Linux iptables:四表五链 + 实用配置
目录
一、安装iptables
语法: iptables -t 表名 链名 动作 匹配条件 -j 目标动作
二、iptables 四表五链
1. 四表五链关系
2. 语法组件详解表格
3. 常用选项详解
(1) 命令
(2) 匹配条件
(3) 目标动作
三、查看防火墙规则
四、综合实例
1. 实例一
在 filter 表的 INPUT 链末尾添加一条规则,拒绝来自 192.168.159.0/24 网段的 TCP 流量访问本机的 80 端口
2. 实例二
ICMP-Ping响应测试
3. 实例三
设置多地址多端口,地址范围与端口范围
4. 实例四
SNAT地址转换
5. 实例五
防火墙规则永久生效
一、安装iptables
[root@iptables ~]# yum -y install iptables-services[root@iptables ~]# systemctl stop firewalld
[root@iptables ~]# systemctl start iptables.service
[root@iptables ~]# systemctl status iptables.service
● iptables.service - IPv4 firewall with iptablesLoaded: loaded (/usr/lib/systemd/system/iptables.service; disabled; preset: disabled)Active: active (exited) since Wed 2025-10-22 10:57:55 CST; 7s agoProcess: 1601 ExecStart=/usr/libexec/iptables/iptables.init start (code=exited, status=0/SUCCESS)Main PID: 1601 (code=exited, status=0/SUCCESS)CPU: 20msOct 22 10:57:55 iptables systemd[1]: Starting IPv4 firewall with iptables...
Oct 22 10:57:55 iptables iptables.init[1601]: iptables: Applying firewall rules: [ OK ]
Oct 22 10:57:55 iptables systemd[1]: Finished IPv4 firewall with iptables.语法: iptables -t 表名 链名 动作 匹配条件 -j 目标动作
二、iptables 四表五链
1. 四表五链关系
| 表 (Table) | 链 (Chain) | 主要功能 | 数据包流向说明 |
|---|---|---|---|
| raw | PREROUTING OUTPUT | 数据包追踪 (连接跟踪处理前,决定是否跳过跟踪) | 路由之前 的数据包 本机 发出 的数据包 |
| mangle | PREROUTING INPUT FORWARD OUTPUT POSTROUTING | 数据包标记 (修改TOS、TTL等包头信息) | 路由之前 的数据包 进入 本机 的数据包 经过 本机转发 的数据包 本机 发出 的数据包 路由之后 的数据包 |
| nat (网络地址转换) | PREROUTING INPUT OUTPUT POSTROUTING | 网络地址转换 (DNAT, SNAT, MASQUERADE) | 路由之前 做目的地址转换(DNAT) 进入 本机 的数据包(较少使用) 本机 发出 的数据包(对输出包做DNAT) 路由之后 做源地址转换(SNAT) |
| filter (默认表) | INPUT FORWARD OUTPUT | 数据包过滤 (允许或拒绝数据包) | 过滤进入 本机 的数据包 过滤经过 本机转发 的数据包 过滤本机 发出 的数据包 |
2. 语法组件详解表格
| 组件 | 含义 | 是否必选 | 常见示例与说明 |
|---|---|---|---|
-t <表名> | 指定规则所在的表 | 否,默认为 filter | -t filter, -t nat, -t mangle, -t raw |
<命令> | 对规则的操作 | 是 | -A (追加), -I (插入), -D (删除), -F (清空) |
<链名> | 规则所属的链 | 是 | INPUT, OUTPUT, FORWARD, PREROUTING, POSTROUTING |
<匹配条件> | 匹配数据包的条件 | 否(但通常都有) | -p tcp --dport 80, -s 192.168.1.0/24 |
-j <目标动作> | 匹配后的处理动作 | 是 | ACCEPT, DROP, REJECT, LOG |
3. 常用选项详解
(1) 命令
| 命令 | 全称 | 作用 |
|---|---|---|
-A | --append | 在链的末尾追加一条新规则。 |
-I | --insert | 在链的开头(或指定位置)插入一条新规则。例如 -I INPUT 3 插入为第3条规则。 |
-D | --delete | 从链中删除一条规则。可以按规则内容或编号删除。 |
-F | --flush | 清空指定链中的所有规则。 |
-L | --list | 列出指定链中的所有规则。 |
| -R | --replace | 替换指定链中的某一条规则。 |
-P | --policy | 设置链的默认策略,如 iptables -P INPUT DROP。 |
| -N | --new-chain | 自定义链。 iptables -N INK |
| -E | --rename-chain | 更名自定义链。 iptables -E INK RE |
| -X | --delete-chain | 删除自定义链。iptables -X INK |
| -j | --jump | 指定规则匹配后的动作(如 ACCEPT、DROP)或跳转到自定义链。 |
| -C | --check | 检查规则是否存在于指定链中。 |
(2) 匹配条件
| 条件 | 作用 | 示例 |
|---|---|---|
-p | 指定协议 | -p tcp, -p udp, -p icmp |
-s | 指定源地址 | -s 192.168.1.100, -s 10.0.0.0/8 |
-d | 指定目标地址 | -d 203.0.113.1 |
--sport | 指定源端口 | --sport 1000:2000 (范围) |
--dport | 指定目标端口 | --dport 80, --dport 22:25 (范围) |
-i | 指定数据包进入的网络接口 | -i eth0 (常用于 INPUT, FORWARD, PREROUTING 链) |
-o | 指定数据包出去的网络接口 | -o eth1 (常用于 OUTPUT, FORWARD, POSTROUTING 链) |
-m | 启用扩展模块,提供更强大的匹配能力 | -m state --state RELATED,ESTABLISHED |
(3) 目标动作
| 动作 | 作用 |
|---|---|
ACCEPT | 接受数据包,允许其通过。 |
DROP | 丢弃数据包,不给出任何响应。 |
REJECT | 拒绝数据包,并向发送方返回一个拒绝错误的响应(如 port-unreachable)。 |
LOG | 将匹配的数据包信息记录到系统日志中,然后继续处理下一条规则。 |
SNAT | 源地址转换,在 nat 表的 POSTROUTING 链中使用。 |
DNAT | 目的地址转换,在 nat 表的 PREROUTING 链中使用。 |
MASQUERADE | 一种特殊的 SNAT,适用于动态获取IP(如拨号上网)的场景。 |
三、查看防火墙规则
防火墙规则读取顺序:默认从上到下的顺序执行,已经被规则匹配到的数据包不会接着匹配
iptables 查看规则参数说明
| 参数 | 全称/简写 | 含义与作用 |
|---|---|---|
-n | --numeric | 不做解析,直接以数字形式显示 IP 地址和端口号,加快显示速度。 |
-L | --list | 列出指定链中的所有规则。 |
--line-numbers | --line | 在规则前面显示其规则编号,便于后续通过编号删除或修改特定规则。 |
-v | --verbose | 显示详细信息,包括数据包和字节计数器的值(可以查看通过该规则的流量)。 |
-S | --list-rules --source | 以 iptables-save 命令的输出格式显示规则,这种格式更紧凑,且显示了默认策略。 |
-t | --table | 指定要操作的表名。默认为 filter 表。其他常用表有 nat, mangle, raw。 |
[root@iptables ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT icmp -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
REJECT all -- anywhere anywhere reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- anywhere anywhere reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT)
target prot opt source destination [root@iptables ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT)
target prot opt source destination [root@iptables ~]# iptables -nL --line
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
2 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
3 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
4 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
5 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)
num target prot opt source destination
1 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT)
num target prot opt source destination [root@iptables ~]# iptables -t filter -nL --line
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
2 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
3 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
4 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
5 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain FORWARD (policy ACCEPT)
num target prot opt source destination
1 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibitedChain OUTPUT (policy ACCEPT)
num target prot opt source destination 四、综合实例
1. 实例一
在 filter 表的 INPUT 链末尾添加一条规则,拒绝来自 192.168.159.0/24 网段的 TCP 流量访问本机的 80 端口
# 客户端ip网段:192.168.159.0/24
[root@client ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host lovalid_lft forever preferred_lft foreverinet6 ::1/128 scope host valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000link/ether 00:0c:29:9c:03:3a brd ff:ff:ff:ff:ff:ffaltname enp2s1inet 192.168.159.230/24 brd 192.168.159.255 scope global dynamic noprefixroute ens33valid_lft 1447sec preferred_lft 1447secinet6 fe80::20c:29ff:fe9c:33a/64 scope link noprefixroute valid_lft forever preferred_lft forever# 目前还能访问
[root@client ~]# curl 192.168.159.129
iptables test# 添加规则
[root@iptables ~]# iptables -A INPUT -p tcp -s 192.168.159.0/24 --dport 80 -j REJECT
[root@iptables ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 192.168.159.0/24 0.0.0.0/0 tcp dpt:80 reject-with icmp-port-unreachableChain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination # 再次curl失败
[root@client ~]# curl 192.168.159.129
curl: (7) Failed to connect to 192.168.159.129 port 80: Connection refused2. 实例二
ICMP-Ping响应测试
# 允许接收外部的ping请求
[root@iptables ~]# iptables -A INPUT -p icmp --icmp-type 8 -j ACCEPT
# 查看规则,确认已允许icmp类型8
[root@iptables ~]# iptables -nL --line
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 8Chain FORWARD (policy ACCEPT)
num target prot opt source destination Chain OUTPUT (policy ACCEPT)
num target prot opt source destination # 测试ping服务器:成功收到回复
[root@client ~]# ping -c3 192.168.159.129
PING 192.168.159.129 (192.168.159.129) 56(84) bytes of data.
64 bytes from 192.168.159.129: icmp_seq=1 ttl=64 time=0.367 ms
64 bytes from 192.168.159.129: icmp_seq=2 ttl=64 time=0.500 ms
64 bytes from 192.168.159.129: icmp_seq=3 ttl=64 time=0.659 ms--- 192.168.159.129 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2053ms
rtt min/avg/max/mdev = 0.367/0.508/0.659/0.119 ms# 将规则改为拒绝ping请求(会返回错误信息)
[root@iptables ~]# iptables -R INPUT 1 -p icmp --icmp-type 8 -j REJECT
# 查看规则,确认动作已改为REJECT
[root@iptables ~]# iptables -nL --line
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 REJECT icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 8 reject-with icmp-port-unreachableChain FORWARD (policy ACCEPT)
num target prot opt source destination Chain OUTPUT (policy ACCEPT)
num target prot opt source destination # 测试ping服务器:收到明确的拒绝消息(Destination Port Unreachable)
[root@client ~]# ping -c3 192.168.159.129
PING 192.168.159.129 (192.168.159.129) 56(84) bytes of data.
From 192.168.159.129 icmp_seq=1 Destination Port Unreachable
From 192.168.159.129 icmp_seq=2 Destination Port Unreachable
From 192.168.159.129 icmp_seq=3 Destination Port Unreachable--- 192.168.159.129 ping statistics ---
3 packets transmitted, 0 received, +3 errors, 100% packet loss, time 2063ms# 将规则改为丢弃ping请求(完全不回应)
[root@iptables ~]# iptables -R INPUT 1 -p icmp --icmp-type 8 -j DROP
# 查看规则,确认动作已改为DROP
[root@iptables ~]# iptables -nL --line
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 8Chain FORWARD (policy ACCEPT)
num target prot opt source destination Chain OUTPUT (policy ACCEPT)
num target prot opt source destination # 测试ping服务器:请求超时,无任何响应
[root@client ~]# ping -c3 192.168.159.129
PING 192.168.159.129 (192.168.159.129) 56(84) bytes of data.
^C
--- 192.168.159.129 ping statistics ---
3 packets transmitted, 0 received, 100% packet loss, time 2051ms常见且重要的 ICMP 类型:
| 类型名称 | 类型编号 | 说明 | 常用场景 |
|---|---|---|---|
echo-reply | 0 | 回显应答 | ping 命令收到的回复 |
echo-request | 8 | 回显请求 | ping 命令发出的请求 |
destination-unreachable | 3 | 目标不可达 | 网络或端口无法访问时的错误信息 |
time-exceeded | 11 | 超时 | traceroute 命令的工作原理 |
# 只允许我Ping你,不允许你ping我
# 本机:192.168.159.129 客户端:192.168.159.230# 方法一
[root@iptables ~]# iptables -A INPUT -p icmp --icmp-type echo-request -s 192.168.159.230 -j REJECT [root@iptables ~]# ping -c2 192.168.159.230
PING 192.168.159.230 (192.168.159.230) 56(84) bytes of data.
64 bytes from 192.168.159.230: icmp_seq=1 ttl=64 time=0.471 ms
64 bytes from 192.168.159.230: icmp_seq=2 ttl=64 time=0.580 ms--- 192.168.159.230 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1046ms
rtt min/avg/max/mdev = 0.471/0.525/0.580/0.054 ms[root@client ~]# ping -c2 192.168.159.129
PING 192.168.159.129 (192.168.159.129) 56(84) bytes of data.
From 192.168.159.129 icmp_seq=1 Destination Port Unreachable
From 192.168.159.129 icmp_seq=2 Destination Port Unreachable--- 192.168.159.129 ping statistics ---
2 packets transmitted, 0 received, +2 errors, 100% packet loss, time 1007ms# 方法二
[root@iptables ~]# iptables -F
[root@iptables ~]# iptables -A OUTPUT -p icmp --icmp-type echo-reply -d 192.168.159.230 -j REJECT[root@iptables ~]# ping -c3 192.168.159.230
PING 192.168.159.230 (192.168.159.230) 56(84) bytes of data.
64 bytes from 192.168.159.230: icmp_seq=1 ttl=64 time=0.628 ms
64 bytes from 192.168.159.230: icmp_seq=2 ttl=64 time=0.641 ms
64 bytes from 192.168.159.230: icmp_seq=3 ttl=64 time=0.480 ms--- 192.168.159.230 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2074ms
rtt min/avg/max/mdev = 0.480/0.583/0.641/0.073 ms[root@client ~]# ping -c3 192.168.159.129
PING 192.168.159.129 (192.168.159.129) 56(84) bytes of data.--- 192.168.159.129 ping statistics ---
3 packets transmitted, 0 received, 100% packet loss, time 2077ms
3. 实例三
设置多地址多端口,地址范围与端口范围
# 多地址
[root@iptables ~]# iptables -t filter -A INPUT -p tcp -s 192.168.159.8,10.55.21.11,123.25.24.14 --dport 22 -j REJECT
[root@iptables ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 192.168.159.8 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
REJECT tcp -- 10.55.21.11 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
REJECT tcp -- 123.25.24.14 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachableChain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination# 地址范围 -m iprange
[root@iptables ~]# iptables -t filter -A INPUT -p udp --dport 22 -m iprange --src-range 192.168.122.99-192.168.122.199 -j DROP
[root@iptables ~]# iptables -nL --line
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 REJECT tcp -- 192.168.159.8 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
2 REJECT tcp -- 10.55.21.11 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
3 REJECT tcp -- 123.25.24.14 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
4 DROP udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:22 source IP range 192.168.122.99-192.168.122.199Chain FORWARD (policy ACCEPT)
num target prot opt source destination Chain OUTPUT (policy ACCEPT)
num target prot opt source destination # 多端口 -m multiport
[root@iptables ~]# iptables -t filter -A INPUT -p tcp -m multiport --dports 8080,9090,6379,10050,10051 -j ACCEPT
[root@iptables ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
REJECT tcp -- 192.168.159.8 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
REJECT tcp -- 10.55.21.11 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
REJECT tcp -- 123.25.24.14 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
DROP udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:22 source IP range 192.168.122.99-192.168.122.199
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 8080,9090,6379,10050,10051Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination#端口范围 例:22:80
[root@iptables ~]# iptables -t filter -I INPUT -p tcp --dport 1001:1999 -j REJECT
[root@iptables ~]# iptables -nL --line-numbers
Chain INPUT (policy ACCEPT)
num target prot opt source destination
1 REJECT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpts:1001:1999 reject-with icmp-port-unreachable
2 REJECT tcp -- 192.168.159.8 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
3 REJECT tcp -- 10.55.21.11 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
4 REJECT tcp -- 123.25.24.14 0.0.0.0/0 tcp dpt:22 reject-with icmp-port-unreachable
5 DROP udp -- 0.0.0.0/0 0.0.0.0/0 udp dpt:22 source IP range 192.168.122.99-192.168.122.199
6 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 multiport dports 8080,9090,6379,10050,10051Chain FORWARD (policy ACCEPT)
num target prot opt source destination Chain OUTPUT (policy ACCEPT)
num target prot opt source destination 4. 实例四
SNAT地址转换
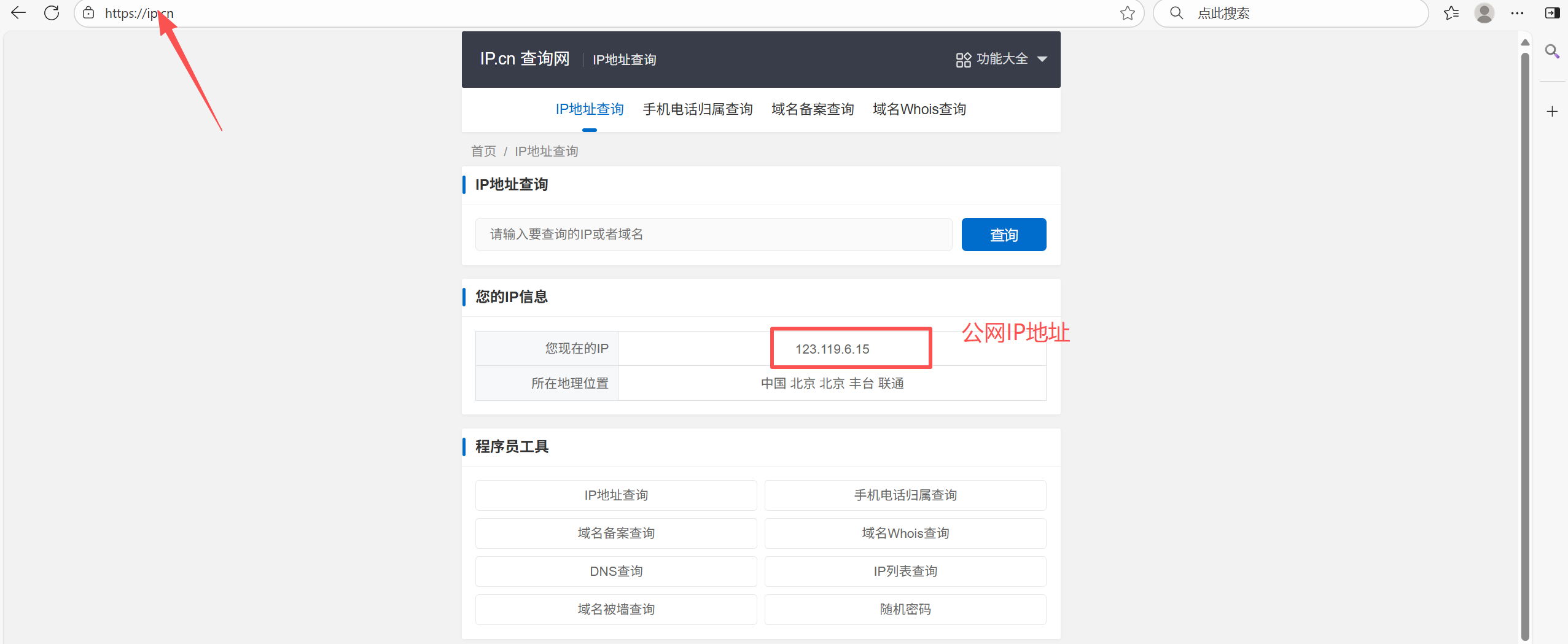
规则 1: SNAT(源地址转换) - 用于内部主机访问互联网 POSTROUTING
[root@iptables ~]# iptables -t nat -F
[root@iptables ~]# iptables -t nat -A POSTROUTING -o ens33 -p tcp --dport 80 -s 192.168.159.129 -j SNAT --to-source 123.119.6.15
[root@iptables ~]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination Chain INPUT (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT tcp -- 192.168.159.129 0.0.0.0/0 tcp dpt:80 to:123.119.6.15规则 2: DNAT(目标地址转换) - 用于从外部访问内部服务 PREROUTING
[root@iptables ~]# iptables -t nat -A PREROUTING -i ens33 -p tcp --dport 22 -j DNAT --to-destination 192.168.159.129:22
[root@iptables ~]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 to:192.168.159.129:22Chain INPUT (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT tcp -- 192.168.159.129 0.0.0.0/0 tcp dpt:80 to:123.119.6.15
5. 实例五
防火墙规则永久生效
# 创建一些测试规则
[root@iptables ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@iptables ~]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination Chain INPUT (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
[root@iptables ~]# iptables -A INPUT -p tcp --dport 8080 -j ACCEPT
[root@iptables ~]# iptables -A INPUT -p icmp --icmp-type echo-request -j DROP
[root@iptables ~]# iptables -t nat -A POSTROUTING -s 192.168.159.0/24 -j MASQUERADE# 查看创建的规则
[root@iptables ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:8080
DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 8Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@iptables ~]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination Chain INPUT (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
MASQUERADE all -- 192.168.159.0/24 0.0.0.0/0# 保存规则到文件
[root@iptables ~]# iptables-save > /etc/sysconfig/iptables.test# 检查保存的文件
[root@iptables ~]# cat /etc/sysconfig/iptables.test
# Generated by iptables-save v1.8.10 (nf_tables) on Thu Oct 23 15:53:08 2025
*filter
:INPUT ACCEPT [54:3456]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -p tcp -m tcp --dport 8080 -j ACCEPT
-A INPUT -p icmp -m icmp --icmp-type 8 -j DROP
COMMIT
# Completed on Thu Oct 23 15:53:08 2025
# Generated by iptables-save v1.8.10 (nf_tables) on Thu Oct 23 15:53:08 2025
*nat
:PREROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
:POSTROUTING ACCEPT [0:0]
-A POSTROUTING -s 192.168.159.0/24 -j MASQUERADE
COMMIT
# Completed on Thu Oct 23 15:53:08 2025# 清空所有规则,模拟系统重启后的状态
[root@iptables ~]# iptables -F
[root@iptables ~]# iptables -t nat -F
[root@iptables ~]# iptables -t mangle -F# 清空后的规则状态
[root@iptables ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@iptables ~]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination Chain INPUT (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination Chain POSTROUTING (policy ACCEPT)
target prot opt source destination # 从保存的文件恢复规则
[root@iptables ~]# iptables-restore < /etc/sysconfig/iptables.test# 查看恢复后的规则
[root@iptables ~]# iptables -nL
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:8080
DROP icmp -- 0.0.0.0/0 0.0.0.0/0 icmptype 8Chain FORWARD (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[root@iptables ~]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination Chain INPUT (policy ACCEPT)
target prot opt source destination Chain OUTPUT (policy ACCEPT)
target prot opt source destination Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
MASQUERADE all -- 192.168.159.0/24 0.0.0.0/0
