kubeadm搭建生产环境的单master多node的k8s集群
k8s环境规划:
podSubnet(pod 网段) 10.20.0.0/16
serviceSubnet(service 网段): 10.10.0.0/16
实验环境规划:
操作系统:centos7.9
配置: 4G 内存/4核CPU/40G 硬盘
网络:NAT
| K8s集群角色 | ip | 主机名 | 安装的组件 |
|---|---|---|---|
| 控制节点(master) | 192.168.121.101 | master1 | apiserver、controller-manager、scheduler、etcd、 docker、keepalived、nginx |
| 工作节点(node) | 192.168.121.102 | node1 | kubelet、kube-proxy、docker、calico、coredns |
| 工作节点(node) | 192.168.121.103 | node2 | kubelet、kube-proxy、docker、calico、coredns |
kubeadm 与二进制安装 k8s 的核心区别在于「自动化程度」和「定制化自由度」:
-
kubeadm:简单高效,自动化处理证书、组件配置等复杂步骤,适合测试 / 开发环境、中小型生产环境(100 节点内),以及运维资源有限的团队,主打低门槛、易维护。
-
二进制安装:全程手动操作,可深度定制组件参数、证书策略等,适合大型 / 核心生产环境(100+ 节点)、有严格合规 / 性能需求的场景,以及需要深入学习 k8s 原理的情况,主打高可控性。
1 初始化
可以按照接下来的步骤新建一台master1手动执行把共同需要初始化的内容完成再进行克隆剩下的三台虚拟机,也可以直接使用shell脚本进行一键初始化,首先在master1上面用脚本进行初始化,完成之后克隆三台虚拟机,依次开机进行修改静态ip以及主机名。因为全都是基于master1来进行完整复制的虚拟机,存在静态ip以及主机名重复,其它初始化保持一致。
cd
vim init.sh#!/bin/bash
# 服务器初始化配置脚本(增强版)
# 功能:配置主机名、hosts文件、生成SSH密钥对、关闭防火墙、关闭SELinux、关闭swap、
# 配置内核参数、配置华为镜像源、安装软件、配置时间同步、开启ipvs等# 检查是否以root权限运行
if [ "$(id -u)" -ne 0 ]; thenecho "错误:此脚本需要root权限运行。请使用sudo或切换到root用户。" >&2exit 1
fi# 配置主机名
configure_hostname() {echo "=== 配置主机名 ==="current_hostname=$(hostname)echo "当前主机名: $current_hostname"read -p "请输入新的主机名 (直接回车保持当前主机名): " new_hostnameif [ -n "$new_hostname" ] && [ "$new_hostname" != "$current_hostname" ]; then# 临时设置主机名hostname "$new_hostname"# 永久设置主机名if [ -f "/etc/hostname" ]; thenecho "$new_hostname" > /etc/hostnamefi# 更新/etc/hosts中的旧主机名sed -i "s/$current_hostname/$new_hostname/g" /etc/hostsecho "主机名已更新为: $new_hostname"elseecho "保持当前主机名不变: $current_hostname"fiecho "------------------------"echo
}# 配置hosts文件
configure_hosts() {echo "=== 配置hosts文件 ==="echo "当前hosts文件内容:"cat /etc/hosts | grep -v '^#' | grep -v '^$'echoread -p "是否需要添加新的主机映射? (y/n): " add_hostsif [[ $add_hosts =~ ^[Yy]$ ]]; thenecho "请输入主机映射 (格式: IP地址 主机名,一行一个,空行结束)"echo "示例: 192.168.1.100 master-node"# 读取用户输入的主机映射while IFS= read -r line; do# 空行退出if [ -z "$line" ]; thenbreakfi# 简单验证输入格式if [[ $line =~ ^[0-9]+\.[0-9]+\.[0-9]+\.[0-9]+\ +[a-zA-Z0-9-]+$ ]]; then# 检查是否已存在该映射if ! grep -q "$line" /etc/hosts; thenecho "$line" >> /etc/hostsecho "已添加: $line"elseecho "已存在: $line,跳过"fielseecho "无效格式: $line,已跳过"fidoneecho "hosts文件更新完成"elseecho "不修改hosts文件"fiecho "------------------------"echo
}# 生成SSH密钥对
generate_ssh_key() {echo "=== 生成SSH密钥对 ==="default_key_path="$HOME/.ssh/id_rsa"read -p "请输入SSH密钥保存路径 (默认: $default_key_path): " key_pathkey_path=${key_path:-$default_key_path}# 检查密钥是否已存在if [ -f "$key_path" ]; thenread -p "密钥 $key_path 已存在,是否覆盖? (y/n): " overwriteif [[ ! $overwrite =~ ^[Yy]$ ]]; thenecho "不生成新的SSH密钥对"echo "------------------------"echoreturnfifi# 创建.ssh目录(如果不存在)mkdir -p "$(dirname "$key_path")"chmod 700 "$(dirname "$key_path")"# 生成密钥对echo "正在生成SSH密钥对..."ssh-keygen -t rsa -f "$key_path" -N "" -qchmod 600 "$key_path"chmod 644 "$key_path.pub"echo "SSH密钥对已生成:"echo "私钥: $key_path"echo "公钥: $key_path.pub"echo "------------------------"echo
}# 关闭firewalld防火墙
disable_firewalld() {echo "=== 关闭firewalld防火墙 ==="# 检查firewalld是否安装if command -v firewalld &> /dev/null; then# 停止firewalld服务systemctl stop firewalld# 禁用firewalld服务(开机不启动)systemctl disable firewalld# 检查状态if systemctl is-active --quiet firewalld; thenecho "警告: firewalld关闭失败"elseecho "firewalld已成功关闭并禁用"fielseecho "firewalld未安装,无需操作"fiecho "------------------------"echo
}# 关闭SELinux
disable_selinux() {echo "=== 关闭SELinux ==="# 检查SELinux状态current_mode=$(getenforce)if [ "$current_mode" = "Disabled" ]; thenecho "SELinux已处于关闭状态"echo "------------------------"echoreturnfi# 临时关闭SELinuxsetenforce 0# 永久关闭SELinux(修改配置文件)sed -i 's/^SELINUX=enforcing/SELINUX=disabled/' /etc/selinux/configsed -i 's/^SELINUX=permissive/SELINUX=disabled/' /etc/selinux/config# 验证修改if grep -q '^SELINUX=disabled' /etc/selinux/config && [ "$(getenforce)" = "Permissive" ]; thenecho "SELinux已临时关闭,永久关闭需重启系统生效"elseecho "警告: SELinux配置修改可能失败"fiecho "------------------------"echo
}# 关闭交换分区swap
disable_swap() {echo "=== 关闭交换分区swap ==="# 临时关闭swapswapoff -a# 永久关闭swap(从fstab中移除swap条目)sed -i '/swap/s/^/#/' /etc/fstab# 验证if free | grep -q 'Swap:.*0.*0.*0'; thenecho "swap已临时关闭,永久关闭需重启系统生效"elseecho "警告: swap关闭可能失败"fiecho "------------------------"echo
}# 配置内核参数
configure_kernel_parameters() {echo "=== 配置内核参数 ==="# 加载br_netfilter模块echo "加载br_netfilter模块..."modprobe br_netfilter# 验证模块是否加载成功if lsmod | grep -q br_netfilter; thenecho "br_netfilter模块加载成功"elseecho "警告: br_netfilter模块加载失败"fi# 创建或修改内核参数配置文件echo "配置内核参数..."cat > /etc/sysctl.d/k8s.conf <<EOF
net.bridge.bridge-nf-call-ip6tables = 1
net.bridge.bridge-nf-call-iptables = 1
net.ipv4.ip_forward = 1
EOF# 使内核参数生效sysctl -p /etc/sysctl.d/k8s.confecho "内核参数配置完成"echo "------------------------"echo
}# 配置华为镜像源
configure_huawei_repo() {echo "=== 配置华为镜像源 ==="# 备份原有repo源echo "备份原有repo源..."mkdir -p /root/repo.bakif [ -d "/etc/yum.repos.d/" ]; thenmv /etc/yum.repos.d/* /root/repo.bak/ 2>/dev/nullecho "原有repo源已备份至/root/repo.bak"elseecho "/etc/yum.repos.d/目录不存在,跳过备份"fi# 下载华为CentOS 7镜像源echo "下载华为镜像源..."if command -v wget &> /dev/null; thenwget -O /etc/yum.repos.d/CentOS-Base.repo https://mirrors.huaweicloud.com/repository/conf/CentOS-7-anon.repoelif command -v curl &> /dev/null; thencurl -o /etc/yum.repos.d/CentOS-Base.repo https://mirrors.huaweicloud.com/repository/conf/CentOS-7-anon.repoelseecho "错误: 未找到wget或curl,无法下载镜像源配置文件"echo "------------------------"echoreturnfi# 清理并重建缓存echo "清理并重建yum缓存..."yum clean allyum makecacheecho "华为镜像源配置完成"echo "------------------------"echo
}# 安装常用工具和配置时间同步
install_utils_and_time_sync() {echo "=== 安装常用工具和配置时间同步 ==="# 安装rzszecho "安装rzsz..."yum install lrzsz -y# 安装openssh-clients (包含scp)echo "安装openssh-clients (包含scp)..."yum install openssh-clients -y# 配置时间同步echo "配置时间同步..."# 安装ntpdateyum install ntpdate -y# 与网络时间服务器同步echo "同步时间..."ntpdate cn.pool.ntp.org# 设置计划任务echo "设置时间同步计划任务..."# 检查是否已有相同的定时任务if ! crontab -l | grep -q "/usr/sbin/ntpdate cn.pool.ntp.org"; then# 添加定时任务(crontab -l 2>/dev/null; echo "* */1 * * * /usr/sbin/ntpdate cn.pool.ntp.org") | crontab -echo "已添加每小时同步一次时间的计划任务"elseecho "时间同步计划任务已存在,无需重复添加"fi# 重启crond服务echo "重启crond服务..."if command -v systemctl &> /dev/null; thensystemctl restart crondelseservice crond restartfiecho "常用工具安装和时间同步配置完成"echo "------------------------"echo
}# 开启ipvs
enable_ipvs() {echo "=== 开启ipvs ==="# 检查ipvs.modules文件是否存在,不存在则创建if [ ! -f "/etc/sysconfig/modules/ipvs.modules" ]; thenecho "创建ipvs.modules配置文件..."mkdir -p /etc/sysconfig/modules/cat > /etc/sysconfig/modules/ipvs.modules <<EOF
#!/bin/bash
modprobe -- ip_vs
modprobe -- ip_vs_rr
modprobe -- ip_vs_wrr
modprobe -- ip_vs_sh
modprobe -- nf_conntrack_ipv4
EOFfi# 配置权限并加载模块echo "加载ipvs模块..."chmod 755 /etc/sysconfig/modules/ipvs.modulesbash /etc/sysconfig/modules/ipvs.modules# 验证echo "验证ipvs模块加载情况..."if lsmod | grep -q ip_vs; thenecho "ipvs模块加载成功"lsmod | grep ip_vselseecho "警告: ipvs模块加载失败"fiecho "ipvs配置完成"echo "------------------------"echo
}# 安装基础软件包
install_base_packages() {echo "=== 安装基础软件包 ==="echo "开始安装基础软件包(这可能需要一些时间)..."yum install -y yum-utils device-mapper-persistent-data lvm2 wget net-tools nfs-utils \lrzsz gcc gcc-c++ make cmake libxml2-devel openssl-devel curl curl-devel unzip sudo ntp \libaio-devel wget vim ncurses-devel autoconf automake zlib-devel python-devel epel-release \openssh-server socat ipvsadm conntrack ntpdate telnet rsyncecho "基础软件包安装完成"echo "------------------------"echo
}# 配置etcd工作目录
configure_etcd_dirs() {echo "=== 配置etcd工作目录 ==="# 创建etcd工作目录echo "创建etcd工作目录..."mkdir -p /etc/etcdmkdir -p /etc/etcd/ssl# 设置权限chmod 755 /etc/etcdchmod 700 /etc/etcd/ssl # SSL目录权限更严格echo "etcd工作目录配置完成"echo "------------------------"echo
}# 主程序
main() {echo "===== 服务器初始化配置开始 ====="echoconfigure_hostnameconfigure_hostsgenerate_ssh_keydisable_firewallddisable_selinuxdisable_swapconfigure_kernel_parametersconfigure_huawei_repoinstall_utils_and_time_syncenable_ipvsinstall_base_packagesconfigure_etcd_dirsecho "===== 服务器初始化配置完成 ====="echo "注意:"echo "1. SELinux和swap的永久关闭需要重启系统才能完全生效"echo "2. 建议重启系统以确保所有配置生效: reboot"
}# 执行主程序
main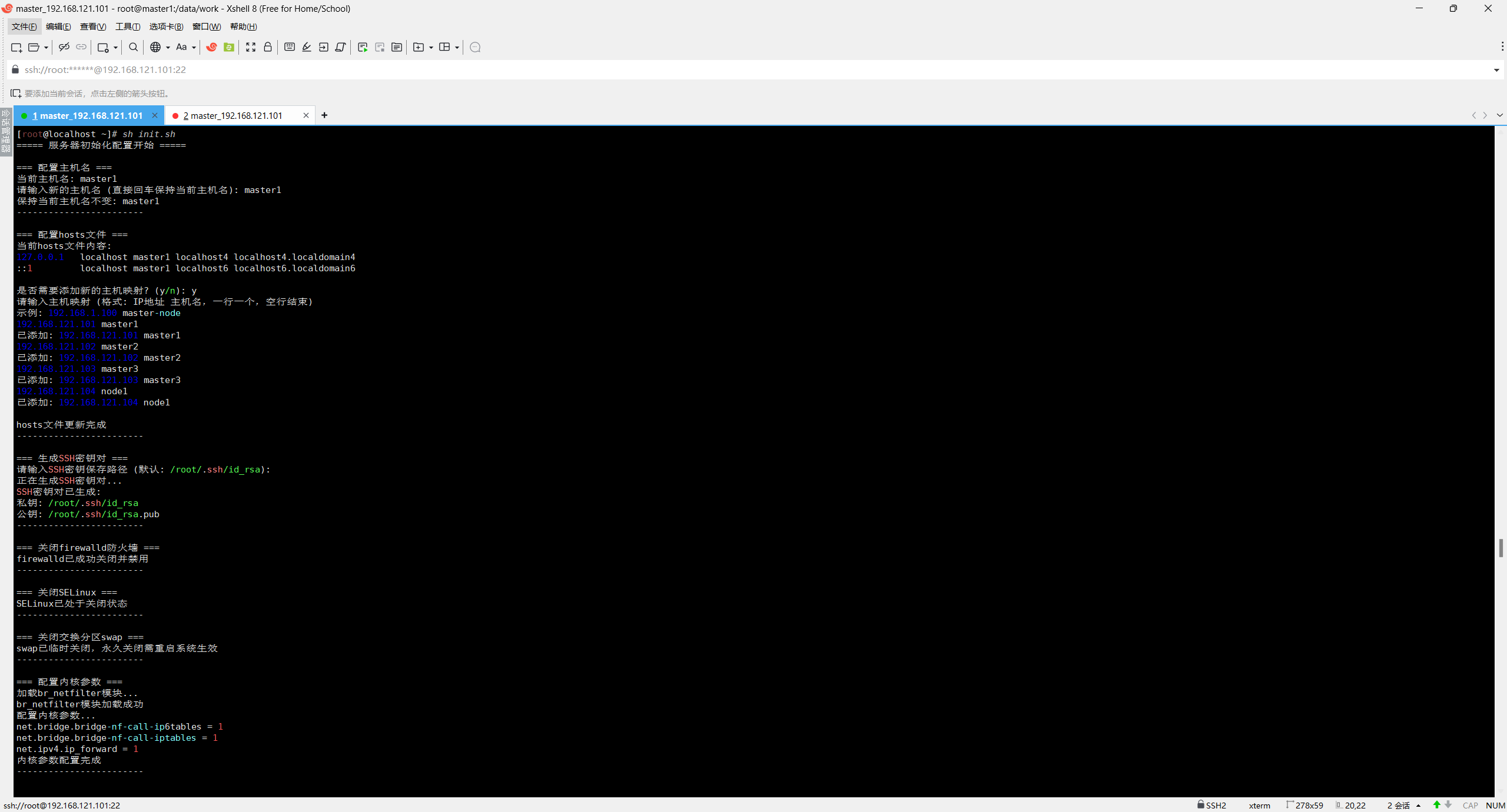
1.1 配置静态 IP
#修改/etc/sysconfig/network-scripts/ifcfg-ens33 文件部分可能是ens32,变成如下:
BOOTPROTO=static # static表示静态IP地址
NAME=ens32 # 网卡名字和DEVICE保持一致
DEVICE=ens32 # 网卡设备名,使用ip a 可以看到自己的这个网卡设备名,每个人的机器可能都不一样,需要填写自己实际名字
ONBOOT=yes # 开启自启动
IPADDR=192.168.121.101 # ip地址,需要跟VMware虚拟网络编辑器内设置的网段一致
NETMASK=255.255.255.0 # 子网掩码
GATEWAY=192.168.121.2 # 网关,需要跟VMware虚拟网络编辑器内设置的网关一致
DNS1=223.5.5.5 # DNS首选
DNS2=8.8.8.8 # DNS备选
1.2 配置主机名
# 命令格式hostnamectl set-hostname 主机名 四台服务器均需要手动改名
hostnamectl set-hostname master11.3 配置 hosts 文件
# 在/etc/hosts文件添加内容,格式为 192.168.121.101 master1
# 需要将集群每台虚拟机的ip和主机名添加进去
[root@master1~]# vim /etc/hosts192.168.121.101 master1
192.168.121.102 master2
192.168.121.103 master3
192.168.121.104 node11.4 配置主机之间无密码登录,每台机器都按照如下操作
# 生成密钥对每台服务器执行
[root@master1~]# ssh-keygen -t rsa -b 4096
[root@master2~]# ssh-keygen -t rsa -b 4096
[root@master3~]# ssh-keygen -t rsa -b 4096
[root@node1~]# ssh-keygen -t rsa -b 4096# 每台服务器执行
ssh-copy-id master1
ssh-copy-id master2
ssh-copy-id master3
ssh-copy-id node11.5 关闭 firewalld 防火墙,在每台机器执行以下操作:
# 关闭防火墙
systemctl stop firewalld
# 禁止开机自启动
systemctl enable firewalld1.6 关闭 selinux 防火墙,在每台机器执行以下操作:
sed -i 's/SELINUX=enforcing/SELINUX=disabled/g' /etc/selinux/config#修改 selinux 配置文件之后,重启机器,selinux 配置才能永久生效
重启之后登录机器验证是否修改成功:
getenforce
#显示 Disabled 说明 selinux 已经关闭1.7 关闭交换分区 swap,在每台机器执行以下操作:
#永久关闭:注释 swap 挂载,给 swap 这行开头加一下注释
vim /etc/fstab
#/dev/mapper/centos-swap swap swap defaults 0 0#如果是克隆的虚拟机,需要删除 UUID1.8 修改内核参数,在每台机器执行以下操作:
#加载 br_netfilter 模块
modprobe br_netfilter
#验证模块是否加载成功:
lsmod |grep br_netfilter
#修改内核参数
cat > /etc/sysctl.d/k8s.conf <<EOF
net.bridge.bridge-nf-call-ip6tables = 1
net.bridge.bridge-nf-call-iptables = 1
net.ipv4.ip_forward = 1
EOF
#使刚才修改的内核参数生效
sysctl -p /etc/sysctl.d/k8s.conf1.9 配置华为 repo 源,在每台机器执行以下操作:
1、备份配置文件:cp -a /etc/yum.repos.d/CentOS-Base.repo /etc/yum.repos.d/CentOS-Base.repo.bak2、配置下列方案。方案:下载新的CentOS-Base.repo文件到/etc/yum.repos.d/目录下,选择 CentOS 版本:
CentOS 7执行如下命令:wget -O /etc/yum.repos.d/CentOS-Base.repo https://mirrors.huaweicloud.com/repository/conf/CentOS-7-anon.repo3、执行yum clean all清除原有 yum 缓存4、执行yum makecache(刷新缓存)或者yum repolist all(查看所有配置可以使用的文件,会自动刷新缓存)。# 安装 rzsz
yum install lrzsz -y# 安装 scp
yum install openssh-clients1.10 配置时间同步,在每台机器执行以下操作:
#安装 ntpdate 命令,
#yum install ntpdate -y
#跟网络源做同步
ntpdate cn.pool.ntp.org
#把时间同步做成计划任务
crontab -e
* */1 * * * /usr/sbin/ntpdate cn.pool.ntp.org
#重启 crond 服务
service crond restart1.11 开启 ipvs,在每台机器执行以下操作:
#不开启 ipvs 将会使用 iptables 进行数据包转发,但是效率低,所以官网推荐需要开通 ipvs。
#把 ipvs.modules 上传到 master1 机器的/etc/sysconfig/modules/目录下
chmod 755 /etc/sysconfig/modules/ipvs.modules && bash /etc/sysconfig/modules/ipvs.modules && lsmod | grep ip_vsip_vs_ftp 13079 0
nf_nat 26583 1 ip_vs_ftp
ip_vs_sed 12519 0
ip_vs_nq 12516 0
ip_vs_sh 12688 0
ip_vs_dh 12688 01.12 安装基础软件包,在每台机器执行以下操作:
yum install -y yum-utils device-mapper-persistent-data lvm2 wget net-tools nfs-utils
lrzsz gcc gcc-c++ make cmake libxml2-devel openssl-devel curl curl-devel unzip sudo ntp
libaio-devel wget vim ncurses-devel autoconf automake zlib-devel python-devel epel-release
openssh-server socat ipvsadm conntrack ntpdate telnet rsync1.13 安装 docker,在每台机器执行以下操作:
参考Docker 入门到实践:从理论到案例的全攻略_docker入门与实战-CSDN博客
3 安装初始化 k8s 需要的软件包
[root@master1 ~]# yum install -y kubelet-1.20.6 kubeadm-1.20.6 kubectl-1.20.6
[root@master1 ~]# systemctl enable kubelet
[root@master1 ~]# systemctl status kubelet[root@node1 ~]# yum install -y kubelet-1.20.6 kubeadm-1.20.6 kubectl-1.20.6
[root@node1 ~]# systemctl enable kubelet
[root@node1 ~]# systemctl status kubelet[root@node2 ~]# yum install -y kubelet-1.20.6 kubeadm-1.20.6 kubectl-1.20.6
[root@node2 ~]# systemctl enable kubelet
[root@node2 ~]# systemctl status kubelet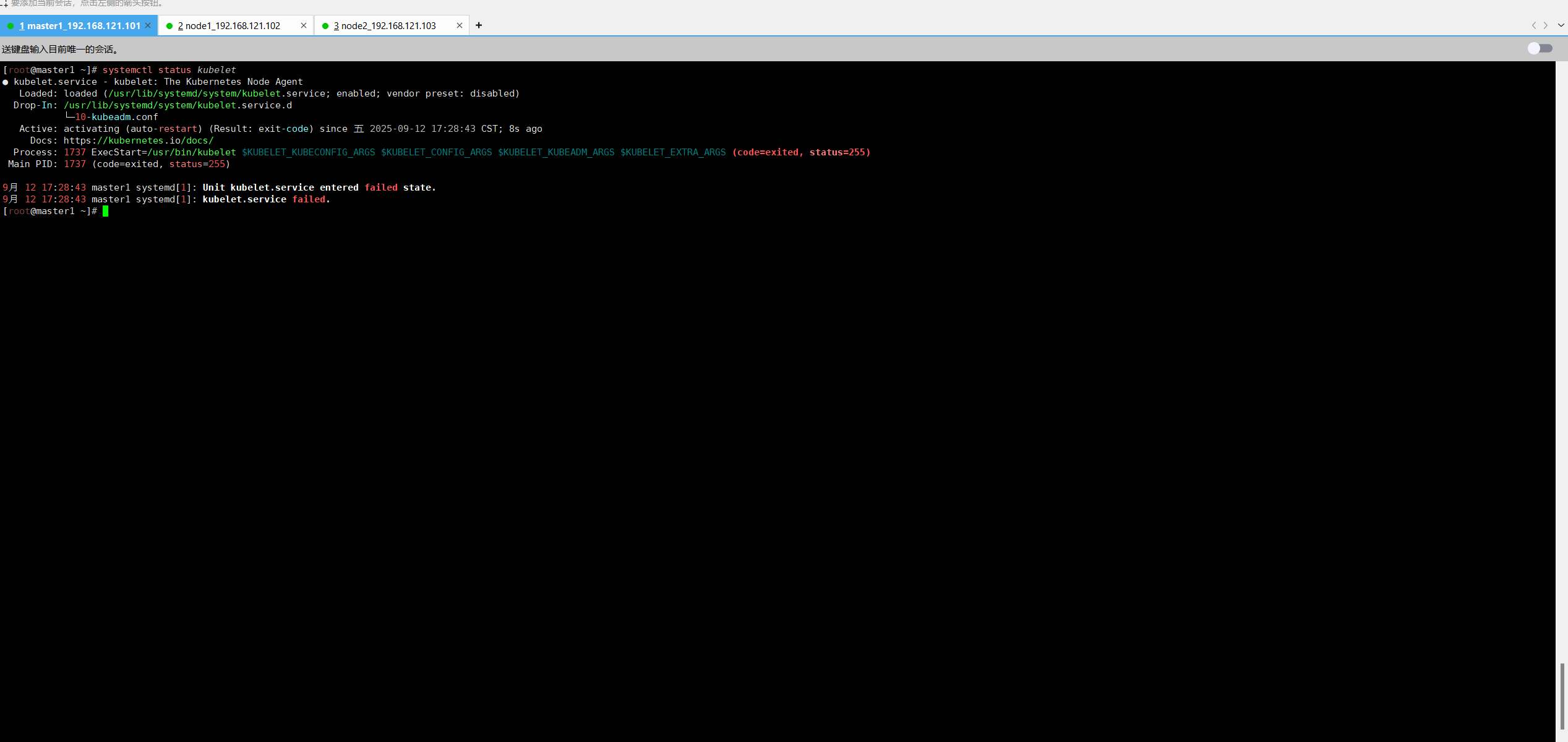
上面可以看到 kubelet 状态不是 running 状态,这个是正常的,不用管,等 k8s 组件起来这个
kubelet 就正常了。
Kubeadm: kubeadm 是一个工具,用来初始化 k8s 集群的
kubelet: 安装在集群所有节点上,用于启动 Pod 的
kubectl: 通过 kubectl 可以部署和管理应用,查看各种资源,创建、删除和更新各种组件
4 kubeadm 初始化 k8s 集群
把初始化 k8s 集群需要的离线镜像包上传到 master1、node1、node2 机器上,手动解压:
[root@master1 ~]# docker load -i k8simage-1-20-6.tar.gz
[root@node1 ~]# docker load -i k8simage-1-20-6.tar.gz
[root@node2 ~]# docker load -i k8simage-1-20-6.tar.gz# 使用kubeadm初始化k8s集群
[root@master1 ~]# kubeadm init --kubernetes-version=1.20.6 --apiserver-advertise-address=192.168.121.101 --image-repository registry.aliyuncs.com/google_containers --pod-network-cidr=10.20.0.0/16 --ignore-preflight-errors=SystemVerification显示以下内容说明初始化完成。
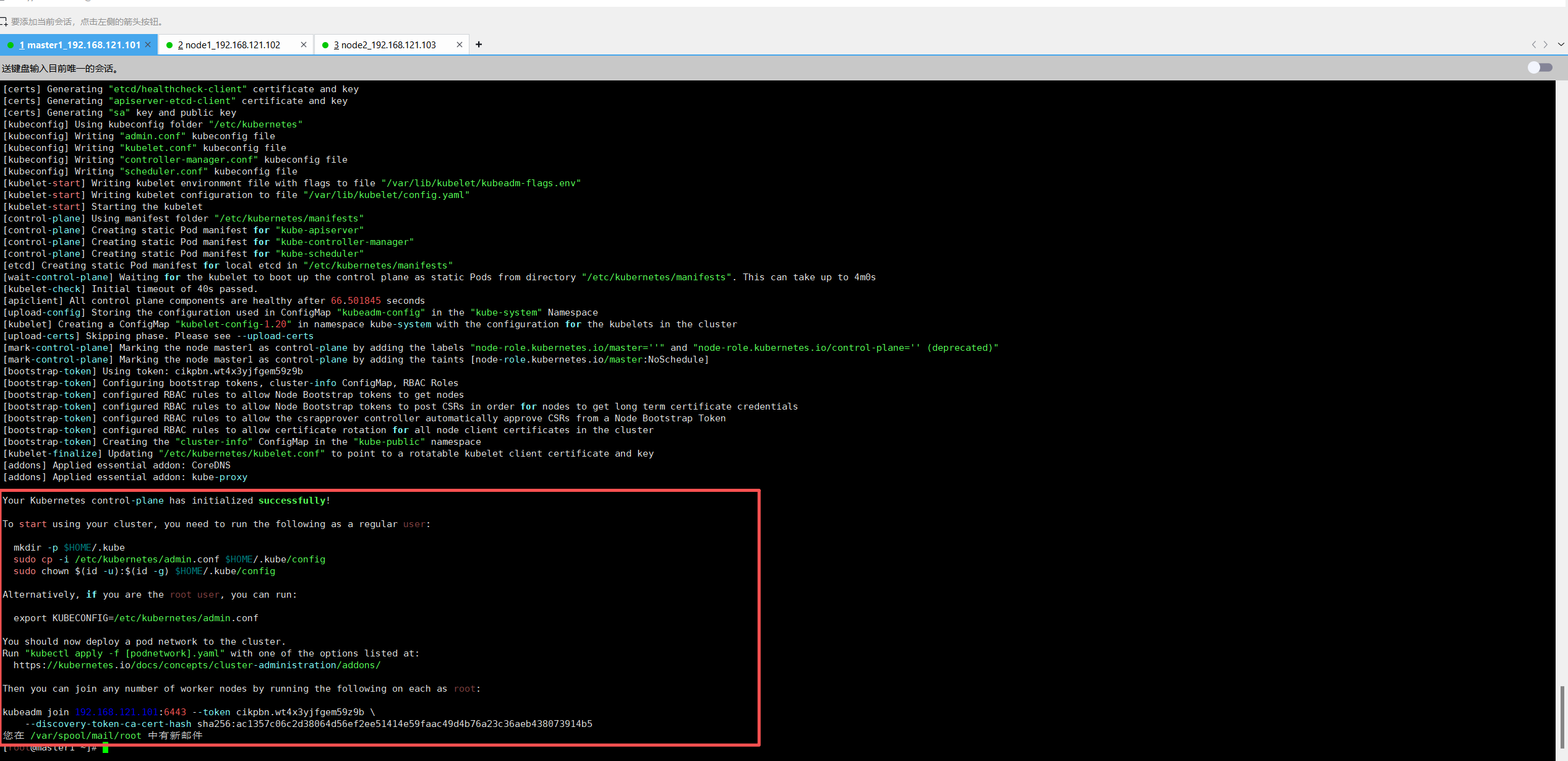
kubeadm join 192.168.121.101:6443 --token cikpbn.wt4x3yjfgem59z9b \
--discovery-token-ca-cert-hash sha256:ac1357c06c2d38064d56ef2ee51414e59faac49d4b76a23c36aeb438073914b5
上面命令是把node节点加入集群,需要保存下来,每个人都不一样
#配置 kubectl 的配置文件 config,相当于对 kubectl 进行授权,这样 kubectl 命令可以使用这个证
书对 k8s 集群进行管理
[root@master1 ~]# mkdir -p $HOME/.kube
[root@master1 ~]# sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
[root@master1 ~]# sudo chown $(id -u):$(id -g) $HOME/.kube/config
[root@master1 ~]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
master1 NotReady control-plane,master 2m6s v1.20.6
# 这时候集群状态还是NotReady状态,因为还没有安装网络插件5 扩容 k8s 集群-添加第一个工作节点
在master1上查看加入节点的命令:
[root@master1 ~]# kubeadm token create --print-join-command
kubeadm join 192.168.121.101:6443 --token 2mj9az.ulq26zooycqcwtrz --discovery-token-ca-cert-hash sha256:ac1357c06c2d38064d56ef2ee51414e59faac49d4b76a23c36aeb438073914b5 # 把node1加入集群
root@node1 ~]# kubeadm join 192.168.121.101:6443 --token 2mj9az.ulq26zooycqcwtrz --discovery-token-ca-cert-hash sha256:ac1357c06c2d38064d56ef2ee51414e59faac49d4b76a23c36aeb438073914b5 [preflight] Running pre-flight checks[WARNING IsDockerSystemdCheck]: detected "cgroupfs" as the Docker cgroup driver. The recommended driver is "systemd". Please follow the guide at https://kubernetes.io/docs/setup/cri/[WARNING SystemVerification]: this Docker version is not on the list of validated versions: 26.1.4. Latest validated version: 19.03
[preflight] Reading configuration from the cluster...
[preflight] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -o yaml'
[kubelet-start] Writing kubelet configuration to file "/var/lib/kubelet/config.yaml"
[kubelet-start] Writing kubelet environment file with flags to file "/var/lib/kubelet/kubeadm-flags.env"
[kubelet-start] Starting the kubelet
[kubelet-start] Waiting for the kubelet to perform the TLS Bootstrap...This node has joined the cluster:
* Certificate signing request was sent to apiserver and a response was received.
* The Kubelet was informed of the new secure connection details.Run 'kubectl get nodes' on the control-plane to see this node join the cluster.
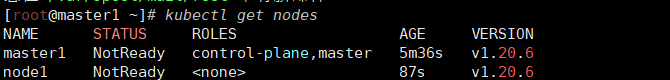
kubectl get nodes 查看一下集群状态,可以看到node1已经加入集群,充当工作节点。
6 扩容 k8s 集群-添加第二个工作节点
[root@master1 ~]# kubeadm token create --print-join-command
kubeadm join 192.168.121.101:6443 --token 09k06n.44qrjdgxu7gmmfs3 --discovery-token-ca-cert-hash sha256:ac1357c06c2d38064d56ef2ee51414e59faac49d4b76a23c36aeb438073914b5# 把node2加入集群
[root@node2 ~]# kubeadm join 192.168.121.101:6443 --token 09k06n.44qrjdgxu7gmmfs3 --discovery-token-ca-cert-hash sha256:ac1357c06c2d38064d56ef2ee51414e59faac49d4b76a23c36aeb438073914b5
[preflight] Running pre-flight checks[WARNING IsDockerSystemdCheck]: detected "cgroupfs" as the Docker cgroup driver. The recommended driver is "systemd". Please follow the guide at https://kubernetes.io/docs/setup/cri/[WARNING SystemVerification]: this Docker version is not on the list of validated versions: 26.1.4. Latest validated version: 19.03
[preflight] Reading configuration from the cluster...
[preflight] FYI: You can look at this config file with 'kubectl -n kube-system get cm kubeadm-config -o yaml'
[kubelet-start] Writing kubelet configuration to file "/var/lib/kubelet/config.yaml"
[kubelet-start] Writing kubelet environment file with flags to file "/var/lib/kubelet/kubeadm-flags.env"
[kubelet-start] Starting the kubelet
[kubelet-start] Waiting for the kubelet to perform the TLS Bootstrap...This node has joined the cluster:
* Certificate signing request was sent to apiserver and a response was received.
* The Kubelet was informed of the new secure connection details.Run 'kubectl get nodes' on the control-plane to see this node join the cluster.
可以看到node2已经加入集群了,充当工作节点,但是roles角色都是空,表示节点是工作节点,记下来把roles变成work。
[root@master1 ~]# kubectl label node node1 node-role.kubernetes.io/work=work
node/node1 labeled
您在 /var/spool/mail/root 中有新邮件
[root@master1 ~]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
master1 NotReady control-plane,master 15m v1.20.6
node1 NotReady work 11m v1.20.6
node2 NotReady <none> 7m53s v1.20.6
[root@master1 ~]# kubectl label node node2 node-role.kubernetes.io/work=work
node/node2 labeled
[root@master1 ~]# kubectl get nodes
NAME STATUS ROLES AGE VERSION
master1 NotReady control-plane,master 16m v1.20.6
node1 NotReady work 11m v1.20.6
node2 NotReady work 7m59s v1.20.6
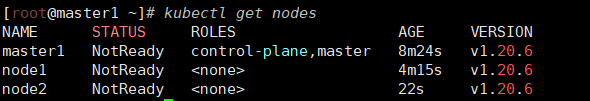
状态都是NotReady说明没有安装网络插件
7 安装 kubernetes 网络组件-Calico
[root@master1 ~]# vim calico.yaml
---
# Source: calico/templates/calico-config.yaml
# This ConfigMap is used to configure a self-hosted Calico installation.
kind: ConfigMap
apiVersion: v1
metadata:name: calico-confignamespace: kube-system
data:# Typha is disabled.typha_service_name: "none"# Configure the backend to use.calico_backend: "bird"# Configure the MTU to use for workload interfaces and tunnels.# By default, MTU is auto-detected, and explicitly setting this field should not be required.# You can override auto-detection by providing a non-zero value.veth_mtu: "0"# The CNI network configuration to install on each node. The special# values in this config will be automatically populated.cni_network_config: |-{"name": "k8s-pod-network","cniVersion": "0.3.1","plugins": [{"type": "calico","log_level": "info","log_file_path": "/var/log/calico/cni/cni.log","datastore_type": "kubernetes","nodename": "__KUBERNETES_NODE_NAME__","mtu": __CNI_MTU__,"ipam": {"type": "calico-ipam"},"policy": {"type": "k8s"},"kubernetes": {"kubeconfig": "__KUBECONFIG_FILEPATH__"}},{"type": "portmap","snat": true,"capabilities": {"portMappings": true}},{"type": "bandwidth","capabilities": {"bandwidth": true}}]}---
# Source: calico/templates/kdd-crds.yamlapiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: bgpconfigurations.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: BGPConfigurationlistKind: BGPConfigurationListplural: bgpconfigurationssingular: bgpconfigurationscope: Clusterversions:- name: v1schema:openAPIV3Schema:description: BGPConfiguration contains the configuration for any BGP routing.properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: BGPConfigurationSpec contains the values of the BGP configuration.properties:asNumber:description: 'ASNumber is the default AS number used by a node. [Default:64512]'format: int32type: integercommunities:description: Communities is a list of BGP community values and theirarbitrary names for tagging routes.items:description: Community contains standard or large community valueand its name.properties:name:description: Name given to community value.type: stringvalue:description: Value must be of format `aa:nn` or `aa:nn:mm`.For standard community use `aa:nn` format, where `aa` and`nn` are 16 bit number. For large community use `aa:nn:mm`format, where `aa`, `nn` and `mm` are 32 bit number. Where,`aa` is an AS Number, `nn` and `mm` are per-AS identifier.pattern: ^(\d+):(\d+)$|^(\d+):(\d+):(\d+)$type: stringtype: objecttype: arraylistenPort:description: ListenPort is the port where BGP protocol should listen.Defaults to 179maximum: 65535minimum: 1type: integerlogSeverityScreen:description: 'LogSeverityScreen is the log severity above which logsare sent to the stdout. [Default: INFO]'type: stringnodeToNodeMeshEnabled:description: 'NodeToNodeMeshEnabled sets whether full node to nodeBGP mesh is enabled. [Default: true]'type: booleanprefixAdvertisements:description: PrefixAdvertisements contains per-prefix advertisementconfiguration.items:description: PrefixAdvertisement configures advertisement propertiesfor the specified CIDR.properties:cidr:description: CIDR for which properties should be advertised.type: stringcommunities:description: Communities can be list of either community namesalready defined in `Specs.Communities` or community valueof format `aa:nn` or `aa:nn:mm`. For standard community use`aa:nn` format, where `aa` and `nn` are 16 bit number. Forlarge community use `aa:nn:mm` format, where `aa`, `nn` and`mm` are 32 bit number. Where,`aa` is an AS Number, `nn` and`mm` are per-AS identifier.items:type: stringtype: arraytype: objecttype: arrayserviceClusterIPs:description: ServiceClusterIPs are the CIDR blocks from which servicecluster IPs are allocated. If specified, Calico will advertise theseblocks, as well as any cluster IPs within them.items:description: ServiceClusterIPBlock represents a single allowed ClusterIPCIDR block.properties:cidr:type: stringtype: objecttype: arrayserviceExternalIPs:description: ServiceExternalIPs are the CIDR blocks for KubernetesService External IPs. Kubernetes Service ExternalIPs will only beadvertised if they are within one of these blocks.items:description: ServiceExternalIPBlock represents a single allowedExternal IP CIDR block.properties:cidr:type: stringtype: objecttype: arrayserviceLoadBalancerIPs:description: ServiceLoadBalancerIPs are the CIDR blocks for KubernetesService LoadBalancer IPs. Kubernetes Service status.LoadBalancer.IngressIPs will only be advertised if they are within one of these blocks.items:description: ServiceLoadBalancerIPBlock represents a single allowedLoadBalancer IP CIDR block.properties:cidr:type: stringtype: objecttype: arraytype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: bgppeers.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: BGPPeerlistKind: BGPPeerListplural: bgppeerssingular: bgppeerscope: Clusterversions:- name: v1schema:openAPIV3Schema:properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: BGPPeerSpec contains the specification for a BGPPeer resource.properties:asNumber:description: The AS Number of the peer.format: int32type: integerkeepOriginalNextHop:description: Option to keep the original nexthop field when routesare sent to a BGP Peer. Setting "true" configures the selected BGPPeers node to use the "next hop keep;" instead of "next hop self;"(default)in the specific branch of the Node on "bird.cfg".type: booleannode:description: The node name identifying the Calico node instance thatis targeted by this peer. If this is not set, and no nodeSelectoris specified, then this BGP peer selects all nodes in the cluster.type: stringnodeSelector:description: Selector for the nodes that should have this peering. Whenthis is set, the Node field must be empty.type: stringpassword:description: Optional BGP password for the peerings generated by thisBGPPeer resource.properties:secretKeyRef:description: Selects a key of a secret in the node pod's namespace.properties:key:description: The key of the secret to select from. Must bea valid secret key.type: stringname:description: 'Name of the referent. More info: https://kubernetes.io/docs/concepts/overview/working-with-objects/names/#namesTODO: Add other useful fields. apiVersion, kind, uid?'type: stringoptional:description: Specify whether the Secret or its key must bedefinedtype: booleanrequired:- keytype: objecttype: objectpeerIP:description: The IP address of the peer followed by an optional portnumber to peer with. If port number is given, format should be `[<IPv6>]:port`or `<IPv4>:<port>` for IPv4. If optional port number is not set,and this peer IP and ASNumber belongs to a calico/node with ListenPortset in BGPConfiguration, then we use that port to peer.type: stringpeerSelector:description: Selector for the remote nodes to peer with. When thisis set, the PeerIP and ASNumber fields must be empty. For eachpeering between the local node and selected remote nodes, we configurean IPv4 peering if both ends have NodeBGPSpec.IPv4Address specified,and an IPv6 peering if both ends have NodeBGPSpec.IPv6Address specified. Theremote AS number comes from the remote node's NodeBGPSpec.ASNumber,or the global default if that is not set.type: stringsourceAddress:description: Specifies whether and how to configure a source addressfor the peerings generated by this BGPPeer resource. Default value"UseNodeIP" means to configure the node IP as the source address. "None"means not to configure a source address.type: stringtype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: blockaffinities.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: BlockAffinitylistKind: BlockAffinityListplural: blockaffinitiessingular: blockaffinityscope: Clusterversions:- name: v1schema:openAPIV3Schema:properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: BlockAffinitySpec contains the specification for a BlockAffinityresource.properties:cidr:type: stringdeleted:description: Deleted indicates that this block affinity is being deleted.This field is a string for compatibility with older releases thatmistakenly treat this field as a string.type: stringnode:type: stringstate:type: stringrequired:- cidr- deleted- node- statetype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: clusterinformations.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: ClusterInformationlistKind: ClusterInformationListplural: clusterinformationssingular: clusterinformationscope: Clusterversions:- name: v1schema:openAPIV3Schema:description: ClusterInformation contains the cluster specific information.properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: ClusterInformationSpec contains the values of describingthe cluster.properties:calicoVersion:description: CalicoVersion is the version of Calico that the clusteris runningtype: stringclusterGUID:description: ClusterGUID is the GUID of the clustertype: stringclusterType:description: ClusterType describes the type of the clustertype: stringdatastoreReady:description: DatastoreReady is used during significant datastore migrationsto signal to components such as Felix that it should wait beforeaccessing the datastore.type: booleanvariant:description: Variant declares which variant of Calico should be active.type: stringtype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: felixconfigurations.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: FelixConfigurationlistKind: FelixConfigurationListplural: felixconfigurationssingular: felixconfigurationscope: Clusterversions:- name: v1schema:openAPIV3Schema:description: Felix Configuration contains the configuration for Felix.properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: FelixConfigurationSpec contains the values of the Felix configuration.properties:allowIPIPPacketsFromWorkloads:description: 'AllowIPIPPacketsFromWorkloads controls whether Felixwill add a rule to drop IPIP encapsulated traffic from workloads[Default: false]'type: booleanallowVXLANPacketsFromWorkloads:description: 'AllowVXLANPacketsFromWorkloads controls whether Felixwill add a rule to drop VXLAN encapsulated traffic from workloads[Default: false]'type: booleanawsSrcDstCheck:description: 'Set source-destination-check on AWS EC2 instances. Acceptedvalue must be one of "DoNothing", "Enabled" or "Disabled". [Default:DoNothing]'enum:- DoNothing- Enable- Disabletype: stringbpfConnectTimeLoadBalancingEnabled:description: 'BPFConnectTimeLoadBalancingEnabled when in BPF mode,controls whether Felix installs the connection-time load balancer. Theconnect-time load balancer is required for the host to be able toreach Kubernetes services and it improves the performance of pod-to-serviceconnections. The only reason to disable it is for debugging purposes. [Default:true]'type: booleanbpfDataIfacePattern:description: BPFDataIfacePattern is a regular expression that controlswhich interfaces Felix should attach BPF programs to in order tocatch traffic to/from the network. This needs to match the interfacesthat Calico workload traffic flows over as well as any interfacesthat handle incoming traffic to nodeports and services from outsidethe cluster. It should not match the workload interfaces (usuallynamed cali...).type: stringbpfDisableUnprivileged:description: 'BPFDisableUnprivileged, if enabled, Felix sets the kernel.unprivileged_bpf_disabledsysctl to disable unprivileged use of BPF. This ensures that unprivilegedusers cannot access Calico''s BPF maps and cannot insert their ownBPF programs to interfere with Calico''s. [Default: true]'type: booleanbpfEnabled:description: 'BPFEnabled, if enabled Felix will use the BPF dataplane.[Default: false]'type: booleanbpfExternalServiceMode:description: 'BPFExternalServiceMode in BPF mode, controls how connectionsfrom outside the cluster to services (node ports and cluster IPs)are forwarded to remote workloads. If set to "Tunnel" then bothrequest and response traffic is tunneled to the remote node. Ifset to "DSR", the request traffic is tunneled but the response trafficis sent directly from the remote node. In "DSR" mode, the remotenode appears to use the IP of the ingress node; this requires apermissive L2 network. [Default: Tunnel]'type: stringbpfKubeProxyEndpointSlicesEnabled:description: BPFKubeProxyEndpointSlicesEnabled in BPF mode, controlswhether Felix's embedded kube-proxy accepts EndpointSlices or not.type: booleanbpfKubeProxyIptablesCleanupEnabled:description: 'BPFKubeProxyIptablesCleanupEnabled, if enabled in BPFmode, Felix will proactively clean up the upstream Kubernetes kube-proxy''siptables chains. Should only be enabled if kube-proxy is not running. [Default:true]'type: booleanbpfKubeProxyMinSyncPeriod:description: 'BPFKubeProxyMinSyncPeriod, in BPF mode, controls theminimum time between updates to the dataplane for Felix''s embeddedkube-proxy. Lower values give reduced set-up latency. Higher valuesreduce Felix CPU usage by batching up more work. [Default: 1s]'type: stringbpfLogLevel:description: 'BPFLogLevel controls the log level of the BPF programswhen in BPF dataplane mode. One of "Off", "Info", or "Debug". Thelogs are emitted to the BPF trace pipe, accessible with the command`tc exec bpf debug`. [Default: Off].'type: stringchainInsertMode:description: 'ChainInsertMode controls whether Felix hooks the kernel''stop-level iptables chains by inserting a rule at the top of thechain or by appending a rule at the bottom. insert is the safe defaultsince it prevents Calico''s rules from being bypassed. If you switchto append mode, be sure that the other rules in the chains signalacceptance by falling through to the Calico rules, otherwise theCalico policy will be bypassed. [Default: insert]'type: stringdataplaneDriver:type: stringdebugDisableLogDropping:type: booleandebugMemoryProfilePath:type: stringdebugSimulateCalcGraphHangAfter:type: stringdebugSimulateDataplaneHangAfter:type: stringdefaultEndpointToHostAction:description: 'DefaultEndpointToHostAction controls what happens totraffic that goes from a workload endpoint to the host itself (afterthe traffic hits the endpoint egress policy). By default Calicoblocks traffic from workload endpoints to the host itself with aniptables "DROP" action. If you want to allow some or all trafficfrom endpoint to host, set this parameter to RETURN or ACCEPT. UseRETURN if you have your own rules in the iptables "INPUT" chain;Calico will insert its rules at the top of that chain, then "RETURN"packets to the "INPUT" chain once it has completed processing workloadendpoint egress policy. Use ACCEPT to unconditionally accept packetsfrom workloads after processing workload endpoint egress policy.[Default: Drop]'type: stringdeviceRouteProtocol:description: This defines the route protocol added to programmed deviceroutes, by default this will be RTPROT_BOOT when left blank.type: integerdeviceRouteSourceAddress:description: This is the source address to use on programmed deviceroutes. By default the source address is left blank, leaving thekernel to choose the source address used.type: stringdisableConntrackInvalidCheck:type: booleanendpointReportingDelay:type: stringendpointReportingEnabled:type: booleanexternalNodesList:description: ExternalNodesCIDRList is a list of CIDR's of external-non-calico-nodeswhich may source tunnel traffic and have the tunneled traffic beaccepted at calico nodes.items:type: stringtype: arrayfailsafeInboundHostPorts:description: 'FailsafeInboundHostPorts is a comma-delimited list ofUDP/TCP ports that Felix will allow incoming traffic to host endpointson irrespective of the security policy. This is useful to avoidaccidentally cutting off a host with incorrect configuration. Eachport should be specified as tcp:<port-number> or udp:<port-number>.For back-compatibility, if the protocol is not specified, it defaultsto "tcp". To disable all inbound host ports, use the value none.The default value allows ssh access and DHCP. [Default: tcp:22,udp:68, tcp:179, tcp:2379, tcp:2380, tcp:6443, tcp:6666, tcp:6667]'items:description: ProtoPort is combination of protocol and port, bothmust be specified.properties:port:type: integerprotocol:type: stringrequired:- port- protocoltype: objecttype: arrayfailsafeOutboundHostPorts:description: 'FailsafeOutboundHostPorts is a comma-delimited listof UDP/TCP ports that Felix will allow outgoing traffic from hostendpoints to irrespective of the security policy. This is usefulto avoid accidentally cutting off a host with incorrect configuration.Each port should be specified as tcp:<port-number> or udp:<port-number>.For back-compatibility, if the protocol is not specified, it defaultsto "tcp". To disable all outbound host ports, use the value none.The default value opens etcd''s standard ports to ensure that Felixdoes not get cut off from etcd as well as allowing DHCP and DNS.[Default: tcp:179, tcp:2379, tcp:2380, tcp:6443, tcp:6666, tcp:6667,udp:53, udp:67]'items:description: ProtoPort is combination of protocol and port, bothmust be specified.properties:port:type: integerprotocol:type: stringrequired:- port- protocoltype: objecttype: arrayfeatureDetectOverride:description: FeatureDetectOverride is used to override the featuredetection. Values are specified in a comma separated list with nospaces, example; "SNATFullyRandom=true,MASQFullyRandom=false,RestoreSupportsLock="."true" or "false" will force the feature, empty or omitted valuesare auto-detected.type: stringgenericXDPEnabled:description: 'GenericXDPEnabled enables Generic XDP so network cardsthat don''t support XDP offload or driver modes can use XDP. Thisis not recommended since it doesn''t provide better performancethan iptables. [Default: false]'type: booleanhealthEnabled:type: booleanhealthHost:type: stringhealthPort:type: integerinterfaceExclude:description: 'InterfaceExclude is a comma-separated list of interfacesthat Felix should exclude when monitoring for host endpoints. Thedefault value ensures that Felix ignores Kubernetes'' IPVS dummyinterface, which is used internally by kube-proxy. If you want toexclude multiple interface names using a single value, the listsupports regular expressions. For regular expressions you must wrapthe value with ''/''. For example having values ''/^kube/,veth1''will exclude all interfaces that begin with ''kube'' and also theinterface ''veth1''. [Default: kube-ipvs0]'type: stringinterfacePrefix:description: 'InterfacePrefix is the interface name prefix that identifiesworkload endpoints and so distinguishes them from host endpointinterfaces. Note: in environments other than bare metal, the orchestratorsconfigure this appropriately. For example our Kubernetes and Dockerintegrations set the ''cali'' value, and our OpenStack integrationsets the ''tap'' value. [Default: cali]'type: stringinterfaceRefreshInterval:description: InterfaceRefreshInterval is the period at which Felixrescans local interfaces to verify their state. The rescan can bedisabled by setting the interval to 0.type: stringipipEnabled:type: booleanipipMTU:description: 'IPIPMTU is the MTU to set on the tunnel device. SeeConfiguring MTU [Default: 1440]'type: integeripsetsRefreshInterval:description: 'IpsetsRefreshInterval is the period at which Felix re-checksall iptables state to ensure that no other process has accidentallybroken Calico''s rules. Set to 0 to disable iptables refresh. [Default:90s]'type: stringiptablesBackend:description: IptablesBackend specifies which backend of iptables willbe used. The default is legacy.type: stringiptablesFilterAllowAction:type: stringiptablesLockFilePath:description: 'IptablesLockFilePath is the location of the iptableslock file. You may need to change this if the lock file is not inits standard location (for example if you have mapped it into Felix''scontainer at a different path). [Default: /run/xtables.lock]'type: stringiptablesLockProbeInterval:description: 'IptablesLockProbeInterval is the time that Felix willwait between attempts to acquire the iptables lock if it is notavailable. Lower values make Felix more responsive when the lockis contended, but use more CPU. [Default: 50ms]'type: stringiptablesLockTimeout:description: 'IptablesLockTimeout is the time that Felix will waitfor the iptables lock, or 0, to disable. To use this feature, Felixmust share the iptables lock file with all other processes thatalso take the lock. When running Felix inside a container, thisrequires the /run directory of the host to be mounted into the calico/nodeor calico/felix container. [Default: 0s disabled]'type: stringiptablesMangleAllowAction:type: stringiptablesMarkMask:description: 'IptablesMarkMask is the mask that Felix selects itsIPTables Mark bits from. Should be a 32 bit hexadecimal number withat least 8 bits set, none of which clash with any other mark bitsin use on the system. [Default: 0xff000000]'format: int32type: integeriptablesNATOutgoingInterfaceFilter:type: stringiptablesPostWriteCheckInterval:description: 'IptablesPostWriteCheckInterval is the period after Felixhas done a write to the dataplane that it schedules an extra readback in order to check the write was not clobbered by another process.This should only occur if another application on the system doesn''trespect the iptables lock. [Default: 1s]'type: stringiptablesRefreshInterval:description: 'IptablesRefreshInterval is the period at which Felixre-checks the IP sets in the dataplane to ensure that no other processhas accidentally broken Calico''s rules. Set to 0 to disable IPsets refresh. Note: the default for this value is lower than theother refresh intervals as a workaround for a Linux kernel bug thatwas fixed in kernel version 4.11. If you are using v4.11 or greateryou may want to set this to, a higher value to reduce Felix CPUusage. [Default: 10s]'type: stringipv6Support:type: booleankubeNodePortRanges:description: 'KubeNodePortRanges holds list of port ranges used forservice node ports. Only used if felix detects kube-proxy runningin ipvs mode. Felix uses these ranges to separate host and workloadtraffic. [Default: 30000:32767].'items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arraylogFilePath:description: 'LogFilePath is the full path to the Felix log. Set tonone to disable file logging. [Default: /var/log/calico/felix.log]'type: stringlogPrefix:description: 'LogPrefix is the log prefix that Felix uses when renderingLOG rules. [Default: calico-packet]'type: stringlogSeverityFile:description: 'LogSeverityFile is the log severity above which logsare sent to the log file. [Default: Info]'type: stringlogSeverityScreen:description: 'LogSeverityScreen is the log severity above which logsare sent to the stdout. [Default: Info]'type: stringlogSeveritySys:description: 'LogSeveritySys is the log severity above which logsare sent to the syslog. Set to None for no logging to syslog. [Default:Info]'type: stringmaxIpsetSize:type: integermetadataAddr:description: 'MetadataAddr is the IP address or domain name of theserver that can answer VM queries for cloud-init metadata. In OpenStack,this corresponds to the machine running nova-api (or in Ubuntu,nova-api-metadata). A value of none (case insensitive) means thatFelix should not set up any NAT rule for the metadata path. [Default:127.0.0.1]'type: stringmetadataPort:description: 'MetadataPort is the port of the metadata server. This,combined with global.MetadataAddr (if not ''None''), is used toset up a NAT rule, from 169.254.169.254:80 to MetadataAddr:MetadataPort.In most cases this should not need to be changed [Default: 8775].'type: integermtuIfacePattern:description: MTUIfacePattern is a regular expression that controlswhich interfaces Felix should scan in order to calculate the host'sMTU. This should not match workload interfaces (usually named cali...).type: stringnatOutgoingAddress:description: NATOutgoingAddress specifies an address to use when performingsource NAT for traffic in a natOutgoing pool that is leaving thenetwork. By default the address used is an address on the interfacethe traffic is leaving on (ie it uses the iptables MASQUERADE target)type: stringnatPortRange:anyOf:- type: integer- type: stringdescription: NATPortRange specifies the range of ports that is usedfor port mapping when doing outgoing NAT. When unset the defaultbehavior of the network stack is used.pattern: ^.*x-kubernetes-int-or-string: truenetlinkTimeout:type: stringopenstackRegion:description: 'OpenstackRegion is the name of the region that a particularFelix belongs to. In a multi-region Calico/OpenStack deployment,this must be configured somehow for each Felix (here in the datamodel,or in felix.cfg or the environment on each compute node), and mustmatch the [calico] openstack_region value configured in neutron.confon each node. [Default: Empty]'type: stringpolicySyncPathPrefix:description: 'PolicySyncPathPrefix is used to by Felix to communicatepolicy changes to external services, like Application layer policy.[Default: Empty]'type: stringprometheusGoMetricsEnabled:description: 'PrometheusGoMetricsEnabled disables Go runtime metricscollection, which the Prometheus client does by default, when setto false. This reduces the number of metrics reported, reducingPrometheus load. [Default: true]'type: booleanprometheusMetricsEnabled:description: 'PrometheusMetricsEnabled enables the Prometheus metricsserver in Felix if set to true. [Default: false]'type: booleanprometheusMetricsHost:description: 'PrometheusMetricsHost is the host that the Prometheusmetrics server should bind to. [Default: empty]'type: stringprometheusMetricsPort:description: 'PrometheusMetricsPort is the TCP port that the Prometheusmetrics server should bind to. [Default: 9091]'type: integerprometheusProcessMetricsEnabled:description: 'PrometheusProcessMetricsEnabled disables process metricscollection, which the Prometheus client does by default, when setto false. This reduces the number of metrics reported, reducingPrometheus load. [Default: true]'type: booleanremoveExternalRoutes:description: Whether or not to remove device routes that have notbeen programmed by Felix. Disabling this will allow external applicationsto also add device routes. This is enabled by default which meanswe will remove externally added routes.type: booleanreportingInterval:description: 'ReportingInterval is the interval at which Felix reportsits status into the datastore or 0 to disable. Must be non-zeroin OpenStack deployments. [Default: 30s]'type: stringreportingTTL:description: 'ReportingTTL is the time-to-live setting for process-widestatus reports. [Default: 90s]'type: stringrouteRefreshInterval:description: 'RouteRefreshInterval is the period at which Felix re-checksthe routes in the dataplane to ensure that no other process hasaccidentally broken Calico''s rules. Set to 0 to disable route refresh.[Default: 90s]'type: stringrouteSource:description: 'RouteSource configures where Felix gets its routinginformation. - WorkloadIPs: use workload endpoints to constructroutes. - CalicoIPAM: the default - use IPAM data to construct routes.'type: stringrouteTableRange:description: Calico programs additional Linux route tables for variouspurposes. RouteTableRange specifies the indices of the route tablesthat Calico should use.properties:max:type: integermin:type: integerrequired:- max- mintype: objectserviceLoopPrevention:description: 'When service IP advertisement is enabled, prevent routingloops to service IPs that are not in use, by dropping or rejectingpackets that do not get DNAT''d by kube-proxy. Unless set to "Disabled",in which case such routing loops continue to be allowed. [Default:Drop]'type: stringsidecarAccelerationEnabled:description: 'SidecarAccelerationEnabled enables experimental sidecaracceleration [Default: false]'type: booleanusageReportingEnabled:description: 'UsageReportingEnabled reports anonymous Calico versionnumber and cluster size to projectcalico.org. Logs warnings returnedby the usage server. For example, if a significant security vulnerabilityhas been discovered in the version of Calico being used. [Default:true]'type: booleanusageReportingInitialDelay:description: 'UsageReportingInitialDelay controls the minimum delaybefore Felix makes a report. [Default: 300s]'type: stringusageReportingInterval:description: 'UsageReportingInterval controls the interval at whichFelix makes reports. [Default: 86400s]'type: stringuseInternalDataplaneDriver:type: booleanvxlanEnabled:type: booleanvxlanMTU:description: 'VXLANMTU is the MTU to set on the tunnel device. SeeConfiguring MTU [Default: 1440]'type: integervxlanPort:type: integervxlanVNI:type: integerwireguardEnabled:description: 'WireguardEnabled controls whether Wireguard is enabled.[Default: false]'type: booleanwireguardInterfaceName:description: 'WireguardInterfaceName specifies the name to use forthe Wireguard interface. [Default: wg.calico]'type: stringwireguardListeningPort:description: 'WireguardListeningPort controls the listening port usedby Wireguard. [Default: 51820]'type: integerwireguardMTU:description: 'WireguardMTU controls the MTU on the Wireguard interface.See Configuring MTU [Default: 1420]'type: integerwireguardRoutingRulePriority:description: 'WireguardRoutingRulePriority controls the priority valueto use for the Wireguard routing rule. [Default: 99]'type: integerxdpEnabled:description: 'XDPEnabled enables XDP acceleration for suitable untrackedincoming deny rules. [Default: true]'type: booleanxdpRefreshInterval:description: 'XDPRefreshInterval is the period at which Felix re-checksall XDP state to ensure that no other process has accidentally brokenCalico''s BPF maps or attached programs. Set to 0 to disable XDPrefresh. [Default: 90s]'type: stringtype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: globalnetworkpolicies.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: GlobalNetworkPolicylistKind: GlobalNetworkPolicyListplural: globalnetworkpoliciessingular: globalnetworkpolicyscope: Clusterversions:- name: v1schema:openAPIV3Schema:properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:properties:applyOnForward:description: ApplyOnForward indicates to apply the rules in this policyon forward traffic.type: booleandoNotTrack:description: DoNotTrack indicates whether packets matched by the rulesin this policy should go through the data plane's connection tracking,such as Linux conntrack. If True, the rules in this policy areapplied before any data plane connection tracking, and packets allowedby this policy are marked as not to be tracked.type: booleanegress:description: The ordered set of egress rules. Each rule containsa set of packet match criteria and a corresponding action to apply.items:description: "A Rule encapsulates a set of match criteria and anaction. Both selector-based security Policy and security Profilesreference rules - separated out as a list of rules for both ingressand egress packet matching. \n Each positive match criteria hasa negated version, prefixed with \"Not\". All the match criteriawithin a rule must be satisfied for a packet to match. A singlerule can contain the positive and negative version of a matchand both must be satisfied for the rule to match."properties:action:type: stringdestination:description: Destination contains the match criteria that applyto destination entity.properties:namespaceSelector:description: "NamespaceSelector is an optional field thatcontains a selector expression. Only traffic that originatesfrom (or terminates at) endpoints within the selectednamespaces will be matched. When both NamespaceSelectorand Selector are defined on the same rule, then only workloadendpoints that are matched by both selectors will be selectedby the rule. \n For NetworkPolicy, an empty NamespaceSelectorimplies that the Selector is limited to selecting onlyworkload endpoints in the same namespace as the NetworkPolicy.\n For NetworkPolicy, `global()` NamespaceSelector impliesthat the Selector is limited to selecting only GlobalNetworkSetor HostEndpoint. \n For GlobalNetworkPolicy, an emptyNamespaceSelector implies the Selector applies to workloadendpoints across all namespaces."type: stringnets:description: Nets is an optional field that restricts therule to only apply to traffic that originates from (orterminates at) IP addresses in any of the given subnets.items:type: stringtype: arraynotNets:description: NotNets is the negated version of the Netsfield.items:type: stringtype: arraynotPorts:description: NotPorts is the negated version of the Portsfield. Since only some protocols have ports, if any portsare specified it requires the Protocol match in the Ruleto be set to "TCP" or "UDP".items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arraynotSelector:description: NotSelector is the negated version of the Selectorfield. See Selector field for subtleties with negatedselectors.type: stringports:description: "Ports is an optional field that restrictsthe rule to only apply to traffic that has a source (destination)port that matches one of these ranges/values. This valueis a list of integers or strings that represent rangesof ports. \n Since only some protocols have ports, ifany ports are specified it requires the Protocol matchin the Rule to be set to \"TCP\" or \"UDP\"."items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arrayselector:description: "Selector is an optional field that containsa selector expression (see Policy for sample syntax).\ Only traffic that originates from (terminates at) endpointsmatching the selector will be matched. \n Note that: inaddition to the negated version of the Selector (see NotSelectorbelow), the selector expression syntax itself supportsnegation. The two types of negation are subtly different.One negates the set of matched endpoints, the other negatesthe whole match: \n \tSelector = \"!has(my_label)\" matchespackets that are from other Calico-controlled \tendpointsthat do not have the label \"my_label\". \n \tNotSelector= \"has(my_label)\" matches packets that are not fromCalico-controlled \tendpoints that do have the label \"my_label\".\n The effect is that the latter will accept packets fromnon-Calico sources whereas the former is limited to packetsfrom Calico-controlled endpoints."type: stringserviceAccounts:description: ServiceAccounts is an optional field that restrictsthe rule to only apply to traffic that originates from(or terminates at) a pod running as a matching serviceaccount.properties:names:description: Names is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount whose name is in the list.items:type: stringtype: arrayselector:description: Selector is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount that matches the given label selector. Ifboth Names and Selector are specified then they areAND'ed.type: stringtype: objecttype: objecthttp:description: HTTP contains match criteria that apply to HTTPrequests.properties:methods:description: Methods is an optional field that restrictsthe rule to apply only to HTTP requests that use one ofthe listed HTTP Methods (e.g. GET, PUT, etc.) Multiplemethods are OR'd together.items:type: stringtype: arraypaths:description: 'Paths is an optional field that restrictsthe rule to apply to HTTP requests that use one of thelisted HTTP Paths. Multiple paths are OR''d together.e.g: - exact: /foo - prefix: /bar NOTE: Each entry mayONLY specify either a `exact` or a `prefix` match. Thevalidator will check for it.'items:description: 'HTTPPath specifies an HTTP path to match.It may be either of the form: exact: <path>: which matchesthe path exactly or prefix: <path-prefix>: which matchesthe path prefix'properties:exact:type: stringprefix:type: stringtype: objecttype: arraytype: objecticmp:description: ICMP is an optional field that restricts the ruleto apply to a specific type and code of ICMP traffic. Thisshould only be specified if the Protocol field is set to "ICMP"or "ICMPv6".properties:code:description: Match on a specific ICMP code. If specified,the Type value must also be specified. This is a technicallimitation imposed by the kernel's iptables firewall,which Calico uses to enforce the rule.type: integertype:description: Match on a specific ICMP type. For examplea value of 8 refers to ICMP Echo Request (i.e. pings).type: integertype: objectipVersion:description: IPVersion is an optional field that restricts therule to only match a specific IP version.type: integermetadata:description: Metadata contains additional information for thisruleproperties:annotations:additionalProperties:type: stringdescription: Annotations is a set of key value pairs thatgive extra information about the ruletype: objecttype: objectnotICMP:description: NotICMP is the negated version of the ICMP field.properties:code:description: Match on a specific ICMP code. If specified,the Type value must also be specified. This is a technicallimitation imposed by the kernel's iptables firewall,which Calico uses to enforce the rule.type: integertype:description: Match on a specific ICMP type. For examplea value of 8 refers to ICMP Echo Request (i.e. pings).type: integertype: objectnotProtocol:anyOf:- type: integer- type: stringdescription: NotProtocol is the negated version of the Protocolfield.pattern: ^.*x-kubernetes-int-or-string: trueprotocol:anyOf:- type: integer- type: stringdescription: "Protocol is an optional field that restricts therule to only apply to traffic of a specific IP protocol. Requiredif any of the EntityRules contain Ports (because ports onlyapply to certain protocols). \n Must be one of these stringvalues: \"TCP\", \"UDP\", \"ICMP\", \"ICMPv6\", \"SCTP\",\"UDPLite\" or an integer in the range 1-255."pattern: ^.*x-kubernetes-int-or-string: truesource:description: Source contains the match criteria that apply tosource entity.properties:namespaceSelector:description: "NamespaceSelector is an optional field thatcontains a selector expression. Only traffic that originatesfrom (or terminates at) endpoints within the selectednamespaces will be matched. When both NamespaceSelectorand Selector are defined on the same rule, then only workloadendpoints that are matched by both selectors will be selectedby the rule. \n For NetworkPolicy, an empty NamespaceSelectorimplies that the Selector is limited to selecting onlyworkload endpoints in the same namespace as the NetworkPolicy.\n For NetworkPolicy, `global()` NamespaceSelector impliesthat the Selector is limited to selecting only GlobalNetworkSetor HostEndpoint. \n For GlobalNetworkPolicy, an emptyNamespaceSelector implies the Selector applies to workloadendpoints across all namespaces."type: stringnets:description: Nets is an optional field that restricts therule to only apply to traffic that originates from (orterminates at) IP addresses in any of the given subnets.items:type: stringtype: arraynotNets:description: NotNets is the negated version of the Netsfield.items:type: stringtype: arraynotPorts:description: NotPorts is the negated version of the Portsfield. Since only some protocols have ports, if any portsare specified it requires the Protocol match in the Ruleto be set to "TCP" or "UDP".items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arraynotSelector:description: NotSelector is the negated version of the Selectorfield. See Selector field for subtleties with negatedselectors.type: stringports:description: "Ports is an optional field that restrictsthe rule to only apply to traffic that has a source (destination)port that matches one of these ranges/values. This valueis a list of integers or strings that represent rangesof ports. \n Since only some protocols have ports, ifany ports are specified it requires the Protocol matchin the Rule to be set to \"TCP\" or \"UDP\"."items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arrayselector:description: "Selector is an optional field that containsa selector expression (see Policy for sample syntax).\ Only traffic that originates from (terminates at) endpointsmatching the selector will be matched. \n Note that: inaddition to the negated version of the Selector (see NotSelectorbelow), the selector expression syntax itself supportsnegation. The two types of negation are subtly different.One negates the set of matched endpoints, the other negatesthe whole match: \n \tSelector = \"!has(my_label)\" matchespackets that are from other Calico-controlled \tendpointsthat do not have the label \"my_label\". \n \tNotSelector= \"has(my_label)\" matches packets that are not fromCalico-controlled \tendpoints that do have the label \"my_label\".\n The effect is that the latter will accept packets fromnon-Calico sources whereas the former is limited to packetsfrom Calico-controlled endpoints."type: stringserviceAccounts:description: ServiceAccounts is an optional field that restrictsthe rule to only apply to traffic that originates from(or terminates at) a pod running as a matching serviceaccount.properties:names:description: Names is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount whose name is in the list.items:type: stringtype: arrayselector:description: Selector is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount that matches the given label selector. Ifboth Names and Selector are specified then they areAND'ed.type: stringtype: objecttype: objectrequired:- actiontype: objecttype: arrayingress:description: The ordered set of ingress rules. Each rule containsa set of packet match criteria and a corresponding action to apply.items:description: "A Rule encapsulates a set of match criteria and anaction. Both selector-based security Policy and security Profilesreference rules - separated out as a list of rules for both ingressand egress packet matching. \n Each positive match criteria hasa negated version, prefixed with \"Not\". All the match criteriawithin a rule must be satisfied for a packet to match. A singlerule can contain the positive and negative version of a matchand both must be satisfied for the rule to match."properties:action:type: stringdestination:description: Destination contains the match criteria that applyto destination entity.properties:namespaceSelector:description: "NamespaceSelector is an optional field thatcontains a selector expression. Only traffic that originatesfrom (or terminates at) endpoints within the selectednamespaces will be matched. When both NamespaceSelectorand Selector are defined on the same rule, then only workloadendpoints that are matched by both selectors will be selectedby the rule. \n For NetworkPolicy, an empty NamespaceSelectorimplies that the Selector is limited to selecting onlyworkload endpoints in the same namespace as the NetworkPolicy.\n For NetworkPolicy, `global()` NamespaceSelector impliesthat the Selector is limited to selecting only GlobalNetworkSetor HostEndpoint. \n For GlobalNetworkPolicy, an emptyNamespaceSelector implies the Selector applies to workloadendpoints across all namespaces."type: stringnets:description: Nets is an optional field that restricts therule to only apply to traffic that originates from (orterminates at) IP addresses in any of the given subnets.items:type: stringtype: arraynotNets:description: NotNets is the negated version of the Netsfield.items:type: stringtype: arraynotPorts:description: NotPorts is the negated version of the Portsfield. Since only some protocols have ports, if any portsare specified it requires the Protocol match in the Ruleto be set to "TCP" or "UDP".items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arraynotSelector:description: NotSelector is the negated version of the Selectorfield. See Selector field for subtleties with negatedselectors.type: stringports:description: "Ports is an optional field that restrictsthe rule to only apply to traffic that has a source (destination)port that matches one of these ranges/values. This valueis a list of integers or strings that represent rangesof ports. \n Since only some protocols have ports, ifany ports are specified it requires the Protocol matchin the Rule to be set to \"TCP\" or \"UDP\"."items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arrayselector:description: "Selector is an optional field that containsa selector expression (see Policy for sample syntax).\ Only traffic that originates from (terminates at) endpointsmatching the selector will be matched. \n Note that: inaddition to the negated version of the Selector (see NotSelectorbelow), the selector expression syntax itself supportsnegation. The two types of negation are subtly different.One negates the set of matched endpoints, the other negatesthe whole match: \n \tSelector = \"!has(my_label)\" matchespackets that are from other Calico-controlled \tendpointsthat do not have the label \"my_label\". \n \tNotSelector= \"has(my_label)\" matches packets that are not fromCalico-controlled \tendpoints that do have the label \"my_label\".\n The effect is that the latter will accept packets fromnon-Calico sources whereas the former is limited to packetsfrom Calico-controlled endpoints."type: stringserviceAccounts:description: ServiceAccounts is an optional field that restrictsthe rule to only apply to traffic that originates from(or terminates at) a pod running as a matching serviceaccount.properties:names:description: Names is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount whose name is in the list.items:type: stringtype: arrayselector:description: Selector is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount that matches the given label selector. Ifboth Names and Selector are specified then they areAND'ed.type: stringtype: objecttype: objecthttp:description: HTTP contains match criteria that apply to HTTPrequests.properties:methods:description: Methods is an optional field that restrictsthe rule to apply only to HTTP requests that use one ofthe listed HTTP Methods (e.g. GET, PUT, etc.) Multiplemethods are OR'd together.items:type: stringtype: arraypaths:description: 'Paths is an optional field that restrictsthe rule to apply to HTTP requests that use one of thelisted HTTP Paths. Multiple paths are OR''d together.e.g: - exact: /foo - prefix: /bar NOTE: Each entry mayONLY specify either a `exact` or a `prefix` match. Thevalidator will check for it.'items:description: 'HTTPPath specifies an HTTP path to match.It may be either of the form: exact: <path>: which matchesthe path exactly or prefix: <path-prefix>: which matchesthe path prefix'properties:exact:type: stringprefix:type: stringtype: objecttype: arraytype: objecticmp:description: ICMP is an optional field that restricts the ruleto apply to a specific type and code of ICMP traffic. Thisshould only be specified if the Protocol field is set to "ICMP"or "ICMPv6".properties:code:description: Match on a specific ICMP code. If specified,the Type value must also be specified. This is a technicallimitation imposed by the kernel's iptables firewall,which Calico uses to enforce the rule.type: integertype:description: Match on a specific ICMP type. For examplea value of 8 refers to ICMP Echo Request (i.e. pings).type: integertype: objectipVersion:description: IPVersion is an optional field that restricts therule to only match a specific IP version.type: integermetadata:description: Metadata contains additional information for thisruleproperties:annotations:additionalProperties:type: stringdescription: Annotations is a set of key value pairs thatgive extra information about the ruletype: objecttype: objectnotICMP:description: NotICMP is the negated version of the ICMP field.properties:code:description: Match on a specific ICMP code. If specified,the Type value must also be specified. This is a technicallimitation imposed by the kernel's iptables firewall,which Calico uses to enforce the rule.type: integertype:description: Match on a specific ICMP type. For examplea value of 8 refers to ICMP Echo Request (i.e. pings).type: integertype: objectnotProtocol:anyOf:- type: integer- type: stringdescription: NotProtocol is the negated version of the Protocolfield.pattern: ^.*x-kubernetes-int-or-string: trueprotocol:anyOf:- type: integer- type: stringdescription: "Protocol is an optional field that restricts therule to only apply to traffic of a specific IP protocol. Requiredif any of the EntityRules contain Ports (because ports onlyapply to certain protocols). \n Must be one of these stringvalues: \"TCP\", \"UDP\", \"ICMP\", \"ICMPv6\", \"SCTP\",\"UDPLite\" or an integer in the range 1-255."pattern: ^.*x-kubernetes-int-or-string: truesource:description: Source contains the match criteria that apply tosource entity.properties:namespaceSelector:description: "NamespaceSelector is an optional field thatcontains a selector expression. Only traffic that originatesfrom (or terminates at) endpoints within the selectednamespaces will be matched. When both NamespaceSelectorand Selector are defined on the same rule, then only workloadendpoints that are matched by both selectors will be selectedby the rule. \n For NetworkPolicy, an empty NamespaceSelectorimplies that the Selector is limited to selecting onlyworkload endpoints in the same namespace as the NetworkPolicy.\n For NetworkPolicy, `global()` NamespaceSelector impliesthat the Selector is limited to selecting only GlobalNetworkSetor HostEndpoint. \n For GlobalNetworkPolicy, an emptyNamespaceSelector implies the Selector applies to workloadendpoints across all namespaces."type: stringnets:description: Nets is an optional field that restricts therule to only apply to traffic that originates from (orterminates at) IP addresses in any of the given subnets.items:type: stringtype: arraynotNets:description: NotNets is the negated version of the Netsfield.items:type: stringtype: arraynotPorts:description: NotPorts is the negated version of the Portsfield. Since only some protocols have ports, if any portsare specified it requires the Protocol match in the Ruleto be set to "TCP" or "UDP".items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arraynotSelector:description: NotSelector is the negated version of the Selectorfield. See Selector field for subtleties with negatedselectors.type: stringports:description: "Ports is an optional field that restrictsthe rule to only apply to traffic that has a source (destination)port that matches one of these ranges/values. This valueis a list of integers or strings that represent rangesof ports. \n Since only some protocols have ports, ifany ports are specified it requires the Protocol matchin the Rule to be set to \"TCP\" or \"UDP\"."items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arrayselector:description: "Selector is an optional field that containsa selector expression (see Policy for sample syntax).\ Only traffic that originates from (terminates at) endpointsmatching the selector will be matched. \n Note that: inaddition to the negated version of the Selector (see NotSelectorbelow), the selector expression syntax itself supportsnegation. The two types of negation are subtly different.One negates the set of matched endpoints, the other negatesthe whole match: \n \tSelector = \"!has(my_label)\" matchespackets that are from other Calico-controlled \tendpointsthat do not have the label \"my_label\". \n \tNotSelector= \"has(my_label)\" matches packets that are not fromCalico-controlled \tendpoints that do have the label \"my_label\".\n The effect is that the latter will accept packets fromnon-Calico sources whereas the former is limited to packetsfrom Calico-controlled endpoints."type: stringserviceAccounts:description: ServiceAccounts is an optional field that restrictsthe rule to only apply to traffic that originates from(or terminates at) a pod running as a matching serviceaccount.properties:names:description: Names is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount whose name is in the list.items:type: stringtype: arrayselector:description: Selector is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount that matches the given label selector. Ifboth Names and Selector are specified then they areAND'ed.type: stringtype: objecttype: objectrequired:- actiontype: objecttype: arraynamespaceSelector:description: NamespaceSelector is an optional field for an expressionused to select a pod based on namespaces.type: stringorder:description: Order is an optional field that specifies the order inwhich the policy is applied. Policies with higher "order" are appliedafter those with lower order. If the order is omitted, it may beconsidered to be "infinite" - i.e. the policy will be applied last. Policieswith identical order will be applied in alphanumerical order basedon the Policy "Name".type: numberpreDNAT:description: PreDNAT indicates to apply the rules in this policy beforeany DNAT.type: booleanselector:description: "The selector is an expression used to pick pick outthe endpoints that the policy should be applied to. \n Selectorexpressions follow this syntax: \n \tlabel == \"string_literal\"\ -> comparison, e.g. my_label == \"foo bar\" \tlabel != \"string_literal\"\ -> not equal; also matches if label is not present \tlabel in{ \"a\", \"b\", \"c\", ... } -> true if the value of label X isone of \"a\", \"b\", \"c\" \tlabel not in { \"a\", \"b\", \"c\",... } -> true if the value of label X is not one of \"a\", \"b\",\"c\" \thas(label_name) -> True if that label is present \t! expr-> negation of expr \texpr && expr -> Short-circuit and \texpr|| expr -> Short-circuit or \t( expr ) -> parens for grouping \tall()or the empty selector -> matches all endpoints. \n Label names areallowed to contain alphanumerics, -, _ and /. String literals aremore permissive but they do not support escape characters. \n Examples(with made-up labels): \n \ttype == \"webserver\" && deployment== \"prod\" \ttype in {\"frontend\", \"backend\"} \tdeployment !=\"dev\" \t! has(label_name)"type: stringserviceAccountSelector:description: ServiceAccountSelector is an optional field for an expressionused to select a pod based on service accounts.type: stringtypes:description: "Types indicates whether this policy applies to ingress,or to egress, or to both. When not explicitly specified (and sothe value on creation is empty or nil), Calico defaults Types accordingto what Ingress and Egress rules are present in the policy. Thedefault is: \n - [ PolicyTypeIngress ], if there are no Egress rules(including the case where there are also no Ingress rules) \n- [ PolicyTypeEgress ], if there are Egress rules but no Ingressrules \n - [ PolicyTypeIngress, PolicyTypeEgress ], if there areboth Ingress and Egress rules. \n When the policy is read back again,Types will always be one of these values, never empty or nil."items:description: PolicyType enumerates the possible values of the PolicySpecTypes field.type: stringtype: arraytype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: globalnetworksets.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: GlobalNetworkSetlistKind: GlobalNetworkSetListplural: globalnetworksetssingular: globalnetworksetscope: Clusterversions:- name: v1schema:openAPIV3Schema:description: GlobalNetworkSet contains a set of arbitrary IP sub-networks/CIDRsthat share labels to allow rules to refer to them via selectors. The labelsof GlobalNetworkSet are not namespaced.properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: GlobalNetworkSetSpec contains the specification for a NetworkSetresource.properties:nets:description: The list of IP networks that belong to this set.items:type: stringtype: arraytype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: hostendpoints.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: HostEndpointlistKind: HostEndpointListplural: hostendpointssingular: hostendpointscope: Clusterversions:- name: v1schema:openAPIV3Schema:properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: HostEndpointSpec contains the specification for a HostEndpointresource.properties:expectedIPs:description: "The expected IP addresses (IPv4 and IPv6) of the endpoint.If \"InterfaceName\" is not present, Calico will look for an interfacematching any of the IPs in the list and apply policy to that. Note:\tWhen using the selector match criteria in an ingress or egresssecurity Policy \tor Profile, Calico converts the selector intoa set of IP addresses. For host \tendpoints, the ExpectedIPs fieldis used for that purpose. (If only the interface \tname is specified,Calico does not learn the IPs of the interface for use in match\tcriteria.)"items:type: stringtype: arrayinterfaceName:description: "Either \"*\", or the name of a specific Linux interfaceto apply policy to; or empty. \"*\" indicates that this HostEndpointgoverns all traffic to, from or through the default network namespaceof the host named by the \"Node\" field; entering and leaving thatnamespace via any interface, including those from/to non-host-networkedlocal workloads. \n If InterfaceName is not \"*\", this HostEndpointonly governs traffic that enters or leaves the host through thespecific interface named by InterfaceName, or - when InterfaceNameis empty - through the specific interface that has one of the IPsin ExpectedIPs. Therefore, when InterfaceName is empty, at leastone expected IP must be specified. Only external interfaces (suchas \"eth0\") are supported here; it isn't possible for a HostEndpointto protect traffic through a specific local workload interface.\n Note: Only some kinds of policy are implemented for \"*\" HostEndpoints;initially just pre-DNAT policy. Please check Calico documentationfor the latest position."type: stringnode:description: The node name identifying the Calico node instance.type: stringports:description: Ports contains the endpoint's named ports, which maybe referenced in security policy rules.items:properties:name:type: stringport:type: integerprotocol:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truerequired:- name- port- protocoltype: objecttype: arrayprofiles:description: A list of identifiers of security Profile objects thatapply to this endpoint. Each profile is applied in the order thatthey appear in this list. Profile rules are applied after the selector-basedsecurity policy.items:type: stringtype: arraytype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: ipamblocks.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: IPAMBlocklistKind: IPAMBlockListplural: ipamblockssingular: ipamblockscope: Clusterversions:- name: v1schema:openAPIV3Schema:properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: IPAMBlockSpec contains the specification for an IPAMBlockresource.properties:affinity:type: stringallocations:items:type: integer# TODO: This nullable is manually added in. We should update controller-gen# to handle []*int properly itself.nullable: truetype: arrayattributes:items:properties:handle_id:type: stringsecondary:additionalProperties:type: stringtype: objecttype: objecttype: arraycidr:type: stringdeleted:type: booleanstrictAffinity:type: booleanunallocated:items:type: integertype: arrayrequired:- allocations- attributes- cidr- strictAffinity- unallocatedtype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: ipamconfigs.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: IPAMConfiglistKind: IPAMConfigListplural: ipamconfigssingular: ipamconfigscope: Clusterversions:- name: v1schema:openAPIV3Schema:properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: IPAMConfigSpec contains the specification for an IPAMConfigresource.properties:autoAllocateBlocks:type: booleanmaxBlocksPerHost:description: MaxBlocksPerHost, if non-zero, is the max number of blocksthat can be affine to each host.type: integerstrictAffinity:type: booleanrequired:- autoAllocateBlocks- strictAffinitytype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: ipamhandles.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: IPAMHandlelistKind: IPAMHandleListplural: ipamhandlessingular: ipamhandlescope: Clusterversions:- name: v1schema:openAPIV3Schema:properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: IPAMHandleSpec contains the specification for an IPAMHandleresource.properties:block:additionalProperties:type: integertype: objectdeleted:type: booleanhandleID:type: stringrequired:- block- handleIDtype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: ippools.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: IPPoollistKind: IPPoolListplural: ippoolssingular: ippoolscope: Clusterversions:- name: v1schema:openAPIV3Schema:properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: IPPoolSpec contains the specification for an IPPool resource.properties:blockSize:description: The block size to use for IP address assignments fromthis pool. Defaults to 26 for IPv4 and 112 for IPv6.type: integercidr:description: The pool CIDR.type: stringdisabled:description: When disabled is true, Calico IPAM will not assign addressesfrom this pool.type: booleanipip:description: 'Deprecated: this field is only used for APIv1 backwardscompatibility. Setting this field is not allowed, this field isfor internal use only.'properties:enabled:description: When enabled is true, ipip tunneling will be usedto deliver packets to destinations within this pool.type: booleanmode:description: The IPIP mode. This can be one of "always" or "cross-subnet". Amode of "always" will also use IPIP tunneling for routing todestination IP addresses within this pool. A mode of "cross-subnet"will only use IPIP tunneling when the destination node is ona different subnet to the originating node. The default value(if not specified) is "always".type: stringtype: objectipipMode:description: Contains configuration for IPIP tunneling for this pool.If not specified, then this is defaulted to "Never" (i.e. IPIP tunnelingis disabled).type: stringnat-outgoing:description: 'Deprecated: this field is only used for APIv1 backwardscompatibility. Setting this field is not allowed, this field isfor internal use only.'type: booleannatOutgoing:description: When nat-outgoing is true, packets sent from Calico networkedcontainers in this pool to destinations outside of this pool willbe masqueraded.type: booleannodeSelector:description: Allows IPPool to allocate for a specific node by labelselector.type: stringvxlanMode:description: Contains configuration for VXLAN tunneling for this pool.If not specified, then this is defaulted to "Never" (i.e. VXLANtunneling is disabled).type: stringrequired:- cidrtype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: kubecontrollersconfigurations.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: KubeControllersConfigurationlistKind: KubeControllersConfigurationListplural: kubecontrollersconfigurationssingular: kubecontrollersconfigurationscope: Clusterversions:- name: v1schema:openAPIV3Schema:properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: KubeControllersConfigurationSpec contains the values of theKubernetes controllers configuration.properties:controllers:description: Controllers enables and configures individual Kubernetescontrollersproperties:namespace:description: Namespace enables and configures the namespace controller.Enabled by default, set to nil to disable.properties:reconcilerPeriod:description: 'ReconcilerPeriod is the period to perform reconciliationwith the Calico datastore. [Default: 5m]'type: stringtype: objectnode:description: Node enables and configures the node controller.Enabled by default, set to nil to disable.properties:hostEndpoint:description: HostEndpoint controls syncing nodes to host endpoints.Disabled by default, set to nil to disable.properties:autoCreate:description: 'AutoCreate enables automatic creation ofhost endpoints for every node. [Default: Disabled]'type: stringtype: objectreconcilerPeriod:description: 'ReconcilerPeriod is the period to perform reconciliationwith the Calico datastore. [Default: 5m]'type: stringsyncLabels:description: 'SyncLabels controls whether to copy Kubernetesnode labels to Calico nodes. [Default: Enabled]'type: stringtype: objectpolicy:description: Policy enables and configures the policy controller.Enabled by default, set to nil to disable.properties:reconcilerPeriod:description: 'ReconcilerPeriod is the period to perform reconciliationwith the Calico datastore. [Default: 5m]'type: stringtype: objectserviceAccount:description: ServiceAccount enables and configures the serviceaccount controller. Enabled by default, set to nil to disable.properties:reconcilerPeriod:description: 'ReconcilerPeriod is the period to perform reconciliationwith the Calico datastore. [Default: 5m]'type: stringtype: objectworkloadEndpoint:description: WorkloadEndpoint enables and configures the workloadendpoint controller. Enabled by default, set to nil to disable.properties:reconcilerPeriod:description: 'ReconcilerPeriod is the period to perform reconciliationwith the Calico datastore. [Default: 5m]'type: stringtype: objecttype: objectetcdV3CompactionPeriod:description: 'EtcdV3CompactionPeriod is the period between etcdv3compaction requests. Set to 0 to disable. [Default: 10m]'type: stringhealthChecks:description: 'HealthChecks enables or disables support for healthchecks [Default: Enabled]'type: stringlogSeverityScreen:description: 'LogSeverityScreen is the log severity above which logsare sent to the stdout. [Default: Info]'type: stringprometheusMetricsPort:description: 'PrometheusMetricsPort is the TCP port that the Prometheusmetrics server should bind to. Set to 0 to disable. [Default: 9094]'type: integerrequired:- controllerstype: objectstatus:description: KubeControllersConfigurationStatus represents the statusof the configuration. It's useful for admins to be able to see the actualconfig that was applied, which can be modified by environment variableson the kube-controllers process.properties:environmentVars:additionalProperties:type: stringdescription: EnvironmentVars contains the environment variables onthe kube-controllers that influenced the RunningConfig.type: objectrunningConfig:description: RunningConfig contains the effective config that is runningin the kube-controllers pod, after merging the API resource withany environment variables.properties:controllers:description: Controllers enables and configures individual Kubernetescontrollersproperties:namespace:description: Namespace enables and configures the namespacecontroller. Enabled by default, set to nil to disable.properties:reconcilerPeriod:description: 'ReconcilerPeriod is the period to performreconciliation with the Calico datastore. [Default:5m]'type: stringtype: objectnode:description: Node enables and configures the node controller.Enabled by default, set to nil to disable.properties:hostEndpoint:description: HostEndpoint controls syncing nodes to hostendpoints. Disabled by default, set to nil to disable.properties:autoCreate:description: 'AutoCreate enables automatic creationof host endpoints for every node. [Default: Disabled]'type: stringtype: objectreconcilerPeriod:description: 'ReconcilerPeriod is the period to performreconciliation with the Calico datastore. [Default:5m]'type: stringsyncLabels:description: 'SyncLabels controls whether to copy Kubernetesnode labels to Calico nodes. [Default: Enabled]'type: stringtype: objectpolicy:description: Policy enables and configures the policy controller.Enabled by default, set to nil to disable.properties:reconcilerPeriod:description: 'ReconcilerPeriod is the period to performreconciliation with the Calico datastore. [Default:5m]'type: stringtype: objectserviceAccount:description: ServiceAccount enables and configures the serviceaccount controller. Enabled by default, set to nil to disable.properties:reconcilerPeriod:description: 'ReconcilerPeriod is the period to performreconciliation with the Calico datastore. [Default:5m]'type: stringtype: objectworkloadEndpoint:description: WorkloadEndpoint enables and configures the workloadendpoint controller. Enabled by default, set to nil to disable.properties:reconcilerPeriod:description: 'ReconcilerPeriod is the period to performreconciliation with the Calico datastore. [Default:5m]'type: stringtype: objecttype: objectetcdV3CompactionPeriod:description: 'EtcdV3CompactionPeriod is the period between etcdv3compaction requests. Set to 0 to disable. [Default: 10m]'type: stringhealthChecks:description: 'HealthChecks enables or disables support for healthchecks [Default: Enabled]'type: stringlogSeverityScreen:description: 'LogSeverityScreen is the log severity above whichlogs are sent to the stdout. [Default: Info]'type: stringprometheusMetricsPort:description: 'PrometheusMetricsPort is the TCP port that the Prometheusmetrics server should bind to. Set to 0 to disable. [Default:9094]'type: integerrequired:- controllerstype: objecttype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: networkpolicies.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: NetworkPolicylistKind: NetworkPolicyListplural: networkpoliciessingular: networkpolicyscope: Namespacedversions:- name: v1schema:openAPIV3Schema:properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:properties:egress:description: The ordered set of egress rules. Each rule containsa set of packet match criteria and a corresponding action to apply.items:description: "A Rule encapsulates a set of match criteria and anaction. Both selector-based security Policy and security Profilesreference rules - separated out as a list of rules for both ingressand egress packet matching. \n Each positive match criteria hasa negated version, prefixed with \"Not\". All the match criteriawithin a rule must be satisfied for a packet to match. A singlerule can contain the positive and negative version of a matchand both must be satisfied for the rule to match."properties:action:type: stringdestination:description: Destination contains the match criteria that applyto destination entity.properties:namespaceSelector:description: "NamespaceSelector is an optional field thatcontains a selector expression. Only traffic that originatesfrom (or terminates at) endpoints within the selectednamespaces will be matched. When both NamespaceSelectorand Selector are defined on the same rule, then only workloadendpoints that are matched by both selectors will be selectedby the rule. \n For NetworkPolicy, an empty NamespaceSelectorimplies that the Selector is limited to selecting onlyworkload endpoints in the same namespace as the NetworkPolicy.\n For NetworkPolicy, `global()` NamespaceSelector impliesthat the Selector is limited to selecting only GlobalNetworkSetor HostEndpoint. \n For GlobalNetworkPolicy, an emptyNamespaceSelector implies the Selector applies to workloadendpoints across all namespaces."type: stringnets:description: Nets is an optional field that restricts therule to only apply to traffic that originates from (orterminates at) IP addresses in any of the given subnets.items:type: stringtype: arraynotNets:description: NotNets is the negated version of the Netsfield.items:type: stringtype: arraynotPorts:description: NotPorts is the negated version of the Portsfield. Since only some protocols have ports, if any portsare specified it requires the Protocol match in the Ruleto be set to "TCP" or "UDP".items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arraynotSelector:description: NotSelector is the negated version of the Selectorfield. See Selector field for subtleties with negatedselectors.type: stringports:description: "Ports is an optional field that restrictsthe rule to only apply to traffic that has a source (destination)port that matches one of these ranges/values. This valueis a list of integers or strings that represent rangesof ports. \n Since only some protocols have ports, ifany ports are specified it requires the Protocol matchin the Rule to be set to \"TCP\" or \"UDP\"."items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arrayselector:description: "Selector is an optional field that containsa selector expression (see Policy for sample syntax).\ Only traffic that originates from (terminates at) endpointsmatching the selector will be matched. \n Note that: inaddition to the negated version of the Selector (see NotSelectorbelow), the selector expression syntax itself supportsnegation. The two types of negation are subtly different.One negates the set of matched endpoints, the other negatesthe whole match: \n \tSelector = \"!has(my_label)\" matchespackets that are from other Calico-controlled \tendpointsthat do not have the label \"my_label\". \n \tNotSelector= \"has(my_label)\" matches packets that are not fromCalico-controlled \tendpoints that do have the label \"my_label\".\n The effect is that the latter will accept packets fromnon-Calico sources whereas the former is limited to packetsfrom Calico-controlled endpoints."type: stringserviceAccounts:description: ServiceAccounts is an optional field that restrictsthe rule to only apply to traffic that originates from(or terminates at) a pod running as a matching serviceaccount.properties:names:description: Names is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount whose name is in the list.items:type: stringtype: arrayselector:description: Selector is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount that matches the given label selector. Ifboth Names and Selector are specified then they areAND'ed.type: stringtype: objecttype: objecthttp:description: HTTP contains match criteria that apply to HTTPrequests.properties:methods:description: Methods is an optional field that restrictsthe rule to apply only to HTTP requests that use one ofthe listed HTTP Methods (e.g. GET, PUT, etc.) Multiplemethods are OR'd together.items:type: stringtype: arraypaths:description: 'Paths is an optional field that restrictsthe rule to apply to HTTP requests that use one of thelisted HTTP Paths. Multiple paths are OR''d together.e.g: - exact: /foo - prefix: /bar NOTE: Each entry mayONLY specify either a `exact` or a `prefix` match. Thevalidator will check for it.'items:description: 'HTTPPath specifies an HTTP path to match.It may be either of the form: exact: <path>: which matchesthe path exactly or prefix: <path-prefix>: which matchesthe path prefix'properties:exact:type: stringprefix:type: stringtype: objecttype: arraytype: objecticmp:description: ICMP is an optional field that restricts the ruleto apply to a specific type and code of ICMP traffic. Thisshould only be specified if the Protocol field is set to "ICMP"or "ICMPv6".properties:code:description: Match on a specific ICMP code. If specified,the Type value must also be specified. This is a technicallimitation imposed by the kernel's iptables firewall,which Calico uses to enforce the rule.type: integertype:description: Match on a specific ICMP type. For examplea value of 8 refers to ICMP Echo Request (i.e. pings).type: integertype: objectipVersion:description: IPVersion is an optional field that restricts therule to only match a specific IP version.type: integermetadata:description: Metadata contains additional information for thisruleproperties:annotations:additionalProperties:type: stringdescription: Annotations is a set of key value pairs thatgive extra information about the ruletype: objecttype: objectnotICMP:description: NotICMP is the negated version of the ICMP field.properties:code:description: Match on a specific ICMP code. If specified,the Type value must also be specified. This is a technicallimitation imposed by the kernel's iptables firewall,which Calico uses to enforce the rule.type: integertype:description: Match on a specific ICMP type. For examplea value of 8 refers to ICMP Echo Request (i.e. pings).type: integertype: objectnotProtocol:anyOf:- type: integer- type: stringdescription: NotProtocol is the negated version of the Protocolfield.pattern: ^.*x-kubernetes-int-or-string: trueprotocol:anyOf:- type: integer- type: stringdescription: "Protocol is an optional field that restricts therule to only apply to traffic of a specific IP protocol. Requiredif any of the EntityRules contain Ports (because ports onlyapply to certain protocols). \n Must be one of these stringvalues: \"TCP\", \"UDP\", \"ICMP\", \"ICMPv6\", \"SCTP\",\"UDPLite\" or an integer in the range 1-255."pattern: ^.*x-kubernetes-int-or-string: truesource:description: Source contains the match criteria that apply tosource entity.properties:namespaceSelector:description: "NamespaceSelector is an optional field thatcontains a selector expression. Only traffic that originatesfrom (or terminates at) endpoints within the selectednamespaces will be matched. When both NamespaceSelectorand Selector are defined on the same rule, then only workloadendpoints that are matched by both selectors will be selectedby the rule. \n For NetworkPolicy, an empty NamespaceSelectorimplies that the Selector is limited to selecting onlyworkload endpoints in the same namespace as the NetworkPolicy.\n For NetworkPolicy, `global()` NamespaceSelector impliesthat the Selector is limited to selecting only GlobalNetworkSetor HostEndpoint. \n For GlobalNetworkPolicy, an emptyNamespaceSelector implies the Selector applies to workloadendpoints across all namespaces."type: stringnets:description: Nets is an optional field that restricts therule to only apply to traffic that originates from (orterminates at) IP addresses in any of the given subnets.items:type: stringtype: arraynotNets:description: NotNets is the negated version of the Netsfield.items:type: stringtype: arraynotPorts:description: NotPorts is the negated version of the Portsfield. Since only some protocols have ports, if any portsare specified it requires the Protocol match in the Ruleto be set to "TCP" or "UDP".items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arraynotSelector:description: NotSelector is the negated version of the Selectorfield. See Selector field for subtleties with negatedselectors.type: stringports:description: "Ports is an optional field that restrictsthe rule to only apply to traffic that has a source (destination)port that matches one of these ranges/values. This valueis a list of integers or strings that represent rangesof ports. \n Since only some protocols have ports, ifany ports are specified it requires the Protocol matchin the Rule to be set to \"TCP\" or \"UDP\"."items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arrayselector:description: "Selector is an optional field that containsa selector expression (see Policy for sample syntax).\ Only traffic that originates from (terminates at) endpointsmatching the selector will be matched. \n Note that: inaddition to the negated version of the Selector (see NotSelectorbelow), the selector expression syntax itself supportsnegation. The two types of negation are subtly different.One negates the set of matched endpoints, the other negatesthe whole match: \n \tSelector = \"!has(my_label)\" matchespackets that are from other Calico-controlled \tendpointsthat do not have the label \"my_label\". \n \tNotSelector= \"has(my_label)\" matches packets that are not fromCalico-controlled \tendpoints that do have the label \"my_label\".\n The effect is that the latter will accept packets fromnon-Calico sources whereas the former is limited to packetsfrom Calico-controlled endpoints."type: stringserviceAccounts:description: ServiceAccounts is an optional field that restrictsthe rule to only apply to traffic that originates from(or terminates at) a pod running as a matching serviceaccount.properties:names:description: Names is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount whose name is in the list.items:type: stringtype: arrayselector:description: Selector is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount that matches the given label selector. Ifboth Names and Selector are specified then they areAND'ed.type: stringtype: objecttype: objectrequired:- actiontype: objecttype: arrayingress:description: The ordered set of ingress rules. Each rule containsa set of packet match criteria and a corresponding action to apply.items:description: "A Rule encapsulates a set of match criteria and anaction. Both selector-based security Policy and security Profilesreference rules - separated out as a list of rules for both ingressand egress packet matching. \n Each positive match criteria hasa negated version, prefixed with \"Not\". All the match criteriawithin a rule must be satisfied for a packet to match. A singlerule can contain the positive and negative version of a matchand both must be satisfied for the rule to match."properties:action:type: stringdestination:description: Destination contains the match criteria that applyto destination entity.properties:namespaceSelector:description: "NamespaceSelector is an optional field thatcontains a selector expression. Only traffic that originatesfrom (or terminates at) endpoints within the selectednamespaces will be matched. When both NamespaceSelectorand Selector are defined on the same rule, then only workloadendpoints that are matched by both selectors will be selectedby the rule. \n For NetworkPolicy, an empty NamespaceSelectorimplies that the Selector is limited to selecting onlyworkload endpoints in the same namespace as the NetworkPolicy.\n For NetworkPolicy, `global()` NamespaceSelector impliesthat the Selector is limited to selecting only GlobalNetworkSetor HostEndpoint. \n For GlobalNetworkPolicy, an emptyNamespaceSelector implies the Selector applies to workloadendpoints across all namespaces."type: stringnets:description: Nets is an optional field that restricts therule to only apply to traffic that originates from (orterminates at) IP addresses in any of the given subnets.items:type: stringtype: arraynotNets:description: NotNets is the negated version of the Netsfield.items:type: stringtype: arraynotPorts:description: NotPorts is the negated version of the Portsfield. Since only some protocols have ports, if any portsare specified it requires the Protocol match in the Ruleto be set to "TCP" or "UDP".items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arraynotSelector:description: NotSelector is the negated version of the Selectorfield. See Selector field for subtleties with negatedselectors.type: stringports:description: "Ports is an optional field that restrictsthe rule to only apply to traffic that has a source (destination)port that matches one of these ranges/values. This valueis a list of integers or strings that represent rangesof ports. \n Since only some protocols have ports, ifany ports are specified it requires the Protocol matchin the Rule to be set to \"TCP\" or \"UDP\"."items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arrayselector:description: "Selector is an optional field that containsa selector expression (see Policy for sample syntax).\ Only traffic that originates from (terminates at) endpointsmatching the selector will be matched. \n Note that: inaddition to the negated version of the Selector (see NotSelectorbelow), the selector expression syntax itself supportsnegation. The two types of negation are subtly different.One negates the set of matched endpoints, the other negatesthe whole match: \n \tSelector = \"!has(my_label)\" matchespackets that are from other Calico-controlled \tendpointsthat do not have the label \"my_label\". \n \tNotSelector= \"has(my_label)\" matches packets that are not fromCalico-controlled \tendpoints that do have the label \"my_label\".\n The effect is that the latter will accept packets fromnon-Calico sources whereas the former is limited to packetsfrom Calico-controlled endpoints."type: stringserviceAccounts:description: ServiceAccounts is an optional field that restrictsthe rule to only apply to traffic that originates from(or terminates at) a pod running as a matching serviceaccount.properties:names:description: Names is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount whose name is in the list.items:type: stringtype: arrayselector:description: Selector is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount that matches the given label selector. Ifboth Names and Selector are specified then they areAND'ed.type: stringtype: objecttype: objecthttp:description: HTTP contains match criteria that apply to HTTPrequests.properties:methods:description: Methods is an optional field that restrictsthe rule to apply only to HTTP requests that use one ofthe listed HTTP Methods (e.g. GET, PUT, etc.) Multiplemethods are OR'd together.items:type: stringtype: arraypaths:description: 'Paths is an optional field that restrictsthe rule to apply to HTTP requests that use one of thelisted HTTP Paths. Multiple paths are OR''d together.e.g: - exact: /foo - prefix: /bar NOTE: Each entry mayONLY specify either a `exact` or a `prefix` match. Thevalidator will check for it.'items:description: 'HTTPPath specifies an HTTP path to match.It may be either of the form: exact: <path>: which matchesthe path exactly or prefix: <path-prefix>: which matchesthe path prefix'properties:exact:type: stringprefix:type: stringtype: objecttype: arraytype: objecticmp:description: ICMP is an optional field that restricts the ruleto apply to a specific type and code of ICMP traffic. Thisshould only be specified if the Protocol field is set to "ICMP"or "ICMPv6".properties:code:description: Match on a specific ICMP code. If specified,the Type value must also be specified. This is a technicallimitation imposed by the kernel's iptables firewall,which Calico uses to enforce the rule.type: integertype:description: Match on a specific ICMP type. For examplea value of 8 refers to ICMP Echo Request (i.e. pings).type: integertype: objectipVersion:description: IPVersion is an optional field that restricts therule to only match a specific IP version.type: integermetadata:description: Metadata contains additional information for thisruleproperties:annotations:additionalProperties:type: stringdescription: Annotations is a set of key value pairs thatgive extra information about the ruletype: objecttype: objectnotICMP:description: NotICMP is the negated version of the ICMP field.properties:code:description: Match on a specific ICMP code. If specified,the Type value must also be specified. This is a technicallimitation imposed by the kernel's iptables firewall,which Calico uses to enforce the rule.type: integertype:description: Match on a specific ICMP type. For examplea value of 8 refers to ICMP Echo Request (i.e. pings).type: integertype: objectnotProtocol:anyOf:- type: integer- type: stringdescription: NotProtocol is the negated version of the Protocolfield.pattern: ^.*x-kubernetes-int-or-string: trueprotocol:anyOf:- type: integer- type: stringdescription: "Protocol is an optional field that restricts therule to only apply to traffic of a specific IP protocol. Requiredif any of the EntityRules contain Ports (because ports onlyapply to certain protocols). \n Must be one of these stringvalues: \"TCP\", \"UDP\", \"ICMP\", \"ICMPv6\", \"SCTP\",\"UDPLite\" or an integer in the range 1-255."pattern: ^.*x-kubernetes-int-or-string: truesource:description: Source contains the match criteria that apply tosource entity.properties:namespaceSelector:description: "NamespaceSelector is an optional field thatcontains a selector expression. Only traffic that originatesfrom (or terminates at) endpoints within the selectednamespaces will be matched. When both NamespaceSelectorand Selector are defined on the same rule, then only workloadendpoints that are matched by both selectors will be selectedby the rule. \n For NetworkPolicy, an empty NamespaceSelectorimplies that the Selector is limited to selecting onlyworkload endpoints in the same namespace as the NetworkPolicy.\n For NetworkPolicy, `global()` NamespaceSelector impliesthat the Selector is limited to selecting only GlobalNetworkSetor HostEndpoint. \n For GlobalNetworkPolicy, an emptyNamespaceSelector implies the Selector applies to workloadendpoints across all namespaces."type: stringnets:description: Nets is an optional field that restricts therule to only apply to traffic that originates from (orterminates at) IP addresses in any of the given subnets.items:type: stringtype: arraynotNets:description: NotNets is the negated version of the Netsfield.items:type: stringtype: arraynotPorts:description: NotPorts is the negated version of the Portsfield. Since only some protocols have ports, if any portsare specified it requires the Protocol match in the Ruleto be set to "TCP" or "UDP".items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arraynotSelector:description: NotSelector is the negated version of the Selectorfield. See Selector field for subtleties with negatedselectors.type: stringports:description: "Ports is an optional field that restrictsthe rule to only apply to traffic that has a source (destination)port that matches one of these ranges/values. This valueis a list of integers or strings that represent rangesof ports. \n Since only some protocols have ports, ifany ports are specified it requires the Protocol matchin the Rule to be set to \"TCP\" or \"UDP\"."items:anyOf:- type: integer- type: stringpattern: ^.*x-kubernetes-int-or-string: truetype: arrayselector:description: "Selector is an optional field that containsa selector expression (see Policy for sample syntax).\ Only traffic that originates from (terminates at) endpointsmatching the selector will be matched. \n Note that: inaddition to the negated version of the Selector (see NotSelectorbelow), the selector expression syntax itself supportsnegation. The two types of negation are subtly different.One negates the set of matched endpoints, the other negatesthe whole match: \n \tSelector = \"!has(my_label)\" matchespackets that are from other Calico-controlled \tendpointsthat do not have the label \"my_label\". \n \tNotSelector= \"has(my_label)\" matches packets that are not fromCalico-controlled \tendpoints that do have the label \"my_label\".\n The effect is that the latter will accept packets fromnon-Calico sources whereas the former is limited to packetsfrom Calico-controlled endpoints."type: stringserviceAccounts:description: ServiceAccounts is an optional field that restrictsthe rule to only apply to traffic that originates from(or terminates at) a pod running as a matching serviceaccount.properties:names:description: Names is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount whose name is in the list.items:type: stringtype: arrayselector:description: Selector is an optional field that restrictsthe rule to only apply to traffic that originatesfrom (or terminates at) a pod running as a serviceaccount that matches the given label selector. Ifboth Names and Selector are specified then they areAND'ed.type: stringtype: objecttype: objectrequired:- actiontype: objecttype: arrayorder:description: Order is an optional field that specifies the order inwhich the policy is applied. Policies with higher "order" are appliedafter those with lower order. If the order is omitted, it may beconsidered to be "infinite" - i.e. the policy will be applied last. Policieswith identical order will be applied in alphanumerical order basedon the Policy "Name".type: numberselector:description: "The selector is an expression used to pick pick outthe endpoints that the policy should be applied to. \n Selectorexpressions follow this syntax: \n \tlabel == \"string_literal\"\ -> comparison, e.g. my_label == \"foo bar\" \tlabel != \"string_literal\"\ -> not equal; also matches if label is not present \tlabel in{ \"a\", \"b\", \"c\", ... } -> true if the value of label X isone of \"a\", \"b\", \"c\" \tlabel not in { \"a\", \"b\", \"c\",... } -> true if the value of label X is not one of \"a\", \"b\",\"c\" \thas(label_name) -> True if that label is present \t! expr-> negation of expr \texpr && expr -> Short-circuit and \texpr|| expr -> Short-circuit or \t( expr ) -> parens for grouping \tall()or the empty selector -> matches all endpoints. \n Label names areallowed to contain alphanumerics, -, _ and /. String literals aremore permissive but they do not support escape characters. \n Examples(with made-up labels): \n \ttype == \"webserver\" && deployment== \"prod\" \ttype in {\"frontend\", \"backend\"} \tdeployment !=\"dev\" \t! has(label_name)"type: stringserviceAccountSelector:description: ServiceAccountSelector is an optional field for an expressionused to select a pod based on service accounts.type: stringtypes:description: "Types indicates whether this policy applies to ingress,or to egress, or to both. When not explicitly specified (and sothe value on creation is empty or nil), Calico defaults Types accordingto what Ingress and Egress are present in the policy. The defaultis: \n - [ PolicyTypeIngress ], if there are no Egress rules (includingthe case where there are also no Ingress rules) \n - [ PolicyTypeEgress], if there are Egress rules but no Ingress rules \n - [ PolicyTypeIngress,PolicyTypeEgress ], if there are both Ingress and Egress rules.\n When the policy is read back again, Types will always be oneof these values, never empty or nil."items:description: PolicyType enumerates the possible values of the PolicySpecTypes field.type: stringtype: arraytype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
apiVersion: apiextensions.k8s.io/v1
kind: CustomResourceDefinition
metadata:name: networksets.crd.projectcalico.org
spec:group: crd.projectcalico.orgnames:kind: NetworkSetlistKind: NetworkSetListplural: networksetssingular: networksetscope: Namespacedversions:- name: v1schema:openAPIV3Schema:description: NetworkSet is the Namespaced-equivalent of the GlobalNetworkSet.properties:apiVersion:description: 'APIVersion defines the versioned schema of this representationof an object. Servers should convert recognized schemas to the latestinternal value, and may reject unrecognized values. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#resources'type: stringkind:description: 'Kind is a string value representing the REST resource thisobject represents. Servers may infer this from the endpoint the clientsubmits requests to. Cannot be updated. In CamelCase. More info: https://git.k8s.io/community/contributors/devel/sig-architecture/api-conventions.md#types-kinds'type: stringmetadata:type: objectspec:description: NetworkSetSpec contains the specification for a NetworkSetresource.properties:nets:description: The list of IP networks that belong to this set.items:type: stringtype: arraytype: objecttype: objectserved: truestorage: true
status:acceptedNames:kind: ""plural: ""conditions: []storedVersions: []---
---
# Source: calico/templates/calico-kube-controllers-rbac.yaml# Include a clusterrole for the kube-controllers component,
# and bind it to the calico-kube-controllers serviceaccount.
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:name: calico-kube-controllers
rules:# Nodes are watched to monitor for deletions.- apiGroups: [""]resources:- nodesverbs:- watch- list- get# Pods are queried to check for existence.- apiGroups: [""]resources:- podsverbs:- get# IPAM resources are manipulated when nodes are deleted.- apiGroups: ["crd.projectcalico.org"]resources:- ippoolsverbs:- list- apiGroups: ["crd.projectcalico.org"]resources:- blockaffinities- ipamblocks- ipamhandlesverbs:- get- list- create- update- delete- watch# kube-controllers manages hostendpoints.- apiGroups: ["crd.projectcalico.org"]resources:- hostendpointsverbs:- get- list- create- update- delete# Needs access to update clusterinformations.- apiGroups: ["crd.projectcalico.org"]resources:- clusterinformationsverbs:- get- create- update# KubeControllersConfiguration is where it gets its config- apiGroups: ["crd.projectcalico.org"]resources:- kubecontrollersconfigurationsverbs:# read its own config- get# create a default if none exists- create# update status- update# watch for changes- watch
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:name: calico-kube-controllers
roleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: calico-kube-controllers
subjects:
- kind: ServiceAccountname: calico-kube-controllersnamespace: kube-system
------
# Source: calico/templates/calico-node-rbac.yaml
# Include a clusterrole for the calico-node DaemonSet,
# and bind it to the calico-node serviceaccount.
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:name: calico-node
rules:# The CNI plugin needs to get pods, nodes, and namespaces.- apiGroups: [""]resources:- pods- nodes- namespacesverbs:- get- apiGroups: [""]resources:- endpoints- servicesverbs:# Used to discover service IPs for advertisement.- watch- list# Used to discover Typhas.- get# Pod CIDR auto-detection on kubeadm needs access to config maps.- apiGroups: [""]resources:- configmapsverbs:- get- apiGroups: [""]resources:- nodes/statusverbs:# Needed for clearing NodeNetworkUnavailable flag.- patch# Calico stores some configuration information in node annotations.- update# Watch for changes to Kubernetes NetworkPolicies.- apiGroups: ["networking.k8s.io"]resources:- networkpoliciesverbs:- watch- list# Used by Calico for policy information.- apiGroups: [""]resources:- pods- namespaces- serviceaccountsverbs:- list- watch# The CNI plugin patches pods/status.- apiGroups: [""]resources:- pods/statusverbs:- patch# Calico monitors various CRDs for config.- apiGroups: ["crd.projectcalico.org"]resources:- globalfelixconfigs- felixconfigurations- bgppeers- globalbgpconfigs- bgpconfigurations- ippools- ipamblocks- globalnetworkpolicies- globalnetworksets- networkpolicies- networksets- clusterinformations- hostendpoints- blockaffinitiesverbs:- get- list- watch# Calico must create and update some CRDs on startup.- apiGroups: ["crd.projectcalico.org"]resources:- ippools- felixconfigurations- clusterinformationsverbs:- create- update# Calico stores some configuration information on the node.- apiGroups: [""]resources:- nodesverbs:- get- list- watch# These permissions are only required for upgrade from v2.6, and can# be removed after upgrade or on fresh installations.- apiGroups: ["crd.projectcalico.org"]resources:- bgpconfigurations- bgppeersverbs:- create- update# These permissions are required for Calico CNI to perform IPAM allocations.- apiGroups: ["crd.projectcalico.org"]resources:- blockaffinities- ipamblocks- ipamhandlesverbs:- get- list- create- update- delete- apiGroups: ["crd.projectcalico.org"]resources:- ipamconfigsverbs:- get# Block affinities must also be watchable by confd for route aggregation.- apiGroups: ["crd.projectcalico.org"]resources:- blockaffinitiesverbs:- watch# The Calico IPAM migration needs to get daemonsets. These permissions can be# removed if not upgrading from an installation using host-local IPAM.- apiGroups: ["apps"]resources:- daemonsetsverbs:- get---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:name: calico-node
roleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: calico-node
subjects:
- kind: ServiceAccountname: calico-nodenamespace: kube-system---
# Source: calico/templates/calico-node.yaml
# This manifest installs the calico-node container, as well
# as the CNI plugins and network config on
# each master and worker node in a Kubernetes cluster.
kind: DaemonSet
apiVersion: apps/v1
metadata:name: calico-nodenamespace: kube-systemlabels:k8s-app: calico-node
spec:selector:matchLabels:k8s-app: calico-nodeupdateStrategy:type: RollingUpdaterollingUpdate:maxUnavailable: 1template:metadata:labels:k8s-app: calico-nodespec:nodeSelector:kubernetes.io/os: linuxhostNetwork: truetolerations:# Make sure calico-node gets scheduled on all nodes.- effect: NoScheduleoperator: Exists# Mark the pod as a critical add-on for rescheduling.- key: CriticalAddonsOnlyoperator: Exists- effect: NoExecuteoperator: ExistsserviceAccountName: calico-node# Minimize downtime during a rolling upgrade or deletion; tell Kubernetes to do a "force# deletion": https://kubernetes.io/docs/concepts/workloads/pods/pod/#termination-of-pods.terminationGracePeriodSeconds: 0priorityClassName: system-node-criticalinitContainers:# This container performs upgrade from host-local IPAM to calico-ipam.# It can be deleted if this is a fresh installation, or if you have already# upgraded to use calico-ipam.- name: upgrade-ipamimage: docker.io/calico/cni:v3.18.0command: ["/opt/cni/bin/calico-ipam", "-upgrade"]envFrom:- configMapRef:# Allow KUBERNETES_SERVICE_HOST and KUBERNETES_SERVICE_PORT to be overridden for eBPF mode.name: kubernetes-services-endpointoptional: trueenv:- name: KUBERNETES_NODE_NAMEvalueFrom:fieldRef:fieldPath: spec.nodeName- name: CALICO_NETWORKING_BACKENDvalueFrom:configMapKeyRef:name: calico-configkey: calico_backendvolumeMounts:- mountPath: /var/lib/cni/networksname: host-local-net-dir- mountPath: /host/opt/cni/binname: cni-bin-dirsecurityContext:privileged: true# This container installs the CNI binaries# and CNI network config file on each node.- name: install-cniimage: docker.io/calico/cni:v3.18.0command: ["/opt/cni/bin/install"]envFrom:- configMapRef:# Allow KUBERNETES_SERVICE_HOST and KUBERNETES_SERVICE_PORT to be overridden for eBPF mode.name: kubernetes-services-endpointoptional: trueenv:# Name of the CNI config file to create.- name: CNI_CONF_NAMEvalue: "10-calico.conflist"# The CNI network config to install on each node.- name: CNI_NETWORK_CONFIGvalueFrom:configMapKeyRef:name: calico-configkey: cni_network_config# Set the hostname based on the k8s node name.- name: KUBERNETES_NODE_NAMEvalueFrom:fieldRef:fieldPath: spec.nodeName# CNI MTU Config variable- name: CNI_MTUvalueFrom:configMapKeyRef:name: calico-configkey: veth_mtu# Prevents the container from sleeping forever.- name: SLEEPvalue: "false"volumeMounts:- mountPath: /host/opt/cni/binname: cni-bin-dir- mountPath: /host/etc/cni/net.dname: cni-net-dirsecurityContext:privileged: true# Adds a Flex Volume Driver that creates a per-pod Unix Domain Socket to allow Dikastes# to communicate with Felix over the Policy Sync API.- name: flexvol-driverimage: docker.io/calico/pod2daemon-flexvol:v3.18.0volumeMounts:- name: flexvol-driver-hostmountPath: /host/driversecurityContext:privileged: truecontainers:# Runs calico-node container on each Kubernetes node. This# container programs network policy and routes on each# host.- name: calico-nodeimage: docker.io/calico/node:v3.18.0envFrom:- configMapRef:# Allow KUBERNETES_SERVICE_HOST and KUBERNETES_SERVICE_PORT to be overridden for eBPF mode.name: kubernetes-services-endpointoptional: trueenv:# Use Kubernetes API as the backing datastore.- name: DATASTORE_TYPEvalue: "kubernetes"# Wait for the datastore.- name: WAIT_FOR_DATASTOREvalue: "true"# Set based on the k8s node name.- name: NODENAMEvalueFrom:fieldRef:fieldPath: spec.nodeName# Choose the backend to use.- name: CALICO_NETWORKING_BACKENDvalueFrom:configMapKeyRef:name: calico-configkey: calico_backend# Cluster type to identify the deployment type- name: CLUSTER_TYPEvalue: "k8s,bgp"# Auto-detect the BGP IP address.- name: IPvalue: "autodetect"# Enable IPIP- name: CALICO_IPV4POOL_IPIPvalue: "Always"# Enable or Disable VXLAN on the default IP pool.- name: CALICO_IPV4POOL_VXLANvalue: "Never"# Set MTU for tunnel device used if ipip is enabled- name: FELIX_IPINIPMTUvalueFrom:configMapKeyRef:name: calico-configkey: veth_mtu# Set MTU for the VXLAN tunnel device.- name: FELIX_VXLANMTUvalueFrom:configMapKeyRef:name: calico-configkey: veth_mtu# Set MTU for the Wireguard tunnel device.- name: FELIX_WIREGUARDMTUvalueFrom:configMapKeyRef:name: calico-configkey: veth_mtu# The default IPv4 pool to create on startup if none exists. Pod IPs will be# chosen from this range. Changing this value after installation will have# no effect. This should fall within `--cluster-cidr`.# - name: CALICO_IPV4POOL_CIDR# value: "192.168.0.0/16"# Disable file logging so `kubectl logs` works.- name: CALICO_DISABLE_FILE_LOGGINGvalue: "true"# Set Felix endpoint to host default action to ACCEPT.- name: FELIX_DEFAULTENDPOINTTOHOSTACTIONvalue: "ACCEPT"# Disable IPv6 on Kubernetes.- name: FELIX_IPV6SUPPORTvalue: "false"# Set Felix logging to "info"- name: FELIX_LOGSEVERITYSCREENvalue: "info"- name: FELIX_HEALTHENABLEDvalue: "true"securityContext:privileged: trueresources:requests:cpu: 250mlivenessProbe:exec:command:- /bin/calico-node- -felix-live- -bird-liveperiodSeconds: 10initialDelaySeconds: 10failureThreshold: 6readinessProbe:exec:command:- /bin/calico-node- -felix-ready- -bird-readyperiodSeconds: 10volumeMounts:- mountPath: /lib/modulesname: lib-modulesreadOnly: true- mountPath: /run/xtables.lockname: xtables-lockreadOnly: false- mountPath: /var/run/caliconame: var-run-calicoreadOnly: false- mountPath: /var/lib/caliconame: var-lib-calicoreadOnly: false- name: policysyncmountPath: /var/run/nodeagent# For eBPF mode, we need to be able to mount the BPF filesystem at /sys/fs/bpf so we mount in the# parent directory.- name: sysfsmountPath: /sys/fs/# Bidirectional means that, if we mount the BPF filesystem at /sys/fs/bpf it will propagate to the host.# If the host is known to mount that filesystem already then Bidirectional can be omitted.mountPropagation: Bidirectional- name: cni-log-dirmountPath: /var/log/calico/cnireadOnly: truevolumes:# Used by calico-node.- name: lib-moduleshostPath:path: /lib/modules- name: var-run-calicohostPath:path: /var/run/calico- name: var-lib-calicohostPath:path: /var/lib/calico- name: xtables-lockhostPath:path: /run/xtables.locktype: FileOrCreate- name: sysfshostPath:path: /sys/fs/type: DirectoryOrCreate# Used to install CNI.- name: cni-bin-dirhostPath:path: /opt/cni/bin- name: cni-net-dirhostPath:path: /etc/cni/net.d# Used to access CNI logs.- name: cni-log-dirhostPath:path: /var/log/calico/cni# Mount in the directory for host-local IPAM allocations. This is# used when upgrading from host-local to calico-ipam, and can be removed# if not using the upgrade-ipam init container.- name: host-local-net-dirhostPath:path: /var/lib/cni/networks# Used to create per-pod Unix Domain Sockets- name: policysynchostPath:type: DirectoryOrCreatepath: /var/run/nodeagent# Used to install Flex Volume Driver- name: flexvol-driver-hosthostPath:type: DirectoryOrCreatepath: /usr/libexec/kubernetes/kubelet-plugins/volume/exec/nodeagent~uds
---apiVersion: v1
kind: ServiceAccount
metadata:name: calico-nodenamespace: kube-system---
# Source: calico/templates/calico-kube-controllers.yaml
# See https://github.com/projectcalico/kube-controllers
apiVersion: apps/v1
kind: Deployment
metadata:name: calico-kube-controllersnamespace: kube-systemlabels:k8s-app: calico-kube-controllers
spec:# The controllers can only have a single active instance.replicas: 1selector:matchLabels:k8s-app: calico-kube-controllersstrategy:type: Recreatetemplate:metadata:name: calico-kube-controllersnamespace: kube-systemlabels:k8s-app: calico-kube-controllersspec:nodeSelector:kubernetes.io/os: linuxtolerations:# Mark the pod as a critical add-on for rescheduling.- key: CriticalAddonsOnlyoperator: Exists- key: node-role.kubernetes.io/mastereffect: NoScheduleserviceAccountName: calico-kube-controllerspriorityClassName: system-cluster-criticalcontainers:- name: calico-kube-controllersimage: docker.io/calico/kube-controllers:v3.18.0env:# Choose which controllers to run.- name: ENABLED_CONTROLLERSvalue: node- name: DATASTORE_TYPEvalue: kubernetesreadinessProbe:exec:command:- /usr/bin/check-status- -r---apiVersion: v1
kind: ServiceAccount
metadata:name: calico-kube-controllersnamespace: kube-system---# This manifest creates a Pod Disruption Budget for Controller to allow K8s Cluster Autoscaler to evictapiVersion: policy/v1beta1
kind: PodDisruptionBudget
metadata:name: calico-kube-controllersnamespace: kube-systemlabels:k8s-app: calico-kube-controllers
spec:maxUnavailable: 1selector:matchLabels:k8s-app: calico-kube-controllers---
# Source: calico/templates/calico-etcd-secrets.yaml---
# Source: calico/templates/calico-typha.yaml---
# Source: calico/templates/configure-canal.yaml[root@master1 ~]# kubectl apply -f calico.yaml
configmap/calico-config created
customresourcedefinition.apiextensions.k8s.io/bgpconfigurations.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/bgppeers.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/blockaffinities.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/clusterinformations.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/felixconfigurations.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/globalnetworkpolicies.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/globalnetworksets.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/hostendpoints.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/ipamblocks.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/ipamconfigs.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/ipamhandles.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/ippools.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/kubecontrollersconfigurations.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/networkpolicies.crd.projectcalico.org created
customresourcedefinition.apiextensions.k8s.io/networksets.crd.projectcalico.org created
clusterrole.rbac.authorization.k8s.io/calico-kube-controllers created
clusterrolebinding.rbac.authorization.k8s.io/calico-kube-controllers created
clusterrole.rbac.authorization.k8s.io/calico-node created
clusterrolebinding.rbac.authorization.k8s.io/calico-node created
daemonset.apps/calico-node created
serviceaccount/calico-node created
deployment.apps/calico-kube-controllers created
serviceaccount/calico-kube-controllers created
poddisruptionbudget.policy/calico-kube-controllers created
[root@master1 ~]# kubectl get pod -n kube-system
NAME READY STATUS RESTARTS AGE
calico-kube-controllers-6949477b58-hdfbw 1/1 Running 0 31s
calico-node-cgdbd 1/1 Running 0 31s
calico-node-gk8sq 1/1 Running 0 31s
calico-node-j2mtd 1/1 Running 0 31s
coredns-7f89b7bc75-4dk9p 1/1 Running 0 19m
coredns-7f89b7bc75-5ttpc 1/1 Running 0 19m
etcd-master1 1/1 Running 0 19m
kube-apiserver-master1 1/1 Running 0 19m
kube-controller-manager-master1 1/1 Running 0 19m
kube-proxy-l27p4 1/1 Running 0 15m
kube-proxy-z7xwj 1/1 Running 0 19m
kube-proxy-zc2hm 1/1 Running 0 11m
kube-scheduler-master1 1/1 Running 0 19m
再次查看集群状态
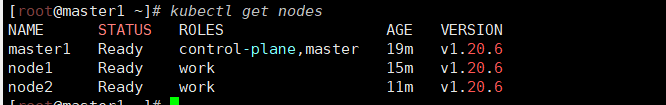
STATUS 状态是 Ready,说明 k8s 集群正常运行了。
8 测试在 k8s 创建 pod 是否可以正常访问网络
#把 busybox-1-28.tar.gz 上传到 node1、node2 节点,手动解压
[root@node1 ~]# docker load -i busybox-1-28.tar.gz
432b65032b94: Loading layer [==================================================>] 1.36MB/1.36MB
Loaded image: busybox:1.28
[root@node2 ~]# docker load -i busybox-1-28.tar.gz
432b65032b94: Loading layer [==================================================>] 1.36MB/1.36MB
Loaded image: busybox:1.28[root@master1 ~]# kubectl run busybox --image busybox:1.28 --restart=Never --rm -it busybox -- sh
If you don't see a command prompt, try pressing enter.
/ # ping www.baidu.com
PING www.baidu.com (103.235.46.102): 56 data bytes
64 bytes from 103.235.46.102: seq=0 ttl=127 time=343.524 ms
64 bytes from 103.235.46.102: seq=1 ttl=127 time=339.330 ms
64 bytes from 103.235.46.102: seq=2 ttl=127 time=351.520 ms
64 bytes from 103.235.46.102: seq=3 ttl=127 time=342.970 ms
64 bytes from 103.235.46.102: seq=4 ttl=127 time=338.878 ms# 通过上面可以看到能访问网络,说明calico网络插件已经被正常安装了9 测试 k8s 集群中部署 tomcat 服务
#把 tomcat.tar.gz 上传到 node1、node2,手动解压
[root@node1 ~]# ls
1ms-helper anaconda-ks.cfg busybox-1-28.tar.gz clash init.sh k8simage-1-20-6.tar.gz repo.bak tomcat.tar.gz
您在 /var/spool/mail/root 中有新邮件
[root@node1 ~]# docker load -i tomcat.tar.gz
f1b5933fe4b5: Loading layer [==================================================>] 5.796MB/5.796MB
9b9b7f3d56a0: Loading layer [==================================================>] 3.584kB/3.584kB
edd61588d126: Loading layer [==================================================>] 80.28MB/80.28MB
48988bb7b861: Loading layer [==================================================>] 2.56kB/2.56kB
8e0feedfd296: Loading layer [==================================================>] 24.06MB/24.06MB
aac21c2169ae: Loading layer [==================================================>] 2.048kB/2.048kB
Loaded image: tomcat:8.5-jre8-alpine[root@node2 ~]# ls
1ms-helper anaconda-ks.cfg busybox-1-28.tar.gz clash init.sh k8simage-1-20-6.tar.gz repo.bak tomcat.tar.gz
您在 /var/spool/mail/root 中有新邮件
[root@node1 ~]# docker load -i tomcat.tar.gz
f1b5933fe4b5: Loading layer [==================================================>] 5.796MB/5.796MB
9b9b7f3d56a0: Loading layer [==================================================>] 3.584kB/3.584kB
edd61588d126: Loading layer [==================================================>] 80.28MB/80.28MB
48988bb7b861: Loading layer [==================================================>] 2.56kB/2.56kB
8e0feedfd296: Loading layer [==================================================>] 24.06MB/24.06MB
aac21c2169ae: Loading layer [==================================================>] 2.048kB/2.048kB
Loaded image: tomcat:8.5-jre8-alpine# 编辑tomcat.yaml文件
[root@master1 ~]#vim tomcat.yamlapiVersion: v1 #pod属于k8s核心组v1
kind: Pod #创建的是一个Pod资源
metadata: #元数据name: demo-pod #pod名字namespace: default #pod所属的名称空间labels:app: myapp #pod具有的标签env: dev #pod具有的标签
spec:containers: #定义一个容器,容器是对象列表,下面可以有多个name- name: tomcat-pod-java #容器的名字ports:- containerPort: 8080image: tomcat:8.5-jre8-alpine #容器使用的镜像imagePullPolicy: IfNotPresent[root@master1 ~]# kubectl apply -f tomcat.yaml
pod/demo-pod created
[root@master1 ~]# kubectl get pods
NAME READY STATUS RESTARTS AGE
demo-pod 1/1 Running 0 8s[root@master1 ~]# vim tomcat-service.yaml
apiVersion: v1
kind: Service
metadata:name: tomcat
spec:type: NodePortports:- port: 8080nodePort: 30080selector:app: myappenv: dev[root@master1 ~]# kubectl apply -f tomcat-service.yaml
service/tomcat created
[root@master1 ~]# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 18h
tomcat NodePort 10.100.108.43 <none> 8080:30080/TCP 5s
在浏览器访问node1节点的ip加30080端口即可访问tomcat的web页面
10 测试 coredns 是否正常
[root@master1 ~]# kubectl run busybox --image busybox:1.28 --restart=Never --rm -it busybox -- sh
If you don't see a command prompt, try pressing enter.
/ # nslookup kubernetes.default.svc.cluster.local
Server: 10.96.0.10
Address 1: 10.96.0.10 kube-dns.kube-system.svc.cluster.localName: kubernetes.default.svc.cluster.local
Address 1: 10.96.0.1 kubernetes.default.svc.cluster.local
/ # 10.96.0.10 就是我们 coreDNS 的 clusterIP,说明 coreDNS 配置好了。
解析内部 Service 的名称,是通过 coreDNS 去解析的。
11 安装 k8s 可视化 UI 界面 dashboard
11.1 安装 dasboard
把安装 kubernetes-dashboard 需要的镜像上传到工作节点node1 和 node2,手动解压:
[root@node1 ~]# docker load -i dashboard_2_0_0.tar.gz
954115f32d73: Loading layer [==================================================>] 91.22MB/91.22MB
Loaded image: kubernetesui/dashboard:v2.0.0-beta8
您在 /var/spool/mail/root 中有新邮件
[root@node1 ~]# docker load -i metrics-scrapter-1-0-1.tar.gz
89ac18ee460b: Loading layer [==================================================>] 238.6kB/238.6kB
878c5d3194b0: Loading layer [==================================================>] 39.87MB/39.87MB
1dc71700363a: Loading layer [==================================================>] 2.048kB/2.048kB
Loaded image: kubernetesui/metrics-scraper:v1.0.1[root@node2 ~]# docker load -i dashboard_2_0_0.tar.gz
954115f32d73: Loading layer [==================================================>] 91.22MB/91.22MB
Loaded image: kubernetesui/dashboard:v2.0.0-beta8
您在 /var/spool/mail/root 中有新邮件
[root@node2 ~]# docker load -i metrics-scrapter-1-0-1.tar.gz
89ac18ee460b: Loading layer [==================================================>] 238.6kB/238.6kB
878c5d3194b0: Loading layer [==================================================>] 39.87MB/39.87MB
1dc71700363a: Loading layer [==================================================>] 2.048kB/2.048kB
Loaded image: kubernetesui/metrics-scraper:v1.0.1[root@master1 ~]# vim kubernetes-dashboard.yaml# Copyright 2017 The Kubernetes Authors.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
# You may obtain a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS,
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.apiVersion: v1
kind: Namespace
metadata:name: kubernetes-dashboard---apiVersion: v1
kind: ServiceAccount
metadata:labels:k8s-app: kubernetes-dashboardname: kubernetes-dashboardnamespace: kubernetes-dashboard---kind: Service
apiVersion: v1
metadata:labels:k8s-app: kubernetes-dashboardname: kubernetes-dashboardnamespace: kubernetes-dashboard
spec:ports:- port: 443targetPort: 8443selector:k8s-app: kubernetes-dashboard---apiVersion: v1
kind: Secret
metadata:labels:k8s-app: kubernetes-dashboardname: kubernetes-dashboard-certsnamespace: kubernetes-dashboard
type: Opaque---apiVersion: v1
kind: Secret
metadata:labels:k8s-app: kubernetes-dashboardname: kubernetes-dashboard-csrfnamespace: kubernetes-dashboard
type: Opaque
data:csrf: ""---apiVersion: v1
kind: Secret
metadata:labels:k8s-app: kubernetes-dashboardname: kubernetes-dashboard-key-holdernamespace: kubernetes-dashboard
type: Opaque---kind: ConfigMap
apiVersion: v1
metadata:labels:k8s-app: kubernetes-dashboardname: kubernetes-dashboard-settingsnamespace: kubernetes-dashboard---kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:labels:k8s-app: kubernetes-dashboardname: kubernetes-dashboardnamespace: kubernetes-dashboard
rules:# Allow Dashboard to get, update and delete Dashboard exclusive secrets.- apiGroups: [""]resources: ["secrets"]resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"]verbs: ["get", "update", "delete"]# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.- apiGroups: [""]resources: ["configmaps"]resourceNames: ["kubernetes-dashboard-settings"]verbs: ["get", "update"]# Allow Dashboard to get metrics.- apiGroups: [""]resources: ["services"]resourceNames: ["heapster", "dashboard-metrics-scraper"]verbs: ["proxy"]- apiGroups: [""]resources: ["services/proxy"]resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"]verbs: ["get"]---kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:labels:k8s-app: kubernetes-dashboardname: kubernetes-dashboard
rules:# Allow Metrics Scraper to get metrics from the Metrics server- apiGroups: ["metrics.k8s.io"]resources: ["pods", "nodes"]verbs: ["get", "list", "watch"]---apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:labels:k8s-app: kubernetes-dashboardname: kubernetes-dashboardnamespace: kubernetes-dashboard
roleRef:apiGroup: rbac.authorization.k8s.iokind: Rolename: kubernetes-dashboard
subjects:- kind: ServiceAccountname: kubernetes-dashboardnamespace: kubernetes-dashboard---apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:name: kubernetes-dashboard
roleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: kubernetes-dashboard
subjects:- kind: ServiceAccountname: kubernetes-dashboardnamespace: kubernetes-dashboard---kind: Deployment
apiVersion: apps/v1
metadata:labels:k8s-app: kubernetes-dashboardname: kubernetes-dashboardnamespace: kubernetes-dashboard
spec:replicas: 1revisionHistoryLimit: 10selector:matchLabels:k8s-app: kubernetes-dashboardtemplate:metadata:labels:k8s-app: kubernetes-dashboardspec:containers:- name: kubernetes-dashboardimage: kubernetesui/dashboard:v2.0.0-beta8imagePullPolicy: IfNotPresentports:- containerPort: 8443protocol: TCPargs:- --auto-generate-certificates- --namespace=kubernetes-dashboard# Uncomment the following line to manually specify Kubernetes API server Host# If not specified, Dashboard will attempt to auto discover the API server and connect# to it. Uncomment only if the default does not work.# - --apiserver-host=http://my-address:portvolumeMounts:- name: kubernetes-dashboard-certsmountPath: /certs# Create on-disk volume to store exec logs- mountPath: /tmpname: tmp-volumelivenessProbe:httpGet:scheme: HTTPSpath: /port: 8443initialDelaySeconds: 30timeoutSeconds: 30securityContext:allowPrivilegeEscalation: falsereadOnlyRootFilesystem: truerunAsUser: 1001runAsGroup: 2001volumes:- name: kubernetes-dashboard-certssecret:secretName: kubernetes-dashboard-certs- name: tmp-volumeemptyDir: {}serviceAccountName: kubernetes-dashboardnodeSelector:"beta.kubernetes.io/os": linux# Comment the following tolerations if Dashboard must not be deployed on mastertolerations:- key: node-role.kubernetes.io/mastereffect: NoSchedule---kind: Service
apiVersion: v1
metadata:labels:k8s-app: dashboard-metrics-scrapername: dashboard-metrics-scrapernamespace: kubernetes-dashboard
spec:ports:- port: 8000targetPort: 8000selector:k8s-app: dashboard-metrics-scraper---kind: Deployment
apiVersion: apps/v1
metadata:labels:k8s-app: dashboard-metrics-scrapername: dashboard-metrics-scrapernamespace: kubernetes-dashboard
spec:replicas: 1revisionHistoryLimit: 10selector:matchLabels:k8s-app: dashboard-metrics-scrapertemplate:metadata:labels:k8s-app: dashboard-metrics-scraperannotations:seccomp.security.alpha.kubernetes.io/pod: 'runtime/default'spec:containers:- name: dashboard-metrics-scraperimage: kubernetesui/metrics-scraper:v1.0.1imagePullPolicy: IfNotPresentports:- containerPort: 8000protocol: TCPlivenessProbe:httpGet:scheme: HTTPpath: /port: 8000initialDelaySeconds: 30timeoutSeconds: 30volumeMounts:- mountPath: /tmpname: tmp-volumesecurityContext:allowPrivilegeEscalation: falsereadOnlyRootFilesystem: truerunAsUser: 1001runAsGroup: 2001serviceAccountName: kubernetes-dashboardnodeSelector:"beta.kubernetes.io/os": linux# Comment the following tolerations if Dashboard must not be deployed on mastertolerations:- key: node-role.kubernetes.io/mastereffect: NoSchedulevolumes:- name: tmp-volumeemptyDir: {}[root@master1 ~]# kubectl apply -f kubernetes-dashboard.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created#显示如下,说明 dashboard 安装成功了
[root@master1 ~]# kubectl get pods -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
dashboard-metrics-scraper-7445d59dfd-qqcw7 1/1 Running 0 13s
kubernetes-dashboard-54f5b6dc4b-rl8wr 1/1 Running 0 13s#查看 dashboard 前端的 service
[root@master1 ~]# kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.99.36.22 <none> 8000/TCP 65s
kubernetes-dashboard ClusterIP 10.98.28.29 <none> 443/TCP 65s#修改 service type 类型变成 NodePort
[root@master1 ~]# kubectl edit svc kubernetes-dashboard -n kubernetes-dashboard# 把 type: ClusterIP 变成 type: NodePort,保存退出即可。[root@master1 ~]# kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.99.36.22 <none> 8000/TCP 2m54s
kubernetes-dashboard NodePort 10.98.28.29 <none> 443:31295/TCP 2m54s上面可看到 service 类型是 NodePort,访问任何一个工作节点 ip: 31295 端口即可访问 kubernetes dashboard,在浏览器(使用火狐浏览器)访问如下地址:
https://192.168.121.102:31295

11.2 通过 token 令牌访问 dashboard
# 通过 Token 登陆 dashboard
# 创建管理员 token,具有查看任何空间的权限,可以管理所有资源对象
[root@master1 ~]# kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:kubernetes-dashboard
clusterrolebinding.rbac.authorization.k8s.io/dashboard-cluster-admin created# 查看 kubernetes-dashboard 名称空间下的 secret
[root@master1 ~]# kubectl get secret -n kubernetes-dashboard
NAME TYPE DATA AGE
default-token-59g55 kubernetes.io/service-account-token 3 7m52s
kubernetes-dashboard-certs Opaque 0 7m52s
kubernetes-dashboard-csrf Opaque 1 7m52s
kubernetes-dashboard-key-holder Opaque 2 7m52s
kubernetes-dashboard-token-7865l kubernetes.io/service-account-token 3 7m52s# 找到对应的带有 token 的 kubernetes-dashboard-token-ppc8c[root@master1 ~]# kubectl describe secret kubernetes-dashboard-token-7865l -n kubernetes-dashboard
Name: kubernetes-dashboard-token-7865l
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: kubernetes.io/service-account.name: kubernetes-dashboardkubernetes.io/service-account.uid: c5675c08-6606-41c2-859d-e8e54d80710aType: kubernetes.io/service-account-tokenData
====
ca.crt: 1066 bytes
namespace: 20 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlkxdExiWm5Xdm0xX0F6emVwTEVTMkpQQy1pX2dTU25EUl91d0hZalpjWDAifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi03ODY1bCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImM1Njc1YzA4LTY2MDYtNDFjMi04NTlkLWU4ZTU0ZDgwNzEwYSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.ZPuldOtmERsqTRBPVADMXWJpC8CwDPdsbOYSfKT6SmXo2hAXU9EqBngGEQecXd2OlBo7UT-748AssQJtBYcIh0KwCz9dwruszuS-KHRqG89D-2wz1Sg_uRTBA445yJctlfclGJFQKbogFvAPCF31lYCi6yLYhNhbzoiIRV3ZtPowKox0yoBXcopLT6x8W-YReQRDuHHu51La33Lu2Xsd8tkYu_4JXlrmTkPxfznUuZ3SArZguww5rirY06V7pLKE54kOMgwQ_Z7bCb2PYbuvXAg2G_h7TgGQIaNuQm2mMEVb_0lspIVj9cRYm38Yn-yOwb_bFu_2YCQfzfiWmvUyww# 将token 后面的值复制到浏览器token登录处即可登录
11.3 通过 kubeconfig 文件访问 dashboard
[root@master1 ~]# cd /etc/kubernetes/pki/# 创建cluster集群
[root@master1 pki]# kubectl config set-cluster kubernetes --certificate-authority=./ca.crt --server="https://192.168.121.101:6443" --embed-certs=true --kubeconfig=/root/dashboard-admin.conf
Cluster "kubernetes" set.
[root@master1 pki]# cat /root/dashboard-admin.conf
apiVersion: v1
clusters:
- cluster:certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJMU1Ea3hNakE1TXpJeU0xb1hEVE0xTURreE1EQTVNekl5TTFvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTVkvCjlSV2lQUHE4dlpLNkw2QjkzZGsrTm1GTDhIbnZYbk5ZSnBXVUVCNmMxZExrRlJIVVVndlJIT0FkZlE3S3lBLzgKazJBWmRpdFZicVhEOTRQMG94N0xaOWdEZjlibnNKMFVPbzduT211anQ5MUZOcHZ2bXUrb2UyR28yTjc0aXUyZgoxRjhZV1ZaSUJKOVpBVnlqWk5xaEt6RTBrMzh5K1RORGxPcHN6YkJxeExKQ0xpanliNmpCd3NqRElQUUpVVDQ3CnBUVWR2alFnQll1M3FhVWk4ZWFCNzFrN0YxT1BzTU1KWW1nemtoU2Z6TXhReFF1aFo5VnJJWnJiKytEY2NZVWUKaG5iNmNIVDJiWU01NWsvWWhnNkpySEluM2xLTkNyemVwM1lhZ0xNMjNMdGQ3eUxoQXNyb1NsRXdkc3puTlBJRAp3Slc4L3MzdmZXUUJYeVhycmxNQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZPcEFyRWVnZE1WS2xlckZpVFdzbkFzY1ZHanlNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFDb3FUMjlTRXBORFM0cjMvT3J2Z1ZKY1ozRmxVemJvNXJma05SeVhDelFqZVpiZFhqMgo2dVBoZ2thdi8yYWNkU1IvZHpCQWJOTlNRMTJkaEY4SmVKYitEb1ptYlpDcUdKU1lMN3REVHJZWmpYV0dTV2ZMCmhudXdJalhVMFMwVmI1dS9vYktFNkxyRDRLRys4NW9PaVpTb0NySzM3ck5KT281TVZyRjBQNmN4QUE5eS9tWEUKOTRObXVKWW1KeTIxc1RwcisxTUQ0UG9od09CM0dKMTF1UkltdkRHaEJqTHF3TThITGp4SHBFWWdpZmU3N2FjcgpobjdvSjdKTHUwRGdGdGdobnBDeG5jWDNnU1BZd08xREpQV2o0Rml0ckJiOFgyNnU0dEtORmVkMUxiblE2YzZnCnA0amlnVHh4eEpENnR1dE1SbUoycTRjd05CSWxVdUZ2UldjUQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==server: https://192.168.121.101:6443name: kubernetes
contexts: null
current-context: ""
kind: Config
preferences: {}
users: null# 创建credentials
创建 credentials 需要使用上面的 kubernetes-dashboard-token-7865l 对应的 token 信息[root@master1 pki]# DEF_NS_ADMIN_TOKEN=$(kubectl get secret kubernetes-dashboard-token-7865l -n kubernetes-dashboard -o jsonpath={.data.token}|base64 -d)
[root@master1 pki]# kubectl config set-credentials dashboard-admin --token=$DEF_NS_ADMIN_TOKEN --kubeconfig=/root/dashboard-admin.conf
User "dashboard-admin" set.[root@master1 pki]# cat /root/dashboard-admin.conf
apiVersion: v1
clusters:
- cluster:certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJMU1Ea3hNakE1TXpJeU0xb1hEVE0xTURreE1EQTVNekl5TTFvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTVkvCjlSV2lQUHE4dlpLNkw2QjkzZGsrTm1GTDhIbnZYbk5ZSnBXVUVCNmMxZExrRlJIVVVndlJIT0FkZlE3S3lBLzgKazJBWmRpdFZicVhEOTRQMG94N0xaOWdEZjlibnNKMFVPbzduT211anQ5MUZOcHZ2bXUrb2UyR28yTjc0aXUyZgoxRjhZV1ZaSUJKOVpBVnlqWk5xaEt6RTBrMzh5K1RORGxPcHN6YkJxeExKQ0xpanliNmpCd3NqRElQUUpVVDQ3CnBUVWR2alFnQll1M3FhVWk4ZWFCNzFrN0YxT1BzTU1KWW1nemtoU2Z6TXhReFF1aFo5VnJJWnJiKytEY2NZVWUKaG5iNmNIVDJiWU01NWsvWWhnNkpySEluM2xLTkNyemVwM1lhZ0xNMjNMdGQ3eUxoQXNyb1NsRXdkc3puTlBJRAp3Slc4L3MzdmZXUUJYeVhycmxNQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZPcEFyRWVnZE1WS2xlckZpVFdzbkFzY1ZHanlNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFDb3FUMjlTRXBORFM0cjMvT3J2Z1ZKY1ozRmxVemJvNXJma05SeVhDelFqZVpiZFhqMgo2dVBoZ2thdi8yYWNkU1IvZHpCQWJOTlNRMTJkaEY4SmVKYitEb1ptYlpDcUdKU1lMN3REVHJZWmpYV0dTV2ZMCmhudXdJalhVMFMwVmI1dS9vYktFNkxyRDRLRys4NW9PaVpTb0NySzM3ck5KT281TVZyRjBQNmN4QUE5eS9tWEUKOTRObXVKWW1KeTIxc1RwcisxTUQ0UG9od09CM0dKMTF1UkltdkRHaEJqTHF3TThITGp4SHBFWWdpZmU3N2FjcgpobjdvSjdKTHUwRGdGdGdobnBDeG5jWDNnU1BZd08xREpQV2o0Rml0ckJiOFgyNnU0dEtORmVkMUxiblE2YzZnCnA0amlnVHh4eEpENnR1dE1SbUoycTRjd05CSWxVdUZ2UldjUQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==server: https://192.168.121.101:6443name: kubernetes
contexts: null
current-context: ""
kind: Config
preferences: {}
users:
- name: dashboard-adminuser:token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlkxdExiWm5Xdm0xX0F6emVwTEVTMkpQQy1pX2dTU25EUl91d0hZalpjWDAifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi03ODY1bCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImM1Njc1YzA4LTY2MDYtNDFjMi04NTlkLWU4ZTU0ZDgwNzEwYSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.ZPuldOtmERsqTRBPVADMXWJpC8CwDPdsbOYSfKT6SmXo2hAXU9EqBngGEQecXd2OlBo7UT-748AssQJtBYcIh0KwCz9dwruszuS-KHRqG89D-2wz1Sg_uRTBA445yJctlfclGJFQKbogFvAPCF31lYCi6yLYhNhbzoiIRV3ZtPowKox0yoBXcopLT6x8W-YReQRDuHHu51La33Lu2Xsd8tkYu_4JXlrmTkPxfznUuZ3SArZguww5rirY06V7pLKE54kOMgwQ_Z7bCb2PYbuvXAg2G_h7TgGQIaNuQm2mMEVb_0lspIVj9cRYm38Yn-yOwb_bFu_2YCQfzfiWmvUyww# 创建 context[root@master1 pki]# kubectl config set-context dashboard-admin@kubernetes --cluster=kubernetes --user=dashboard-admin --kubeconfig=/root/dashboard-admin.conf
Context "dashboard-admin@kubernetes" created.
[root@master1 pki]# cat /root/dashboard-admin.conf
apiVersion: v1
clusters:
- cluster:certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJMU1Ea3hNakE1TXpJeU0xb1hEVE0xTURreE1EQTVNekl5TTFvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTVkvCjlSV2lQUHE4dlpLNkw2QjkzZGsrTm1GTDhIbnZYbk5ZSnBXVUVCNmMxZExrRlJIVVVndlJIT0FkZlE3S3lBLzgKazJBWmRpdFZicVhEOTRQMG94N0xaOWdEZjlibnNKMFVPbzduT211anQ5MUZOcHZ2bXUrb2UyR28yTjc0aXUyZgoxRjhZV1ZaSUJKOVpBVnlqWk5xaEt6RTBrMzh5K1RORGxPcHN6YkJxeExKQ0xpanliNmpCd3NqRElQUUpVVDQ3CnBUVWR2alFnQll1M3FhVWk4ZWFCNzFrN0YxT1BzTU1KWW1nemtoU2Z6TXhReFF1aFo5VnJJWnJiKytEY2NZVWUKaG5iNmNIVDJiWU01NWsvWWhnNkpySEluM2xLTkNyemVwM1lhZ0xNMjNMdGQ3eUxoQXNyb1NsRXdkc3puTlBJRAp3Slc4L3MzdmZXUUJYeVhycmxNQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZPcEFyRWVnZE1WS2xlckZpVFdzbkFzY1ZHanlNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFDb3FUMjlTRXBORFM0cjMvT3J2Z1ZKY1ozRmxVemJvNXJma05SeVhDelFqZVpiZFhqMgo2dVBoZ2thdi8yYWNkU1IvZHpCQWJOTlNRMTJkaEY4SmVKYitEb1ptYlpDcUdKU1lMN3REVHJZWmpYV0dTV2ZMCmhudXdJalhVMFMwVmI1dS9vYktFNkxyRDRLRys4NW9PaVpTb0NySzM3ck5KT281TVZyRjBQNmN4QUE5eS9tWEUKOTRObXVKWW1KeTIxc1RwcisxTUQ0UG9od09CM0dKMTF1UkltdkRHaEJqTHF3TThITGp4SHBFWWdpZmU3N2FjcgpobjdvSjdKTHUwRGdGdGdobnBDeG5jWDNnU1BZd08xREpQV2o0Rml0ckJiOFgyNnU0dEtORmVkMUxiblE2YzZnCnA0amlnVHh4eEpENnR1dE1SbUoycTRjd05CSWxVdUZ2UldjUQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==server: https://192.168.121.101:6443name: kubernetes
contexts:
- context:cluster: kubernetesuser: dashboard-adminname: dashboard-admin@kubernetes
current-context: ""
kind: Config
preferences: {}
users:
- name: dashboard-adminuser:token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlkxdExiWm5Xdm0xX0F6emVwTEVTMkpQQy1pX2dTU25EUl91d0hZalpjWDAifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi03ODY1bCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImM1Njc1YzA4LTY2MDYtNDFjMi04NTlkLWU4ZTU0ZDgwNzEwYSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.ZPuldOtmERsqTRBPVADMXWJpC8CwDPdsbOYSfKT6SmXo2hAXU9EqBngGEQecXd2OlBo7UT-748AssQJtBYcIh0KwCz9dwruszuS-KHRqG89D-2wz1Sg_uRTBA445yJctlfclGJFQKbogFvAPCF31lYCi6yLYhNhbzoiIRV3ZtPowKox0yoBXcopLT6x8W-YReQRDuHHu51La33Lu2Xsd8tkYu_4JXlrmTkPxfznUuZ3SArZguww5rirY06V7pLKE54kOMgwQ_Z7bCb2PYbuvXAg2G_h7TgGQIaNuQm2mMEVb_0lspIVj9cRYm38Yn-yOwb_bFu_2YCQfzfiWmvUyww# 切换context的current-context是dashboard-admin@kubernetes
[root@master1 pki]# kubectl config use-context dashboard-admin@kubernetes --kubeconfig=/root/dashboard-admin.conf
Switched to context "dashboard-admin@kubernetes".
[root@master1 pki]# cat /root/dashboard-admin.conf
apiVersion: v1
clusters:
- cluster:certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUM1ekNDQWMrZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJMU1Ea3hNakE1TXpJeU0xb1hEVE0xTURreE1EQTVNekl5TTFvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTVkvCjlSV2lQUHE4dlpLNkw2QjkzZGsrTm1GTDhIbnZYbk5ZSnBXVUVCNmMxZExrRlJIVVVndlJIT0FkZlE3S3lBLzgKazJBWmRpdFZicVhEOTRQMG94N0xaOWdEZjlibnNKMFVPbzduT211anQ5MUZOcHZ2bXUrb2UyR28yTjc0aXUyZgoxRjhZV1ZaSUJKOVpBVnlqWk5xaEt6RTBrMzh5K1RORGxPcHN6YkJxeExKQ0xpanliNmpCd3NqRElQUUpVVDQ3CnBUVWR2alFnQll1M3FhVWk4ZWFCNzFrN0YxT1BzTU1KWW1nemtoU2Z6TXhReFF1aFo5VnJJWnJiKytEY2NZVWUKaG5iNmNIVDJiWU01NWsvWWhnNkpySEluM2xLTkNyemVwM1lhZ0xNMjNMdGQ3eUxoQXNyb1NsRXdkc3puTlBJRAp3Slc4L3MzdmZXUUJYeVhycmxNQ0F3RUFBYU5DTUVBd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZPcEFyRWVnZE1WS2xlckZpVFdzbkFzY1ZHanlNQTBHQ1NxR1NJYjMKRFFFQkN3VUFBNElCQVFDb3FUMjlTRXBORFM0cjMvT3J2Z1ZKY1ozRmxVemJvNXJma05SeVhDelFqZVpiZFhqMgo2dVBoZ2thdi8yYWNkU1IvZHpCQWJOTlNRMTJkaEY4SmVKYitEb1ptYlpDcUdKU1lMN3REVHJZWmpYV0dTV2ZMCmhudXdJalhVMFMwVmI1dS9vYktFNkxyRDRLRys4NW9PaVpTb0NySzM3ck5KT281TVZyRjBQNmN4QUE5eS9tWEUKOTRObXVKWW1KeTIxc1RwcisxTUQ0UG9od09CM0dKMTF1UkltdkRHaEJqTHF3TThITGp4SHBFWWdpZmU3N2FjcgpobjdvSjdKTHUwRGdGdGdobnBDeG5jWDNnU1BZd08xREpQV2o0Rml0ckJiOFgyNnU0dEtORmVkMUxiblE2YzZnCnA0amlnVHh4eEpENnR1dE1SbUoycTRjd05CSWxVdUZ2UldjUQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==server: https://192.168.121.101:6443name: kubernetes
contexts:
- context:cluster: kubernetesuser: dashboard-adminname: dashboard-admin@kubernetes
current-context: dashboard-admin@kubernetes
kind: Config
preferences: {}
users:
- name: dashboard-adminuser:token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlkxdExiWm5Xdm0xX0F6emVwTEVTMkpQQy1pX2dTU25EUl91d0hZalpjWDAifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZC10b2tlbi03ODY1bCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImM1Njc1YzA4LTY2MDYtNDFjMi04NTlkLWU4ZTU0ZDgwNzEwYSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDprdWJlcm5ldGVzLWRhc2hib2FyZCJ9.ZPuldOtmERsqTRBPVADMXWJpC8CwDPdsbOYSfKT6SmXo2hAXU9EqBngGEQecXd2OlBo7UT-748AssQJtBYcIh0KwCz9dwruszuS-KHRqG89D-2wz1Sg_uRTBA445yJctlfclGJFQKbogFvAPCF31lYCi6yLYhNhbzoiIRV3ZtPowKox0yoBXcopLT6x8W-YReQRDuHHu51La33Lu2Xsd8tkYu_4JXlrmTkPxfznUuZ3SArZguww5rirY06V7pLKE54kOMgwQ_Z7bCb2PYbuvXAg2G_h7TgGQIaNuQm2mMEVb_0lspIVj9cRYm38Yn-yOwb_bFu_2YCQfzfiWmvUyww把刚才的 kubeconfig 文件 dashboard-admin.conf 复制到桌面
浏览器访问时使用 kubeconfig 认证,把刚才的 dashboard-admin.conf 导入到 web 界面,那么就可以登陆了

11.4 通过 kubernetes-dashboard 创建容器
把 nginx.tar.gz 镜像压缩包上传到 node1 和 node2 上,手动解压: docker load -i nginx.tar.gz
[root@node1 ~]# docker load -i nginx.tar.gz
02c055ef67f5: Loading layer [==================================================>] 72.53MB/72.53MB
766fe2c3fc08: Loading layer [==================================================>] 64.8MB/64.8MB
83634f76e732: Loading layer [==================================================>] 3.072kB/3.072kB
134e19b2fac5: Loading layer [==================================================>] 4.096kB/4.096kB
5c865c78bc96: Loading layer [==================================================>] 3.584kB/3.584kB
075508cf8f04: Loading layer [==================================================>] 7.168kB/7.168kB
Loaded image: nginx:latest[root@node2 ~]# docker load -i nginx.tar.gz
02c055ef67f5: Loading layer [==================================================>] 72.53MB/72.53MB
766fe2c3fc08: Loading layer [==================================================>] 64.8MB/64.8MB
83634f76e732: Loading layer [==================================================>] 3.072kB/3.072kB
134e19b2fac5: Loading layer [==================================================>] 4.096kB/4.096kB
5c865c78bc96: Loading layer [==================================================>] 3.584kB/3.584kB
075508cf8f04: Loading layer [==================================================>] 7.168kB/7.168kB
Loaded image: nginx:latest
打开 kubernetes 的 dashboard 界面(https://192.168.121.102:31295/),点开右上角红色箭头标注的 “+”,如下图所示:

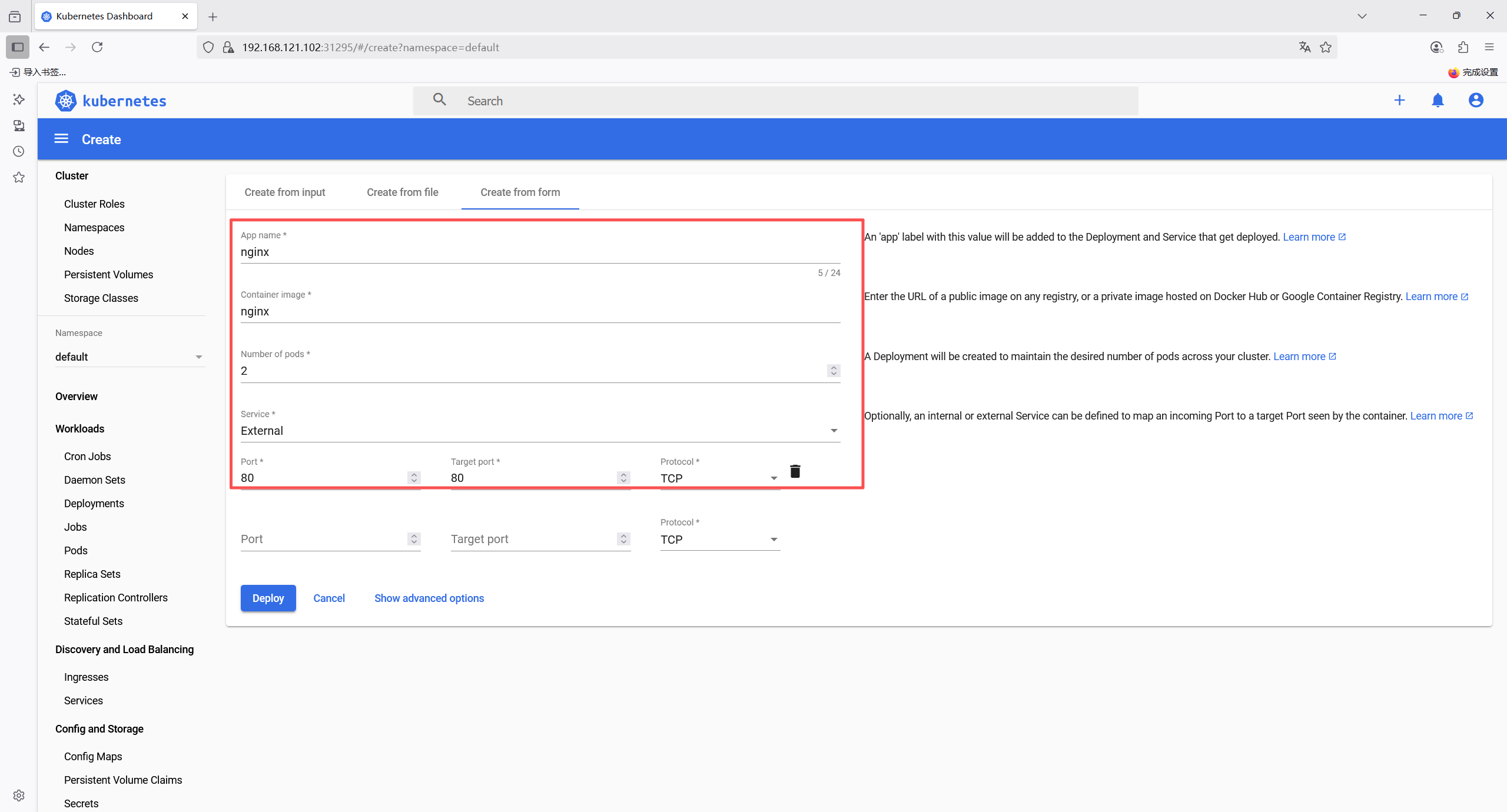
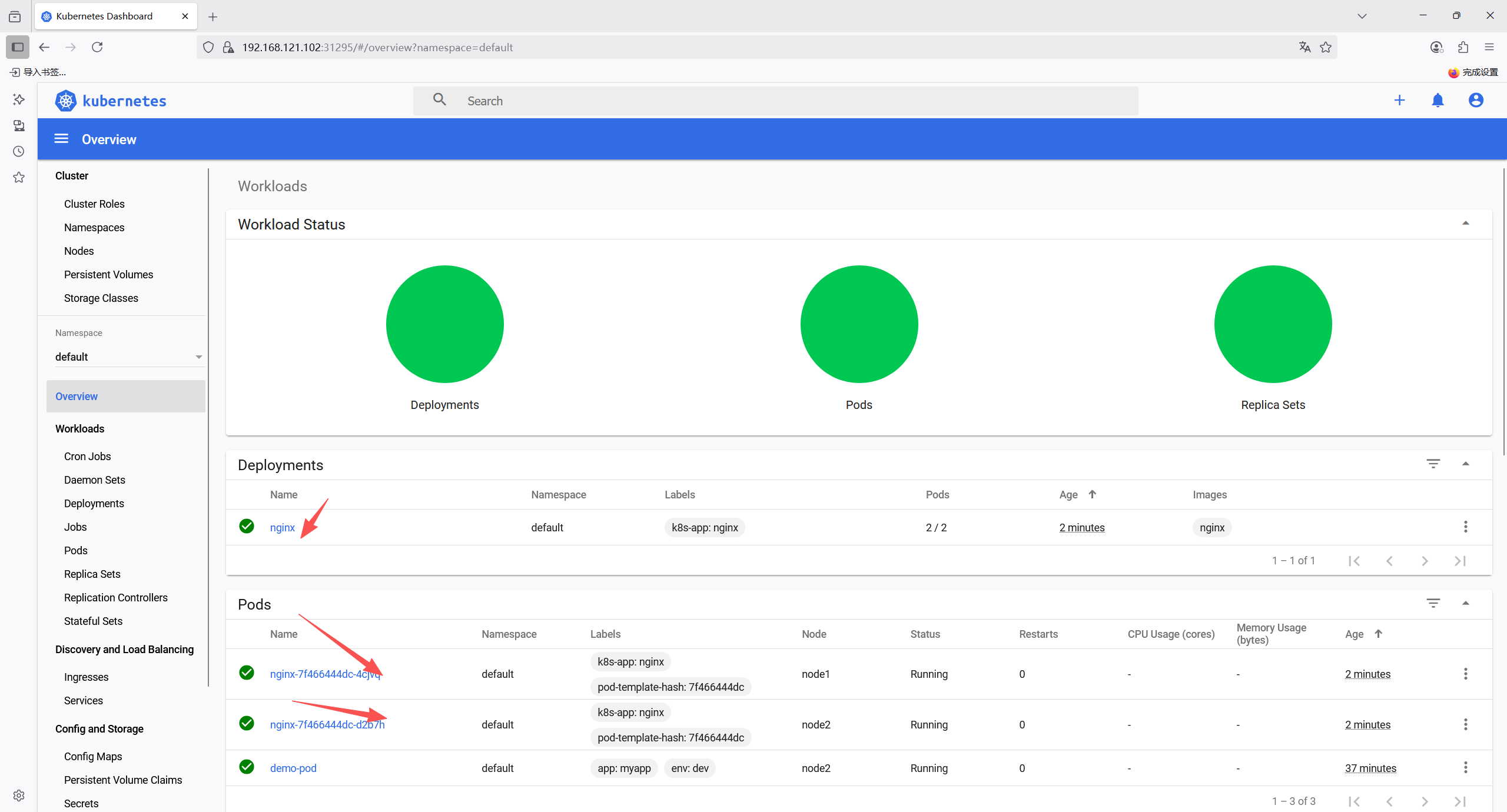
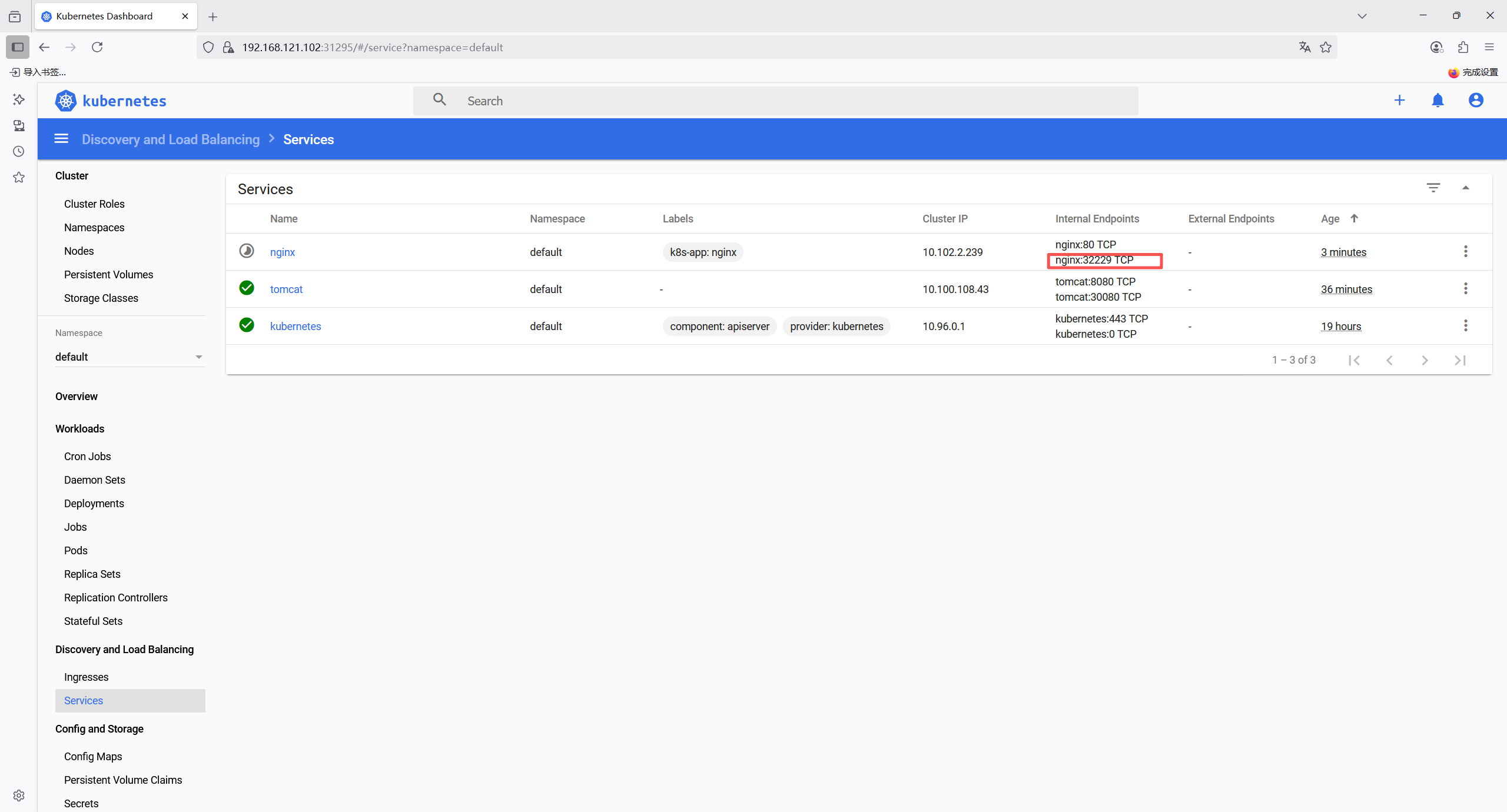
可以看到刚才nginx的service在宿主机映射的端口是32229,在浏览器访问192.168.121.101:32229
看到nginx欢迎页面说明nginx部署成功了
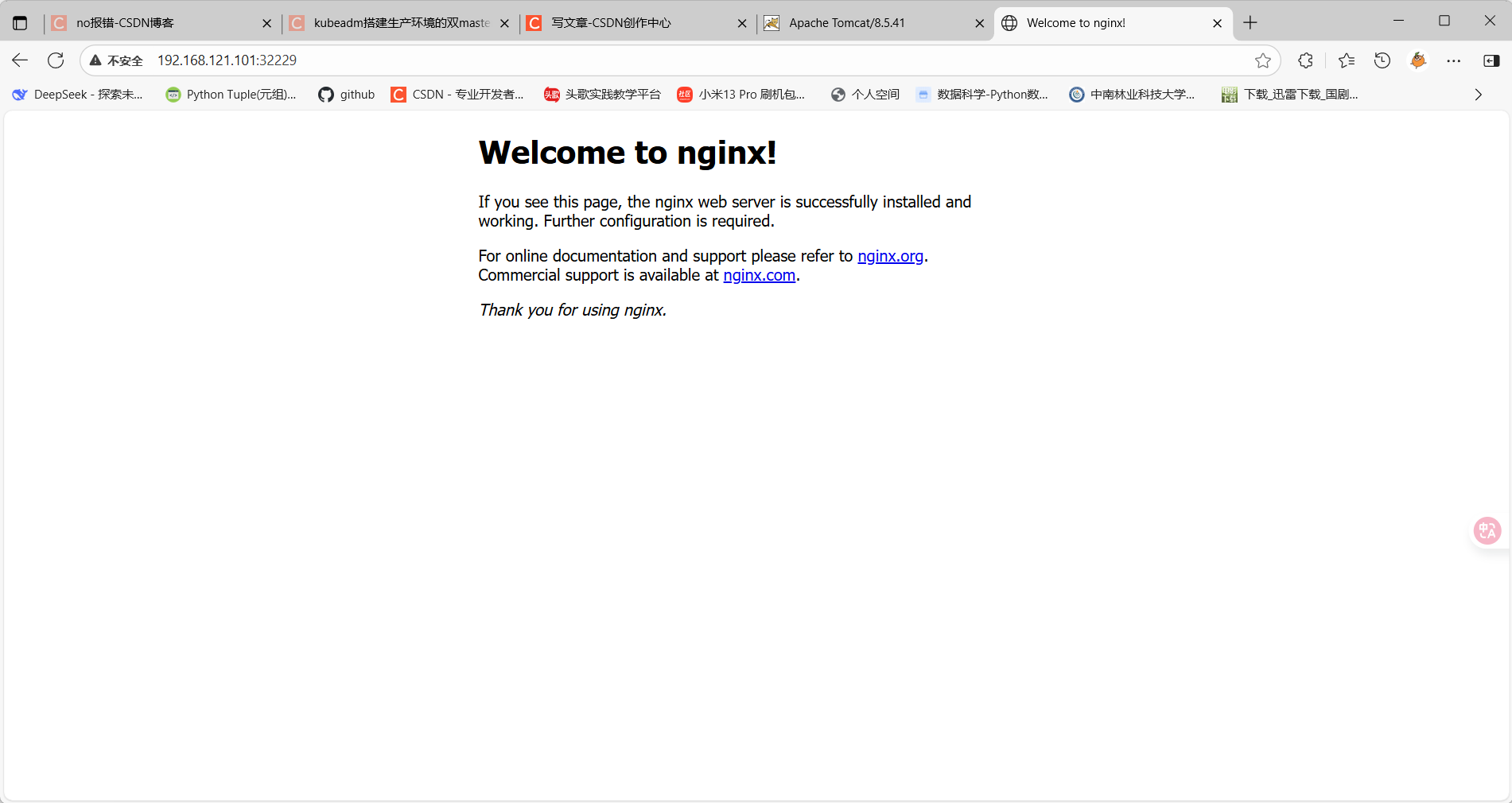
12 安装 metrics-server 组件
metrics-server 是一个集群范围内的资源数据集和工具,同样的,metrics-server 也只是显示数 据,并不提供数据存储服务,主要关注的是资源度量 API 的实现,比如 CPU、文件描述符、内存、请求延时等指标,metric-server 收集数据给 k8s 集群内使用,如 kubectl,hpa,scheduler 等
12.1 部署 metrics-server 组件
#把离线镜像压缩包上传到 k8s 的各个节点,按如下方法手动解压:
[root@master1 ~]# docker load -i metrics-server-amd64-0-3-6.tar.gz
932da5156413: Loading layer [==================================================>] 3.062MB/3.062MB
7bf3709d22bb: Loading layer [==================================================>] 38.13MB/38.13MB
Loaded image: k8s.gcr.io/metrics-server-amd64:v0.3.6
[root@master1 ~]# docker load -i addon.tar.gz
8a788232037e: Loading layer [==================================================>] 1.37MB/1.37MB
cd05ae2f58b4: Loading layer [==================================================>] 37.2MB/37.2MB
Loaded image: k8s.gcr.io/addon-resizer:1.8.4[root@node1 ~]# docker load -i metrics-server-amd64-0-3-6.tar.gz
932da5156413: Loading layer [==================================================>] 3.062MB/3.062MB
7bf3709d22bb: Loading layer [==================================================>] 38.13MB/38.13MB
Loaded image: k8s.gcr.io/metrics-server-amd64:v0.3.6
[root@node1 ~]# docker load -i addon.tar.gz
8a788232037e: Loading layer [==================================================>] 1.37MB/1.37MB
cd05ae2f58b4: Loading layer [==================================================>] 37.2MB/37.2MB
Loaded image: k8s.gcr.io/addon-resizer:1.8.4[root@node2 ~]# docker load -i metrics-server-amd64-0-3-6.tar.gz
932da5156413: Loading layer [==================================================>] 3.062MB/3.062MB
7bf3709d22bb: Loading layer [==================================================>] 38.13MB/38.13MB
Loaded image: k8s.gcr.io/metrics-server-amd64:v0.3.6
[root@node2 ~]# docker load -i addon.tar.gz
8a788232037e: Loading layer [==================================================>] 1.37MB/1.37MB
cd05ae2f58b4: Loading layer [==================================================>] 37.2MB/37.2MB
Loaded image: k8s.gcr.io/addon-resizer:1.8.4#部署 metrics-server 服务
#在/etc/kubernetes/manifests 里面改一下 apiserver 的配置
[root@master1 ~]# vim /etc/kubernetes/manifests/kube-apiserver.yaml
#增加如下内容:
- --enable-aggregator-routing=true[root@master1 ~]# kubectl apply -f /etc/kubernetes/manifests/kube-apiserver.yaml
[root@master1 ~]# kubectl get pods -n kube-system
把 CrashLoopBackOff 状态的 pod 删除
[root@master1 ~]# kubectl delete pods kube-apiserver -n kube-system
pod "kube-apiserver" deleted
[root@master1 ~]# vim metrics.yaml apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:name: metrics-server:system:auth-delegatorlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcile
roleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: system:auth-delegator
subjects:
- kind: ServiceAccountname: metrics-servernamespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:name: metrics-server-auth-readernamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcile
roleRef:apiGroup: rbac.authorization.k8s.iokind: Rolename: extension-apiserver-authentication-reader
subjects:
- kind: ServiceAccountname: metrics-servernamespace: kube-system
---
apiVersion: v1
kind: ServiceAccount
metadata:name: metrics-servernamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcile
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:name: system:metrics-serverlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcile
rules:
- apiGroups:- ""resources:- pods- nodes- nodes/stats- namespacesverbs:- get- list- watch
- apiGroups:- "extensions"resources:- deploymentsverbs:- get- list- update- watch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:name: system:metrics-serverlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcile
roleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: system:metrics-server
subjects:
- kind: ServiceAccountname: metrics-servernamespace: kube-system
---
apiVersion: v1
kind: ConfigMap
metadata:name: metrics-server-confignamespace: kube-systemlabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: EnsureExists
data:NannyConfiguration: |-apiVersion: nannyconfig/v1alpha1kind: NannyConfiguration
---
apiVersion: apps/v1
kind: Deployment
metadata:name: metrics-servernamespace: kube-systemlabels:k8s-app: metrics-serverkubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcileversion: v0.3.6
spec:selector:matchLabels:k8s-app: metrics-serverversion: v0.3.6template:metadata:name: metrics-serverlabels:k8s-app: metrics-serverversion: v0.3.6annotations:scheduler.alpha.kubernetes.io/critical-pod: ''seccomp.security.alpha.kubernetes.io/pod: 'docker/default'spec:priorityClassName: system-cluster-criticalserviceAccountName: metrics-servercontainers:- name: metrics-serverimage: k8s.gcr.io/metrics-server-amd64:v0.3.6imagePullPolicy: IfNotPresentcommand:- /metrics-server- --metric-resolution=30s- --kubelet-preferred-address-types=InternalIP- --kubelet-insecure-tlsports:- containerPort: 443name: httpsprotocol: TCP- name: metrics-server-nannyimage: k8s.gcr.io/addon-resizer:1.8.4imagePullPolicy: IfNotPresentresources:limits:cpu: 100mmemory: 300Mirequests:cpu: 5mmemory: 50Mienv:- name: MY_POD_NAMEvalueFrom:fieldRef:fieldPath: metadata.name- name: MY_POD_NAMESPACEvalueFrom:fieldRef:fieldPath: metadata.namespacevolumeMounts:- name: metrics-server-config-volumemountPath: /etc/configcommand:- /pod_nanny- --config-dir=/etc/config- --cpu=300m- --extra-cpu=20m- --memory=200Mi- --extra-memory=10Mi- --threshold=5- --deployment=metrics-server- --container=metrics-server- --poll-period=300000- --estimator=exponential- --minClusterSize=2volumes:- name: metrics-server-config-volumeconfigMap:name: metrics-server-configtolerations:- key: "CriticalAddonsOnly"operator: "Exists"- key: node-role.kubernetes.io/mastereffect: NoSchedule
---
apiVersion: v1
kind: Service
metadata:name: metrics-servernamespace: kube-systemlabels:addonmanager.kubernetes.io/mode: Reconcilekubernetes.io/cluster-service: "true"kubernetes.io/name: "Metrics-server"
spec:selector:k8s-app: metrics-serverports:- port: 443protocol: TCPtargetPort: https
---
apiVersion: apiregistration.k8s.io/v1
kind: APIService
metadata:name: v1beta1.metrics.k8s.iolabels:kubernetes.io/cluster-service: "true"addonmanager.kubernetes.io/mode: Reconcile
spec:service:name: metrics-servernamespace: kube-systemgroup: metrics.k8s.ioversion: v1beta1insecureSkipTLSVerify: truegroupPriorityMinimum: 100versionPriority: 100[root@master1 ~]# kubectl apply -f metrics.yaml
clusterrolebinding.rbac.authorization.k8s.io/metrics-server:system:auth-delegator created
rolebinding.rbac.authorization.k8s.io/metrics-server-auth-reader created
serviceaccount/metrics-server created
clusterrole.rbac.authorization.k8s.io/system:metrics-server created
clusterrolebinding.rbac.authorization.k8s.io/system:metrics-server created
configmap/metrics-server-config created
deployment.apps/metrics-server created
service/metrics-server created
apiservice.apiregistration.k8s.io/v1beta1.metrics.k8s.io created
[root@master1 ~]# kubectl get pods -n kube-system | grep metrics
metrics-server-6595f875d6-tlhs5 2/2 Running 0 57s
12.2 测试 kubectl top 命令
[root@master1 ~]# kubectl top pods -n kube-system
NAME CPU(cores) MEMORY(bytes)
calico-kube-controllers-6949477b58-hdfbw 1m 34Mi
calico-node-cgdbd 29m 113Mi
calico-node-gk8sq 30m 96Mi
calico-node-j2mtd 31m 112Mi
coredns-7f89b7bc75-4dk9p 3m 24Mi
coredns-7f89b7bc75-5ttpc 3m 14Mi
etcd-master1 11m 62Mi
kube-apiserver-master1 42m 417Mi
kube-controller-manager-master1 15m 59Mi
kube-proxy-l27p4 1m 36Mi
kube-proxy-z7xwj 1m 33Mi
kube-proxy-zc2hm 1m 30Mi
kube-scheduler-master1 3m 20Mi
metrics-server-6595f875d6-tlhs5 1m 16Mi [root@master1 ~]# kubectl top nodes
NAME CPU(cores) CPU% MEMORY(bytes) MEMORY%
master1 137m 6% 1186Mi 69%
node1 78m 3% 859Mi 49%
node2 69m 3% 908Mi 52%把 scheduler、controller-manager 端口变成物理机可以监听的端口
[root@master1 ~]# kubectl get cs
Warning: v1 ComponentStatus is deprecated in v1.19+
NAME STATUS MESSAGE ERROR
scheduler Unhealthy Get "http://127.0.0.1:10251/healthz": dial tcp 127.0.0.1:10251: connect: connection refused
controller-manager Unhealthy Get "http://127.0.0.1:10252/healthz": dial tcp 127.0.0.1:10252: connect: connection refused
etcd-0 Healthy {"health":"true"} 默认在 1.19 之后 10252 和 10251 都是绑定在 127 的,如果想要通过 prometheus 监控,会采集不到
数据,所以可以把端口绑定到物理机 可按如下方法处理:
vim /etc/kubernetes/manifests/kube-scheduler.yaml
修改如下内容:
把--bind-address=127.0.0.1 变成--bind-address=192.168.121.101
把 httpGet:字段下的 hosts 由 127.0.0.1 变成 192.168.121.101
把—port=0 删除
#注意:192.168.121.101 是 k8s 的控制节点 master1 的 ip
vim /etc/kubernetes/manifests/kube-controller-manager.yaml
把--bind-address=127.0.0.1 变成--bind-address=192.168.121.101
把 httpGet:字段下的 hosts 由 127.0.0.1 变成 192.168.121.101
把—port=0 删除
修改之后在 k8s 各个节点重启下 kubelet
systemctl restart kubelet
[root@master1 prometheus]# kubectl get cs
Warning: v1 ComponentStatus is deprecated in v1.19+
NAME STATUS MESSAGE ERROR
scheduler Healthy ok
controller-manager Healthy ok
etcd-0 Healthy {"health":"true"}
ss -antulp | grep :10251
ss -antulp | grep :10252
可以看到相应的端口已经被物理机监听了