IPsec实验笔记
实验内容和目标
本次实验需要根据实验教程组网要求,搭建实验拓扑,并完成以下实验任务:
(1)配置IPsec+预共享密钥的IKE主模式
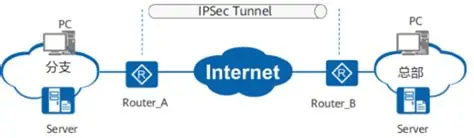
本端RouterA:新华三M9000防火墙,g0/2/12端口ip为:1.1.1.240,业务ip为:192.168.30.0/24
对端RouterB:华为USG6710F防火墙,10ge 0/0/16端口ip为:2.1.1.47,业务ip为:192.168.31.0/24
注:
1、本次采用的是ike是v2版本,因为对端的USG6710F防火墙默认为v2版本,v1版本需要额外打补丁。
2、采用与共享密钥认证方式
配置步骤:
新华三M9000的配置步骤
1、基础接口配置
1.1 接口地址配置
配置公网ip地址和静态路由
<M9000-1>system-view
[M9000-1]interface Ten-GigabitEthernet0/2/12
[M9000-1-Ten-GigabitEthernet0/2/12]ip address 1.1.1.240 26
[M9000-1-Ten-GigabitEthernet0/2/12]]quit
[M9000-1]ip route-static 0.0.0.0 0.0.0.0 1.1.1.192
1.2 配置接口加入安全域
[M9000-1]security-zone name trust
[M9000-1-security-zone-Trust]import interface gigabitethernet 0/2/1
[M9000-1-security-zone-Trust]quit
[M9000-1]security-zone name untrust
[M9000-1-security-zone-untrust]import interface gigabitethernet 0/2/12
[M9000-1-security-zone-untrust]quit
1.3 配置安全策略
配置安全策略放通对端过来方向的untrust和local安全域的流量,用于设备之间可以建立ipsec隧道
a、放通出去方向流量
[M9000-1]security-policy ip
[M9000-1-security-policy-ip]rule name ipseclocalout
[M9000-1-security-policy-ip-1-ipseclocalout]source-zone local
[M9000-1-security-policy-ip-1-ipseclocalout]destination-zone untrust
[M9000-1-security-policy-ip-1-ipseclocalout]source-ip-host 1.1.1.240
[M9000-1-security-policy-ip-1-ipseclocalout]destination-ip-host 2.1.1.47
[M9000-1-security-policy-ip-1-ipseclocalout]action pass
[M9000-1-security-policy-ip-1-ipseclocalout]quit
b、放通进来方向流量
[M9000-1-security-policy-ip]rule name ipseclocalin
[M9000-1-security-policy-ip-1-ipseclocalin]source-zone untrust
[M9000-1-security-policy-ip-1-ipseclocalin]destination-zone local
[M9000-1-security-policy-ip-1-ipseclocalin]source-ip-host 2.1.1.47
[M9000-1-security-policy-ip-1-ipseclocalin]destination-ip-host 1.1.1.240
[M9000-1-security-policy-ip-1-ipseclocalin]action pass
[M9000-1-security-policy-ip-1-ipseclocalin]quit
配置安全策略放通业务地址之间的流量,用于两端业务地址互访
a、放通出去方向流量
[M9000-1-security-policy-ip] rule name trust-untrust
[M9000-1-security-policy-ip-3-trust-untrust] source-zone trust
[M9000-1-security-policy-ip-3-trust-untrust] destination-zone untrust
[M9000-1-security-policy-ip-3-trust-untrust] source-ip-subnet 192.168.30.0 24
[M9000-1-security-policy-ip-3-trust-untrust] destination-ip-subnet 192.168.31.0 24
[M9000-1-security-policy-ip-3-trust-untrust] action pass
[M9000-1-security-policy-ip-3-trust-untrust] quit
b、放通进来方向流量
[M9000-1-security-policy-ip] rule name untrust-trust
[M9000-1-security-policy-ip-4-untrust-trust] source-zone untrust
[M9000-1-security-policy-ip-4-untrust-trust] destination-zone trust
[M9000-1-security-policy-ip-4-untrust-trust] source-ip-subnet 192.168.31.0 24
[M9000-1-security-policy-ip-4-untrust-trust] destination-ip-subnet 192.168.30.0 24
[M9000-1-security-policy-ip-4-untrust-trust] action pass
[M9000-1-security-policy-ip-4-untrust-trust] quit
[M9000-1-security-policy-ip] quit
2、IPSEC配置
2.1 定义业务数据流
[M9000-1] acl advanced 3000
[M9000-1-acl-ipv4-adv-3000] rule permit ip source 192.168.30.0 0.0.0.255 destination 192.168.31.0 0.0.0.255
[M9000-1-acl-ipv4-adv-3000] quit
2.2 配置IKEv2 ISAKMP
[M9000-1]ikev2 proposal 1
[M9000-1-ikev2-proposal-1] encryption aes-cbc-256
[M9000-1-ikev2-proposal-1] integrity sha256
[M9000-1-ikev2-proposal-1] dh group14
[M9000-1-ikev2-proposal-1] prf sha256
[M9000-1-ikev2-proposal-1]qui
2.3 配置IKEv2 Keychain
约定通信双方使用的密钥信息,两端得配置一致
[M9000-1] ikev2 keychain key1
[M9000-1-ikev2-keychain-keychain1] peer ike99191658763
[M9000-1-ikev2-keychain-keychain1-peer-peer1] address 2.1.1.47 255.255.255.255
[M9000-1-ikev2-keychain-keychain1-peer-peer1] identity address 2.1.1.47
[M9000-1-ikev2-keychain-keychain1-peer-peer1] pre-shared-key plaintext abc123456
[M9000-1-ikev2-keychain-keychain1-peer-peer1] quit
[M9000-1-ikev2-keychain-keychain1] quit
2.4 配置IKEv2 profile
约定建立IKE SA所需的安全参数
[M9000-1] ikev2 profile p1
[M9000-1-ikev2-profile-profile1] authentication-method local pre-share
[M9000-1-ikev2-profile-profile1] authentication-method remote pre-share
[M9000-1-ikev2-profile-profile1] keychain key1
[M9000-1-ikev2-profile-profile1] match remote identity address 2.1.1.47 255.255.255.255
[M9000-1-ikev2-profile-profile1] quit
2.5 配置IPsec安全提议
协商封装报文使用的各种安全协议
[M9000-1] ipsec transform-set tran1
[M9000-1-ipsec-transform-set-tran1] encapsulation-mode tunnel
[M9000-1-ipsec-transform-set-tran1] protocol esp
[M9000-1-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-256
[M9000-1-ipsec-transform-set-tran1] esp authentication-algorithm sha256
[M9000-1-ipsec-transform-set-tran1] quit
2.6 配置IPsec安全策略
建立IPsec隧道,保护需要防护的数据流
[M9000-1] ipsec policy ipsec_policy 10 isakmp
[M9000-1-ipsec-policy-isakmp-map1-10] remote-address 2.1.1.47
[M9000-1-ipsec-policy-isakmp-map1-10] security acl 3000
[M9000-1-ipsec-policy-isakmp-map1-10] transform-set tran1
[M9000-1-ipsec-policy-isakmp-map1-10] ikev2-profile p1
[M9000-1-ipsec-policy-isakmp-map1-10] quit
2.7 在接口上应用IPsec策略
对接口上的流量进行保护
[M9000-1] interface gigabitethernet 0/2/12
[M9000-1]-GigabitEthernet 0/2/12] ipsec apply policy ipsec_policy
[M9000-1]-GigabitEthernet 0/2/12]quit
华为USG6710F的配置步骤
1、基础接口配置
1.1 接口地址配置
配置公网ip地址和静态路由[USG] interface 10ge 0/0/16
[USG-GE1/0/9] ip address 2.1.1.47 24
[USG-GE1/0/9] quit
[USG]ip route-static 0.0.0.0 0.0.0.0 2.1.1.1
1.2 配置接口加入安全域
[USG] firewall zone untrust
[USG-zone-untrust] add interface 10ge 0/0/16
[USG-zone-untrust] quit
[USG] firewall zone trust
[USG-zone-trust] add interface 10ge 1/0/5
[USG-zone-trust] quit
1.3 配置安全策略
配置安全策略放通对端过来方向的untrust和local安全域的流量,用于设备之间可以建立ipsec隧道a、放通出去方向流量
[USG] security-policy
[USG-policy-security] rule name 1
[USG-policy-security-rule-3] source-zone local
[USG-policy-security-rule-3] destination-zone untrust
[USG-policy-security-rule-3] source-address 2.1.1.47 24
[USG-policy-security-rule-3] destination-address 1.1.1.240 24
[USG-policy-security-rule-3] action permit
[USG-policy-security-rule-3] quit
b、放通进来方向流量
[USG-policy-security] rule name 2
[USG-policy-security-rule-4] source-zone untrust
[USG-policy-security-rule-4] destination-zone local
[USG-policy-security-rule-4] source-address 1.1.1.240 24
[USG-policy-security-rule-4] destination-address 2.1.1.47 24
[USG-policy-security-rule-4] action permit
[USG-policy-security-rule-4] quit
配置安全策略放通业务地址之间的流量,用于两端业务地址互访
a、放通出去方向流量
[USG-policy-security] rule name 3
[USG-policy-security-rule-2] source-zone trust
[USG-policy-security-rule-2] destination-zone untrust
[USG-policy-security-rule-2] source-address 192.168.31.0 24
[USG-policy-security-rule-2] destination-address 192.168.30.0 24
[USG-policy-security-rule-2] action permit
[USG-policy-security-rule-2] quit
b、放通进来方向流量
[USG-policy-security] rule name 4
[USG-policy-security-rule-1] source-zone untrust
[USG-policy-security-rule-1] destination-zone trust
[USG-policy-security-rule-1] source-address 192.168.30.0 24
[USG-policy-security-rule-1] destination-address 192.168.31.0 24
[USG-policy-security-rule-1] action permit
[USG-policy-security-rule-1] quit
2、IPSEC配置
2.1 定义业务数据流
源地址为192.168.30.0/24,目的地址为192.168.31.0/24的报文,需要经过IPSec隧道传输
[USG] acl 3000
[USG-acl4-advance-3000] rule permit ip source 192.168.31.0 0.0.0.255 destination 192.168.30.0 0.0.0.255
[USG-acl4-advance-3000] quit
2.2 配置IKEv2 SA
ikev1版本需要安装weakea特性包和IKEv1模块文件包,v1特性包安装过程如下,
<USG_A>install feature-software WEAKEA
<USG> install-module Product_Version_IKEv1_MOD00X.MOD
配置IKE安全提议,指定加密算法、认证算法、DH。由于本次没有安装IKEv1模块包,默认使用ikev2版本
[USG] ike proposal 1
[USG-ike-proposal-1] encryption-algorithm aes-256
[USG-ike-proposal-1] authentication-algorithm sha2-256
[USG-ike-proposal-1] authentication-method pre-share
[USG-ike-proposal-1] integrity-algorithm hmac-sha2-256
[USG-ike-proposal-1] dh group14
[USG-ike-proposal-1] prf hmac-sha2-256
[USG-ike-proposal-1] quit
2.3 配置IKEv2对等体
配置IKE对等体,指定协商模式、IKE版本、预共享密钥,对端IP地址。
如果使用的是v1版本,peer里面就要undo version 2,但我使用的是v2对接,默认就是v2版本,模式为主模式
[USG] ike peer h3c
[USG-ike-peer-h3c] ike-proposal 1
[USG-ike-peer-h3c] pre-shared-key abc123456
[USG-ike-peer-h3c] remote-address 1.1.1.240
[USG-ike-peer-h3c] quit
2.4 配置IPsec安全提议
指定封装模式、安全协议,加密算法、认证算法
[USG]ipsec proposal tran1
[USG-ipsec-proposal-tran1]esp authentication-algorithm sha2-256
[USG-ipsec-proposal-tran1]esp encryption-algorithm aes-256
[USG-ipsec-proposal-tran1]quit
2.5 配置IPsec策略
绑定IKE对等体、IPSec安全提议、ACL
[USG] ipsec policy map1 1 isakmp
[USG-ipsec-policy-isakmp-map1-1] ike-peer h3c
[USG-ipsec-policy-isakmp-map1-1] proposal tran1
[USG-ipsec-policy-isakmp-map1-1] security acl 3000
[USG-ipsec-policy-isakmp-map1-1] quit
2.6 在接口上应用IPsec策略
[USG]interface 10ge 0/0/16
[USG-10GE0/0/16]ipsec policy map1
[USG-10GE0/0/16]quit
结果验证
由于对方设备不能远程去操作,故只需看本端专题亦可
1、第一阶段
查看第一阶段的IKEv2 sa是否建立成功,看到status为EST表面IKEv2 sa建立成功
<M9000-1>dis ikev2 sa
Tunnel ID Local Remote Status
---------------------------------------------------------------------------
79743 1.1.1.240/500 2.1.1.47/500 EST
Status:
IN-NEGO: Negotiating, EST: Established, DEL:Deleting
2、第二阶段
查看第二阶段的ipsec sa是否建立成功,若显示如下信息,表明IPSec SA建立成功。
<M9000-1>dis ipsec sa
-------------------------------
Interface: Ten-GigabitEthernet0/2/12 //外网接口
-------------------------------
-----------------------------
IPsec policy: ipsec_policy
Sequence number: 10
Mode: ISAKMP
Flow table status: Active //policy状态active
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N
Traffic Flow Confidentiality enable: N
Transmitting entity: Initiator
Path MTU: 1424
Tunnel:
local address: 1.1.1.240
remote address: 2.1.1.47
Flow:
sour addr: 192.168.30.0/255.255.255.0 port: 0 protocol: ip
dest addr: 192.168.31.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 2934505847 (0xaee90177)
Connection ID: 1593432866817
Transform set: ESP-ENCRYPT-AES-CBC-256 ESP-AUTH-SHA256
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/214
Max received sequence-number: 0
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 280614243 (0x10b9d563)
Connection ID: 673609785802752
Transform set: ESP-ENCRYPT-AES-CBC-256 ESP-AUTH-SHA256
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/214
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: N
Status: Active
3、业务测试
广州侧业务地址:192.168.30.1去ping北京侧业务地址:192.168.31.1也能通
<M9000-1>ping -a 192.168.30.1 192.168.31.1
