k8s-RBAC鉴权
k8s-RBAC鉴权
- 一、核心概念
- 二、ServiceAccount使用
- 三、创建clusterrole访问
- 四、普通用户访问
- 五、Linux 系统用户与 Kubernetes 用户账号的关联,达成多租户权限隔离
官方文档:https://kubernetes.io/zh-cn/docs/reference/access-authn-authz/rbac/
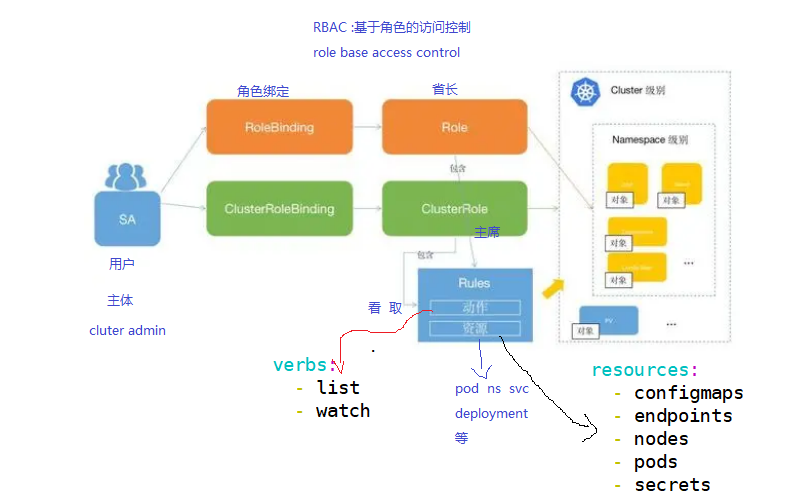
一、核心概念
- 主体(
Subjects):可以是用户、组或服务账户- User:由管理员手动创建的用户
- Group:用户的集合
- ServiceAccount:由 Kubernetes 管理的用于 Pod 内部进程的账户
- 资源(
Resources):Kubernetes API 中的对象,如 pods、services、deployments 等 - 操作(
Verbs):对资源的操作,如 get、list、create、update、delete 等 - 角色(
Roles):定义了一组权限规则(哪些操作可以对哪些资源执行)- Role:用于定义一组对 Kubernetes API 对象操作的一组规则,范围限定在单个 namespace
- ClusterRole:集群范围有效,可访问集群级资源或跨命名空间的资源
- 绑定(
Bindings):将角色与主体关联起来- RoleBinding:将 Role 绑定到主体,仅在单个命名空间内有效
- ClusterRoleBinding:将 ClusterRole 绑定到主体,集群范围有效
- Rule:规则,一组属于不同 API Group 的操作集合
鉴权: 鉴别权限 --》识别出某个主体(用户、组、服务账户)具有什么权限 —》鉴定权限
鉴定权限的目的: 保障安全 ,防止没有得到授权的用户访问我们的k8s资源,破坏k8s里的资源
RBAC: 基于角色的访问控制 —》鉴权
Role-based access control (RBAC) is a method of regulating access to computer or network resources based on the roles of individual users within your organization.
基于角色的访问控制(RBAC)是一种基于组织中各个用户的角色来调节对计算机或网络资源的访问的方法
用户 --》角色 --》权限–》资源对象
目的:防止k8s里的pod(会运行程序)能随意获取整个集群里的信息和访问集群里的资源
二、ServiceAccount使用
- 创建sa,并绑定到pod
[root@k8s-1 sa]# vim sa.yaml
apiVersion: v1
kind: Namespace
metadata:name: sanchuang
---
apiVersion: v1
kind: ServiceAccount
metadata:name: huangnamespace: sanchuang
[root@k8s-1 sa]# kubectl apply -f sa.yaml
namespace/sanchuang created
serviceaccount/huang created
[root@k8s-1 sa]# kubectl get sa
NAME SECRETS AGE
default 1 11d
[root@k8s-1 sa]# kubectl get sa -n sanchuang
NAME SECRETS AGE
default 1 17s
huang 1 17s# 命令创建
[root@k8s-1 sa]# kubectl create sa cjj -n sanchuang
serviceaccount/cjj created
[root@k8s-1 sa]# kubectl get sa -n sanchuang
NAME SECRETS AGE
cjj 1 2s
default 1 86s
huang 1 86s
- 创建pod
[root@k8s-1 sa]# cat sa-pod.yaml
apiVersion: v1
kind: Pod
metadata:name: sa-huangnamespace: sanchuanglabels:app: sa-huang
spec:serviceAccountName: huang # pod use service accoutcontainers:- name: sa-nginxports:- containerPort: 80image: nginximagePullPolicy: IfNotPresent
[root@k8s-1 sa]# kubectl apply -f sa-pod.yaml
pod/sa-huang created
[root@k8s-1 sa]# kubectl get pod -n sanchuang
NAME READY STATUS RESTARTS AGE
sa-huang 1/1 Running 0 16s
因为pod 会去访问k8s集群的apiserver,所以需要进入到pod里
初始状态下,SA 没有任何权限,访问 kube-system 命名空间时返回 403 Forbidden
[root@k8s-1 sa]# kubectl exec -n sanchuang -it sa-huang -- bash
root@sa-huang:/# cd /var/run/secrets/kubernetes.io/serviceaccount/
root@sa-huang:/var/run/secrets/kubernetes.io/serviceaccount# ls
ca.crt namespace token# 访问我们的apiserver,使用完整的域名
root@sa-huang:/var/run/secrets/kubernetes.io/serviceaccount# curl --cacert ./ca.crt -H "Authorization: Bearer $(cat ./token)" https://kubernetes.default.svc.cluster.local/api/v1/namespaces/kube-system
{"kind": "Status","apiVersion": "v1","metadata": {},"status": "Failure","message": "namespaces \"kube-system\" is forbidden: User \"system:serviceaccount:sanchuang:huang\" cannot get resource \"namespaces\" in API group \"\" in the namespace \"kube-system\"","reason": "Forbidden","details": {"name": "kube-system","kind": "namespaces"},"code": 403
}Kubernetes 内部服务的全限定域名(FQDN) 格式为
<service-name>.<namespace-name>.svc.<cluster-domain>
<service-name>:服务(Service)的名称,由用户在创建 Service 时定义(例如 nginx-service)
<namespace-name>:服务所在的命名空间(Namespace)名称(例如 default、kube-system)
svc:固定标识,代表这是一个 Kubernetes Service 的 DNS 记录("service" 的缩写)
<cluster-domain>:集群的基础域名,默认是 cluster.local(可通过集群配置自定义,例如 my-k8s-cluster.com)
查看集群角色
cluster-admin 这是一个权力非常大的clusterrole 集群角色
[root@k8s-1 sa]# kubectl get clusterrole
NAME CREATED AT
admin 2025-09-15T06:49:37Z
calico-kube-controllers 2025-09-15T08:25:22Z
calico-node 2025-09-15T08:25:22Z
cluster-admin 2025-09-15T06:49:37Z
# 查看详细信息
[root@k8s-1 sa]# kubectl describe clusterrole cluster-admin
Name: cluster-admin
Labels: kubernetes.io/bootstrapping=rbac-defaults
Annotations: rbac.authorization.kubernetes.io/autoupdate: true
PolicyRule:Resources Non-Resource URLs Resource Names Verbs--------- ----------------- -------------- -----*.* [] [] [*][*] [] [*]
- 对sa做授权
[root@k8s-1 sa]# kubectl create clusterrolebinding sa-test-huang --clusterrole=cluster-admin --serviceaccount=sanchuang:huang
clusterrolebinding.rbac.authorization.k8s.io/sa-test-huang created
- 访问namespace
[root@k8s-1 sa]# kubectl exec -n sanchuang -it sa-huang -- bash
root@sa-huang:/# cd /var/run/secrets/kubernetes.io/serviceaccount/
root@sa-huang:/var/run/secrets/kubernetes.io/serviceaccount# curl --cacert ./ca.crt -H "Authorization: Bearer $(cat ./token)" https://kubernetes.default.svc.cluster.local/api/v1/namespaces/kube-system
{"kind": "Namespace","apiVersion": "v1","metadata": {"name": "kube-system","uid": "b122bfb0-1529-442b-91f0-9b730b64d2a0","resourceVersion": "27","creationTimestamp": "2025-09-15T06:49:36Z","labels": {"kubernetes.io/metadata.name": "kube-system"},"managedFields": [{"manager": "kube-apiserver","operation": "Update","apiVersion": "v1","time": "2025-09-15T06:49:36Z","fieldsType": "FieldsV1","fieldsV1": {"f:metadata": {"f:labels": {".": {},"f:kubernetes.io/metadata.name": {}}}}}]},"spec": {"finalizers": ["kubernetes"]},"status": {"phase": "Active"}
}
查看整个k8s集群内部有那些资源
[root@k8s-1 sa]# kubectl api-resources
NAME SHORTNAMES APIVERSION NAMESPACED KIND
bindings v1 true Binding
componentstatuses cs v1 false ComponentStatus
configmaps cm v1 true ConfigMap
endpoints ep v1 true Endpoints
events ev v1 true Event
limitranges limits v1 true LimitRange
三、创建clusterrole访问
- 创建一个clusterrole -> secret-reader 集群角色(仅允许读取 secrets 资源)
[root@k8s-1 sa]# cat clusterrole.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:# "namespace" 被忽略,因为 ClusterRoles 不受名字空间限制name: secret-reader
rules:
- apiGroups: [""]# 在 HTTP 层面,用来访问 Secret 资源的名称为 "secrets"resources: ["secrets"] #具体的资源对象verbs: ["get", "watch", "list"] #动作
[root@k8s-1 sa]# kubectl apply -f clusterrole.yaml
clusterrole.rbac.authorization.k8s.io/secret-reader created
[root@k8s-1 sa]# kubectl get clusterrole|grep secret
secret-reader 2025-09-27T03:41:20Z
- 将cjj绑定到secret-reader 的集群角色上
[root@k8s-1 sa]# kubectl create clusterrolebinding sa-test-cjj --clusterrole=secret-reader --serviceaccount=sanchuang:cjj
clusterrolebinding.rbac.authorization.k8s.io/sa-test-cjj created
[root@k8s-1 sa]# cp sa-pod.yaml sa-pod-2.yaml
[root@k8s-1 sa]# vim sa-pod-2.yaml
apiVersion: v1
kind: Pod
metadata:name: sa-cjjnamespace: sanchuanglabels:app: sa-cjj
spec:serviceAccountName: cjj # pod use service accoutcontainers:- name: sa-nginxports:- containerPort: 80image: nginximagePullPolicy: IfNotPresent
[root@k8s-1 sa]# kubectl apply -f sa-pod-2.yaml
pod/sa-cjj created
[root@k8s-1 sa]# kubectl get pod -n sanchuang
NAME READY STATUS RESTARTS AGE
sa-cjj 1/1 Running 0 7s
sa-huang 1/1 Running 0 42m
- 验证:进入huang启动的pod,去访问apiserver里的pods资源和secrets资源
[root@k8s-1 sa]# kubectl exec -n sanchuang -it sa-cjj -- bash
root@sa-cjj:/# cd /var/run/secrets/kubernetes.io/serviceaccount/
root@sa-cjj:/var/run/secrets/kubernetes.io/servieaccount# curl --cacert ./ca.crt -H "Authorization: Bearer $(cat ./token)" https://kubernetes.default.svc.cluster.local/api/v1/namespaces/kube-system
root@sa-cjj:/var/run/secrets/kubernetes.io/serviceaccount# curl --cacert ./ca.crt -H "Authorization: Bearer $(cat ./token)" https://kubernetes.default.svc.cluster.local/api/v1/secrets
四、普通用户访问
ssl认证: 需要使用root用户去创建证书
生成一个证书
# 生成一个私钥
[root@k8s-1 ~]# cd /etc/kubernetes/pki/
[root@k8s-1 pki]# (umask 077; openssl genrsa -out xa.key 2048) # 生成一个证书请求
[root@k8s-1 pki]# openssl req -new -key xa.key -out xa.csr -subj "/CN=xa"# 生成一个CA签名的公钥证书
[root@k8s-1 pki]# openssl x509 -req -in xa.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out xa.crt -days 3650
Certificate request self-signature ok
subject=CN=xa
在kubeconfig下新增加一个xa这个用户
# 把xa这个用户添加到kubernetes集群中,可以用来认证apiserver的连接
[root@k8s-1 pki]# kubectl config set-credentials xa --client-certificate=./xa.crt --client-key=./xa.key --embed-certs=true
User "xa" set.# 可以去/root/.kube/config文件里查看,有xa的信息# 在kubeconfig下新增加一个xa这个账号,相当于在~/.kube/config添加xa用户
[root@k8s-1 pki]# kubectl config set-context xa@kubernetes --cluster=kubernetes --user=xa
Context "xa@kubernetes" created.# 切换账号到xa,默认没有任何权限
[root@k8s-1 pki]# kubectl config use-context xa@kubernetes
Switched to context "xa@kubernetes".[root@k8s-1 pki]# kubectl get node
Error from server (Forbidden): nodes is forbidden: User "xa" cannot list resource "nodes" in API group "" at the cluster scope# 发现xa这个k8s里的用户不能访问api server
#没有任何权限,然后使用下面的命令切换回去kubernetes-admin@kubernetes用户[root@k8s-1 pki]# kubectl config use-context kubernetes-admin@kubernetes
Switched to context "kubernetes-admin@kubernetes".
把xa 这个用户通过rolebinding绑定到clusterrole上,授予权限,权限只是在xa这个名称空间有效
# 把xa这个用户通过rolebinding绑定到clusterrole上
[root@k8s-1 pki]# kubectl create ns xa-test
namespace/xa-test created
[root@k8s-1 pki]# kubectl create rolebinding xa -n xa-test --clusterrole=cluster-admin --user=xa
rolebinding.rbac.authorization.k8s.io/xa created# 切换到xa这个用户
[root@k8s-1 pki]# kubectl config use-context xa@kubernetes
Switched to context "xa@kubernetes".# 测试是否有权限
[root@k8s-1 pki]# kubectl get node
Error from server (Forbidden): nodes is forbidden: User "xa" cannot list resource "nodes" in API group "" at the cluster scope# 查看xa-test命名空间就可以,有权限操作这个xa-test名称空间
[root@k8s-1 pki]# kubectl get pods -n xa-test
No resources found in xa-test namespace.
五、Linux 系统用户与 Kubernetes 用户账号的关联,达成多租户权限隔离

在linux操作系统里创建xa这个用户,可以用来登录k8s集群所在的linux系统
不同租户给与不同的linux系统账号,然后关联不同的k8s集群里的useraccount
添加一个xa的普通用户
[root@k8s-1 pki]# useradd xa
[root@k8s-1 pki]# echo "xa:123456"|chpasswd
[root@k8s-1 pki]# cp -ar /root/.kube/ /home/xa/
[root@k8s-1 pki]# chown -R xa:xa /home/xa
修改/home/xa/.kube/config文件,把kubernetes-admin相关的删除,只留xa用户
[root@k8s-1 pki]# cd /home/xa/.kube
[root@k8s-1 .kube]# ls
cache config
# 删除kubernetes-admin后相关的效果如下:
[root@k8s-1 .kube]# cat config
apiVersion: v1
clusters:
- cluster:certificate-authority-data: ...server: https://192.168.168.145:6443name: kubernetes
contexts:
- context:cluster: kubernetesuser: kubernetes-adminname: kubernetes-admin@kubernetes
- context:cluster: kubernetesuser: xaname: xa@kubernetes
current-context: xa@kubernetes
kind: Config
preferences: {}
users:
- name: xauser:client-certificate-data: ...client-key-data: ...
使用xa登录linux系统
[root@k8s-1 .kube]# su - xa
# 不可以访问default命名空间
[xa@k8s-1 ~]$ kubectl get pods
Error from server (Forbidden): pods is forbidden: User "xa" cannot list resource "pods" in API group "" in the namespace "default"
# 可以访问xa-test命名空间
[xa@k8s-1 ~]$ kubectl get pods -n xa-test
No resources found in xa-test namespace.
退出xa用户返回到root用户,需要在把集群环境切换成管理员权限
[xa@k8s-1 ~]$ exit
logout
[root@k8s-1 .kube]# kubectl get pods
Error from server (Forbidden): pods is forbidden: User "xa" cannot list resource "pods" in API group "" in the namespace "default"# 把集群环境切换成管理员权限,就可以查看pod的资源
[root@k8s-1 .kube]# kubectl config use-context kubernetes-admin@kubernetes
Switched to context "kubernetes-admin@kubernetes".
