Create/Assemble/Link x64 Windows
假期最后1天,学习一下windows.课程,视频在油管,前面贴过链接。
windows汇编-CSDN博客
有个github地址:AshleyT3/tutorial-sample-code
简介
High-level Overview
1) Write a Windows assembly .asm program.
2) Hands-on with Microsoft macro Assembler(Masm... since 1981!)
3) Setup, use Debugging Tools for Windows with focus on Windbg.
4) x64 calling convention... Overview of Windows x64 shadow store.(aka "shadow space"
5) x64 processor registers,zero-exending
6) Examine stack, shadow area in VS Debugger/WindDbg
7) Assembler .1st listing files, moern reverse engineering listings.
安装
第一步下载visual studio 2022,选择destop程序。我已安装,更新一下:
好久没有更新了,更新时间比较长,听说已经有了2026版本,暂不做大版本升级
然后下载vscode,这个我也有,更新一下。
然后下载windbg,我也下载了,网址:
https://learn.microsoft.com/en-us/windows-hardware/driver/debugger
不要使用这个,安装方法我前面的博客有介绍,可以更新:
debugging tools for windows, 在安装vs2022时已经安装了SDK,这个SDK就包括了windbg
刚刚我更新了vs2022,应该已经更新了SDK,可以再看看
search: 添加或删除程序
search: kit
共有3个:用哪个?
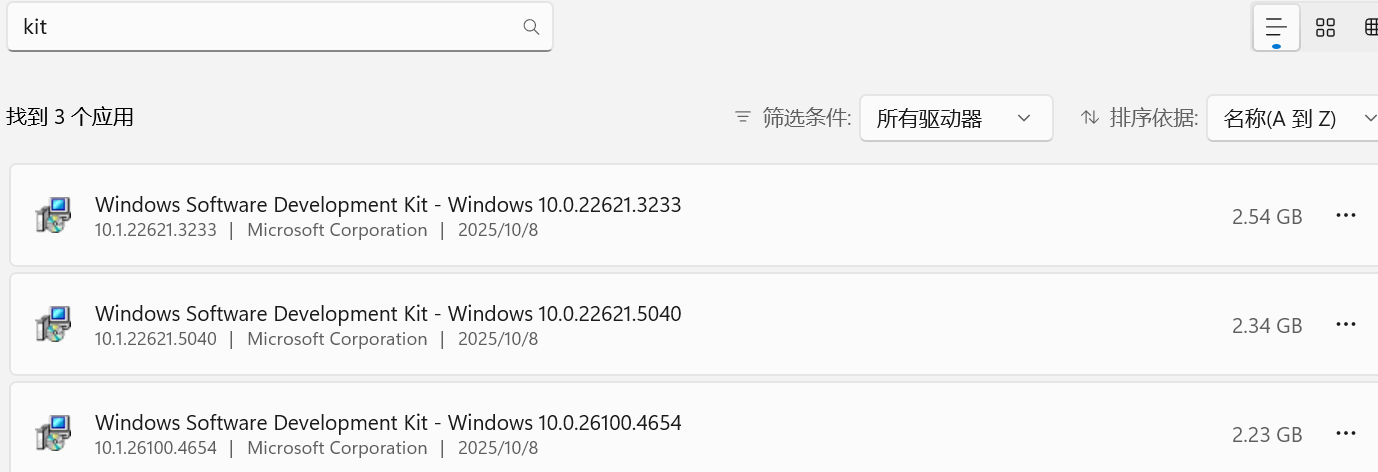
更新:
搜索windbg: 发现在:C:\Program Files (x86)\Windows Kits\10\Debuggers\x64
为了查找方便,copy到一个更浅的目录c:debuggerx64
命令行启动windbg
PS C:\debuggerx64\asm> C:\debuggerx64\windbg
搜索命令行用法:
下面开始用vscode写个汇编程序:
code .
还要检查一下汇编器程序是否可用:ml64
阅读ml64的文档:
ML and ML64 command-line reference | Microsoft Learn
第一个汇编程序
.CODE
.CODE | Microsoft Learn
.CODE
main PROCret
main ENDP
END编译:
C:\asm>ml64 /Zi ourprogram.asm /link /subsystem:console /entry:main /DEBUG
Microsoft (R) Macro Assembler (x64) Version 14.44.35217.0
Copyright (C) Microsoft Corporation. All rights reserved.
Assembling: ourprogram.asm
Microsoft (R) Incremental Linker Version 14.44.35217.0
Copyright (C) Microsoft Corporation. All rights reserved.
/DEBUG
/OUT:ourprogram.exe
ourprogram.obj
/subsystem:console
/entry:main
/DEBUG
/Zi: Add symbolic debug info
C:\asm>link /?
Microsoft (R) Incremental Linker Version 14.44.35217.0
Copyright (C) Microsoft Corporation. All rights reserved.用法: LINK [选项] [文件] [@commandfile]选项:/ALIGN:#/ALLOWBIND[:NO]/ALLOWISOLATION[:NO]/APPCONTAINER[:NO]/ASSEMBLYDEBUG[:DISABLE]/ASSEMBLYLINKRESOURCE:文件名/ASSEMBLYMODULE:文件名/ASSEMBLYRESOURCE:文件名[,[名称][,PRIVATE]]/BASE:{地址[,大小]|@文件名,键}/CLRIMAGETYPE:{IJW|PURE|SAFE|SAFE32BITPREFERRED}/CLRLOADEROPTIMIZATION:{MD|MDH|NONE|SD}/CLRSUPPORTLASTERROR[:{NO|SYSTEMDLL}]/CLRTHREADATTRIBUTE:{MTA|NONE|STA}/CLRUNMANAGEDCODECHECK[:NO]/DEBUG[:{FASTLINK|FULL|NONE}]/DEF:文件名/DEFAULTLIB:库/DELAY:{NOBIND|UNLOAD}/DELAYLOAD:dll/DELAYSIGN[:NO]/DEPENDENTLOADFLAG:flag/DLL/DRIVER[:{UPONLY|WDM}]/DYNAMICBASE[:NO]/DYNAMICDEOPTC:\asm>c:\debuggerx64\windbg.exe ourprogram.exe
windbg界面排列了一下
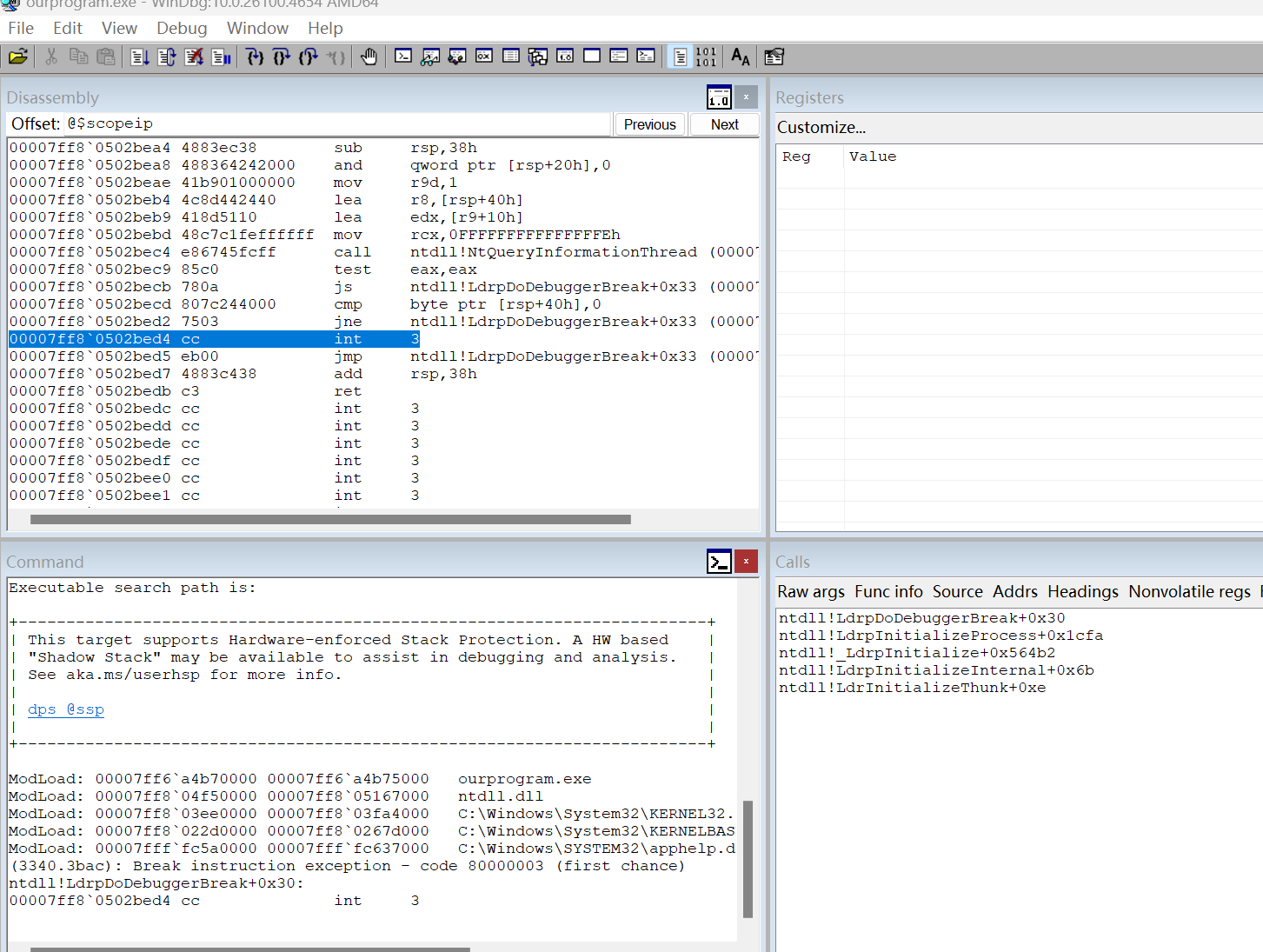
save workspace保存
c:\debuggerx64\windbg.exe -WF mydbhws.WEW ourprogram.exe
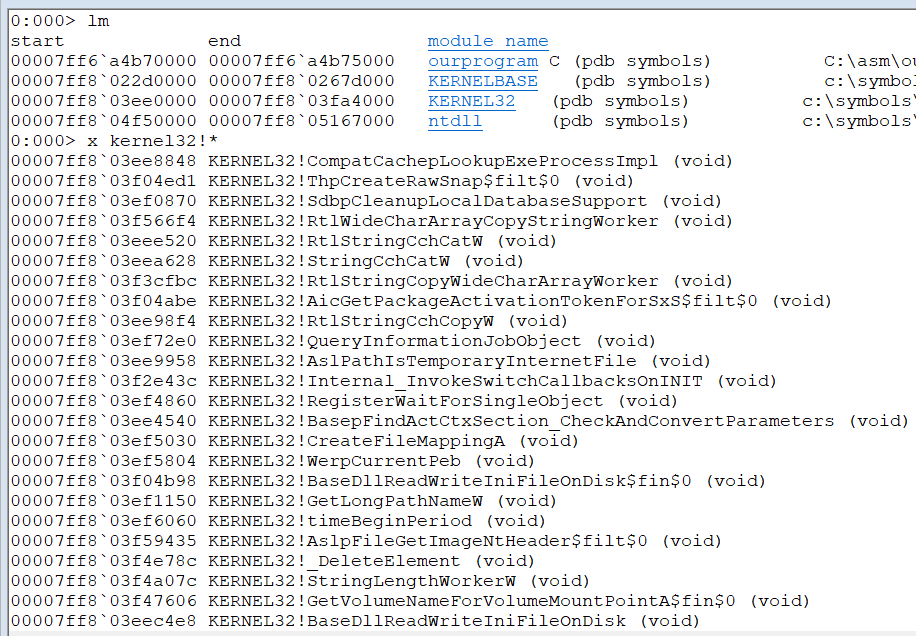
查看模块
0:000> lm
start end module name
00007ff6`a4b70000 00007ff6`a4b75000 ourprogram (deferred)
00007ff8`022d0000 00007ff8`0267d000 KERNELBASE (deferred)
00007ff8`03ee0000 00007ff8`03fa4000 KERNEL32 (deferred)
00007ff8`04f50000 00007ff8`05167000 ntdll (pdb symbols) c:\symbols\ntdll.pdb\3F9B0A9DA2F01CB5571242F6EE73BFD61\ntdll.pdb
0:000> lmDvmourprogram
Browse full module list
start end module name
00007ff6`a4b70000 00007ff6`a4b75000 ourprogram (deferred)
Image path: ourprogram.exe
Image name: ourprogram.exe
Browse all global symbols functions data
Timestamp: Wed Oct 8 20:10:07 2025 (68E6549F)
CheckSum: 00000000
ImageSize: 00005000
Translations: 0000.04b0 0000.04e4 0409.04b0 0409.04e4
Information from resource tables:
查看函数
0:000> x ourprogram!*
*** WARNING: Unable to verify checksum for ourprogram.exe
00007ff6`a4b71010 ourprogram!main (void)
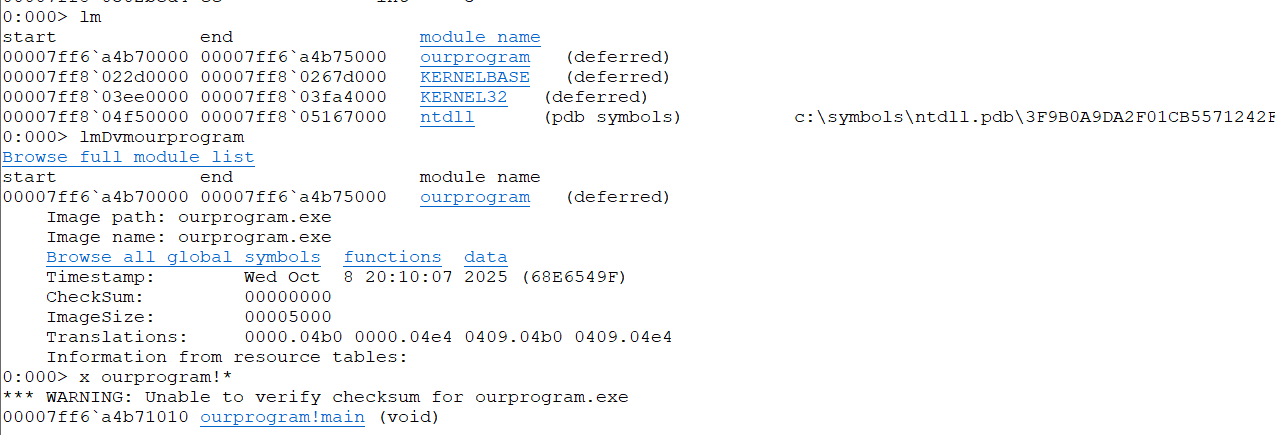
反汇编
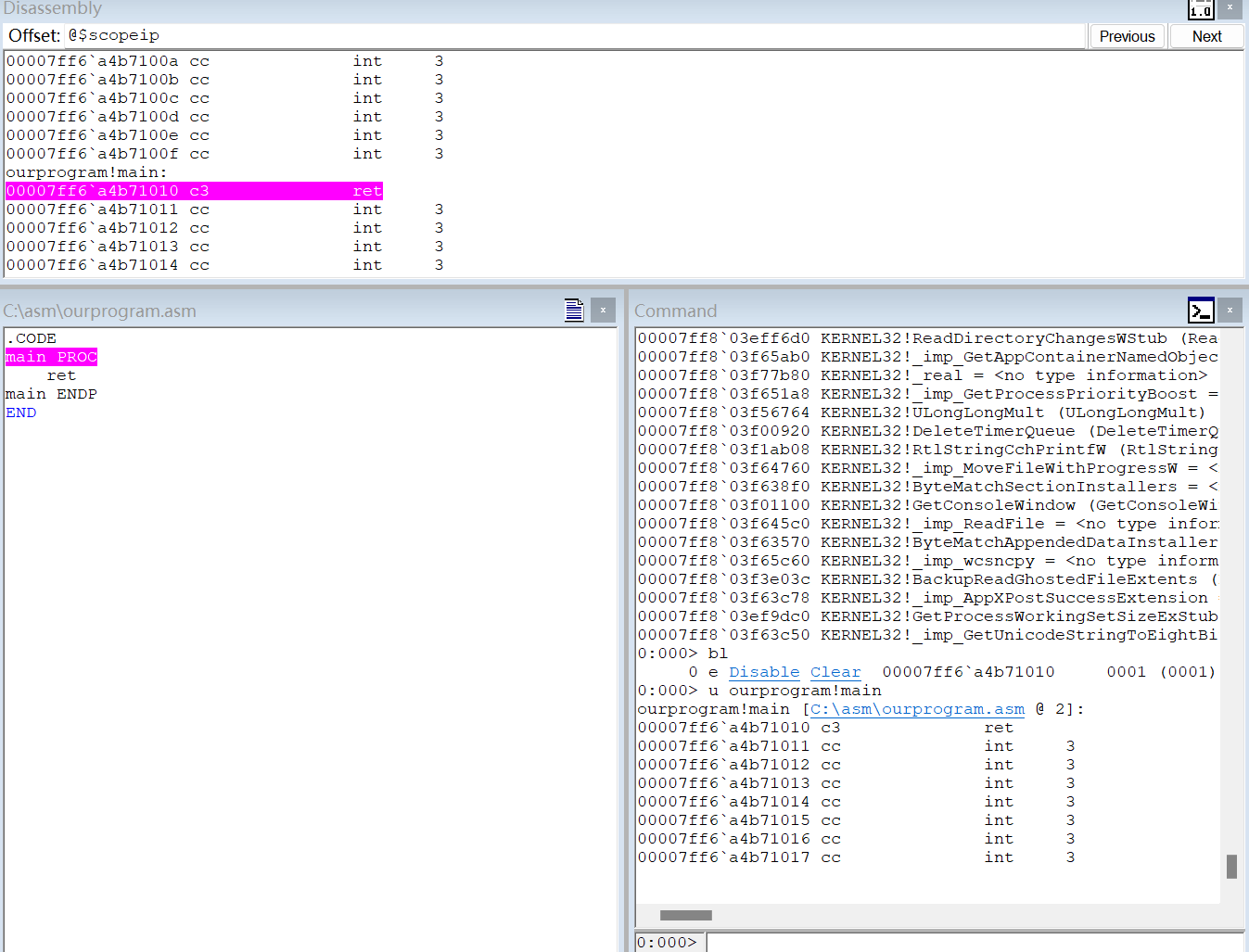
0:000> u ourprogram!main
ourprogram!main [C:\asm\ourprogram.asm @ 2]:
00007ff6`a4b71010 c3 ret
00007ff6`a4b71011 cc int 3
00007ff6`a4b71012 cc int 3
00007ff6`a4b71013 cc int 3
00007ff6`a4b71014 cc int 3
00007ff6`a4b71015 cc int 3
00007ff6`a4b71016 cc int 3
00007ff6`a4b71017 cc int 3
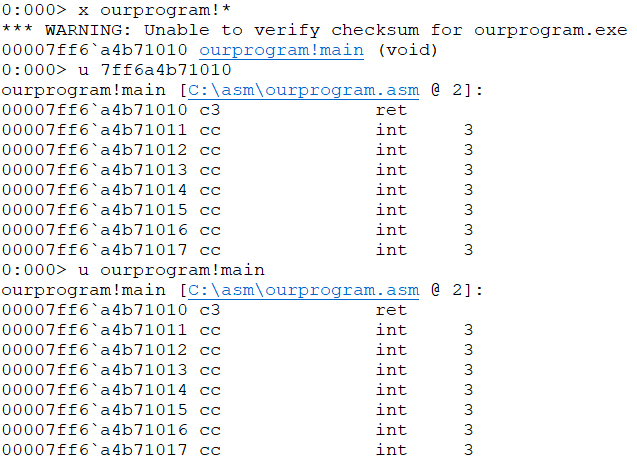
证明确实只有ret一句话,并标明了代码行,windbg确实很强大。
windbg的exe都是基于一个引擎:
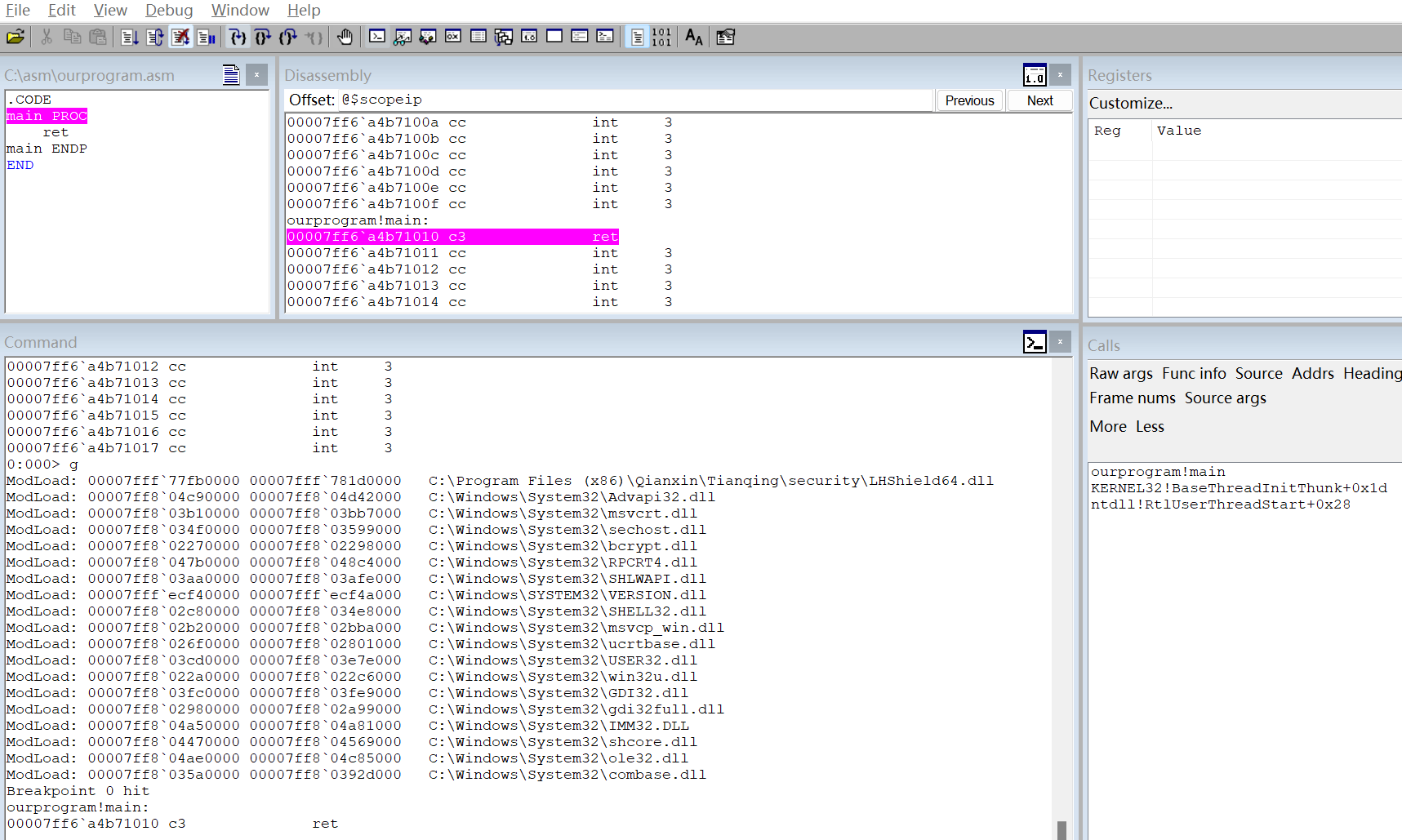
设置断点
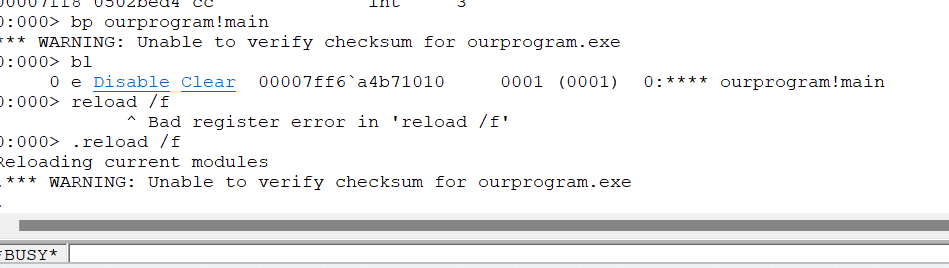
0:000> bp ourprogram!main
*** WARNING: Unable to verify checksum for ourprogram.exe
0:000> bl
0 e Disable Clear 00007ff6`a4b71010 0001 (0001) 0:**** ourprogram!main
有些古老命令源自1980...
D Dump: Dumps memory at specified address.
R Register: Dumps CPU registers.
R Trace: Executes one instruction,stepping in if applicable.
U Unassemble: Disassemble bytes at specified address.
A Assemble: Assembles instructions entered by user into machine code.
G Go: Run the program to the end or next break/exception.
重新加载符号
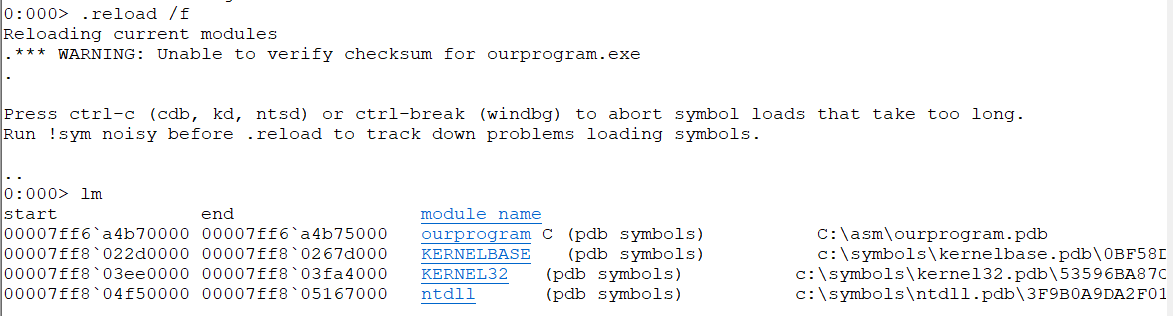
.reload /f
lm 发现PDB全了
x kernel32!*
这个函数就太多了
ctrl+g弹出一个框
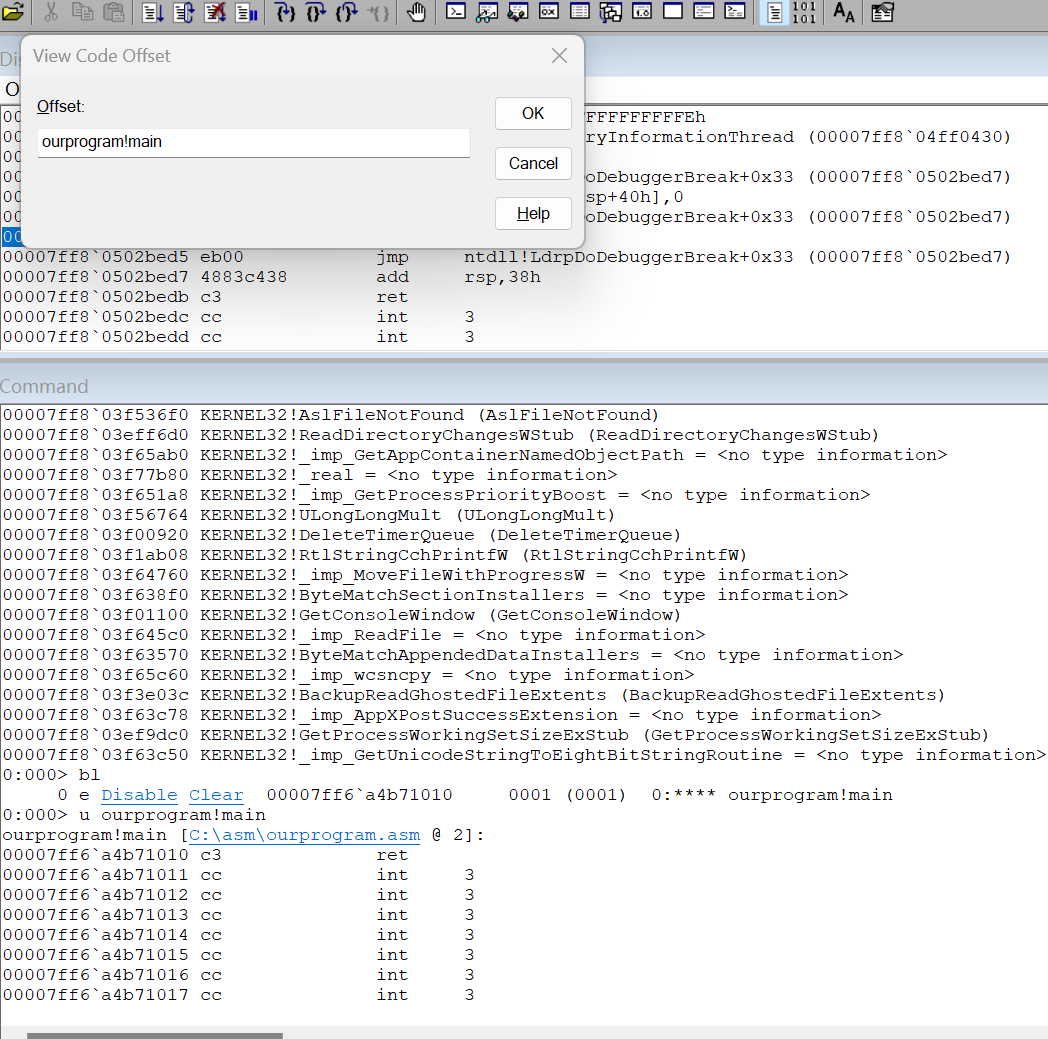
点OK打开了代码