了解学习DNS服务管理
一、概述
作用
正向解析:将已知的域名解析为IP地址
反向解析:将已知的IP地址解析为域名
监听端口
53/udp | 53/TCP
默认运行用户
named
二、 完全限定域名
组成
主机名.三级域.二级域名.顶级域名.
域类型
| 类型 | 举例 |
|---|---|
| 根域 | . |
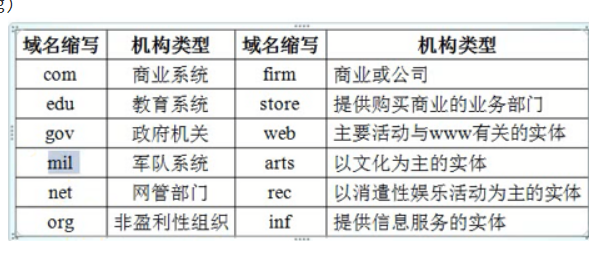
| 顶级域 | cn、hk、uk、org、edu、com、mil、gov、net |
| 二级域 | baidu、163、sina、sohu |
三、DNS解析过程
客户端如何解析域名(必须背会)
本地DNS缓存
本地hosts文件,在DNS服务器诞生之前,所有的主机之间都是通过hosts文件进行的。
指向的DNS服务器IP:
递归查询:直接给出解析结果,客户机与本地DNS服务器之间的查询。(所答即所问)迭代查询:没有给出解析结果,本地DNS服务器与根等其他DNS服务器之间的查询。(所答非所问)
四、域名服务器的分类
1.根域名服务器:最高层次的域名服务器,也是最重要的域名服务器。所有的根域名服务器都知道所有的顶级域名服务器的域名和IP地址。
2.顶级域名服务器:负责管理该顶级域名注册的二级域名。
3.权限域名服务器:负责一个“区”的域名服务器。
4.本地域名服务器:本地域名服务器不属于域名服务器的层次结构,但是它对域名系统非常重要。当一个主机发出DNS查询请求时,这个查询请求报文就发送给本地域名服务器
根据应用场景
主服务器(Primary Name server) 为客户端提供域名解析的主要区域,主DNS服务器宕机,会启用从DNS服务器提供服务。
辅助服务器(Second Name Server) 主服务器DNS长期无应答,从服务器也会停止提供服务,主从区域治安的同步采用周期性检查+通知的机制,从服务器周期性地检查主服务器上地记录情况,一旦发现修改就会同步,另外主服务器上如果又数据被修改了,会立即通知从服务器更新记录。
高速缓存服务器(Cache-only server) 缓存服务器是一种不负责域名数据维护,也不负责域名解析地DNS服务类型。它将用户经常使用到的域名与IP地址解析记录保存在主机本地中,来提升下次解析的效率。
五、DNS服务器部署
安装bind包
yum install -y bind
核心文件解析
####查看安装生成的核心文件###
[root@localhost ~]# rpm -ql bind
/etc/named.conf #服务主配置文件
/etc/named.rfc1912.zones #服务主配置的额外配置文件
/var/named #区域文件数据目录
/var/named/named.ca #可信的根域名服务器,不要擅自更改
/var/named/named.empty #区域文件的模版文件
/var/named/named.localhost #区域文件的本地接口模版文件
/var/named/named.loopback #区域文件回环接口的模版文件
/var/named/slaves #从服务器的区域数据存储目录
/var/log/named.log #服务日志文件
命令解析
/usr/sbin/named #主服务运行命令
/usr/sbin/named-checkconf #服务主配置语法检查命令
/usr/sbin/named-checkzone #区域文件配置语法检查命令
/usr/sbin/named-journalprint #打印named程序运行日志正向解析文件配置
[root@localhost named]# cat jx.com.zone
$TTL 3H
@ IN SOA jx.com. root.jx.com. (0 ; serial1D ; refresh1H ; retry1W ; expire3H ) ; minimum
@ NS dns1.jx.com.
dns1 A 192.168.115.128
www A 192.168.115.129
mail A 192.168.115.130
ftp A 192.168.115.131
ww CNAME www.jx.com.
mail MX 10 mail.jx.com.反向解析文件配置
[root@localhost named]# cat 192.168.115.zone
$TTL 3H
@ IN SOA jx.com. root.jx.com. (0 ; serial1D ; refresh1H ; retry1W ; expire3H ) ; minimum
@ NS dns1.jx.com.
128 PTR dns1.jx.com.
129 PTR www.jx.com.
130 PTR mail.jx.com.
131 PTR ftp.jx.com.
启动服务
[root@localhost named]# systemctl start named六、 配置DNS主从架构
主服务配置
//
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
// See the BIND Administrator's Reference Manual (ARM) for details about the
// configuration located in /usr/share/doc/bind-{version}/Bv9ARM.htmloptions {listen-on port 53 { 192.168.115.128; };listen-on-v6 port 53 { ::1; };directory "/var/named";dump-file "/var/named/data/cache_dump.db";statistics-file "/var/named/data/named_stats.txt";memstatistics-file "/var/named/data/named_mem_stats.txt";recursing-file "/var/named/data/named.recursing";secroots-file "/var/named/data/named.secroots";allow-query { any; };/* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.- If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so willcause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatlyreduce such attack surface */recursion yes;dnssec-enable yes;dnssec-validation yes;/* Path to ISC DLV key */bindkeys-file "/etc/named.root.key";managed-keys-directory "/var/named/dynamic";pid-file "/run/named/named.pid";session-keyfile "/run/named/session.key";
};logging {channel default_debug {file "data/named.run";severity dynamic;};
};zone "." IN {type hint;file "named.ca";
};include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";定义区域文件配置
// named.rfc1912.zones:
//
// Provided by Red Hat caching-nameserver package
//
// ISC BIND named zone configuration for zones recommended by
// RFC 1912 section 4.1 : localhost TLDs and address zones
// and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt
// (c)2007 R W Franks
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//zone "jx.com" IN {type master;file "jx.com.zone";allow-update { none; };allow-transfer { 192.168.115.132; };
};zone "115.168.192.in-addr.arpa" IN {type master;file "192.168.115.zone";allow-update { none; };allow-transfer { 192.168.115.132; };
};
从服务器配置
//
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
// See the BIND Administrator's Reference Manual (ARM) for details about the
// configuration located in /usr/share/doc/bind-{version}/Bv9ARM.htmloptions {listen-on port 53 { 192.168.115.132; };listen-on-v6 port 53 { ::1; };directory "/var/named";dump-file "/var/named/data/cache_dump.db";statistics-file "/var/named/data/named_stats.txt";memstatistics-file "/var/named/data/named_mem_stats.txt";recursing-file "/var/named/data/named.recursing";secroots-file "/var/named/data/named.secroots";allow-query { any; };/* - If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.- If you are building a RECURSIVE (caching) DNS server, you need to enable recursion. - If your recursive DNS server has a public IP address, you MUST enable access control to limit queries to your legitimate users. Failing to do so willcause your server to become part of large scale DNS amplification attacks. Implementing BCP38 within your network would greatlyreduce such attack surface */recursion yes;dnssec-enable yes;dnssec-validation yes;/* Path to ISC DLV key */bindkeys-file "/etc/named.root.key";managed-keys-directory "/var/named/dynamic";pid-file "/run/named/named.pid";session-keyfile "/run/named/session.key";
};logging {channel default_debug {file "data/named.run";severity dynamic;};
};zone "." IN {type hint;file "named.ca";
};include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";定义区域文件配置
// named.rfc1912.zones:
//
// Provided by Red Hat caching-nameserver package
//
// ISC BIND named zone configuration for zones recommended by
// RFC 1912 section 4.1 : localhost TLDs and address zones
// and http://www.ietf.org/internet-drafts/draft-ietf-dnsop-default-local-zones-02.txt
// (c)2007 R W Franks
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//zone "jx.com" IN {type slave;file "slaves/jx.com.zone"; masters { 192.168.115.128; }; ##主服务器地址
};
zone "115.168.192.in-addr.arpa" IN {type slave;file "slaves/192.168.115.zone";masters { 192.168.115.128; };
};
启动服务
[root@localhost named]# systemctl start named