关于网站篡改应急演练剧本编写(模拟真实场景)
应急演练是网络安全服务项目里很常见的一个服务项,那么要怎么去实施模拟真实场景去实现应急演练。
一、模拟网站
现在很多网站都可以直接通过右键另存为然后保存到本地上,但是保存到本地上的网站会多多少少缺点东西,现在的图片资源基本上都有防盗链,或者路径由图床改成了本地的相对路径,单纯的复制粘贴很难把网站复制下来。导致页面不是很真实总是东缺什么西缺什么。客户看着这也不像我们网站。不够模拟真实场景下的操作。
HTTrack Website Copier是开源的工具,可以从互联网上下载指定的网站进行线下浏览(离线浏览),也可以用来收集信息(甚至有网站使用隐藏的密码文件),一些仿真度极高的伪网站(为了骗取用户密码),也是使用类似工具做的。
搭建模拟网站要怎么搭呢?
大部分的官方网站都有防护(意思是没有漏洞),我们要怎么去创造漏洞是一个问题,所以选择什么搭建平台是最重要的。我一般会选择使用phpstudy进行搭建网站。因为phpstudy会自带一个phpmyadmin和phpinfo和php探针,然后phpmyadmin是可以写入webshell的漏洞。
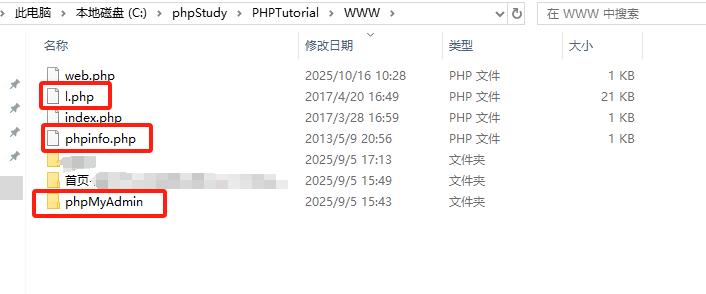
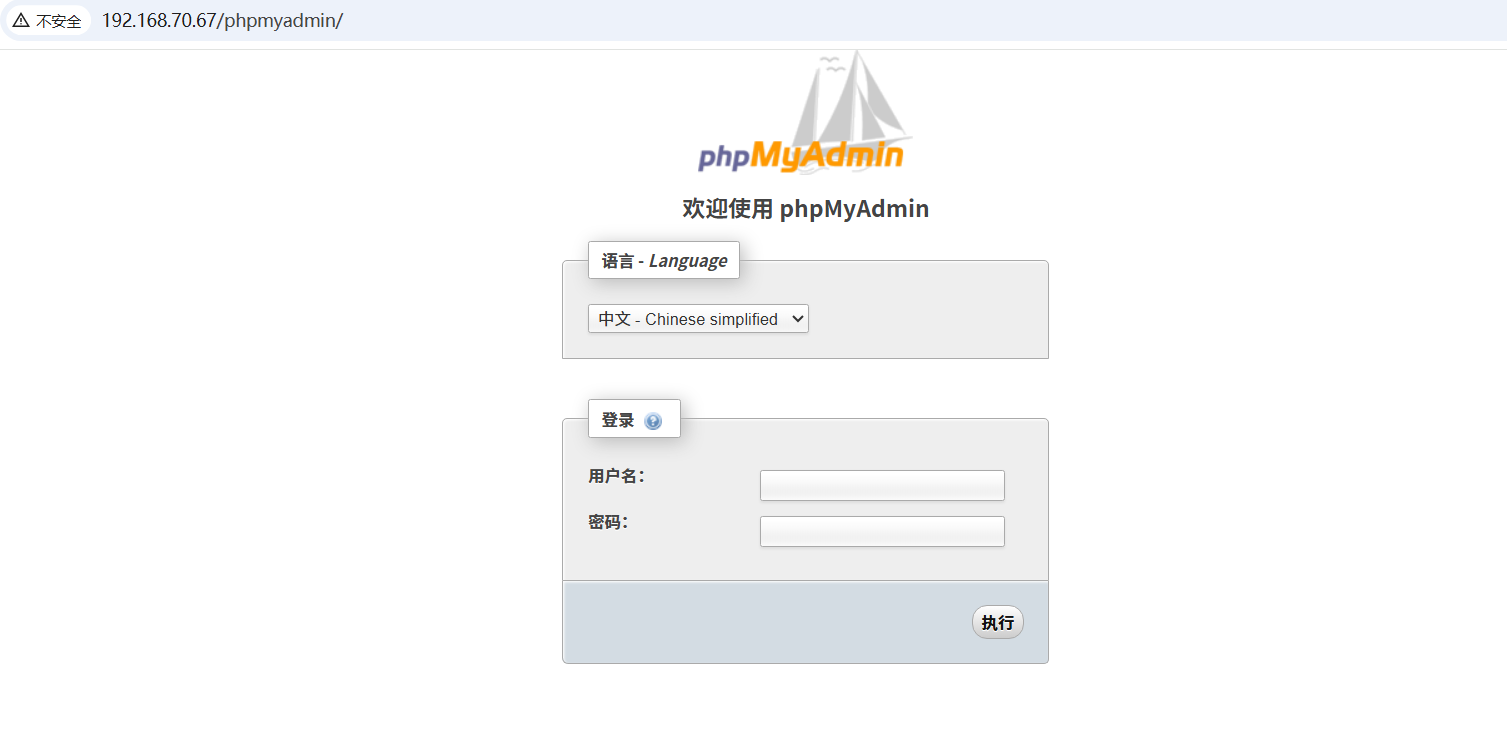
二、篡改网站
篡改网站要怎么去构造呢?我一般是将原网站的index.html换成其他后缀然后将自己弄的篡改后的网站改为index.html。篡改网站要怎么构造呢?我这里有一个感觉还可以
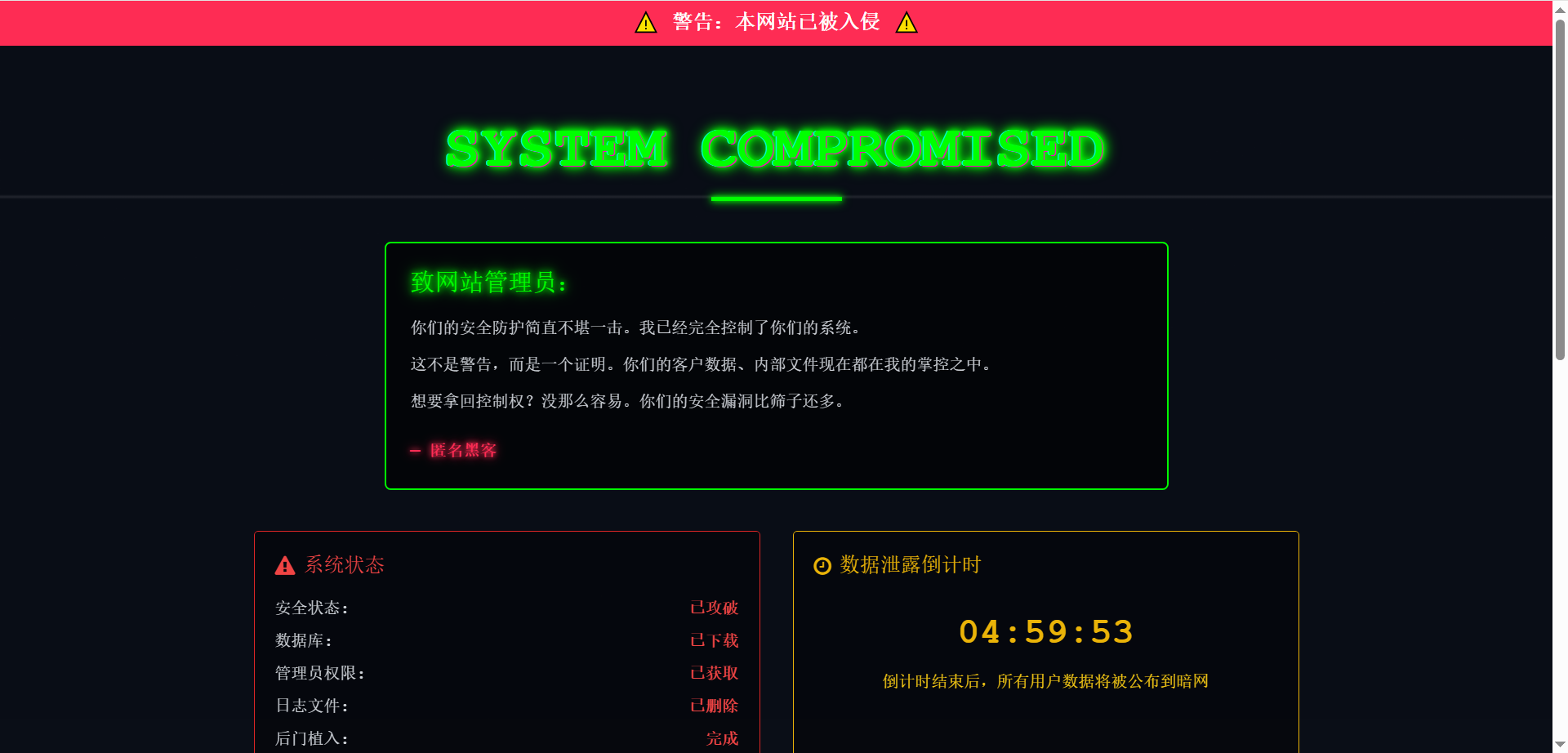
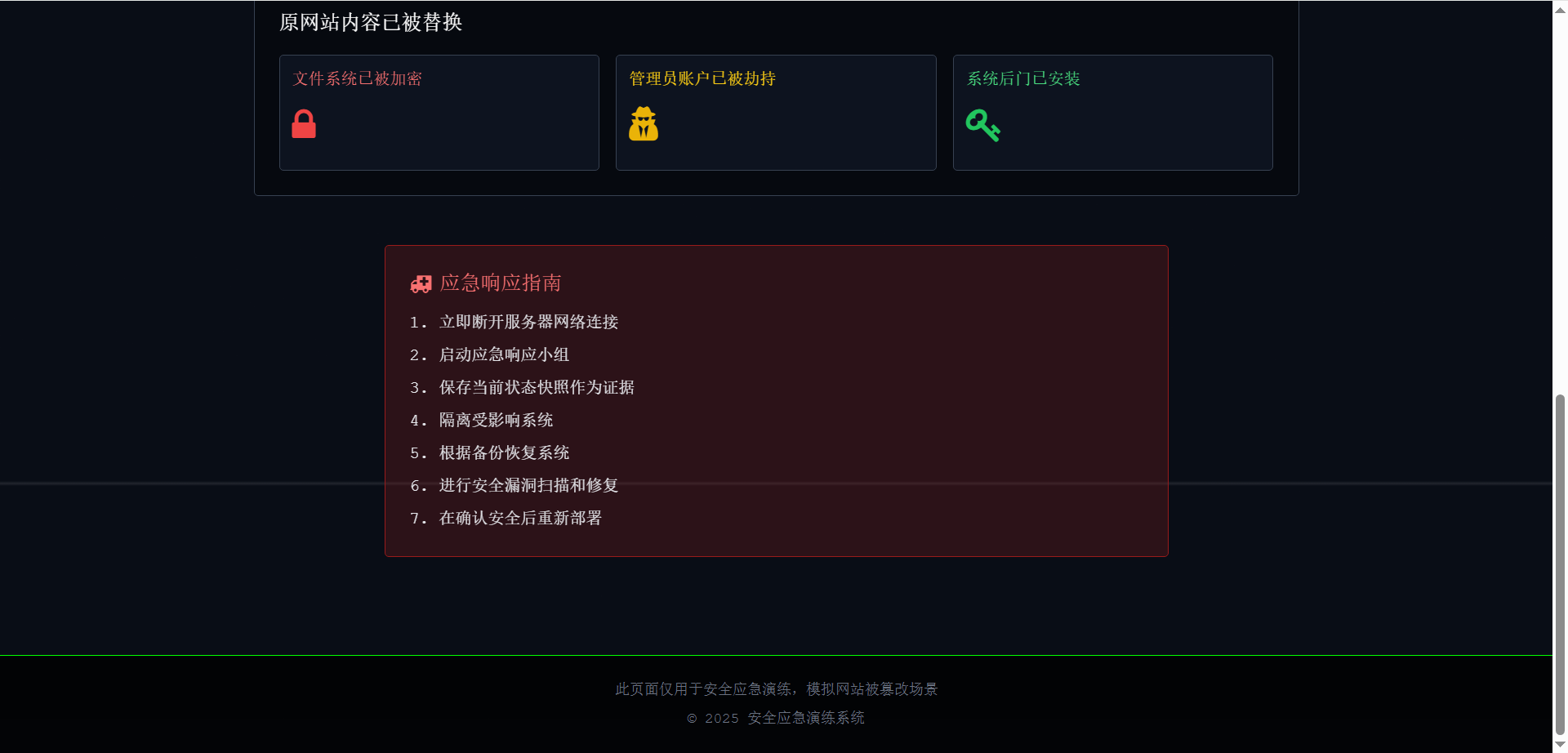
网站代码在下面
<!DOCTYPE html>
<html lang="zh-CN">
<head><meta charset="UTF-8"><meta name="viewport" content="width=device-width, initial-scale=1.0"><title>网站已被入侵 - 应急演练</title><script src="https://cdn.tailwindcss.com"></script><link href="https://cdn.jsdelivr.net/npm/font-awesome@4.7.0/css/font-awesome.min.css" rel="stylesheet"><script>// 配置Tailwind自定义颜色和字体tailwind.config = {theme: {extend: {colors: {hack: {red: '#ff2d55',dark: '#121212',glow: '#00ff00',darkblue: '#0a0e17'}},fontFamily: {mono: ['Courier New', 'monospace']}}}}</script><style type="text/tailwindcss">@layer utilities {.text-shadow-glow {text-shadow: 0 0 5px #00ff00, 0 0 10px #00ff00, 0 0 15px #00ff00;}.text-shadow-red {text-shadow: 0 0 5px #ff2d55, 0 0 10px #ff2d55;}.border-glow {box-shadow: 0 0 5px #00ff00, 0 0 10px #00ff00;}.scanline {background: linear-gradient(to bottom, rgba(255,255,255,0) 0%,rgba(255,255,255,0.1) 50%,rgba(255,255,255,0) 100%);position: absolute;width: 100%;height: 5px;animation: scan 6s linear infinite;}@keyframes scan {0% { top: 0; }100% { top: 100%; }}.flicker {animation: flicker 0.3s infinite alternate;}@keyframes flicker {0%, 19.999%, 22%, 62.999%, 64%, 64.999%, 70%, 100% { opacity: 1; }20%, 21.999%, 63%, 63.999%, 65%, 69.999% { opacity: 0.4; }}.glitch {position: relative;}.glitch::before, .glitch::after {content: attr(data-text);position: absolute;top: 0;left: 0;width: 100%;height: 100%;}.glitch::before {left: 2px;text-shadow: -1px 0 #ff00c1;clip: rect(44px, 450px, 56px, 0);animation: glitch-anim 5s infinite linear alternate-reverse;}.glitch::after {left: -2px;text-shadow: -1px 0 #00fff9, 1px 1px #ff00c1;clip: rect(24px, 450px, 36px, 0);animation: glitch-anim2 1s infinite linear alternate-reverse;}@keyframes glitch-anim {0% { clip: rect(42px, 9999px, 44px, 0); }5% { clip: rect(12px, 9999px, 59px, 0); }10% { clip: rect(48px, 9999px, 29px, 0); }15% { clip: rect(42px, 9999px, 73px, 0); }20% { clip: rect(63px, 9999px, 27px, 0); }25% { clip: rect(34px, 9999px, 55px, 0); }30% { clip: rect(86px, 9999px, 73px, 0); }35% { clip: rect(20px, 9999px, 20px, 0); }40% { clip: rect(26px, 9999px, 60px, 0); }45% { clip: rect(25px, 9999px, 66px, 0); }50% { clip: rect(57px, 9999px, 98px, 0); }55% { clip: rect(5px, 9999px, 46px, 0); }60% { clip: rect(82px, 9999px, 31px, 0); }65% { clip: rect(54px, 9999px, 27px, 0); }70% { clip: rect(28px, 9999px, 99px, 0); }75% { clip: rect(45px, 9999px, 69px, 0); }80% { clip: rect(23px, 9999px, 85px, 0); }85% { clip: rect(54px, 9999px, 84px, 0); }90% { clip: rect(45px, 9999px, 47px, 0); }95% { clip: rect(37px, 9999px, 20px, 0); }100% { clip: rect(4px, 9999px, 91px, 0); }}@keyframes glitch-anim2 {0% { clip: rect(65px, 9999px, 100px, 0); }5% { clip: rect(52px, 9999px, 74px, 0); }10% { clip: rect(79px, 9999px, 85px, 0); }15% { clip: rect(75px, 9999px, 5px, 0); }20% { clip: rect(67px, 9999px, 61px, 0); }25% { clip: rect(14px, 9999px, 79px, 0); }30% { clip: rect(1px, 9999px, 66px, 0); }35% { clip: rect(86px, 9999px, 30px, 0); }40% { clip: rect(23px, 9999px, 98px, 0); }45% { clip: rect(85px, 9999px, 72px, 0); }50% { clip: rect(71px, 9999px, 75px, 0); }55% { clip: rect(2px, 9999px, 48px, 0); }60% { clip: rect(30px, 9999px, 16px, 0); }65% { clip: rect(59px, 9999px, 50px, 0); }70% { clip: rect(41px, 9999px, 62px, 0); }75% { clip: rect(2px, 9999px, 82px, 0); }80% { clip: rect(47px, 9999px, 73px, 0); }85% { clip: rect(3px, 9999px, 27px, 0); }90% { clip: rect(26px, 9999px, 55px, 0); }95% { clip: rect(42px, 9999px, 97px, 0); }100% { clip: rect(38px, 9999px, 49px, 0); }}}</style>
</head>
<body class="bg-hack-darkblue text-gray-300 min-h-screen font-mono relative overflow-x-hidden"><!-- 扫描线效果 --><div class="scanline"></div><!-- 顶部警告栏 --><div class="bg-hack-red text-white py-2 px-4 text-center flicker"><p class="text-lg md:text-xl font-bold">⚠️ 警告:本网站已被入侵 ⚠️</p></div><!-- 主内容区 --><div class="container mx-auto px-4 py-8 relative z-10"><!-- 黑客标志/标题 --><div class="text-center my-10"><h1 class="text-4xl md:text-6xl font-bold text-hack-glow text-shadow-glow mb-4 glitch" data-text="SYSTEM COMPROMISED">SYSTEM COMPROMISED</h1><div class="w-32 h-1 bg-hack-glow mx-auto border-glow"></div></div><!-- 黑客留言区 --><div class="max-w-3xl mx-auto bg-black/60 p-6 border-2 border-hack-glow rounded-md mb-10"><h2 class="text-2xl text-hack-glow text-shadow-glow mb-4">致网站管理员:</h2><p class="mb-3">你们的安全防护简直不堪一击。我已经完全控制了你们的系统。</p><p class="mb-3">这不是警告,而是一个证明。你们的客户数据、内部文件现在都在我的掌控之中。</p><p class="mb-3">想要拿回控制权?没那么容易。你们的安全漏洞比筛子还多。</p><p class="text-hack-red text-shadow-red mt-6 font-bold">— 匿名黑客</p></div><!-- 篡改内容展示 --><div class="grid grid-cols-1 md:grid-cols-2 gap-8 max-w-5xl mx-auto"><!-- 左侧:系统信息被篡改 --><div class="bg-black/40 p-5 rounded border border-red-600"><h3 class="text-xl text-red-500 mb-4 flex items-center"><i class="fa fa-exclamation-triangle mr-2"></i>系统状态</h3><ul class="space-y-2"><li class="flex justify-between"><span>安全状态:</span> <span class="text-red-500 font-bold">已攻破</span></li><li class="flex justify-between"><span>数据库:</span> <span class="text-red-500 font-bold">已下载</span></li><li class="flex justify-between"><span>管理员权限:</span> <span class="text-red-500 font-bold">已获取</span></li><li class="flex justify-between"><span>日志文件:</span> <span class="text-red-500 font-bold">已删除</span></li><li class="flex justify-between"><span>后门植入:</span> <span class="text-red-500 font-bold">完成</span></li></ul></div><!-- 右侧:倒计时/威胁 --><div class="bg-black/40 p-5 rounded border border-yellow-500"><h3 class="text-xl text-yellow-500 mb-4 flex items-center"><i class="fa fa-clock-o mr-2"></i>数据泄露倒计时</h3><div class="text-center py-4"><div id="countdown" class="text-4xl font-bold text-yellow-500">05:00:00</div><p class="mt-4 text-yellow-400">倒计时结束后,所有用户数据将被公布到暗网</p></div></div></div><!-- 被篡改的页面内容 --><div class="max-w-5xl mx-auto mt-10 bg-black/30 p-6 rounded border border-gray-700"><h3 class="text-xl text-white mb-4">原网站内容已被替换</h3><div class="grid grid-cols-1 md:grid-cols-3 gap-4"><div class="bg-gray-900/70 p-3 rounded border border-gray-700"><p class="text-red-400">文件系统已被加密</p><i class="fa fa-lock text-4xl text-center my-3 text-red-500"></i></div><div class="bg-gray-900/70 p-3 rounded border border-gray-700"><p class="text-yellow-400">管理员账户已被劫持</p><i class="fa fa-user-secret text-4xl text-center my-3 text-yellow-500"></i></div><div class="bg-gray-900/70 p-3 rounded border border-gray-700"><p class="text-green-400">系统后门已安装</p><i class="fa fa-key text-4xl text-center my-3 text-green-500"></i></div></div></div><!-- 应急响应提示 --><div class="max-w-3xl mx-auto mt-12 bg-red-900/30 p-6 rounded border border-red-800"><h3 class="text-xl text-red-400 mb-3 flex items-center"><i class="fa fa-ambulance mr-2"></i>应急响应指南</h3><ol class="list-decimal list-inside space-y-2 text-gray-200"><li>立即断开服务器网络连接</li><li>启动应急响应小组</li><li>保存当前状态快照作为证据</li><li>隔离受影响系统</li><li>根据备份恢复系统</li><li>进行安全漏洞扫描和修复</li><li>在确认安全后重新部署</li></ol></div></div><!-- 底部信息 --><footer class="mt-16 py-6 bg-black/70 border-t border-hack-glow"><div class="container mx-auto px-4 text-center text-gray-500 text-sm"><p>此页面仅用于安全应急演练,模拟网站被篡改场景</p><p class="mt-2">© 2025 安全应急演练系统</p></div></footer><!-- 背景噪点效果 --><div class="fixed inset-0 pointer-events-none z-0 opacity-10" id="noise"></div><script>// 生成背景噪点function createNoise() {const noise = document.getElementById('noise');const canvas = document.createElement('canvas');const ctx = canvas.getContext('2d');const width = window.innerWidth;const height = window.innerHeight;canvas.width = width;canvas.height = height;const imageData = ctx.createImageData(width, height);const data = imageData.data;for (let i = 0; i < data.length; i += 4) {const value = Math.random() * 255;data[i] = value;data[i + 1] = value;data[i + 2] = value;data[i + 3] = 10;}ctx.putImageData(imageData, 0, 0);noise.appendChild(canvas);}// 倒计时功能function startCountdown() {const countdownEl = document.getElementById('countdown');let hours = 5;let minutes = 0;let seconds = 0;const updateCountdown = () => {if (seconds === 0) {if (minutes === 0) {if (hours === 0) {countdownEl.textContent = "数据已泄露!";return;}hours--;minutes = 59;} else {minutes--;}seconds = 59;} else {seconds--;}const hh = hours.toString().padStart(2, '0');const mm = minutes.toString().padStart(2, '0');const ss = seconds.toString().padStart(2, '0');countdownEl.textContent = `${hh}:${mm}:${ss}`;};updateCountdown();setInterval(updateCountdown, 1000);}// 随机文字闪烁效果function randomFlicker() {const elements = document.querySelectorAll('p, li, h3');setInterval(() => {const randomIndex = Math.floor(Math.random() * elements.length);const element = elements[randomIndex];element.classList.add('flicker');setTimeout(() => {element.classList.remove('flicker');}, 300);}, 2000);}// 页面加载完成后初始化window.addEventListener('load', () => {createNoise();startCountdown();randomFlicker();// 随机生成一些干扰性文字setInterval(() => {const glitchText = document.createElement('div');glitchText.classList.add('absolute', 'text-hack-glow', 'opacity-30', 'text-shadow-glow', 'flicker');glitchText.style.left = `${Math.random() * 100}vw`;glitchText.style.top = `${Math.random() * 100}vh`;glitchText.style.fontSize = `${Math.random() * 20 + 10}px`;glitchText.textContent = 'ACCESS GRANTED';document.body.appendChild(glitchText);setTimeout(() => {glitchText.remove();}, 1500);}, 5000);});</script>
</body>
</html>
三、模拟应急演练
这里就可以开始写剧本了,涉及到web安全事件管理了,我就说一下我大概是通过phpmyadmin进行上传webshell然后更改index.html文件。然后告警触发,开始走应急响应流程。就这样结束了。通过溯源找到webshell然后更改回源文件 删除phpmyadmin和phpinfo等漏洞存在的地方。结束
