termsrv!InitializeSystemTrace函数分析开启调试TraceEnable和TraceClass和TraceDebugger
termsrv!InitializeSystemTrace函数分析开启调试TraceEnable和TraceClass和TraceDebugger
第一部分:
void InitializeSystemTrace(HKEY hKeyTermSrv)
{
ICA_TRACE Trace;
NTSTATUS Status;
WCHAR SystemDir[256];
DWORD ValueType;
DWORD ValueSize;
ULONG fDebugger;
UINT uiWinDirSize;
ASSERT(hKeyTermSrv != NULL);
RtlZeroMemory( &Trace , sizeof( ICA_TRACE ) );
/*
* Query trace enable flag
*/
ValueSize = sizeof(Trace.TraceEnable);
Status = RegQueryValueEx(hKeyTermSrv, WIN_TRACEENABLE, NULL, &ValueType,
(LPBYTE) &Trace.TraceEnable, &ValueSize);
if (Status == ERROR_SUCCESS && Trace.TraceEnable != 0) {
/*
* Query trace class flag
*/
ValueSize = sizeof(Trace.TraceClass);
Status = RegQueryValueEx(hKeyTermSrv, WIN_TRACECLASS, NULL,
&ValueType, (LPBYTE)&Trace.TraceClass, &ValueSize);
if (Status != ERROR_SUCCESS) {
Trace.TraceClass = 0xffffffff;
}
/*
* Query trace to debugger flag
*/
ValueSize = sizeof(fDebugger);
Status = RegQueryValueEx(hKeyTermSrv, WIN_TRACEDEBUGGER, NULL,
&ValueType, (LPBYTE)&fDebugger, &ValueSize);
if (Status != ERROR_SUCCESS) {
fDebugger = FALSE;
}
Trace.fDebugger = (BOOLEAN)fDebugger;
Trace.fTimestamp = TRUE;
uiWinDirSize = GetWindowsDirectory(SystemDir, sizeof(SystemDir)/sizeof(WCHAR));
if ((uiWinDirSize == 0) ||
((uiWinDirSize + wcslen(L"\\ICADD.log") + 1) > sizeof(Trace.TraceFile)/sizeof(WCHAR)))
{
// we failed to get the windows directory or we dont have enough buffer for the logfile.
Trace.TraceEnable = 0;
}
else
{
wsprintf(Trace.TraceFile, L"%s\\ICADD.log", SystemDir);
/*
* Open TermDD.
*/
Status = IcaOpen(&hTrace);
if (NT_SUCCESS(Status)) {
Status = IcaIoControl(hTrace, IOCTL_ICA_SET_SYSTEM_TRACE, &Trace,
sizeof(Trace), NULL, 0, NULL);
if (!NT_SUCCESS(Status)) {
IcaClose(hTrace);
hTrace = NULL;
}
}
KdPrintEx((DPFLTR_TERMSRV_ID, DPFLTR_TRACE_LEVEL, "TRACE: %S, c:%x, e:%x d:%d, Status=0x%x\n", Trace.TraceFile,
Trace.TraceClass, Trace.TraceEnable, Trace.fDebugger, Status ));
}
}
}
第二部分:
#define REG_CONTROL L"System\\CurrentControlSet\\Control"
#define REG_CONTROL_A "System\\CurrentControlSet\\Control"
#define REG_NTAPI_CONTROL L"\\Registry\\Machine\\" REG_CONTROL
#define REG_TSERVER L"Terminal Server"
#define REG_TSERVER_A "Terminal Server"
/*
* CONTROL key defines
*/
#define REG_CONTROL_TSERVER REG_CONTROL L"\\" REG_TSERVER
#define REG_CONTROL_TSERVER_A REG_CONTROL_A "\\" REG_TSERVER_A
#define WIN_TRACEENABLE L"TraceEnable"
#define WIN_TRACEENABLE_A "TraceEnable"
#define WIN_TRACECLASS L"TraceClass"
#define WIN_TRACECLASS_A "TraceClass"
#define WIN_TRACEDEBUGGER L"TraceDebugger"
#define WIN_TRACEDEBUGGER_A "TraceDebugger"
#define WIN_TRACEOPTION L"TraceOption"
WIN_TRACEENABLE regapi.h (public\internal\termsrv\inc)
第三部分:
0: kd> kc
#
00 termsrv!InitializeSystemTrace
01 termsrv!ServiceMain
02 svchost!ServiceStarter
03 ADVAPI32!ScSvcctrlThreadA
04 kernel32!BaseThreadStart
0: kd> kv
# ChildEBP RetAddr Args to Child
00 007fff44 74882e19 00000464 77e5e963 77e662fd termsrv!InitializeSystemTrace (FPO: [Non-Fpo]) (CONV: stdcall) [d:\srv03rtm\termsrv\winsta\server\misc.c @ 87]
01 007fff6c 01002ed6 00000001 00084870 00000000 termsrv!ServiceMain+0x2f5 (FPO: [Non-Fpo]) (CONV: stdcall) [d:\srv03rtm\termsrv\winsta\server\icasrv.c @ 699]
02 007fffa4 77dc0bd4 00000001 00084870 00000000 svchost!ServiceStarter+0x132 (FPO: [Non-Fpo]) (CONV: stdcall) [d:\srv03rtm\base\screg\sc\svchost\svchost.c @ 1049]
03 007fffb8 77e41be7 00084868 00000000 00000000 ADVAPI32!ScSvcctrlThreadA+0x10 (FPO: [Non-Fpo]) (CONV: stdcall) [d:\srv03rtm\base\screg\sc\client\scapi.cxx @ 2760]
04 007fffec 00000000 77dc0bc4 00084868 00000000 kernel32!BaseThreadStart+0x34 (FPO: [Non-Fpo]) (CONV: stdcall) [d:\srv03rtm\base\win32\client\support.c @ 533]
0: kd> dv
hKeyTermSrv = 0x00000464
SystemDir = unsigned short [256]
ValueSize = 0x33004c
Trace = struct _ICA_TRACE
ValueType = 0x480053
fDebugger = 0x4c0045
0: kd> !handle 0x00000464
PROCESS 8987ba48 SessionId: 0 Cid: 02f4 Peb: 7ffdf000 ParentCid: 01f4
DirBase: 79d1e000 ObjectTable: e172c440 HandleCount: 85.
Image: svchost.exe
Handle table at e172c440 with 85 entries in use
0464: Object: e1724688 GrantedAccess: 00020019 Entry: e17428c8
Object: e1724688 Type: (89996048) Key
ObjectHeader: e1724670 (old version)
HandleCount: 1 PointerCount: 1
Directory Object: 00000000 Name: \REGISTRY\MACHINE\SYSTEM\CONTROLSET001\CONTROL\TERMINAL SERVER
0: kd> p
termsrv!InitializeSystemTrace+0x6c:
001b:74896c67 85c0 test eax,eax
0: kd> dv
hKeyTermSrv = 0x00000464
SystemDir = unsigned short [256]
ValueSize = 4
Trace = struct _ICA_TRACE
ValueType = 4
fDebugger = 0x4c0045
0: kd> dx -id 0,0,8987ba48 -r1 (*((termsrv!_ICA_TRACE *)0x7ffcb4))
(*((termsrv!_ICA_TRACE *)0x7ffcb4)) [Type: _ICA_TRACE]
[+0x000] TraceFile [Type: unsigned short [256]]
[+0x200] fDebugger : 0x0 [Type: unsigned char]
[+0x201] fTimestamp : 0x0 [Type: unsigned char]
[+0x204] TraceClass : 0x0 [Type: unsigned long]
[+0x208] TraceEnable : 0xffffffff [Type: unsigned long]
[+0x20c] TraceOption [Type: unsigned short [64]]
0: kd> p
termsrv!InitializeSystemTrace+0xe1:
001b:74896cdc 8a8568fbffff mov al,byte ptr [ebp-498h]
0: kd> dv
hKeyTermSrv = 0x00000464
SystemDir = unsigned short [256]
ValueSize = 4
Trace = struct _ICA_TRACE
ValueType = 4
fDebugger = 1
0: kd> dx -id 0,0,8987ba48 -r1 (*((termsrv!_ICA_TRACE *)0x7ffcb4))
(*((termsrv!_ICA_TRACE *)0x7ffcb4)) [Type: _ICA_TRACE]
[+0x000] TraceFile [Type: unsigned short [256]]
[+0x200] fDebugger : 0x0 [Type: unsigned char]
[+0x201] fTimestamp : 0x0 [Type: unsigned char]
[+0x204] TraceClass : 0xffffffff [Type: unsigned long]
[+0x208] TraceEnable : 0xffffffff [Type: unsigned long]
[+0x20c] TraceOption [Type: unsigned short [64]]
0: kd> !handle 0x00000464
PROCESS 8987ba48 SessionId: 0 Cid: 02f4 Peb: 7ffdf000 ParentCid: 01f4
DirBase: 79d1e000 ObjectTable: e172c440 HandleCount: 85.
Image: svchost.exe
Handle table at e172c440 with 85 entries in use
0464: Object: e1724688 GrantedAccess: 00020019 Entry: e17428c8
Object: e1724688 Type: (89996048) Key
ObjectHeader: e1724670 (old version)
HandleCount: 1 PointerCount: 1
Directory Object: 00000000 Name: \REGISTRY\MACHINE\SYSTEM\CONTROLSET001\CONTROL\TERMINAL SERVER
wsprintf(Trace.TraceFile, L"%s\\ICADD.log", SystemDir);
0: kd> x termsrv!htrace
748b5008 termsrv!hTrace = 0x000005b4
0: kd> !handle 0x000005b4
PROCESS 8987ba48 SessionId: 0 Cid: 02f4 Peb: 7ffdf000 ParentCid: 01f4
DirBase: 79d1e000 ObjectTable: e172c440 HandleCount: 86.
Image: svchost.exe
Handle table at e172c440 with 86 entries in use
05b4: Object: 898e8bb8 GrantedAccess: 0012019f Entry: e1742b68
Object: 898e8bb8 Type: (89987710) File
ObjectHeader: 898e8ba0 (old version)
HandleCount: 1 PointerCount: 1
第四部分:
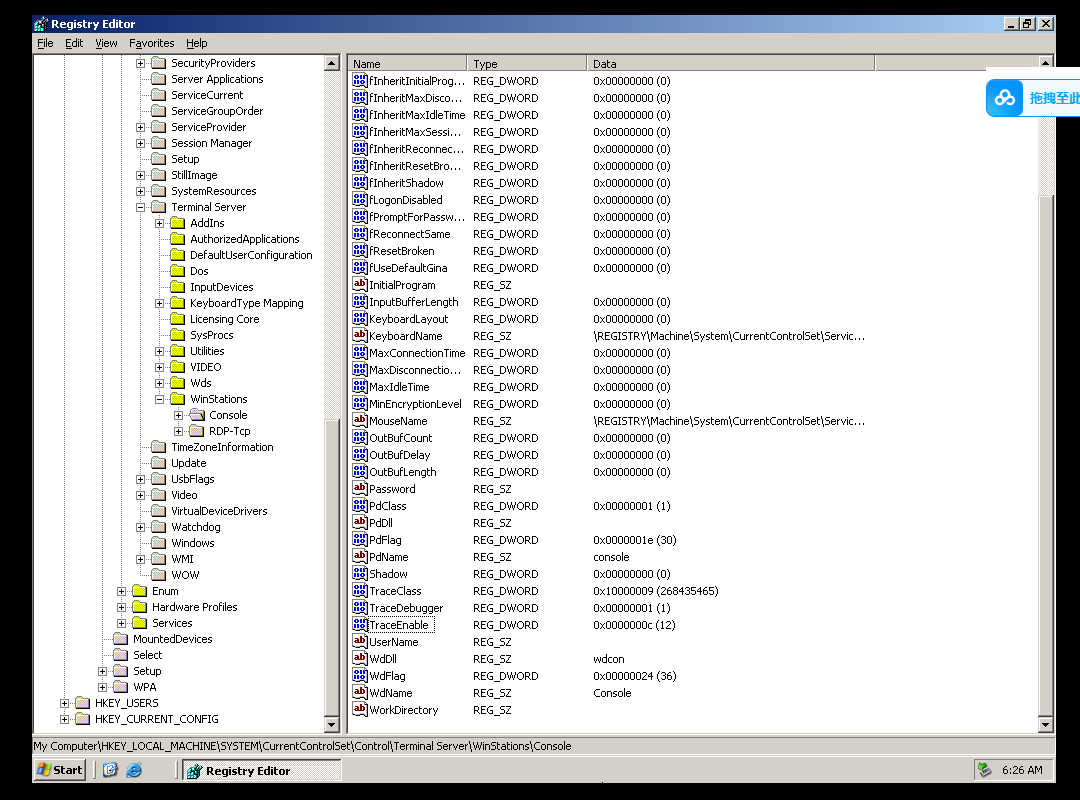
上边的图是和termsrv!InitializeTrace有关的
WinStations-Console-TraceClass-TraceDebugger-TraceEnable
第五部分:
通过网盘分享的文件:TERMSRV开启调试后调试日志.txt
链接: https://pan.baidu.com/s/14slaGD0WehoInx0pOGLxKg?pwd=3790 提取码: 3790
--来自百度网盘超级会员v8的分享
调试内容:开始没有登录,无法远程桌面
第二,登录后,开启远程桌面。
第三,远程登录
第六部分:
通过网盘分享的文件:TERMSRV开启调试后调试日志2远程登录后断开连接.txt
链接: https://pan.baidu.com/s/1vl3GqKxDzpmp17DXT9gs-g?pwd=3790 提取码: 3790
--来自百度网盘超级会员v8的分享
