30、ICS/OT 攻击溯源 (电力系统) 模拟组件 - /安全与维护组件/ics-attack-forensics
76个工业组件库示例汇总
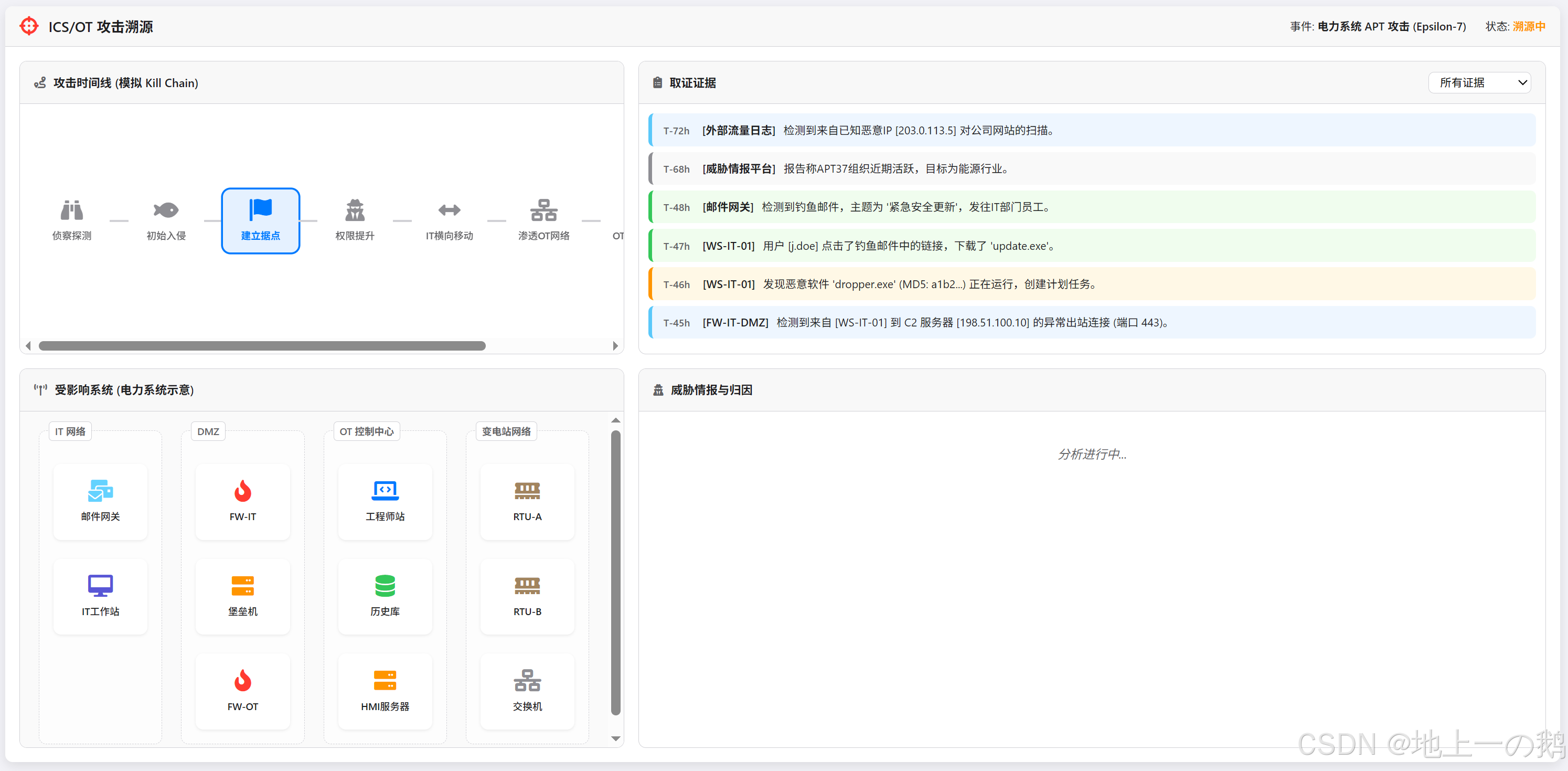
ICS/OT 攻击溯源 (电力系统) 模拟组件
1. 组件概述
ics-attack-forensics 组件是一个前端模拟界面,旨在可视化展示针对工业控制系统 (ICS) / 操作技术 (OT) 环境的网络攻击溯源过程。该组件特别模拟了一个针对电力系统的复杂持续性威胁 (APT) 攻击场景,帮助用户(如安全分析师、学生、运维人员)理解攻击链、分析取证数据、识别受影响系统,并关联威胁情报。
它提供了一个交互式的环境,用于探索攻击的不同阶段,并查看在每个阶段可能收集到的证据类型。
2. 核心功能
- 攻击时间线可视化: 以类似 MITRE ATT&CK Kill Chain 的方式,展示攻击从初始侦察到最终影响的各个阶段。
- 清晰标记当前分析阶段。
- 鼠标悬停显示阶段描述。
- 点击阶段可聚焦相关证据和系统影响。
- 多源取证证据展示: 模拟展示来自不同来源的日志和证据,包括:
- 网络流量日志 (Network Logs)
- 主机事件日志 (Host Logs)
- 恶意软件分析指标 (Malware Indicators)
- ICS 操作记录 (ICS Operational Data)
- 威胁情报信息 (Threat Intelligence)
- 证据筛选与排序: 用户可以根据证据类型(网络、主机、恶意软件、ICS)进行筛选,并按时间戳排序,以便快速定位关键信息。
- 受影响系统可视化: 提供一个简化的电力系统架构图(包含 IT、DMZ、OT 控制中心、变电站等区域),并根据所选攻击阶段高亮显示:
involved(卷入): 攻击过程中被利用或经过的系统。affected(受影响): 攻击最终目标或直接遭受破坏的系统,通常带有动画效果。
- 威胁情报关联: 展示与模拟攻击相关的威胁情报信息:
- 攻击归属 (Attribution)
- 攻击动机 (Motivation)
- 使用的战术、技术和过程 (TTPs, 映射到 MITRE ATT&CK for ICS 框架)
- 关键危害指标 (IOCs),如恶意 IP、域名、文件哈希等。
- 响应式设计: 界面布局能在不同屏幕尺寸下自动调整,保证可用性。
- 苹果科技工业风格: 采用简洁、清晰、现代化的界面设计风格。
3. 文件结构
安全与维护组件/
└── ics-attack-forensics/├── index.html # 组件的 HTML 结构,定义了各个面板布局├── styles.css # CSS 样式文件,负责组件的外观和响应式设计├── script.js # JavaScript 文件,包含模拟逻辑、数据处理和交互└── README.md # 组件说明文档 (本文件)
4. 使用方法
- 确保你的计算机上有现代网页浏览器(如 Chrome, Firefox, Edge)。
- 直接在浏览器中打开
安全与维护组件/ics-attack-forensics/index.html文件。 - 界面加载后,默认会显示第一个攻击阶段及其相关的证据。
- 交互:
- 点击攻击时间线上的不同阶段图标,可以切换当前分析的焦点。
- 证据面板右上角的下拉菜单可以选择筛选不同类型的证据。
- 观察受影响系统面板,高亮的设备会随着时间线的推进而变化。
- 查看威胁情报面板获取攻击的背景信息。
5. 技术栈
- HTML5: 构建页面结构。
- CSS3: 样式设计、布局(Grid)、动画和响应式设计。
- JavaScript (ES6+): 实现模拟逻辑、DOM 操作、事件处理和数据可视化驱动。
- Font Awesome: 提供图标。
6. 模拟说明与限制
- 内置场景: 当前版本内置了一个硬编码的、针对电力系统的 APT 攻击场景 (
attackScenario对象在script.js中定义)。所有展示的数据(时间线、证据、系统状态、情报)都基于这个预设场景。 - 非实时模拟: 这不是一个实时的动态模拟器。它主要用于展示一个已完成攻击的溯源分析过程。
- 简化模型: 无论是电力系统架构图还是攻击证据链,都是为了教学和演示目的而简化的模型,并未完全反映真实世界的复杂性。
- 数据来源: 所有数据均为模拟生成,并非来自真实攻击事件。
效果展示
源码
index.html
<!DOCTYPE html>
<html lang="zh-CN">
<head><meta charset="UTF-8"><meta name="viewport" content="width=device-width, initial-scale=1.0"><title>ICS/OT 攻击溯源 (电力系统)</title><link rel="stylesheet" href="styles.css"><!-- Font Awesome for Icons --><link rel="stylesheet" href="https://cdnjs.cloudflare.com/ajax/libs/font-awesome/6.0.0/css/all.min.css">
</head>
<body><div class="app-container"><!-- Header --><header class="app-header"><div class="header-title"><i class="fas fa-crosshairs header-icon"></i><h1>ICS/OT 攻击溯源</h1></div><div class="attack-summary"><span>事件: <strong id="attack-event-name">电力系统 APT 攻击 (Epsilon-7)</strong></span><span>状态: <strong id="attack-status">分析中</strong></span></div></header><!-- Main Content Grid --><main class="app-content"><!-- Attack Timeline Panel --><section class="panel timeline-panel"><div class="panel-header"><h2><i class="fas fa-route"></i> 攻击时间线 (模拟 Kill Chain)</h2></div><div id="attack-timeline" class="panel-content timeline-content"><!-- Timeline stages will be added by JS --><div class="timeline-stage" data-stage-id="initial-access" title="初始访问 - 钓鱼邮件攻击工程师站"><div class="stage-icon"><i class="fas fa-envelope-open-text"></i></div><div class="stage-name">初始访问</div></div><div class="timeline-connector"></div><div class="timeline-stage" data-stage-id="execution" title="执行 - 恶意软件在工程师站运行"><div class="stage-icon"><i class="fas fa-play-circle"></i></div><div class="stage-name">执行</div></div><div class="timeline-connector"></div><div class="timeline-stage" data-stage-id="persistence" title="持久化 - 恶意软件建立后门"><div class="stage-icon"><i class="fas fa-user-secret"></i></div><div class="stage-name">持久化</div></div><div class="timeline-connector"></div><div class="timeline-stage" data-stage-id="lateral-movement" title="横向移动 - 从工程师站扫描并访问RTU"><div class="stage-icon"><i class="fas fa-exchange-alt"></i></div><div class="stage-name">横向移动</div></div><div class="timeline-connector"></div><div class="timeline-stage" data-stage-id="collection" title="收集 - 读取RTU配置和状态"><div class="stage-icon"><i class="fas fa-folder-open"></i></div><div class="stage-name">收集</div></div><div class="timeline-connector"></div><div class="timeline-stage" data-stage-id="command-control" title="命令与控制 - 与外部C2服务器通信"><div class="stage-icon"><i class="fas fa-satellite-dish"></i></div><div class="stage-name">命令控制</div></div><div class="timeline-connector"></div><div class="timeline-stage" data-stage-id="impact" title="影响 - 向RTU发送非法控制指令"><div class="stage-icon"><i class="fas fa-bolt"></i></div><div class="stage-name">影响</div></div></div></section><!-- Evidence Log Panel --><section class="panel evidence-panel"><div class="panel-header"><h2><i class="fas fa-clipboard-list"></i> 取证证据</h2><select id="evidence-filter" class="header-filter"><option value="all">所有证据</option><option value="network">网络日志</option><option value="host">主机日志</option><option value="malware">恶意软件指标</option><option value="ics">ICS操作记录</option></select></div><div id="evidence-log" class="panel-content log-content scrollable"><p class="placeholder">请选择攻击时间线阶段以查看相关证据...</p><!-- Evidence entries will be loaded here --></div></section><!-- Affected Systems Panel --><section class="panel systems-panel"><div class="panel-header"><h2><i class="fas fa-broadcast-tower"></i> 受影响系统 (电力系统示意)</h2></div><div id="affected-systems" class="panel-content systems-map"><!-- Simplified Power System Diagram --><div class="system-zone it-zone"><div class="zone-label">IT 网络</div><div class="system-device email-gw" data-device-id="EMAIL-GW" title="邮件网关"><div><i class="fas fa-mail-bulk"></i><span>邮件网关</span></div></div><div class="system-device ws-it" data-device-id="WS-IT" title="IT办公网络工作站"><div><i class="fas fa-desktop"></i><span>IT工作站</span></div></div></div><div class="system-zone dmz-zone"><div class="zone-label">DMZ</div><div class="system-device fw-it-dmz" data-device-id="FW-IT-DMZ" title="IT-DMZ防火墙"><div><i class="fas fa-fire-alt"></i><span>FW-IT</span></div></div><div class="system-device jump-server" data-device-id="JUMP" title="堡垒机/跳转服务器"><div><i class="fas fa-server"></i><span>堡垒机</span></div></div><div class="system-device fw-dmz-ot" data-device-id="FW-DMZ-OT" title="DMZ-OT防火墙"><div><i class="fas fa-fire-alt"></i><span>FW-OT</span></div></div></div><div class="system-zone ot-control-zone"><div class="zone-label">OT 控制中心</div><div class="system-device eng-ws-ot" data-device-id="ENG-WS-OT" title="工程师站(OT)"><div><i class="fas fa-laptop-code"></i><span>工程师站</span></div></div><div class="system-device historian-ot" data-device-id="HIST-OT" title="历史数据库(OT)"><div><i class="fas fa-database"></i><span>历史库</span></div></div><div class="system-device hmi-server" data-device-id="HMI-SRV" title="HMI服务器"><div><i class="fas fa-server"></i><span>HMI服务器</span></div></div></div><div class="system-zone ot-substation-zone"><div class="zone-label">变电站网络</div><div class="system-device rtu-a" data-device-id="RTU-A" title="RTU A (变电站1)"><div><i class="fas fa-memory"></i><span>RTU-A</span></div></div><div class="system-device rtu-b" data-device-id="RTU-B" title="RTU B (变电站2)"><div><i class="fas fa-memory"></i><span>RTU-B</span></div></div><div class="system-device field-switch" data-device-id="SW-SUB" title="变电站交换机"><div><i class="fas fa-network-wired"></i><span>交换机</span></div></div></div><!-- Connections represented visually by CSS/Layout --></div></section><!-- Threat Intel Panel --><section class="panel intel-panel"><div class="panel-header"><h2><i class="fas fa-user-secret"></i> 威胁情报与归因</h2></div><div id="threat-intel" class="panel-content intel-content"><p class="placeholder">分析进行中...</p><!-- Threat intel info (APT group, TTPs, IOCs) loaded here --><!-- Example Structure:<div class="intel-section"><h4>疑似攻击者: SandWorm Variant (模拟)</h4><p>与已知的针对能源行业的国家背景攻击活动特征相似。</p></div><div class="intel-section"><h4>关键 TTPs (MITRE ATT&CK for ICS):</h4><ul><li><span class="ttp-id">T0886</span> - Spearphishing Attachment</li><li><span class="ttp-id">T0869</span> - Standard Application Layer Protocol</li><li><span class="ttp-id">T0845</span> - Remote System Discovery</li><li><span class="ttp-id">T0813</span> - Command-Line Interface</li><li><span class="ttp-id">T0884</span> - Connection Proxy</li><li><span class="ttp-id">T0831</span> - Manipulation of Control</li></ul></div><div class="intel-section"><h4>关键 IOCs:</h4><ul class="ioc-list"><li><span class="ioc-type file">文件Hash:</span> <span class="ioc-value">e8a3...d9f4</span></li><li><span class="ioc-type ip">C2 IP:</span> <span class="ioc-value">185.x.x.x</span></li><li><span class="ioc-type domain">C2 域名:</span> <span class="ioc-value">updates.secure-dns.org</span></li></ul></div>--></div></section></main></div><script src="script.js"></script>
</body>
</html>
styles.css
:root {--primary-color: #007aff; /* Apple Blue */--secondary-color: #8e8e93; /* Apple Gray */--background-color: #f2f2f7;--panel-background-color: #ffffff;--text-color: #1c1c1e;--text-color-secondary: #636366;--border-color: #d1d1d6;--success-color: #34c759; /* Apple Green */--warning-color: #ff9500; /* Apple Orange */--error-color: #ff3b30; /* Apple Red */--info-color: #5ac8fa; /* Apple Light Blue */--timeline-active-color: var(--primary-color);--timeline-inactive-color: var(--secondary-color);--evidence-network-bg: #eef6ff;--evidence-host-bg: #f0fdee;--evidence-malware-bg: #fff8e6;--evidence-ics-bg: #ffebee;--affected-color: var(--error-color);--involved-color: var(--warning-color);--font-family: -apple-system, BlinkMacSystemFont, "Segoe UI", Roboto, Helvetica, Arial, sans-serif;--border-radius: 8px;--panel-padding: 15px;--panel-header-height: 45px;--animation-duration: 0.3s;
}* {box-sizing: border-box;margin: 0;padding: 0;
}body {font-family: var(--font-family);background-color: var(--background-color);color: var(--text-color);line-height: 1.5;font-size: 13px;overflow-x: hidden;
}.app-container {display: flex;flex-direction: column;height: 100vh; /* Fallback */height: 100dvh;max-height: 800px; /* Limit height */overflow: hidden;background-color: var(--panel-background-color);border-radius: var(--border-radius);box-shadow: 0 4px 12px rgba(0, 0, 0, 0.1);margin: 10px;
}/* Header */
.app-header {display: flex;justify-content: space-between;align-items: center;padding: 10px var(--panel-padding);border-bottom: 1px solid var(--border-color);background-color: #f8f8f8;border-top-left-radius: var(--border-radius);border-top-right-radius: var(--border-radius);
}.header-title {display: flex;align-items: center;
}.header-icon {font-size: 1.6em;color: var(--error-color); /* Use red for attack theme */margin-right: 10px;
}.app-header h1 {font-size: 1.15em;font-weight: 600;
}.attack-summary {display: flex;align-items: center;gap: 20px;font-size: 0.9em;
}.attack-summary strong {font-weight: 600;
}#attack-status {color: var(--warning-color);
}/* Main Content Grid */
.app-content {display: grid;grid-template-columns: 1fr 1.5fr; /* Timeline+Systems | Evidence+Intel */grid-template-rows: auto 1fr; /* Top row auto height, bottom row takes remaining */grid-template-areas:"timeline evidence""systems intel";gap: var(--panel-padding);padding: var(--panel-padding);flex-grow: 1;overflow: hidden;
}/* Panels */
.panel {background-color: var(--panel-background-color);border: 1px solid var(--border-color);border-radius: var(--border-radius);display: flex;flex-direction: column;overflow: hidden;
}.panel-header {display: flex;justify-content: space-between;align-items: center;padding: 8px var(--panel-padding);border-bottom: 1px solid var(--border-color);background-color: #f8f8f8;height: var(--panel-header-height);flex-shrink: 0;
}.panel-header h2 {font-size: 0.95em;font-weight: 600;display: flex;align-items: center;gap: 8px;
}.panel-header h2 i {color: var(--text-color-secondary);
}.panel-content {padding: var(--panel-padding);flex-grow: 1;overflow: auto; /* Allow scrolling within panels */
}.scrollable {overflow-y: auto;
}/* Specific Panel Assignments */
.timeline-panel { grid-area: timeline; }
.evidence-panel { grid-area: evidence; }
.systems-panel { grid-area: systems; }
.intel-panel { grid-area: intel; }/* Timeline Panel */
.timeline-content {display: flex;align-items: center;justify-content: space-around; /* Distribute stages */padding: 20px var(--panel-padding);overflow-x: auto; /* Allow horizontal scroll if needed */
}.timeline-stage {display: flex;flex-direction: column;align-items: center;text-align: center;cursor: pointer;padding: 10px;border-radius: var(--border-radius);transition: background-color var(--animation-duration) ease, transform var(--animation-duration) ease;min-width: 80px; /* Ensure some width */
}.timeline-stage:hover {background-color: rgba(0, 122, 255, 0.05);transform: translateY(-3px);
}.timeline-stage.active {background-color: rgba(0, 122, 255, 0.1);box-shadow: 0 0 0 2px var(--timeline-active-color);
}.timeline-stage .stage-icon {font-size: 1.8em;margin-bottom: 8px;color: var(--timeline-inactive-color);transition: color var(--animation-duration) ease;
}.timeline-stage.active .stage-icon {color: var(--timeline-active-color);
}.timeline-stage .stage-name {font-size: 0.8em;font-weight: 500;color: var(--text-color-secondary);
}.timeline-stage.active .stage-name {color: var(--timeline-active-color);font-weight: 600;
}.timeline-connector {height: 2px;background-color: var(--border-color);flex-grow: 1;min-width: 20px; /* Ensure connector is visible */
}/* Evidence Panel */
.log-content {font-size: 0.9em;line-height: 1.6;padding: 10px;
}.evidence-entry {padding: 8px 12px;margin-bottom: 6px;border-radius: 6px;border-left: 4px solid var(--secondary-color);background-color: #f9f9f9;transition: border-color var(--animation-duration) ease, background-color var(--animation-duration) ease;cursor: default; /* Can make clickable later if needed */
}.evidence-entry:hover {background-color: #f0f0f0;
}/* Evidence type styling */
.evidence-entry[data-evidence-type="network"] { border-left-color: var(--info-color); background-color: var(--evidence-network-bg); }
.evidence-entry[data-evidence-type="host"] { border-left-color: var(--success-color); background-color: var(--evidence-host-bg); }
.evidence-entry[data-evidence-type="malware"] { border-left-color: var(--warning-color); background-color: var(--evidence-malware-bg); }
.evidence-entry[data-evidence-type="ics"] { border-left-color: var(--error-color); background-color: var(--evidence-ics-bg); }.evidence-timestamp {font-weight: 500;color: var(--text-color-secondary);margin-right: 10px;font-size: 0.9em;
}.evidence-source {font-weight: 600;color: var(--text-color);margin-right: 5px;
}.evidence-description {/* No special style needed currently */
}.header-filter {padding: 4px 8px;border: 1px solid var(--border-color);border-radius: 6px;font-size: 0.9em;background-color: #fff;
}/* Affected Systems Panel */
.systems-map {display: grid;grid-template-columns: repeat(auto-fit, minmax(120px, 1fr));gap: 20px;padding: 20px;background-color: #fafafa;position: relative; /* For potential connection lines */overflow: auto;
}.system-zone {border: 1px dashed var(--border-color);border-radius: var(--border-radius);padding: 15px;position: relative;background-color: rgba(255, 255, 255, 0.5);
}.zone-label {position: absolute;top: -10px;left: 10px;background-color: var(--panel-background-color);padding: 2px 6px;font-size: 0.8em;font-weight: 600;color: var(--text-color-secondary);border: 1px solid var(--border-color);border-radius: 4px;
}.system-device {display: flex;justify-content: center;align-items: center;text-align: center;padding: 15px 10px;border: 2px solid transparent;border-radius: var(--border-radius);background-color: #fff;box-shadow: 0 1px 3px rgba(0, 0, 0, 0.08);transition: border-color var(--animation-duration) ease, background-color var(--animation-duration) ease;margin-top: 20px; /* Space below label */
}.system-device div {display: flex;flex-direction: column;align-items: center;
}.system-device i {font-size: 1.8em;margin-bottom: 8px;color: var(--text-color-secondary);
}.system-device span {font-size: 0.8em;font-weight: 500;
}/* Specific device colors */
.system-device.email-gw i { color: #64d2ff; }
.system-device.ws-it i { color: #5856d6; }
.system-device.fw-it-dmz i, .system-device.fw-dmz-ot i { color: var(--error-color); }
.system-device.jump-server i, .system-device.hmi-server i { color: #ff9500; } /* Orange */
.system-device.eng-ws-ot i { color: var(--primary-color); }
.system-device.historian-ot i { color: #34c759; }
.system-device.rtu-a i, .system-device.rtu-b i { color: #a2845e; } /* Brownish */
.system-device.field-switch i { color: var(--secondary-color); }/* Highlight states */
.system-device.involved {border-color: var(--involved-color);background-color: rgba(255, 149, 0, 0.05);
}.system-device.affected {border-color: var(--affected-color);background-color: rgba(255, 59, 48, 0.05);animation: pulse-affected 1.5s infinite;
}@keyframes pulse-affected {0% { box-shadow: 0 0 0 0 rgba(255, 59, 48, 0.4); }70% { box-shadow: 0 0 0 6px rgba(255, 59, 48, 0); }100% { box-shadow: 0 0 0 0 rgba(255, 59, 48, 0); }
}/* Threat Intel Panel */
.intel-content {padding: 15px;
}.intel-section {margin-bottom: 20px;
}.intel-section h4 {font-size: 1em;font-weight: 600;margin-bottom: 8px;color: var(--text-color);border-bottom: 1px solid var(--border-color);padding-bottom: 4px;
}.intel-section p {font-size: 0.9em;color: var(--text-color-secondary);margin-bottom: 5px;
}.intel-section ul {list-style: none;padding-left: 0;font-size: 0.9em;
}.intel-section li {margin-bottom: 5px;padding-left: 15px;position: relative;
}.intel-section li::before {content: "\f105"; /* Font Awesome angle-right */font-family: "Font Awesome 6 Free";font-weight: 900;position: absolute;left: 0;color: var(--primary-color);
}.ttp-id {display: inline-block;background-color: #eef6ff;color: var(--primary-color);font-weight: 600;padding: 2px 5px;border-radius: 4px;font-size: 0.9em;margin-right: 5px;
}.ioc-list li {display: flex;align-items: baseline;gap: 5px;
}.ioc-type {font-weight: 600;color: var(--text-color-secondary);min-width: 60px;display: inline-block;
}
.ioc-type.file { color: var(--warning-color); }
.ioc-type.ip { color: var(--error-color); }
.ioc-type.domain { color: var(--info-color); }.ioc-value {font-family: monospace;background-color: #eee;padding: 1px 4px;border-radius: 3px;word-break: break-all;
}/* Placeholder */
.placeholder {text-align: center;color: var(--text-color-secondary);font-style: italic;padding: 20px;width: 100%;
}/* Responsive Adjustments */
@media (max-width: 1000px) {.app-content {grid-template-columns: 1fr; /* Stack all panels */grid-template-rows: auto auto auto auto; /* One row per panel */grid-template-areas:"timeline""evidence""systems""intel";overflow-y: auto;}.app-container {max-height: none;margin: 0;border-radius: 0;}.panel-content {min-height: 150px;}.timeline-content {flex-wrap: wrap; /* Allow wrapping on small screens */justify-content: flex-start;}.timeline-stage {margin-bottom: 10px;}.timeline-connector {display: none; /* Hide connectors when wrapping */}.systems-map {grid-template-columns: repeat(auto-fit, minmax(100px, 1fr));gap: 15px;}
}
script.js
document.addEventListener('DOMContentLoaded', () => {console.log('ICS Attack Forensics Component Initializing...');// --- Configuration & Constants ---const EVIDENCE_TYPES = {NETWORK: 'network',HOST: 'host',MALWARE: 'malware',ICS: 'ics',INTEL: 'intel' // Special type for context};// --- DOM Elements --- Caching elements for performanceconst timelineStages = document.querySelectorAll('.timeline-stage');const evidenceLogContainer = document.getElementById('evidence-log');const evidenceFilter = document.getElementById('evidence-filter');const systemDevices = document.querySelectorAll('.system-device');const intelContentContainer = document.getElementById('intel-content');const attackStatusElement = document.getElementById('attack-status');const attackDurationElement = document.getElementById('attack-duration');const evidenceCountElement = document.getElementById('evidence-count');// --- Application State ---let currentState = {activeStageId: null,attackData: null, // Will hold the loaded attack scenariofilteredEvidenceType: 'all',simulationTime: 0, // Could be used for dynamic simulation laterevidenceItems: []};// --- Simulation Data (Example APT Scenario Targeting Power Grid) ---const attackScenario = {id: "APT37_GRID_SCADA",name: "Operation Silent Energy (Simulated)",status: "溯源中",duration: "72 小时",stages: [{id: 'reconnaissance',name: '侦察探测',icon: 'fa-binoculars',description: '收集目标电网信息,识别脆弱点。'},{id: 'initial-compromise',name: '初始入侵',icon: 'fa-fish',description: '通过钓鱼邮件攻击IT网络员工。'},{id: 'establish-foothold',name: '建立据点',icon: 'fa-flag',description: '在IT网络部署恶意软件,建立持久访问。'},{id: 'escalate-privileges',name: '权限提升',icon: 'fa-user-secret',description: '获取更高权限,访问更多IT系统。'},{id: 'lateral-movement-it',name: 'IT横向移动',icon: 'fa-arrows-alt-h',description: '在IT网络内部移动,寻找通往OT网络的路径。'},{id: 'pivot-to-ot',name: '渗透OT网络',icon: 'fa-network-wired',description: '利用DMZ区的跳转服务器进入OT网络。'},{id: 'discover-ot',name: 'OT环境探测',icon: 'fa-search-location',description: '扫描OT网络,识别HMI、工程站和RTU。'},{id: 'impact',name: '实施攻击',icon: 'fa-bolt',description: '向RTU发送恶意指令,干扰电网运行。'}],evidence: [// Reconnaissance{ timestamp: "T-72h", type: EVIDENCE_TYPES.NETWORK, source: "外部流量日志", description: "检测到来自已知恶意IP [203.0.113.5] 对公司网站的扫描。", stageId: 'reconnaissance', deviceId: null },{ timestamp: "T-68h", type: EVIDENCE_TYPES.INTEL, source: "威胁情报平台", description: "报告称APT37组织近期活跃,目标为能源行业。", stageId: 'reconnaissance', deviceId: null },// Initial Compromise{ timestamp: "T-48h", type: EVIDENCE_TYPES.HOST, source: "邮件网关", description: "检测到钓鱼邮件,主题为 '紧急安全更新',发往IT部门员工。", stageId: 'initial-compromise', deviceId: 'email-gw' },{ timestamp: "T-47h", type: EVIDENCE_TYPES.HOST, source: "WS-IT-01", description: "用户 [j.doe] 点击了钓鱼邮件中的链接,下载了 'update.exe'。", stageId: 'initial-compromise', deviceId: 'ws-it' },{ timestamp: "T-46h", type: EVIDENCE_TYPES.MALWARE, source: "WS-IT-01", description: "发现恶意软件 'dropper.exe' (MD5: a1b2...) 正在运行,创建计划任务。", stageId: 'initial-compromise', deviceId: 'ws-it' },// Establish Foothold{ timestamp: "T-45h", type: EVIDENCE_TYPES.NETWORK, source: "FW-IT-DMZ", description: "检测到来自 [WS-IT-01] 到 C2 服务器 [198.51.100.10] 的异常出站连接 (端口 443)。", stageId: 'establish-foothold', deviceId: 'ws-it' },// Escalate Privileges{ timestamp: "T-30h", type: EVIDENCE_TYPES.HOST, source: "WS-IT-01", description: "检测到 Mimikatz 工具执行,尝试获取本地管理员凭证。", stageId: 'escalate-privileges', deviceId: 'ws-it' },{ timestamp: "T-29h", type: EVIDENCE_TYPES.HOST, source: "Domain Controller", description: "账户 [admin_it] 登录失败多次,随后成功登录来自 [WS-IT-01]。", stageId: 'escalate-privileges', deviceId: 'ws-it' },// Lateral Movement IT{ timestamp: "T-20h", type: EVIDENCE_TYPES.NETWORK, source: "内部网络日志", description: "检测到 [WS-IT-01] 使用 [admin_it] 凭证对 [Jump-Server] 进行 SMB 访问。", stageId: 'lateral-movement-it', deviceId: 'jump-server' },{ timestamp: "T-19h", type: EVIDENCE_TYPES.HOST, source: "Jump-Server", description: "检测到 C2 恶意软件变种 'beacon.dll' (MD5: c3d4...) 被部署并执行。", stageId: 'lateral-movement-it', deviceId: 'jump-server' },// Pivot to OT{ timestamp: "T-10h", type: EVIDENCE_TYPES.NETWORK, source: "FW-DMZ-OT", description: "检测到 [Jump-Server] 向 [HMI-Server] 发起 RDP 连接。", stageId: 'pivot-to-ot', deviceId: 'hmi-server' },{ timestamp: "T-9h", type: EVIDENCE_TYPES.HOST, source: "HMI-Server", description: "[admin_it] 账户通过 RDP 登录成功。", stageId: 'pivot-to-ot', deviceId: 'hmi-server' },// Discover OT{ timestamp: "T-8h", type: EVIDENCE_TYPES.NETWORK, source: "OT网络流量", description: "检测到 [HMI-Server] 对 OT 网段 (10.10.0.0/16) 进行 Modbus (TCP 502) 扫描。", stageId: 'discover-ot', deviceId: 'hmi-server' },{ timestamp: "T-7h", type: EVIDENCE_TYPES.HOST, source: "ENG-WS-OT", description: "发现从 [HMI-Server] 传输过来的工程项目文件 'config.zip'。", stageId: 'discover-ot', deviceId: 'eng-ws-ot' },{ timestamp: "T-6h", type: EVIDENCE_TYPES.HOST, source: "Historian-OT", description: "系统日志显示 [HMI-Server] 尝试访问历史数据库,多次失败后成功。", stageId: 'discover-ot', deviceId: 'historian-ot' },// Impact{ timestamp: "T-1h", type: EVIDENCE_TYPES.ICS, source: "HMI-Server", description: "操作员界面软件检测到异常配置更改命令被下发。", stageId: 'impact', deviceId: 'hmi-server' },{ timestamp: "T-0h", type: EVIDENCE_TYPES.NETWORK, source: "Field-Switch", description: "检测到来自 [HMI-Server] 向 [RTU-A] 和 [RTU-B] 发送的异常 Modbus 写指令。", stageId: 'impact', deviceId: ['rtu-a', 'rtu-b'] }, // Can affect multiple{ timestamp: "T+0.1h", type: EVIDENCE_TYPES.ICS, source: "RTU-A", description: "RTU-A 状态变为 '异常',物理断路器跳闸。", stageId: 'impact', deviceId: 'rtu-a' },{ timestamp: "T+0.2h", type: EVIDENCE_TYPES.HOST, source: "HMI-Server", description: "攻击者删除了 C2 恶意软件和相关日志。", stageId: 'impact', deviceId: 'hmi-server' },],threatIntel: {attribution: "APT37 (疑似)",motivation: "破坏关键基础设施,制造社会影响",ttps: [{ id: "T1566.001", name: "钓鱼邮件附件" },{ id: "T1059.003", name: "Windows命令解释器" },{ id: "T1547.001", name: "注册表运行键/启动文件夹" },{ id: "T1053.005", name: "计划任务" },{ id: "T1078", name: "有效账户" },{ id: "T1021.001", name: "远程桌面协议 (RDP)" },{ id: "T1110.001", name: "密码猜测" },{ id: "T1046", name: "网络扫描" },{ id: "T1005", name: "数据收集 (本地)" },{ id: "T1071.001", name: "Web协议 (C2)" },{ id: "T1133", name: "外部远程服务 (VPN/Jump Box)" },{ id: "T1105", name: "入口工具传输" },{ id: "T1070.004", name: "文件删除" },{ id: "T1485", name: "数据销毁" },{ id: "TA0040", name: "ICS Impact" }, // Specific to ICS],iocs: [{ type: "ip", value: "203.0.113.5", description: "扫描源" },{ type: "ip", value: "198.51.100.10", description: "C2 服务器" },{ type: "domain", value: "secure-update-service.com", description: "钓鱼链接指向域名" },{ type: "file", value: "dropper.exe", description: "初始恶意软件下载器 (MD5: a1b2...)" },{ type: "file", value: "beacon.dll", description: "C2 通信模块 (MD5: c3d4...)" },]}};// --- Functions ---/*** Renders the attack timeline stages.*/function renderTimeline() {const timelineContent = document.querySelector('.timeline-content');timelineContent.innerHTML = ''; // Clear existingconst stages = currentState.attackData.stages;for (let i = 0; i < stages.length; i++) {const stage = stages[i];const stageElement = document.createElement('div');stageElement.classList.add('timeline-stage');stageElement.dataset.stageId = stage.id;stageElement.innerHTML = `<i class="fas ${stage.icon} stage-icon"></i><span class="stage-name">${stage.name}</span>`;stageElement.title = stage.description; // TooltipstageElement.addEventListener('click', () => handleStageClick(stage.id));timelineContent.appendChild(stageElement);// Add connector if not the last stageif (i < stages.length - 1) {const connector = document.createElement('div');connector.classList.add('timeline-connector');timelineContent.appendChild(connector);}}}/*** Handles clicking on a timeline stage.* @param {string} stageId The ID of the clicked stage.*/function handleStageClick(stageId) {console.log(`Stage clicked: ${stageId}`);currentState.activeStageId = stageId;updateTimelineUI();filterAndRenderEvidence();updateSystemsMap();renderThreatIntel(); // Update intel based on stage context (optional)}/*** Updates the visual state of the timeline stages.*/function updateTimelineUI() {timelineStages.forEach(stage => {if (stage.dataset.stageId === currentState.activeStageId) {stage.classList.add('active');} else {stage.classList.remove('active');}});// Re-query timelineStages as they are dynamically generateddocument.querySelectorAll('.timeline-stage').forEach(stage => {if (stage.dataset.stageId === currentState.activeStageId) {stage.classList.add('active');} else {stage.classList.remove('active');}});}/*** Filters evidence based on the active stage and selected filter, then renders it.*/function filterAndRenderEvidence() {const stageId = currentState.activeStageId;const filterType = currentState.filteredEvidenceType;let filteredEvidence = [];if (stageId) {// Filter by stage firstfilteredEvidence = currentState.evidenceItems.filter(item => {// Check if the evidence belongs to the current stage or earlier stagesconst stageIndex = currentState.attackData.stages.findIndex(s => s.id === stageId);const evidenceStageIndex = currentState.attackData.stages.findIndex(s => s.id === item.stageId);return evidenceStageIndex <= stageIndex;});} else {// Show all evidence if no stage is selected (or a cumulative view)filteredEvidence = [...currentState.evidenceItems];}// Then filter by type (if not 'all')if (filterType !== 'all') {filteredEvidence = filteredEvidence.filter(item => item.type === filterType);}renderEvidenceLog(filteredEvidence);if (evidenceCountElement) {evidenceCountElement.textContent = filteredEvidence.length;} else {console.warn("Element with ID 'evidence-count' not found.");}}/*** Renders the evidence log entries.* @param {Array} evidenceItems The evidence items to render.*/function renderEvidenceLog(evidenceItems) {evidenceLogContainer.innerHTML = ''; // Clear existing logif (evidenceItems.length === 0) {evidenceLogContainer.innerHTML = '<p class="placeholder">当前阶段无匹配证据。</p>';return;}evidenceItems.sort((a, b) => {// Basic sort by timestamp - needs more robust parsing for real scenariosconst timeA = parseTimestamp(a.timestamp);const timeB = parseTimestamp(b.timestamp);return timeA - timeB;});evidenceItems.forEach(item => {const entry = document.createElement('div');entry.classList.add('evidence-entry');entry.dataset.evidenceType = item.type;entry.innerHTML = `<span class="evidence-timestamp">${item.timestamp}</span><span class="evidence-source">[${item.source}]</span><span class="evidence-description">${item.description}</span>`;evidenceLogContainer.appendChild(entry);});}// Helper to parse T-minus timestamps (simplistic)function parseTimestamp(ts) {if (ts.startsWith('T+')) {return parseFloat(ts.substring(2).replace('h', '')) * 1000; // Positive offset}if (ts.startsWith('T-')) {return parseFloat(ts.substring(2).replace('h', '')) * -1000; // Negative offset}return 0; // Default for T-0 or invalid}/*** Updates the highlighting on the affected systems map.*/function updateSystemsMap() {systemDevices.forEach(device => {device.classList.remove('involved', 'affected');});if (!currentState.activeStageId) return;const currentStageIndex = currentState.attackData.stages.findIndex(s => s.id === currentState.activeStageId);// Get all evidence up to and including the current stageconst relevantEvidence = currentState.evidenceItems.filter(item => {const evidenceStageIndex = currentState.attackData.stages.findIndex(s => s.id === item.stageId);return evidenceStageIndex <= currentStageIndex && item.deviceId;});const affectedDeviceIds = new Set();const involvedDeviceIds = new Set();relevantEvidence.forEach(item => {const deviceIds = Array.isArray(item.deviceId) ? item.deviceId : [item.deviceId];deviceIds.forEach(id => {// Mark as affected if it's the impact stage, otherwise involvedif (item.stageId === 'impact' && item.type === EVIDENCE_TYPES.ICS) {affectedDeviceIds.add(id);involvedDeviceIds.delete(id); // Ensure it's only marked as affected} else if (!affectedDeviceIds.has(id)){involvedDeviceIds.add(id);}// Also mark devices involved in pivoting/movementif (item.type === EVIDENCE_TYPES.NETWORK && item.description.includes(id)) {involvedDeviceIds.add(id);}if (item.type === EVIDENCE_TYPES.HOST && item.source.toLowerCase().includes(id)){involvedDeviceIds.add(id);}});});systemDevices.forEach(device => {const deviceId = device.dataset.deviceId;if (affectedDeviceIds.has(deviceId)) {device.classList.add('affected');} else if (involvedDeviceIds.has(deviceId)) {device.classList.add('involved');}});}/*** Renders the threat intelligence information.*/function renderThreatIntel() {const intel = currentState.attackData.threatIntel;if (!intel) {intelContentContainer.innerHTML = '<p class="placeholder">无可用威胁情报。</p>';return;}// Basic intel display - could be enhanced to show stage-specific TTPs/IOCsintelContentContainer.innerHTML = `<div class="intel-section"><h4><i class="fas fa-user-secret"></i> 归属分析</h4><p><strong>组织名称:</strong> ${intel.attribution}</p><p><strong>主要动机:</strong> ${intel.motivation}</p></div><div class="intel-section"><h4><i class="fas fa-tasks"></i> 战术、技术和过程 (TTPs)</h4><ul>${intel.ttps.map(ttp => `<li><span class="ttp-id">${ttp.id}</span> ${ttp.name}</li>`).join('')}</ul></div><div class="intel-section"><h4><i class="fas fa-shield-virus"></i> 危害指标 (IOCs)</h4><ul class="ioc-list">${intel.iocs.map(ioc => `<li><span class="ioc-type ${ioc.type}">${ioc.type.toUpperCase()}:</span> <span class="ioc-value">${ioc.value}</span> ${ioc.description ? '('+ioc.description+')' : ''}</li>`).join('')}</ul></div>`;}/*** Initializes the application.*/function initializeApp() {console.log('Initializing app with scenario data...');currentState.attackData = attackScenario;currentState.evidenceItems = attackScenario.evidence;// Populate header with null checksif (attackStatusElement) {attackStatusElement.textContent = currentState.attackData.status;} else {console.warn("Element with ID 'attack-status' not found.");}if (attackDurationElement) {attackDurationElement.textContent = currentState.attackData.duration;} else {console.warn("Element with ID 'attack-duration' not found.");}renderTimeline();// Set up event listenersif (evidenceFilter) {evidenceFilter.addEventListener('change', (e) => {currentState.filteredEvidenceType = e.target.value;filterAndRenderEvidence();});} else {console.warn("Element with ID 'evidence-filter' not found.");}// Initial render (select first stage by default?)if (currentState.attackData.stages.length > 0) {handleStageClick(currentState.attackData.stages[0].id); // Select first stage}else {filterAndRenderEvidence(); // Render all evidence initially if no stagesupdateSystemsMap();renderThreatIntel();}console.log('ICS Attack Forensics Component Ready.');}// --- Start Application ---initializeApp();
});
