区块链论文速读 CCF A--USENIX Security 2025(2)

Conference:34th USENIX Security Symposium
CCF level:CCF A
Year:2025
Conference time:August 13–15, 2025 Seattle, WA, USA
区块链可投会议CCF A--Security 2026 截止2.5 附录用率
区块链论文速读 CCF A--USENIX Security 2025(1)
4
Title:
Approve Once, Regret Forever: On the Exploitation of Ethereum's Approve-TransferFrom Ecosystem
一次批准,终身后悔:以太坊 Approve-TransferFrom 生态系统的开发
Authors:

Abstract:
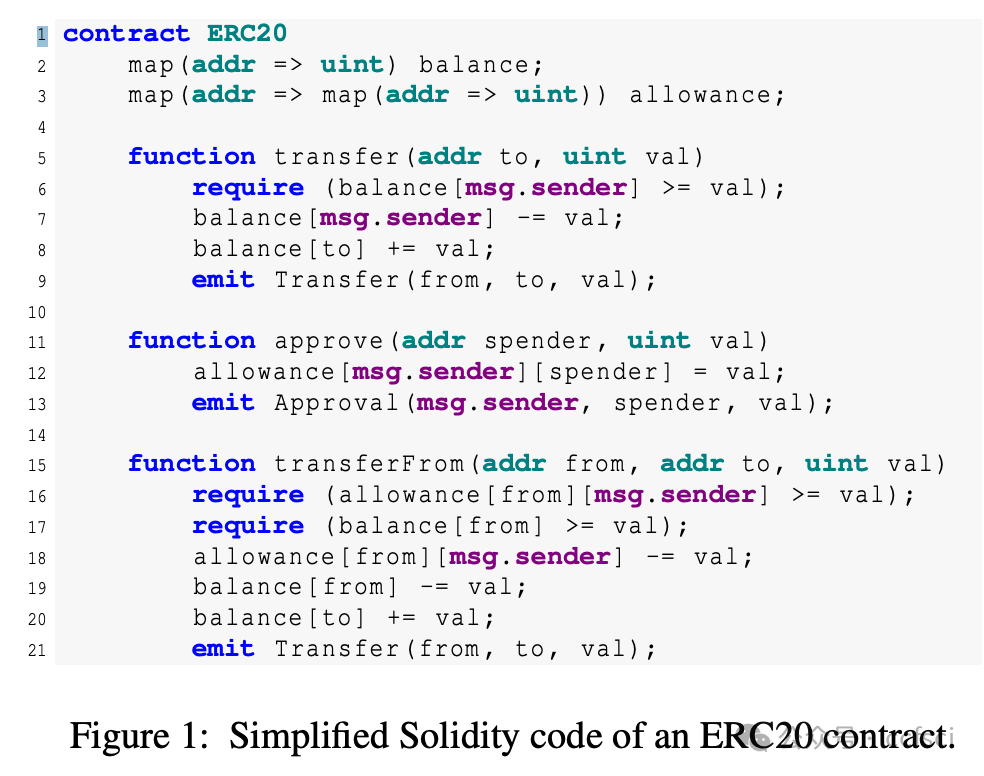
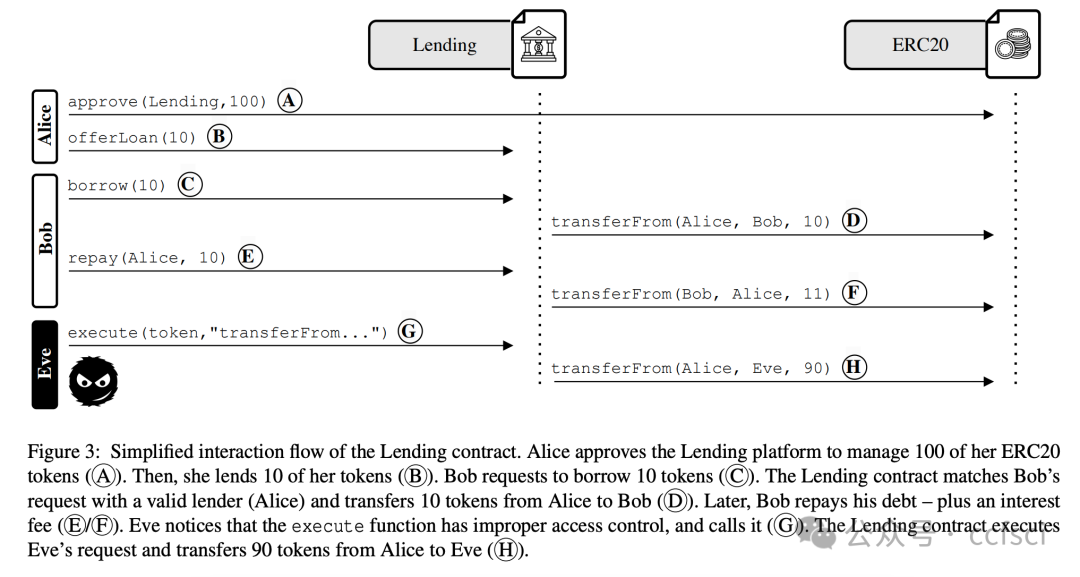
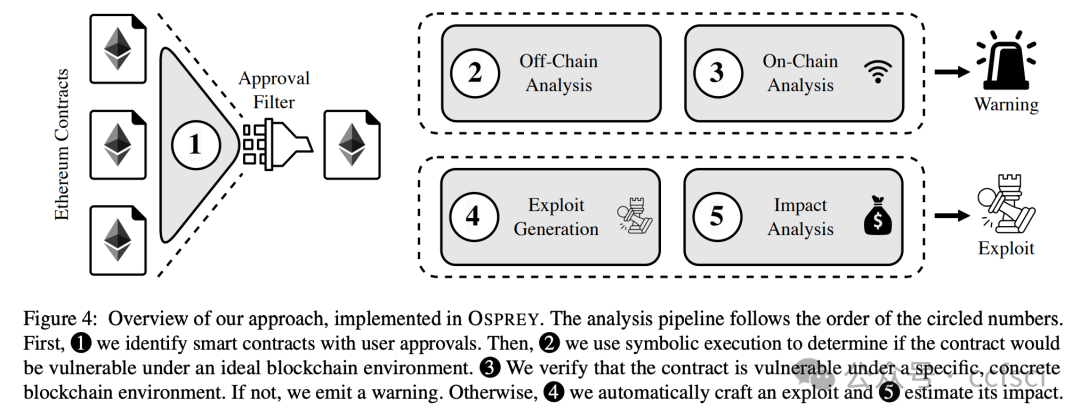
Smart contracts are immutable programs hosted on the blockchain that power decentralized applications. With the growth of decentralized finance (DeFi), many services interact with contracts that must be trusted to manage digital assets. To this end, several Ethereum standards (e.g., ERC20, ERC721) introduced an approval mechanism that allows decentralized applications to trade digital assets (or "tokens") on behalf of others. After receiving an approval, the (approved) application can invoke the token's transferFrom function to trade the approved tokens. Unfortunately, approved applications often contain vulnerabilities. If an attacker maliciously controls the parameters of a transferFrom call, they can steal not only the application's assets but also the assets of any user who previously approved the application. We refer to this widespread issue as Approved Controllable TransferFrom (ACT), which has already led to losses exceeding 65 million USD.
We present Osprey, an end-to-end system that detects ACT vulnerabilities and automatically generates proof-of-concept attacks. Our evaluation across the entire Ethereum ecosystem identified 32,582 potentially vulnerable contracts, with 410 confirmed exploitable at the time of writing. Our findings reveal previously unknown attack vectors threatening digital assets worth over 3.4 million USD.
智能合约是托管在区块链上的不可变程序,为去中心化应用程序提供支持。随着去中心化金融 (DeFi) 的发展,许多服务都需要与合约交互,而这些合约必须获得信任才能管理数字资产。为此,一些以太坊标准(例如 ERC20、ERC721)引入了一种批准机制,允许去中心化应用程序代表他人交易数字资产(或称“代币”)。获得批准后,(已批准的)应用程序可以调用代币的 transferFrom 函数来交易已批准的代币。然而,已批准的应用程序通常存在漏洞。如果攻击者恶意控制 transferFrom 调用的参数,他们不仅可以窃取应用程序的资产,还可以窃取任何先前批准该应用程序的用户的资产。我们将这种普遍存在的问题称为“已批准可控 TransferFrom”(ACT),该问题已造成超过 6500 万美元的损失。
我们推出了 Osprey,这是一个端到端的系统,可以检测 ACT 漏洞并自动生成概念验证攻击。我们对整个以太坊生态系统的评估发现了 32,582 个潜在易受攻击的合约,其中 410 个在撰写本文时已确认可被利用。我们的发现揭示了此前未知的攻击向量,威胁着价值超过 340 万美元的数字资产。

Pdf下载链接:
https://www.usenix.org/system/files/usenixsecurity25-ruaro.pdf
5
Title:
Voting-Bloc Entropy: A New Metric for DAO Decentralization
投票区块熵:DAO 去中心化的新指标
Authors:

Abstract:
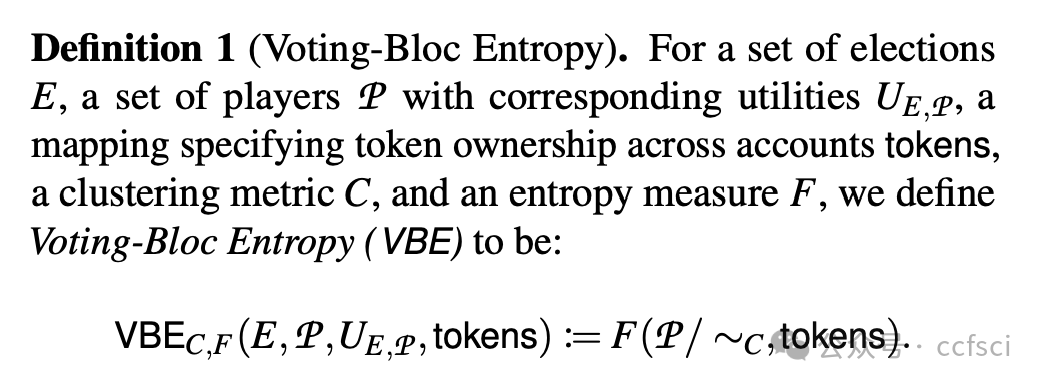
Decentralized Autonomous Organizations (DAOs) use smart contracts to foster communities working toward common goals. Existing definitions of decentralization, however—the 'D' in DAO—fall short of capturing the key properties characteristic of diverse and equitable participation.
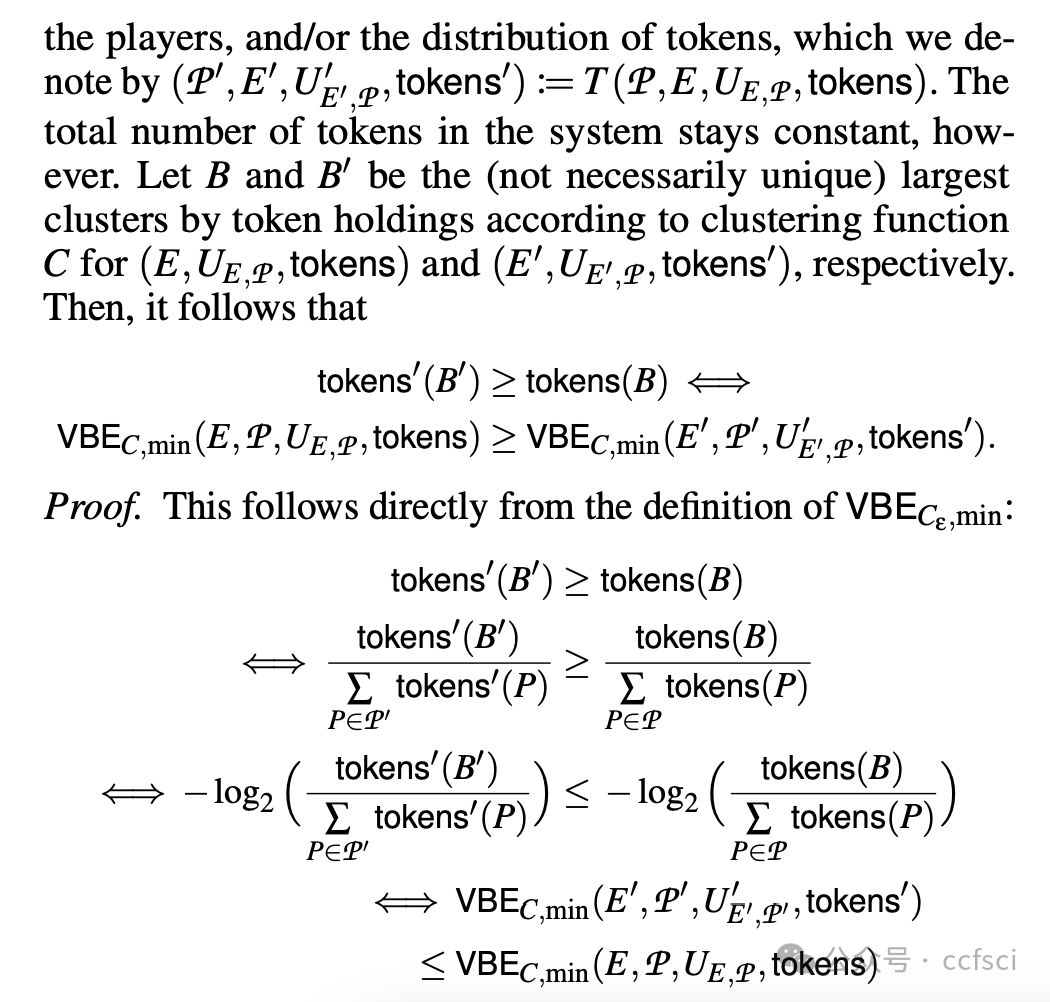
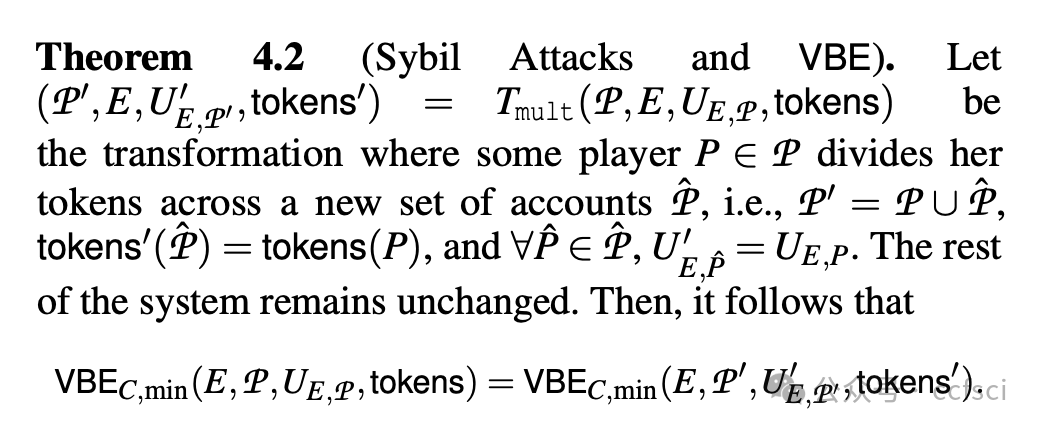
This work proposes a new framework for measuring DAO decentralization called Voting-Bloc Entropy (VBE, pronounced "vibe"). VBE is based on the idea that voters with closely aligned interests act as a centralizing force and should be modeled as such. VBE formalizes this notion by measuring the similarity of participants' utility functions across a set of voting rounds. Unlike prior, ad hoc definitions of decentralization, VBE derives from first principles: We introduce a simple (yet powerful) reinforcement learning-based conceptual model for voting, that in turn implies VBE.
We first show VBE's utility as a theoretical tool. We prove a number of results about the (de)centralizing effects of vote delegation, proposal bundling, bribery, etc. that are overlooked in previous notions of DAO decentralization. Our results lead to practical suggestions for enhancing DAO decentralization.
We also show how VBE can be used empirically by presenting measurement studies and VBE-based governance experiments. We make the tools we developed for these results available to the community in the form of open-source artifacts in order to facilitate future study of DAO decentralization.
去中心化自治组织 (DAO) 使用智能合约来促进社区朝着共同目标努力。然而,现有的去中心化定义——DAO 中的“D”——未能捕捉多元化和公平参与的关键特征。
本研究提出了一个用于衡量 DAO 去中心化程度的新框架,称为投票区块熵 (VBE,发音为“vibe”)。VBE 基于这样一种理念:利益紧密一致的选民会形成一种中心化力量,因此应该被建模为一种中心化力量。VBE 通过衡量参与者在一系列投票轮次中效用函数的相似性来形式化这一概念。与以往对去中心化的临时定义不同,VBE 源于第一性原理:我们引入了一个简单(但功能强大)的基于强化学习的投票概念模型,该模型反过来又隐含了 VBE。
我们首先展示了 VBE 作为理论工具的效用。我们证明了一些关于投票委托、提案捆绑、贿赂等(去)中心化效应的结果,这些效应在之前的 DAO 去中心化概念中被忽视了。我们的研究结果为增强 DAO 去中心化提出了切实可行的建议。
我们还通过展示测量研究和基于 VBE 的治理实验,展示了如何将 VBE 应用于实证研究。我们将为这些结果开发的工具以开源构件的形式提供给社区,以促进未来对 DAO 去中心化的研究。

Pdf下载链接:
https://www.usenix.org/system/files/usenixsecurity25-fabrega-entropy.pdf
6
Title:
Deanonymizing Ethereum Validators: The P2P Network Has a Privacy Issue
以太坊验证者去匿名化:P2P 网络存在隐私问题
Authors:

Abstract:
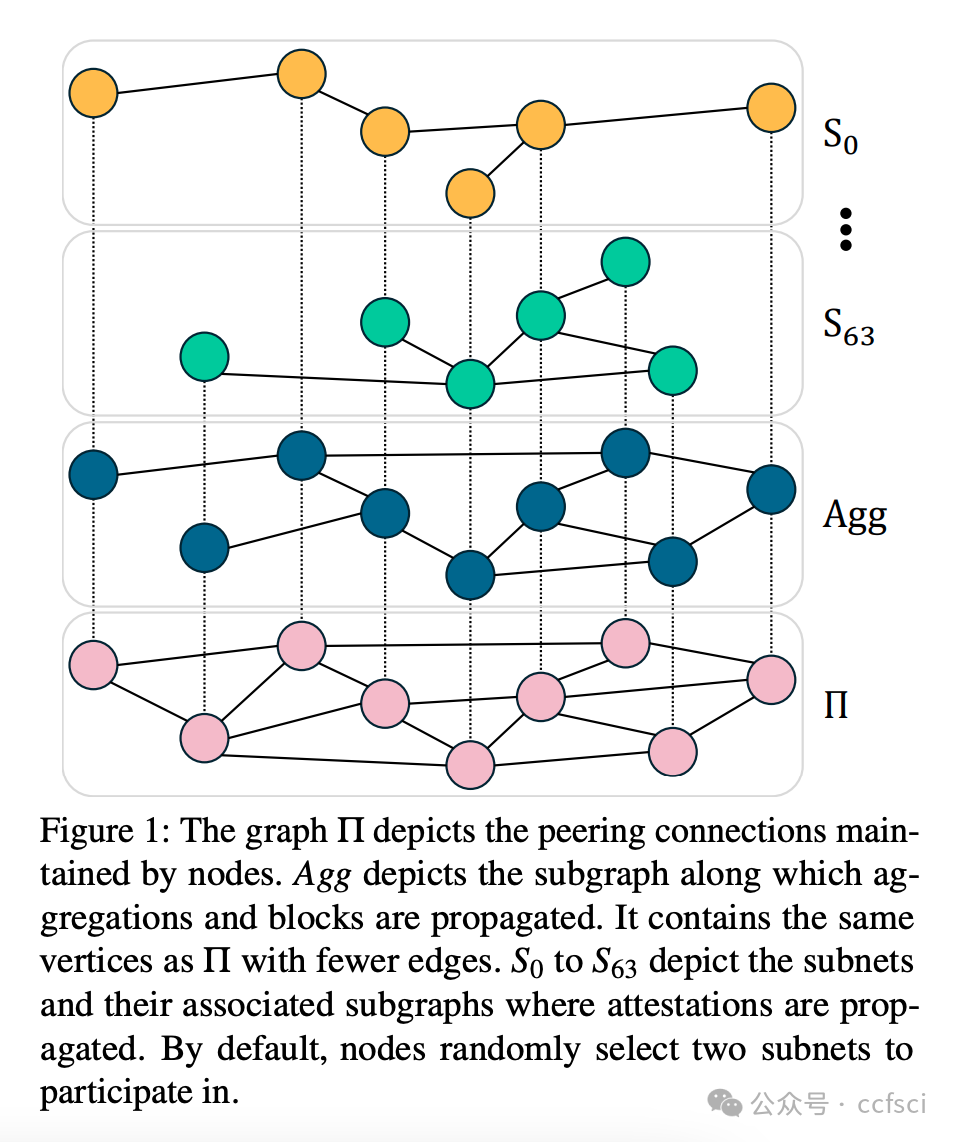
Many blockchain networks aim to preserve the anonymity of validators in the peer-to-peer (P2P) network, ensuring that no adversary can link a validator's identifier to the IP address of a peer due to associated privacy and security concerns.
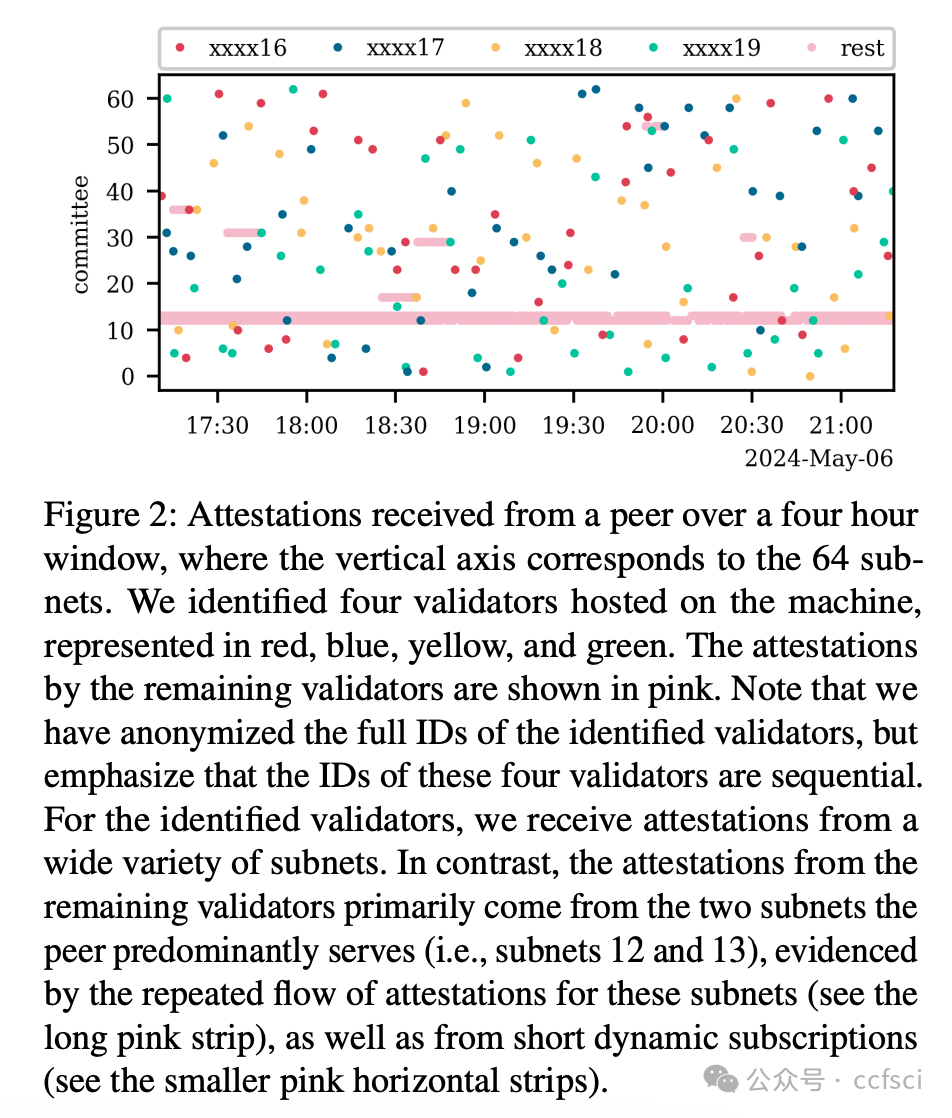
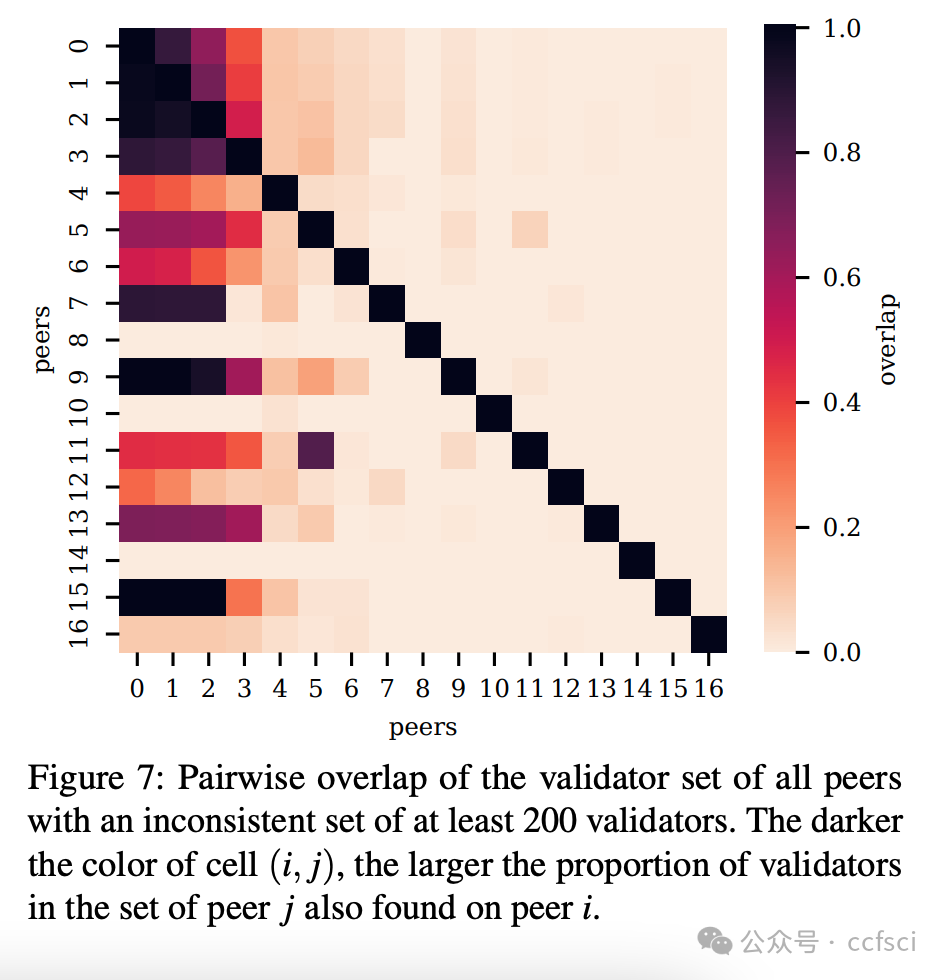
This work demonstrates that the Ethereum P2P network does not offer this anonymity. We present a methodology that enables any node in the network to identify validators hosted on connected peers and empirically verify the feasibility of our proposed method. Using data collected from four nodes over three days, we locate more than 15% of Ethereum validators in the P2P network. The insights gained from our deanonymization technique provide valuable information on the distribution of validators across peers, their geographic locations, and hosting organizations. We further discuss the implications and risks associated with the lack of anonymity in the P2P network and propose methods to help validators protect their privacy.
The Ethereum Foundation has awarded us a bug bounty, acknowledging the impact of our results.
许多区块链网络都致力于在点对点 (P2P) 网络中保护验证者的匿名性,以确保任何对手都无法将验证者的标识符与对等节点的 IP 地址关联起来,从而避免隐私和安全方面的担忧。
本研究表明,以太坊 P2P 网络并不具备这种匿名性。我们提出了一种方法,使网络中的任何节点都能识别托管在已连接对等节点上的验证者,并通过实证验证了我们提出的方法的可行性。利用三天内从四个节点收集的数据,我们定位了 P2P 网络中超过 15% 的以太坊验证者。从我们的去匿名化技术中获得的洞察,提供了关于验证者在对等节点之间的分布、地理位置和托管机构的宝贵信息。我们进一步讨论了 P2P 网络中缺乏匿名性所带来的影响和风险,并提出了帮助验证者保护隐私的方法。
以太坊基金会已授予我们漏洞赏金,以表彰我们研究成果的影响力。
Pdf下载链接:
https://www.usenix.org/system/files/usenixsecurity25-heimbach.pdf
7
Title:
Let's Move2EVM
让我们 Move2EVM
Authors:

Abstract:
The Move programming language, designed with strong safety guarantees such as linear resource semantics and borrow-checking, has emerged as a secure and reliable choice for writing smart contracts. However, these guarantees depend on the assumption that all interacting contracts are well-formed—a condition naturally met in Move's native execution environment but not in heterogeneous or untrusted platforms like the Ethereum Virtual Machine (EVM). This hinders the usage of Move as a source language for such platforms: for instance, we show in this paper that the existing Move-to-EVM compiler is not secure, meaning the compilation of secure Move contracts yields vulnerable EVM bytecode.
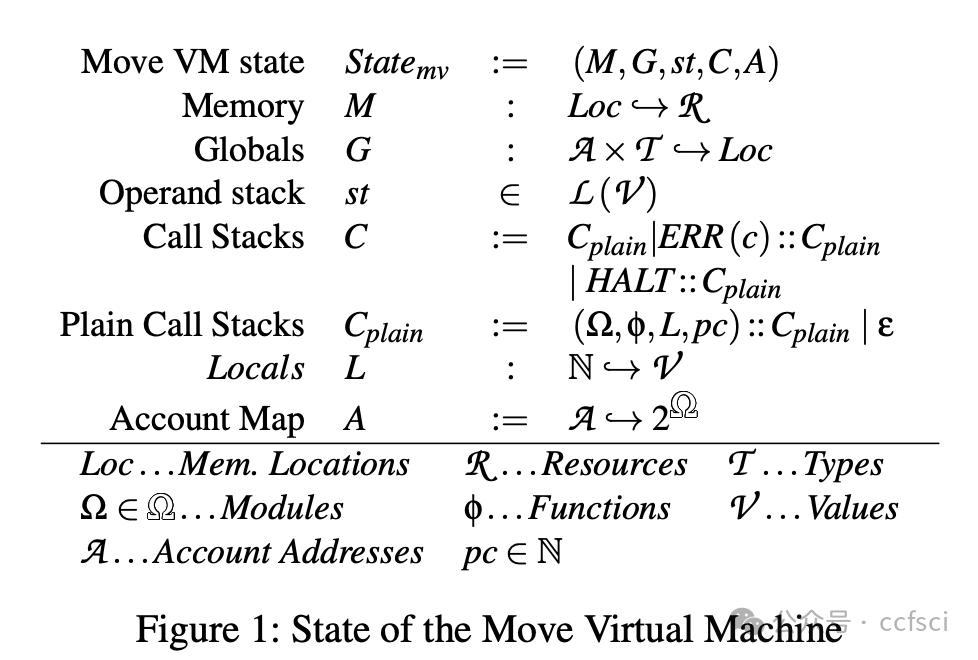
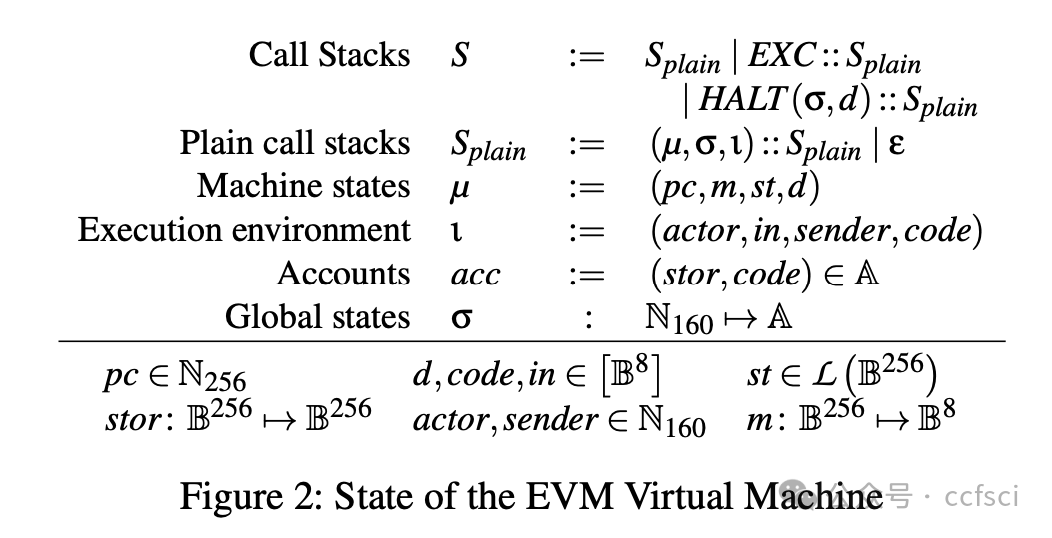
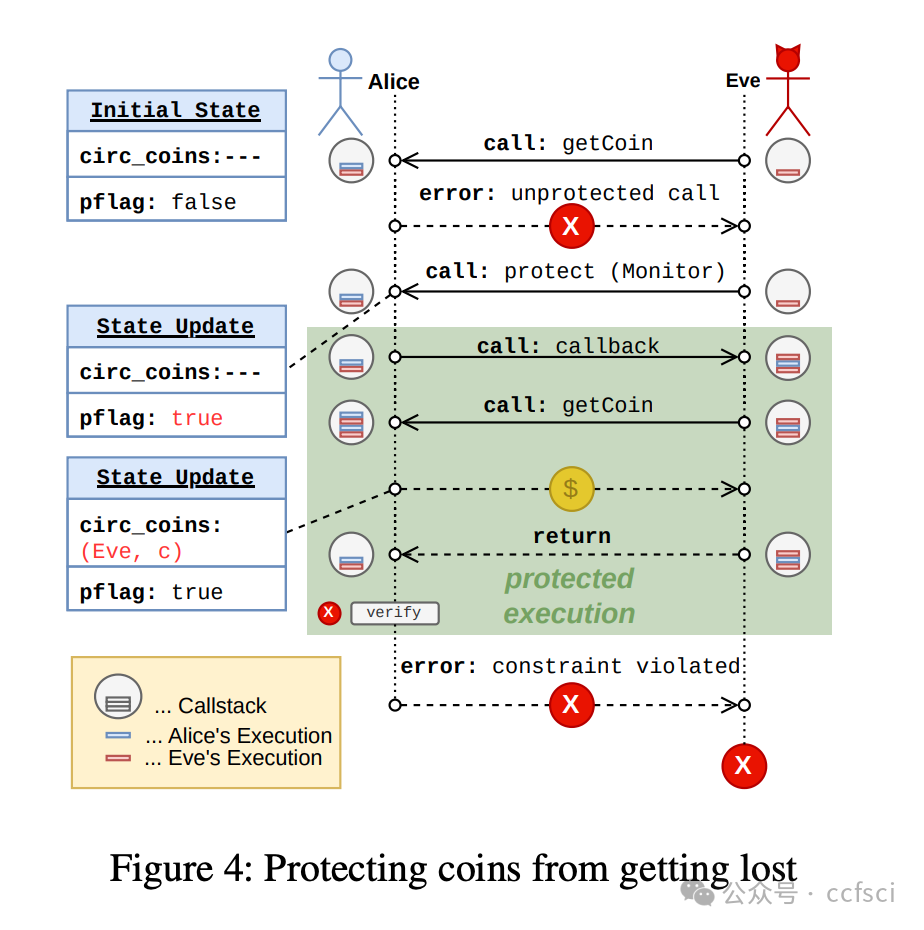
This work addresses the challenge of preserving Move's security guarantees when compiling to EVM. We introduce a novel compiler design extending the existing Move-to-EVM compiler with an Inlined-Reference-Monitor-(IRM)-based protection layer. Our approach enforces Move's linear semantics and borrow-checking rules at runtime in EVM, ensuring the correctness and safety of the compiled smart contracts, even in adversarial execution environments. We formally define the compilation process, establish correctness guarantees for the translation, and implement our protection mechanism in the original compiler. Our evaluation draws on three datasets: (i) an ERC-20 implementation in Solidity and Move, (ii) the Rosetta dataset curated by Bartoletti et al., and (iii) modules scraped from the Aptos blockchain. The performance evaluation shows that the gas cost overhead introduced by our compiler—compared both to the original compiler and Solidity-compiled code—is modest, thereby confirming our approach as a practical solution for bringing the security guarantees of Move code to the EVM.
Move 编程语言设计有强大的安全保障,例如线性资源语义和借用检查,已成为编写智能合约的安全可靠之选。然而,这些保障依赖于所有交互合约都符合规范的假设——这一条件在 Move 的原生执行环境中自然满足,但在以太坊虚拟机 (EVM) 等异构或不可信平台中则无法实现。这阻碍了 Move 作为此类平台的源语言的使用:例如,我们在本文中指出,现有的 Move-to-EVM 编译器并不安全,这意味着编译安全的 Move 合约会产生易受攻击的 EVM 字节码。
这项工作解决了在编译到 EVM 时如何保持 Move 安全保障的挑战。我们引入了一种新颖的编译器设计,在现有的 Move-to-EVM 编译器的基础上,添加了一个基于内联引用监视器 (IRM) 的保护层。我们的方法在 EVM 运行时强制执行 Move 的线性语义和借用检查规则,即使在对抗性执行环境中也能确保编译后的智能合约的正确性和安全性。我们正式定义了编译流程,建立了翻译的正确性保证,并在原始编译器中实现了我们的保护机制。我们的评估基于三个数据集:(i) Solidity 和 Move 语言的 ERC-20 实现,(ii) Bartoletti 等人整理的 Rosetta 数据集,以及 (iii) 从 Aptos 区块链中抓取的模块。性能评估表明,与原始编译器和 Solidity 编译的代码相比,我们的编译器引入的 Gas 成本开销较小,从而证实了我们的方法是一种将 Move 代码的安全保障引入 EVM 的实用解决方案。
Pdf下载链接:
https://www.usenix.org/system/files/usenixsecurity25-benetollo.pdf
