]# firewall-cmd --add-rich-rule='rule family=ipv4 source address=192.168.100.0/24 service name=http accept' --permanent
success
[root@stw ~]# firewall-cmd --reload
success
[root@stw ~]# firewall-cmd --list-all
public (active)target: defaulticmp-block-inversion: nointerfaces: ens33sources: services: ssh dhcpv6-client httpports: protocols: masquerade: noforward-ports: source-ports: icmp-blocks: rich rules: rule family="ipv4" source address="192.168.100.0/24" service name="http" accept
7、富规则设置记录到审计子系统的基本语法
audit limit value=rate/duration
rate:数字
duration:单位有秒s、分m、时h和天d
接受来自192.168.100.0/24网络内主机从public区域访问http服务连接,以notice的日志级别且每分钟最多10条的速率将新连接消息记录到syslog,更改永久设置
firewall-cmd --add-rich-rule=‘rule family=ipv4 source address=192.168.100.0/24 service name=http
log prefix=http level=notice limit value=10/m accept’ --zone=public --permanent
firewall-cmd --reload
[root@stw ~]# firewall-cmd --add-rich-rule='rule family=ipv4 source address=192.168.100.0/24 service name=http log prefix=http level=notice limit value=10/m accept' --zone=public --permanent
success
[root@stw ~]# firewall-cmd --reload
success
[root@stw ~]# firewall-cmd --list-all
public (active)target: defaulticmp-block-inversion: nointerfaces: ens33sources: services: ssh dhcpv6-client httpports: protocols: masquerade: noforward-ports: source-ports: icmp-blocks: rich rules: rule family="ipv4" source address="192.168.100.0/24" service name="http" acceptrule family="ipv4" source address="192.168.100.0/24" service name="http" log prefix="http" level="notice" limit value="10/m" accept
在未来10分钟内,拒绝来自172.16.30.0/24网络内主机进行ssh连接,将拒绝连接的消息以每分钟最多2条的
速率记录到审计子系统,更改运行时配置(不用firewall-cmd --reload)
firewall-cmd --add-rich-rule=‘rule family=ipv4 source address=172.16.30.0/24
service name=ssh audit limit value=2/m reject’ --timeout=600
[root@stw ~]# firewall-cmd --add-rich-rule='rule family=ipv4 source address=172.16.30.0/24 service name=ssh audit limit value=2/m reject' --timeout=600
success
[root@stw ~]# firewall-cmd --list-all
public (active)target: defaulticmp-block-inversion: nointerfaces: ens33sources: services: ssh dhcpv6-client httpports: protocols: masquerade: noforward-ports: source-ports: icmp-blocks: rich rules: rule family="ipv4" source address="192.168.100.0/24" service name="http" acceptrule family="ipv4" source address="192.168.100.0/24" service name="http" log prefix="http" level="notice" limit value="10/m" acceptrule family="ipv4" source address="172.16.30.0/24" service name="ssh" audit limit value="2/m" reject
8、伪装(必须开启IP转发)
(1)开启IP转发
[root@stw ~]# vim /etc/sysctl.conf
[root@stw ~]# sysctl -p
net.ipv4.ip_forward = 1
(2)启用伪装
firewall-cmd --add-rich-rule=‘rule family=ipv4 source address=172.16.30.0/24 masquerade’ --zone=public --permanent
(3)对某个区域启用伪装
firewall-cmd --add-masquerade --zone=public
9、端口转发
1、对来自网络中主机访问本地8000/tcp端口流量转发到80/tcp端口上,更改运行时设置
firewall-cmd --add-forward-port=port=8000:proto=tcp:toport=80:toaddr=172.16.30.130
2、使用富规则设置对来自12.12.12.0/24网络中主机访问本地80/tcp端口流量,转发到172.16.30.30主机的80/tcp端口上 更改永久配置
firewall-cmd --add-rich-rule=‘rule family=ipv4 source address=12.12.12.0/24 forward-port port=80
protocol=tcp to-port=80 to-addr=172.16.30.30’ --permanent
3、在主机Server30上配置端口转发,在172.16.30.0/24网络中的系统,访问Server30的本地端口9527时将被转发到80端口,此设置必须永久有效
firewall-cmd --add-rich-rule=‘rule family=ipv4 source address=172.16.30.0/24 forward-port port=9527 protocol=tcp to-port=80’ --permanent
firewall-cmd --reload
