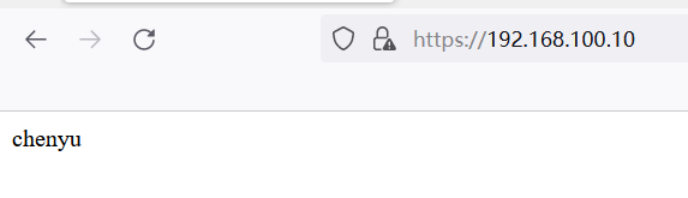
Nginx 访问控制、用户认证与 HTTPS 配置指南
Nginx 访问控制、用户认证与 HTTPS 配置指南
一、Nginx 访问控制
1.1 基本语法
用于 location 段中控制客户端访问权限:
- allow:允许指定的 IP 或网段访问,多个参数用空格隔开。
- deny:禁止指定的 IP 或网段访问,多个参数用空格隔开。
示例:
allow 192.168.100.20 192.168.100.30;
deny all;
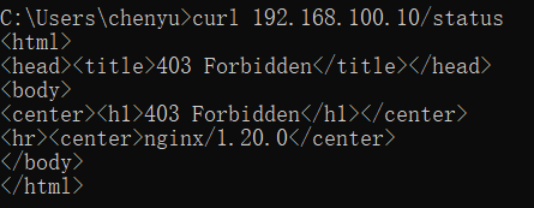
1.2 拒绝指定主机访问nginx状态页面
location /status {echo "chenyu";deny 192.168.100.111;
}
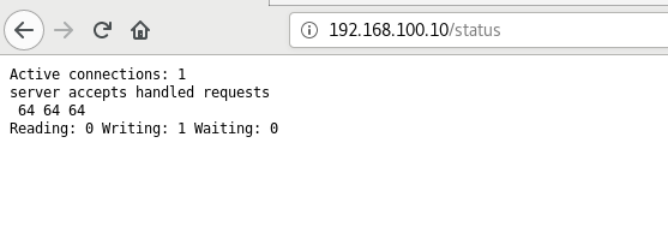
1.3 启用 stub_status 模块查看nginx状态信息
location /status {echo "chenyu";stub_status on;
}
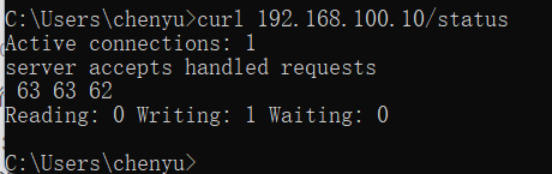
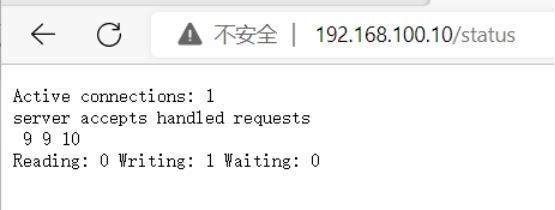
状态信息说明:
Active connections:当前nginx正在处理的活动连接数Server accepts handled requests:nginx总共处理了63个连接,成功创建63次握手,总共处理了62个请求Reading:nginx读取到客户端的Header信息数Writing:nginx返回给客户端的Header信息数Waiting:开启keep-alive的情况下,这个值等于active-(reading+writing),意思就是nginx已经处理完成,正在等候下一次请求指令的驻留连接。所以,在访问效率高、请求很快就被处理完毕的情况下,waiting数比较多是正常的。如果reading+writing数较多,则说明并发访问量非常大,正在处理过程中
1.4 allow 与 deny 同时存在时的优先级
location /status {stub_status on;allow 192.168.100.111;deny all;
}
1.5 常见访问控制策略
只允许指定 IP 访问,禁止其他所有 IP:
allow 192.168.100.11;
allow 192.168.100.12;
deny all;
只禁止指定 IP 访问,允许其他所有 IP:
deny 192.168.100.11;
deny 192.168.100.12;
allow all;
二、用户认证
2.1 基本配置语法
auth_basic "欢迎信息";
auth_basic_user_file "/path/to/user_auth_file";
2.2 user_auth_file用户认证文件格式
每行为一个用户,格式为:
username:加密密码
2.3 使用 htpasswd 创建认证文件
htpasswd -c -m /path/to/.user_auth_file USERNAME
授权用户
安装 httpd-tools:
yum -y install httpd-tools
创建用户密钥文件:
cd /usr/local/nginx/conf/
htpasswd -c -m .user_auth_file chenyucat .user_auth_file
chenyu:$apr1$whXqcpS.$EORacQbsq0P6JblZ0ayM5/
2.4 配置 Nginx 启用认证(注意auth_basic_user_file必须用绝对路径)
location /status {stub_status on;auth_basic "welcome to hyedu";auth_basic_user_file "/usr/local/nginx/conf/.user_auth_file";
}
2.5 测试并重载配置
nginx -t
nginx -s reload
三、HTTPS 配置
3.1 环境说明
- Nginx 服务器:192.168.100.10
- CA 服务器:192.168.100.30
3.2 在 CA 服务器上生成一对密钥,根证书
mkdir -p /etc/pki/CA/private
cd /etc/pki/CA/
(umask 077; openssl genrsa -out private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus (2 primes)
.+++++
....................+++++
e is 65537 (0x010001)openssl rsa -in private/cakey.pem -pubout
writing RSA key
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvaWtkdtUn3T+pXIvD1Rf
LUGP8NdmlVqwamSU7fxqRA5BiWi7gKsNpnSBHlXGJ3PeFBRbNfff/IOpZLnMWDB4
OKDp63pB4OcB3GKWNoJsDYEg5m4HYdhHjJRywTkfmuUNoIok8fBg6gsYYHov9EVK
tmV9FTZBRIPSq7hiVm8dYPDFsuAhvi5CUxGO/VEXRsiJvePSQ1IAaMYUv/mDDMKC
GXX/qvyWPRMA6KdFmr6hO32jbY3fzllzfQpN3tjNrXbQPRa1o6GFQ9nQC8kHzo5L
qtRdeJ0ZMqQyU76f6kJQwcBPS2t/ByTGxq8DRAiVATNK2xO3LuNvfCv+CYRYuVwV
bwIDAQAB
-----END PUBLIC KEY-----openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 1024
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:luoqi
Organizational Unit Name (eg, section) []:linux
Common Name (eg, your name or your server's hostname) []:chenyu
Email Address []:cy@example.com
3.3 在 Nginx 服务器上生成证书请求,发送给CA
cd /usr/local/nginx/conf/
(umask 077; openssl genrsa -out httpd.key 2048)
Generating RSA private key, 2048 bit long modulus (2 primes)
................................................................................+++++
............................................................................................................+++++
e is 65537 (0x010001)openssl req -new -key httpd.key -days 1024 -out httpd.csr
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:luoqi
Organizational Unit Name (eg, section) []:linux
Common Name (eg, your name or your server's hostname) []:chenyu
Email Address []:cy@example.comscp httpd.csr root@192.168.100.30:/root/
3.4 CA签署证书并发送给NGINX,在 CA 服务器上签署证书
mkdir /etc/pki/CA/newcerts
touch /etc/pki/CA/index.txt
echo "01" > /etc/pki/CA/serial
openssl ca -in httpd.csr -out httpd.crt -days 1024
# 将CA签署的证书httpd.crt和服务器的证书cacert.pem发送给nginx
scp httpd.crt root@192.168.100.10:/usr/local/nginx/conf/
scp /etc/pki/CA/cacert.pem root@192.168.100.10:/usr/local/nginx/conf/
3.5 配置 Nginx 启用 HTTPS /usr/local/nginx/conf/nginx.conf
server {listen 443 ssl;server_name localhost;ssl_certificate httpd.crt;ssl_certificate_key httpd.key;ssl_session_cache shared:SSL:1m;ssl_session_timeout 5m;ssl_ciphers HIGH:!aNULL:!MD5;ssl_prefer_server_ciphers on;location / {root html;index index.html index.htm;}
}
3.6 nginx -t 测试配置文件
nginx -t
nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successfulcd /usr/local/nginx/html/
echo "chenyu" > /usr/local/nginx/html/index.html
nginx -s reload